| File name: | UmmyVD-Web-Loader-110.exe |
| Full analysis: | https://app.any.run/tasks/31b5a992-201a-4702-b371-d591baefabb5 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2024, 13:05:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 8F9EEEA1DF75607D37E493297DB30CCB |
| SHA1: | 56BEB570D2BFC708EFDA1CD55754E563D2DF9D86 |
| SHA256: | B672198BD63B9C13DA35133E1C39BF5781631A396D69E7FB2C3AE6AF701FEB30 |
| SSDEEP: | 12288:oURbq9E44hatZZ7vRCgvQElXtDtmAA5IfH+VKlqt7:oURbpavVvRCCPA5IfH+VD |
MALICIOUS
Drops the executable file immediately after the start
- UmmyVD-Web-Loader-110.exe (PID: 3384)
SUSPICIOUS
Reads security settings of Internet Explorer
- UmmyVD-Web-Loader-110.exe (PID: 3384)
Reads the Internet Settings
- UmmyVD-Web-Loader-110.exe (PID: 3384)
Process requests binary or script from the Internet
- UmmyVD-Web-Loader-110.exe (PID: 3384)
Reads settings of System Certificates
- UmmyVD-Web-Loader-110.exe (PID: 3384)
INFO
Checks supported languages
- UmmyVD-Web-Loader-110.exe (PID: 3384)
Reads the computer name
- UmmyVD-Web-Loader-110.exe (PID: 3384)
Reads the machine GUID from the registry
- UmmyVD-Web-Loader-110.exe (PID: 3384)
Reads the software policy settings
- UmmyVD-Web-Loader-110.exe (PID: 3384)
Checks proxy server information
- UmmyVD-Web-Loader-110.exe (PID: 3384)
Creates files or folders in the user directory
- UmmyVD-Web-Loader-110.exe (PID: 3384)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (63.7) |
|---|---|---|
| .scr | | | Windows screen saver (20) |
| .exe | | | Win32 Executable (generic) (6.9) |
| .exe | | | Win16/32 Executable Delphi generic (3.1) |
| .exe | | | Generic Win/DOS Executable (3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2014:11:23 19:39:18+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 709120 |
| InitializedDataSize: | 98816 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xadc64 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
Total processes
40
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3384 | "C:\Users\admin\AppData\Local\Temp\UmmyVD-Web-Loader-110.exe" | C:\Users\admin\AppData\Local\Temp\UmmyVD-Web-Loader-110.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
3 574
Read events
3 507
Write events
55
Delete events
12
Modification events
| (PID) Process: | (3384) UmmyVD-Web-Loader-110.exe | Key: | HKEY_CURRENT_USER\Software\Magicbit\UmmyVideoDownloader |
| Operation: | write | Name: | userid |
Value: 40bab7dc-883a-4baf-a02f-ceb328a8232f | |||
| (PID) Process: | (3384) UmmyVD-Web-Loader-110.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3384) UmmyVD-Web-Loader-110.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3384) UmmyVD-Web-Loader-110.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3384) UmmyVD-Web-Loader-110.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3384) UmmyVD-Web-Loader-110.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3384) UmmyVD-Web-Loader-110.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyServer |
Value: | |||
| (PID) Process: | (3384) UmmyVD-Web-Loader-110.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyOverride |
Value: | |||
| (PID) Process: | (3384) UmmyVD-Web-Loader-110.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoConfigURL |
Value: | |||
| (PID) Process: | (3384) UmmyVD-Web-Loader-110.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoDetect |
Value: | |||
Executable files
0
Suspicious files
0
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3384 | UmmyVD-Web-Loader-110.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\T604PFXT.txt | text | |
MD5:50244978A3BD674DA8859236CA73764C | SHA256:0C71B1DB97B79F7D22DDD23FFE4485AF9145E7CC313C0060847F7A4C92254C4E | |||
| 3384 | UmmyVD-Web-Loader-110.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\02PXUSZD.txt | text | |
MD5:75995E259AD7D424F387D05B86DEDCA3 | SHA256:A7785AAEB88806F5C50843FF69985E2C189F7BC873F02450E42A7ACEF54C0A3F | |||
| 3384 | UmmyVD-Web-Loader-110.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\AKA4HANS.txt | text | |
MD5:4B1BF9B5696356802854B6A7B9F4C51A | SHA256:6233263791F2ECB62DAE137DC281D736DAAB14BC51CF0D6FCC2AA695A2D05065 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
16
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
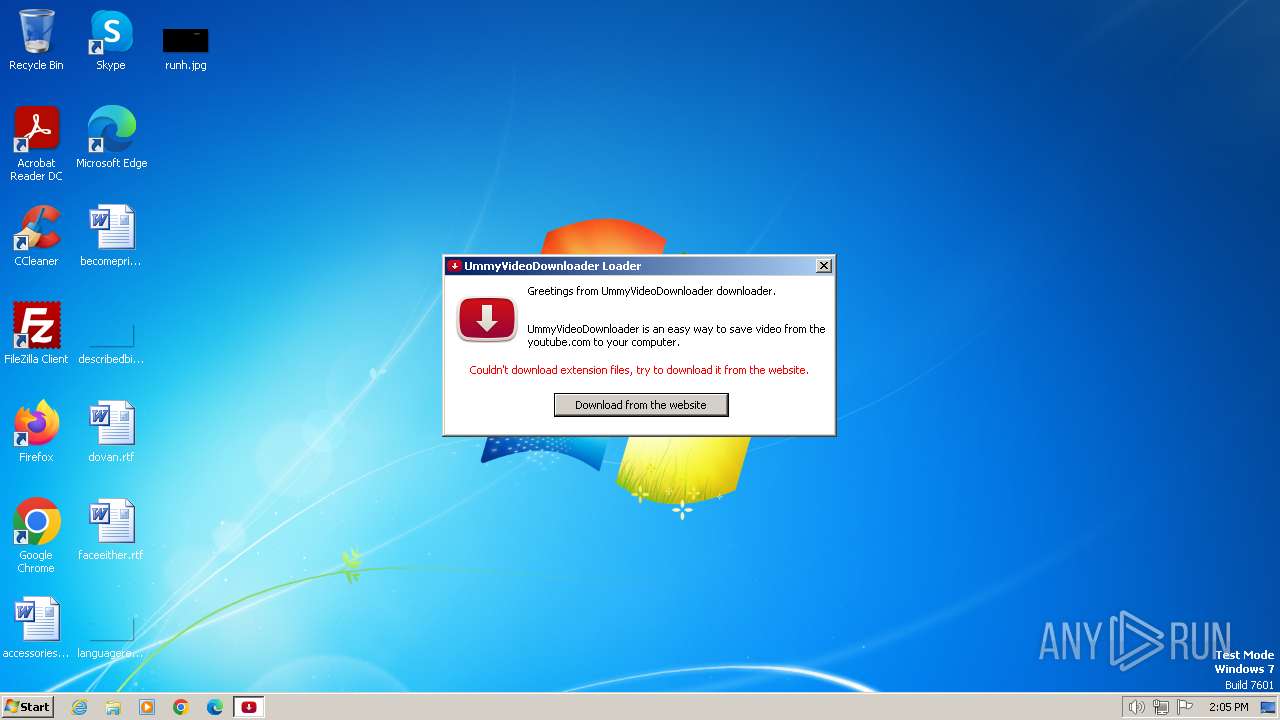
3384 | UmmyVD-Web-Loader-110.exe | GET | 404 | 104.26.6.120:80 | http://videodownloader.ummy.net/assets/UmmyVideoDownloader_setup.exe | unknown | — | — | unknown |
3384 | UmmyVD-Web-Loader-110.exe | GET | — | 104.26.6.120:80 | http://videodownloader.ummy.net/assets/UmmyVideoDownloader_setup.exe | unknown | — | — | unknown |
3384 | UmmyVD-Web-Loader-110.exe | GET | — | 104.26.6.120:80 | http://videodownloader.ummy.net/assets/UmmyVideoDownloader_setup.exe | unknown | — | — | unknown |
3384 | UmmyVD-Web-Loader-110.exe | GET | 404 | 104.26.6.120:80 | http://videodownloader.ummy.net/assets/UmmyVideoDownloader_setup.exe | unknown | — | — | unknown |
1372 | svchost.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 2.16.164.24:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8f69642324cc87bd | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3384 | UmmyVD-Web-Loader-110.exe | 216.58.206.46:443 | www.google-analytics.com | GOOGLE | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1372 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3384 | UmmyVD-Web-Loader-110.exe | 104.26.6.120:80 | videodownloader.ummy.net | CLOUDFLARENET | US | shared |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
1372 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1372 | svchost.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
1372 | svchost.exe | 2.16.164.24:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google-analytics.com |
| whitelisted |
videodownloader.ummy.net |
| unknown |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |