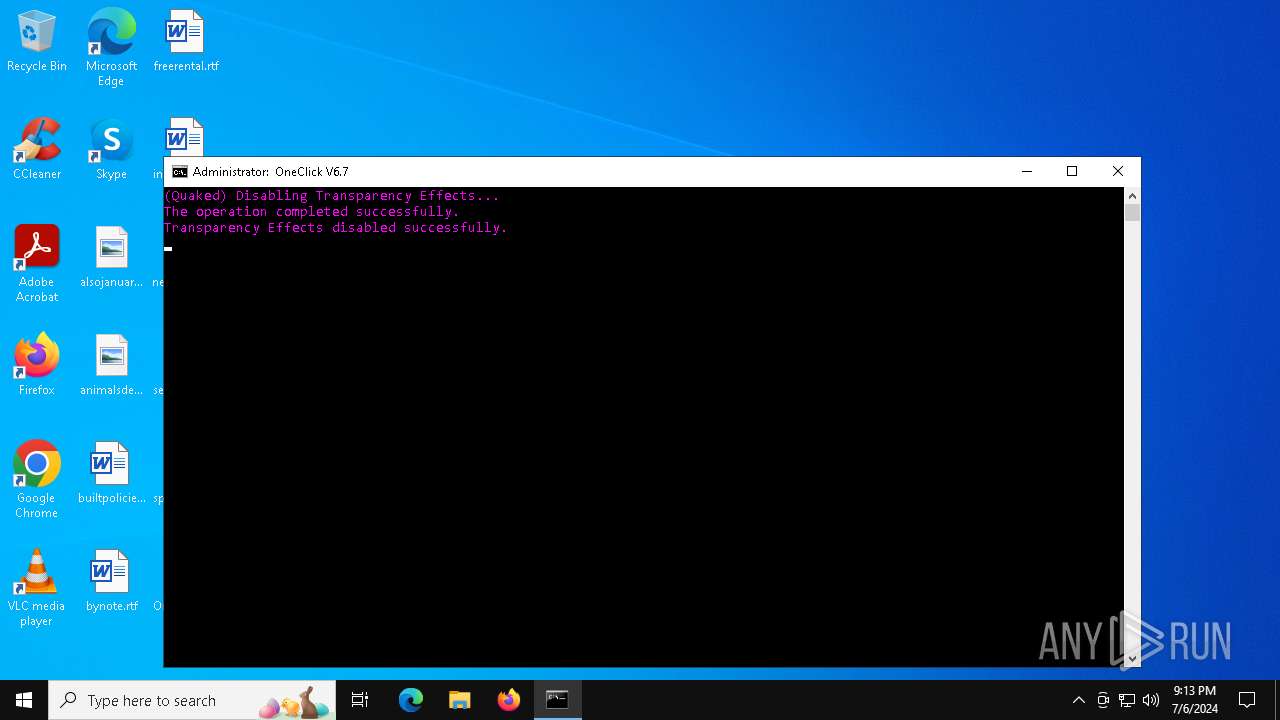
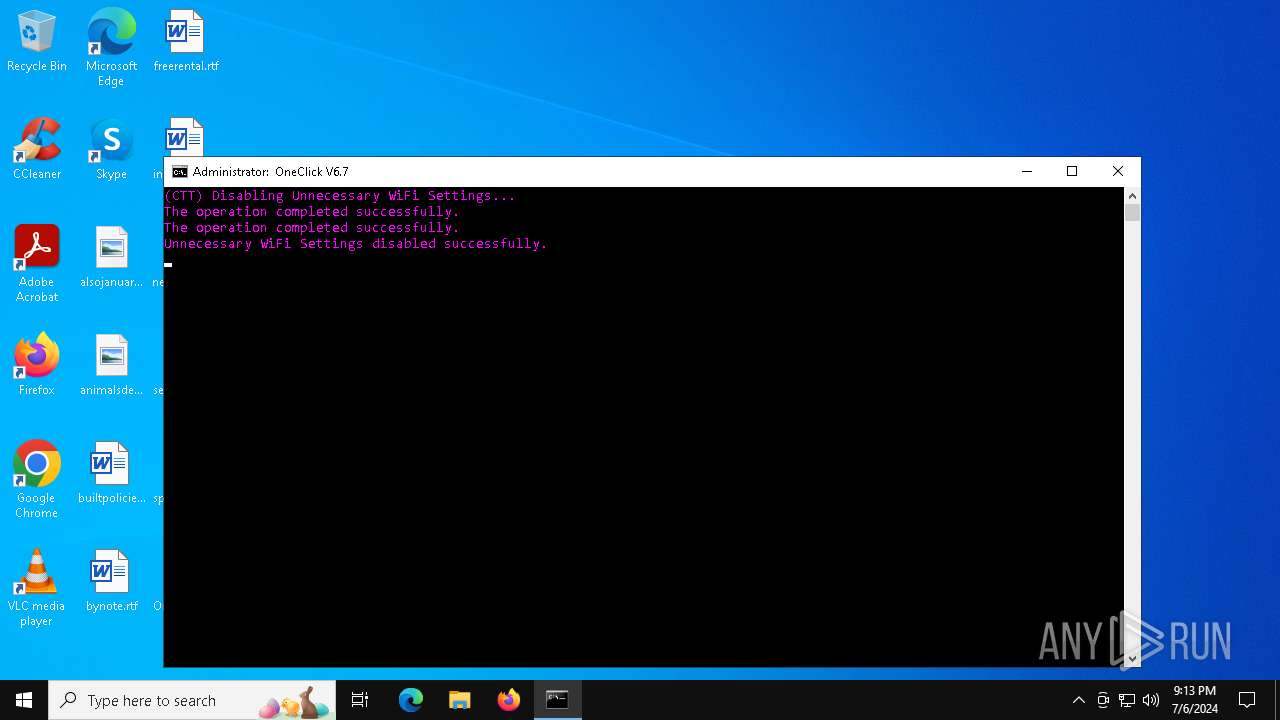
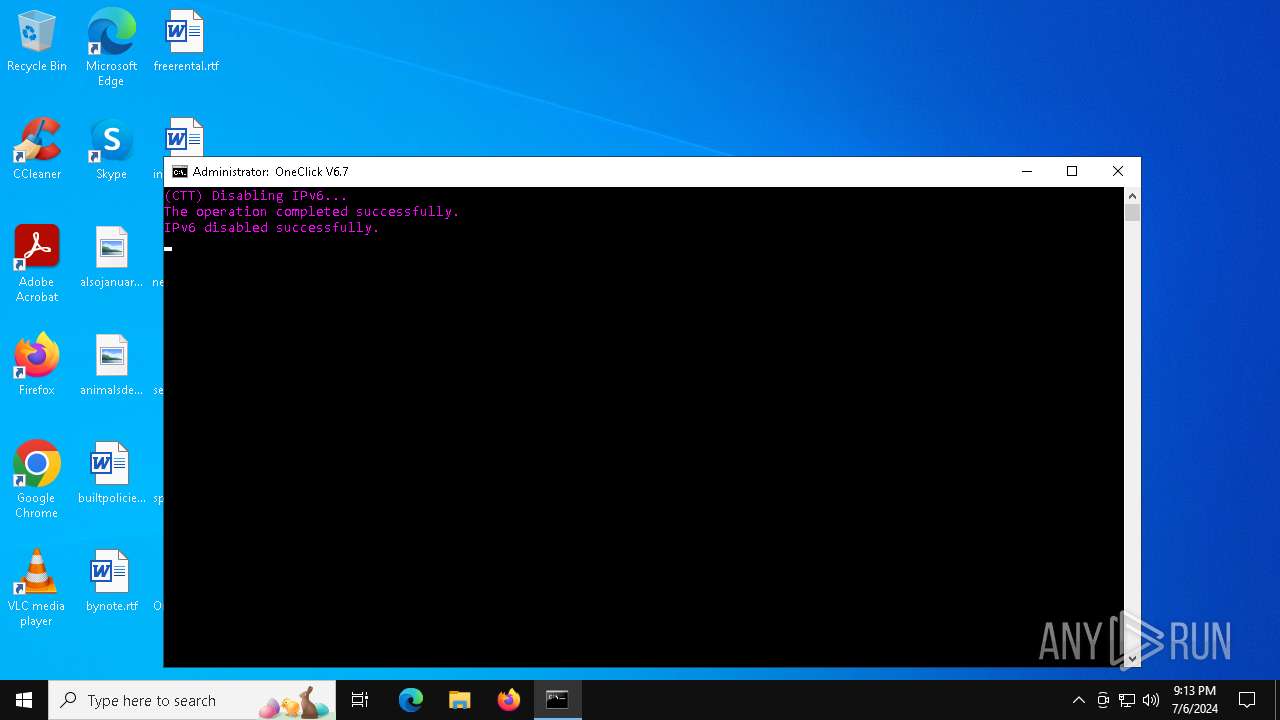
| File name: | Oneclick-V6.7.bat |
| Full analysis: | https://app.any.run/tasks/1f9c3609-2f39-41e2-9cf6-a8421ce67b21 |
| Verdict: | Malicious activity |
| Analysis date: | July 06, 2024, 21:11:08 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-8 text, with CRLF line terminators |
| MD5: | 4ACD7D1E7294D4AB4E9DB8977D5135E4 |
| SHA1: | 07C5474FCD09FF5843DF3F776D665DCF0EEF4284 |
| SHA256: | B66CD5D6A39C016D0C39E270BED5CC8DBEB1920B3F827D78BC9D36A4A1E3F84F |
| SSDEEP: | 1536:97SPKdigMQgPTjIV4wJzSwTgfGH/ngfHH4pX/paZSiDk2IWOmXmomk:9nnHgvOh4KmXmomk |
MALICIOUS
Changes powershell execution policy (Unrestricted)
- cmd.exe (PID: 7056)
UAC/LUA settings modification
- reg.exe (PID: 6944)
SUSPICIOUS
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 6612)
- cmd.exe (PID: 7056)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 6924)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6612)
- cmd.exe (PID: 7056)
Executing commands from a ".bat" file
- powershell.exe (PID: 6924)
Starts application with an unusual extension
- cmd.exe (PID: 7056)
Starts SC.EXE for service management
- cmd.exe (PID: 7056)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 7056)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7056)
Executes as Windows Service
- VSSVC.exe (PID: 2868)
Searches for installed software
- dllhost.exe (PID: 1920)
Uses powercfg.exe to modify the power settings
- cmd.exe (PID: 7056)
Process uses powershell cmdlet to discover network configuration
- cmd.exe (PID: 7056)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 1968)
INFO
Application launched itself
- Acrobat.exe (PID: 3516)
- AcroCEF.exe (PID: 1112)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 1824)
Checks supported languages
- acrobat_sl.exe (PID: 6168)
- curl.exe (PID: 1200)
- chcp.com (PID: 6388)
- tar.exe (PID: 2052)
- chcp.com (PID: 4800)
- chcp.com (PID: 6652)
- chcp.com (PID: 7160)
- chcp.com (PID: 3628)
- chcp.com (PID: 1052)
- chcp.com (PID: 3088)
- ShellExperienceHost.exe (PID: 1968)
- chcp.com (PID: 6900)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 1824)
Manual execution by a user
- cmd.exe (PID: 6612)
Reads the computer name
- curl.exe (PID: 1200)
- ShellExperienceHost.exe (PID: 1968)
Executable content was dropped or overwritten
- AdobeARM.exe (PID: 1272)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 4796)
Gets data length (POWERSHELL)
- powershell.exe (PID: 4796)
Changes appearance of the Explorer extensions
- reg.exe (PID: 1292)
- reg.exe (PID: 1388)
Changes the registry key values via Powershell
- cmd.exe (PID: 7056)
Reads mouse settings
- reg.exe (PID: 6696)
- reg.exe (PID: 6800)
- reg.exe (PID: 2456)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
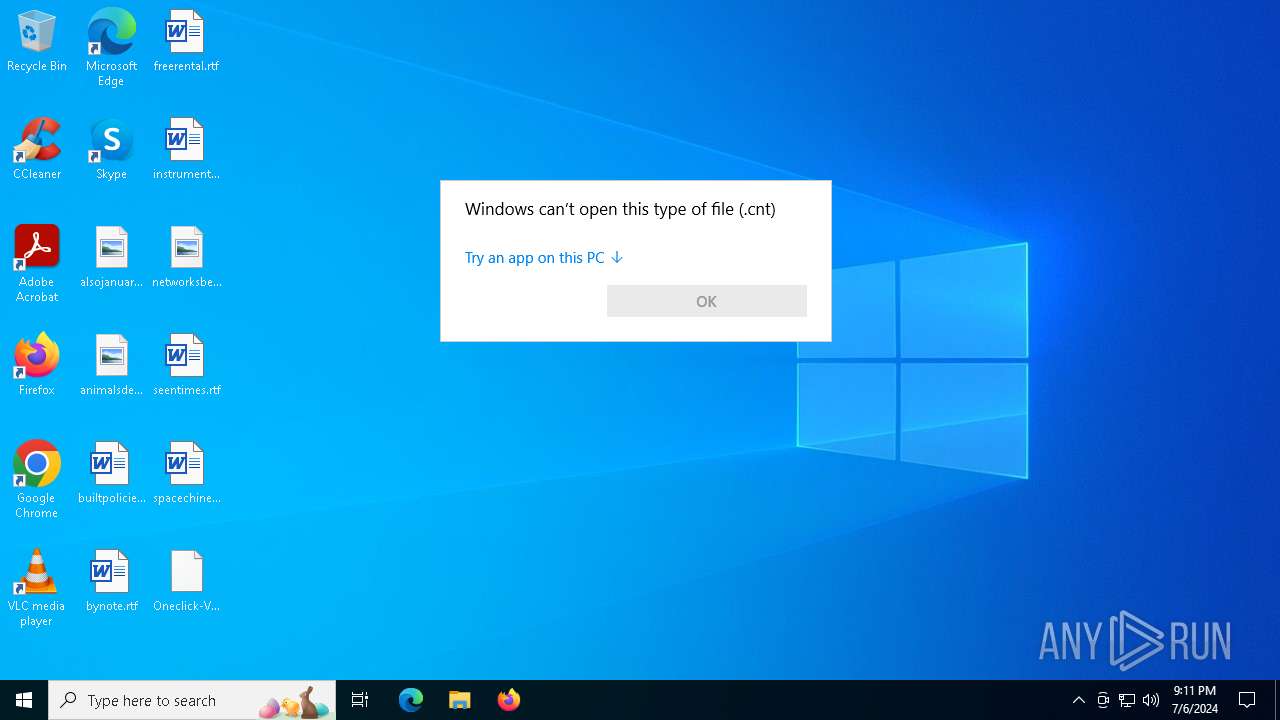
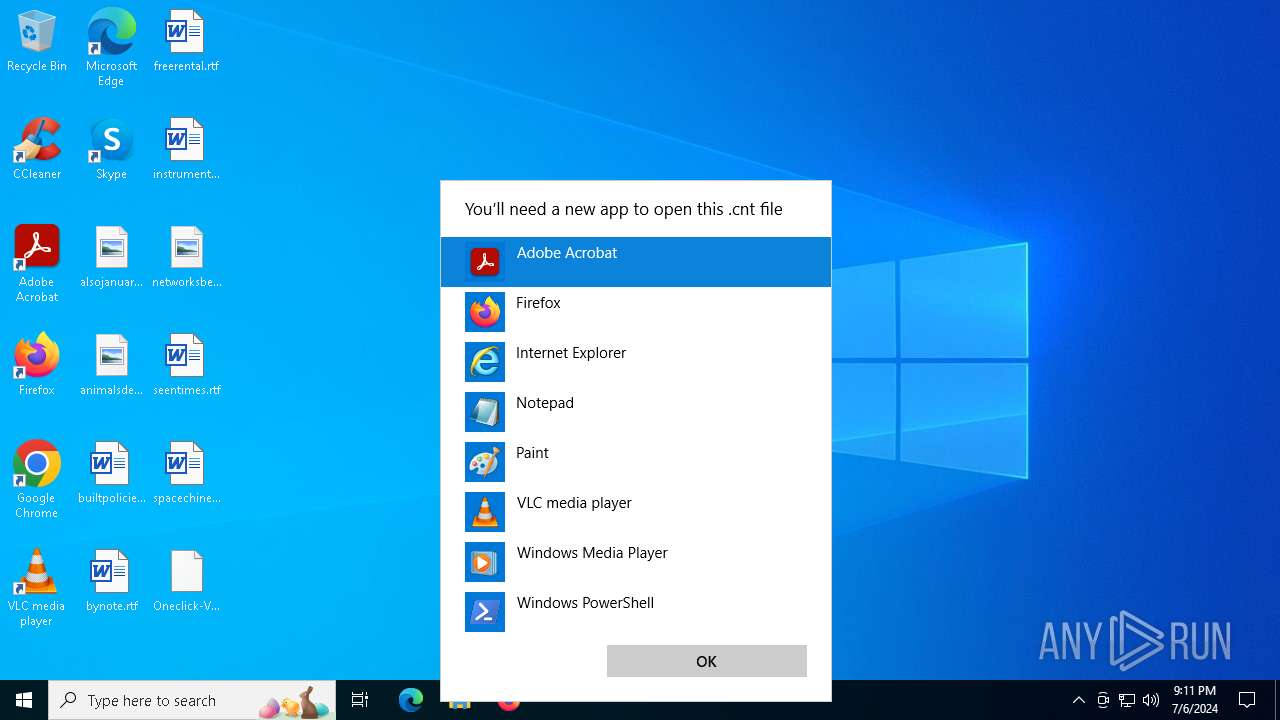
| .cnt | | | Help File Contents (100) |
|---|
Total processes
355
Monitored processes
229
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 420 | sc config CoreMessagingRegistrar start=auto | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 5 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 420 | sc config MpsSvc start=auto | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 5 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 448 | reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\GraphicsDrivers" /v "HwSchMode" /t REG_DWORD /d 2 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 640 | sc config AppIDSvc start=demand | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 5 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 640 | sc config FDResPub start=demand | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | chcp 437 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1068 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=1592 --field-trial-handle=1572,i,13219889067550103614,18263033026198858155,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1068 | timeout 1 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1068 | sc config DeviceInstall start=demand | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1112 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --backgroundcolor=16514043 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
Total events
93 241
Read events
92 655
Write events
551
Delete events
35
Modification events
| (PID) Process: | (1824) OpenWith.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\Office16\oregres.dll,-205 |
Value: Word | |||
| (PID) Process: | (1824) OpenWith.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @wmploc.dll,-102 |
Value: Windows Media Player | |||
| (PID) Process: | (1824) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1824) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1824) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1824) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3516) Acrobat.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Mappings\S-1-15-2-2034283098-2252572593-1072577386-2659511007-3245387615-27016815-3920691934 |
| Operation: | write | Name: | DisplayName |
Value: Adobe Acrobat Reader Protected Mode | |||
| (PID) Process: | (1436) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (1436) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVEntitlement |
| Operation: | write | Name: | bSynchronizeOPL |
Value: 0 | |||
| (PID) Process: | (1436) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVGeneral |
| Operation: | write | Name: | uLastAppLaunchTimeStamp |
Value: | |||
Executable files
1
Suspicious files
106
Text files
39
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1112 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\LOG.old~RF1d5f1a.TMP | text | |
MD5:FCD96552DAA6924F8C1E9C378163E2C9 | SHA256:E8EC8E1501E489B27B564C363F4E60963DD57180453B35B092A4B3769E7AA5CA | |||
| 1436 | Acrobat.exe | C:\USERS\ADMIN\APPDATA\LOCAL\ADOBE\ACROBAT\DC\SOPHIA\ACROBAT\SOPHIA.JSON | binary | |
MD5:79270D9595B259B53E39403366436A8E | SHA256:AD0552A8B392315C512F6DC945F318AD83B98FB64415C0CED694843A3C5D2083 | |||
| 1436 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SharedDataEvents-journal | binary | |
MD5:157A9DF0531353D8F9DE17EE597D7E28 | SHA256:E51531A5FC617E74E55C3DA6C4E566AFCD55266E5578D2ADE0D3D751E87BA00F | |||
| 1436 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeFnt23.lst.1436 | binary | |
MD5:366B140BAFC863B7E366AA1E51604759 | SHA256:CBC8B288DBD2C72432081CF33CEF431572A94C7FB89DBCD59973B99E3871814E | |||
| 1112 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Local Storage\leveldb\LOG.old | text | |
MD5:43D1F53B48631F8B32E040219417874B | SHA256:AA4C99C362EB18EB8B91EEB8821960807F725E7C5DE1FBABBA7B910BDA3EEEB8 | |||
| 1112 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Local Storage\leveldb\LOG.old~RF1d5de2.TMP | text | |
MD5:E26AF4B6A1AD62E54D67510EEFE20B2C | SHA256:BF001234CF5F261254DEA1EA459BBFD4A35D15166C765CA3ED9B56D49A04BE1B | |||
| 1112 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Session Storage\LOG.old~RF1d5f59.TMP | text | |
MD5:B875B798FCFA464DB41DDC9789BDB161 | SHA256:F6259A0B5E546CB737118D559D0FBDFFDCEC68AD4F7B95451FED263058606B13 | |||
| 1436 | Acrobat.exe | C:\USERS\ADMIN\APPDATA\LOCAL\ADOBE\ACROBAT\DC\SHAREDDATAEVENTS | binary | |
MD5:FFB9B4FDC8B66DD724CEC92379495733 | SHA256:ADD7A245467CEE6C4EEA505EB99B8DED37B23C24F063CD7F8CEA66DCD432D74B | |||
| 1112 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Session Storage\LOG.old | text | |
MD5:EC382FFF4B7232181CDB8226E9C289C7 | SHA256:27BDA724E8E0654E4BDA2F8E98FE399EF826F052F73FBBDB19CDF78954DB9954 | |||
| 1436 | Acrobat.exe | C:\Users\admin\AppData\Local\Temp\acrobat_sbx\acroNGLLog.txt | text | |
MD5:893C9C357407124657737316800807AF | SHA256:03BBF18E25513002292153C428896F21A955E99AB85195073952FB3D3C0C2C37 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
53
TCP/UDP connections
34
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4448 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
2476 | RUXIMICS.exe | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1928 | svchost.exe | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
2476 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
4448 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
— | — | OPTIONS | 204 | 34.237.241.83:443 | https://p13n.adobe.io/psdk/v2/content?surfaceId=ACROBAT_READER_MASTER_SURFACEID&surfaceId=DC_READER_LAUNCH_CARD&surfaceId=DC_Reader_RHP_Banner&surfaceId=DC_Reader_RHP_Retention&surfaceId=Edit_InApp_Aug2020&surfaceId=DC_FirstMile_Right_Sec_Surface&surfaceId=DC_Reader_Upsell_Cards&surfaceId=DC_FirstMile_Home_View_Surface&surfaceId=DC_Reader_RHP_Intent_Banner&surfaceId=DC_Reader_Disc_LHP_Banner&surfaceId=DC_Reader_Edit_LHP_Banner&surfaceId=DC_Reader_Convert_LHP_Banner&surfaceId=DC_Reader_Sign_LHP_Banner&surfaceId=DC_Reader_More_LHP_Banner&surfaceId=DC_Reader_Disc_LHP_Retention&adcProductLanguage=en-us&adcVersion=23.1.20093&adcProductType=SingleClientMini&adcOSType=WIN&adcCountryCode=GB&adcXAPIClientID=api_reader_desktop_win_23.1.20093&encodingScheme=BASE_64 | unknown | — | — | unknown |
1272 | AdobeARM.exe | GET | 304 | 23.48.23.149:80 | http://acroipm2.adobe.com/assets/Owner/arm/ReportOwner.txt | unknown | — | — | unknown |
1272 | AdobeARM.exe | GET | 404 | 23.48.23.149:80 | http://acroipm2.adobe.com/assets/Owner/arm/2024/7/OwnerAPI/Rdr.txt | unknown | — | — | unknown |
1272 | AdobeARM.exe | GET | 404 | 23.48.23.149:80 | http://acroipm2.adobe.com/assets/Owner/arm/2024/7/UC/Other.txt | unknown | — | — | unknown |
1272 | AdobeARM.exe | GET | 304 | 23.48.23.149:80 | http://acroipm2.adobe.com/assets/Owner/arm/ProcessMAU.txt | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1928 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2476 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4448 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4448 | MoUsoCoreWorker.exe | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
2476 | RUXIMICS.exe | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1928 | svchost.exe | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
4448 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2476 | RUXIMICS.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |
acroipm2.adobe.com |
| whitelisted |
p13n.adobe.io |
| whitelisted |
armmf.adobe.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
github.com |
| shared |
ocsp.digicert.com |
| whitelisted |