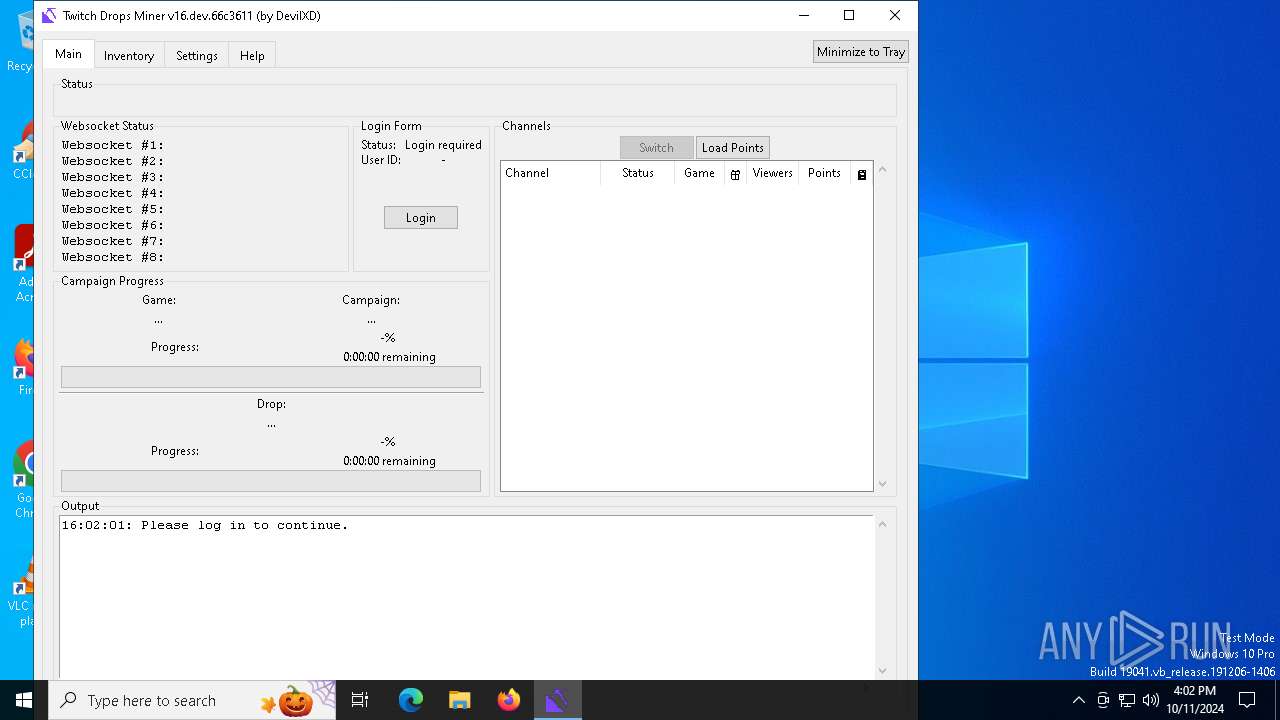
| File name: | Twitch Drops Miner (by DevilXD).exe |
| Full analysis: | https://app.any.run/tasks/80fedb0d-63e1-4695-bb1a-c1cc4dcc72c7 |
| Verdict: | Malicious activity |
| Analysis date: | October 11, 2024, 16:01:06 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | 01F5DAB81179771A93E7D12C7F3DE070 |
| SHA1: | 8A762ACC59722FB43DC158EFF3824D73AD988275 |
| SHA256: | B6697612CE630403017513460D783F3A901B133B8E44EAD7ED75B57EC54E18FB |
| SSDEEP: | 98304:F6CH6SYoo0MPwW6dfwFnbLLuXwWrSABGYS/Bh6NZDMnH74X+KLTAHNMl/v0TqKJe:2PuVNKI4rz5ooicJYzigN/ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops python dynamic module
- Twitch Drops Miner (by DevilXD).exe (PID: 5240)
Process drops legitimate windows executable
- Twitch Drops Miner (by DevilXD).exe (PID: 5240)
Executable content was dropped or overwritten
- Twitch Drops Miner (by DevilXD).exe (PID: 5240)
Application launched itself
- Twitch Drops Miner (by DevilXD).exe (PID: 5240)
The process drops C-runtime libraries
- Twitch Drops Miner (by DevilXD).exe (PID: 5240)
Starts CMD.EXE for commands execution
- Twitch Drops Miner (by DevilXD).exe (PID: 6356)
INFO
Checks supported languages
- Twitch Drops Miner (by DevilXD).exe (PID: 5240)
Create files in a temporary directory
- Twitch Drops Miner (by DevilXD).exe (PID: 5240)
Reads the computer name
- Twitch Drops Miner (by DevilXD).exe (PID: 5240)
Checks operating system version
- Twitch Drops Miner (by DevilXD).exe (PID: 6356)
PyInstaller has been detected (YARA)
- Twitch Drops Miner (by DevilXD).exe (PID: 5240)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (57.6) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.9) |
| .exe | | | Generic Win/DOS Executable (2.6) |
| .exe | | | DOS Executable Generic (2.6) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:09:29 20:22:33+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.4 |
| CodeSize: | 172032 |
| InitializedDataSize: | 161280 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xcdb0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
137
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2808 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4448 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5240 | "C:\Users\admin\AppData\Local\Temp\Twitch Drops Miner (by DevilXD).exe" | C:\Users\admin\AppData\Local\Temp\Twitch Drops Miner (by DevilXD).exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6172 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6356 | "C:\Users\admin\AppData\Local\Temp\Twitch Drops Miner (by DevilXD).exe" | C:\Users\admin\AppData\Local\Temp\Twitch Drops Miner (by DevilXD).exe | Twitch Drops Miner (by DevilXD).exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6608 | C:\WINDOWS\system32\cmd.exe /c "ver" | C:\Windows\System32\cmd.exe | — | Twitch Drops Miner (by DevilXD).exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
9 181
Read events
9 181
Write events
0
Delete events
0
Modification events
Executable files
86
Suspicious files
14
Text files
944
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5240 | Twitch Drops Miner (by DevilXD).exe | C:\Users\admin\AppData\Local\Temp\_MEI52402\PIL\_imagingcms.cp310-win_amd64.pyd | executable | |
MD5:12E0EE16947627A1A20BD3268F8A5A53 | SHA256:709DFC2B7A2A3A354A2DD17189142A8C2BB09DFB867941C5251F211F787D8FF1 | |||
| 5240 | Twitch Drops Miner (by DevilXD).exe | C:\Users\admin\AppData\Local\Temp\_MEI52402\PIL\_webp.cp310-win_amd64.pyd | executable | |
MD5:E96703F62275BA5F281A19F18EEB0A0D | SHA256:DEA85389547C6DFB9787A26F32DF93F9422A741B07AAEFDA750266D1E04A8429 | |||
| 5240 | Twitch Drops Miner (by DevilXD).exe | C:\Users\admin\AppData\Local\Temp\_MEI52402\PIL\_imagingtk.cp310-win_amd64.pyd | executable | |
MD5:75CAD10547C722A9A324DDCE64675B19 | SHA256:93B5D5E66F19C64566D3C3DF614D4FA45B3C318DBE9A77A5182F95A1CBF4C838 | |||
| 5240 | Twitch Drops Miner (by DevilXD).exe | C:\Users\admin\AppData\Local\Temp\_MEI52402\Pythonwin\mfc140u.dll | executable | |
MD5:03A161718F1D5E41897236D48C91AE3C | SHA256:E06C4BD078F4690AA8874A3DEB38E802B2A16CCB602A7EDC2E077E98C05B5807 | |||
| 5240 | Twitch Drops Miner (by DevilXD).exe | C:\Users\admin\AppData\Local\Temp\_MEI52402\PIL\_imaging.cp310-win_amd64.pyd | executable | |
MD5:E98E0056492D8E016A32010465F3AB71 | SHA256:073F0D7E0D4F72743CBA514DBAA75871C5B3C8B957DBEFF91F327DF44DC10CE3 | |||
| 5240 | Twitch Drops Miner (by DevilXD).exe | C:\Users\admin\AppData\Local\Temp\_MEI52402\PIL\_imagingmath.cp310-win_amd64.pyd | executable | |
MD5:32434F1220A0749F3F392D52974DDA4B | SHA256:04B22E5A8B02EFCFAB61278056288AF713DE0BDA3495CABAB92C3A44E0F85470 | |||
| 5240 | Twitch Drops Miner (by DevilXD).exe | C:\Users\admin\AppData\Local\Temp\_MEI52402\_bz2.pyd | executable | |
MD5:FBA120A94A072459011133DA3A989DB2 | SHA256:055A93C8B127DC840AC40CA70D4B0246AC88C9CDE1EF99267BBE904086E0B7D3 | |||
| 5240 | Twitch Drops Miner (by DevilXD).exe | C:\Users\admin\AppData\Local\Temp\_MEI52402\_lzma.pyd | executable | |
MD5:864B22495372FA4D8B18E1C535962AE2 | SHA256:FC57BD20B6B128AFA5FAAAC1FD0CE783031FAAF39F71B58C9CACF87A16F3325F | |||
| 5240 | Twitch Drops Miner (by DevilXD).exe | C:\Users\admin\AppData\Local\Temp\_MEI52402\_asyncio.pyd | executable | |
MD5:4679FB6C4927612A1F13FA3883533F47 | SHA256:A2EA28CA2BE4326A113DA539A081C8A889D55C13AABED755AD27C1738A1D10C1 | |||
| 5240 | Twitch Drops Miner (by DevilXD).exe | C:\Users\admin\AppData\Local\Temp\_MEI52402\Pythonwin\win32ui.pyd | executable | |
MD5:2DC4AFB4D80FE4F45CE23446D27A291E | SHA256:EFBD6798CE0F26704DF18139BECAF03CA47DA80B5BC127178EB0B67E36C60A69 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
54
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4700 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3744 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3744 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2928 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5700 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6944 | svchost.exe | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4360 | SearchApp.exe | 92.123.104.52:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |