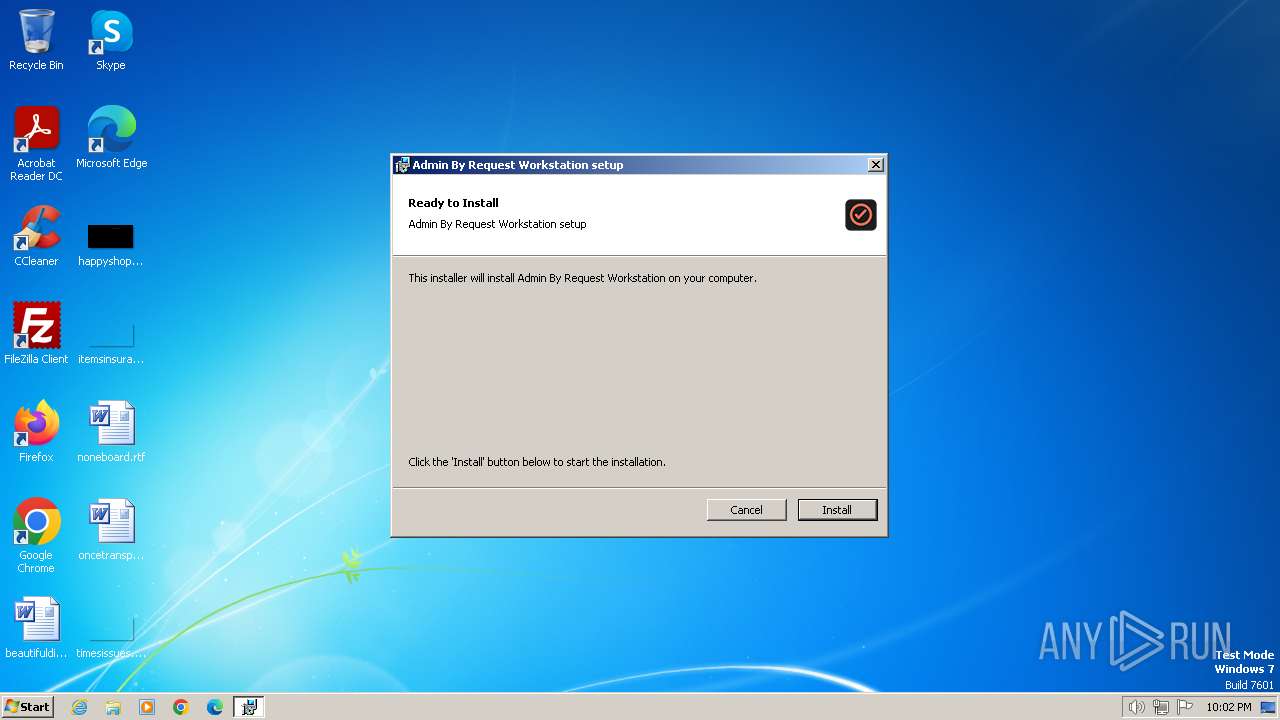
| File name: | Admin By Request 8.3 Workstation.msi |
| Full analysis: | https://app.any.run/tasks/90211b04-b1e8-42ec-b815-a3976e5aeafd |
| Verdict: | Malicious activity |
| Analysis date: | June 18, 2024, 21:01:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: Admin By Request Workstation, Author: FastTrack Software, Keywords: Installer, Comments: Admin By Request Workstation 8.3.1.0, Template: Intel;1033, Revision Number: {A246AF5A-3A17-4FAB-8247-FE56D9D56BAF}, Create Time/Date: Tue Jun 18 20:43:20 2024, Last Saved Time/Date: Tue Jun 18 20:43:20 2024, Number of Pages: 200, Number of Words: 2, Name of Creating Application: Windows Installer XML (3.5.2519.0), Security: 2 |
| MD5: | 0857F6C79B81FC1035BB4E7CD00F41A3 |
| SHA1: | CFA9C12E6490E2339AF391A2AC6F449F1A304995 |
| SHA256: | B660029AA90A59A136366E534CA2CF68AC8A8372313FB4A98728955668B7E4B1 |
| SSDEEP: | 98304:CHopsdwY+fVU/C7w0XM6VNuGW58C26mHsPKXJ3zEr70ODrcbguLXp5Re4DwPEWax:ii |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 3424)
- msiexec.exe (PID: 3396)
- Audckq32.exe (PID: 3084)
Changes the autorun value in the registry
- Audckq32.exe (PID: 3084)
- msiexec.exe (PID: 3396)
- adminbyrequest.exe (PID: 4052)
UAC/LUA settings modification
- Audckq32.exe (PID: 3084)
Creates a writable file in the system directory
- Audckq32.exe (PID: 3084)
Application was injected by another process
- explorer.exe (PID: 1296)
Runs injected code in another process
- Shell.exe (PID: 3404)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 3204)
- Audckq32.exe (PID: 3084)
Checks Windows Trust Settings
- msiexec.exe (PID: 3396)
- Audckq32.exe (PID: 3084)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 3396)
- Audckq32.exe (PID: 3084)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 3396)
The process creates files with name similar to system file names
- msiexec.exe (PID: 3396)
- Audckq32.exe (PID: 3084)
Executable content was dropped or overwritten
- Audckq32.exe (PID: 3084)
Process drops legitimate windows executable
- msiexec.exe (PID: 3396)
Reads security settings of Internet Explorer
- adminbyrequest.exe (PID: 4052)
Reads the Internet Settings
- adminbyrequest.exe (PID: 4052)
Changes default file association
- adminbyrequest.exe (PID: 4052)
The process executes via Task Scheduler
- Wafbsr32.exe (PID: 2276)
Searches for installed software
- Audckq32.exe (PID: 3084)
INFO
Reads the machine GUID from the registry
- msiexec.exe (PID: 3396)
- Switchback.exe (PID: 932)
- Audckq32.exe (PID: 3084)
- adminbyrequest.exe (PID: 4052)
- Wafbsr32.exe (PID: 2276)
Checks supported languages
- msiexec.exe (PID: 3396)
- Audckq32.exe (PID: 3084)
- Switchback.exe (PID: 932)
- adminbyrequest.exe (PID: 4052)
- Shell.exe (PID: 3404)
- Wafbsr32.exe (PID: 2276)
Reads the software policy settings
- msiexec.exe (PID: 3424)
- msiexec.exe (PID: 3396)
- Audckq32.exe (PID: 3084)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 3424)
- explorer.exe (PID: 1296)
Reads the computer name
- msiexec.exe (PID: 3396)
- Switchback.exe (PID: 932)
- Audckq32.exe (PID: 3084)
- adminbyrequest.exe (PID: 4052)
- Wafbsr32.exe (PID: 2276)
Executable content was dropped or overwritten
- msiexec.exe (PID: 3396)
Create files in a temporary directory
- msiexec.exe (PID: 3396)
Reads Environment values
- Audckq32.exe (PID: 3084)
- adminbyrequest.exe (PID: 4052)
Creates files in the program directory
- Audckq32.exe (PID: 3084)
Creates a software uninstall entry
- msiexec.exe (PID: 3396)
Reads CPU info
- Audckq32.exe (PID: 3084)
Disables trace logs
- adminbyrequest.exe (PID: 4052)
- Audckq32.exe (PID: 3084)
Creates files or folders in the user directory
- adminbyrequest.exe (PID: 4052)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | Admin By Request Workstation |
| Author: | FastTrack Software |
| Keywords: | Installer |
| Comments: | Admin By Request Workstation 8.3.1.0 |
| Template: | Intel;1033 |
| RevisionNumber: | {A246AF5A-3A17-4FAB-8247-FE56D9D56BAF} |
| CreateDate: | 2024:06:18 20:43:20 |
| ModifyDate: | 2024:06:18 20:43:20 |
| Pages: | 200 |
| Words: | 2 |
| Software: | Windows Installer XML (3.5.2519.0) |
| Security: | Read-only recommended |
Total processes
48
Monitored processes
9
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 932 | "C:\Program Files\FastTrack Software\Admin By Request\Switchback.exe" /CheckRuntime | C:\Program Files\FastTrack Software\Admin By Request\Switchback.exe | — | msiexec.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Switchback Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1296 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2276 | "C:\Program Files\Common Files\VAudio\WAFBSR32.exe" | C:\Program Files\Common Files\VAudio\Wafbsr32.exe | — | taskeng.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Description: Watchdog Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3084 | "C:\Program Files\Common Files\VAudio\Audckq32.exe" | C:\Program Files\Common Files\VAudio\Audckq32.exe | services.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Description: Audio provider Version: 8.3.1.0 Modules
| |||||||||||||||
| 3204 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3396 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3404 | "C:\Program Files\FastTrack Software\Admin By Request\shell.exe" | C:\Program Files\FastTrack Software\Admin By Request\Shell.exe | — | adminbyrequest.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3424 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\Admin By Request 8.3 Workstation.msi" | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4052 | "C:\Program Files\FastTrack Software\Admin By Request\adminbyrequest.exe" | C:\Program Files\FastTrack Software\Admin By Request\adminbyrequest.exe | Audckq32.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Admin By Request Version: 8.3.1.0 Modules
| |||||||||||||||
Total events
32 224
Read events
31 707
Write events
500
Delete events
17
Modification events
| (PID) Process: | (1296) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB010000000A82066E518DA4419A50D76DC5E2963D0000000002000000000010660000000100002000000060FD4D95194EF83BCC1FF4D2A48929933CD8A0EB3D545CB75B7FC09CCE5654BE000000000E80000000020000200000001B0FCB3E360D49EA6F8F3B145C9597318246CB8FDEA349EBE2D27680F8F2BE803000000039F2D382AF56A6B288BE7396260A0C6EFB07DD6DDDB17A52F542024A32C58B5219DC2959A9150DC3EEE764DC3EB9A5F3400000003E991413B88EC04D349E08C09D7320D3901CE6C498F424B65C1D44756B2A0FF3FD53622B1E422226857D4882FBA6AFCFC0144E97308126E2F7DA9D69786752DC | |||
| (PID) Process: | (3424) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1296) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | Zvpebfbsg.Jvaqbjf.JvaqbjfVafgnyyre |
Value: 00000000000000000200000008FE0000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF000000000000000000000000 | |||
| (PID) Process: | (1296) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000DF01000052030000A4CC9801440000008A000000427732007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E00650078006500000000000000F8E2A100FFFFFFFF482F2A00FFFFFFFF70594E75000000000000000094E2A1007C904A750004000000000000F8E2A100FFFFFFFF482F2A00FFFFFFFF98F72900E8FA2900402F2A00C4E2A100F7AF017680D0347604F0A100081D0276E4610276E8232800F8E2A10000000000840000000A70D6A8D8E2A100A1690276E8232800F8E2A1000000000004E5A1003F610276E8232800F8E2A10000000400000000804C610276E823280063003A005C00750073006500720073005C00610064006D0069006E005C0061007000700064006100740061005C0072006F0061006D0069006E0067005C006D00690063001100000090522800885228005C006900BCE300009A71D6A86CE3A1005E900276BCE3A10034550000A671D6A880E3A100929B0276385505024C06000098E3A100A8500502A4E3A100549B02761290027611000000905228008852280040E4A100C850050210E400006671D6A8C0E3A1005E90027610E4A100C4E3A100039402760000000034550502ECE3A100A99302763455050298E4A100A8500502BD93027600000000A850050298E4A100F4E3A100440000008A000000427732007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E00650078006500000000000000F8E2A100FFFFFFFF482F2A00FFFFFFFF70594E75000000000000000094E2A1007C904A750004000000000000F8E2A100FFFFFFFF482F2A00FFFFFFFF98F72900E8FA2900402F2A00C4E2A100F7AF017680D0347604F0A100081D0276E4610276E8232800F8E2A10000000000840000000A70D6A8D8E2A100A1690276E8232800F8E2A1000000000004E5A1003F610276E8232800F8E2A10000000400000000804C610276E823280063003A005C00750073006500720073005C00610064006D0069006E005C0061007000700064006100740061005C0072006F0061006D0069006E0067005C006D00690063001100000090522800885228005C006900BCE300009A71D6A86CE3A1005E900276BCE3A10034550000A671D6A880E3A100929B0276385505024C06000098E3A100A8500502A4E3A100549B02761290027611000000905228008852280040E4A100C850050210E400006671D6A8C0E3A1005E90027610E4A100C4E3A100039402760000000034550502ECE3A100A99302763455050298E4A100A8500502BD93027600000000A850050298E4A100F4E3A100440000008A000000427732007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E00650078006500000000000000F8E2A100FFFFFFFF482F2A00FFFFFFFF70594E75000000000000000094E2A1007C904A750004000000000000F8E2A100FFFFFFFF482F2A00FFFFFFFF98F72900E8FA2900402F2A00C4E2A100F7AF017680D0347604F0A100081D0276E4610276E8232800F8E2A10000000000840000000A70D6A8D8E2A100A1690276E8232800F8E2A1000000000004E5A1003F610276E8232800F8E2A10000000400000000804C610276E823280063003A005C00750073006500720073005C00610064006D0069006E005C0061007000700064006100740061005C0072006F0061006D0069006E0067005C006D00690063001100000090522800885228005C006900BCE300009A71D6A86CE3A1005E900276BCE3A10034550000A671D6A880E3A100929B0276385505024C06000098E3A100A8500502A4E3A100549B02761290027611000000905228008852280040E4A100C850050210E400006671D6A8C0E3A1005E90027610E4A100C4E3A100039402760000000034550502ECE3A100A99302763455050298E4A100A8500502BD93027600000000A850050298E4A100F4E3A100 | |||
| (PID) Process: | (3396) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000727F55D0C2C1DA01440D00007C0E0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3396) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4000000000000000CCE157D0C2C1DA01440D00007C0E0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3396) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 75 | |||
| (PID) Process: | (3396) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4000000000000000287BB2D0C2C1DA01440D00007C0E0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3396) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000287BB2D0C2C1DA01440D0000480C0000E80300000100000000000000000000006889467F55AE4245BD45BBD4EA370C670000000000000000 | |||
| (PID) Process: | (3204) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000036A2B9D0C2C1DA01840C00007C0C0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
20
Suspicious files
13
Text files
9
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3396 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3396 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:49C341478F985C53E303C81BB35B53F4 | SHA256:C052905A9DA55713FA711DBF7DBC329360B45B15DF662C56F6B0102931614FAF | |||
| 3396 | msiexec.exe | C:\Windows\Installer\5306e.msi | executable | |
MD5:0857F6C79B81FC1035BB4E7CD00F41A3 | SHA256:B660029AA90A59A136366E534CA2CF68AC8A8372313FB4A98728955668B7E4B1 | |||
| 3396 | msiexec.exe | C:\Program Files\FastTrack Software\Admin By Request\AdminByRequest.exe | executable | |
MD5:1C36E742813872FE0A7EAD5D99AF8F46 | SHA256:335D76AFB270F825D1BE0FD1249DDF08E4DAB64E34C1E52AC216D210A5E3D044 | |||
| 3396 | msiexec.exe | C:\Program Files\FastTrack Software\Admin By Request\ShellHelper32.dll | executable | |
MD5:3995260518373F4FDBB5B2B8DCD4395A | SHA256:8B27C7FEF77ED2646B9AD74D360DA1FE610E89E19E08ADB7A5133E391D3FD49A | |||
| 3396 | msiexec.exe | C:\Program Files\FastTrack Software\Admin By Request\ProcMon.sys | executable | |
MD5:B1060A68BC6D063FA61099C006937495 | SHA256:5442A2A266EFB9F6DA363D9A75188C50C229342836EDE71B76C767A5AB59B0E5 | |||
| 3396 | msiexec.exe | C:\Program Files\Common Files\VAudio\Interop.Exe | executable | |
MD5:A4A5695A68463C073C9CE479479EEE5A | SHA256:684E2CDF6270401C3B6678936004F708DBB26AC4ECA11C85CA5EF0BA5891A9A9 | |||
| 3396 | msiexec.exe | C:\Program Files\Common Files\VAudio\Loader.Exe | executable | |
MD5:8C4BE1B51FA71498545DA769F610AA39 | SHA256:3E0659BB412E78F049A2F2F080DC9E19008C8020B2566AB13B94ABDD3C652491 | |||
| 3396 | msiexec.exe | C:\Program Files\FastTrack Software\Admin By Request\Shell.dll | executable | |
MD5:131F9A5ABF0F04E166CB0C7768F4C4ED | SHA256:AF7535903606088E00D02778DFA35CC938BBEF485F28367325769125DA40D387 | |||
| 3396 | msiexec.exe | C:\Program Files\FastTrack Software\Admin By Request\Shell.exe | executable | |
MD5:7A37ACA78F21B462A1AC0F0E13F54FD0 | SHA256:220472181658F89ECE47B13C3510E22B7D8498D9A411196194F25306D2F2F1DE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
13
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 72.247.153.178:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 104.124.11.17:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
3084 | Audckq32.exe | GET | 304 | 72.247.153.178:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?28687b728381fc1a | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 92.122.89.124:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
3084 | Audckq32.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | unknown |
3084 | Audckq32.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAhEhm9tYYXSsl4OtiIihwE%3D | unknown | — | — | unknown |
3084 | Audckq32.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 72.247.153.178:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?67a3611ec3c0260d | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1372 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1372 | svchost.exe | 72.247.153.178:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 104.124.11.17:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 92.122.89.124:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
3084 | Audckq32.exe | 137.117.73.20:443 | api2.adminbyrequest.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3084 | Audckq32.exe | 72.247.153.178:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | whitelisted |
3084 | Audckq32.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
api2.adminbyrequest.com |
| unknown |
ocsp.digicert.com |
| whitelisted |