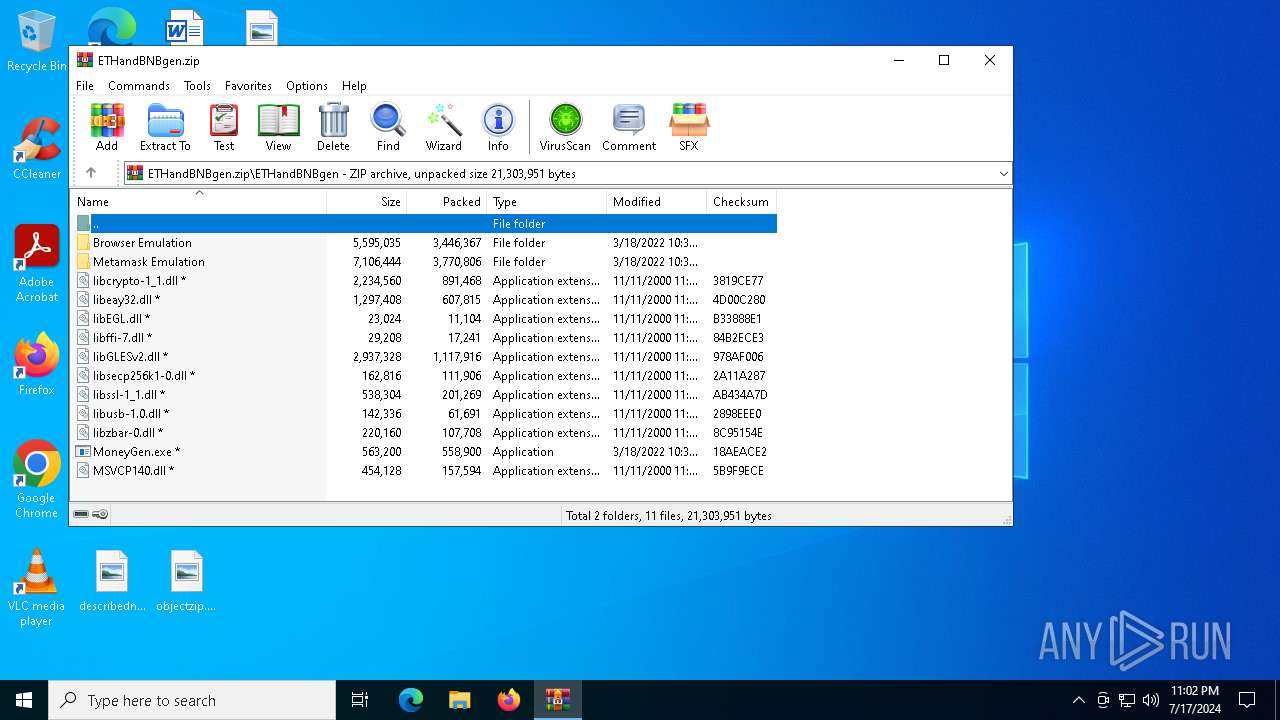
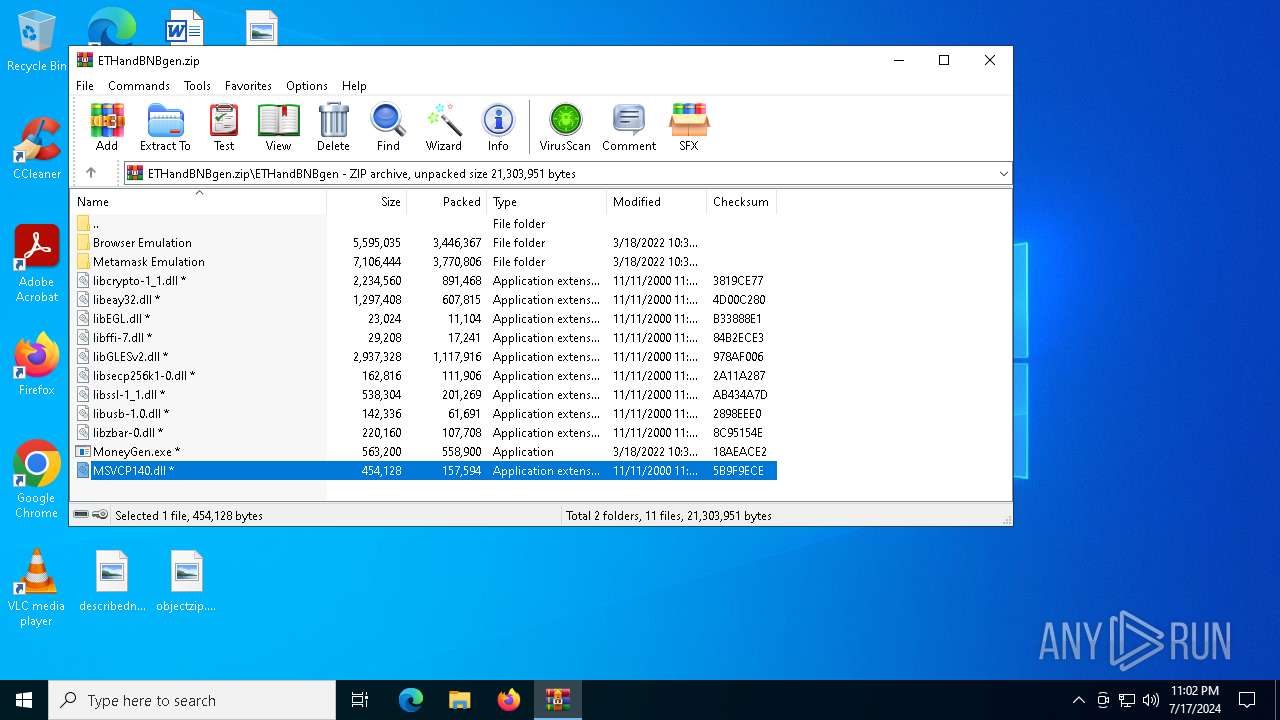
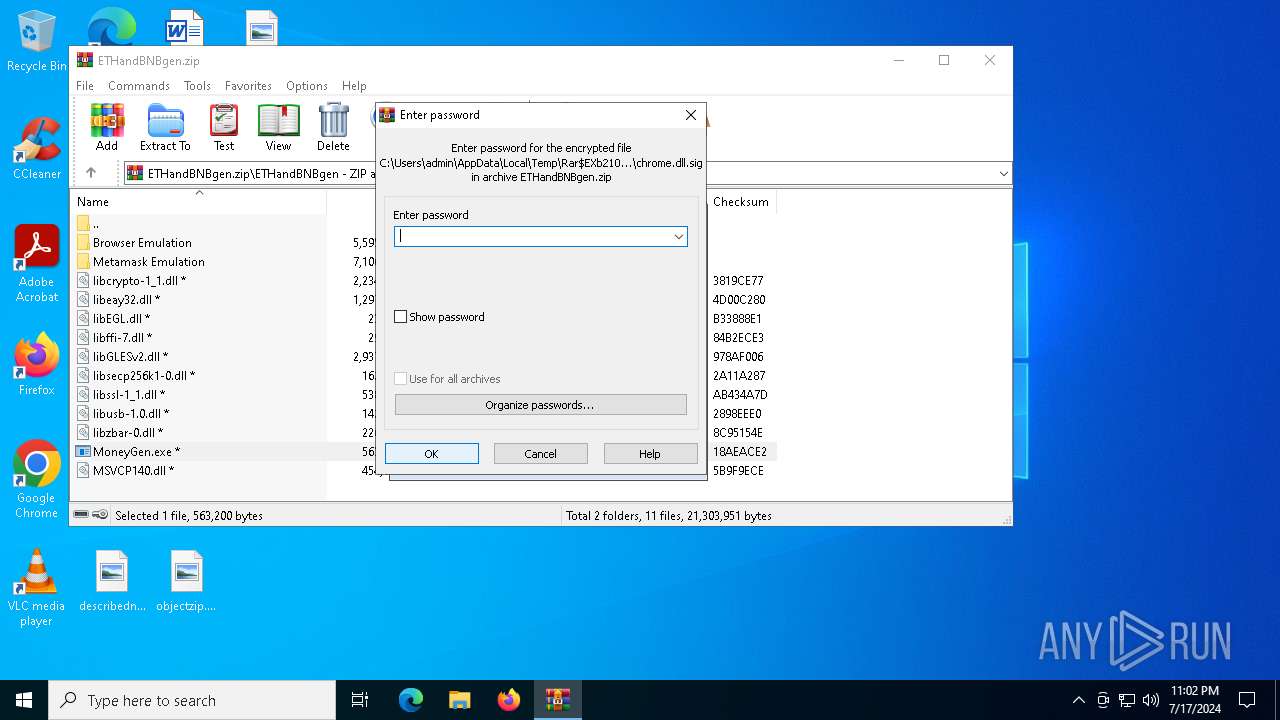
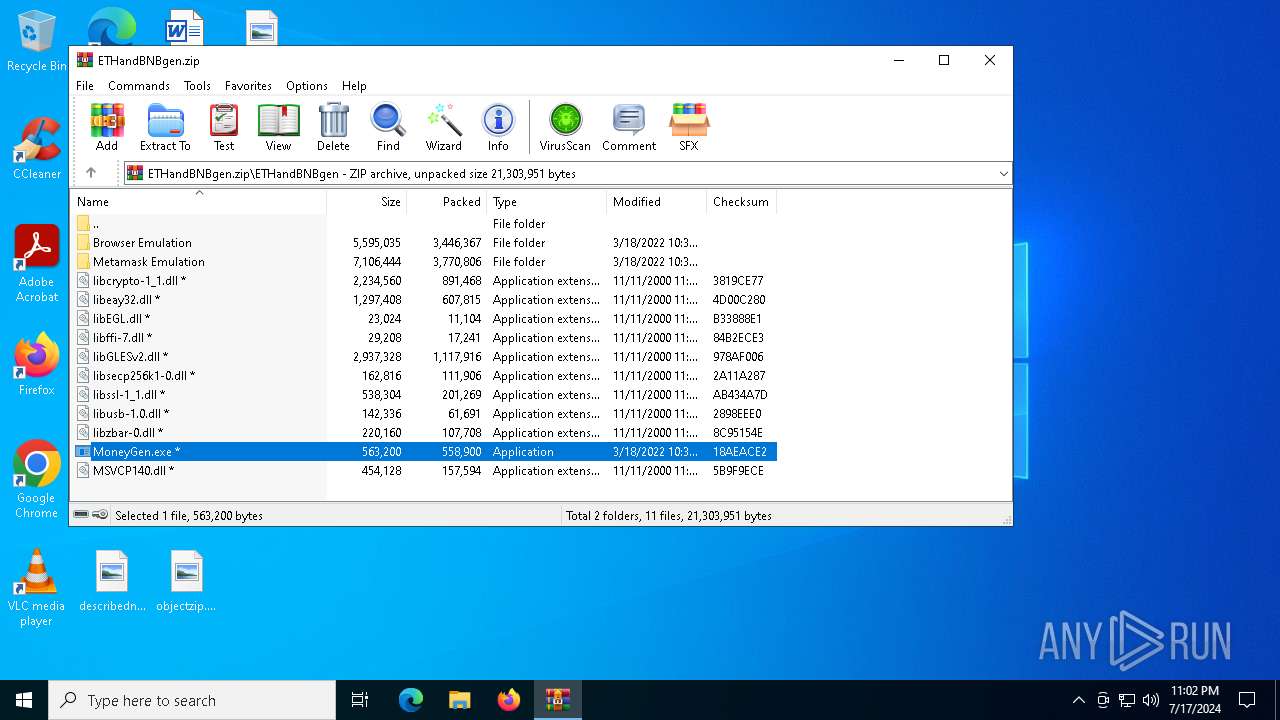
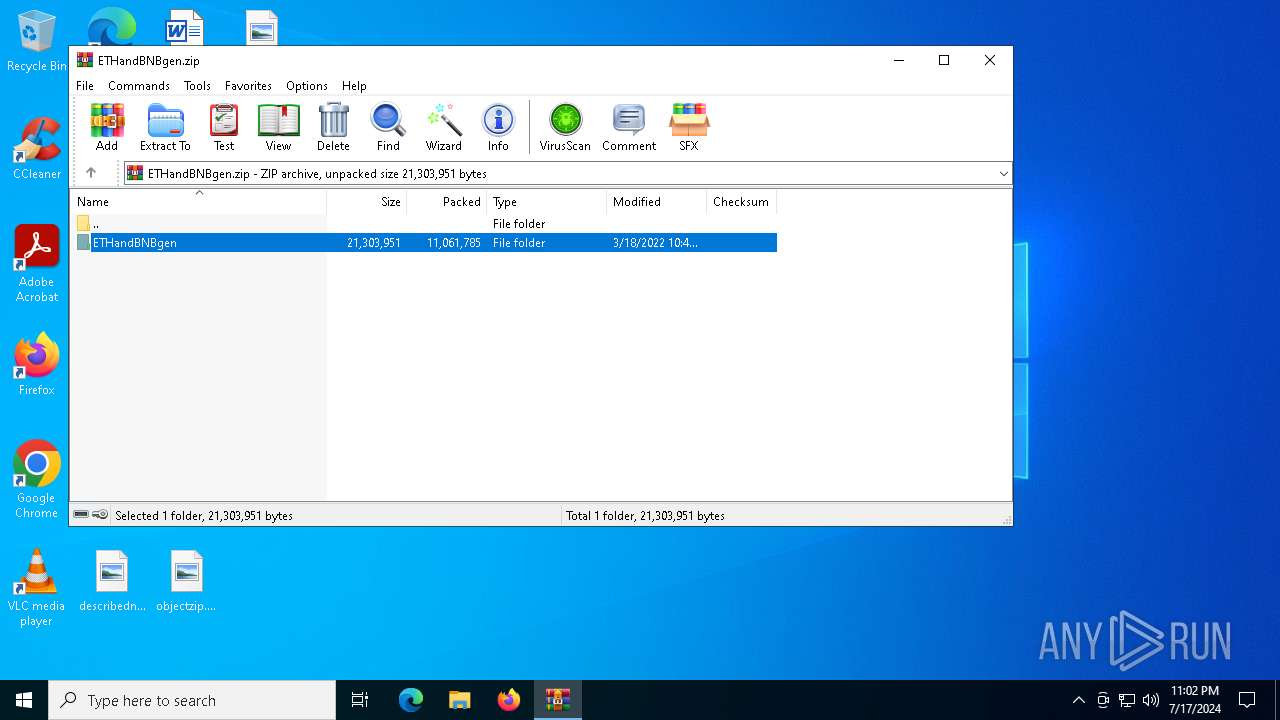
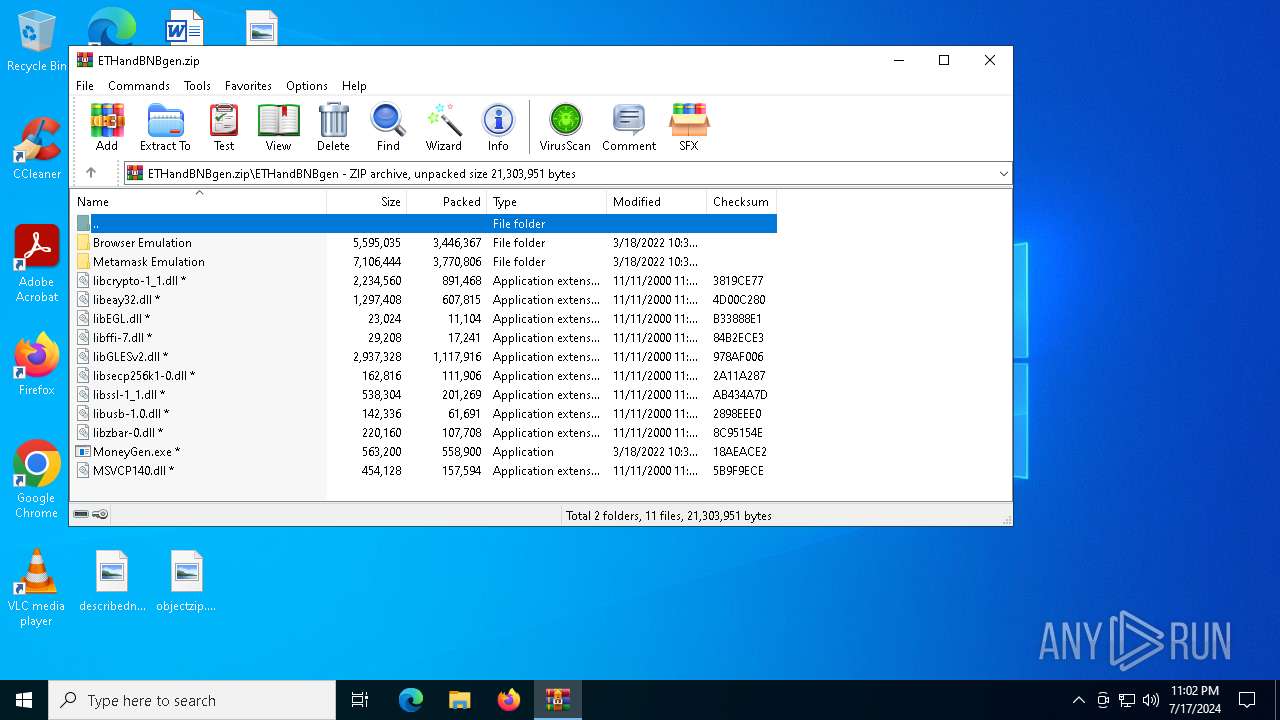
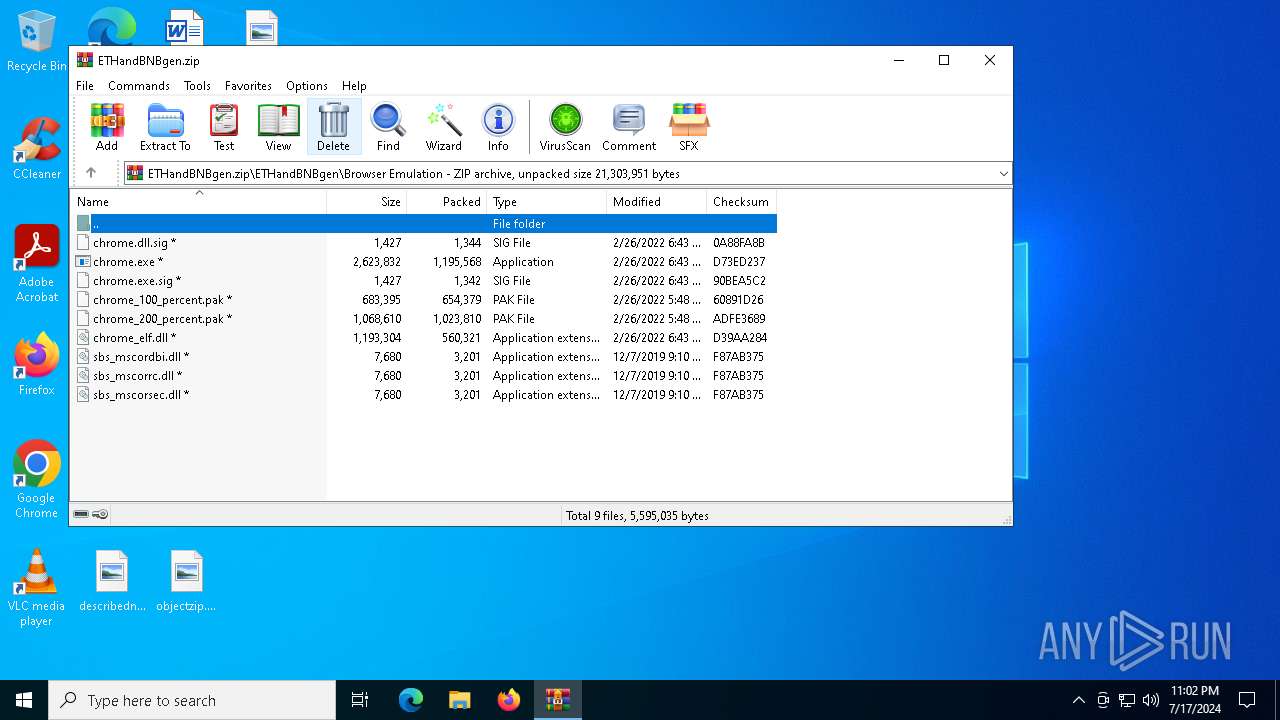
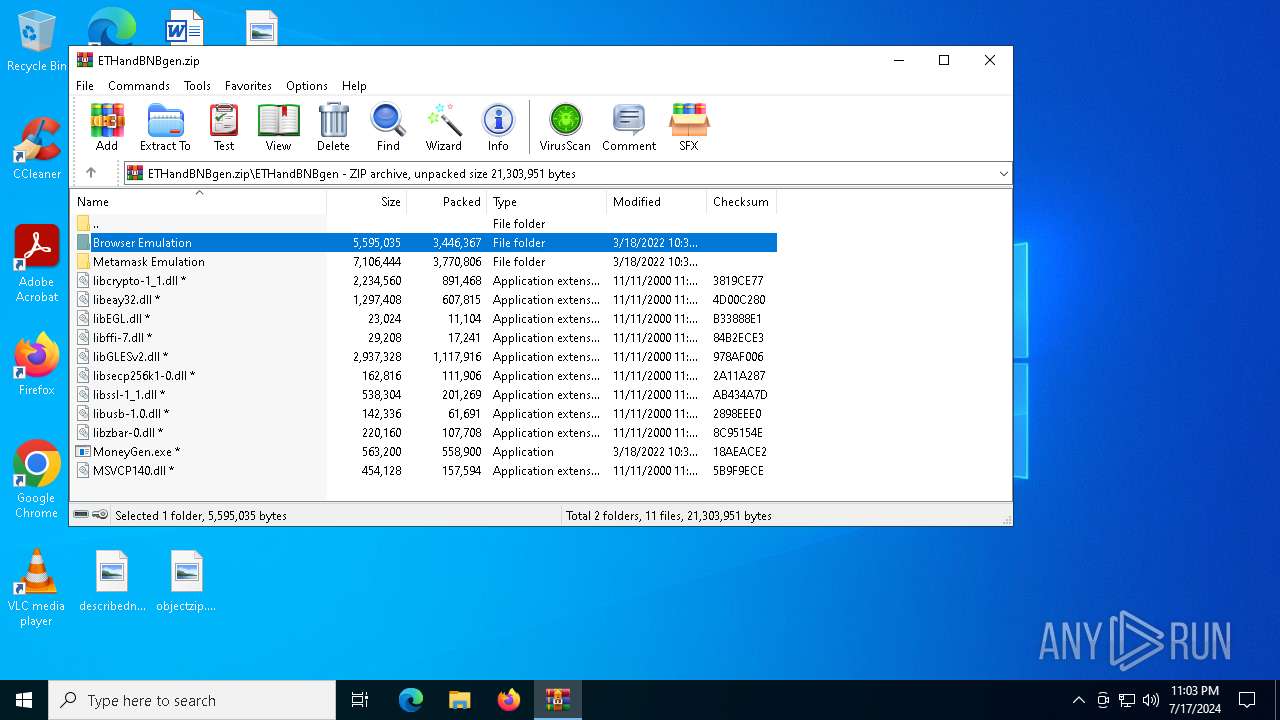
| File name: | ETHandBNBgen.zip |
| Full analysis: | https://app.any.run/tasks/4b7fb57f-65e1-4fec-aef6-2b7d6c5b733e |
| Verdict: | Malicious activity |
| Analysis date: | July 17, 2024, 23:02:03 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | E2FEB040D96AB80F29E47961C6551BFD |
| SHA1: | FD1C48A5EBD7251EF14712320964D58D3659AC41 |
| SHA256: | B6563EFDAF9745B7E05F2D4F3A9363C8A06A90BD6C5789B4C109128FE41195F2 |
| SSDEEP: | 98304:wZjTk8NX7v1BLhNw1yGUi1INtqY76d3yAua4KaxeT0kiN0jcMmbwk8MN8VtqLYfz:1geTiWXRHWgHia0JD8 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2104)
Process drops legitimate windows executable
- WinRAR.exe (PID: 2104)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2104)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2104)
Checks supported languages
- MoneyGen.exe (PID: 1920)
- AppLaunch.exe (PID: 4680)
Reads the computer name
- AppLaunch.exe (PID: 4680)
Reads the machine GUID from the registry
- AppLaunch.exe (PID: 4680)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2022:03:18 18:40:02 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | ETHandBNBgen/ |
Total processes
133
Monitored processes
4
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1920 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2104.15105\ETHandBNBgen\MoneyGen.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2104.15105\ETHandBNBgen\MoneyGen.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2104 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\ETHandBNBgen.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4680 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe | MoneyGen.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET ClickOnce Launch Utility Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 5228 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | MoneyGen.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 714
Read events
7 685
Write events
29
Delete events
0
Modification events
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\ETHandBNBgen.zip | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
17
Suspicious files
9
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
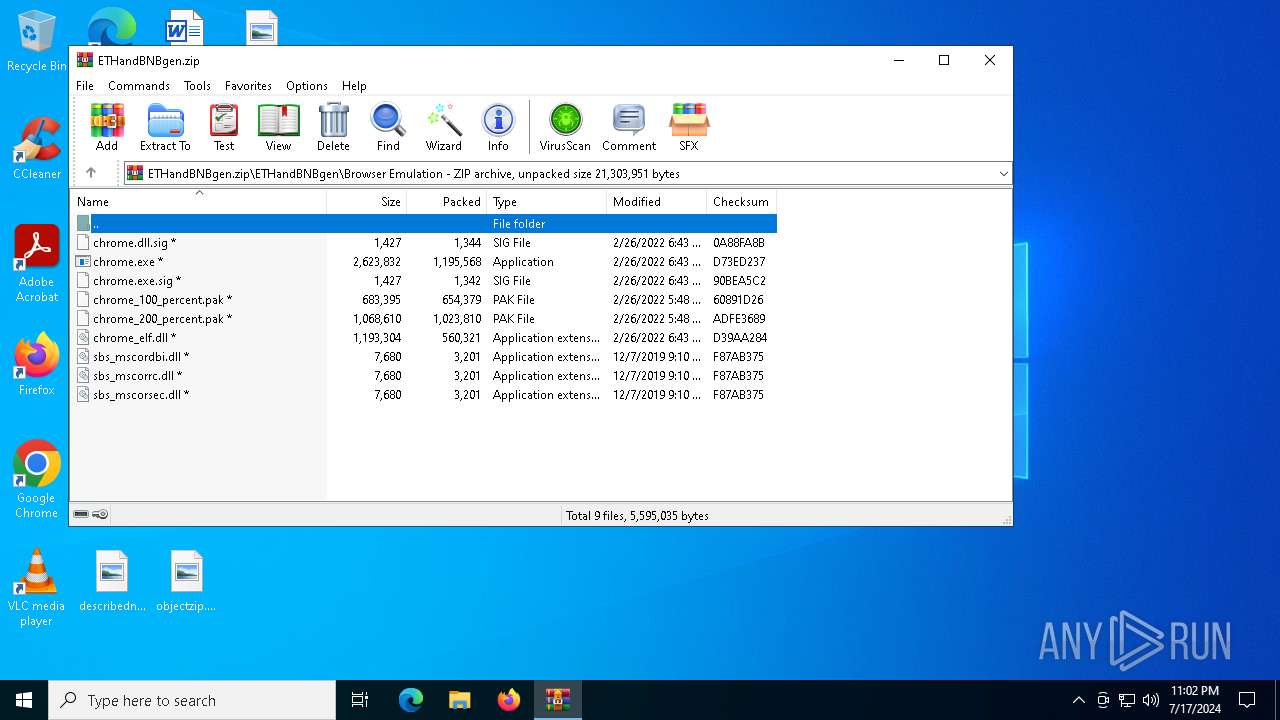
| 2104 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2104.15105\ETHandBNBgen\Browser Emulation\chrome.dll.sig | binary | |
MD5:725F1DF138C65F82FD1B418066CFE80D | SHA256:61DB5F0D075E9EA9BDA5055FE89AA4288D2018B17C4B5870020A574042B71685 | |||
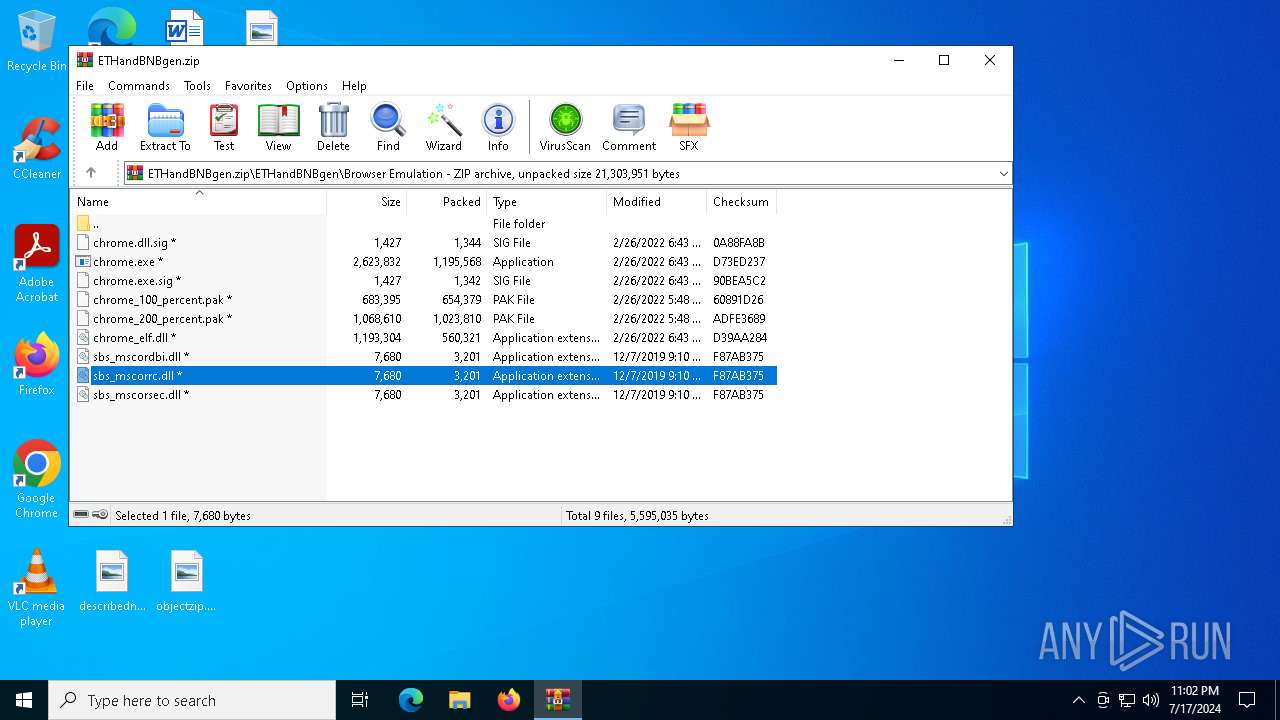
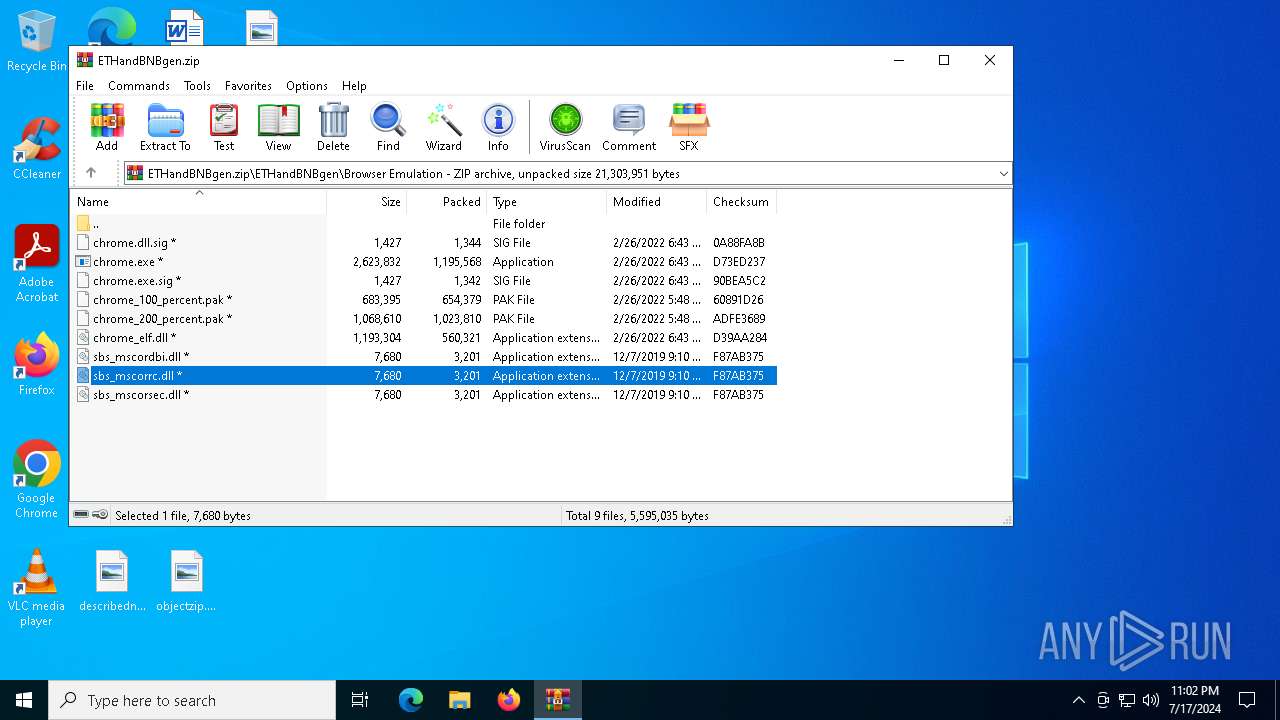
| 2104 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2104.15105\ETHandBNBgen\Browser Emulation\sbs_mscorrc.dll | executable | |
MD5:A1A3F9E8A096B629CBA87F9A1EF0CAC6 | SHA256:118361EDEB3AE2C7F791A454FD08969F8D8288D735DB44A3C150BAFE332D4A66 | |||
| 2104 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2104.15105\ETHandBNBgen\Browser Emulation\sbs_mscordbi.dll | executable | |
MD5:A1A3F9E8A096B629CBA87F9A1EF0CAC6 | SHA256:118361EDEB3AE2C7F791A454FD08969F8D8288D735DB44A3C150BAFE332D4A66 | |||
| 2104 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2104.15105\ETHandBNBgen\Browser Emulation\chrome_200_percent.pak | binary | |
MD5:16996BD829DB5A6C697D7CEE6F2EC753 | SHA256:D809BF0B6DF7F4DCEC443D2E58A7163A085F6D94300C36954454C98931F70C42 | |||
| 2104 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2104.15105\ETHandBNBgen\libsecp256k1-0.dll | executable | |
MD5:86F9A94EA3E532631858FE716D5A705A | SHA256:81C322BC990F3E9F0D4DCB5E441A6D6CAAC0D784A607D559D912D4D1CB43BFEC | |||
| 2104 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2104.15105\ETHandBNBgen\libcrypto-1_1.dll | executable | |
MD5:76DA35FDE4E3E110331612AB351A811C | SHA256:ECABC901FA89CD771405C004849384A5148644C273A88048AE16C86BD14EF4DD | |||
| 2104 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2104.15105\ETHandBNBgen\Browser Emulation\sbs_mscorsec.dll | executable | |
MD5:A1A3F9E8A096B629CBA87F9A1EF0CAC6 | SHA256:118361EDEB3AE2C7F791A454FD08969F8D8288D735DB44A3C150BAFE332D4A66 | |||
| 2104 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2104.15105\ETHandBNBgen\libffi-7.dll | executable | |
MD5:BC20614744EBF4C2B8ACD28D1FE54174 | SHA256:0C7EC6DE19C246A23756B8550E6178AC2394B1093E96D0F43789124149486F57 | |||
| 2104 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2104.15105\ETHandBNBgen\Browser Emulation\chrome_100_percent.pak | binary | |
MD5:542FCCF0937F7BC6BCA587CA63395A78 | SHA256:046FF2F7C1C6C2C217E65D9883375F4D7E4DCB5ED8192F5588A2361C0E87C773 | |||
| 2104 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2104.15105\ETHandBNBgen\libEGL.dll | executable | |
MD5:371AEB50F7816108B346B67EF2B11E1A | SHA256:12903D93A7F57B479401602A533849E6F813FF5C2C92F3A02D468FC98E7AC1D5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
60
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6072 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4912 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3156 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4912 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4656 | SearchApp.exe | 104.126.37.130:443 | www.bing.com | Akamai International B.V. | DE | unknown |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
4724 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6072 | svchost.exe | 20.190.159.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
arc.msn.com |
| whitelisted |