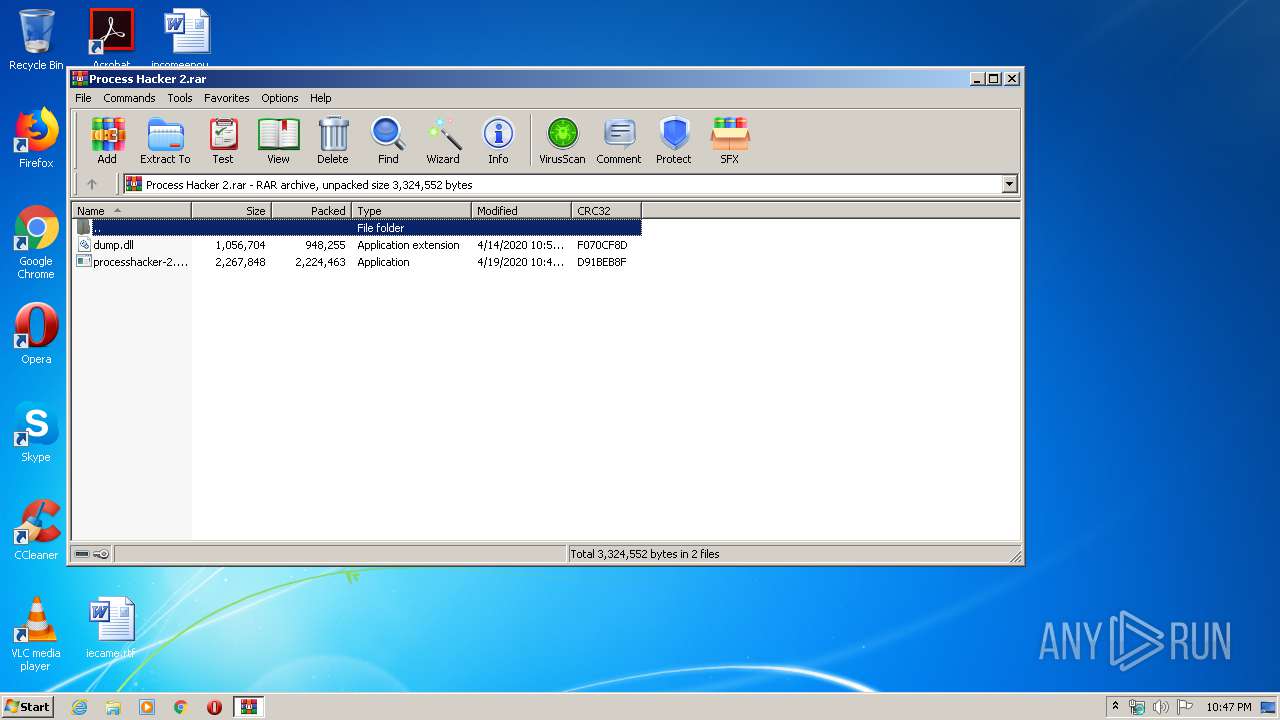
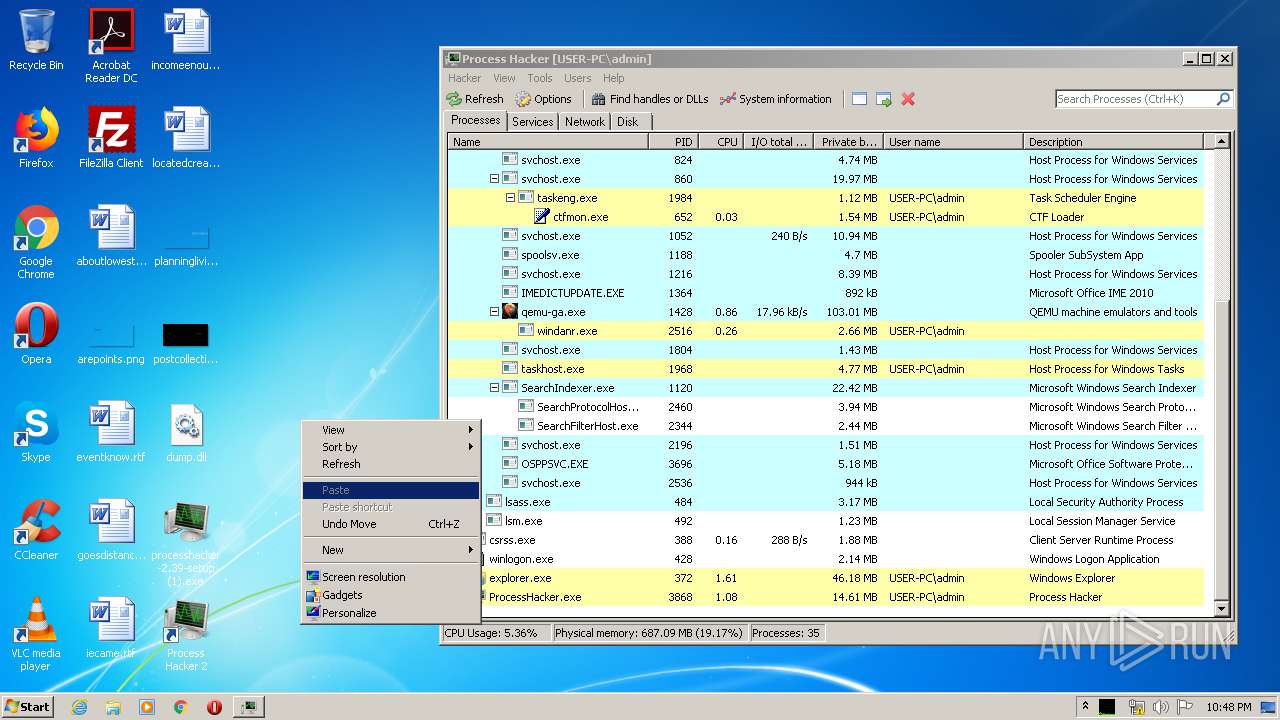
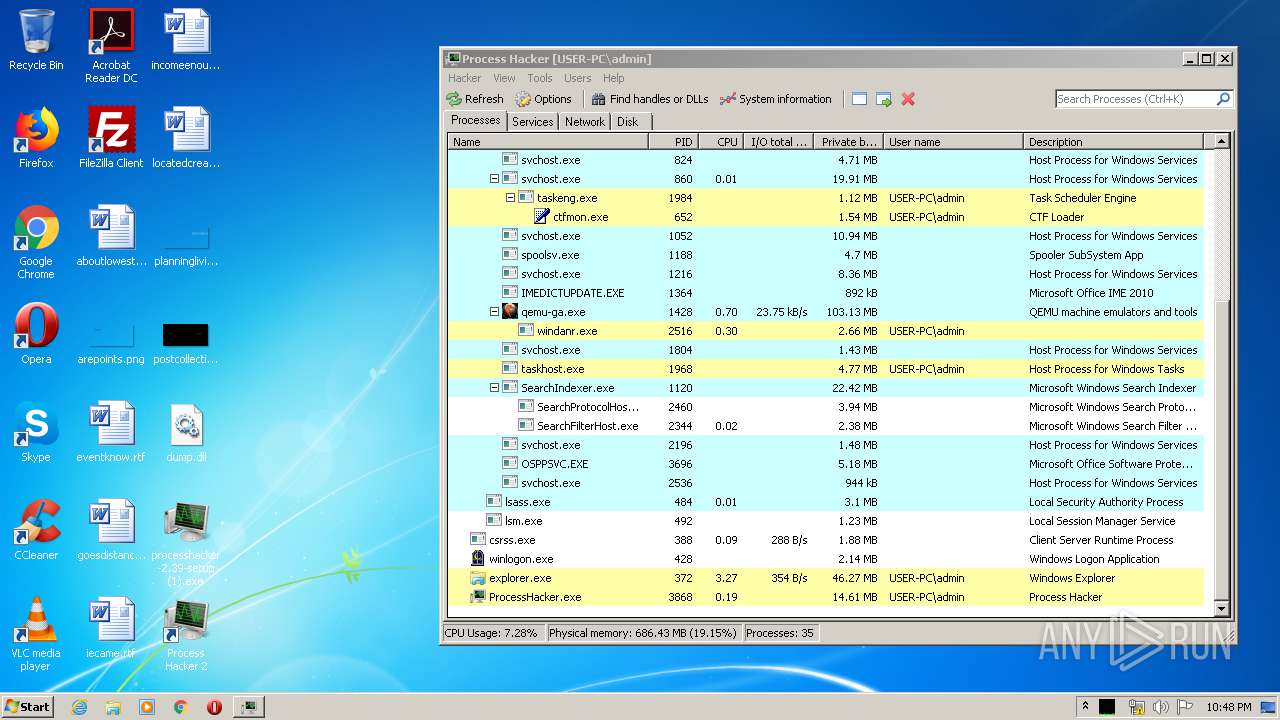
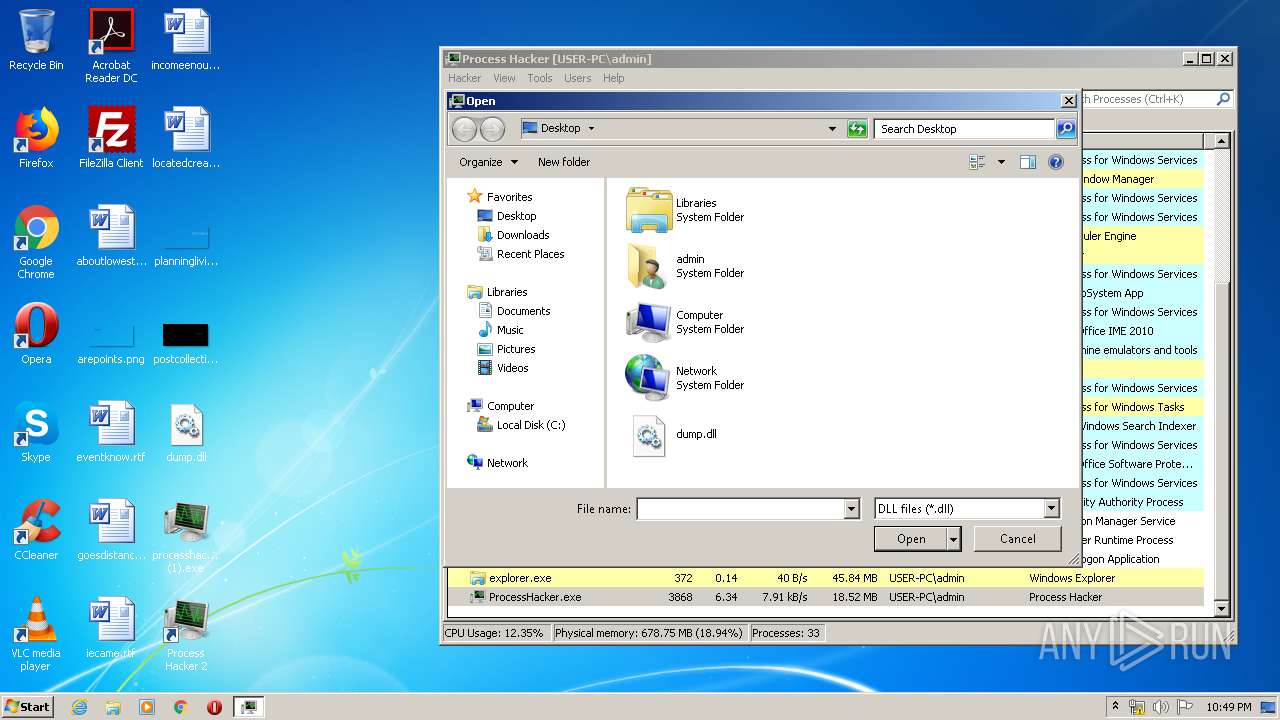
| File name: | Process Hacker 2.rar |
| Full analysis: | https://app.any.run/tasks/12120e47-5611-406f-be82-38eed3981695 |
| Verdict: | Malicious activity |
| Analysis date: | April 19, 2020, 21:47:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 923967427D8B6A6BF2CB006146B4BF99 |
| SHA1: | 39E09EE6F43F8A344BF5A6F87964D2EBF023CE91 |
| SHA256: | B614463EBAE5C1FCDEA2C15731270D619A114F6A04EDBBBE244D4A71420E1621 |
| SSDEEP: | 98304:Ilk3jChxuwDpPLAAOKeiCsJBLVAkOhWYYKHG:vmGCPLOYJBLqZNm |
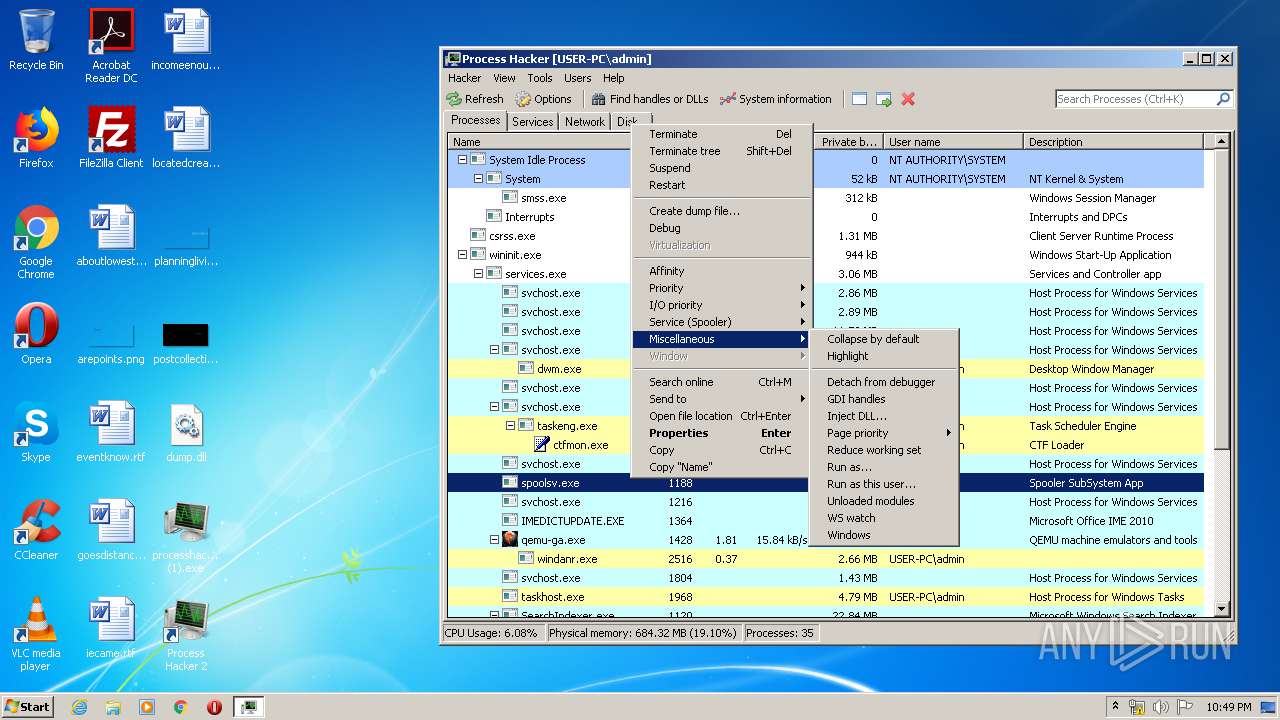
MALICIOUS
Application was dropped or rewritten from another process
- processhacker-2.39-setup (1).exe (PID: 3188)
- processhacker-2.39-setup (1).exe (PID: 3088)
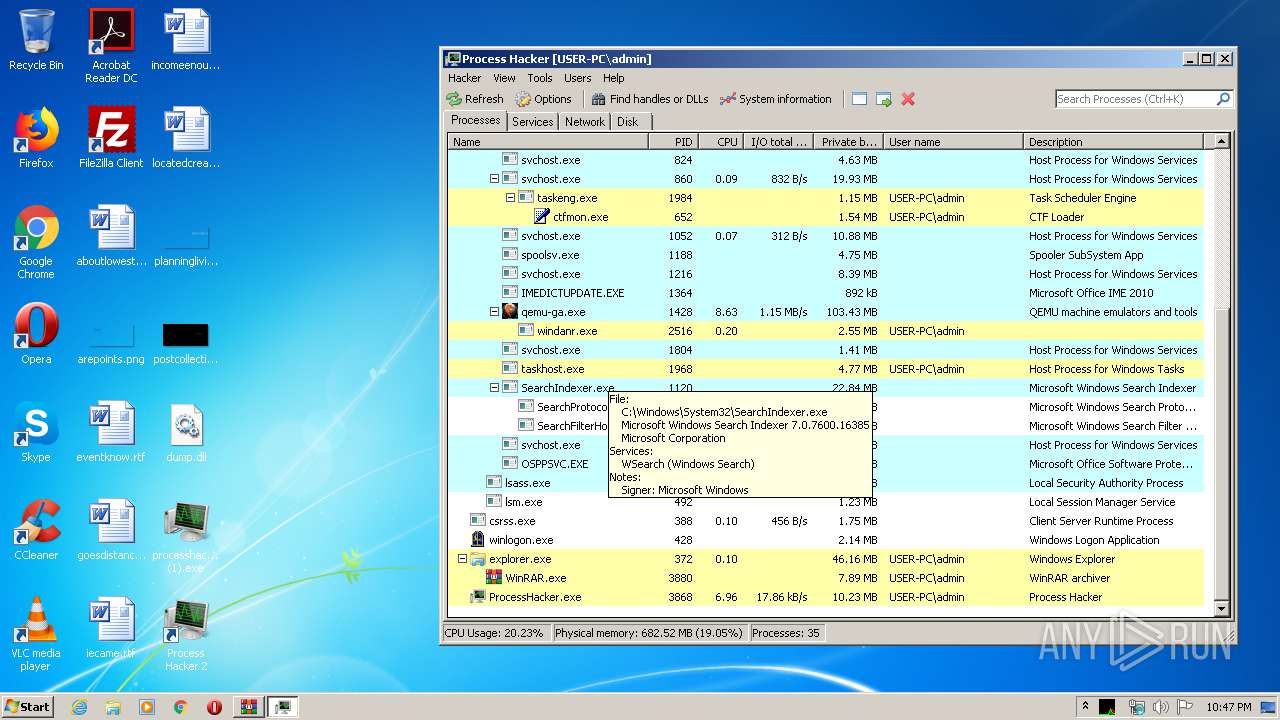
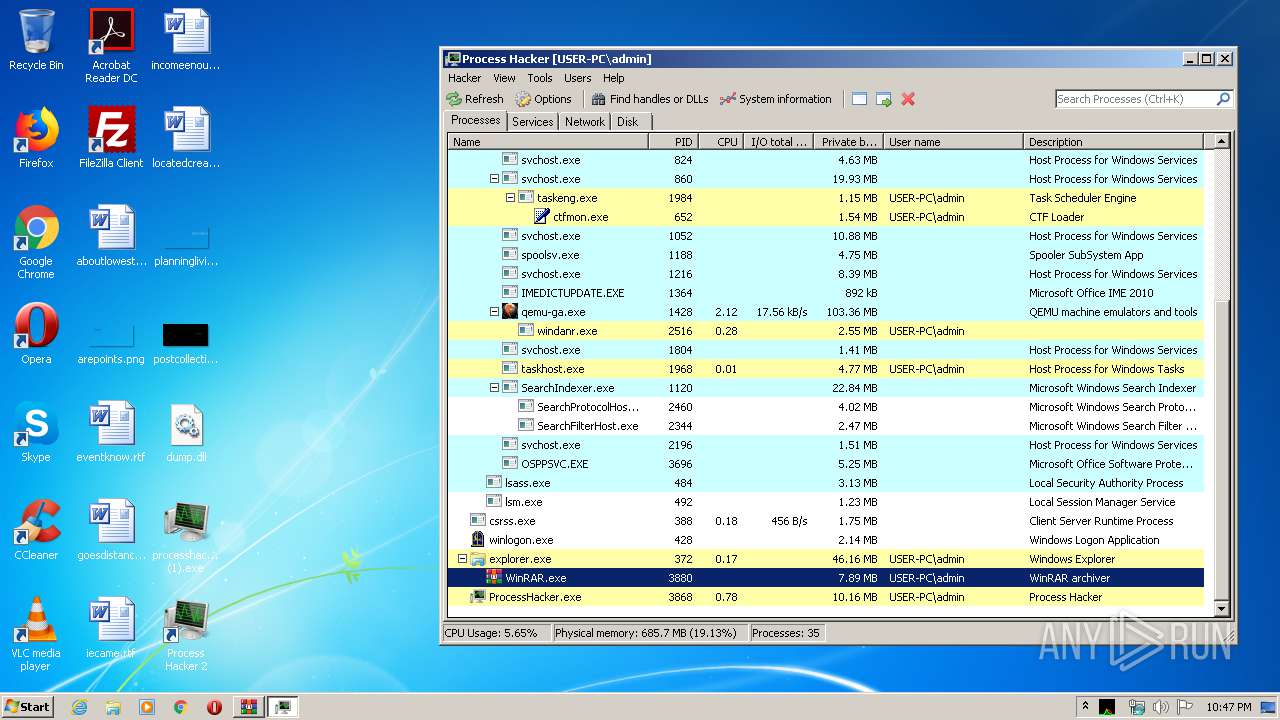
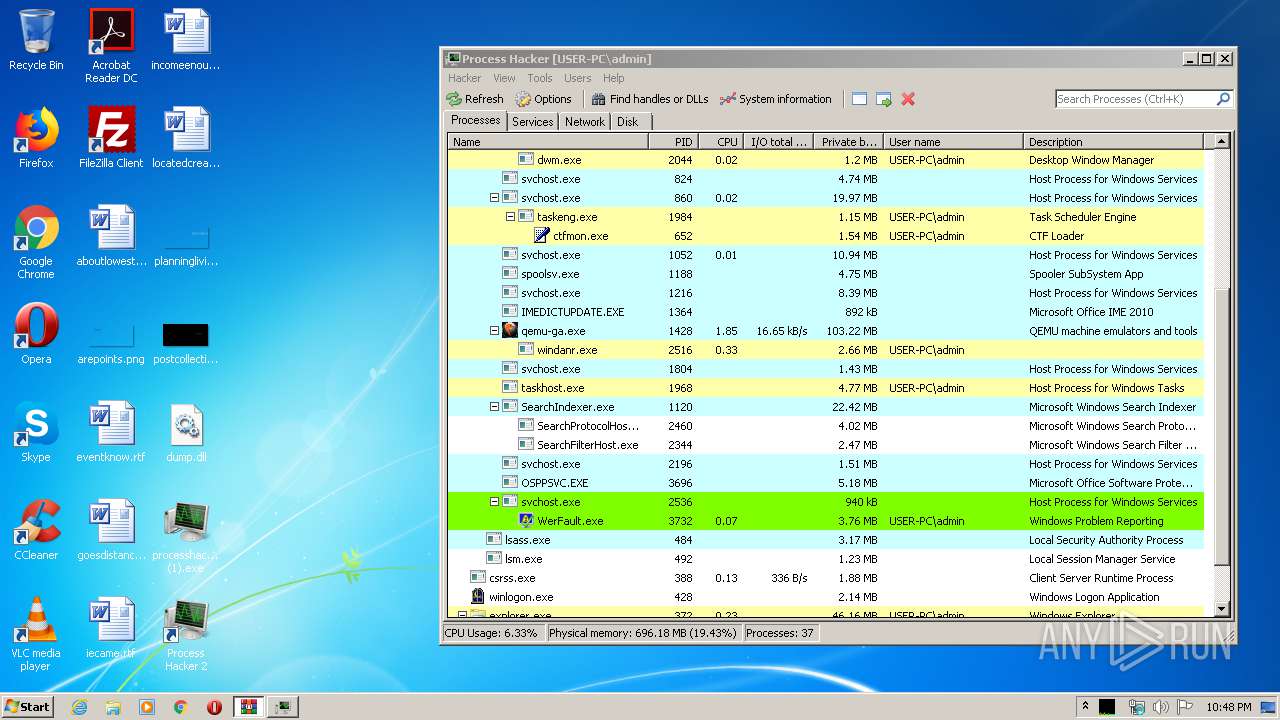
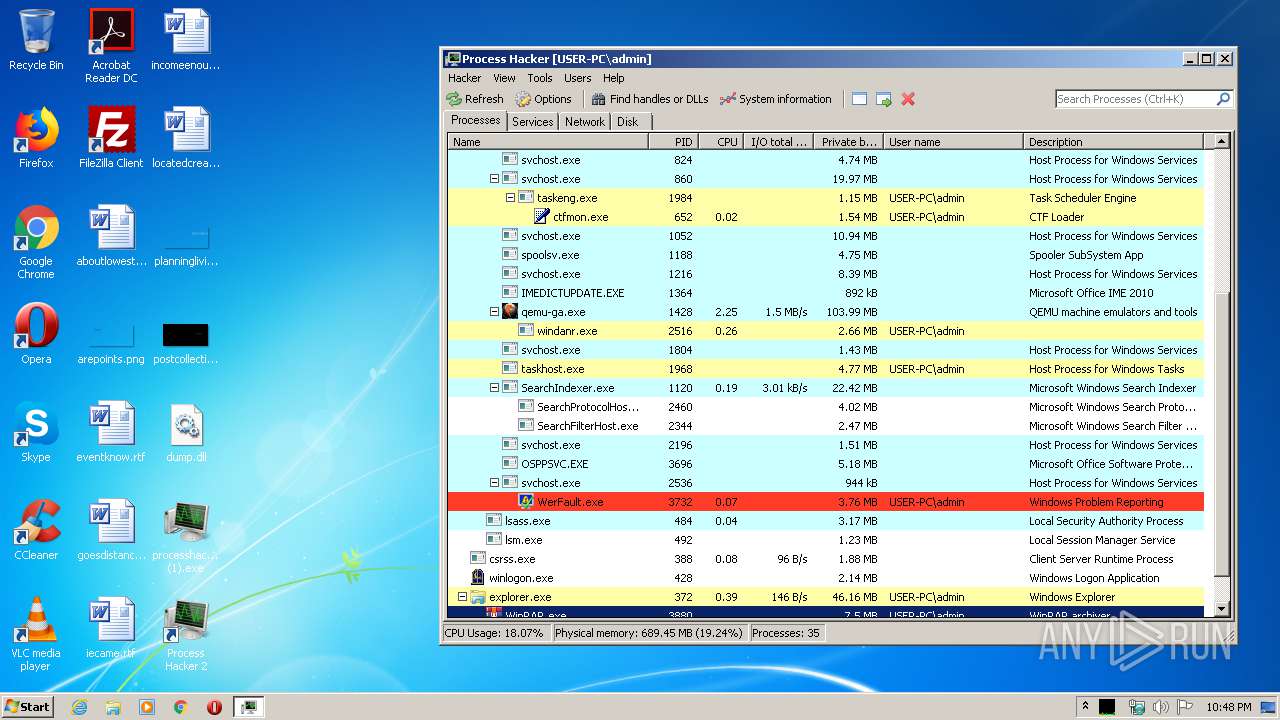
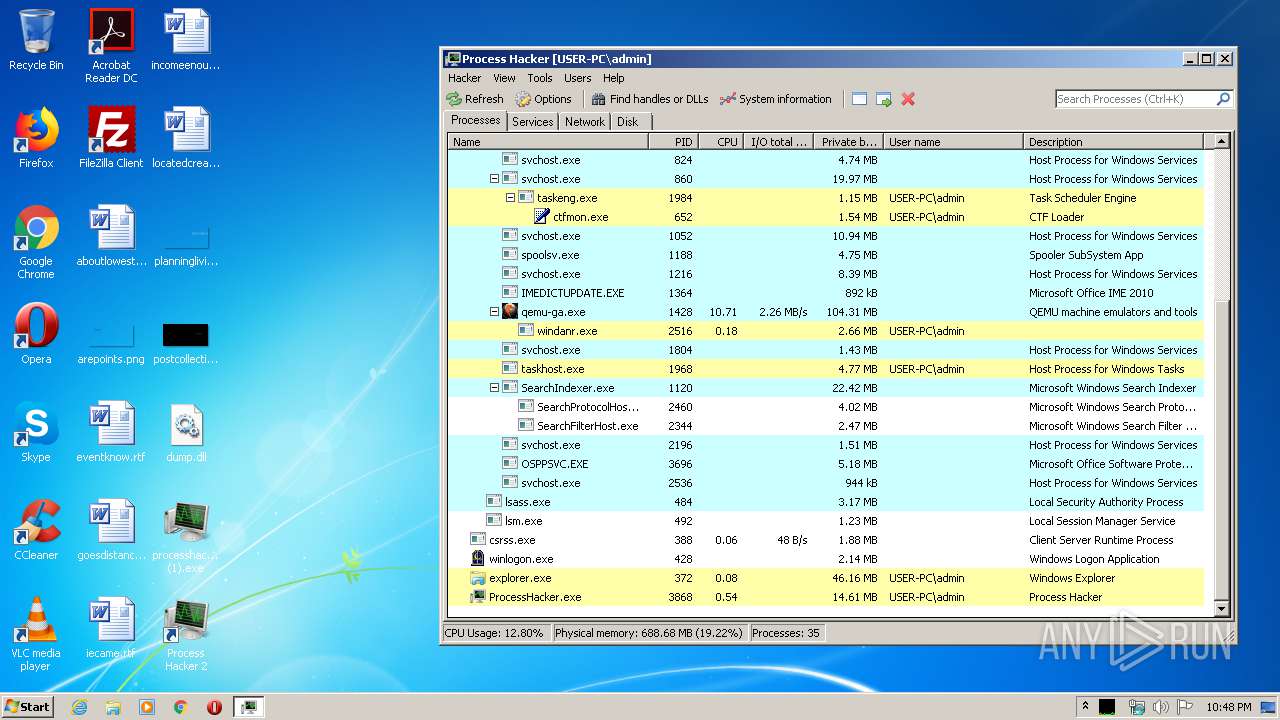
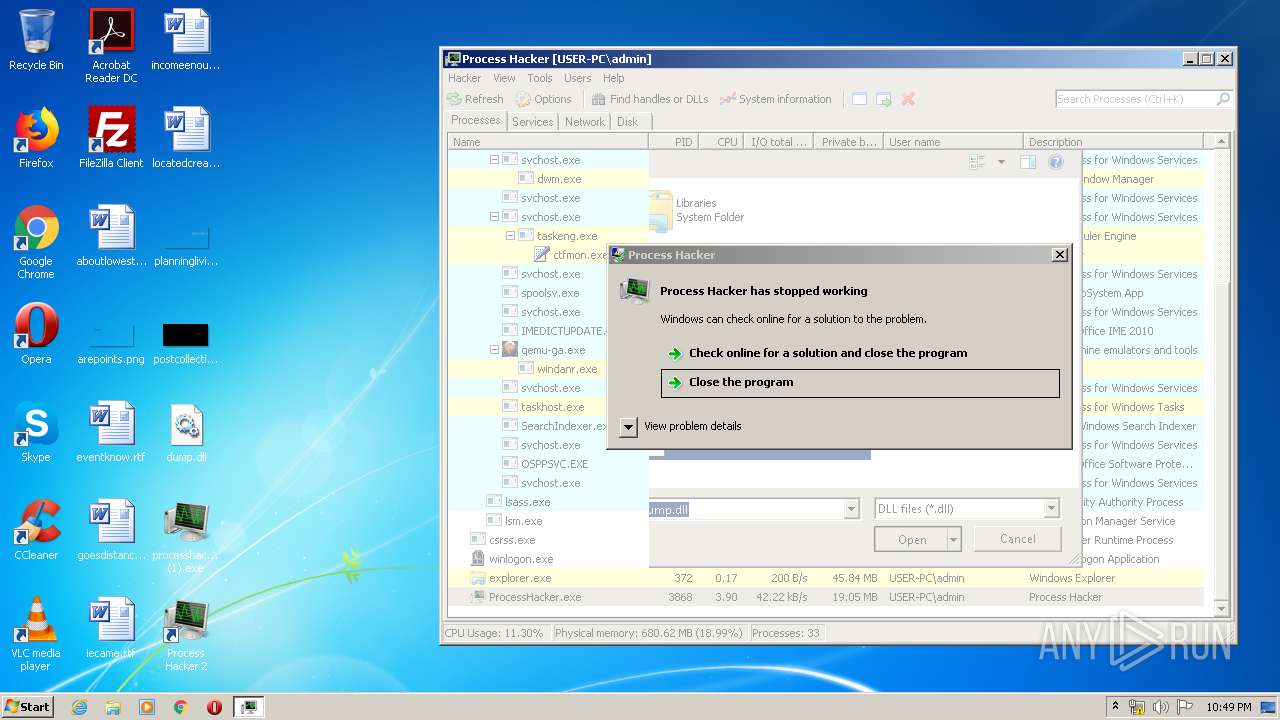
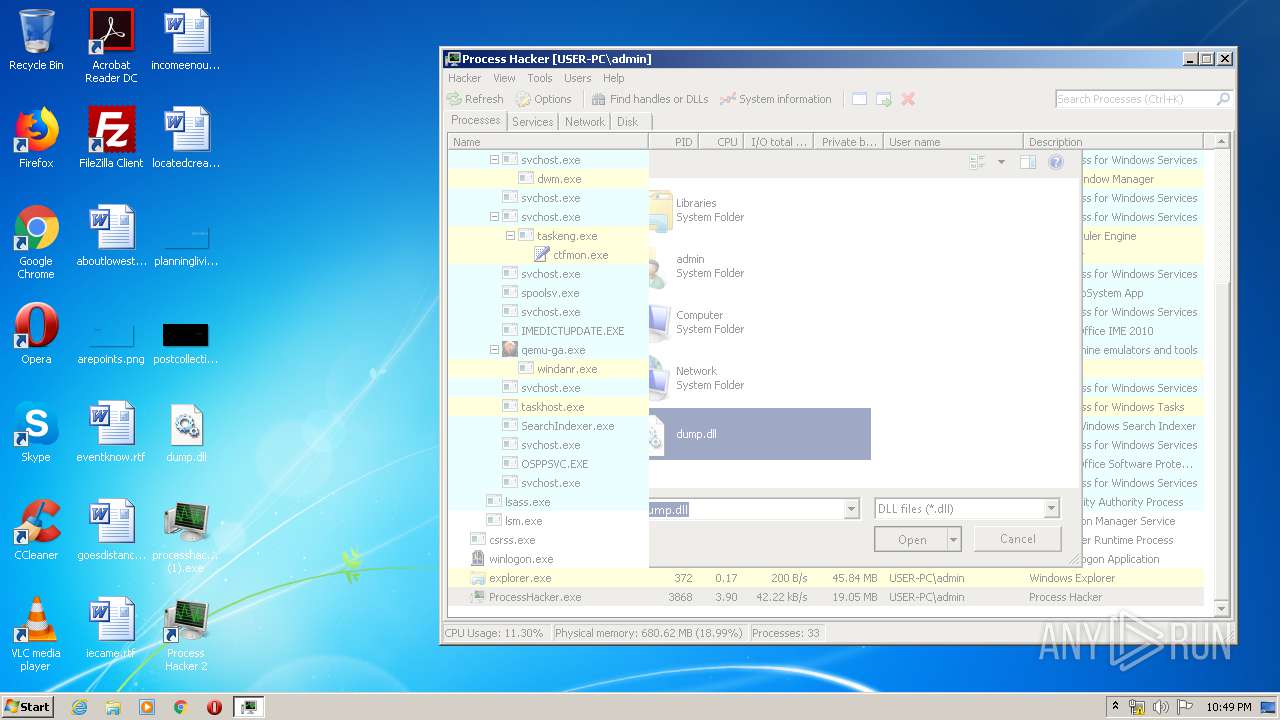
- ProcessHacker.exe (PID: 3868)
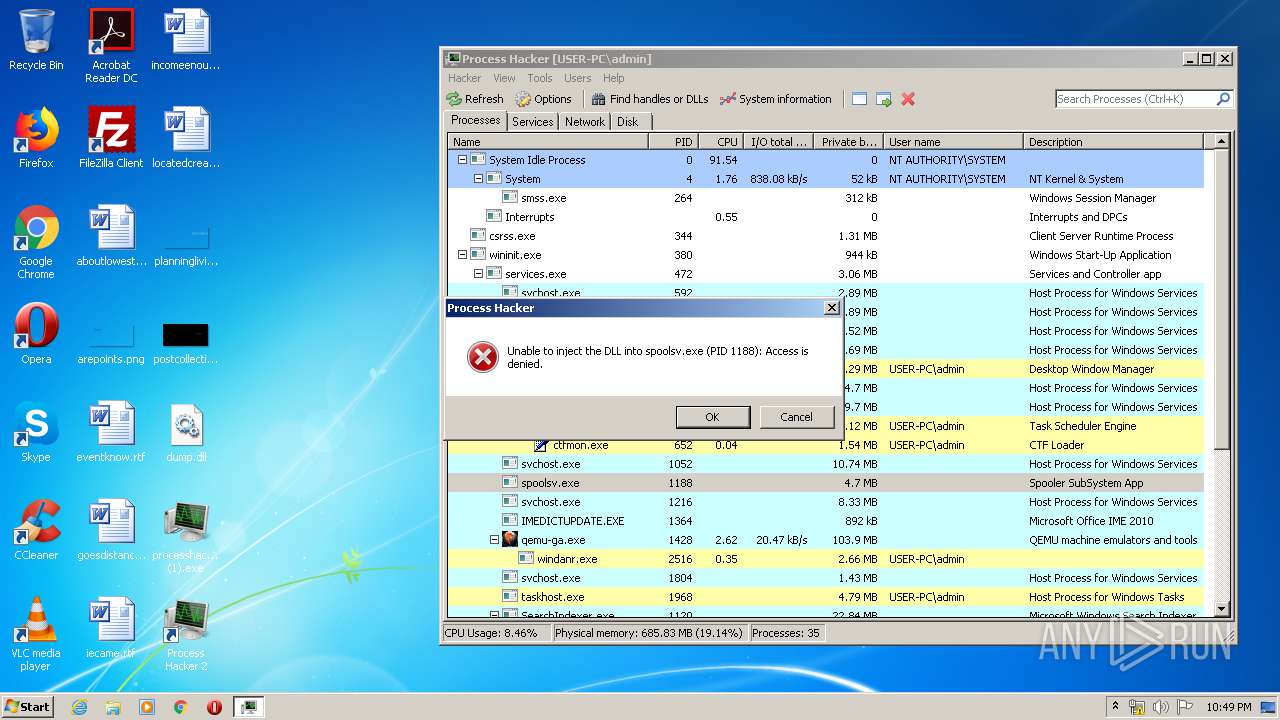
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 2460)
- WinRAR.exe (PID: 3880)
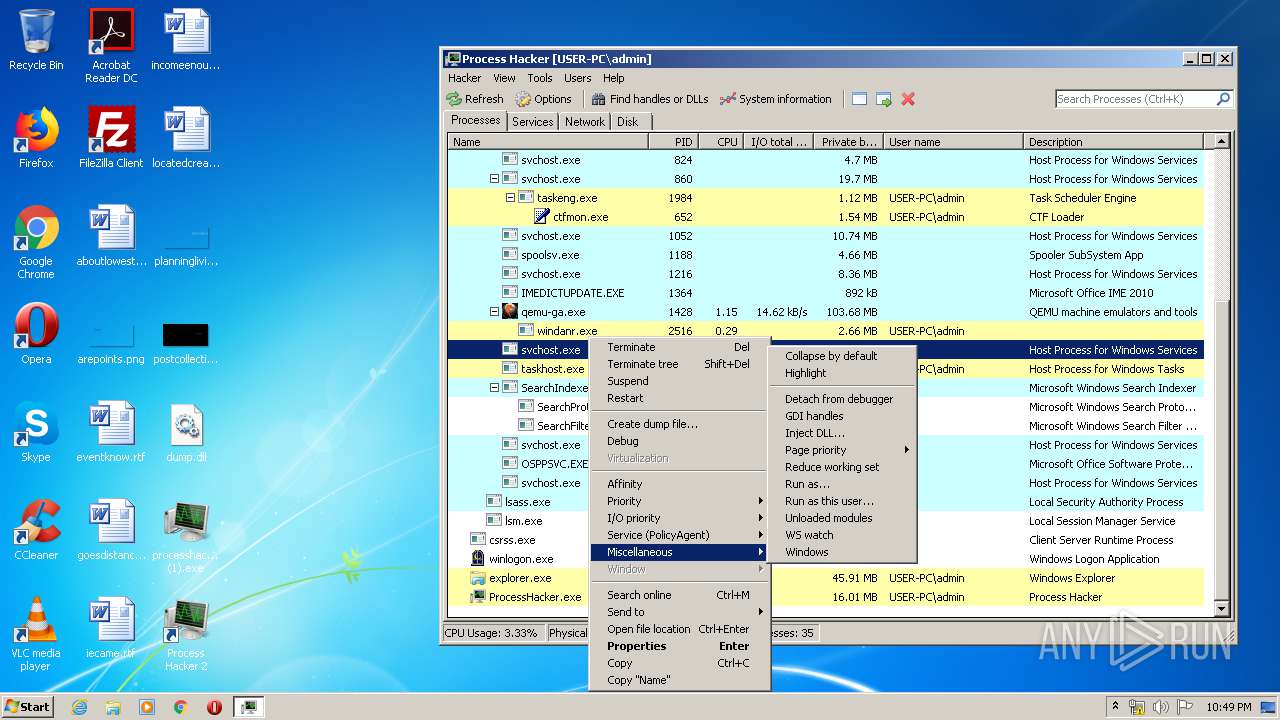
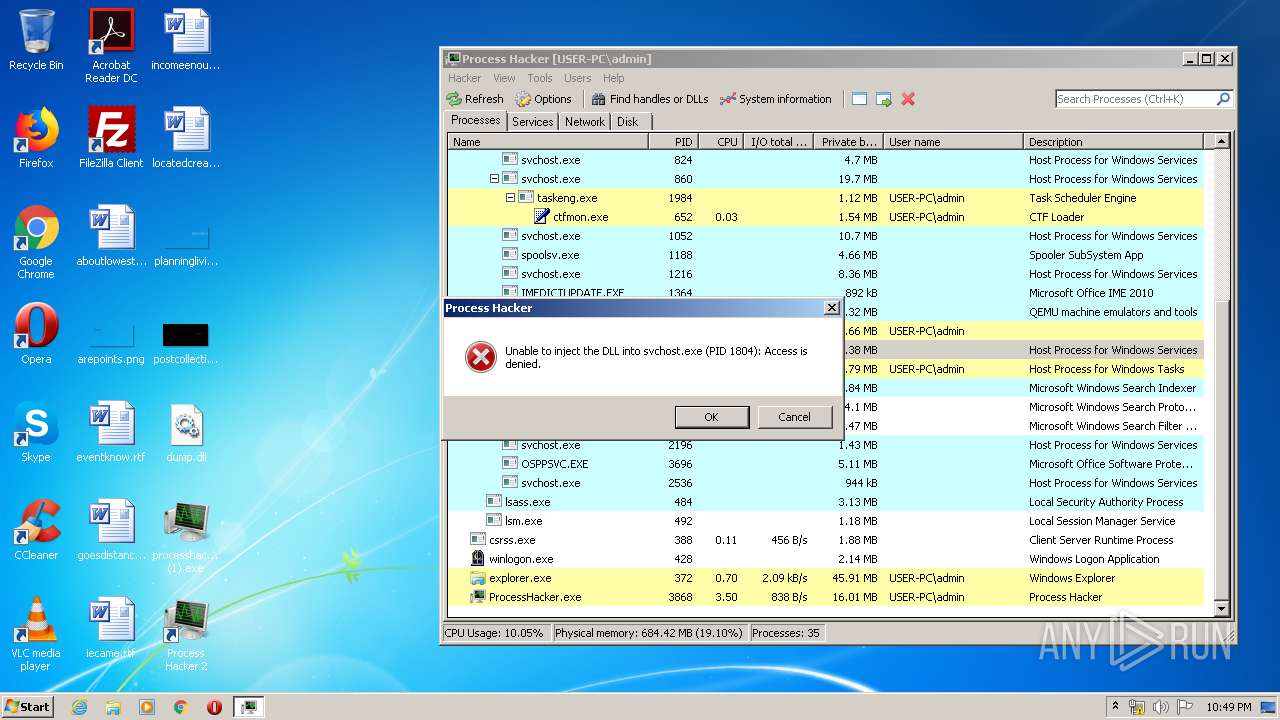
- ProcessHacker.exe (PID: 3868)
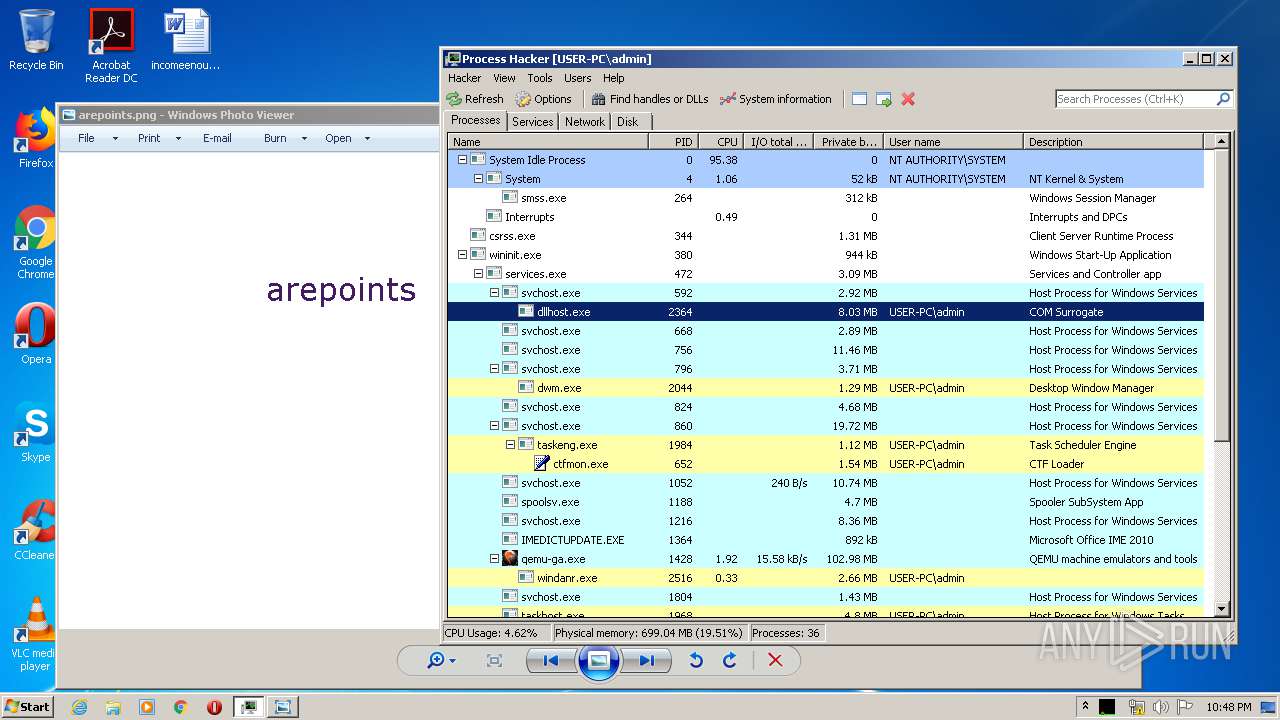
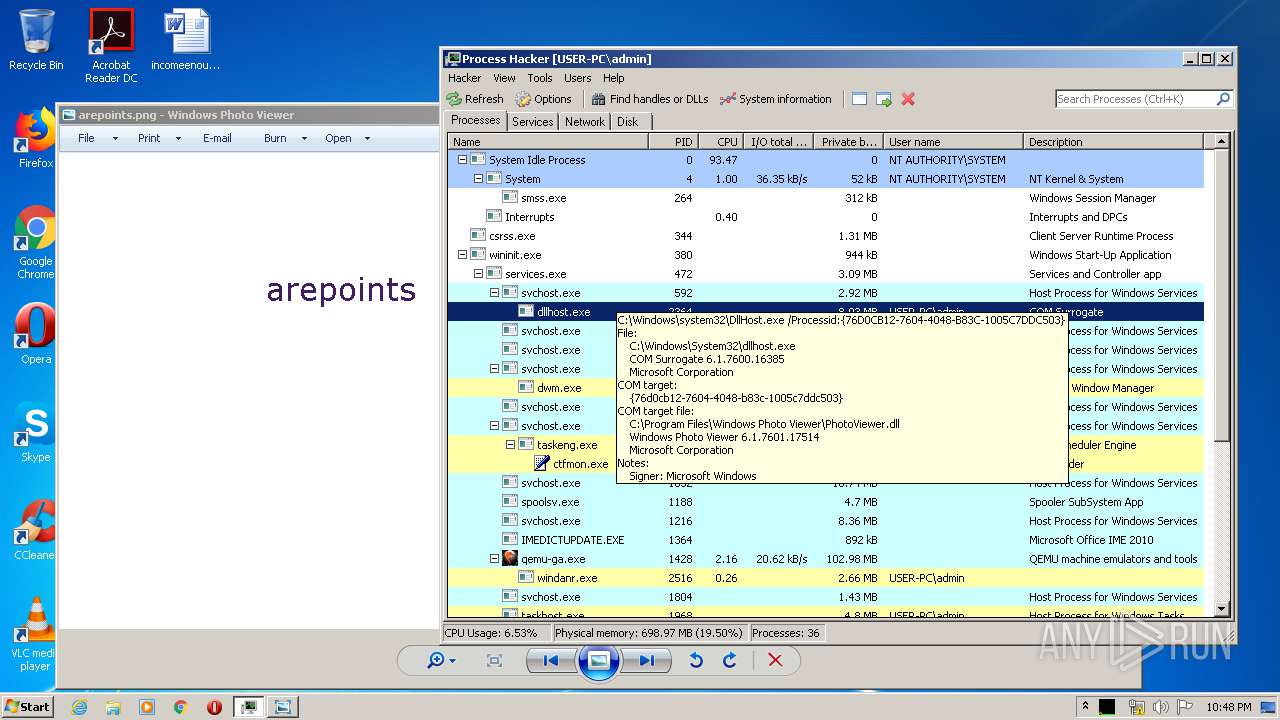
- DllHost.exe (PID: 2364)
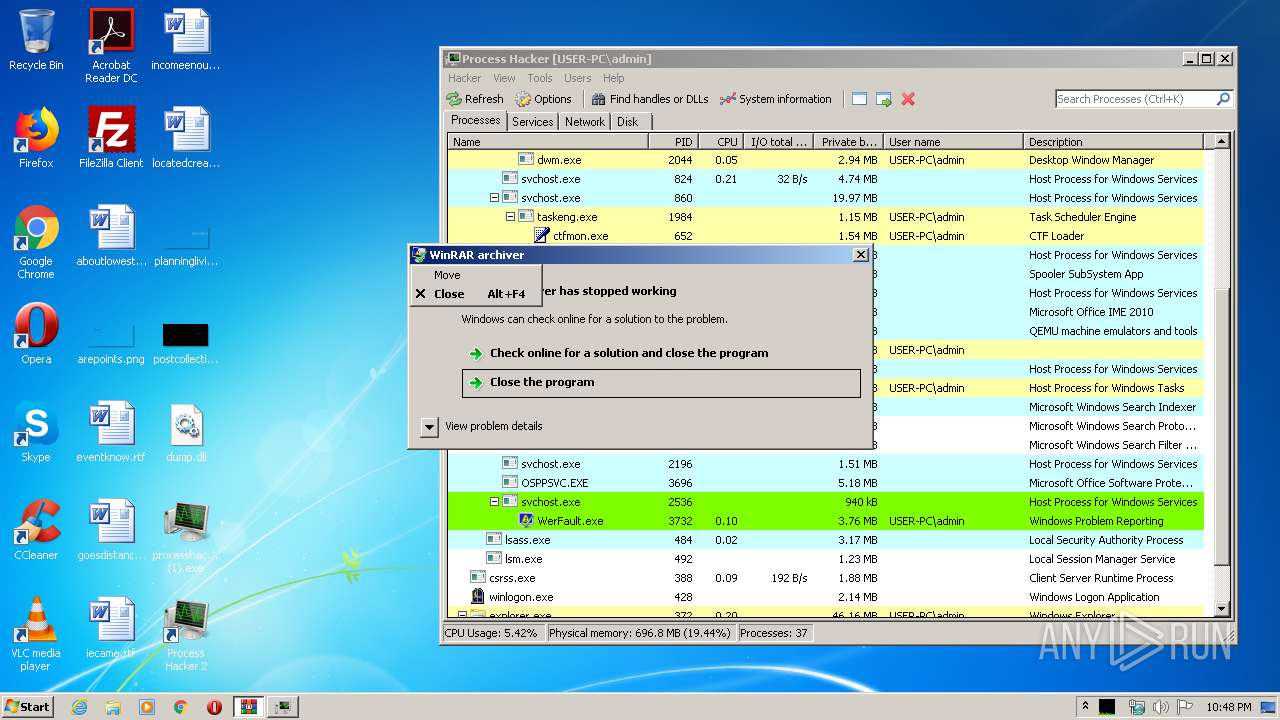
- WerFault.exe (PID: 1836)
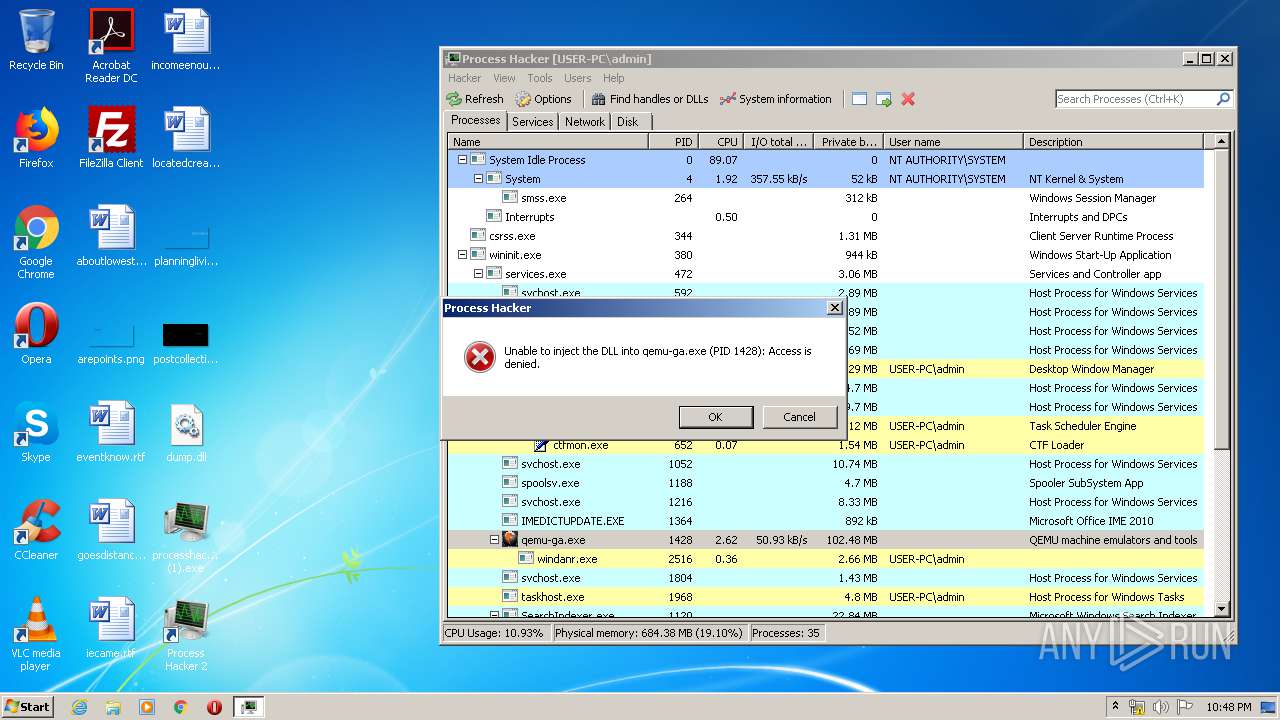
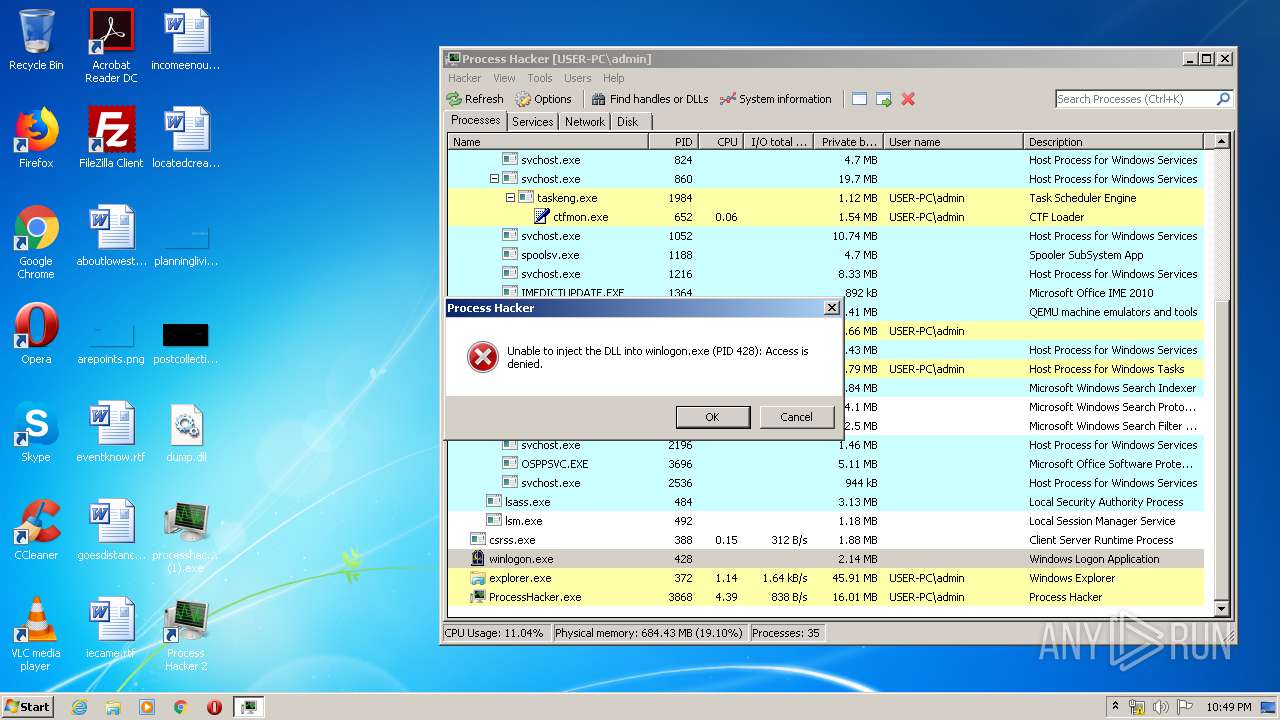
Actions looks like stealing of personal data
- DllHost.exe (PID: 2364)
- ProcessHacker.exe (PID: 3868)
Loads the Task Scheduler COM API
- WerFault.exe (PID: 1836)
- ProcessHacker.exe (PID: 3868)
SUSPICIOUS
Executable content was dropped or overwritten
- processhacker-2.39-setup (1).exe (PID: 3088)
- WinRAR.exe (PID: 3880)
- processhacker-2.39-setup (1).exe (PID: 3188)
- processhacker-2.39-setup (1).tmp (PID: 3892)
Executed via COM
- DllHost.exe (PID: 2364)
INFO
Application was dropped or rewritten from another process
- processhacker-2.39-setup (1).tmp (PID: 3892)
- processhacker-2.39-setup (1).tmp (PID: 2580)
Manual execution by user
- processhacker-2.39-setup (1).exe (PID: 3188)
Loads dropped or rewritten executable
- processhacker-2.39-setup (1).tmp (PID: 3892)
Creates files in the program directory
- processhacker-2.39-setup (1).tmp (PID: 3892)
Creates a software uninstall entry
- processhacker-2.39-setup (1).tmp (PID: 3892)
Reads settings of System Certificates
- ProcessHacker.exe (PID: 3868)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
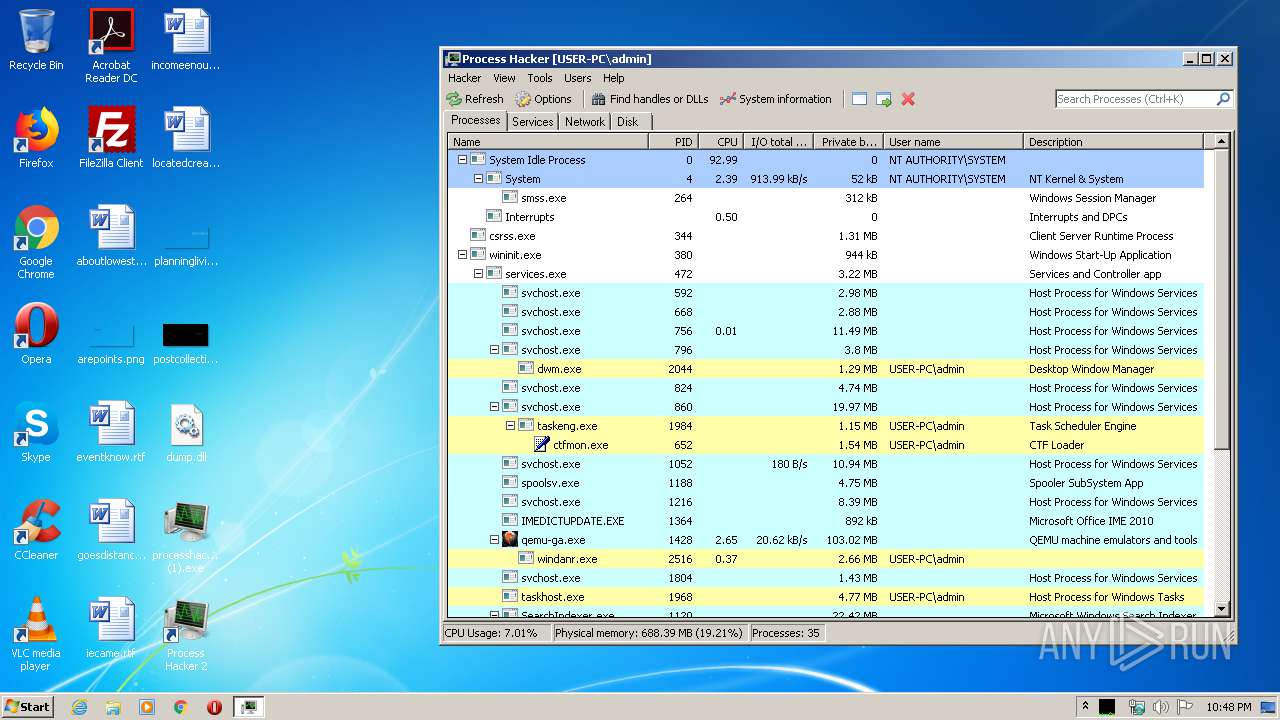
Total processes
50
Monitored processes
9
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1836 | C:\Windows\system32\WerFault.exe -u -p 3868 -s 2900 | C:\Windows\system32\WerFault.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2364 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 3221225477 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2460 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2580 | "C:\Users\admin\AppData\Local\Temp\is-JLTCP.tmp\processhacker-2.39-setup (1).tmp" /SL5="$801E6,1874675,150016,C:\Users\admin\Desktop\processhacker-2.39-setup (1).exe" | C:\Users\admin\AppData\Local\Temp\is-JLTCP.tmp\processhacker-2.39-setup (1).tmp | — | processhacker-2.39-setup (1).exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 3088 | "C:\Users\admin\Desktop\processhacker-2.39-setup (1).exe" /SPAWNWND=$90148 /NOTIFYWND=$801E6 | C:\Users\admin\Desktop\processhacker-2.39-setup (1).exe | processhacker-2.39-setup (1).tmp | ||||||||||||
User: admin Company: wj32 Integrity Level: HIGH Description: Process Hacker Setup Exit code: 0 Version: 2.39 (r124) Modules
| |||||||||||||||
| 3188 | "C:\Users\admin\Desktop\processhacker-2.39-setup (1).exe" | C:\Users\admin\Desktop\processhacker-2.39-setup (1).exe | explorer.exe | ||||||||||||
User: admin Company: wj32 Integrity Level: MEDIUM Description: Process Hacker Setup Exit code: 0 Version: 2.39 (r124) Modules
| |||||||||||||||
| 3868 | "C:\Program Files\Process Hacker 2\ProcessHacker.exe" | C:\Program Files\Process Hacker 2\ProcessHacker.exe | processhacker-2.39-setup (1).tmp | ||||||||||||
User: admin Company: wj32 Integrity Level: MEDIUM Description: Process Hacker Exit code: 3221225477 Version: 2.39.0.124 Modules
| |||||||||||||||
| 3880 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Process Hacker 2.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 3221225477 Version: 5.60.0 Modules
| |||||||||||||||
| 3892 | "C:\Users\admin\AppData\Local\Temp\is-792HP.tmp\processhacker-2.39-setup (1).tmp" /SL5="$80158,1874675,150016,C:\Users\admin\Desktop\processhacker-2.39-setup (1).exe" /SPAWNWND=$90148 /NOTIFYWND=$801E6 | C:\Users\admin\AppData\Local\Temp\is-792HP.tmp\processhacker-2.39-setup (1).tmp | processhacker-2.39-setup (1).exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
Total events
2 729
Read events
2 451
Write events
253
Delete events
25
Modification events
| (PID) Process: | (3880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3880) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Process Hacker 2.rar | |||
| (PID) Process: | (3880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (3892) processhacker-2.39-setup (1).tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 340F000080C576259416D601 | |||
Executable files
21
Suspicious files
1
Text files
6
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3892 | processhacker-2.39-setup (1).tmp | C:\Program Files\Process Hacker 2\is-GTPTH.tmp | — | |
MD5:— | SHA256:— | |||
| 3892 | processhacker-2.39-setup (1).tmp | C:\Program Files\Process Hacker 2\is-G8CUI.tmp | — | |
MD5:— | SHA256:— | |||
| 3892 | processhacker-2.39-setup (1).tmp | C:\Program Files\Process Hacker 2\is-2LTO1.tmp | — | |
MD5:— | SHA256:— | |||
| 3892 | processhacker-2.39-setup (1).tmp | C:\Program Files\Process Hacker 2\is-LGHSK.tmp | — | |
MD5:— | SHA256:— | |||
| 3892 | processhacker-2.39-setup (1).tmp | C:\Program Files\Process Hacker 2\is-ULVDP.tmp | — | |
MD5:— | SHA256:— | |||
| 3892 | processhacker-2.39-setup (1).tmp | C:\Program Files\Process Hacker 2\is-AKN6P.tmp | — | |
MD5:— | SHA256:— | |||
| 3892 | processhacker-2.39-setup (1).tmp | C:\Program Files\Process Hacker 2\is-8BQK2.tmp | — | |
MD5:— | SHA256:— | |||
| 3892 | processhacker-2.39-setup (1).tmp | C:\Program Files\Process Hacker 2\is-7AI7P.tmp | — | |
MD5:— | SHA256:— | |||
| 3892 | processhacker-2.39-setup (1).tmp | C:\Program Files\Process Hacker 2\is-1LH0H.tmp | — | |
MD5:— | SHA256:— | |||
| 3892 | processhacker-2.39-setup (1).tmp | C:\Program Files\Process Hacker 2\plugins\is-60UBI.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
2
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3868 | ProcessHacker.exe | GET | 404 | 216.105.38.10:80 | http://processhacker.sourceforge.net/update.php | US | xml | 345 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3868 | ProcessHacker.exe | 162.243.25.33:443 | wj32.org | Digital Ocean, Inc. | US | suspicious |
3868 | ProcessHacker.exe | 216.105.38.10:80 | processhacker.sourceforge.net | American Internet Services, LLC. | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
wj32.org |
| whitelisted |
processhacker.sourceforge.net |
| suspicious |