| download: | sysdiag-full-5.0.60.1-20210424.exe |
| Full analysis: | https://app.any.run/tasks/de0f0963-7690-43fa-a198-eee4281f5924 |
| Verdict: | Malicious activity |
| Analysis date: | April 25, 2021, 00:16:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | E0F9EEF3AD8CEF7AE45B4A67E5198888 |
| SHA1: | 4AE9E1500EE848BC7B5A806E357729135D95BE3F |
| SHA256: | B60FC8EDD3ABFAD5F8E6B95066B863EE183F8CE0FA10AC68A3884A3C58AAD672 |
| SSDEEP: | 393216:cbg7iUaFptkYoFCH60x7TFWqnluiZ4OHgdjXWEFX8BRD+:cZUaFDJSI60x7UqwiLEp4C |
MALICIOUS
Loads dropped or rewritten executable
- sysdiag-full-5.0.60.1-20210424.exe (PID: 2208)
- HipsDaemon.exe (PID: 2676)
- regsvr32.exe (PID: 3968)
- explorer.exe (PID: 3492)
- explorer.exe (PID: 3824)
- HipsMain.exe (PID: 600)
- HipsTray.exe (PID: 628)
- HRUpdate.exe (PID: 2592)
Application was dropped or rewritten from another process
- ns6529.tmp (PID: 3292)
- ns674D.tmp (PID: 608)
- ns6913.tmp (PID: 1688)
- ns8111.tmp (PID: 2124)
- HipsDaemon.exe (PID: 2676)
- HRUpdate.exe (PID: 2592)
- usysdiag.exe (PID: 1456)
- wsctrl.exe (PID: 868)
- HipsTray.exe (PID: 628)
- ns7EED.tmp (PID: 2992)
- HipsMain.exe (PID: 600)
- HipsTray.exe (PID: 2624)
Registers / Runs the DLL via REGSVR32.EXE
- ns7EED.tmp (PID: 2992)
Changes the autorun value in the registry
- sysdiag-full-5.0.60.1-20210424.exe (PID: 2208)
Starts NET.EXE for service management
- ns8111.tmp (PID: 2124)
Loads the Task Scheduler COM API
- HipsDaemon.exe (PID: 2676)
SUSPICIOUS
Creates a directory in Program Files
- sysdiag-full-5.0.60.1-20210424.exe (PID: 2208)
Drops a file that was compiled in debug mode
- sysdiag-full-5.0.60.1-20210424.exe (PID: 2208)
Executable content was dropped or overwritten
- sysdiag-full-5.0.60.1-20210424.exe (PID: 2208)
Drops a file with a compile date too recent
- sysdiag-full-5.0.60.1-20210424.exe (PID: 2208)
Creates files in the driver directory
- sysdiag-full-5.0.60.1-20210424.exe (PID: 2208)
Executed via COM
- DllHost.exe (PID: 440)
- explorer.exe (PID: 3824)
- DllHost.exe (PID: 1948)
Creates or modifies windows services
- sysdiag-full-5.0.60.1-20210424.exe (PID: 2208)
- HipsDaemon.exe (PID: 2676)
Starts application with an unusual extension
- sysdiag-full-5.0.60.1-20210424.exe (PID: 2208)
Searches for installed software
- sysdiag-full-5.0.60.1-20210424.exe (PID: 2208)
Creates files in the program directory
- sysdiag-full-5.0.60.1-20210424.exe (PID: 2208)
- HipsDaemon.exe (PID: 2676)
- HipsMain.exe (PID: 600)
- HipsTray.exe (PID: 628)
Creates files in the Windows directory
- sysdiag-full-5.0.60.1-20210424.exe (PID: 2208)
- HipsDaemon.exe (PID: 2676)
Starts SC.EXE for service management
- ns674D.tmp (PID: 608)
- ns6529.tmp (PID: 3292)
- ns6913.tmp (PID: 1688)
Creates a software uninstall entry
- sysdiag-full-5.0.60.1-20210424.exe (PID: 2208)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 3968)
Executed as Windows Service
- HipsDaemon.exe (PID: 2676)
INFO
Dropped object may contain Bitcoin addresses
- sysdiag-full-5.0.60.1-20210424.exe (PID: 2208)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:12:15 23:24:36+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26112 |
| InitializedDataSize: | 141824 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x34a5 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.0.60.1 |
| ProductVersionNumber: | 5.0.60.1 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
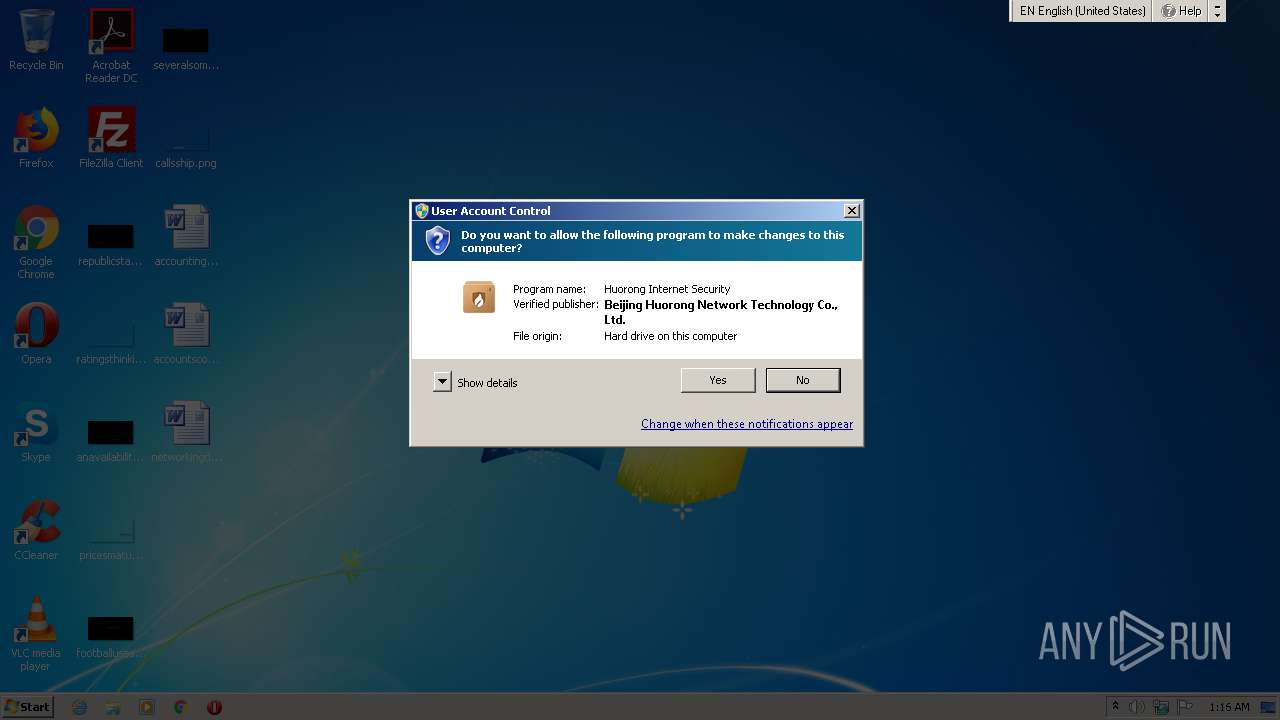
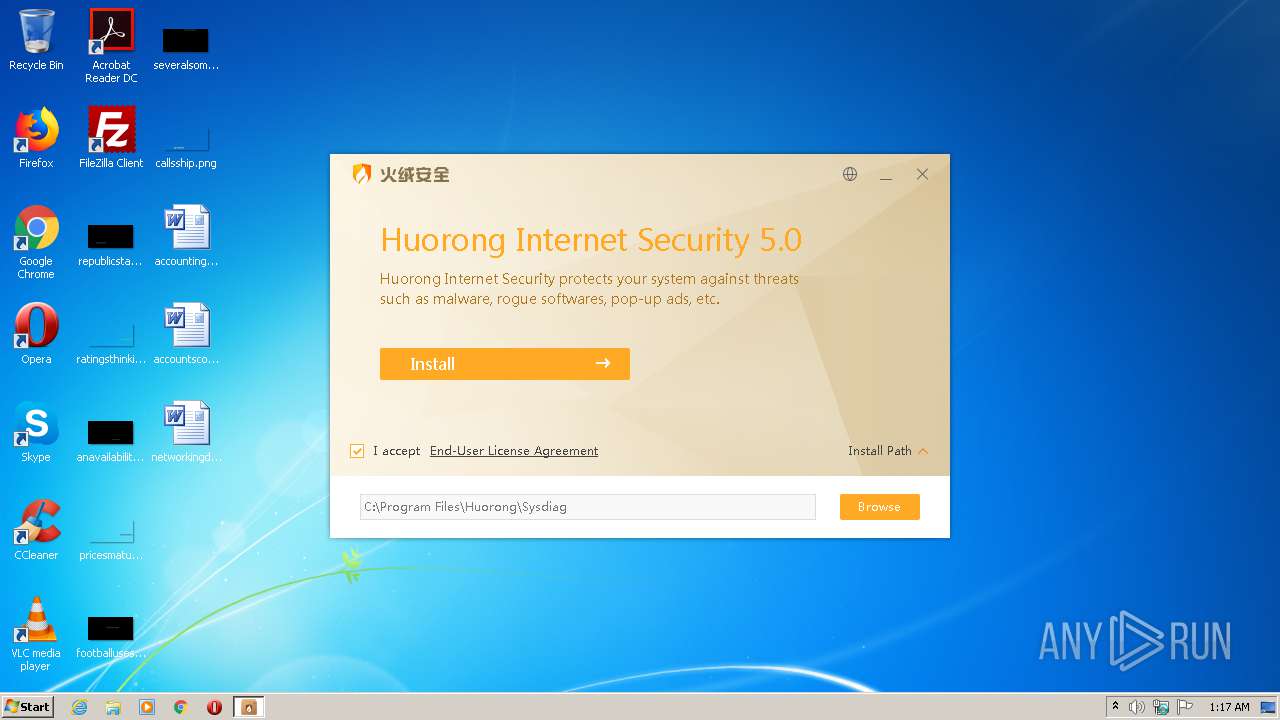
| CompanyName: | Beijing Huorong Network Technology Co., Ltd. |
| FileDescription: | Huorong Internet Security |
| FileVersion: | 5.0.60.1 |
| LegalCopyright: | Beijing Huorong Network Technology Co., Ltd. |
| ProductName: | Huorong Internet Security |
| ProductVersion: | 5.0.0.0 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 15-Dec-2018 22:24:36 |
| Detected languages: |
|
| CompanyName: | 北京火绒网络科技有限公司 |
| FileDescription: | 火绒安全软件 |
| FileVersion: | 5.0.60.1 |
| LegalCopyright: | 北京火绒网络科技有限公司 |
| ProductName: | 火绒安全软件 |
| ProductVersion: | 5.0.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 15-Dec-2018 22:24:36 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00006409 | 0x00006600 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.41619 |
.rdata | 0x00008000 | 0x00001396 | 0x00001400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.15491 |
.data | 0x0000A000 | 0x00020358 | 0x00000600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.0044 |
.ndata | 0x0002B000 | 0x00016000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x00041000 | 0x0000D2E8 | 0x0000C600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.98654 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.28733 | 841 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 6.19529 | 9640 | UNKNOWN | English - United States | RT_ICON |
3 | 6.28245 | 4264 | UNKNOWN | English - United States | RT_ICON |
4 | 6.53576 | 3752 | UNKNOWN | English - United States | RT_ICON |
5 | 6.37836 | 2440 | UNKNOWN | English - United States | RT_ICON |
6 | 6.66868 | 2216 | UNKNOWN | English - United States | RT_ICON |
7 | 6.4353 | 1736 | UNKNOWN | English - United States | RT_ICON |
8 | 3.63645 | 1640 | UNKNOWN | English - United States | RT_ICON |
9 | 5.86807 | 1384 | UNKNOWN | English - United States | RT_ICON |
10 | 6.18477 | 1128 | UNKNOWN | English - United States | RT_ICON |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
72
Monitored processes
24
Malicious processes
8
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 440 | C:\Windows\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 600 | "C:\Program Files\Huorong\Sysdiag\bin\HipsMain.exe" | C:\Program Files\Huorong\Sysdiag\bin\HipsMain.exe | explorer.exe | ||||||||||||
User: admin Company: Beijing Huorong Network Technology Co., Ltd. Integrity Level: MEDIUM Description: Huorong Internet Security Main UI Exit code: 0 Version: 5.0.1.1 Modules
| |||||||||||||||
| 608 | "C:\Users\admin\AppData\Local\Temp\nsd1255.tmp\ns674D.tmp" sc config HipsDaemon binpath= "\"C:\Program Files\Huorong\Sysdiag\bin\HipsDaemon.exe\" -sHipsDaemon" type= own type= interact start= auto group= Base DisplayName= "Huorong Internet Security Daemon" | C:\Users\admin\AppData\Local\Temp\nsd1255.tmp\ns674D.tmp | — | sysdiag-full-5.0.60.1-20210424.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 628 | "C:\Program Files\Huorong\Sysdiag\bin\HipsTray.exe" | C:\Program Files\Huorong\Sysdiag\bin\HipsTray.exe | — | sysdiag-full-5.0.60.1-20210424.exe | |||||||||||
User: admin Company: Beijing Huorong Network Technology Co., Ltd. Integrity Level: HIGH Description: Huorong Internet Security Tray Exit code: 0 Version: 5.0.1.1 Modules
| |||||||||||||||
| 868 | "C:\Program Files\Huorong\Sysdiag\\bin\wsctrl.exe" | C:\Program Files\Huorong\Sysdiag\bin\wsctrl.exe | — | HipsDaemon.exe | |||||||||||
User: SYSTEM Company: Beijing Huorong Network Technology Co., Ltd. Integrity Level: SYSTEM Description: Huorong Internet Security WSC Component Exit code: 0 Version: 5.0.0.0 Modules
| |||||||||||||||
| 988 | C:\Windows\system32\net1 start HipsDaemon | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1456 | "C:\Program Files\Huorong\Sysdiag\bin\usysdiag.exe" 460 | C:\Program Files\Huorong\Sysdiag\bin\usysdiag.exe | — | HipsDaemon.exe | |||||||||||
User: SYSTEM Company: Beijing Huorong Network Technology Co., Ltd. Integrity Level: SYSTEM Description: Huorong Sysdiag Helper Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 1688 | "C:\Users\admin\AppData\Local\Temp\nsd1255.tmp\ns6913.tmp" sc description HipsDaemon "Huorong Internet Security Daemon" | C:\Users\admin\AppData\Local\Temp\nsd1255.tmp\ns6913.tmp | — | sysdiag-full-5.0.60.1-20210424.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1948 | C:\Windows\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2080 | sc config HipsDaemon binpath= "\"C:\Program Files\Huorong\Sysdiag\bin\HipsDaemon.exe\" -sHipsDaemon" type= own type= interact start= auto group= Base DisplayName= "Huorong Internet Security Daemon" | C:\Windows\system32\sc.exe | — | ns674D.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
760
Read events
627
Write events
133
Delete events
0
Modification events
| (PID) Process: | (440) DllHost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP\Clients |
| Operation: | write | Name: | {09F7EDC5-294E-4180-AF6A-FB0E6A0E9513} |
Value: \\?\Volume{e1a82db4-a9f0-11e7-b142-806e6f6e6963}\:(C%3A) | |||
| (PID) Process: | (2208) sysdiag-full-5.0.60.1-20210424.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 400000000000000024B902526839D701A0080000100B0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2208) sysdiag-full-5.0.60.1-20210424.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 400000000000000024B902526839D701A0080000100B0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2208) sysdiag-full-5.0.60.1-20210424.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 44 | |||
| (PID) Process: | (2208) sysdiag-full-5.0.60.1-20210424.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 40000000000000008C420C526839D701A0080000100B0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2208) sysdiag-full-5.0.60.1-20210424.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000E6A40E526839D701A00800007C0F0000E8030000010000000000000000000000D915C5E914A6B843A469231A0910A1FF0000000000000000 | |||
| (PID) Process: | (2208) sysdiag-full-5.0.60.1-20210424.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4000000000000000ACFECA526839D701A00800007C0F0000E8030000000000000000000000000000D915C5E914A6B843A469231A0910A1FF0000000000000000 | |||
| (PID) Process: | (2208) sysdiag-full-5.0.60.1-20210424.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Leave) |
Value: 4000000000000000A45DC2596839D701A0080000100B0000D3070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2208) sysdiag-full-5.0.60.1-20210424.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppAddInterestingComponents (Enter) |
Value: 4000000000000000A45DC2596839D701A0080000100B0000D4070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2208) sysdiag-full-5.0.60.1-20210424.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppAddInterestingComponents (Leave) |
Value: 40000000000000008297DC596839D701A0080000100B0000D4070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
48
Suspicious files
49
Text files
4
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2208 | sysdiag-full-5.0.60.1-20210424.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 2208 | sysdiag-full-5.0.60.1-20210424.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{e9c515d9-a614-43b8-a469-231a0910a1ff}_OnDiskSnapshotProp | binary | |
MD5:— | SHA256:— | |||
| 2208 | sysdiag-full-5.0.60.1-20210424.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:— | SHA256:— | |||
| 2208 | sysdiag-full-5.0.60.1-20210424.exe | C:\Users\admin\AppData\Local\Temp\nsd1255.tmp\AccessControl.dll | executable | |
MD5:F894E7068EE5F5B4489D7ACDDE7112C9 | SHA256:3948484BC6A6E8652C2220BE411CDCABAB73EAB46578FACA8C0BD01D3EA290AB | |||
| 2208 | sysdiag-full-5.0.60.1-20210424.exe | C:\Users\admin\AppData\Local\Temp\nsd1255.tmp\ns6529.tmp | executable | |
MD5:— | SHA256:— | |||
| 2208 | sysdiag-full-5.0.60.1-20210424.exe | C:\Users\admin\AppData\Local\Temp\nsd1255.tmp\ns674D.tmp | executable | |
MD5:— | SHA256:— | |||
| 2208 | sysdiag-full-5.0.60.1-20210424.exe | C:\Users\admin\AppData\Local\Temp\nsd1255.tmp\ns6913.tmp | executable | |
MD5:— | SHA256:— | |||
| 2208 | sysdiag-full-5.0.60.1-20210424.exe | C:\Users\admin\AppData\Local\Temp\nsd1255.tmp\inst.ui | compressed | |
MD5:692C13E0B2E33D68A3EE3237C252FB4B | SHA256:E3C13E8BFAA41A65EB2061EB350ED030873208ED01BA254A325DF775C1C5DAB8 | |||
| 2208 | sysdiag-full-5.0.60.1-20210424.exe | C:\Windows\system32\drivers\hrelam.sys | executable | |
MD5:C284F322D32454D98F1C50686F53F9CF | SHA256:EA8DF3D3002236FC2E34BF14A185BEAE96AD421B437B132D522520EE8B14AE6A | |||
| 2208 | sysdiag-full-5.0.60.1-20210424.exe | C:\Windows\system32\drivers\hrwfpdrv.sys | executable | |
MD5:0AC7BB3E34240706AF171C118D57C4BE | SHA256:58B3E96022A65EE22ECF40699F5A906D4C00FD420736EFDCB82E19E73652C550 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
4
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
600 | HipsMain.exe | GET | 200 | 121.199.251.28:80 | http://update.huorong.cn/upgrade7/upgrade.php?type=chk&uid2=B2C0D2E4B1C30E581D582BA1B751CBC700000000&instm=2021-04-25%2000%3A17&ver=5.0.60.1&os=11&bn=7601&lid=1033&pt=0&channel=0&client=0&confts=0&skq=00003e0b& | CN | binary | 5.95 Kb | unknown |
600 | HipsMain.exe | GET | 200 | 121.199.251.28:80 | http://update.huorong.cn/upgrade7vdb/upgrade.php?type=chk&uid2=B2C0D2E4B1C30E581D582BA1B751CBC700000000&instm=2021-04-25%2000%3A17&ver=5.0.60.1&os=11&bn=7601&lid=1033&pt=0&channel=0&client=0&confts=0&skq=00003e11& | CN | binary | 3.87 Kb | unknown |
600 | HipsMain.exe | GET | 200 | 114.80.187.124:80 | http://down2.huorong.cn/upgrade7/1618553595/upgrade.html | CN | text | 12 b | suspicious |
600 | HipsMain.exe | GET | 200 | 114.80.187.124:80 | http://down2.huorong.cn/upgrade7/1619257177/upgrade.html | CN | text | 12 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
600 | HipsMain.exe | 121.199.251.28:80 | update.huorong.cn | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
600 | HipsMain.exe | 114.80.187.124:80 | down2.huorong.cn | China Telecom (Group) | CN | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
update.huorong.cn |
| unknown |
down2.huorong.cn |
| suspicious |