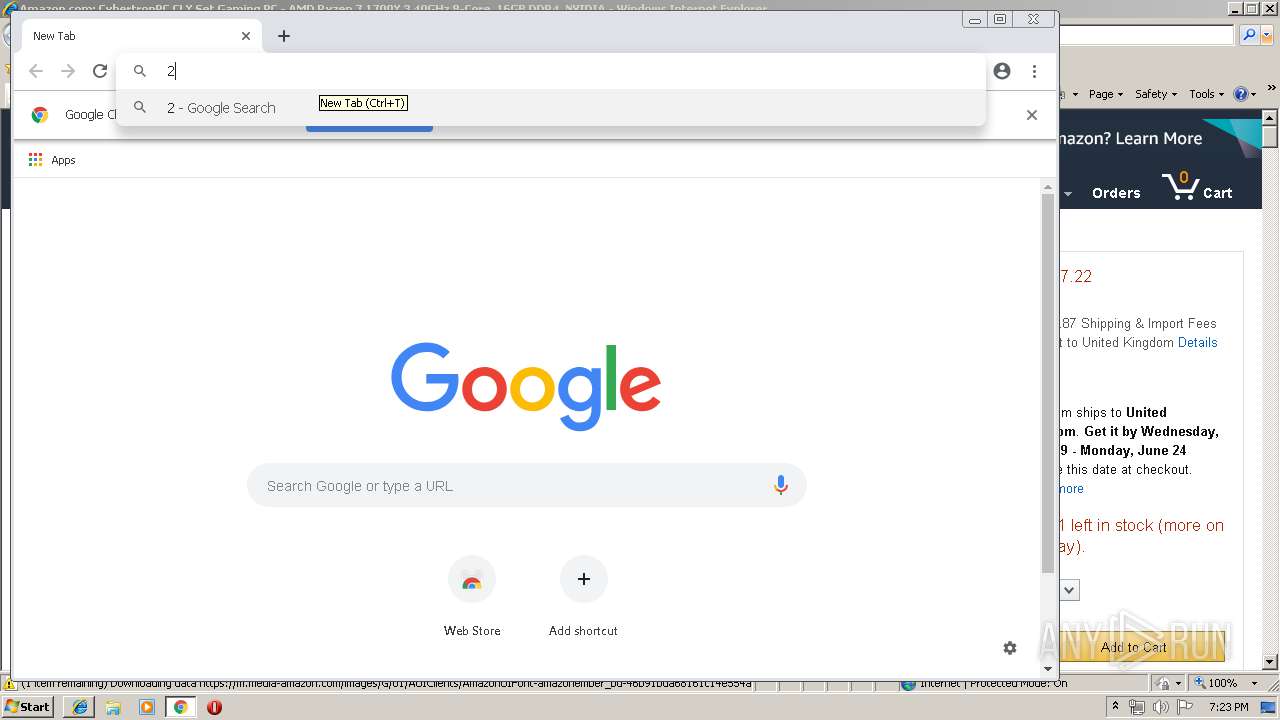
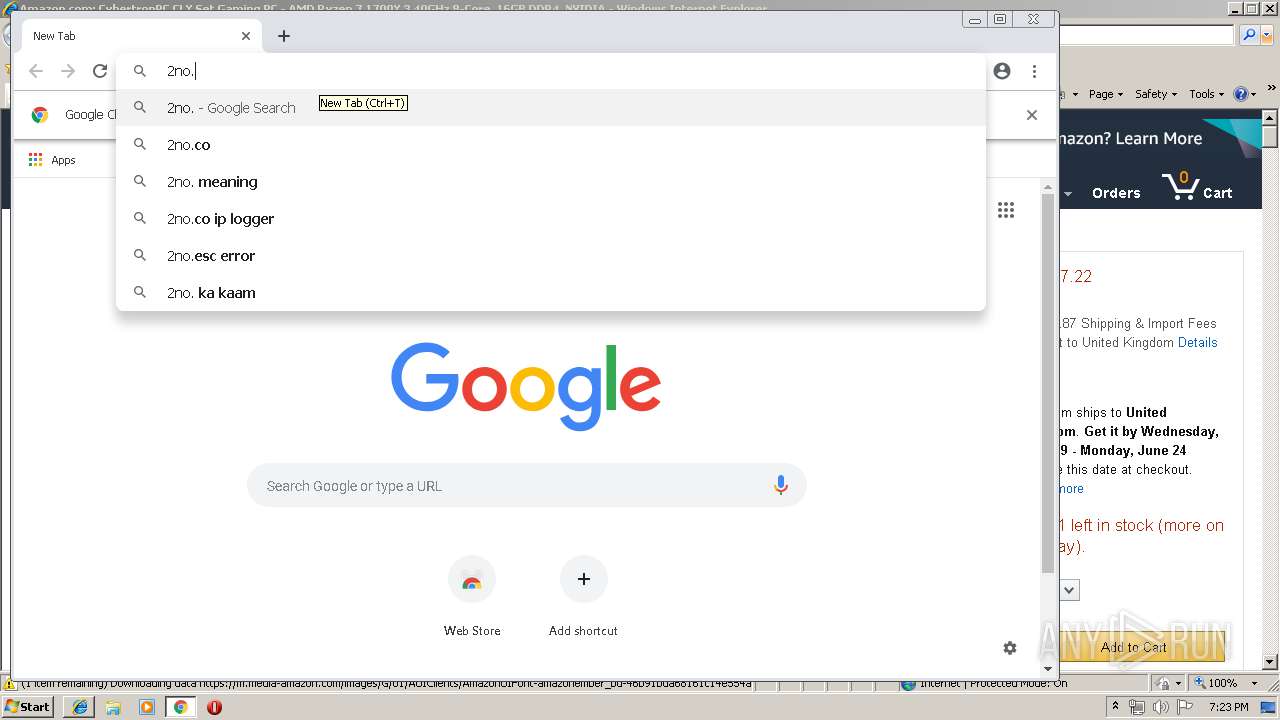
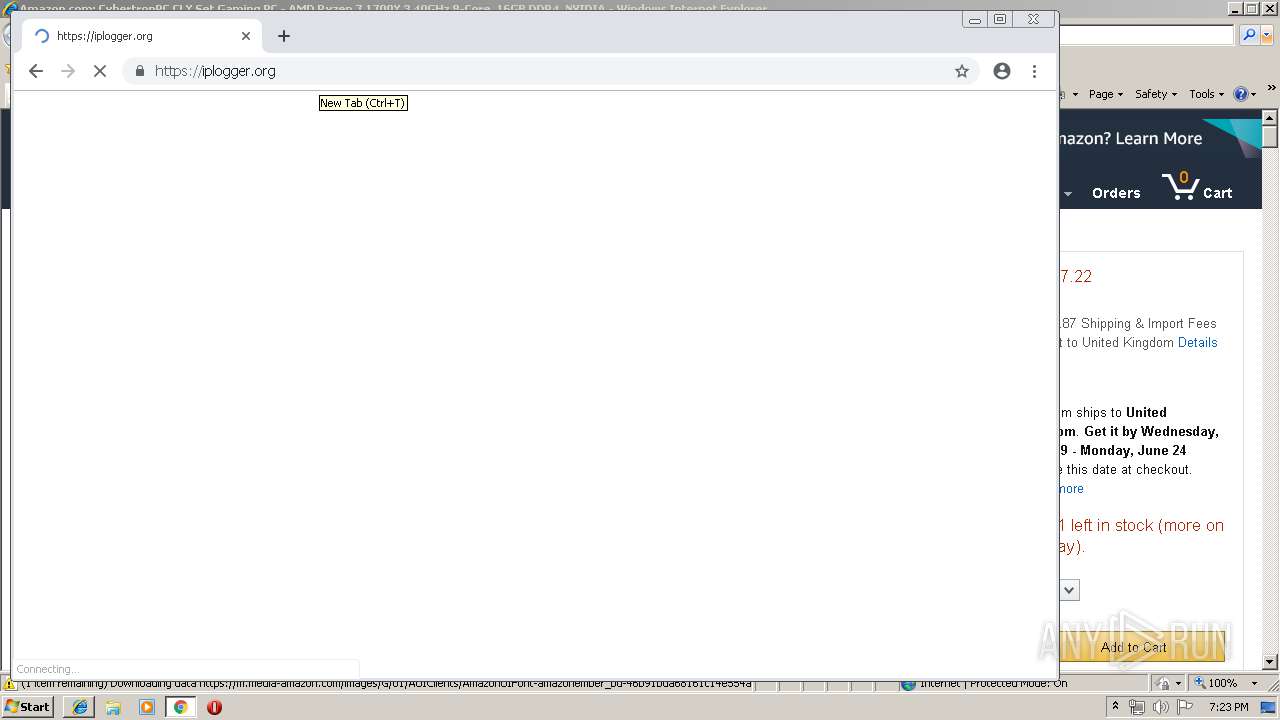
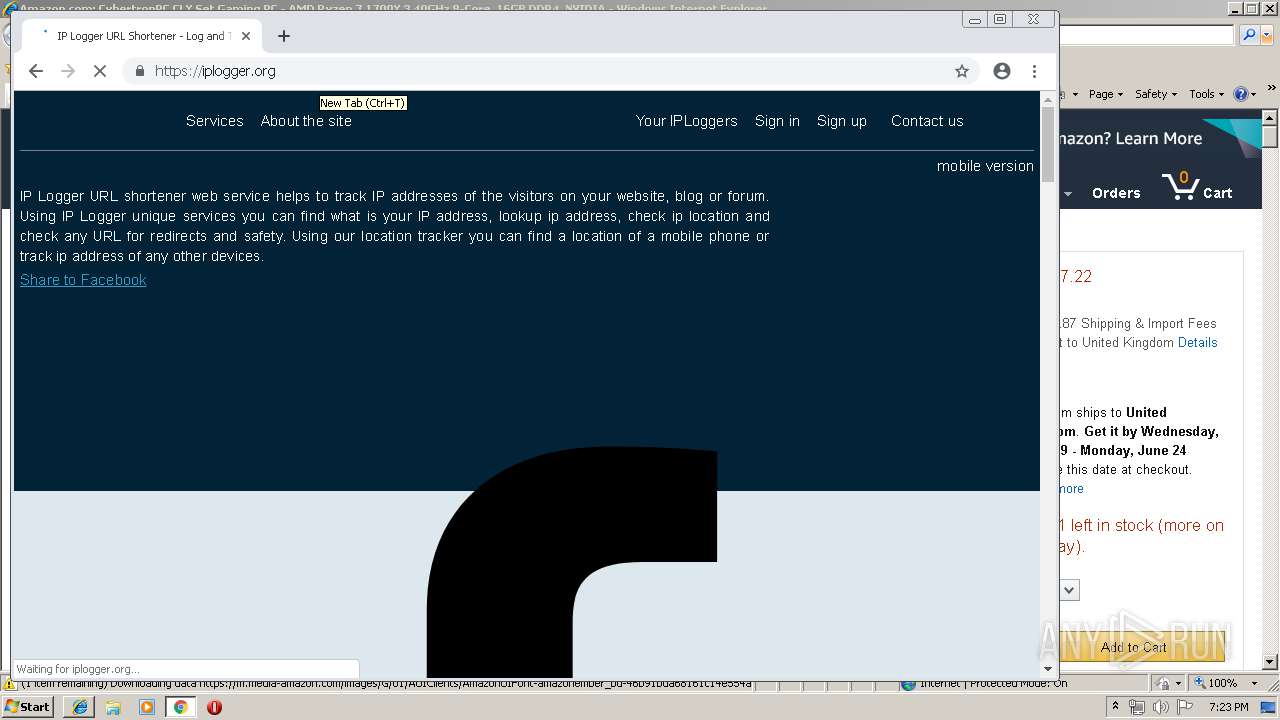
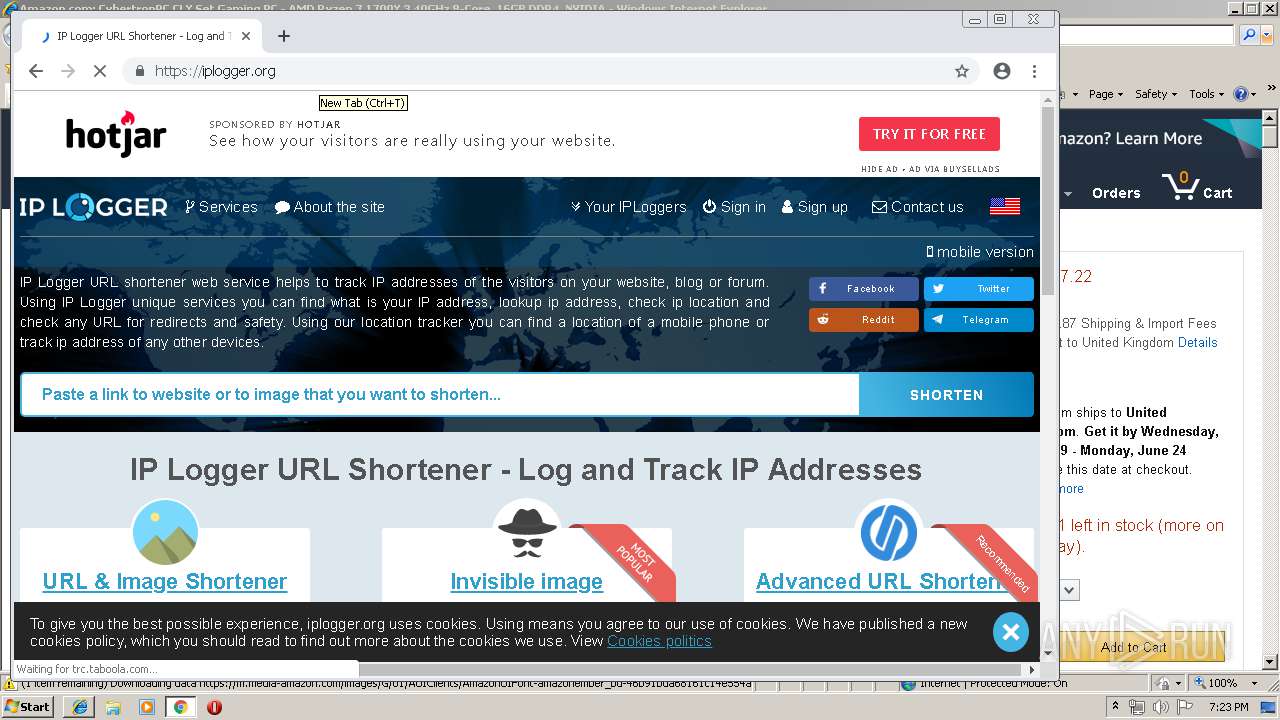
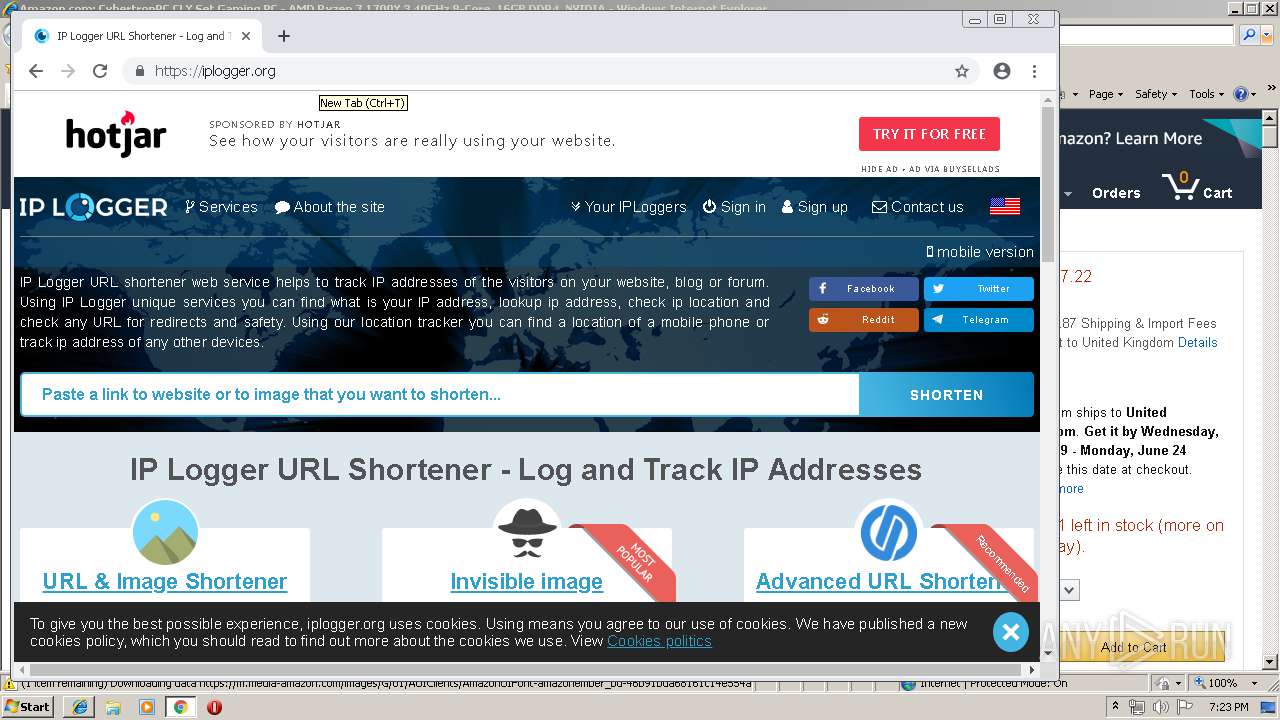
| URL: | https://2no.co/2u3ii5.jpeg |
| Full analysis: | https://app.any.run/tasks/69a03a0a-1ed6-4a8f-867b-83de4a66f54b |
| Verdict: | Malicious activity |
| Analysis date: | June 16, 2019, 18:22:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 7A3AF32F23F9168D97CA98115B9F003B |
| SHA1: | C4A219CA46D2BA1D1CB6DD13535A9DA85BAA0895 |
| SHA256: | B60F4A39637804317FBF825286ECE49045263B39FF70746B827236AB2CF1FD0A |
| SSDEEP: | 3:N8LDMMQRACn:2LQR1n |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Changes internet zones settings
- iexplore.exe (PID: 1892)
Reads settings of System Certificates
- chrome.exe (PID: 2328)
- iexplore.exe (PID: 1892)
Changes settings of System certificates
- iexplore.exe (PID: 1892)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1892)
Application launched itself
- chrome.exe (PID: 2328)
Creates files in the user directory
- iexplore.exe (PID: 1892)
- iexplore.exe (PID: 3416)
Reads Internet Cache Settings
- iexplore.exe (PID: 3416)
Reads internet explorer settings
- iexplore.exe (PID: 3416)
Manual execution by user
- chrome.exe (PID: 2328)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
58
Monitored processes
25
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 944 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=964,11724036674344745164,15824269247204196827,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=15007387185781879638 --mojo-platform-channel-handle=4652 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1664 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=964,11724036674344745164,15824269247204196827,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAACAAwAAAQAAAAAAAAAAAGAAAAAAAAEAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=17028365057545619062 --mojo-platform-channel-handle=5060 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1712 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=964,11724036674344745164,15824269247204196827,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=6708346556592512924 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=6708346556592512924 --renderer-client-id=10 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4208 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1892 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1920 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=964,11724036674344745164,15824269247204196827,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=16724572749820457696 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=16724572749820457696 --renderer-client-id=16 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4076 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2236 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=964,11724036674344745164,15824269247204196827,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=15266724770797804043 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=15266724770797804043 --renderer-client-id=7 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3716 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2312 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=964,11724036674344745164,15824269247204196827,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=6681605681666123586 --mojo-platform-channel-handle=4516 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2328 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2460 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=964,11724036674344745164,15824269247204196827,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=843407992351739264 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=843407992351739264 --renderer-client-id=9 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2040 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2464 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=964,11724036674344745164,15824269247204196827,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=8713117269321547453 --mojo-platform-channel-handle=3872 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
Total events
669
Read events
537
Write events
126
Delete events
6
Modification events
| (PID) Process: | (1892) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1892) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1892) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (1892) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (1892) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1892) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000071000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1892) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {BBA66BA1-9063-11E9-A370-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (1892) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (1892) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 1 | |||
| (PID) Process: | (1892) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E307060000001000120016002D00D800 | |||
Executable files
0
Suspicious files
77
Text files
318
Unknown types
24
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1892 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 1892 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3416 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@amazon[1].txt | — | |
MD5:— | SHA256:— | |||
| 3416 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3416 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3416 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\VUN1MXE5\ref=mp_s_a_1_8[1].htm | html | |
MD5:— | SHA256:— | |||
| 3416 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3416 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\DOMStore\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3416 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@amazon[2].txt | text | |
MD5:— | SHA256:— | |||
| 3416 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\MSIMGSIZ.DAT | smt | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
74
DNS requests
61
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3416 | iexplore.exe | GET | 200 | 13.107.4.50:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 56.2 Kb | whitelisted |
2328 | chrome.exe | GET | 200 | 173.194.183.201:80 | http://r4---sn-aigl6nl7.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=217.147.89.18&mm=28&mn=sn-aigl6nl7&ms=nvh&mt=1560709349&mv=m&pl=22&shardbypass=yes | US | crx | 842 Kb | whitelisted |
2328 | chrome.exe | GET | 302 | 216.58.205.238:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 504 b | whitelisted |
1892 | iexplore.exe | GET | 200 | 52.85.22.175:80 | http://d2lo25i6d3q8zm.cloudfront.net/browser-plugins/AmazonSearchSuggestionsOSD.DPIE.xml | US | xml | 1.18 Kb | shared |
2328 | chrome.exe | GET | 301 | 88.99.66.31:80 | http://2no.co/ | DE | html | 178 b | whitelisted |
3416 | iexplore.exe | GET | 200 | 52.85.22.120:80 | http://x.ss2.us/x.cer | US | der | 1.27 Kb | whitelisted |
2328 | chrome.exe | GET | 200 | 204.13.202.71:80 | http://ssl.trustwave.com/issuers/STCA.crt | US | der | 956 b | whitelisted |
1892 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3416 | iexplore.exe | 104.108.41.30:443 | www.amazon.com | Akamai Technologies, Inc. | NL | whitelisted |
1892 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3416 | iexplore.exe | 88.99.66.31:443 | 2no.co | Hetzner Online GmbH | DE | malicious |
3416 | iexplore.exe | 54.192.218.146:443 | images-na.ssl-images-amazon.com | Amazon.com, Inc. | US | unknown |
2328 | chrome.exe | 172.217.18.99:443 | www.google.com.ua | Google Inc. | US | whitelisted |
2328 | chrome.exe | 172.217.16.141:443 | accounts.google.com | Google Inc. | US | suspicious |
2328 | chrome.exe | 172.217.23.174:443 | clients1.google.com | Google Inc. | US | whitelisted |
2328 | chrome.exe | 216.58.207.67:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
3416 | iexplore.exe | 52.85.22.120:80 | x.ss2.us | Amazon.com, Inc. | US | unknown |
2328 | chrome.exe | 216.58.206.3:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
2no.co |
| whitelisted |
www.amazon.com |
| whitelisted |
images-na.ssl-images-amazon.com |
| shared |
m.media-amazon.com |
| whitelisted |
fls-na.amazon.com |
| shared |
x.ss2.us |
| whitelisted |
www.download.windowsupdate.com |
| whitelisted |
d2lo25i6d3q8zm.cloudfront.net |
| shared |
clientservices.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3416 | iexplore.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
3416 | iexplore.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
2328 | chrome.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
2328 | chrome.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
1 ETPRO signatures available at the full report