| File name: | Amus.exe |
| Full analysis: | https://app.any.run/tasks/6c0505dc-1a61-4265-89de-7e130f586acd |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 16:05:42 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | 47ABD68080EEE0EA1B95AE31968A3069 |
| SHA1: | FFBDF4B2224B92BD78779A7C5AC366CCB007C14D |
| SHA256: | B5FC4FD50E4BA69F0C8C8E5C402813C107C605CAB659960AC31B3C8356C4E0EC |
| SSDEEP: | 768:/9NC1eO7wvsgyjgLCtKbqvYGjaESiKMH6BJJE+XqYq7wvefY:/9NC1eOMFyjt2/wDrcq/Mveg |
MALICIOUS
NETWORM mutex has been found
- Amus.exe (PID: 4920)
Changes the autorun value in the registry
- Amus.exe (PID: 4920)
SUSPICIOUS
Reads security settings of Internet Explorer
- Amus.exe (PID: 4920)
Creates file in the systems drive root
- Amus.exe (PID: 4920)
INFO
Checks supported languages
- Amus.exe (PID: 4920)
Reads the computer name
- Amus.exe (PID: 4920)
Reads the machine GUID from the registry
- Amus.exe (PID: 4920)
Creates files or folders in the user directory
- Amus.exe (PID: 4920)
The sample compiled with english language support
- Amus.exe (PID: 4920)
Failed to create an executable file in Windows directory
- Amus.exe (PID: 4920)
Create files in a temporary directory
- Amus.exe (PID: 4920)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Microsoft Visual Basic 6 (90.6) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (4.9) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2004:08:06 08:47:16+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 28672 |
| InitializedDataSize: | 16384 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1534 |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Masum |
| LegalTrademarks: | @2004 Eregli |
| ProductName: | Masum |
| FileVersion: | 1 |
| ProductVersion: | 1 |
| InternalName: | Masum |
| OriginalFileName: | Masum.exe |
Total processes
132
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3888 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4920 | "C:\Users\admin\AppData\Local\Temp\Amus.exe" | C:\Users\admin\AppData\Local\Temp\Amus.exe | explorer.exe | ||||||||||||
User: admin Company: Masum Integrity Level: MEDIUM Version: 1.00 Modules
| |||||||||||||||
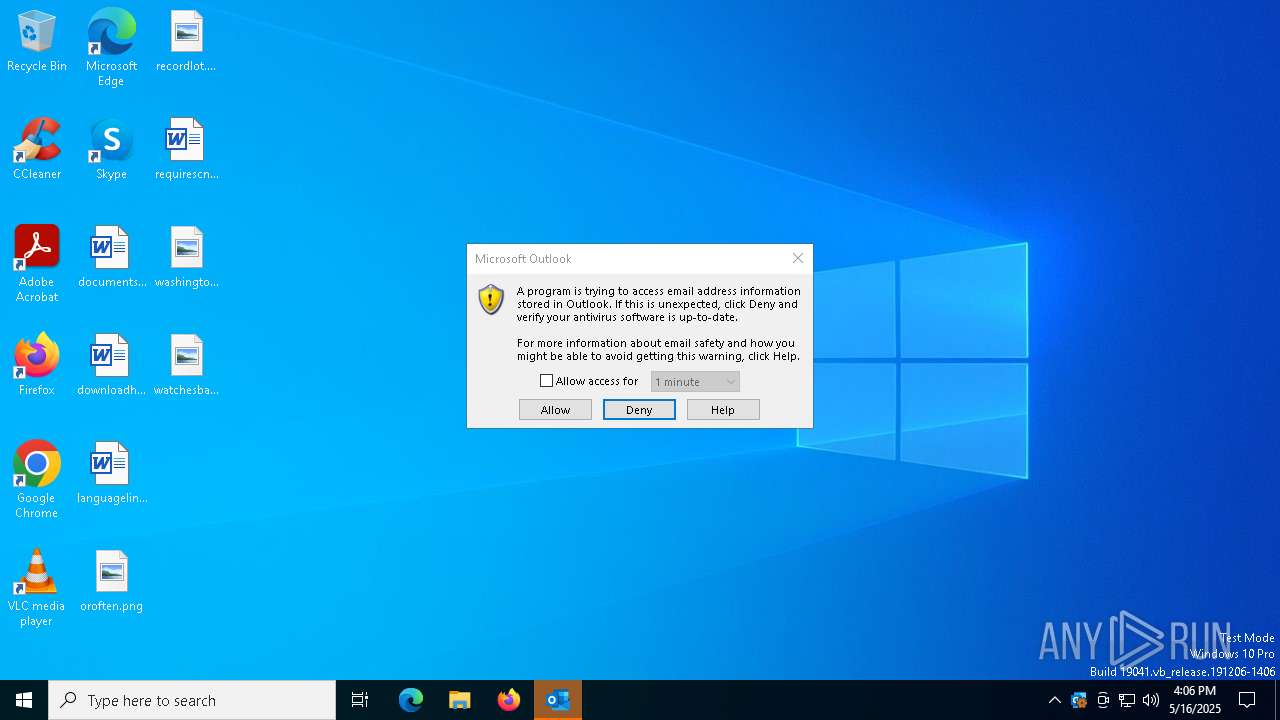
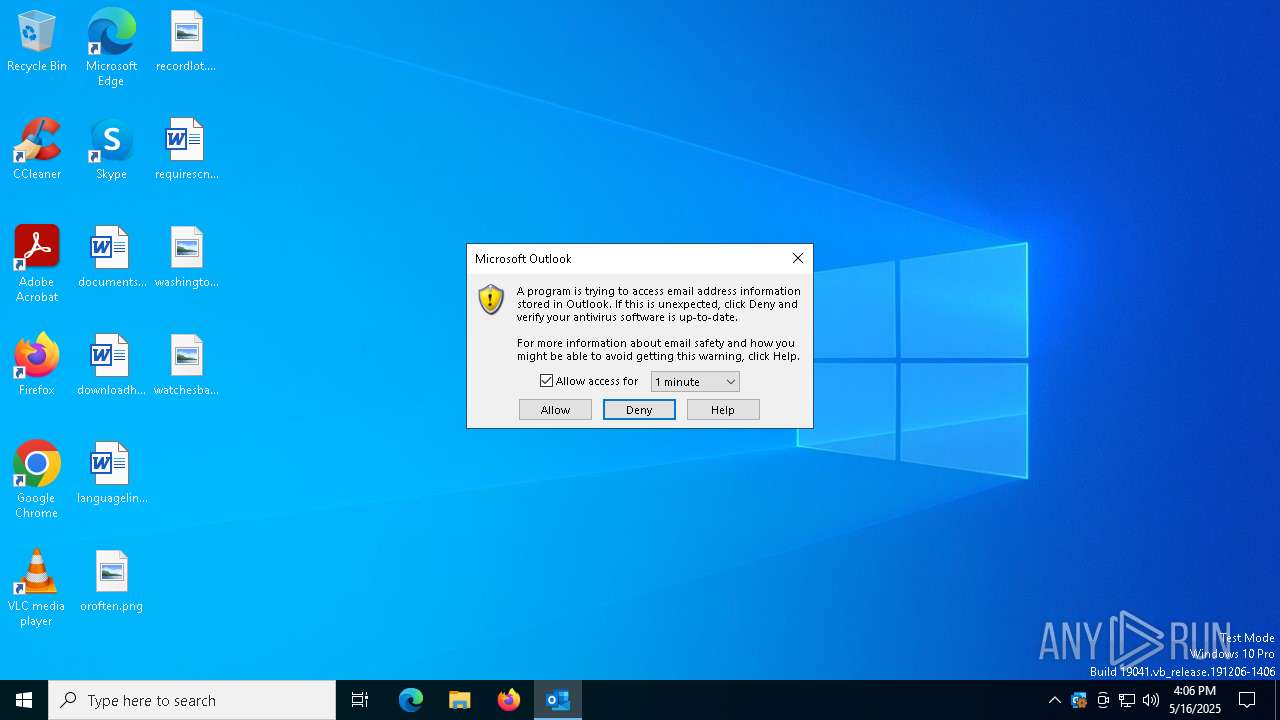
| 5436 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" -Embedding | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 6988 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 389
Read events
8 090
Write events
272
Delete events
27
Modification events
| (PID) Process: | (4920) Amus.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Speech\AudioOutput\TokenEnums\MMAudioOut\{0.0.0.00000000}.{9a7a2494-d921-4b91-8899-38d44cd79857} |
| Operation: | write | Name: | CLSID |
Value: {A8C680EB-3D32-11D2-9EE7-00C04F797396} | |||
| (PID) Process: | (4920) Amus.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Speech\AudioOutput\TokenEnums\MMAudioOut\{0.0.0.00000000}.{9a7a2494-d921-4b91-8899-38d44cd79857} |
| Operation: | write | Name: | DeviceName |
Value: Speakers (2- Realtek AC'97 Audio) | |||
| (PID) Process: | (4920) Amus.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Speech\AudioOutput\TokenEnums\MMAudioOut\{0.0.0.00000000}.{9a7a2494-d921-4b91-8899-38d44cd79857} |
| Operation: | write | Name: | DeviceId |
Value: {0.0.0.00000000}.{9a7a2494-d921-4b91-8899-38d44cd79857} | |||
| (PID) Process: | (4920) Amus.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Speech\AudioOutput\TokenEnums\MMAudioOut\{0.0.0.00000000}.{9a7a2494-d921-4b91-8899-38d44cd79857}\Attributes |
| Operation: | write | Name: | Vendor |
Value: Microsoft | |||
| (PID) Process: | (4920) Amus.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Speech\AudioOutput\TokenEnums\MMAudioOut\{0.0.0.00000000}.{9a7a2494-d921-4b91-8899-38d44cd79857}\Attributes |
| Operation: | write | Name: | Technology |
Value: MMSys | |||
| (PID) Process: | (4920) Amus.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Speech\AudioOutput |
| Operation: | write | Name: | DefaultTokenId |
Value: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Speech\AudioOutput\TokenEnums\MMAudioOut\ | |||
| (PID) Process: | (4920) Amus.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Masum |
| Operation: | write | Name: | Who |
Value: OnEmLi_DeGiL | |||
| (PID) Process: | (4920) Amus.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Microzoft_Ofiz |
Value: C:\Windows\KdzEregli.exe | |||
| (PID) Process: | (4920) Amus.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Speech_OneCore\Isolated\YJRP-ZYlwId9yXOMu3hKgnjScm7zbtzqWEDUfG9O1D0\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Speech_OneCore\AudioInput |
| Operation: | write | Name: | DefaultDefaultTokenId |
Value: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Speech_OneCore\AudioInput\TokenEnums\MMAudioIn\ | |||
| (PID) Process: | (4920) Amus.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Speech_OneCore\Isolated\YJRP-ZYlwId9yXOMu3hKgnjScm7zbtzqWEDUfG9O1D0\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Speech_OneCore\AudioInput\TokenEnums\MMAudioIn |
| Operation: | write | Name: | CLSID |
Value: {14E74C62-DC97-43B0-8F2F-581496A65D60} | |||
Executable files
0
Suspicious files
7
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5436 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 4920 | Amus.exe | C:\Users\admin\AppData\Roaming\Microsoft\Speech\Files\UserLexicons\SP_3168B5EDEB5F42BD9DD1DC03248DE8B4.dat | binary | |
MD5:10426E2D312735B39D9EE7BD70665D9B | SHA256:D894B8B8F396FDD19743012E3FD2230E96373F1E3BE7946DFC68B2B34B6D15F9 | |||
| 5436 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\OTele\outlook.exe.db-shm | binary | |
MD5:3D1DBBAB939B8C9F4162974C348DB23B | SHA256:5BC7B1DBA951D7A4B01FC8D3EA373A109A626B6A119A6708AED5AA2DA2CCFCF6 | |||
| 5436 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_TableViewPreviewPrefs_2_3C7AA58948EFAE48B939EB8CE1D40991.dat | xml | |
MD5:0E092DB99AEE99FDFF9B5B222C732CFD | SHA256:D1614AD99ADED9F6F5C1BE7FE7FFA5124BD04A526580DA3818EA8A954E852AA6 | |||
| 5436 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:A2C131F2DFF7D8428BD4791A4593B7EB | SHA256:C035642B94935AE284CC1D03F485A4C7823ECEAE5907A4B0631EC02443E275C6 | |||
| 5436 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:96F2E9BF39FF50A163E5C5B93D13E178 | SHA256:F7845ADEF957F6FD109F5A4904D2B5CD8F3589F1775EC167721CB2F049862F82 | |||
| 5436 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\~Outlook1.pst.tmp | binary | |
MD5:5AFC4E777796933682361196B536484F | SHA256:E60B2208EFE8C58A292E41CBAED975F0A51AA657819DB6C3DAA94EF912DF5844 | |||
| 5436 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20250516T1606000139-5436.etl | binary | |
MD5:C356F227CD2A0B3A47CF29C9ACC642F6 | SHA256:F2D4EAFEA587E0478961C4ADF75847F0C5B5B80E9ABD393D6DD905F101F8A145 | |||
| 5436 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\OTele\outlook.exe.db-wal | binary | |
MD5:D3F45BFAB932E71E454CE26D3686ACAD | SHA256:D8ADC5AEEBD640FF38AEEA643FA6BA56A9450370D88EE373DDB1A4C26668142C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
27
DNS requests
6
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5436 | OUTLOOK.EXE | 52.123.129.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5436 | OUTLOOK.EXE | 23.50.131.87:443 | omex.cdn.office.net | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5436 | OUTLOOK.EXE | 104.208.16.95:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |