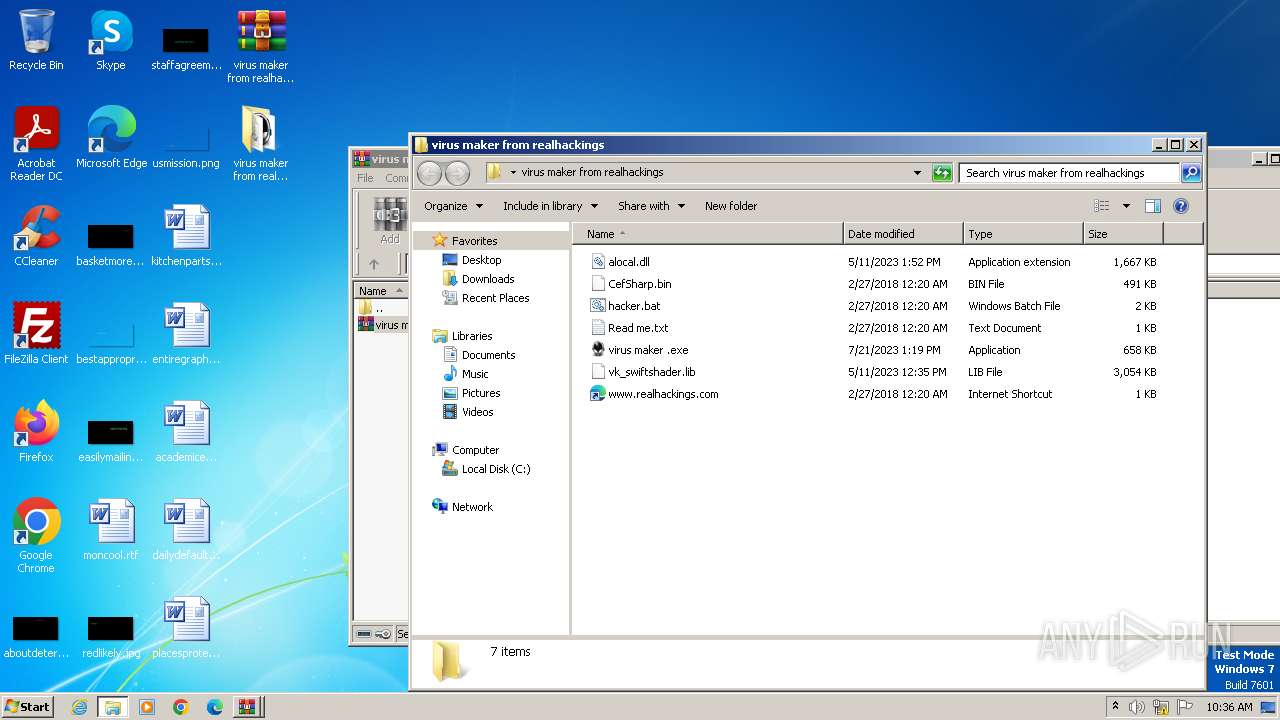
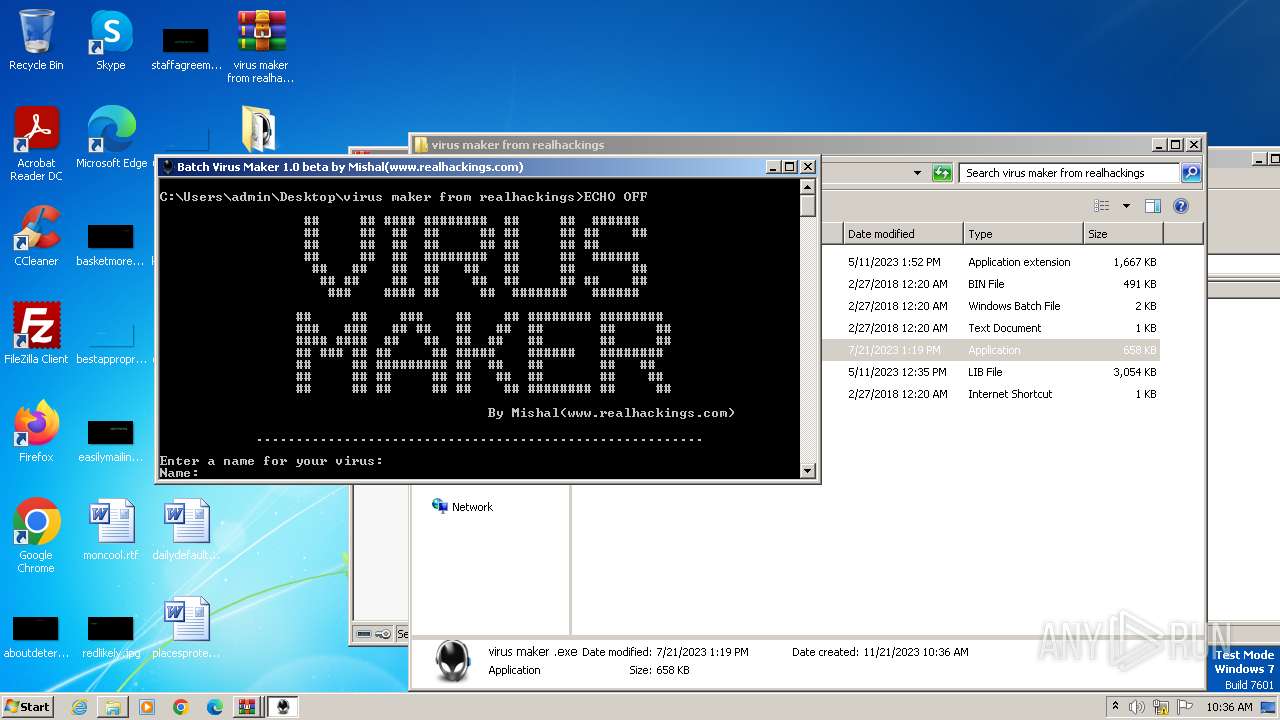
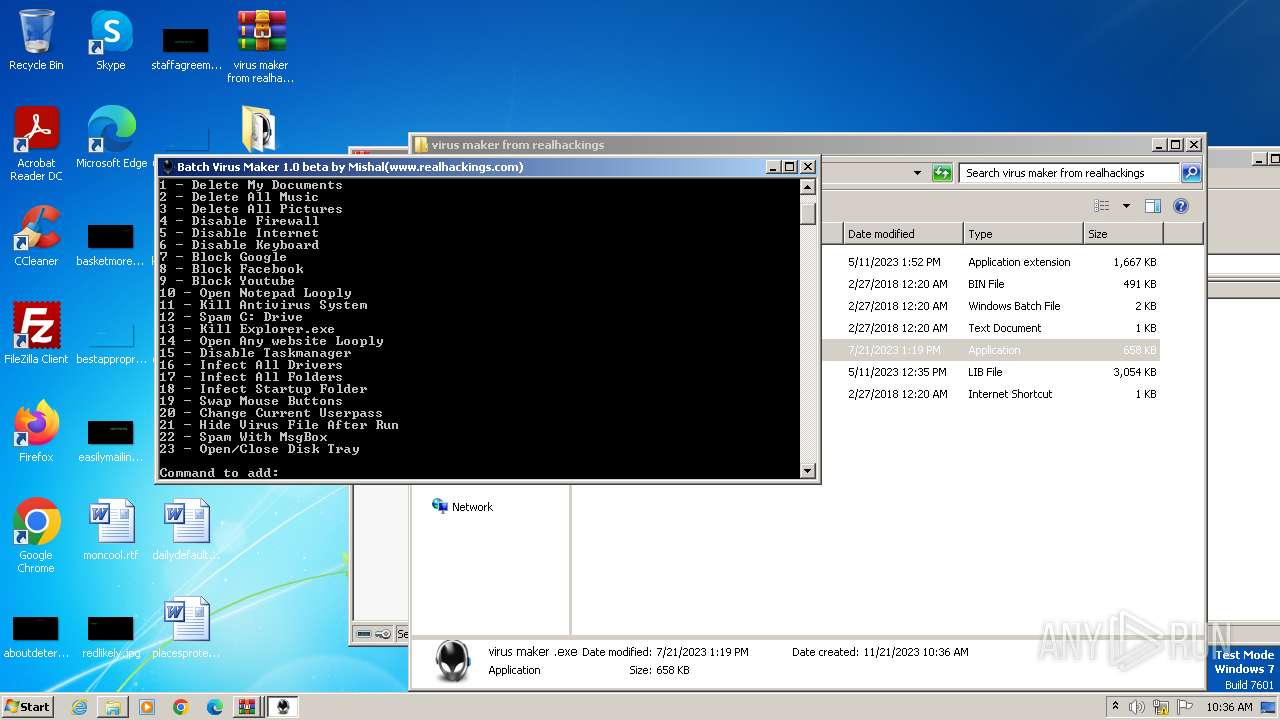
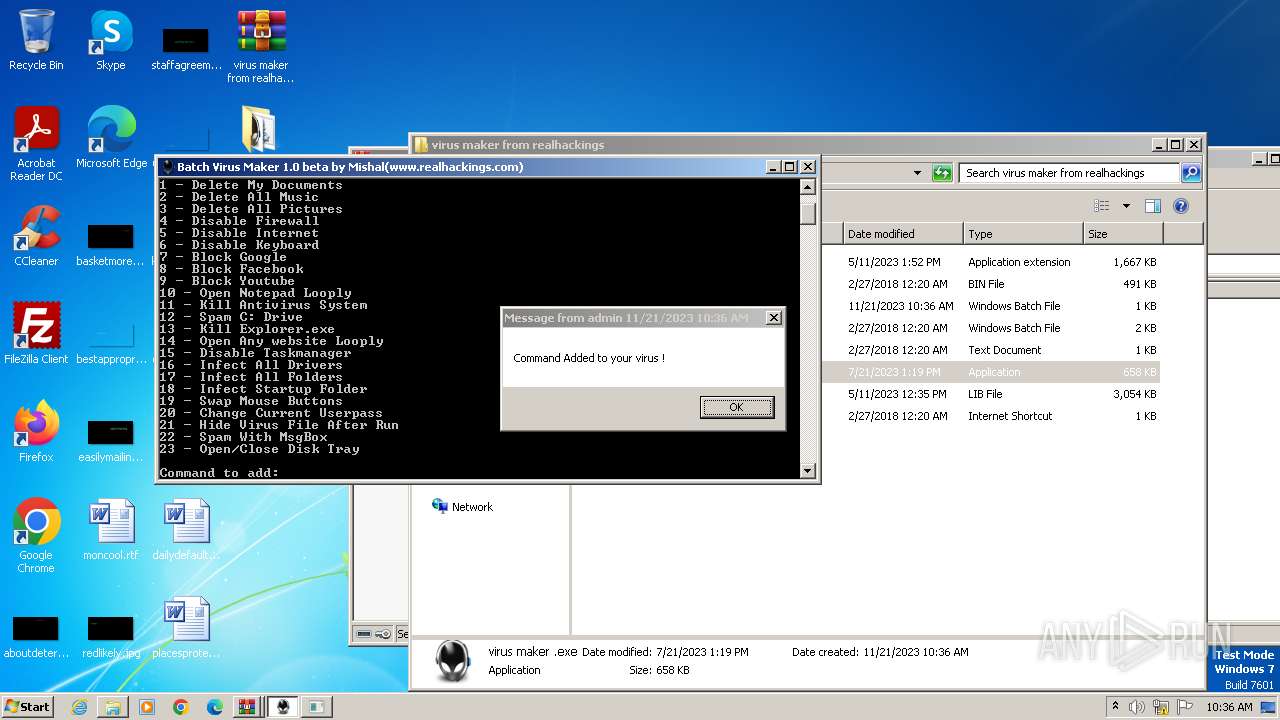
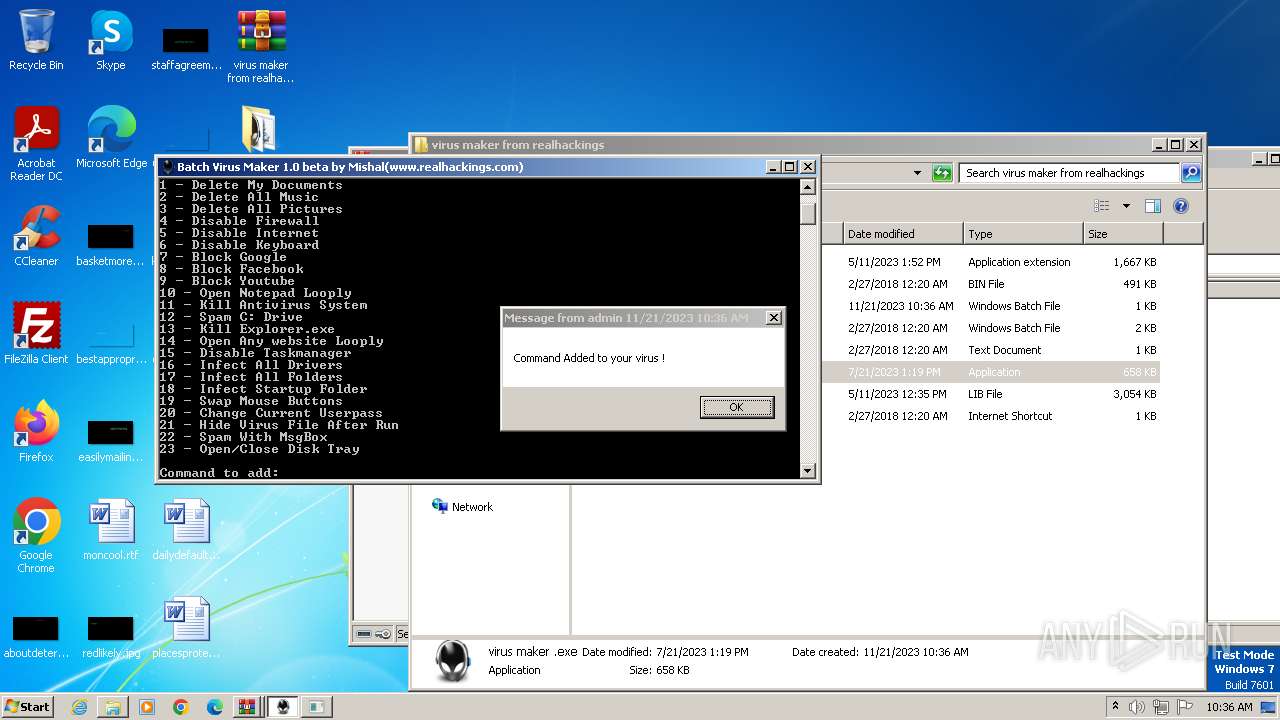
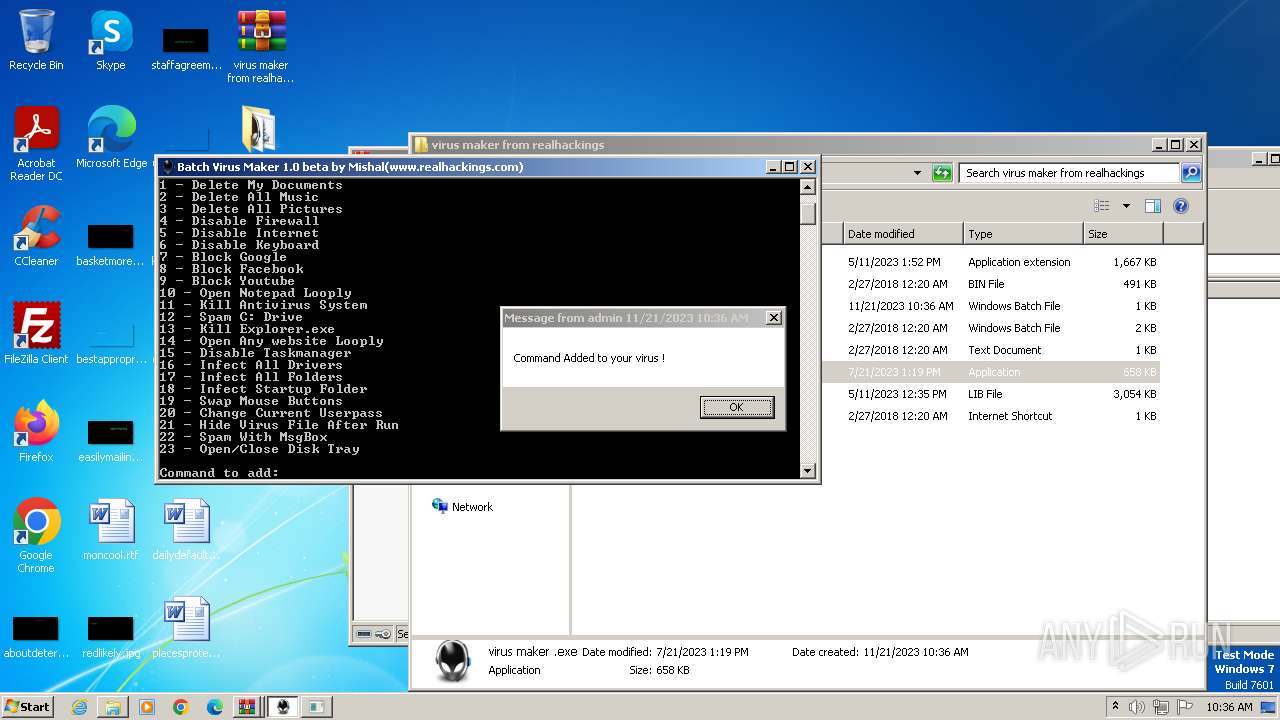
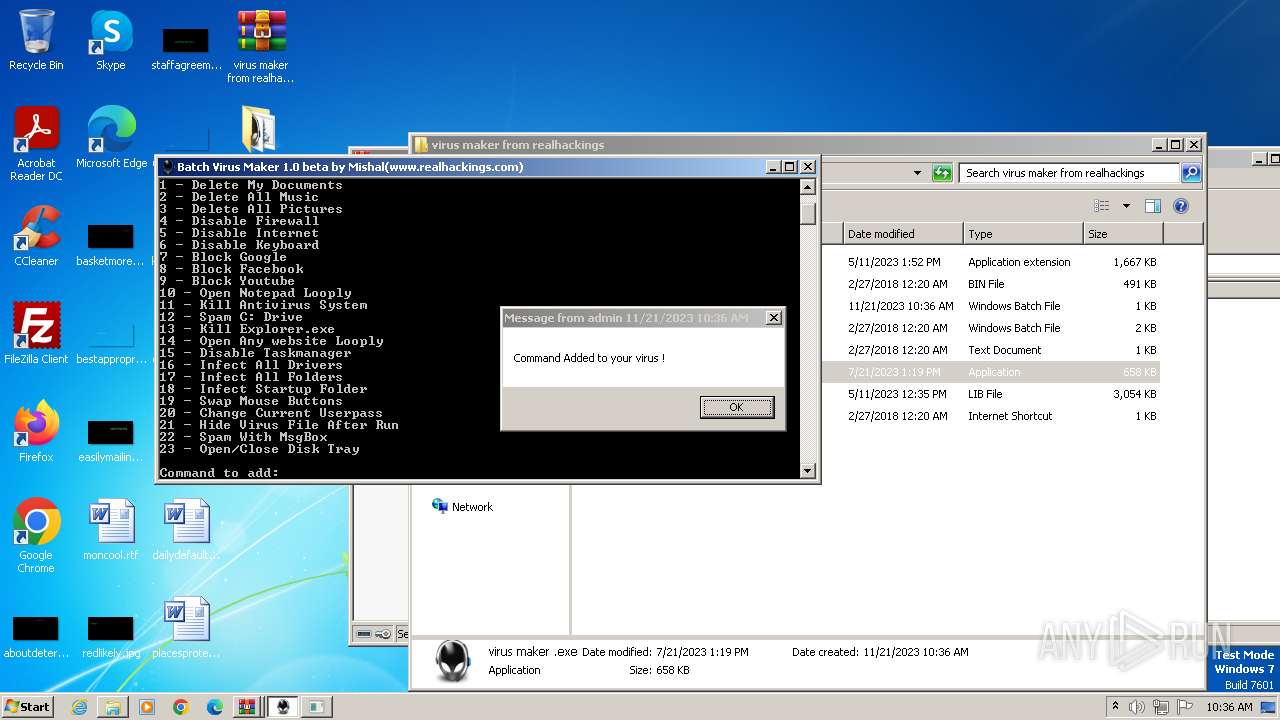
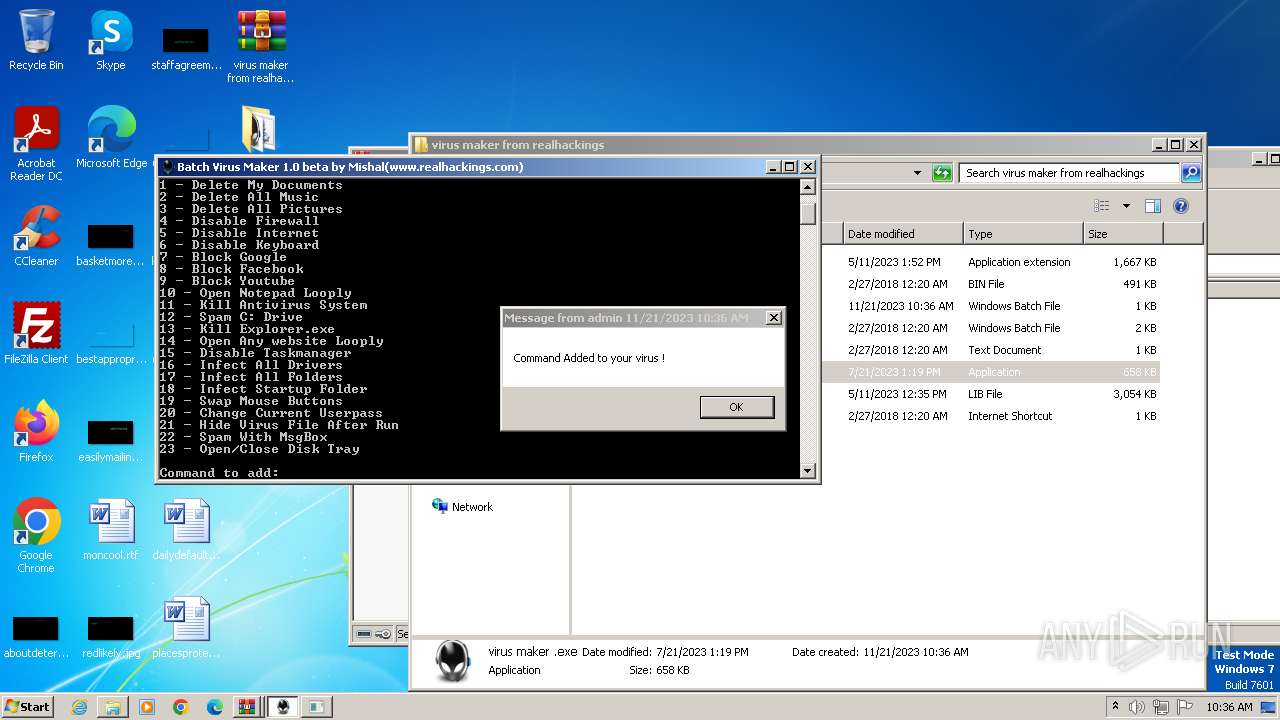
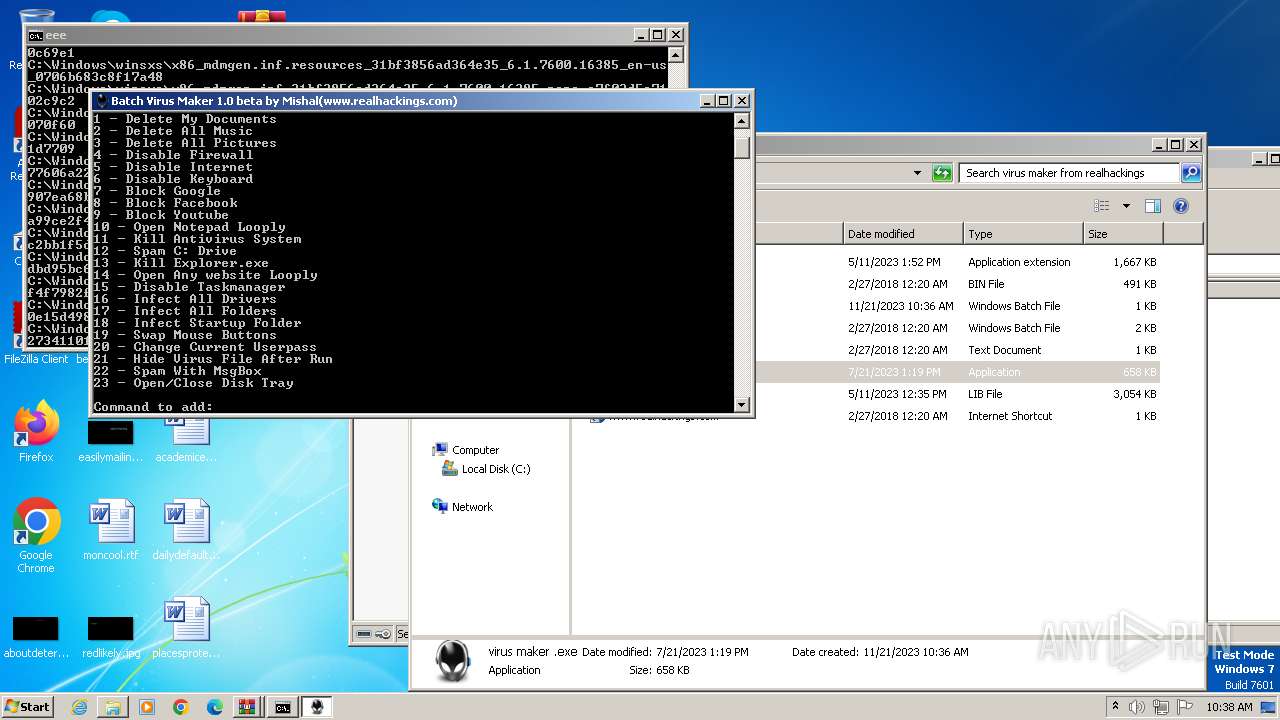
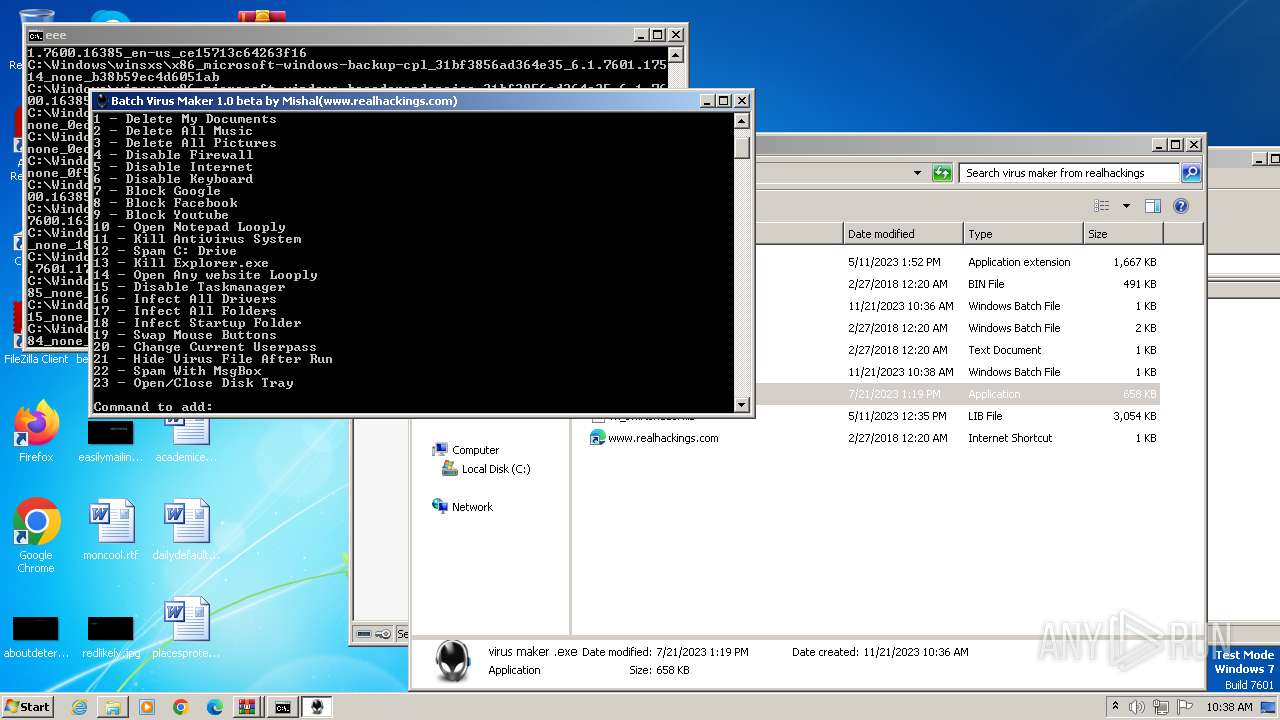
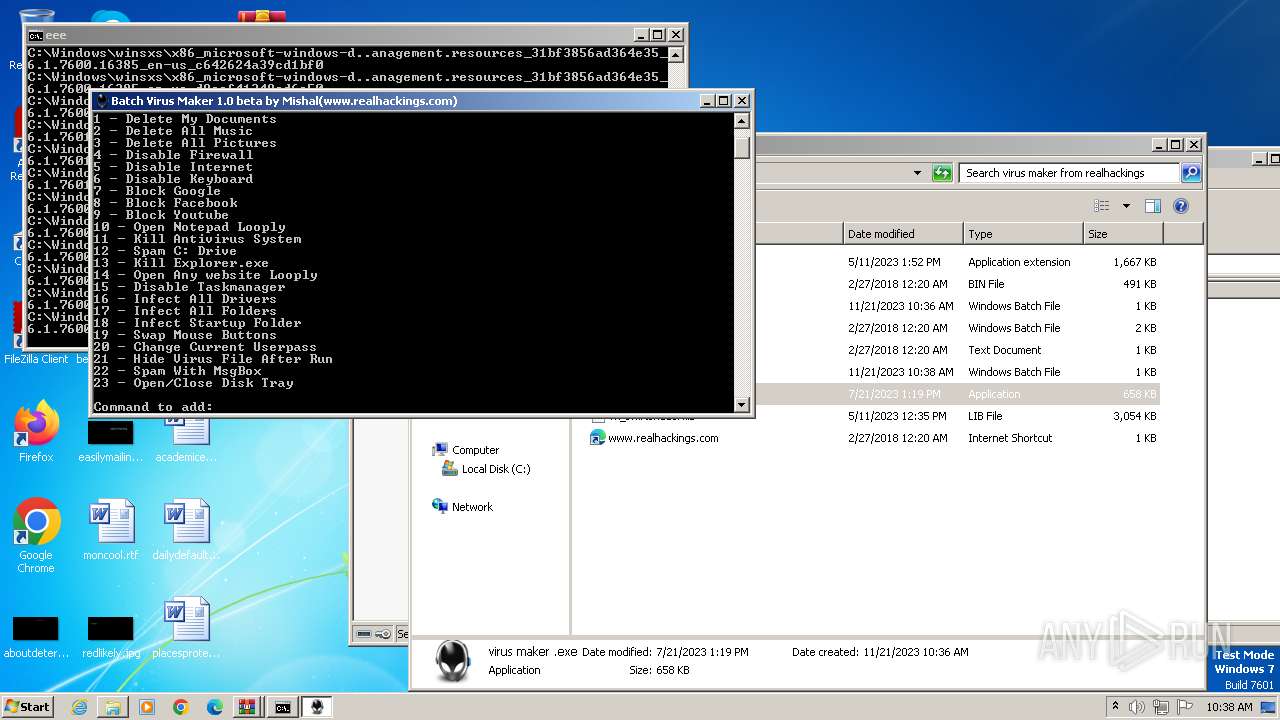
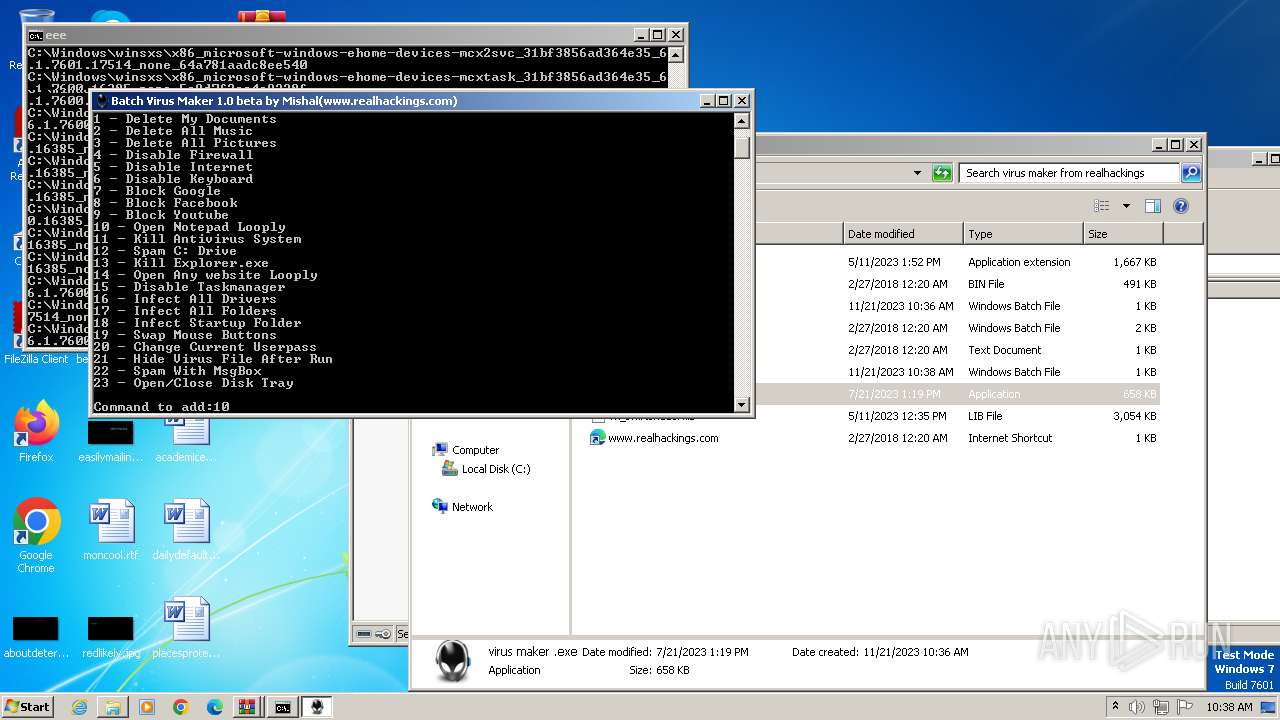
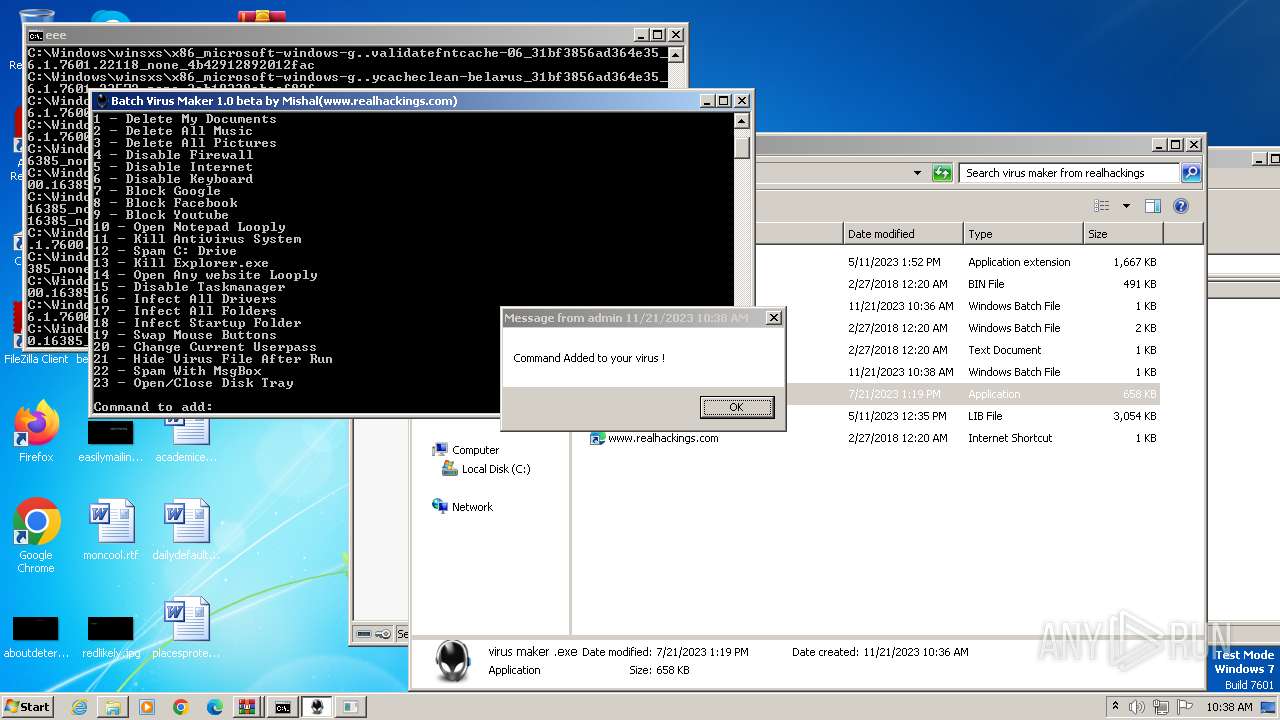
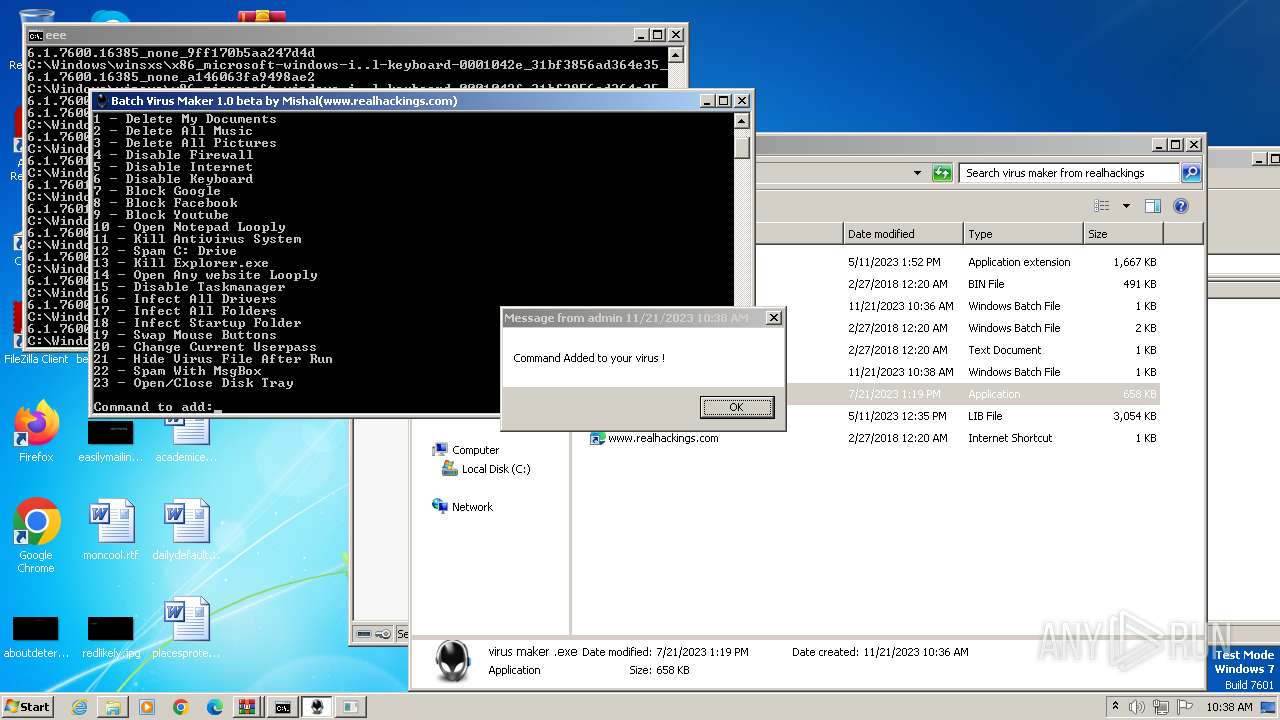
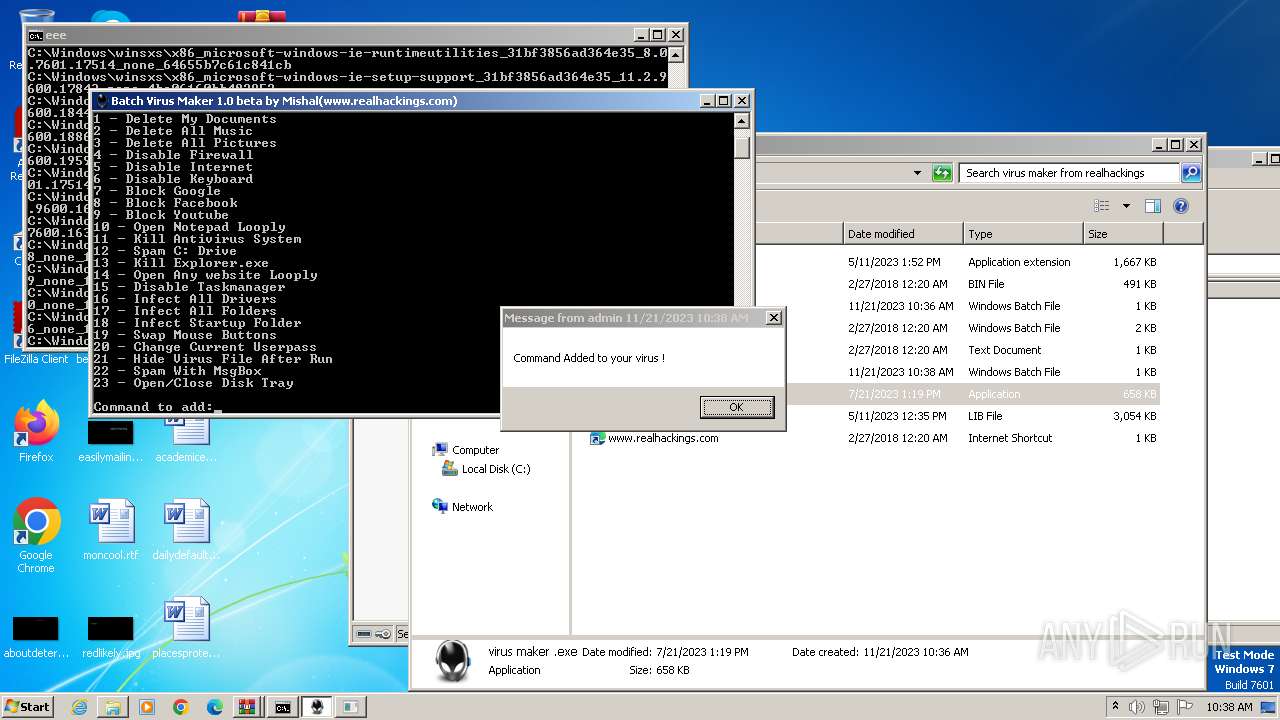
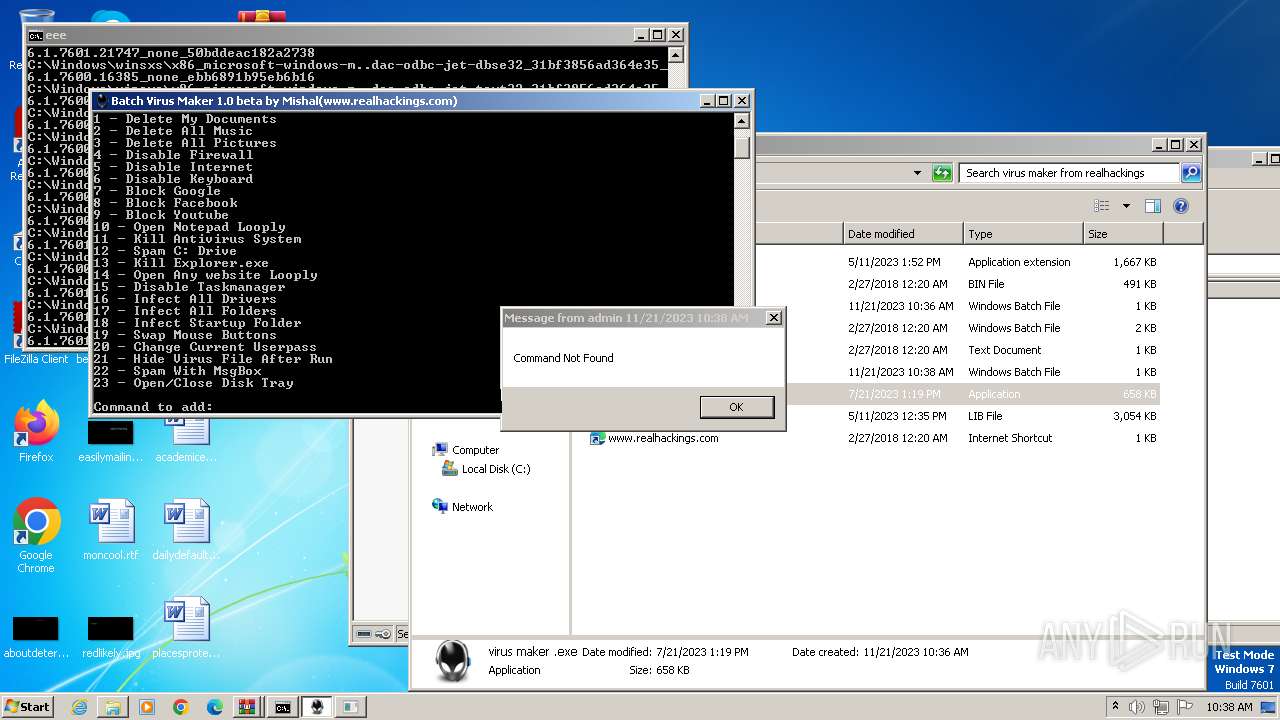
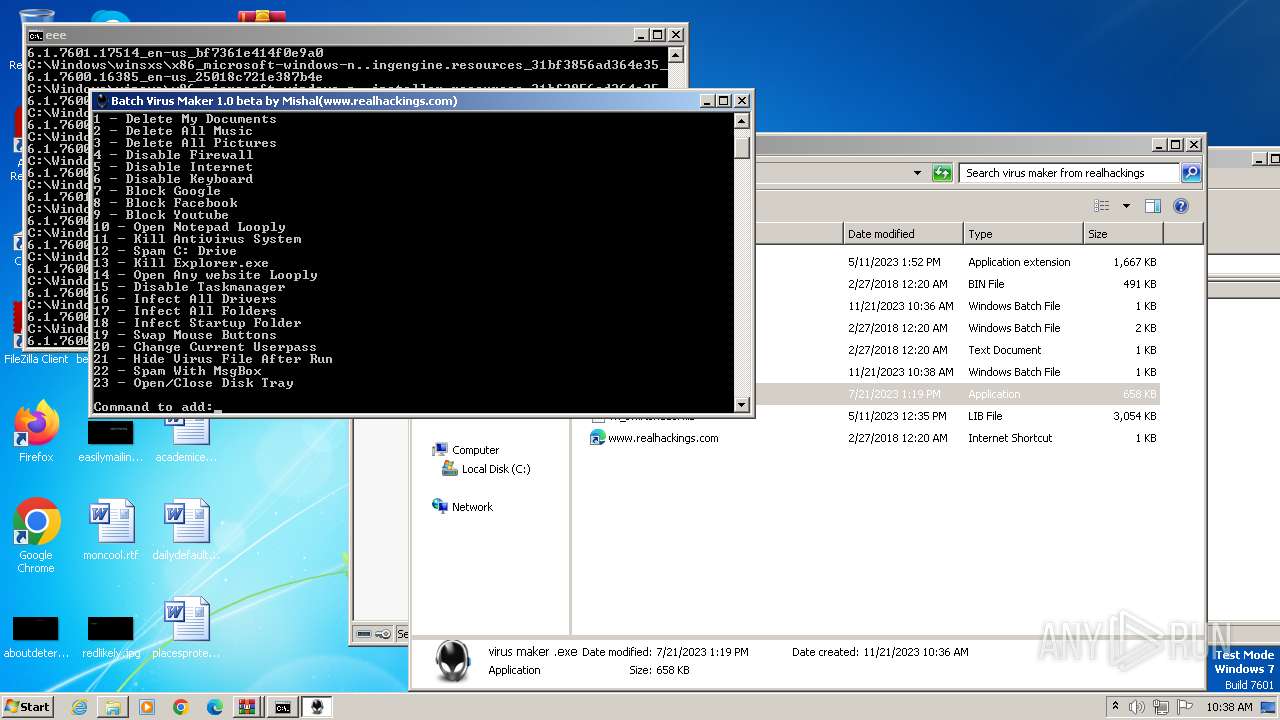
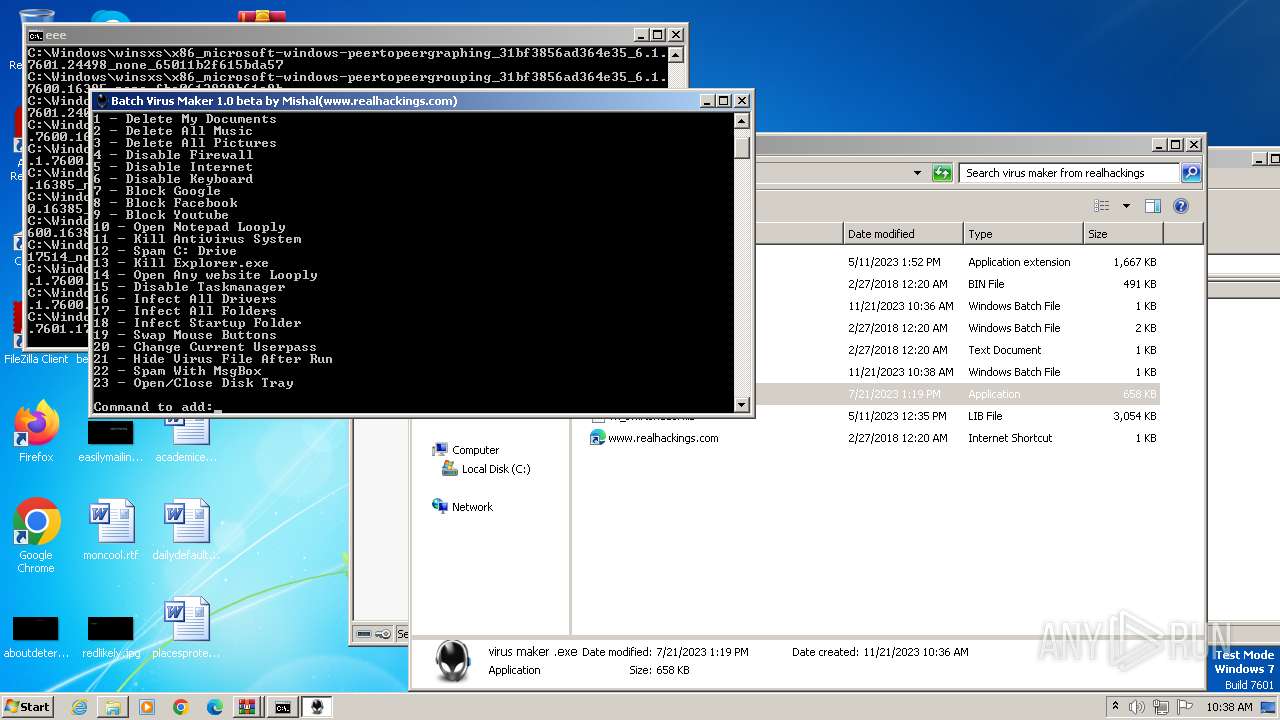
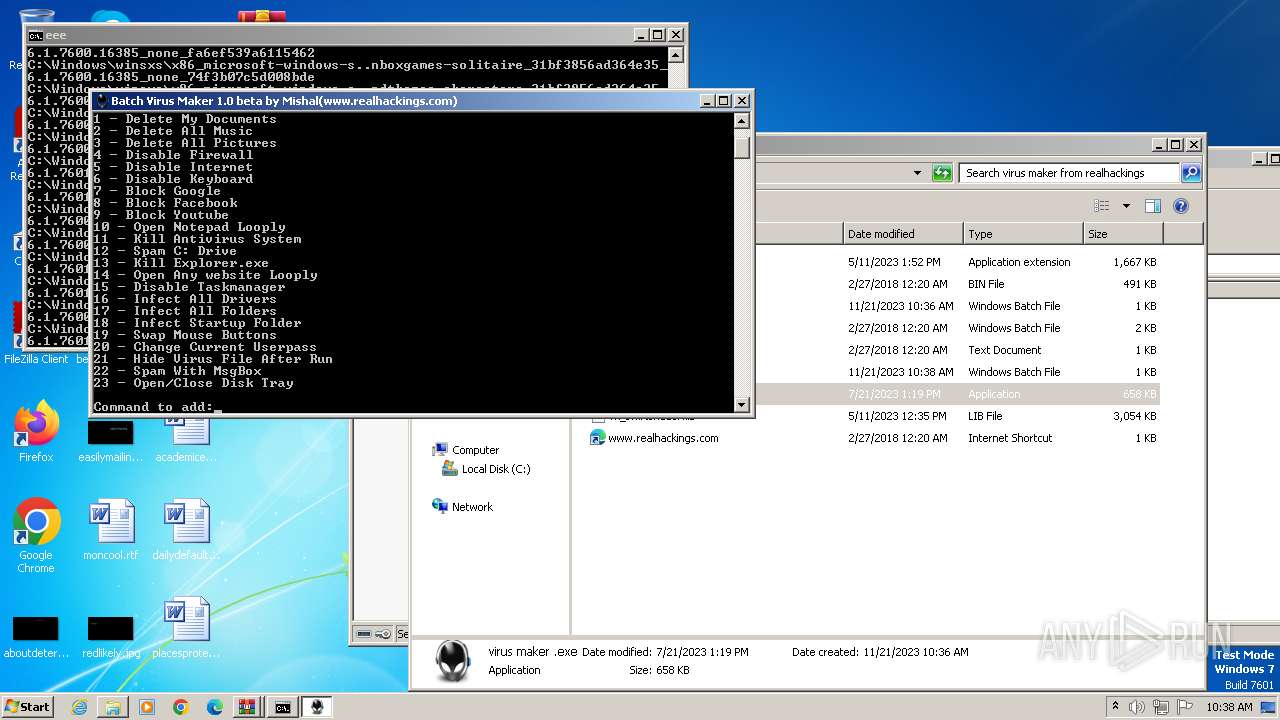
| File name: | virus maker from realhackings.tar.gz |
| Full analysis: | https://app.any.run/tasks/4ee1b519-dd8f-4a12-a232-72df633617a1 |
| Verdict: | Malicious activity |
| Analysis date: | November 21, 2023, 10:35:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/gzip |
| File info: | gzip compressed data, last modified: Tue Nov 21 10:31:18 2023, from Unix, original size modulo 2^32 6018048 |
| MD5: | 182BB80C4CFBB0F29988B9977828C53A |
| SHA1: | 03387C6810B33FC2E7C905F27428442D479E261F |
| SHA256: | B5BB62D865329D9CF0D647B496B65BF31DD853ED40DC30F7F4888F3792B577D3 |
| SSDEEP: | 98304:FGgwSFyT/0Y1oRjyPCqE3BETpQatkPRQhj8Ldr3Xb/deR4HbVeRbp8aS5HKNaCRD:KuXw |
MALICIOUS
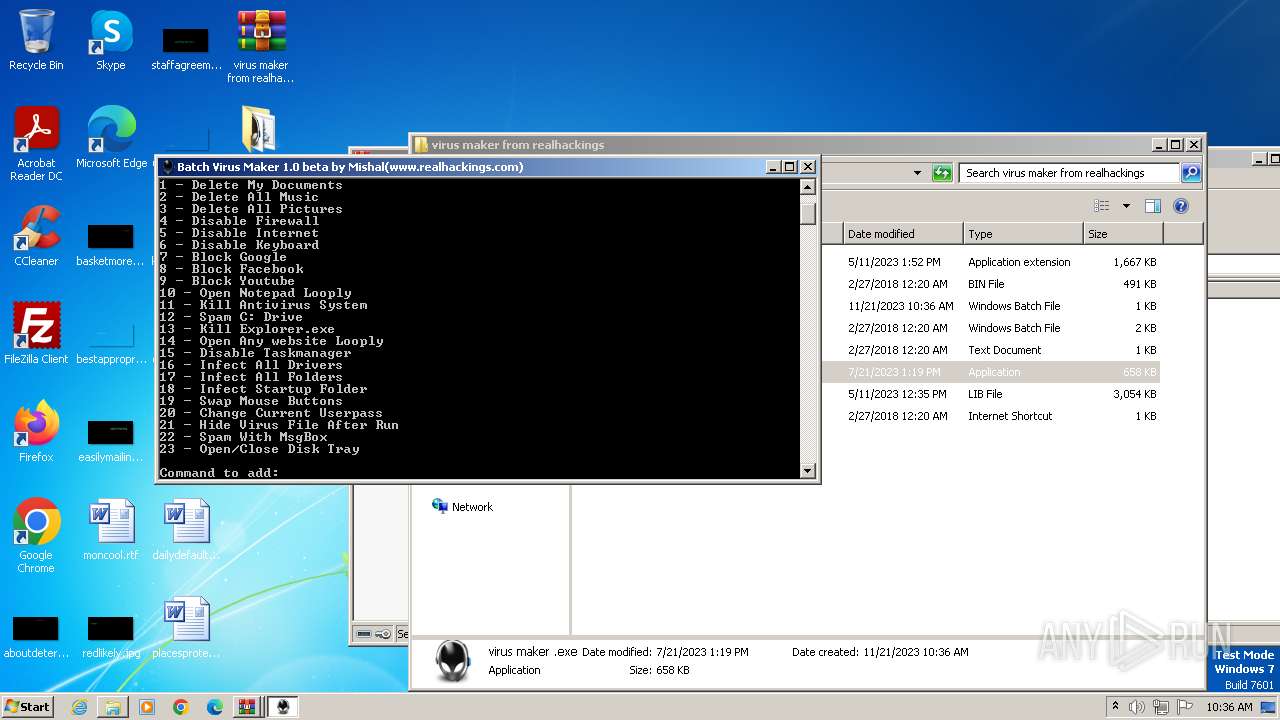
Create files in the Startup directory
- virus maker .exe (PID: 3444)
Drops the executable file immediately after the start
- virus maker .exe (PID: 3444)
SUSPICIOUS
Starts application with an unusual extension
- virus maker .exe (PID: 3444)
- virus maker .exe (PID: 284)
The process creates files with name similar to system file names
- virus maker .exe (PID: 3444)
Starts CMD.EXE for commands execution
- CefSharp.bin (PID: 3656)
- CefSharp.bin (PID: 2296)
Executing commands from ".cmd" file
- CefSharp.bin (PID: 3656)
- CefSharp.bin (PID: 2296)
Reads the BIOS version
- winsrvhost.exe (PID: 3756)
Process uses IPCONFIG to discard the IP address configuration
- cmd.exe (PID: 2196)
- cmd.exe (PID: 1600)
- cmd.exe (PID: 1152)
Reads the Internet Settings
- virus maker .exe (PID: 284)
Uses pipe srvsvc via SMB (transferring data)
- virus maker .exe (PID: 284)
INFO
Creates files or folders in the user directory
- virus maker .exe (PID: 3444)
Manual execution by a user
- WinRAR.exe (PID: 3504)
- virus maker .exe (PID: 3444)
- wmpnscfg.exe (PID: 4008)
- cmd.exe (PID: 3788)
- cmd.exe (PID: 1600)
- cmd.exe (PID: 2196)
- wmpnscfg.exe (PID: 296)
- cmd.exe (PID: 1152)
- cmd.exe (PID: 3796)
- virus maker .exe (PID: 284)
Checks supported languages
- virus maker .exe (PID: 3444)
- CefSharp.bin (PID: 3656)
- UserOOOBE.exe (PID: 3664)
- winsrvhost.exe (PID: 3756)
- wmpnscfg.exe (PID: 4008)
- CefSharp.bin (PID: 2296)
- virus maker .exe (PID: 284)
- wmpnscfg.exe (PID: 296)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3504)
Reads the computer name
- virus maker .exe (PID: 3444)
- winsrvhost.exe (PID: 3756)
- wmpnscfg.exe (PID: 4008)
- virus maker .exe (PID: 284)
- wmpnscfg.exe (PID: 296)
Create files in a temporary directory
- CefSharp.bin (PID: 3656)
- CefSharp.bin (PID: 2296)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 296)
- wmpnscfg.exe (PID: 4008)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .z/gz/gzip | | | GZipped data (100) |
|---|
EXIF
ZIP
| Compression: | Deflated |
|---|---|
| Flags: | (none) |
| ModifyDate: | 2023:11:21 11:31:18+01:00 |
| ExtraFlags: | (none) |
| OperatingSystem: | Unix |
Total processes
338
Monitored processes
289
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 272 | notepad.exe | C:\Windows\System32\notepad.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 280 | notepad.exe | C:\Windows\System32\notepad.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 284 | "C:\Users\admin\Desktop\virus maker from realhackings\virus maker .exe" | C:\Users\admin\Desktop\virus maker from realhackings\virus maker .exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 292 | notepad.exe | C:\Windows\System32\notepad.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 296 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 300 | notepad.exe | C:\Windows\System32\notepad.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 368 | notepad.exe | C:\Windows\System32\notepad.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 372 | notepad.exe | C:\Windows\System32\notepad.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 544 | notepad.exe | C:\Windows\System32\notepad.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 552 | notepad.exe | C:\Windows\System32\notepad.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
6 384
Read events
6 356
Write events
22
Delete events
6
Modification events
| (PID) Process: | (3212) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3212) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3212) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3212) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3212) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3212) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3212) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3212) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3212) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (3504) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
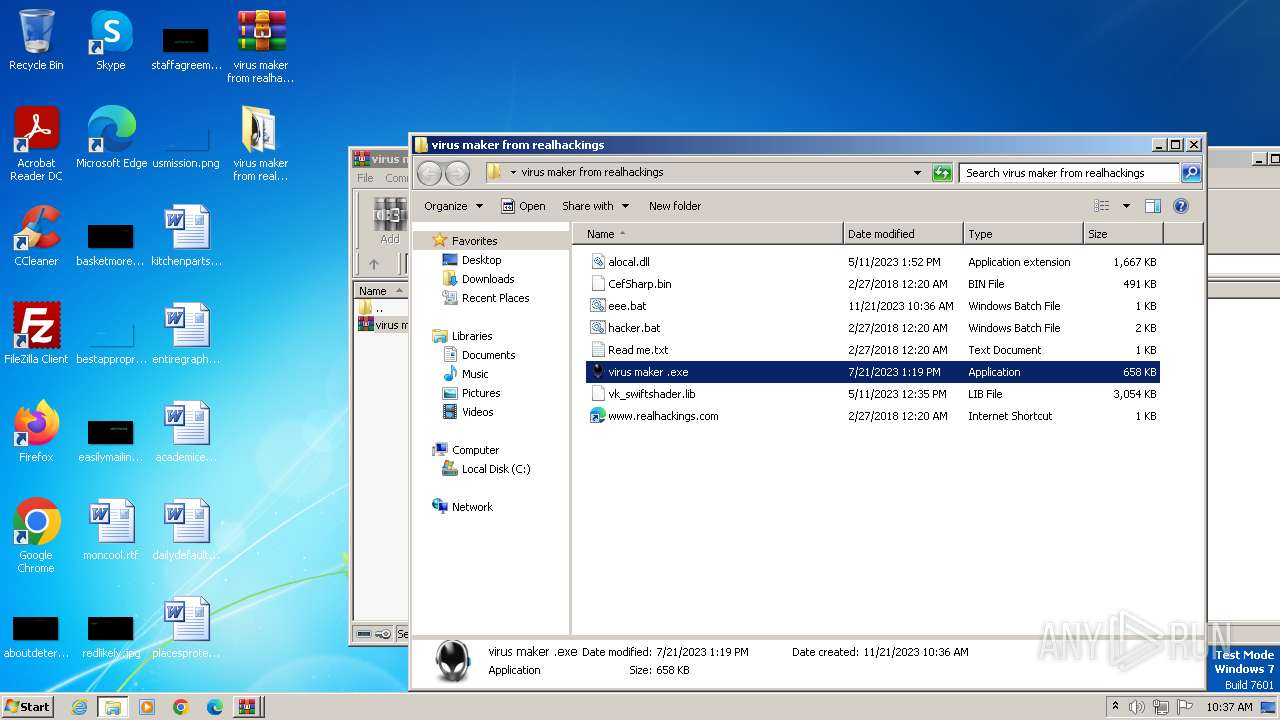
Executable files
6
Suspicious files
3
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3212 | WinRAR.exe | C:\Users\admin\Desktop\virus maker from realhackings.tar.gz | — | |
MD5:— | SHA256:— | |||
| 3444 | virus maker .exe | C:\Users\admin\AppData\Local\UserOOOBE\UserOOOBE.exe | executable | |
MD5:939712A4D4341FB67C0214621A78FCA7 | SHA256:F594FF49EA0A51DC4A76609291B7C3E44FCC92789378F899349609407AC55B61 | |||
| 3504 | WinRAR.exe | C:\Users\admin\Desktop\virus maker from realhackings\vk_swiftshader.lib | executable | |
MD5:A553208EA4A57F1334669FE1E80113B7 | SHA256:C868A800BEF638FD579202534FA763A584CF78A01447AFC89908ED1BAE308ACE | |||
| 3504 | WinRAR.exe | C:\Users\admin\Desktop\virus maker from realhackings\alocal.dll | executable | |
MD5:939712A4D4341FB67C0214621A78FCA7 | SHA256:F594FF49EA0A51DC4A76609291B7C3E44FCC92789378F899349609407AC55B61 | |||
| 3644 | cmd.exe | C:\Users\admin\Desktop\virus maker from realhackings\eee.bat | text | |
MD5:EEB086A7854DAE6CDCE64F49EB87D64C | SHA256:5822C2222C4A4121A1667C7D483FF8B91E489A4C5E881C75A4354712BFE6F435 | |||
| 2296 | CefSharp.bin | C:\Users\admin\AppData\Local\Temp\2296UPBH.cmd | text | |
MD5:F4E01D7ADEBCD2F0E1112AD442C9F152 | SHA256:A03984F944D77AE86AD8318DC33C9968A7B5E0A0E08FADC1C3BDC18549FBBBCE | |||
| 2444 | cmd.exe | C:\Users\admin\Desktop\virus maker from realhackings\rhhhwjwj.bat | text | |
MD5:EEB086A7854DAE6CDCE64F49EB87D64C | SHA256:5822C2222C4A4121A1667C7D483FF8B91E489A4C5E881C75A4354712BFE6F435 | |||
| 3656 | CefSharp.bin | C:\Users\admin\AppData\Local\Temp\3656IM15.cmd | text | |
MD5:F4E01D7ADEBCD2F0E1112AD442C9F152 | SHA256:A03984F944D77AE86AD8318DC33C9968A7B5E0A0E08FADC1C3BDC18549FBBBCE | |||
| 3504 | WinRAR.exe | C:\Users\admin\Desktop\virus maker from realhackings\Read me.txt | text | |
MD5:0F369536A543578BF3F608291AFD00BF | SHA256:05DA9BF8959DED4A7126CFAD6EC972C9CFB707C9233160BB3E38E6A69111F59A | |||
| 3504 | WinRAR.exe | C:\Users\admin\Desktop\virus maker from realhackings\hacker.bat | text | |
MD5:6ED7A2BBAE91EE346334C1966776B4DA | SHA256:6F49B912B4CC566E2B08334D447B609759A8DDBDA6D153BF7CC5BE1679682C47 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
10
DNS requests
9
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3756 | winsrvhost.exe | GET | 302 | 162.216.242.206:80 | http://stlaip578223.ddnsgeek.com/ | unknown | html | 163 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
868 | svchost.exe | 184.30.20.134:80 | armmf.adobe.com | AKAMAI-AS | DE | unknown |
3756 | winsrvhost.exe | 162.216.242.206:80 | stlaip578223.ddnsgeek.com | DYNU | US | unknown |
3756 | winsrvhost.exe | 185.247.224.98:443 | stlaep34621.ddnsgeek.com | Flokinet Ltd | SC | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
armmf.adobe.com |
| whitelisted |
stlaip742915.ddnsgeek.com |
| unknown |
stlaip578223.ddnsgeek.com |
| unknown |
stlaep34621.ddnsgeek.com |
| unknown |
dns.msftncsi.com |
| shared |
winsrvhost.lnk |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.ddnsgeek .com Domain |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.ddnsgeek .com Domain |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.ddnsgeek .com Domain |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.ddnsgeek .com Domain |
4 ETPRO signatures available at the full report