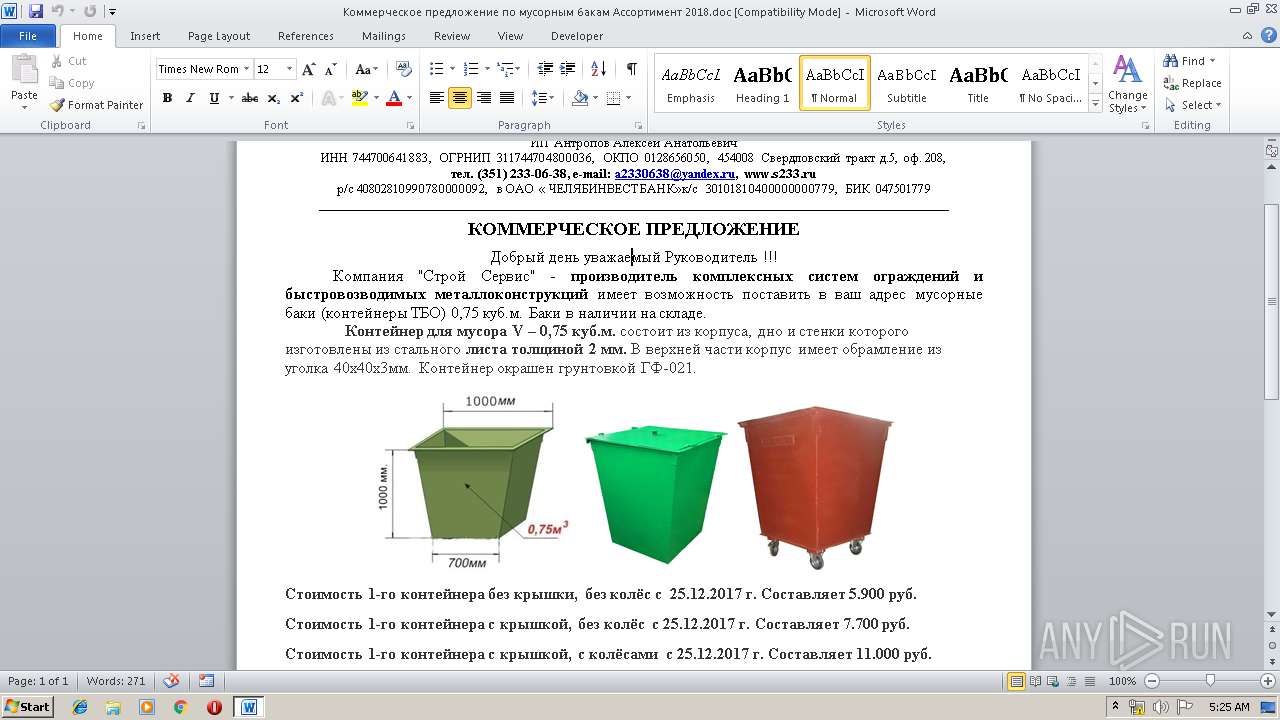
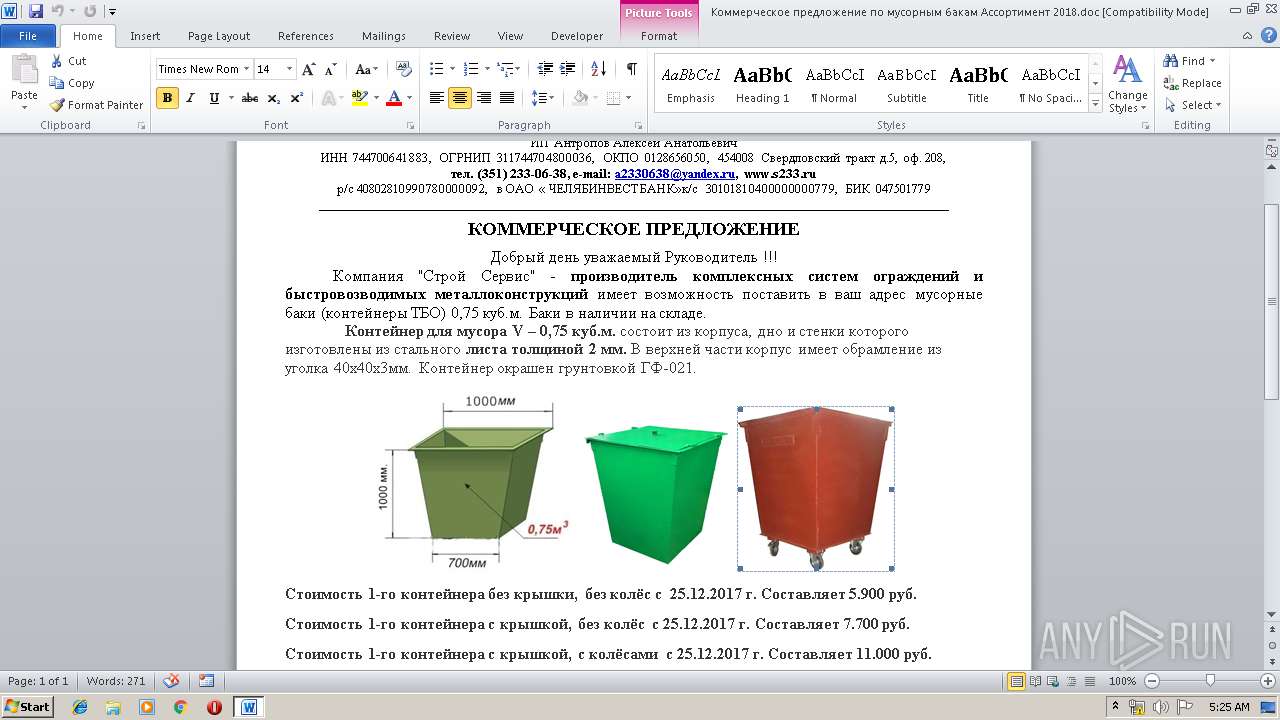
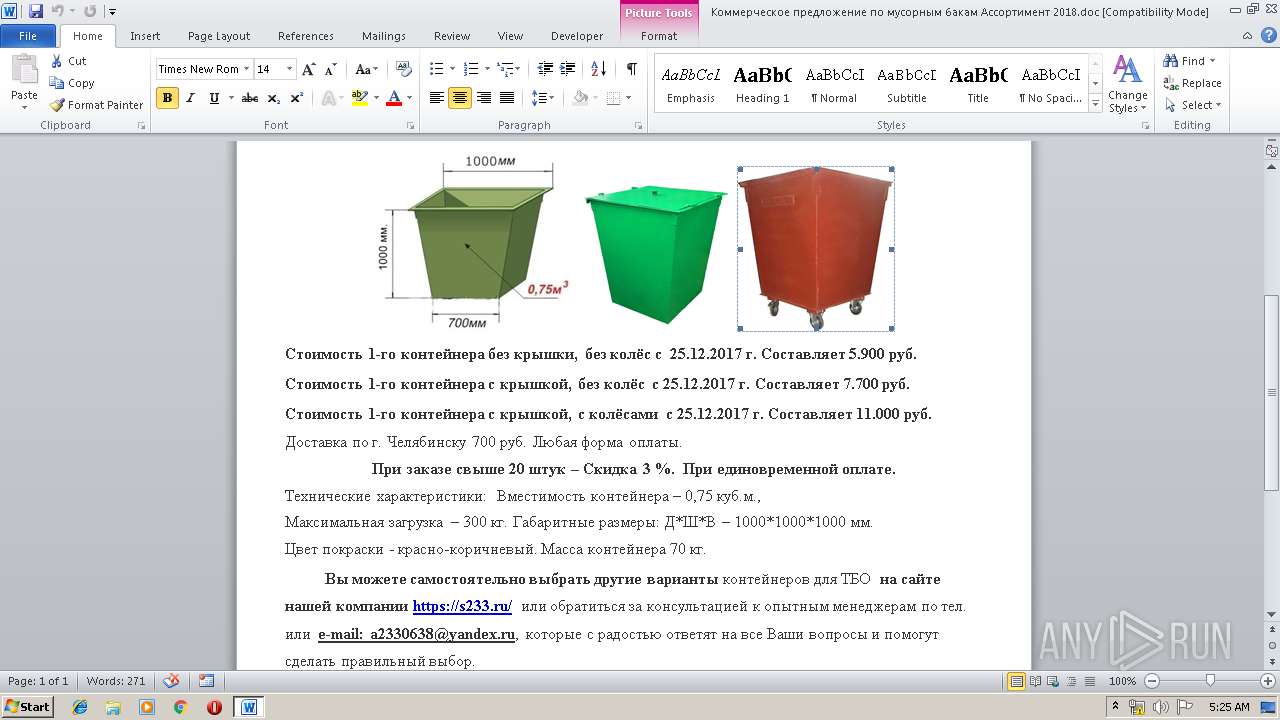
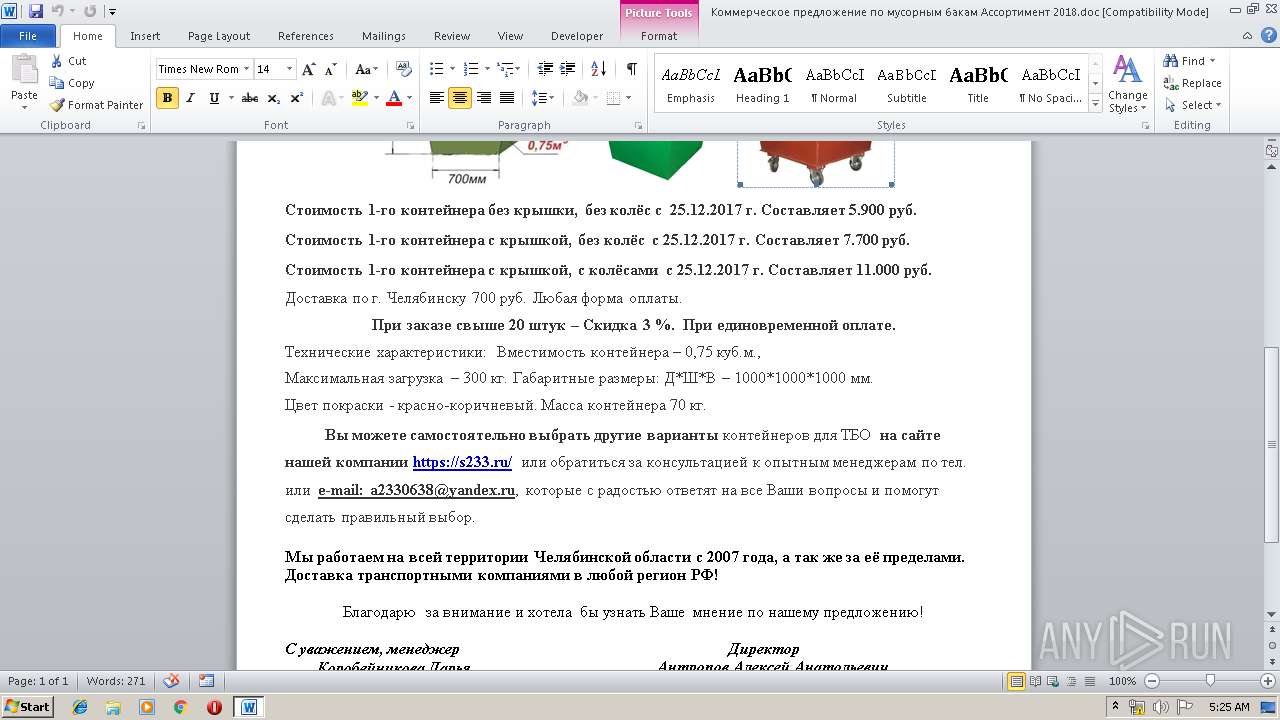
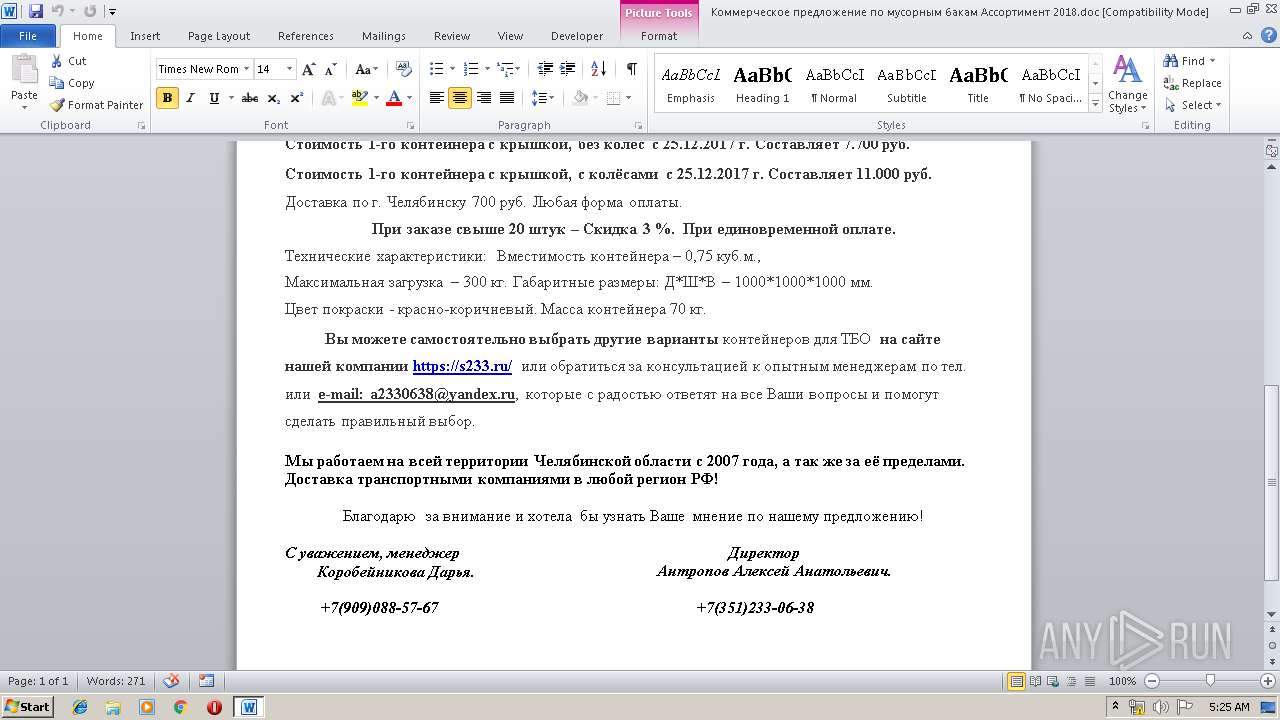
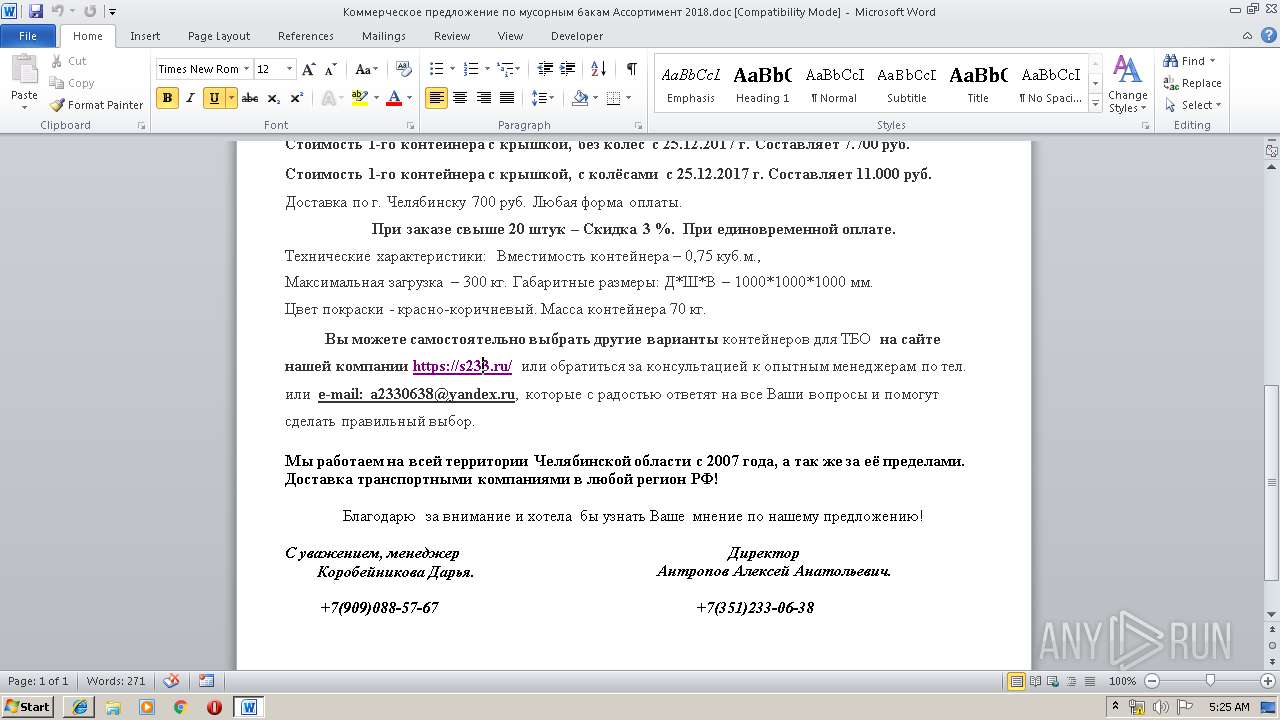
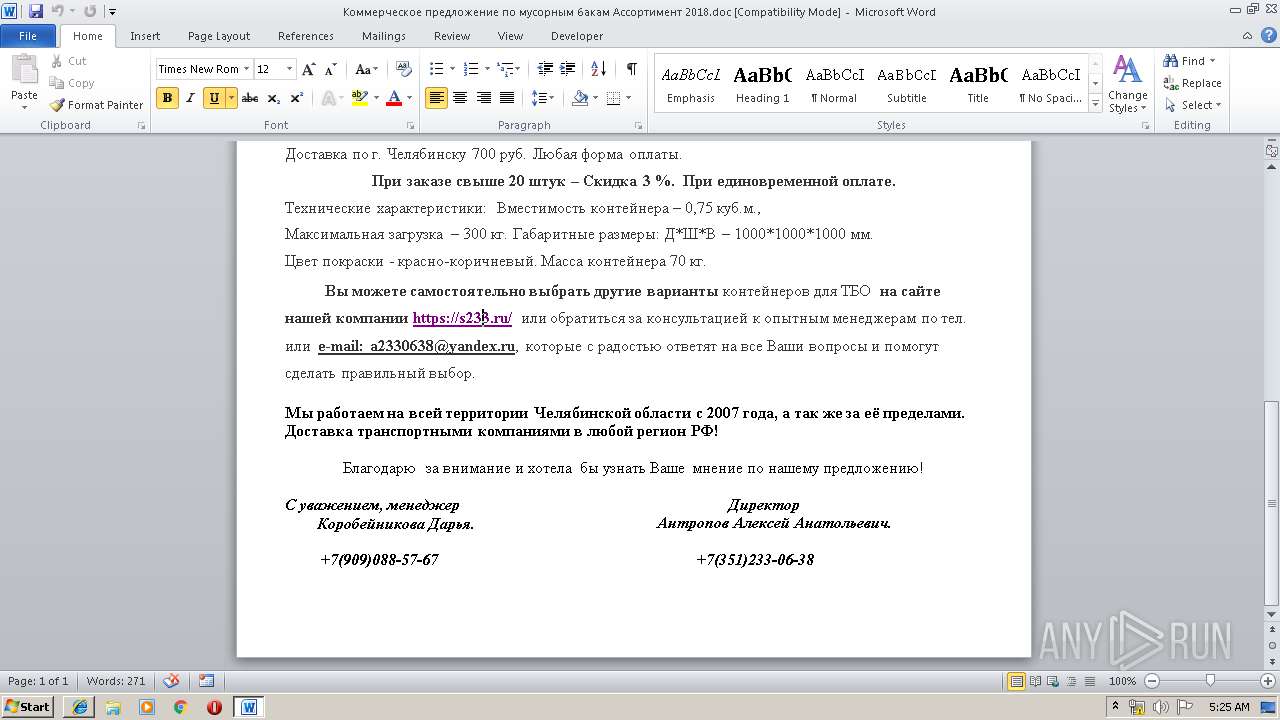
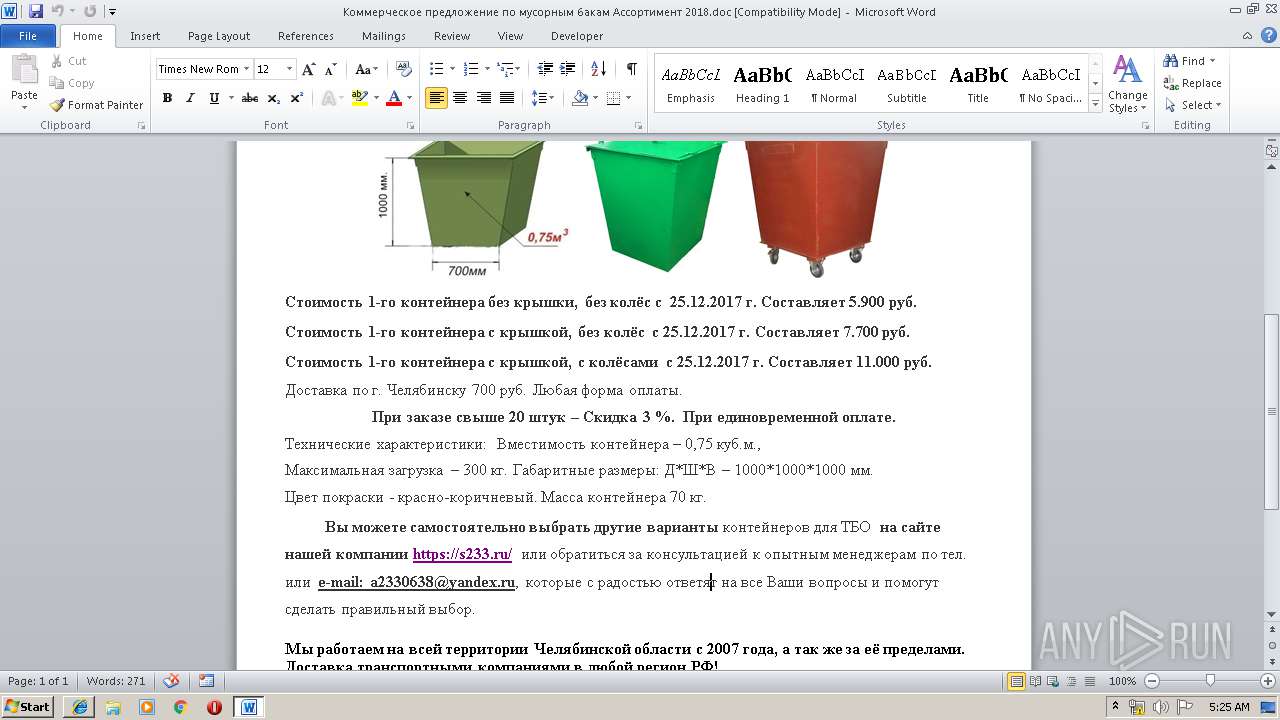
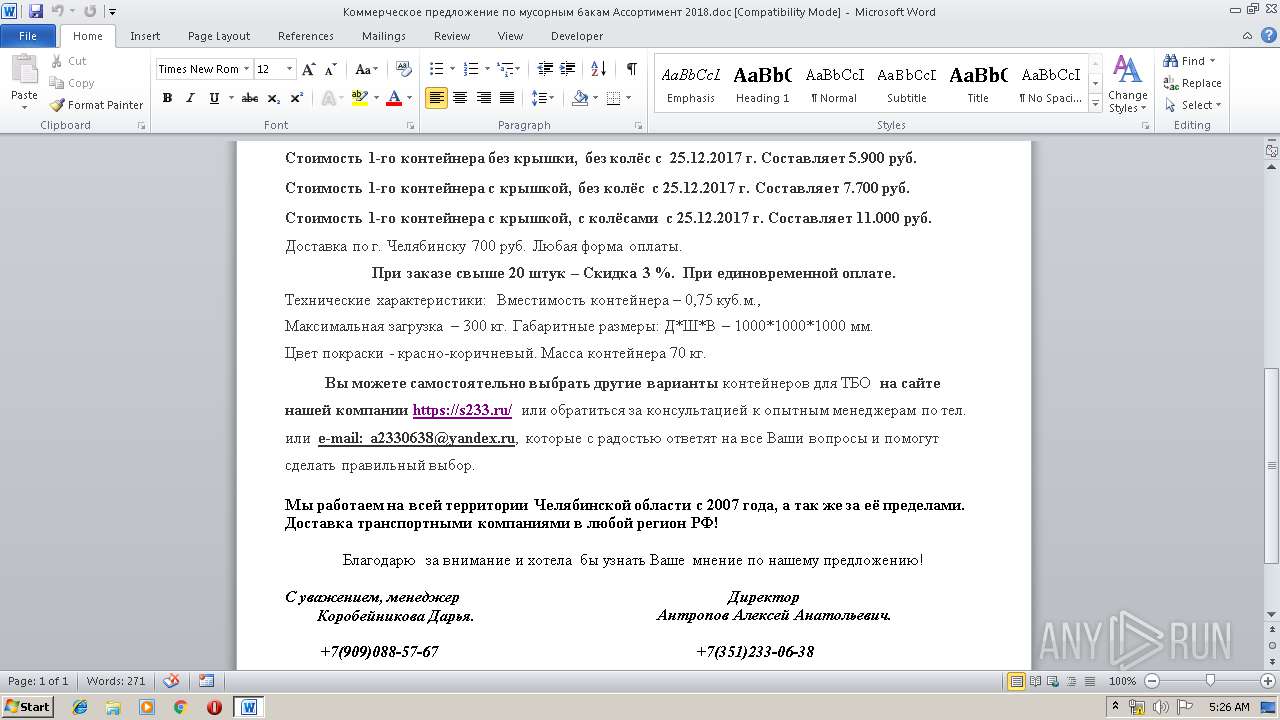
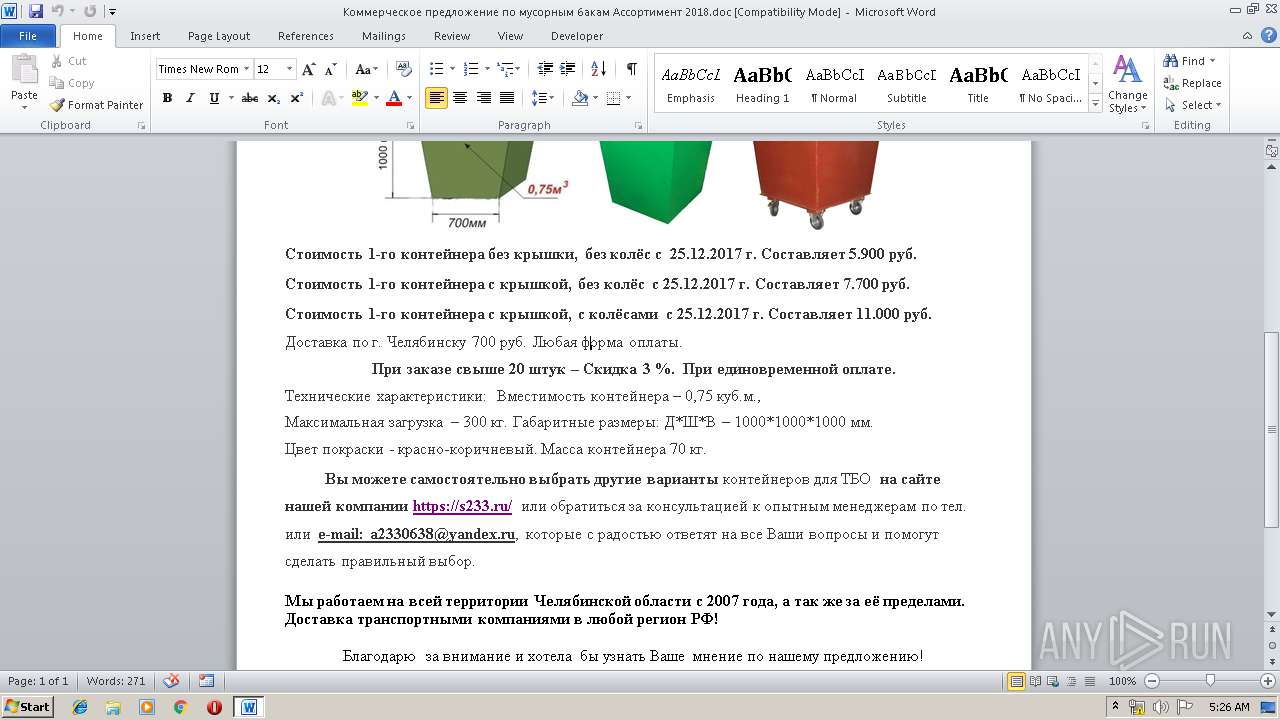
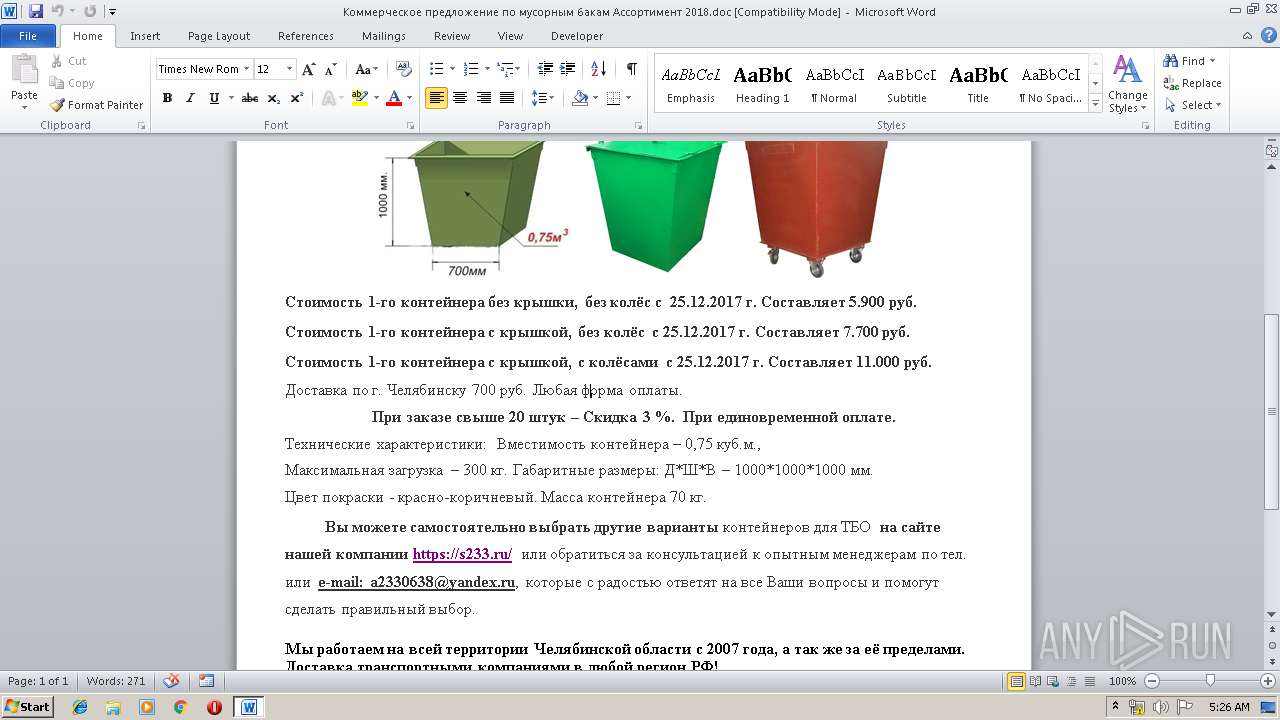
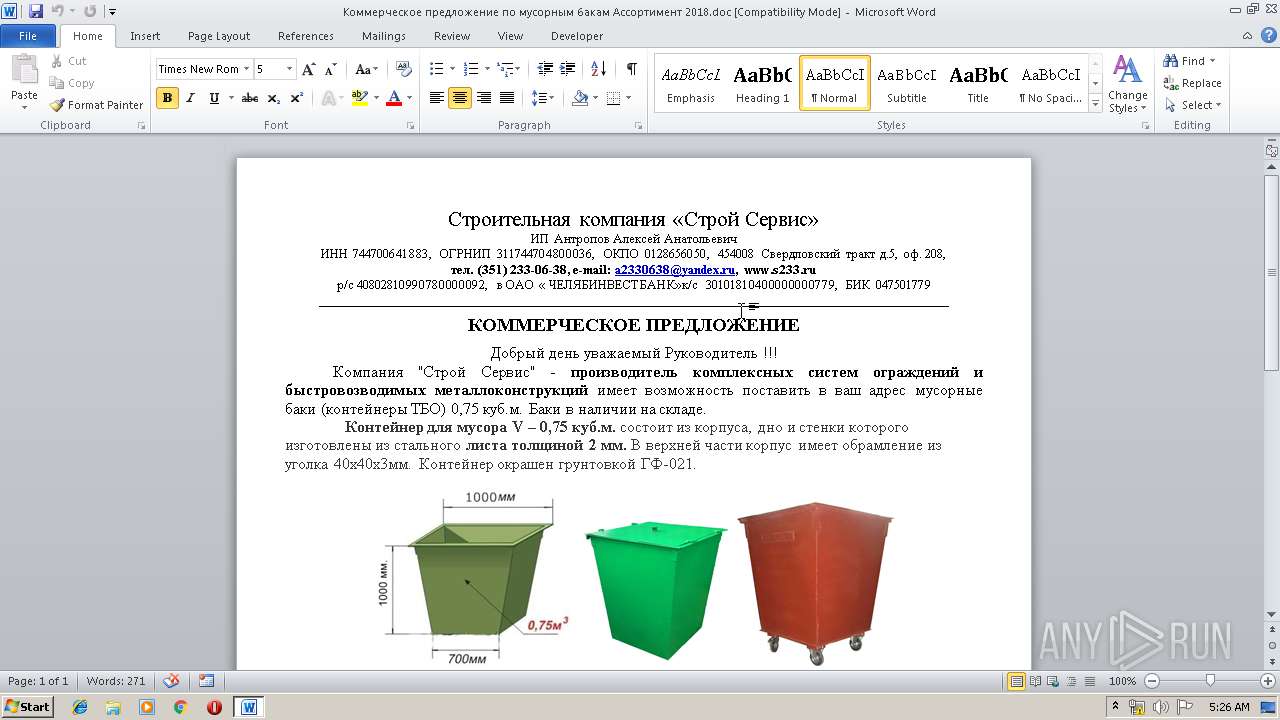
| File name: | Коммерческое предложение по мусорным бакам Ассортимент 2018.doc |
| Full analysis: | https://app.any.run/tasks/3e298a09-1da3-4cfc-9ede-2c09f0fed0b1 |
| Verdict: | Malicious activity |
| Analysis date: | April 24, 2019, 04:24:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 5.1, Code page: 1251, Title: N, Author: Shelkova, Template: Normal.dot, Last Saved By: Admin, Revision Number: 77, Name of Creating Application: Microsoft Office Word, Total Editing Time: 05:01:00, Last Printed: Wed Jun 27 14:40:00 2018, Create Time/Date: Tue Aug 27 11:24:00 2013, Last Saved Time/Date: Mon Apr 22 06:34:00 2019, Number of Pages: 1, Number of Words: 343, Number of Characters: 1961, Security: 0 |
| MD5: | B0A0BA3E69A5A8733D8460E724347B01 |
| SHA1: | B9C3147D2A415ABB04172A1E6E6D1B5C3478E930 |
| SHA256: | B5B145FCADA2ACF80E21F45C62DE1F109583AE2E6459420B344EC7BD80D33031 |
| SSDEEP: | 1536:BjV7Qc7KE4PBPGj7NIswxL6V+9yauwQxsVO910lhgR0eKiwgCHEgNqTAB3Vb+2bz:BjV74BhOgL6V+rabXHKeKiwovTAhJ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads internet explorer settings
- WINWORD.EXE (PID: 1792)
INFO
Application launched itself
- iexplore.exe (PID: 3280)
Changes internet zones settings
- iexplore.exe (PID: 3280)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 1792)
Creates files in the user directory
- WINWORD.EXE (PID: 1792)
- iexplore.exe (PID: 3264)
- iexplore.exe (PID: 3280)
Reads Internet Cache Settings
- iexplore.exe (PID: 3264)
Reads internet explorer settings
- iexplore.exe (PID: 3264)
Reads settings of System Certificates
- iexplore.exe (PID: 3280)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3280)
Changes settings of System certificates
- iexplore.exe (PID: 3280)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (80) |
|---|
EXIF
FlashPix
| Title: | N |
|---|---|
| Subject: | - |
| Author: | Shelkova |
| Keywords: | - |
| Template: | Normal.dot |
| LastModifiedBy: | Admin |
| RevisionNumber: | 77 |
| Software: | Microsoft Office Word |
| TotalEditTime: | 5.0 hours |
| LastPrinted: | 2018:06:27 13:40:00 |
| CreateDate: | 2013:08:27 10:24:00 |
| ModifyDate: | 2019:04:22 05:34:00 |
| Pages: | 1 |
| Words: | 343 |
| Characters: | 1961 |
| Security: | None |
| Company: | * |
| Lines: | 16 |
| Paragraphs: | 4 |
| CharCountWithSpaces: | 2300 |
| AppVersion: | 11.9999 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | N |
| HeadingPairs: |
|
| CodePage: | Windows Cyrillic |
| Hyperlinks: |
|
| CompObjUserTypeLen: | 31 |
| CompObjUserType: | ???????? Microsoft Office Word |
Total processes
35
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1792 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Коммерческое предложение по мусорным бакам Ассортимент 2018.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3264 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3280 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3280 | "C:\Program Files\Internet Explorer\iexplore.exe" -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 575
Read events
1 163
Write events
402
Delete events
10
Modification events
| (PID) Process: | (1792) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | l(< |
Value: 6C283C0000070000010000000000000000000000 | |||
| (PID) Process: | (1792) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1792) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (1792) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1318584350 | |||
| (PID) Process: | (1792) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1318584464 | |||
| (PID) Process: | (1792) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1318584465 | |||
| (PID) Process: | (1792) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 00070000A80385BC55FAD40100000000 | |||
| (PID) Process: | (1792) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 0*< |
Value: 302A3C000007000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (1792) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | 0*< |
Value: 302A3C000007000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (1792) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
0
Suspicious files
6
Text files
70
Unknown types
19
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1792 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR604C.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3280 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3280 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 1792 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF321E4F9206DF02BF.TMP | — | |
MD5:— | SHA256:— | |||
| 3264 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OTFEV868\s233_ru[1].txt | — | |
MD5:— | SHA256:— | |||
| 1792 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 1792 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$ммерческое предложение по мусорным бакам Ассортимент 2018.doc | pgc | |
MD5:— | SHA256:— | |||
| 3264 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3264 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3264 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@s233[1].txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
44
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3264 | iexplore.exe | GET | 200 | 91.199.212.52:80 | http://crt.comodoca.com/COMODORSAAddTrustCA.crt | GB | der | 1.37 Kb | whitelisted |
3280 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3280 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
1792 | WINWORD.EXE | 178.248.237.63:443 | s233.ru | HLL LLC | RU | suspicious |
3264 | iexplore.exe | 178.248.237.63:443 | s233.ru | HLL LLC | RU | suspicious |
3264 | iexplore.exe | 77.88.21.119:443 | mc.yandex.ru | YANDEX LLC | RU | whitelisted |
3264 | iexplore.exe | 216.58.207.78:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
3264 | iexplore.exe | 193.34.169.14:443 | ruprom-uc.prom.st | UAPROM LLC | UA | unknown |
3264 | iexplore.exe | 193.34.169.18:443 | tracker.tiu.ru | UAPROM LLC | UA | suspicious |
3264 | iexplore.exe | 193.34.169.9:443 | uaprom-static.c2.prom.st | UAPROM LLC | UA | suspicious |
3264 | iexplore.exe | 193.34.169.2:443 | images.ru.prom.st | UAPROM LLC | UA | suspicious |
3264 | iexplore.exe | 188.42.30.20:443 | cdn.callbackhunter.com | Servers.com, Inc. | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
s233.ru |
| suspicious |
www.bing.com |
| whitelisted |
uaprom-static.c2.prom.st |
| suspicious |
www.google-analytics.com |
| whitelisted |
mc.yandex.ru |
| whitelisted |
ruprom-uc.prom.st |
| unknown |
tracker.tiu.ru |
| suspicious |
my.tiu.ru |
| suspicious |
images.ru.prom.st |
| suspicious |
cdn.callbackhunter.com |
| suspicious |