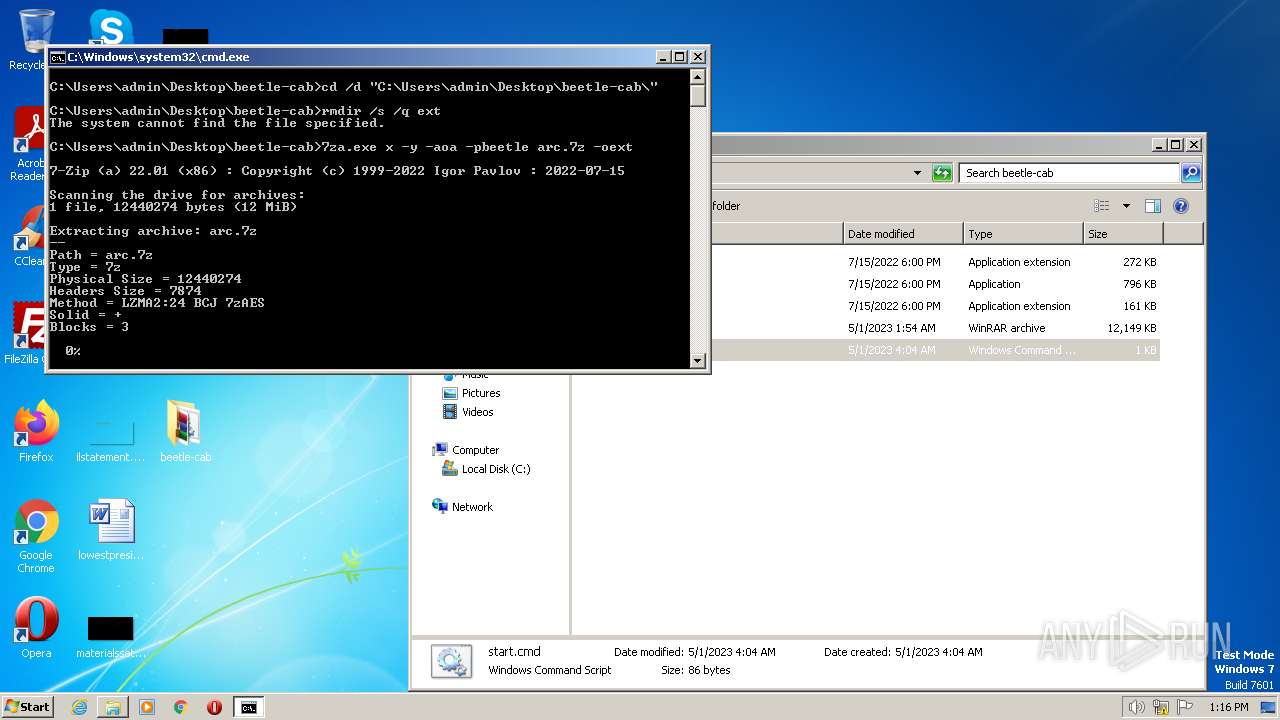
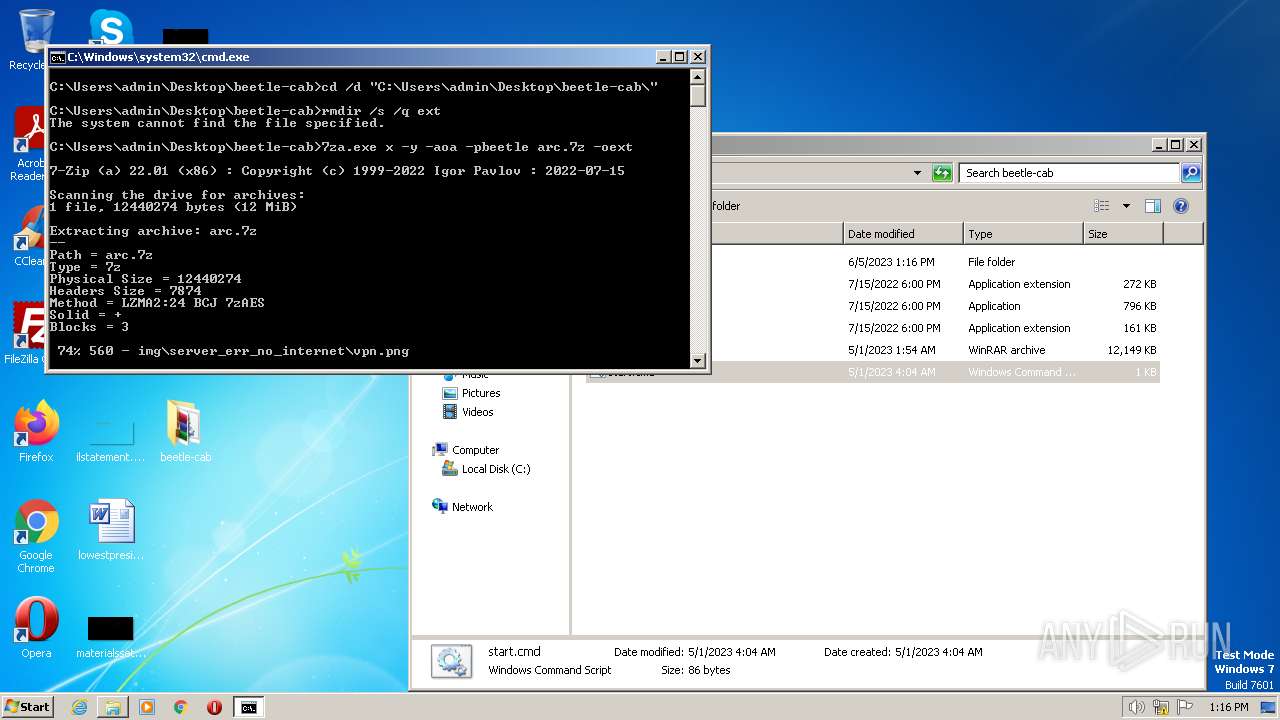
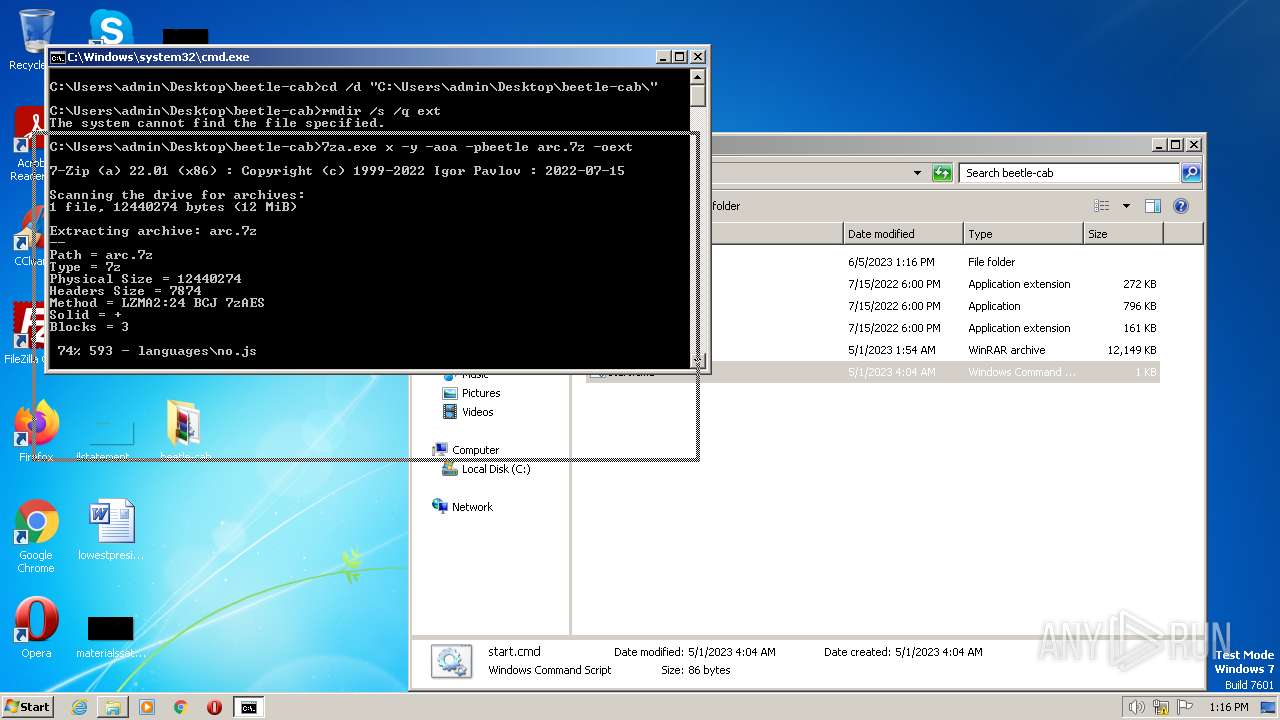
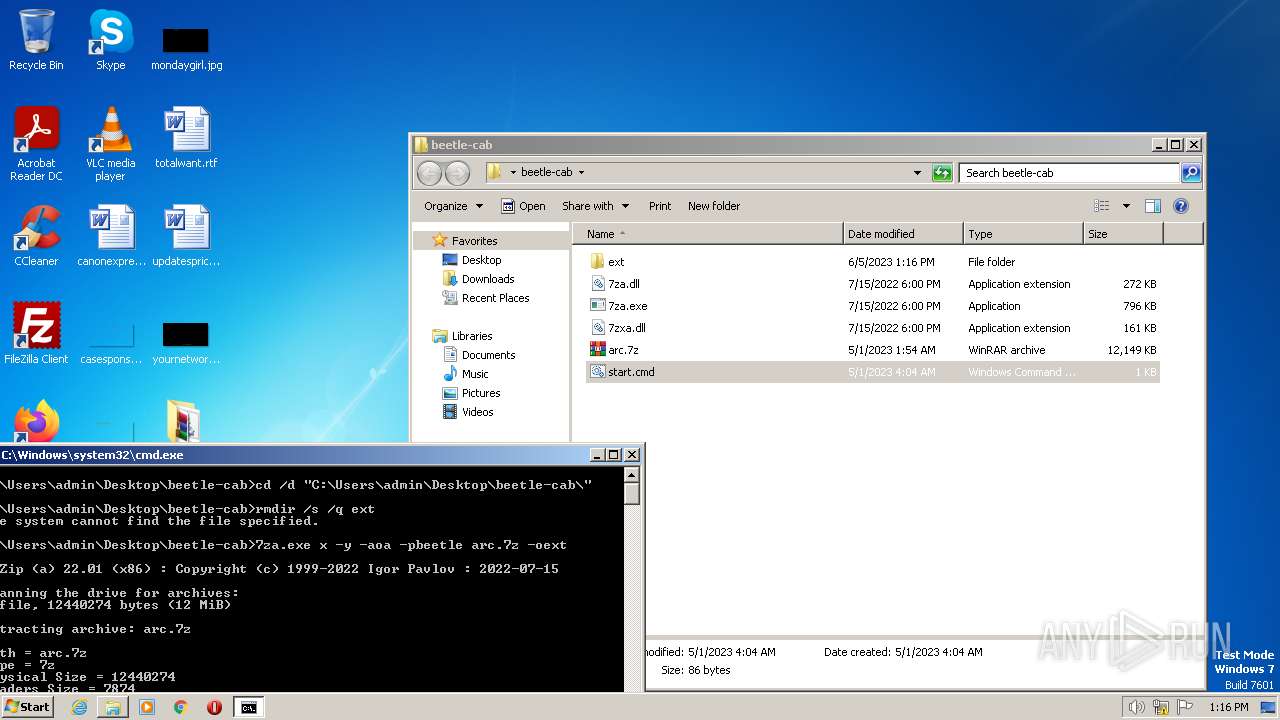
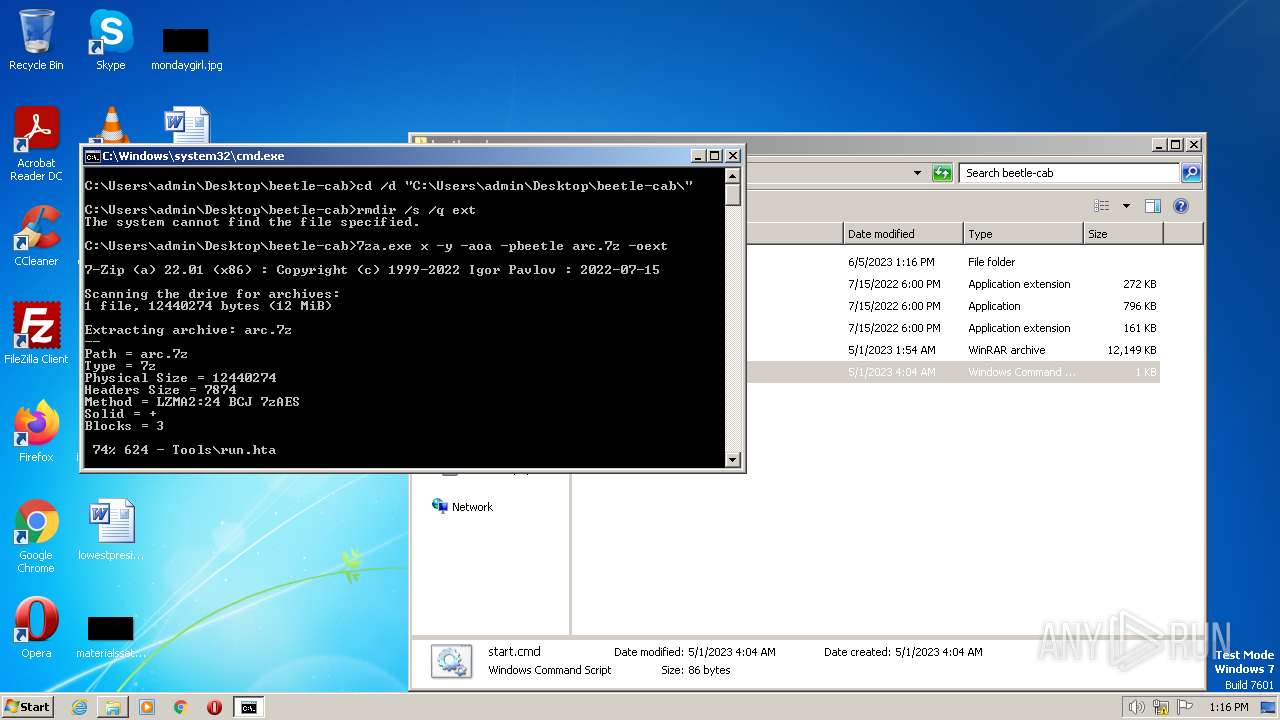
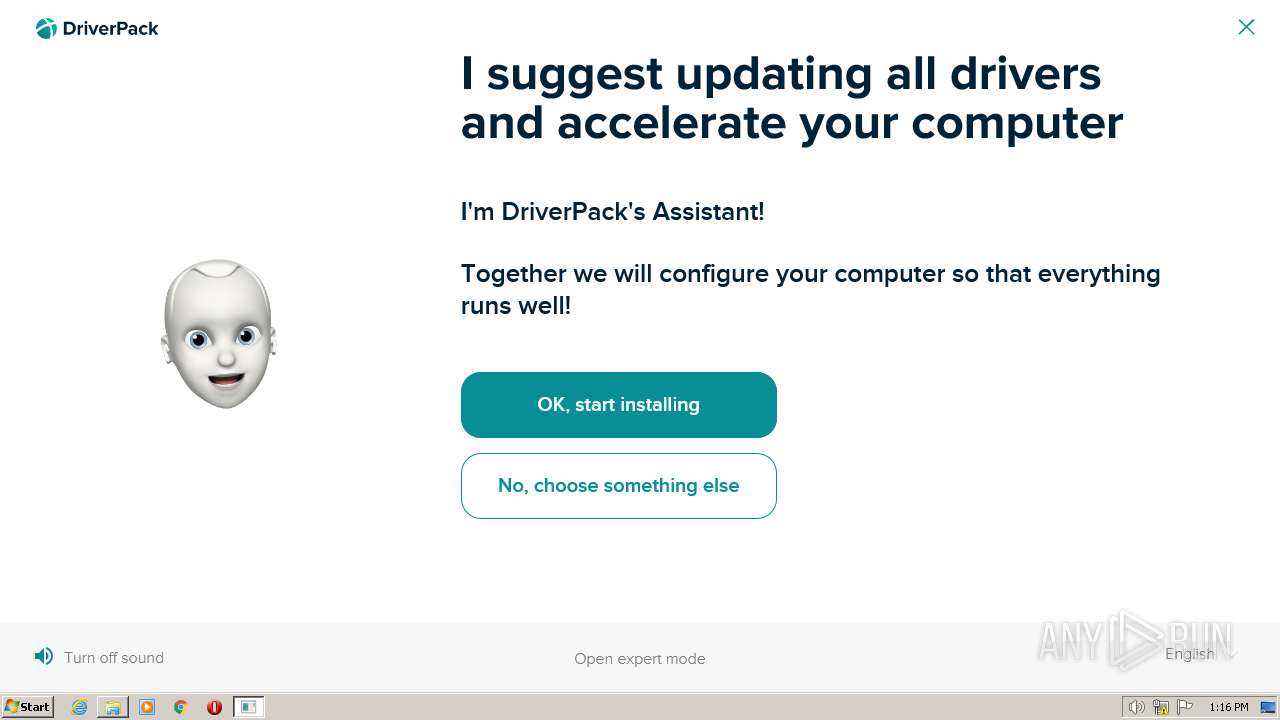
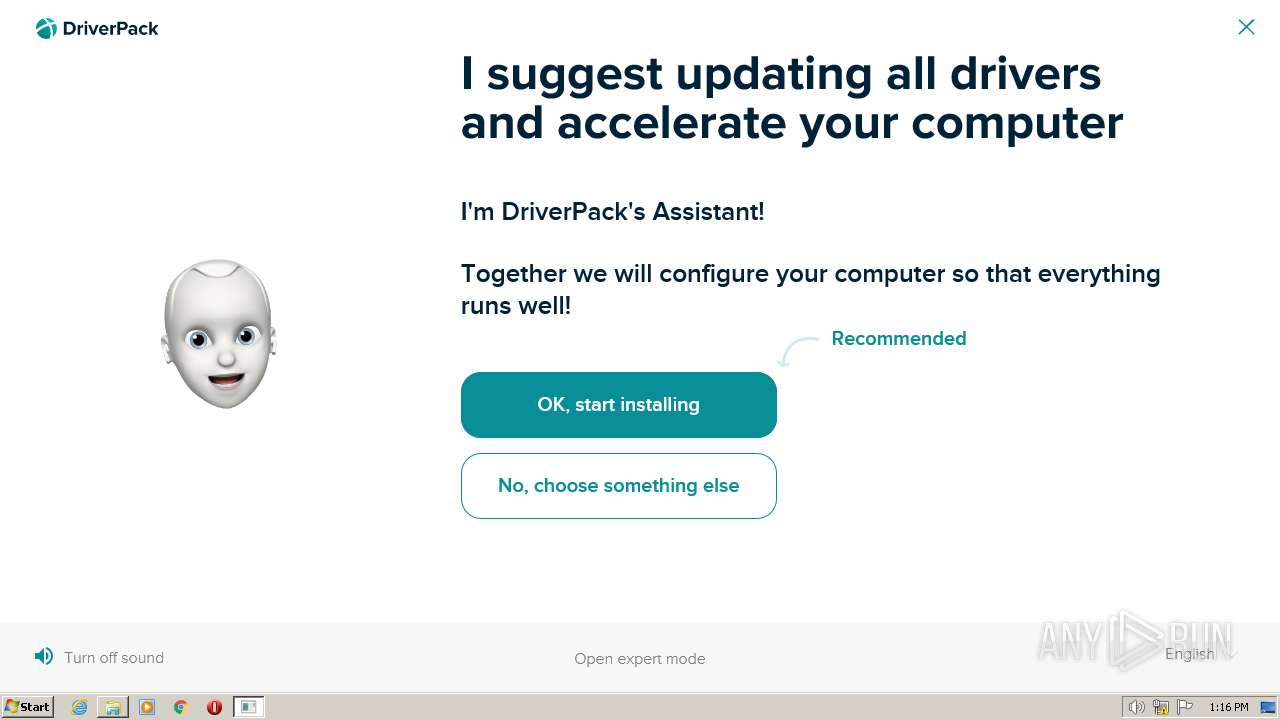
| download: | beetle-cab.cab |
| Full analysis: | https://app.any.run/tasks/d3ba9d95-bd81-4b5d-bb9f-cf3e939a788d |
| Verdict: | Malicious activity |
| Analysis date: | June 05, 2023, 12:15:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-cab-compressed |
| File info: | Microsoft Cabinet archive data, many, 13140694 bytes, 5 files, at 0x2c +A "beetle-cab\7za.dll" +A "beetle-cab\7za.exe", number 1, 419 datablocks, 0x1 compression |
| MD5: | 6179E6DCDD9D0C1223A7DC76FC350E37 |
| SHA1: | 856799DB415BA9EF398D489E29E093F132FDC0DF |
| SHA256: | B5A91D9C0614412D975E2E2CE82D5AAA3453ED467BF011FDD1C8AE765D6C8C1C |
| SSDEEP: | 196608:dBR6ZkXHrtQbiY7YO0jJsmraB6vexQnwJSvu+lOdLpFlh6ENP5gxIlO:3R6iXH2ipjJsmr/eSWKyjlJNPiilO |
MALICIOUS
Application was dropped or rewritten from another process
- 7za.exe (PID: 2848)
Bypass execution policy to execute commands
- powershell.exe (PID: 1832)
Starts Visual C# compiler
- powershell.exe (PID: 1832)
SUSPICIOUS
Get information on the list of running processes
- cmd.exe (PID: 1172)
Starts CMD.EXE for commands execution
- explorer.exe (PID: 1068)
- mshta.exe (PID: 4008)
Executing commands from ".cmd" file
- mshta.exe (PID: 4008)
- explorer.exe (PID: 1068)
Executable content was dropped or overwritten
- 7za.exe (PID: 3928)
- csc.exe (PID: 1816)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1172)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 1172)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 1172)
The process hides Powershell's copyright startup banner
- cmd.exe (PID: 1172)
Uses RUNDLL32.EXE to load library
- mshta.exe (PID: 4008)
The process hide an interactive prompt from the user
- cmd.exe (PID: 1172)
Uses .NET C# to load dll
- powershell.exe (PID: 1832)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- cmd.exe (PID: 3520)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 1044)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2044)
Checks supported languages
- 7za.exe (PID: 2848)
Manual execution by a user
- 7za.exe (PID: 2848)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .cab | | | Microsoft Cabinet Archive (100) |
|---|
Total processes
97
Monitored processes
41
Malicious processes
4
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 308 | "C:\Windows\System32\cmd.exe" /c ""tools\driverpack-wget.exe" --tries=3 --timeout 5 --retry-connrefused --wait=5 --timestamping --directory-prefix="C:\Users\admin\Desktop\beetle-cab\ext\audio\en" "http://dl.driverpack.io/assistant/beetle/audio/en/CONTINUOUS-2.mp3" -o "C:\Users\admin\AppData\Roaming\DRPSu\temp\wget_log_97372.log" & echo DONE > "C:\Users\admin\AppData\Roaming\DRPSu\temp\wget_finished_97372.txt"" | C:\Windows\System32\cmd.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | |||||||||||||||
| 1004 | "C:\Windows\System32\cmd.exe" /c ""tools\driverpack-wget.exe" --tries=3 --timeout 5 --retry-connrefused --wait=5 --timestamping --directory-prefix="C:\Users\admin\Desktop\beetle-cab\ext\audio\en" "http://dl.driverpack.io/assistant/beetle/audio/en/START-LOADED-1.mp3" -o "C:\Users\admin\AppData\Roaming\DRPSu\temp\wget_log_36939.log" & echo DONE > "C:\Users\admin\AppData\Roaming\DRPSu\temp\wget_finished_36939.txt"" | C:\Windows\System32\cmd.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | |||||||||||||||
| 1024 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES5F72.tmp" "c:\Users\admin\AppData\Local\Temp\CSCF7BF2EF756454B8F8DE059C1DE123D5.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 12.00.51209.34209 built by: FX452RTMGDR | |||||||||||||||
| 1044 | "C:\Windows\System32\cmd.exe" /c "netsh advfirewall firewall add rule name="DriverPack aria2c.exe" dir=in action=allow program="C:\Users\admin\Desktop\beetle-cab\ext\tools\aria2c.exe" || echo Done & call echo Done %^errorLevel% > "C:\Users\admin\AppData\Roaming\DRPSu\temp\run_command_34504.txt"" | C:\Windows\System32\cmd.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | |||||||||||||||
| 1068 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1172 | "C:\Windows\System32\cmd.exe" /C powershell -NonInteractive -NoLogo -NoProfile -ExecutionPolicy Bypass "Get-Content 'C:\Users\admin\AppData\Roaming\DRPSu\temp\ps.liitgkhh.47dm1.cmd.txt' -Wait | Invoke-Expression" > "C:\Users\admin\AppData\Roaming\DRPSu\temp\ps.liitgkhh.47dm1.stdout.log" 2> "C:\Users\admin\AppData\Roaming\DRPSu\temp\ps.liitgkhh.47dm1.stderr.log" | C:\Windows\System32\cmd.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | |||||||||||||||
| 1588 | "tools\driverpack-wget.exe" --tries=3 --timeout 5 --retry-connrefused --wait=5 --timestamping --directory-prefix="C:\Users\admin\Desktop\beetle-cab\ext\audio\en" "http://dl.driverpack.io/assistant/beetle/audio/en/TEAM-PROOF-3.mp3" -o "C:\Users\admin\AppData\Roaming\DRPSu\temp\wget_log_82313.log" | C:\Users\admin\Desktop\beetle-cab\ext\Tools\driverpack-wget.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 | |||||||||||||||
| 1812 | "C:\Windows\System32\cmd.exe" /c ""tools\driverpack-wget.exe" --tries=3 --timeout 5 --retry-connrefused --wait=5 --timestamping --directory-prefix="C:\Users\admin\Desktop\beetle-cab\ext\audio\en" "http://dl.driverpack.io/assistant/beetle/audio/en/EXPERT-DRIVERS-1.mp3" -o "C:\Users\admin\AppData\Roaming\DRPSu\temp\wget_log_43680.log" & echo DONE > "C:\Users\admin\AppData\Roaming\DRPSu\temp\wget_finished_43680.txt"" | C:\Windows\System32\cmd.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | |||||||||||||||
| 1816 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\4mvbqs1v.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.0.30319.34209 built by: FX452RTMGDR | |||||||||||||||
| 1832 | powershell -NonInteractive -NoLogo -NoProfile -ExecutionPolicy Bypass "Get-Content 'C:\Users\admin\AppData\Roaming\DRPSu\temp\ps.liitgkhh.47dm1.cmd.txt' -Wait | Invoke-Expression" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) | |||||||||||||||
Total events
2 868
Read events
2 815
Write events
53
Delete events
0
Modification events
| (PID) Process: | (1068) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB010000003D77C3133A5D7248BA6D7744BB9A3E16000000000200000000001066000000010000200000004A9CAAC251DD88A0E7E33FFB23F636A225CB7CC4485369C7C9B03862A811D096000000000E8000000002000020000000659B7585C71088AEEB1875008044DFB4B07623A0B20C3E867A78A9695191E29230000000F9C4E47AAD7D214C673E4CDC8385C59DDC5AE0E28396FCF21F9D028C590E79749BDDC16862F8E26B3D4F8E8966EEF17C4000000006EE6EDF8BC2D3544F7C9D682CF07277A50A34FA9DF6D8FB7B39CA5834F62523E20C12EF252EC87A75BE0FA4A5D7BD80B713248892E659363C3419474A1FEA18 | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1068) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | {7P5N40RS-N0SO-4OSP-874N-P0S2R0O9SN8R}\JvaENE\JvaENE.rkr |
Value: 000000000700000005000000408A0000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFFA0B93321CCFAD80100000000 | |||
Executable files
9
Suspicious files
133
Text files
517
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2044 | WinRAR.exe | C:\Users\admin\Desktop\beetle-cab\arc.7z | — | |
MD5:— | SHA256:— | |||
| 2044 | WinRAR.exe | C:\Users\admin\Desktop\beetle-cab\7za.exe | executable | |
MD5:90AAC6489F6B226BF7DC1ADABFDB1259 | SHA256:BA7F3627715614D113C1E1CD7DD9D47E3402A1E8A7404043E08BC14939364549 | |||
| 2044 | WinRAR.exe | C:\Users\admin\Desktop\beetle-cab\7za.dll | executable | |
MD5:B54E2DCD1A3D593CA0AE4CB71910710E | SHA256:D7F1224CC4AFB90AF3792DADFDF2F14BAD4A19329EE0F3C87C111611AA36B7B1 | |||
| 2044 | WinRAR.exe | C:\Users\admin\Desktop\beetle-cab\start.cmd | text | |
MD5:232EBF167EA35163EA69A1570BE7B03E | SHA256:030EE398E53CAF0928E757162F3C7BE7D593A59DDE2795991EC7E4FD8E71F2E3 | |||
| 3928 | 7za.exe | C:\Users\admin\Desktop\beetle-cab\ext\audio\ru\CHECKING-2.mp3 | binary | |
MD5:E6F82457DF1D0918E9EC2D62588DD012 | SHA256:B0BF4F6D33CAB5B44C117258A85A2D490BAFB8E9E07BF8C3EAEB1E5B5E9B29AE | |||
| 3928 | 7za.exe | C:\Users\admin\Desktop\beetle-cab\ext\audio\ru\ANTIVIRUS-3.mp3 | binary | |
MD5:4FC18A9B71EBC68921ED074E31D9270E | SHA256:772899FCBDD6CE22770DFE71E1C3351F61C8CCDB1D143D54CD603B2CCF751B1B | |||
| 3928 | 7za.exe | C:\Users\admin\Desktop\beetle-cab\ext\audio\ru\CHECKING-1.mp3 | binary | |
MD5:9AAB5F195CD31E373FADF4D6805695F2 | SHA256:CC0046FDD1961C7591898D075198429A986B5D61B825AAF07A77B932F5414866 | |||
| 2044 | WinRAR.exe | C:\Users\admin\Desktop\beetle-cab\7zxa.dll | executable | |
MD5:72DCC77BA25EBC4984D959A78C8646D5 | SHA256:6B4888207C46C23D2D4E4EACE8A2DB01711692BC7D4BB93F3750BC41E91BB73C | |||
| 3928 | 7za.exe | C:\Users\admin\Desktop\beetle-cab\ext\audio\ru\COMPILATION-2.mp3 | binary | |
MD5:E4360CB22B1B602A1BECF017C4D6B220 | SHA256:9C1C807DC3D200B1639E4DCECDE44B3C181F4A18ABA6797924FF34D209F62FDF | |||
| 3928 | 7za.exe | C:\Users\admin\Desktop\beetle-cab\ext\audio\ru\ANTIVIRUS-2.mp3 | binary | |
MD5:31ECE55FDDC2A8321AA5C3F9DB6C988A | SHA256:E45CB0E8E3EA147CA3503A369442AAA1B7E8B7A699E9C175089F8208D8CB6649 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
89
TCP/UDP connections
21
DNS requests
14
Threats
53
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 301 | 188.114.97.3:80 | http://allfont.ru/allfont.css?fonts=lucida-console | US | — | — | whitelisted |
— | — | HEAD | 200 | 81.94.192.167:80 | http://dl.driverpack.io/updates/beetle/driverpack-wget.exe | GB | — | — | malicious |
— | — | GET | 301 | 188.114.97.3:80 | http://allfont.ru/cache/css/lucida-console.css | US | — | — | whitelisted |
— | — | GET | 200 | 8.238.41.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?3182043e2236e210 | US | compressed | 4.70 Kb | whitelisted |
— | — | POST | 202 | 37.9.8.75:80 | http://update.drp.su/api/logs | RU | — | — | malicious |
— | — | POST | 202 | 37.9.8.75:80 | http://update.drp.su/api/logs | RU | compressed | 141 b | malicious |
— | — | POST | 202 | 37.9.8.75:80 | http://update.drp.su/api/logs | RU | compressed | 141 b | malicious |
— | — | GET | 200 | 172.217.16.206:80 | http://www.google-analytics.com/collect?v=1&ds=hta&tid=UA-69093127-16&cid=377950222.7104647400&t=event&ec=driverpack%20online&ea=new%20ui%20experiment%20detected%20enabled&el=17.11.108%20online&ul=&z=506967174557434&cd1=377950222.7104647400&cd2=17.11.108%20Online&cd3=7%20x86&cd4=SP%201&cd5=Windows%207%20Professional%20&cd6=(not%20set) | US | image | 35 b | whitelisted |
— | — | GET | 200 | 172.217.16.206:80 | http://www.google-analytics.com/collect?v=1&ds=hta&tid=UA-69093127-16&cid=377950222.7104647400&t=event&ec=driverpack%20online&ea=application%20opened&el=17.11.108%20online&ul=&z=01204325465532674&cd1=377950222.7104647400&cd2=17.11.108%20Online&cd3=7%20x86&cd4=SP%201&cd5=Windows%207%20Professional%20&cd6=(not%20set) | US | image | 35 b | whitelisted |
— | — | GET | 200 | 172.217.16.206:80 | http://www.google-analytics.com/collect?v=1&ds=hta&tid=UA-68879973-26&cid=377950222.7104647400&t=event&ec=driverpack%20online&ea=new%20ui%20experiment%20detected%20enabled&el=17.11.108%20online&ul=&z=48924390470428663&cd1=377950222.7104647400&cd2=17.11.108%20Online&cd3=7%20x86&cd4=SP%201&cd5=Windows%207%20Professional%20&cd6=(not%20set) | US | image | 35 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 188.114.97.3:443 | allfont.ru | CLOUDFLARENET | NL | malicious |
— | — | 188.114.97.3:80 | allfont.ru | CLOUDFLARENET | NL | malicious |
— | — | 142.250.186.163:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
— | — | 87.117.235.115:80 | auth.drp.su | Iomart Cloud Services Limited | GB | suspicious |
— | — | 37.9.8.75:80 | update.drp.su | OOO Network of data-centers Selectel | RU | malicious |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 81.94.192.167:80 | dl.driverpack.io | Iomart Cloud Services Limited | GB | malicious |
— | — | 8.238.41.126:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
— | — | 93.158.134.119:443 | mc.yandex.ru | YANDEX LLC | RU | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
allfont.ru |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
auth.drp.su |
| suspicious |
mc.yandex.ru |
| whitelisted |
update.drp.su |
| malicious |
www.google-analytics.com |
| whitelisted |
dl.driverpack.io |
| malicious |
ocsp.globalsign.com |
| whitelisted |
ocsp2.globalsign.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
— | — | Possibly Unwanted Program Detected | ET ADWARE_PUP DriverPack Domain in DNS Query |
— | — | Possibly Unwanted Program Detected | ET ADWARE_PUP Observed DNS Query to DriverPack Domain ( .drp .su) |
— | — | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
— | — | Possibly Unwanted Program Detected | ET ADWARE_PUP DriverPack Domain in DNS Query |
— | — | Possibly Unwanted Program Detected | ET ADWARE_PUP Observed DNS Query to DriverPack Domain ( .drp .su) |
— | — | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
— | — | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
— | — | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
— | — | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |