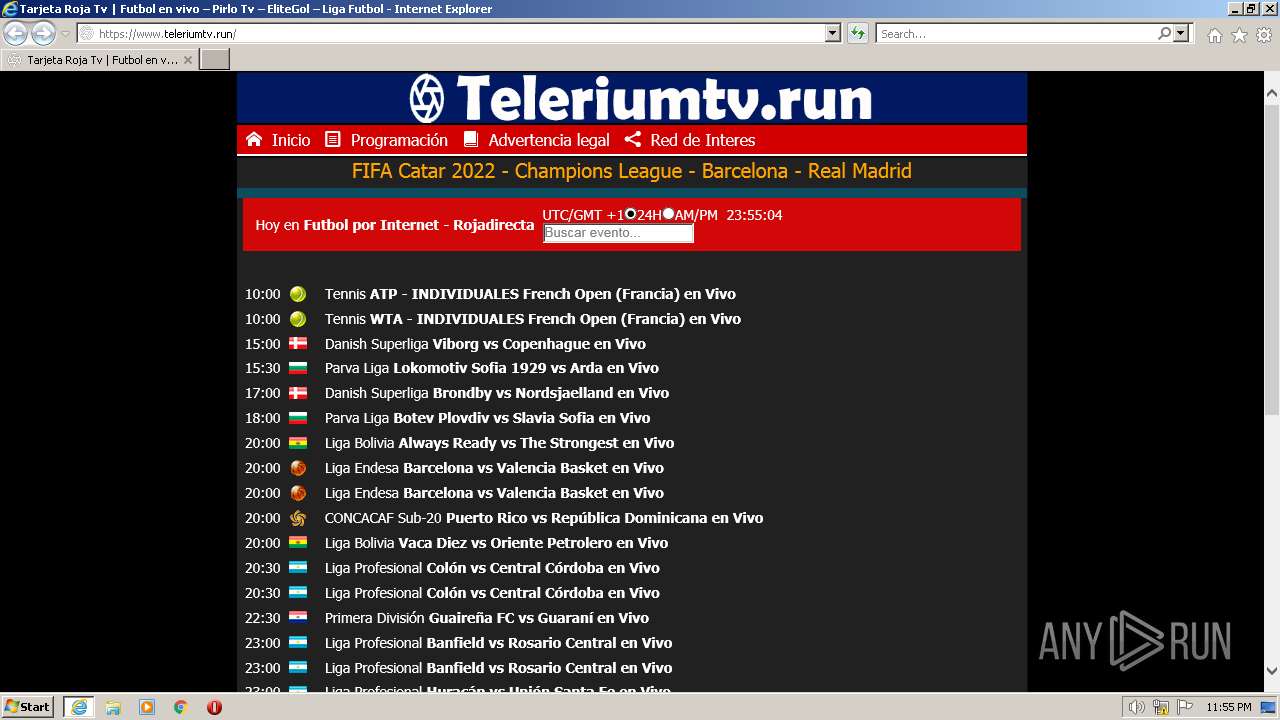
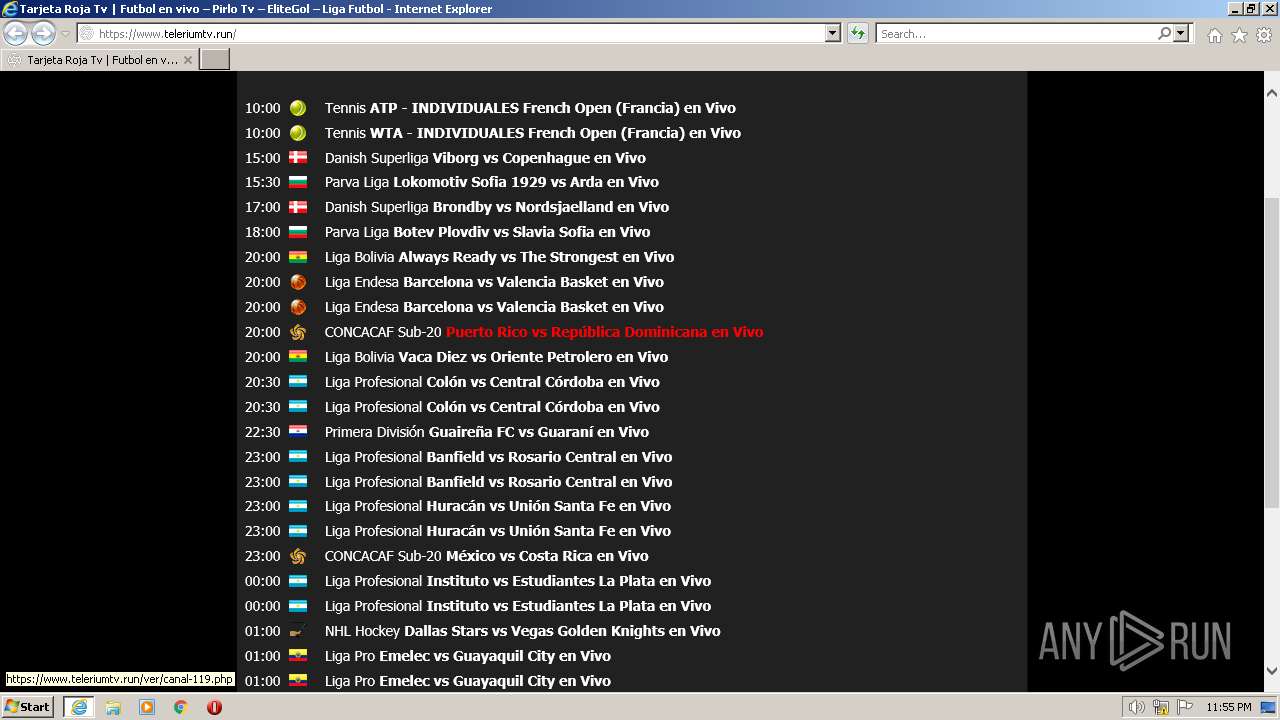
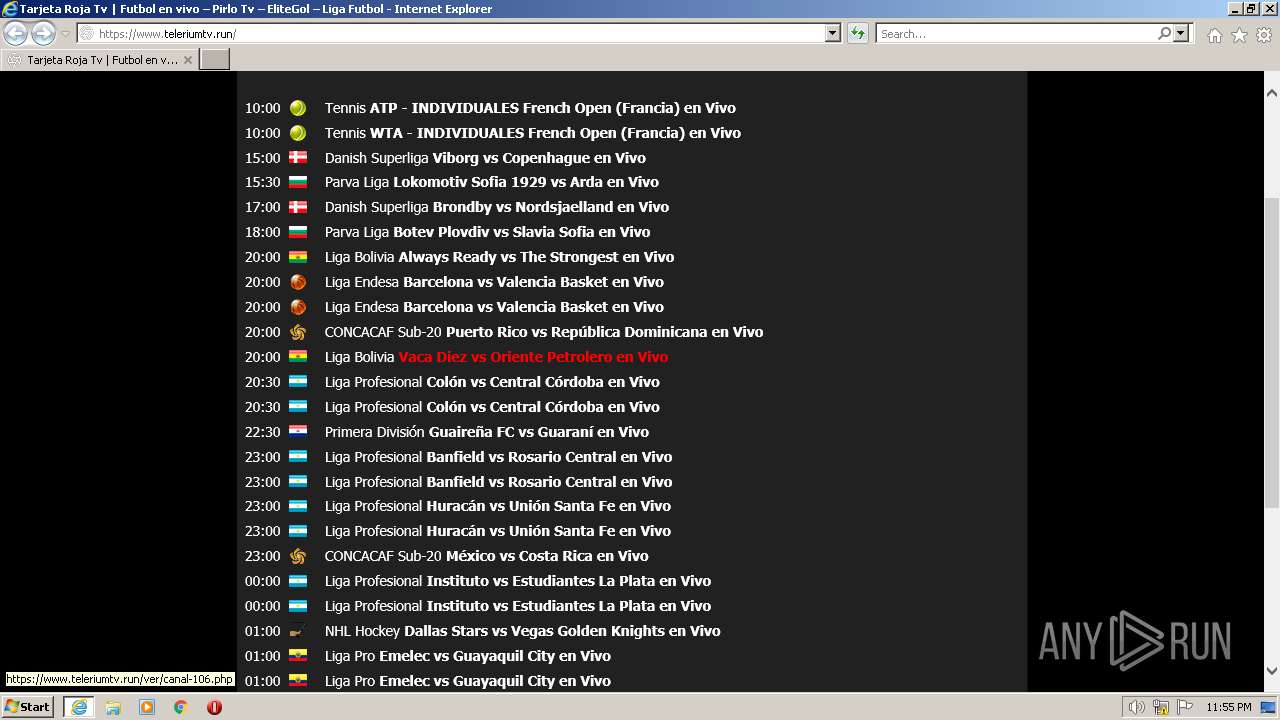
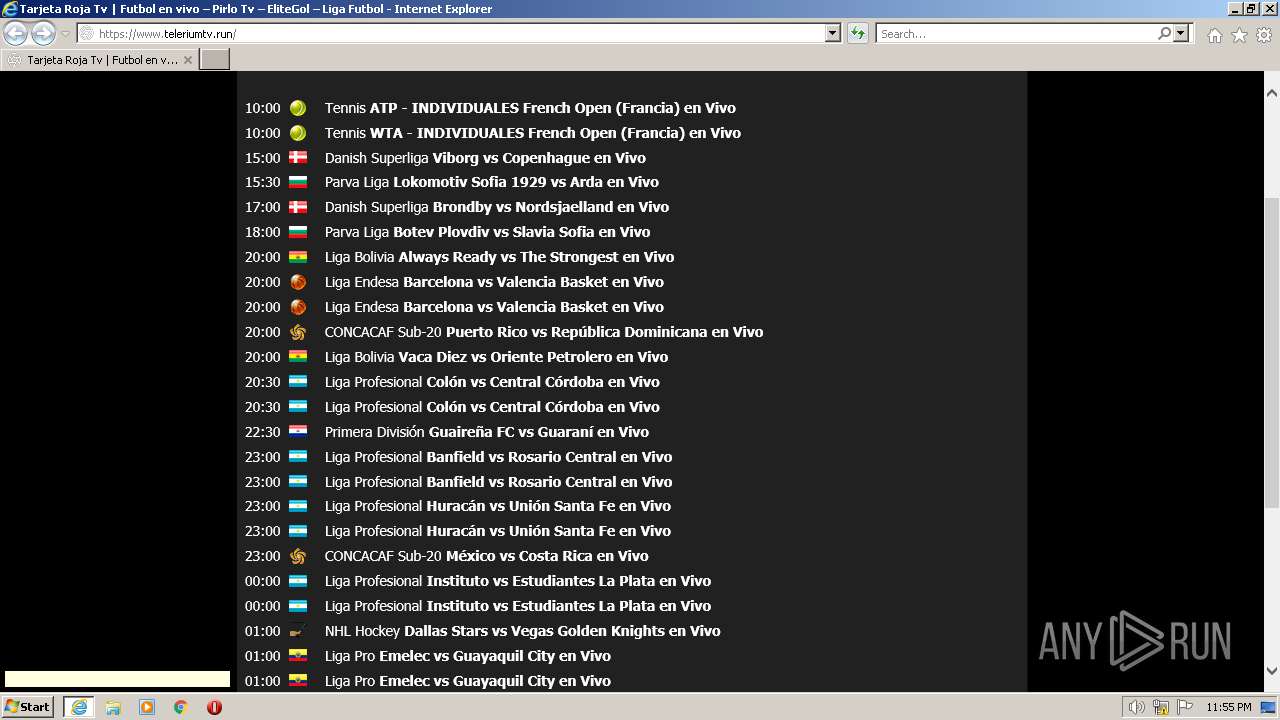
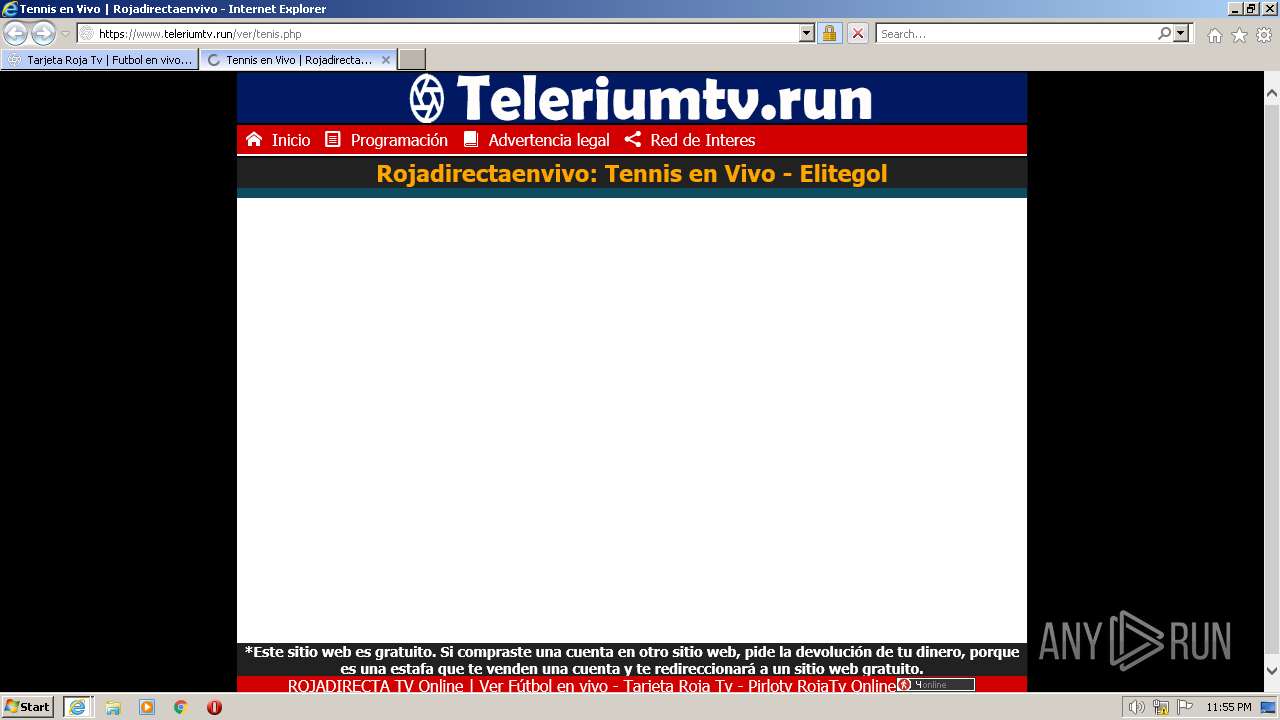
| URL: | https://www.teleriumtv.run |
| Full analysis: | https://app.any.run/tasks/1770ed50-3f92-49fc-a545-d32b43d71d18 |
| Verdict: | Malicious activity |
| Analysis date: | May 29, 2023, 22:54:52 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 11937F803667831BEA5CB37738753717 |
| SHA1: | 19B174BDBFE893948A5B807110594B536E412579 |
| SHA256: | B5A1D91A0E17CE210218498FBBD30C732126E56EBA21FCEE9A980B12D60BD466 |
| SSDEEP: | 3:N8DSLEe:2OLEe |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 748)
Create files in a temporary directory
- iexplore.exe (PID: 748)
- iexplore.exe (PID: 3464)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
40
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 748 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.teleriumtv.run" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1848 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:748 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3464 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:748 CREDAT:595209 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
28 836
Read events
28 698
Write events
136
Delete events
2
Modification events
| (PID) Process: | (748) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (748) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (748) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (748) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (748) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (748) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (748) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (748) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (748) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (748) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
52
Text files
50
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1848 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:CFBC16E33DCBEF6F773F0F79AF528F45 | SHA256:F0937890FB1053069BAAC97B7992C6D22CB74CAE20317FC05D51070D96950FFA | |||
| 1848 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\fonts[1].css | text | |
MD5:AA16CCDE7DF129C669AA5A20F9446A76 | SHA256:E72FEA94C6A3490CF088E45B6E2D3E578E29AB417E1F592E53F22D46ECAA5F9C | |||
| 1848 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\teleriumtvrun[1].png | image | |
MD5:4148C2A92E47626EAD631727611D2200 | SHA256:EF2161CCE24713401FF8E546E761292A7096CFB49200EA2771A1FBD7F8E2EEAB | |||
| 1848 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 1848 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:4B6F061B7B18371F56689E9A27606B9C | SHA256:1B9D0BAFA1779FF0DB1DC517AFA574D26B332A6083F7A875F25FB77F2705D1A3 | |||
| 1848 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:0B43CDB46AF0BF4A4BCE830A2F2CD59C | SHA256:170A040FACF35F72732E3FB8A9EF4695064A866DAB1A33139C32D7D1D3A3ABC3 | |||
| 1848 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:D92DDF4DFB1050568CB33385D78F0825 | SHA256:6493C0A8E836A83A290B0C917830894B57E6A5274767377C52F2BDB095E52023 | |||
| 1848 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\265C0DEB29181DD1891051371C5F863A_5F062E97657E16CB07F77F3A67E74B7A | binary | |
MD5:B2EB4D042105518EFDC5FAC61E9788DB | SHA256:6175AD4BADA00420C6ACCDBC977A9AB144E0B3DB8A3D39E5B0700E771FAA5A4D | |||
| 1848 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:0DE5553E9827815659002DB71DAADBA3 | SHA256:E7EE0D4FB41F5F483E55F53E97817CCB66BC54031B658094EF4B1B1EF9BD00AD | |||
| 1848 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\KIAPZ775.htm | html | |
MD5:B29C163C367D382603035C0AAE175B2A | SHA256:392AC7D3CB58DDA09D64F91DD8A6AC8B394A61C542C99669AB7D9AAB140E0F25 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
32
TCP/UDP connections
115
DNS requests
42
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3464 | iexplore.exe | GET | — | 95.140.236.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?9b04043c556bd24b | GB | — | — | whitelisted |
3464 | iexplore.exe | GET | — | 95.140.236.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?0f7b1915c0517858 | GB | — | — | whitelisted |
3464 | iexplore.exe | GET | — | 95.140.236.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?5f1d47b70b5b3e70 | GB | — | — | whitelisted |
3464 | iexplore.exe | GET | — | 95.140.236.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?2042151d4164be3f | GB | — | — | whitelisted |
3464 | iexplore.exe | GET | — | 52.222.250.42:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEjgLnWaIozse2b%2BczaaODg8%3D | US | — | — | shared |
— | — | GET | — | 95.140.236.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?93320e02d964f4e3 | GB | — | — | whitelisted |
1848 | iexplore.exe | GET | 200 | 104.18.14.101:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 2.18 Kb | whitelisted |
1848 | iexplore.exe | GET | 200 | 104.18.15.101:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | der | 1.42 Kb | whitelisted |
1848 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCf4d%2FNemnDwxJHGtU61rL9 | US | der | 472 b | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | binary | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1848 | iexplore.exe | 142.250.186.131:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
1848 | iexplore.exe | 142.250.185.138:443 | ajax.googleapis.com | GOOGLE | US | whitelisted |
1848 | iexplore.exe | 104.26.5.7:443 | waust.at | CLOUDFLARENET | US | suspicious |
1848 | iexplore.exe | 13.32.99.34:443 | platform-api.sharethis.com | AMAZON-02 | US | suspicious |
748 | iexplore.exe | 184.86.251.27:443 | www.bing.com | Akamai International B.V. | DE | suspicious |
1848 | iexplore.exe | 104.18.15.101:80 | ocsp.comodoca.com | CLOUDFLARENET | — | whitelisted |
1848 | iexplore.exe | 104.18.14.101:80 | ocsp.comodoca.com | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
waust.at |
| malicious |
code.jquery.com |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
ajax.googleapis.com |
| whitelisted |
platform-api.sharethis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1076 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .icu Domain |
3464 | iexplore.exe | Potentially Bad Traffic | ET INFO Suspicious Domain (*.icu) in TLS SNI |