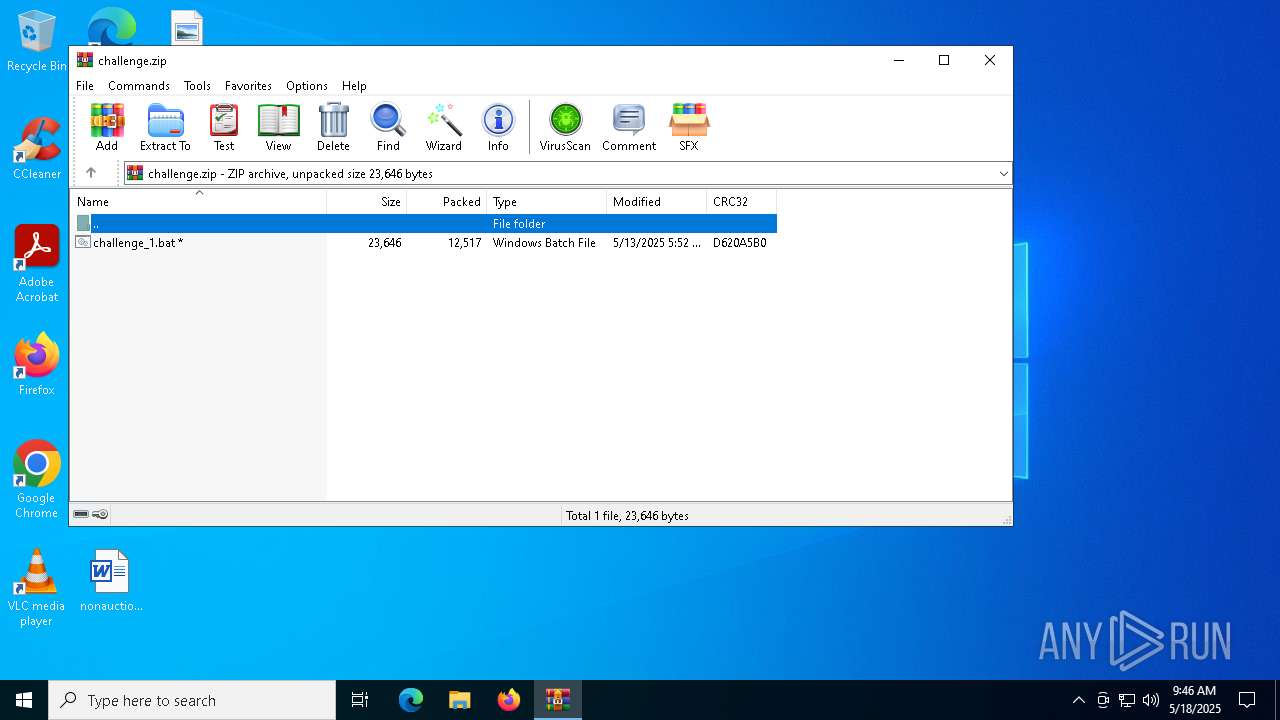
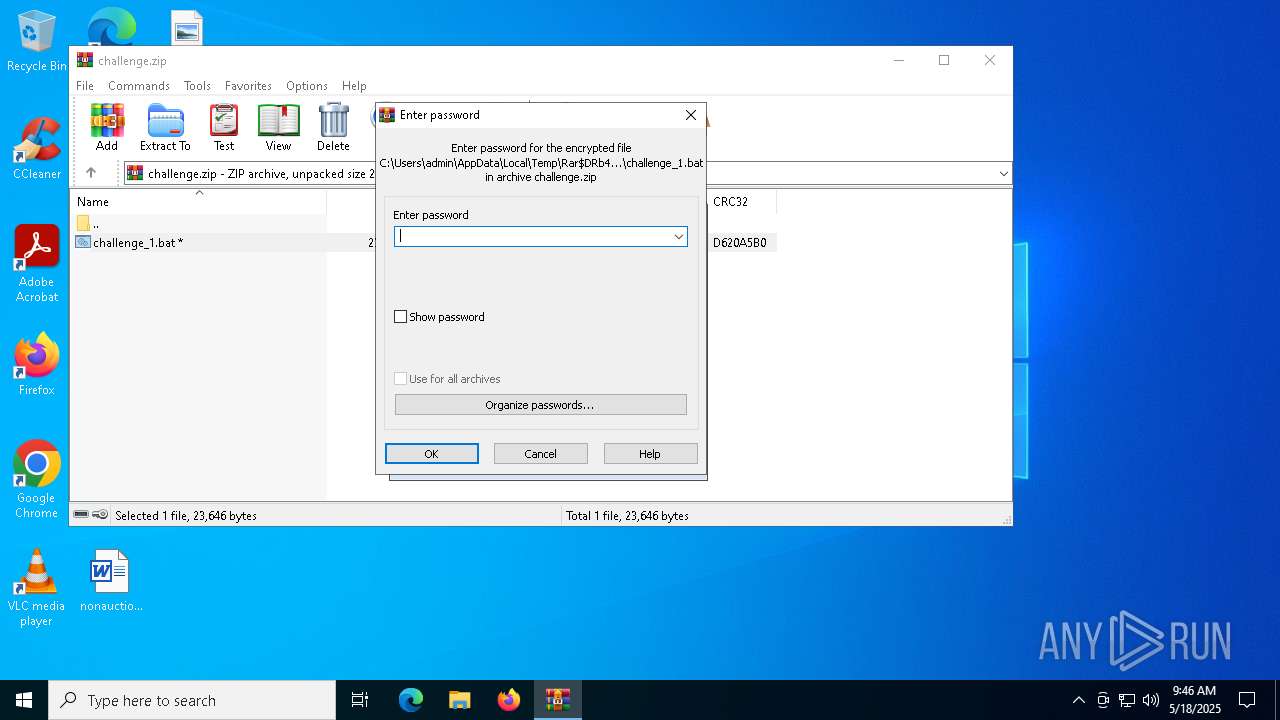
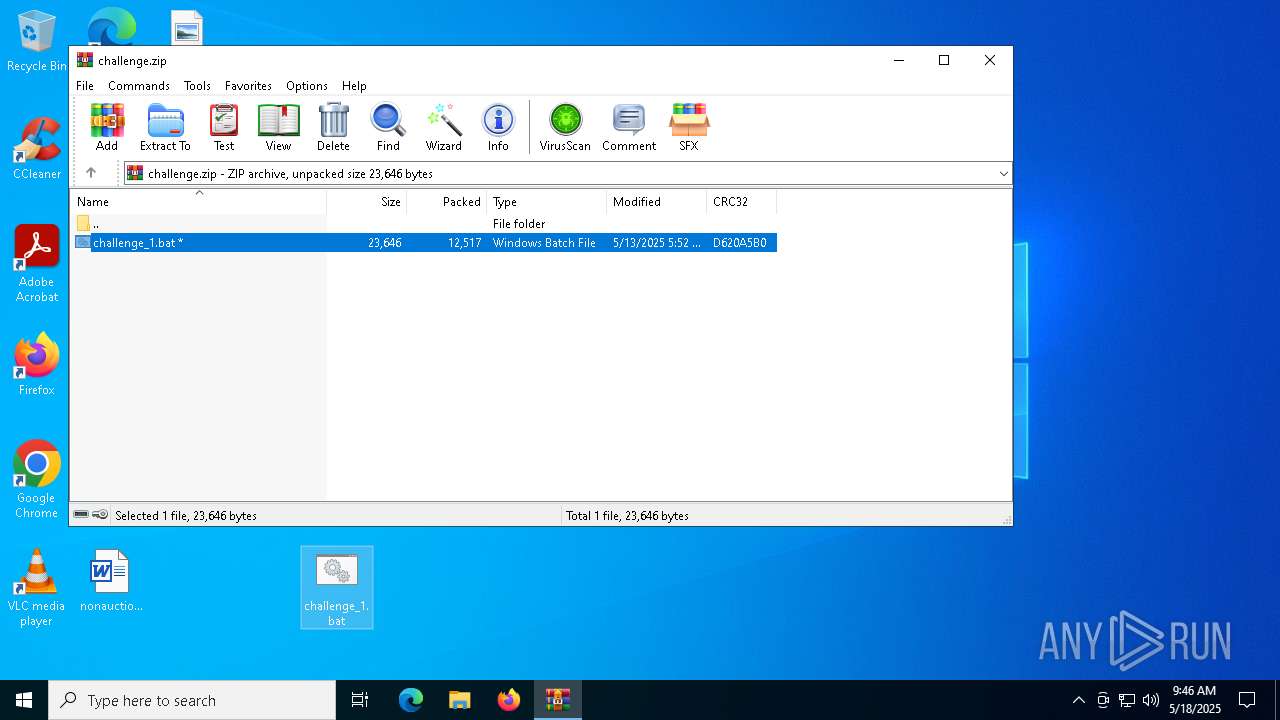
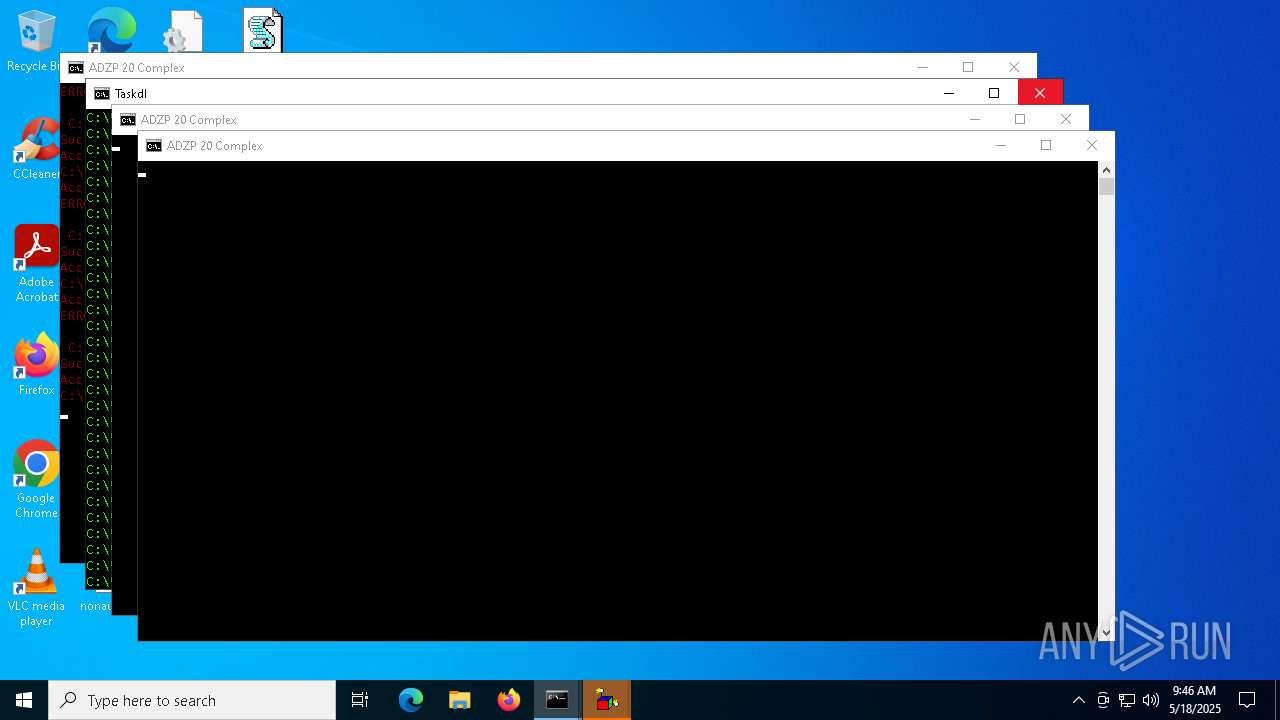
| File name: | challenge.zip |
| Full analysis: | https://app.any.run/tasks/94c59a0d-dee8-4117-b997-4fa26dc619ca |
| Verdict: | Malicious activity |
| Analysis date: | May 18, 2025, 09:46:03 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 52F9551DECA942A8A88ED0A619684FAA |
| SHA1: | 4ADB581F7D20B0A51F09AF6E966495BA9BF35E86 |
| SHA256: | B58E493A5E7780611A2A3337448F57EE21A6AF0EA6722674DC80D80F06235275 |
| SSDEEP: | 384:U7g5i/kW5kN4v3P4741m54OmajzzXvcv72:/W+qvf474U54cnXvX |
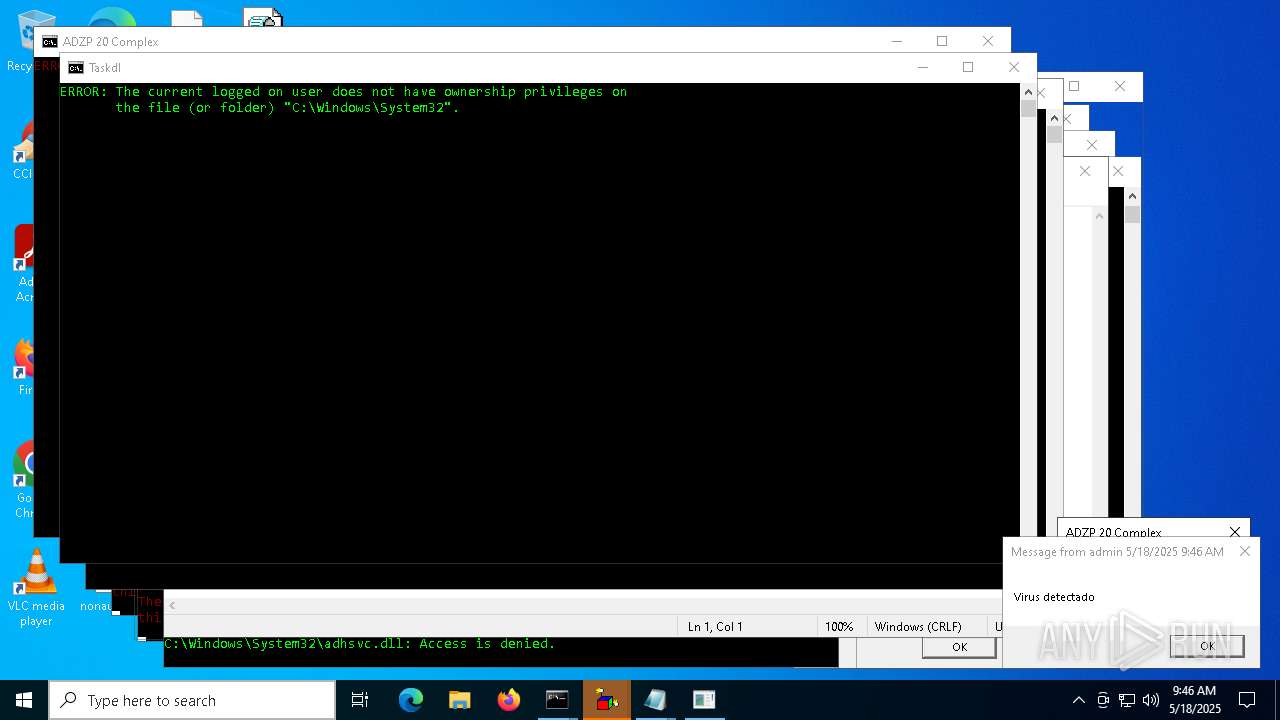
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 4880)
Create files in the Startup directory
- cmd.exe (PID: 7668)
Changes the autorun value in the registry
- reg.exe (PID: 1760)
- reg.exe (PID: 3332)
- reg.exe (PID: 8904)
- reg.exe (PID: 8440)
SONIC has been detected
- cmd.exe (PID: 7668)
- cmd.exe (PID: 5008)
- cmd.exe (PID: 7632)
SUSPICIOUS
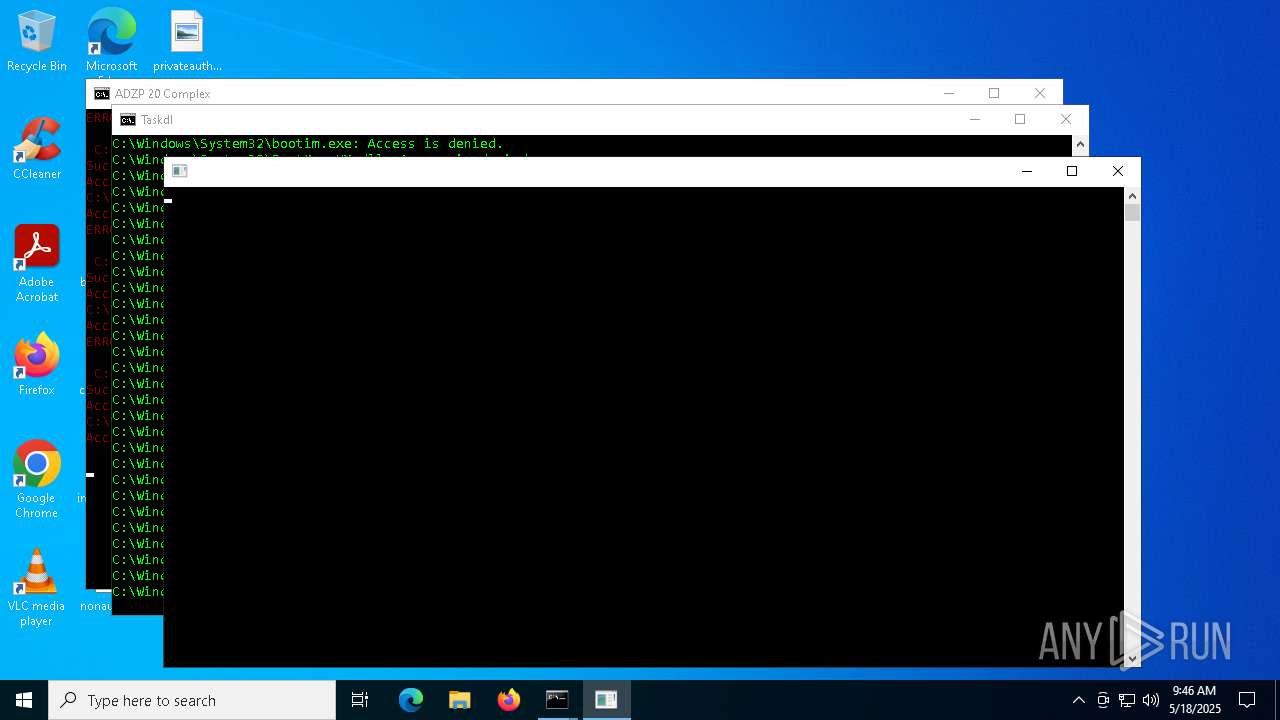
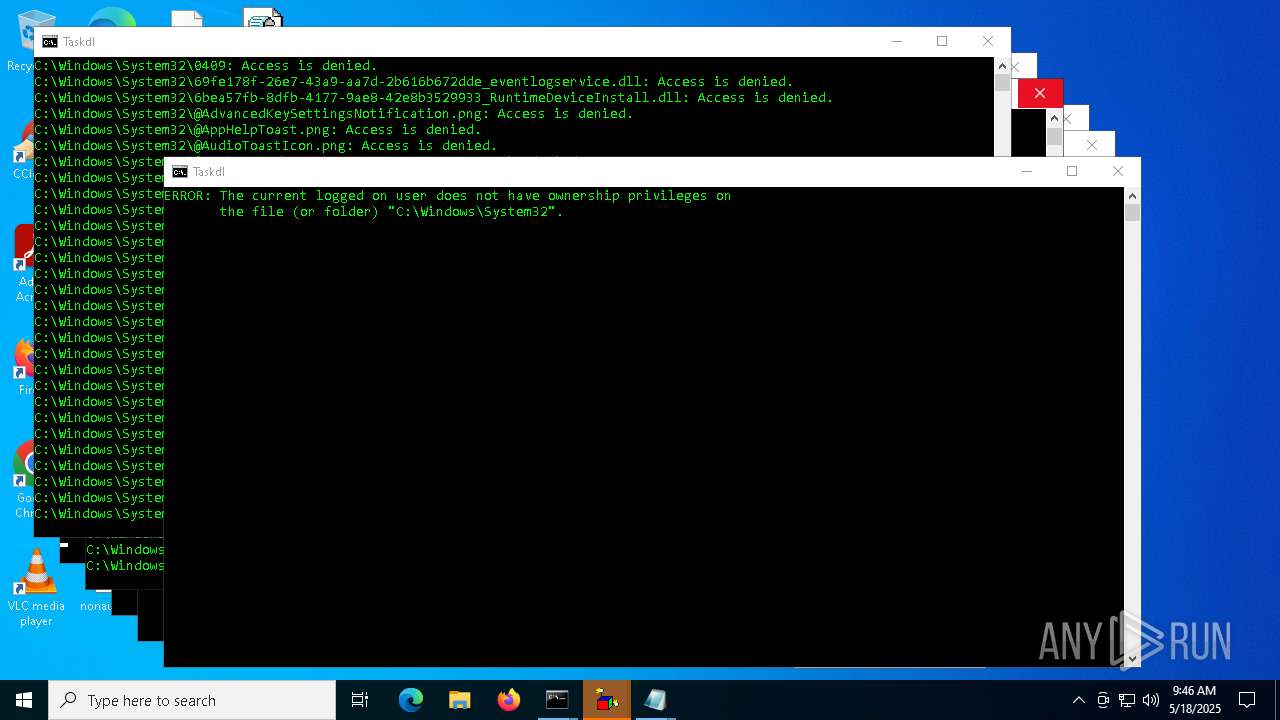
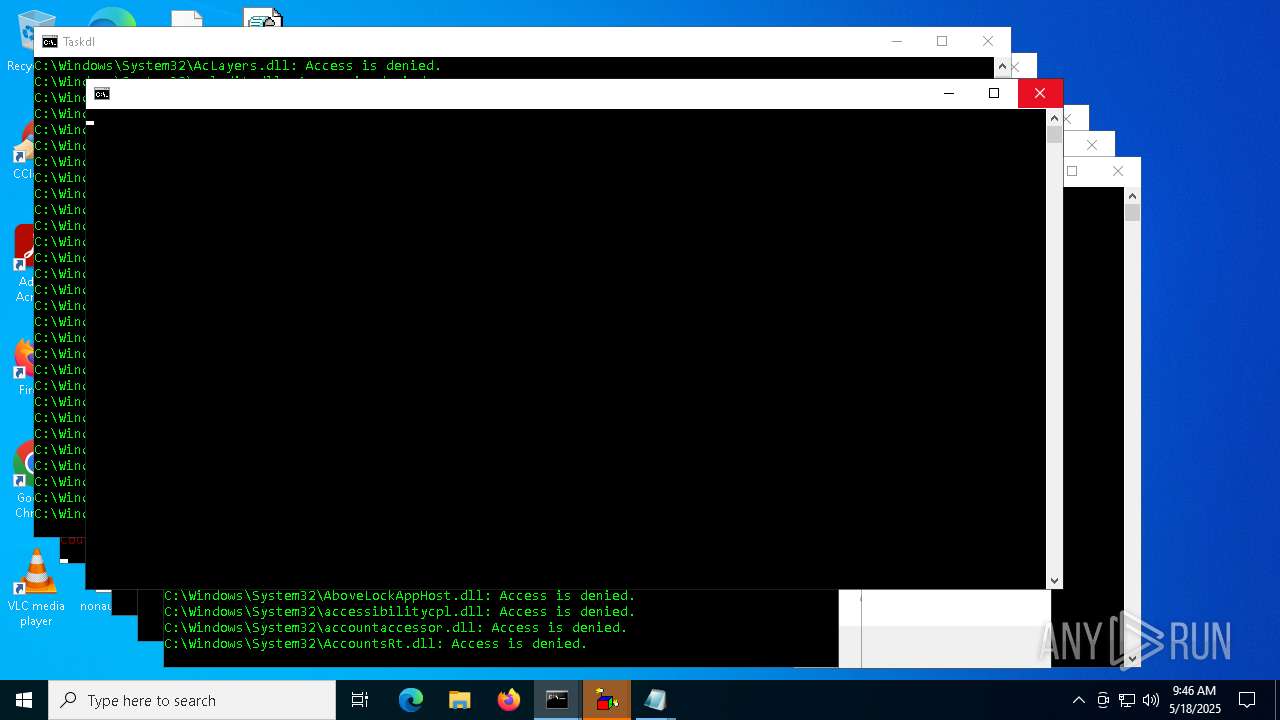
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 7728)
- cmd.exe (PID: 7668)
- cmd.exe (PID: 5008)
- cmd.exe (PID: 5376)
- cmd.exe (PID: 7592)
- cmd.exe (PID: 7552)
- cmd.exe (PID: 7632)
- cmd.exe (PID: 5548)
- cmd.exe (PID: 9148)
- cmd.exe (PID: 8496)
- cmd.exe (PID: 8876)
- cmd.exe (PID: 6572)
- cmd.exe (PID: 8708)
- cmd.exe (PID: 8464)
- cmd.exe (PID: 10256)
- cmd.exe (PID: 9640)
- cmd.exe (PID: 10108)
- cmd.exe (PID: 10348)
- cmd.exe (PID: 10872)
- cmd.exe (PID: 12544)
- cmd.exe (PID: 9612)
- cmd.exe (PID: 10668)
- cmd.exe (PID: 10580)
- cmd.exe (PID: 8472)
- cmd.exe (PID: 8312)
- cmd.exe (PID: 12760)
- cmd.exe (PID: 13068)
- cmd.exe (PID: 12868)
- cmd.exe (PID: 12600)
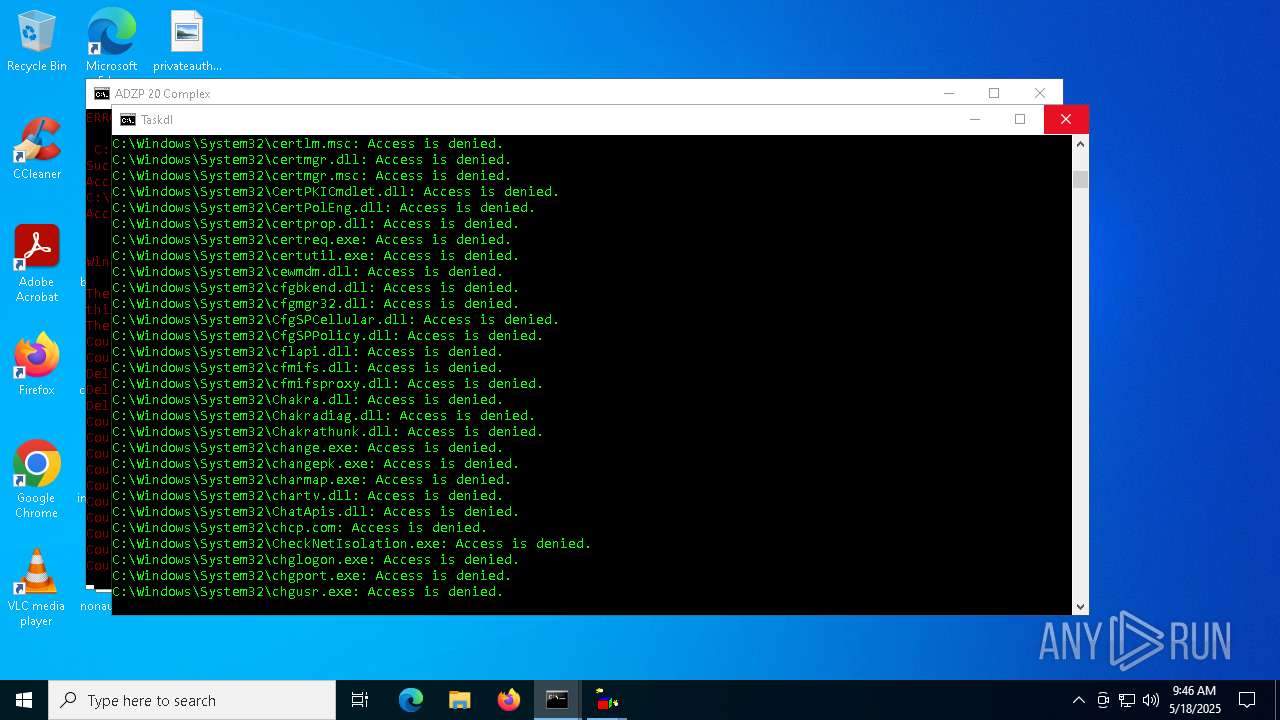
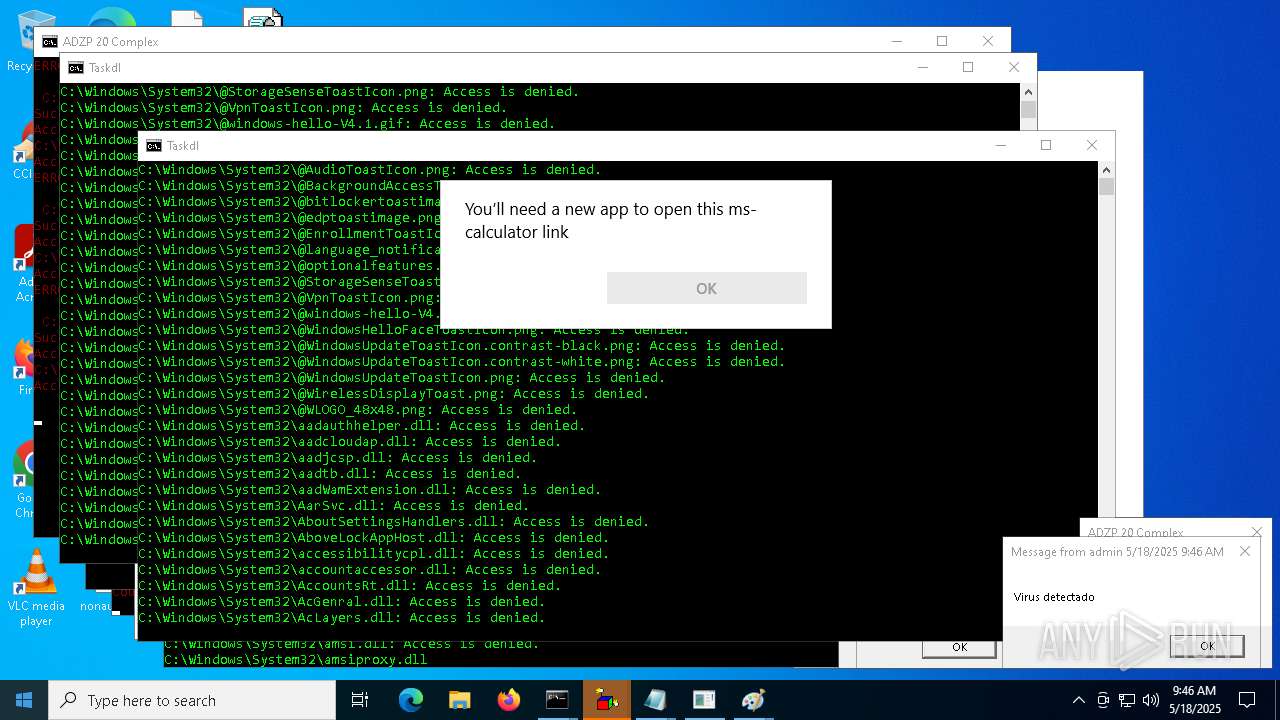
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 7728)
- cmd.exe (PID: 7668)
- cmd.exe (PID: 5376)
- cmd.exe (PID: 5008)
- cmd.exe (PID: 7632)
- cmd.exe (PID: 7592)
- cmd.exe (PID: 7552)
- cmd.exe (PID: 5548)
- cmd.exe (PID: 6572)
- cmd.exe (PID: 8464)
- cmd.exe (PID: 9148)
- cmd.exe (PID: 8708)
- cmd.exe (PID: 8496)
- cmd.exe (PID: 8876)
- cmd.exe (PID: 10348)
- cmd.exe (PID: 9640)
- cmd.exe (PID: 10668)
- cmd.exe (PID: 10580)
- cmd.exe (PID: 10108)
- cmd.exe (PID: 12544)
- cmd.exe (PID: 12600)
- cmd.exe (PID: 10256)
- cmd.exe (PID: 8472)
- cmd.exe (PID: 10872)
- cmd.exe (PID: 9612)
- cmd.exe (PID: 8312)
- cmd.exe (PID: 13068)
- cmd.exe (PID: 12868)
- cmd.exe (PID: 12760)
Decoding a file from Base64 using CertUtil
- cmd.exe (PID: 7668)
Executable content was dropped or overwritten
- certutil.exe (PID: 8032)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 7668)
- cmd.exe (PID: 5008)
- cmd.exe (PID: 7592)
- cmd.exe (PID: 7632)
- cmd.exe (PID: 6572)
- cmd.exe (PID: 8876)
- cmd.exe (PID: 8464)
Process uses IPCONFIG to discard the IP address configuration
- cmd.exe (PID: 7668)
- cmd.exe (PID: 5008)
- cmd.exe (PID: 7632)
- cmd.exe (PID: 7592)
- cmd.exe (PID: 6572)
- cmd.exe (PID: 8464)
- cmd.exe (PID: 8876)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 7668)
- cmd.exe (PID: 5008)
- cmd.exe (PID: 7592)
- cmd.exe (PID: 7632)
- cmd.exe (PID: 6572)
- cmd.exe (PID: 8464)
- cmd.exe (PID: 8876)
- cmd.exe (PID: 8472)
- cmd.exe (PID: 10256)
- cmd.exe (PID: 9640)
- cmd.exe (PID: 10348)
- cmd.exe (PID: 10108)
- cmd.exe (PID: 10668)
- cmd.exe (PID: 10580)
The process executes VB scripts
- cmd.exe (PID: 7668)
- cmd.exe (PID: 5008)
- cmd.exe (PID: 7632)
- cmd.exe (PID: 7592)
- cmd.exe (PID: 6572)
- cmd.exe (PID: 8876)
- cmd.exe (PID: 8464)
Executing commands from a ".bat" file
- cmd.exe (PID: 5008)
- cmd.exe (PID: 7668)
- cmd.exe (PID: 7592)
- cmd.exe (PID: 7632)
- cmd.exe (PID: 6572)
- cmd.exe (PID: 8464)
- cmd.exe (PID: 8876)
- cmd.exe (PID: 10256)
- cmd.exe (PID: 8472)
- cmd.exe (PID: 10348)
- cmd.exe (PID: 9640)
- cmd.exe (PID: 10580)
- cmd.exe (PID: 10668)
- cmd.exe (PID: 10108)
- cmd.exe (PID: 8312)
Application launched itself
- cmd.exe (PID: 5008)
- cmd.exe (PID: 7668)
- cmd.exe (PID: 7592)
- cmd.exe (PID: 7632)
- cmd.exe (PID: 6572)
- cmd.exe (PID: 8876)
- cmd.exe (PID: 8464)
- cmd.exe (PID: 10256)
- cmd.exe (PID: 8472)
- cmd.exe (PID: 10348)
- cmd.exe (PID: 9640)
- cmd.exe (PID: 10668)
- cmd.exe (PID: 10108)
- cmd.exe (PID: 10580)
- cmd.exe (PID: 8312)
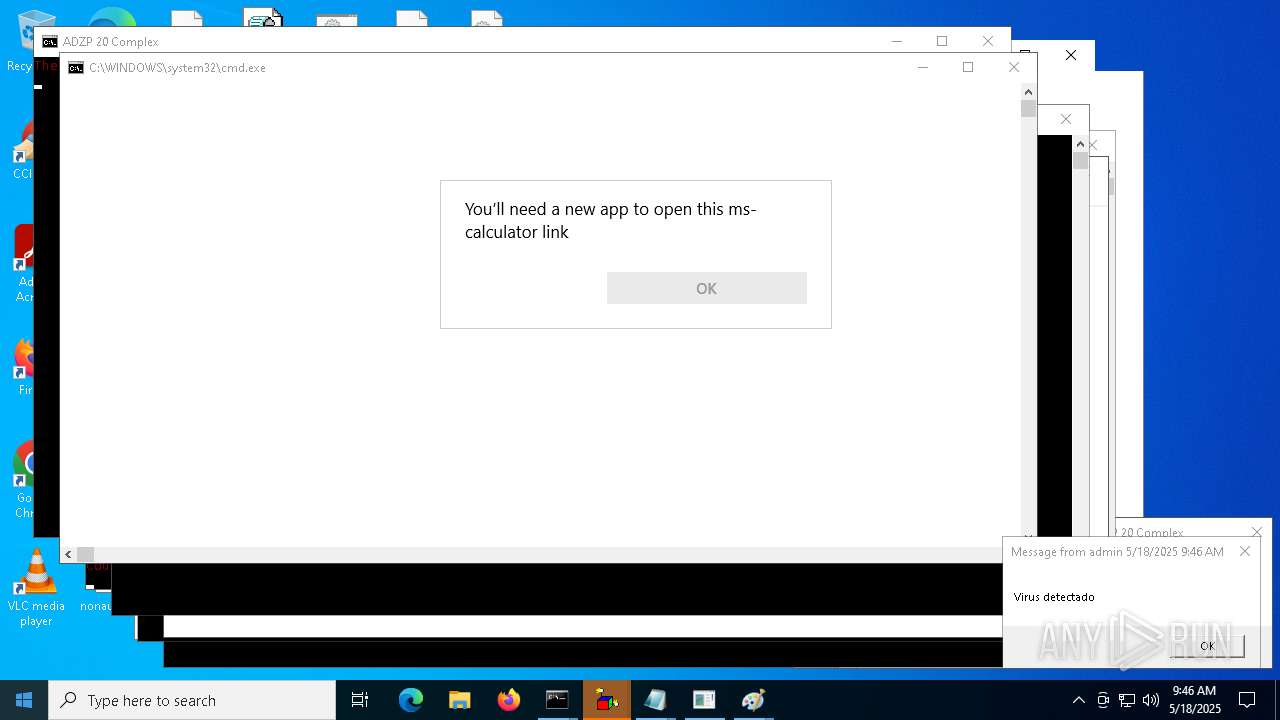
Starts CMD.EXE for commands execution
- cmd.exe (PID: 5008)
- cmd.exe (PID: 7668)
- cmd.exe (PID: 7592)
- cmd.exe (PID: 7632)
- cmd.exe (PID: 6572)
- cmd.exe (PID: 8464)
- cmd.exe (PID: 8876)
- cmd.exe (PID: 10256)
- cmd.exe (PID: 8472)
- cmd.exe (PID: 9640)
- cmd.exe (PID: 10348)
- cmd.exe (PID: 10580)
- cmd.exe (PID: 10668)
- cmd.exe (PID: 10108)
- cmd.exe (PID: 8312)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7668)
- cmd.exe (PID: 5008)
- cmd.exe (PID: 7632)
- cmd.exe (PID: 7592)
- cmd.exe (PID: 6572)
- cmd.exe (PID: 8876)
- cmd.exe (PID: 8464)
Uses NETSH.EXE to change the status of the firewall
- cmd.exe (PID: 7668)
- cmd.exe (PID: 5008)
- cmd.exe (PID: 7632)
- cmd.exe (PID: 7592)
The process checks if it is being run in the virtual environment
- icacls.exe (PID: 8896)
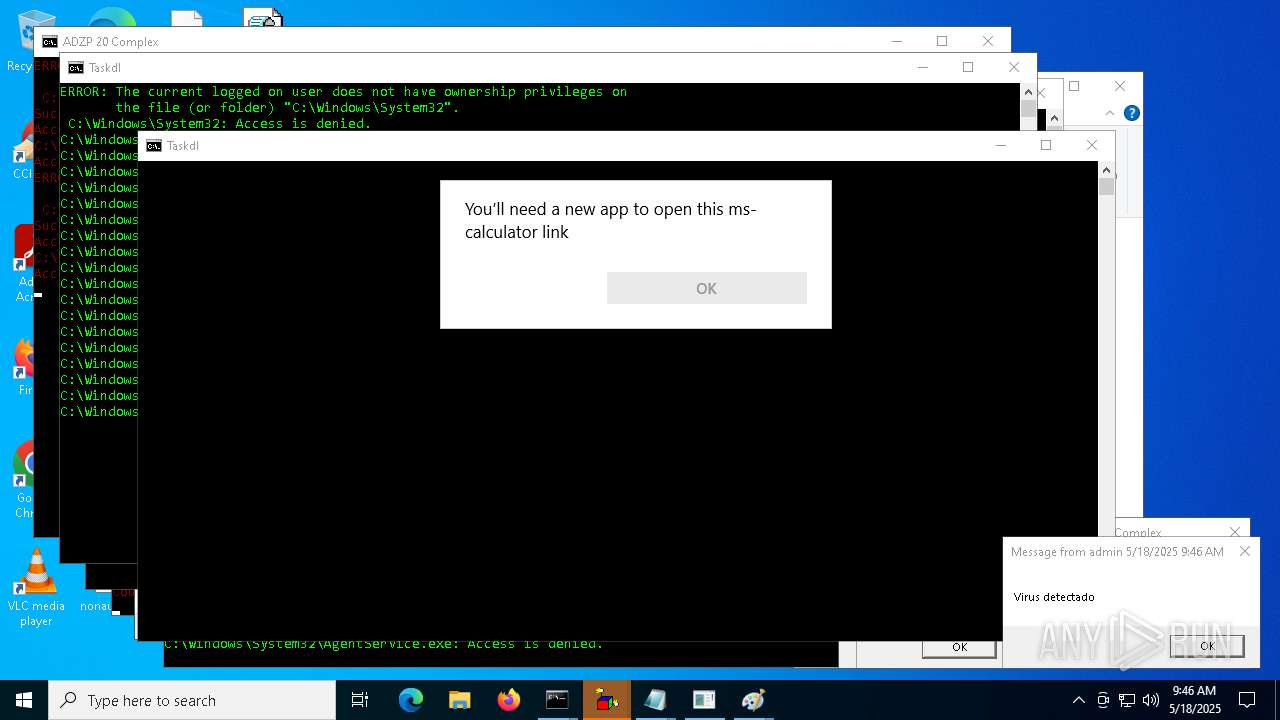
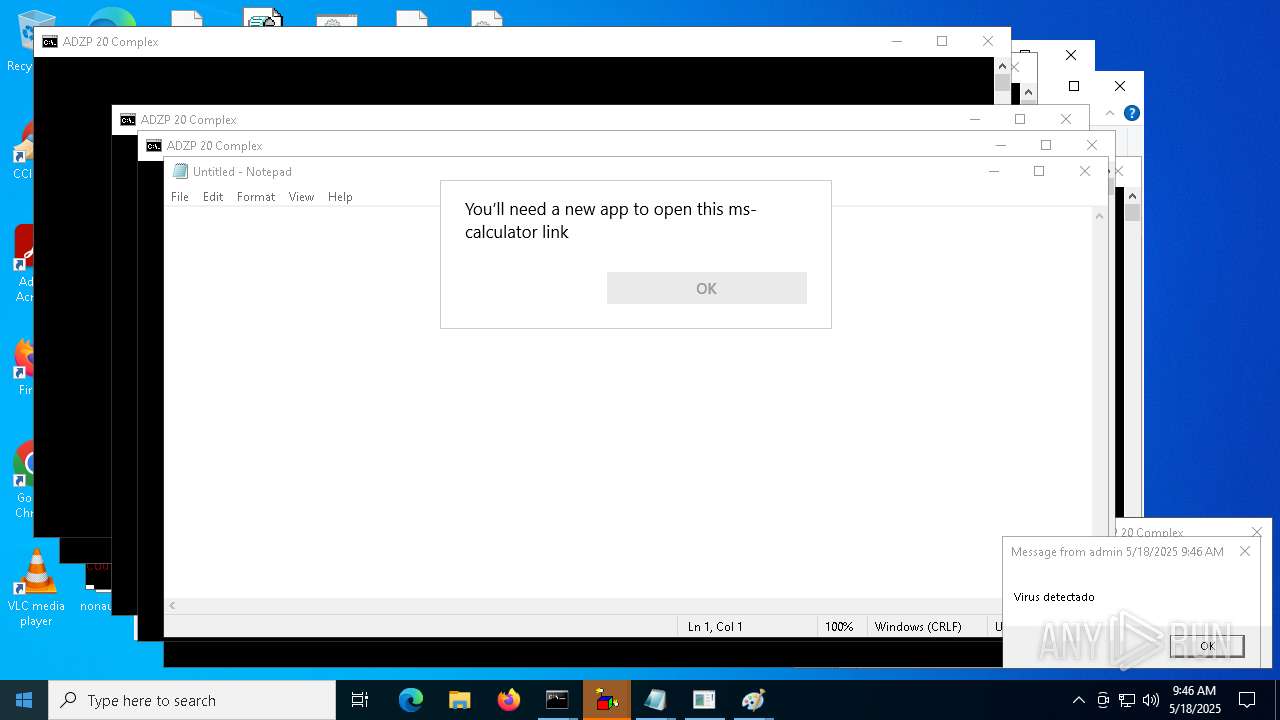
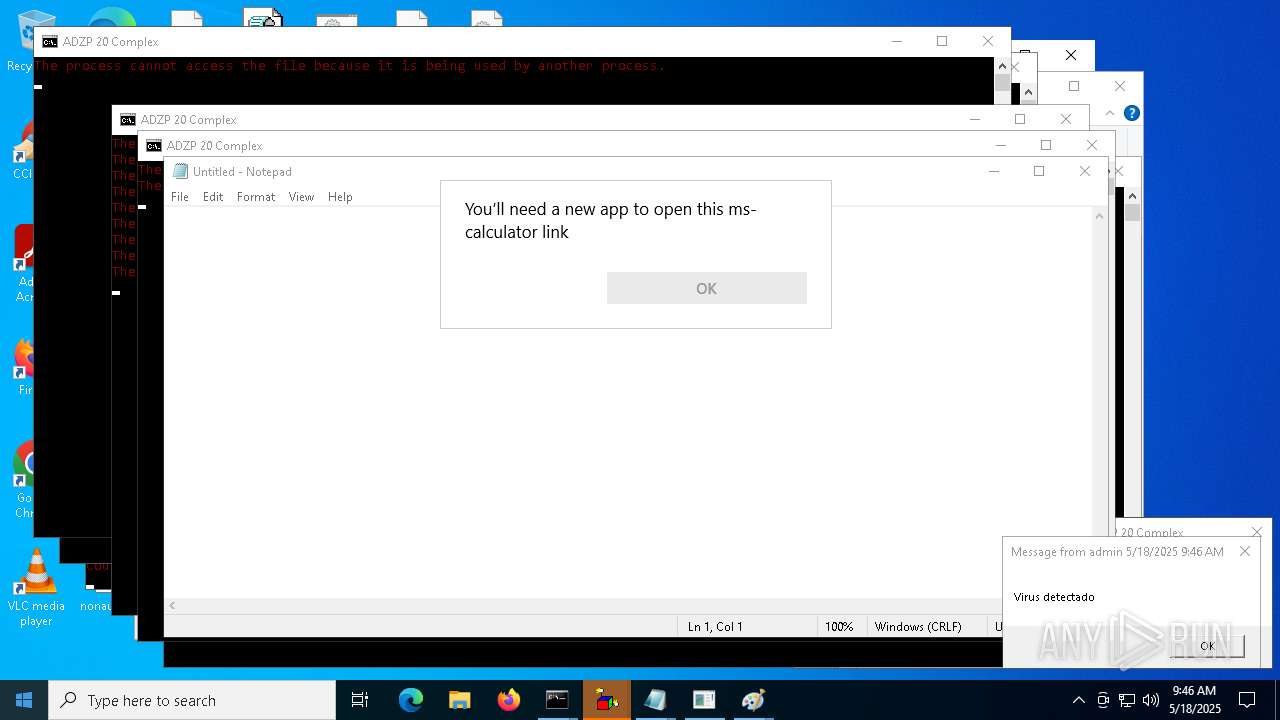
Starts application with an unusual extension
- cmd.exe (PID: 7668)
- cmd.exe (PID: 5008)
INFO
Manual execution by a user
- cmd.exe (PID: 7668)
Reads the computer name
- Tasksvc.exe (PID: 8060)
Checks supported languages
- Tasksvc.exe (PID: 8060)
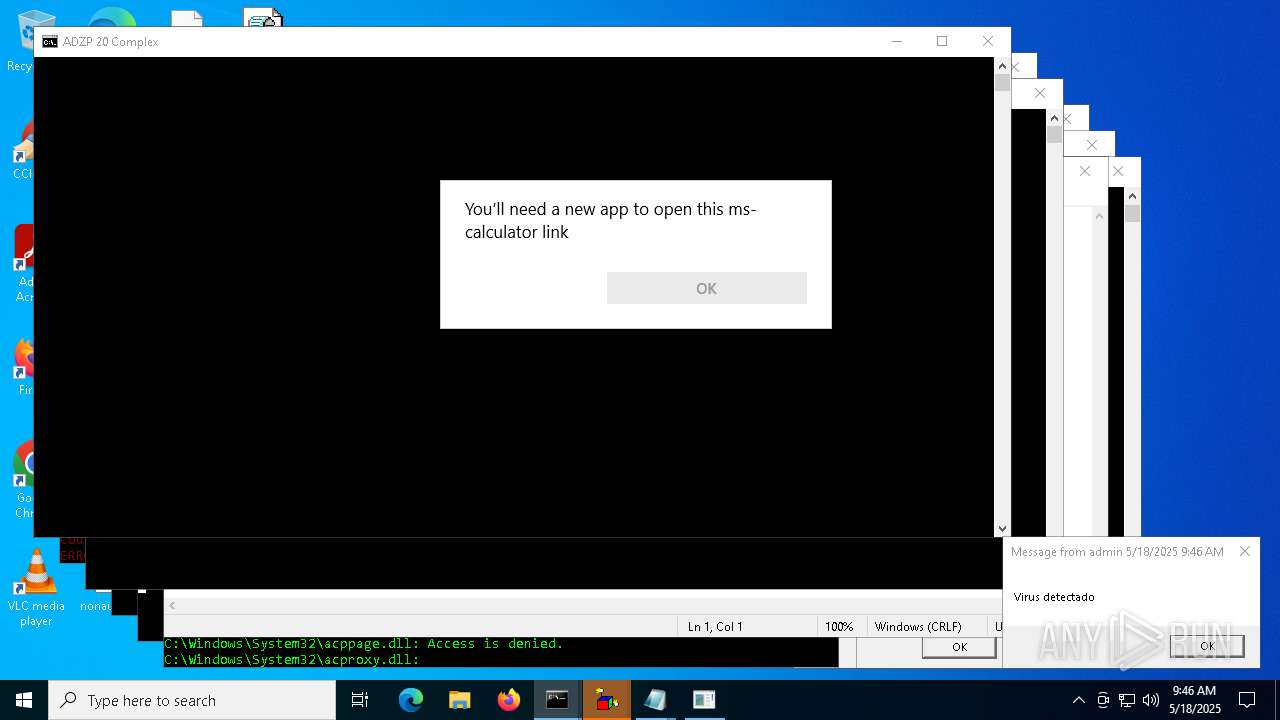
Reads security settings of Internet Explorer
- calc.exe (PID: 7432)
- calc.exe (PID: 1912)
- calc.exe (PID: 632)
- OpenWith.exe (PID: 1300)
- OpenWith.exe (PID: 8024)
- OpenWith.exe (PID: 7832)
- calc.exe (PID: 8660)
- calc.exe (PID: 8984)
- OpenWith.exe (PID: 8760)
- OpenWith.exe (PID: 9036)
- calc.exe (PID: 8312)
- OpenWith.exe (PID: 5436)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:13 05:52:44 |
| ZipCRC: | 0xd620a5b0 |
| ZipCompressedSize: | 12517 |
| ZipUncompressedSize: | 23646 |
| ZipFileName: | challenge_1.bat |
Total processes
596
Monitored processes
468
Malicious processes
8
Suspicious processes
11
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | WScript Advertencia.vbs | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 632 | calc | C:\Windows\System32\calc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Calculator Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | takeown /f "C:\Windows\System32" /r | C:\Windows\System32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Takes ownership of a file Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | attrib -r -a -s -h *.* | C:\Windows\System32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | WScript Advertencia.vbs | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 780 | icacls "C:\Windows\System32" /reset /t /c /q | C:\Windows\System32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | WScript ErrorCritico.vbs | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 856 | explorer.exe | C:\Windows\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | ipconfig /release | C:\Windows\System32\ipconfig.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IP Configuration Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | WScript Advertencia.vbs | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
Total events
48 355
Read events
48 161
Write events
194
Delete events
0
Modification events
| (PID) Process: | (4880) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4880) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4880) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4880) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\challenge.zip | |||
| (PID) Process: | (4880) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4880) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4880) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4880) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4880) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (4880) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
2
Suspicious files
0
Text files
40
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7668 | cmd.exe | C:\Users\admin\Desktop\Virus.sys | text | |
MD5:B23DB54E8D86436E4084D1AB0F0A1750 | SHA256:8525E26CD8120992DEE8597E93B4675B9D949EB6C66C31432F81FEA346C538CB | |||
| 7668 | cmd.exe | C:\Users\admin\Desktop\Advertencia.vbs | text | |
MD5:08121EA7E3B2EB7EDFC85252B937AAEB | SHA256:31CD4463ECC62DC846DBAEE0A5446D4BF11100BEFF1B01AE88E234B6C29329C2 | |||
| 4880 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb4880.38804\challenge_1.bat | text | |
MD5:39830FCB4FFB54FEAAF9A659C07ACED3 | SHA256:D13E2C505021D99FD969A85F1FD530066E48ABDCA9161166D38D7593C8EF275D | |||
| 7668 | cmd.exe | C:\Users\admin\Desktop\Virus.ini | text | |
MD5:248B4100FAF1E6190D15A315DACCF0B7 | SHA256:7B7DAAECC7D2D78656AA87CD5A6212D0B7936EEDE12BAD422A2E58FE933F2384 | |||
| 7668 | cmd.exe | C:\Users\admin\Desktop\ErrorCritico.vbs | text | |
MD5:08121EA7E3B2EB7EDFC85252B937AAEB | SHA256:31CD4463ECC62DC846DBAEE0A5446D4BF11100BEFF1B01AE88E234B6C29329C2 | |||
| 7668 | cmd.exe | C:\Users\admin\Desktop\Taskse.exe | text | |
MD5:49EA0A2F9C6D92C9634CCEC836B896B9 | SHA256:0089AE0E1A8ABD8E35DC82B83D750C57D267C99CB6D54ABE737E58341AE36C2F | |||
| 7668 | cmd.exe | C:\Users\admin\Desktop\Autorun.inf | text | |
MD5:9A9FED65AE5AECB2E2723DCCF0F0B34E | SHA256:B9EB9A01994285B8A10189321D0CF6055AD92AE659D6603F7D1FE835F39CA1D2 | |||
| 7668 | cmd.exe | C:\Users\admin\AppData\Local\Temp\Bytebeat.Shingapi.tmp | text | |
MD5:0BF50EA68E7B825549C09F0E81EA1E41 | SHA256:54530C881B0D32EA17870D396712ABF94589F906AC294C1D1893A68DE4E522F4 | |||
| 7668 | cmd.exe | C:\Users\admin\Desktop\Taskdl.bat | text | |
MD5:9905E5A33C6EDD8EB5F59780AFBF74DE | SHA256:C134B2F85415BA5CFCE3E3FE4745688335745A9BB22152AC8F5C77F190D8AEE3 | |||
| 7668 | cmd.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\challenge_1.bat | text | |
MD5:39830FCB4FFB54FEAAF9A659C07ACED3 | SHA256:D13E2C505021D99FD969A85F1FD530066E48ABDCA9161166D38D7593C8EF275D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
18
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.18:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
10060 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
10060 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.18:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.132:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
10060 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |