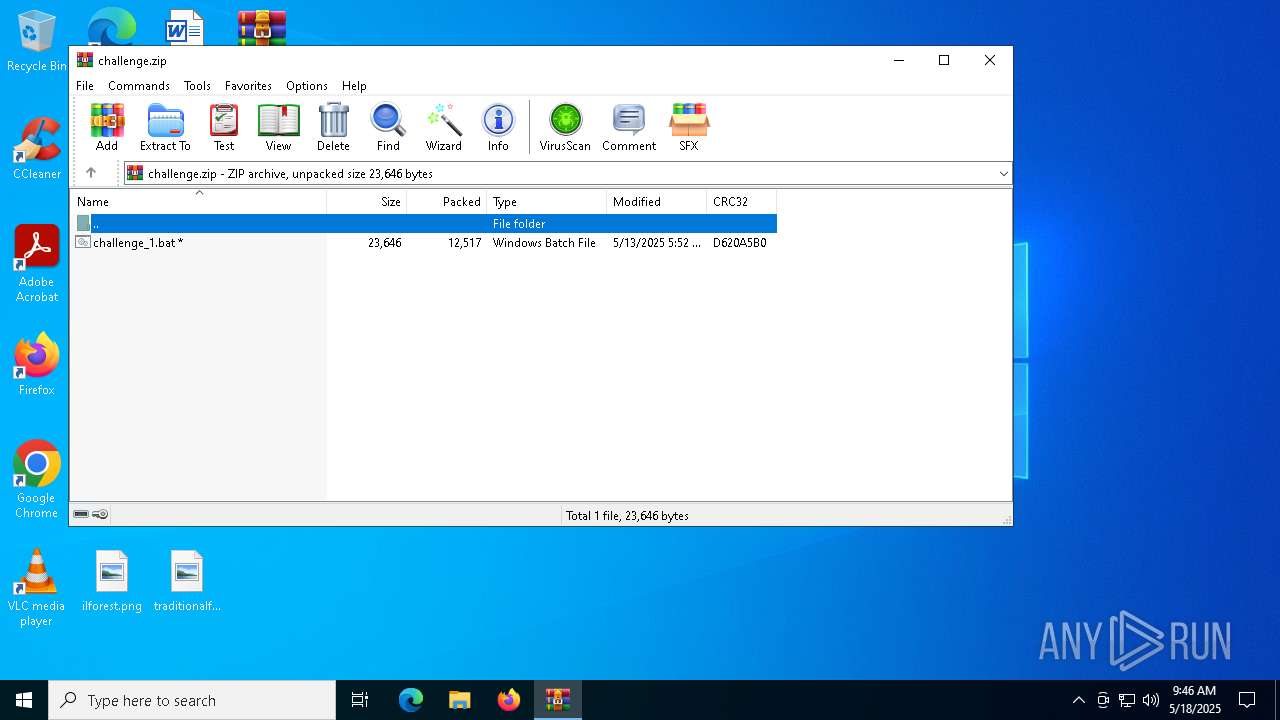
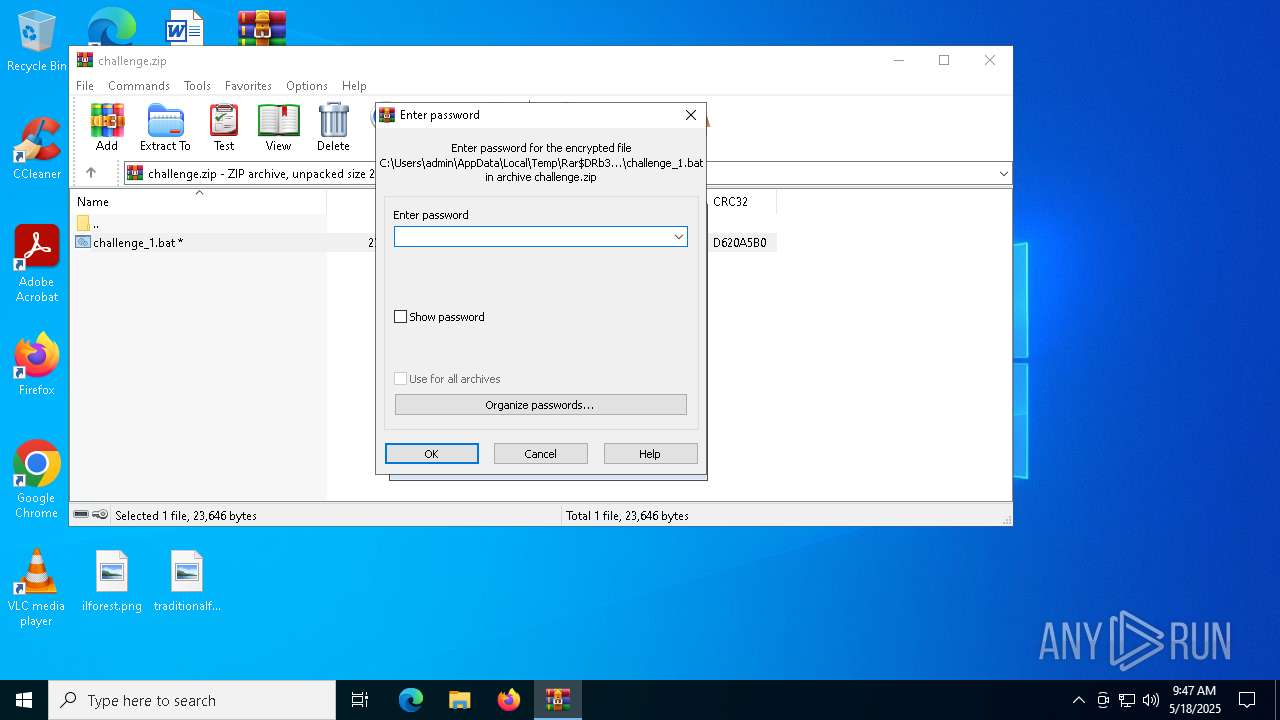
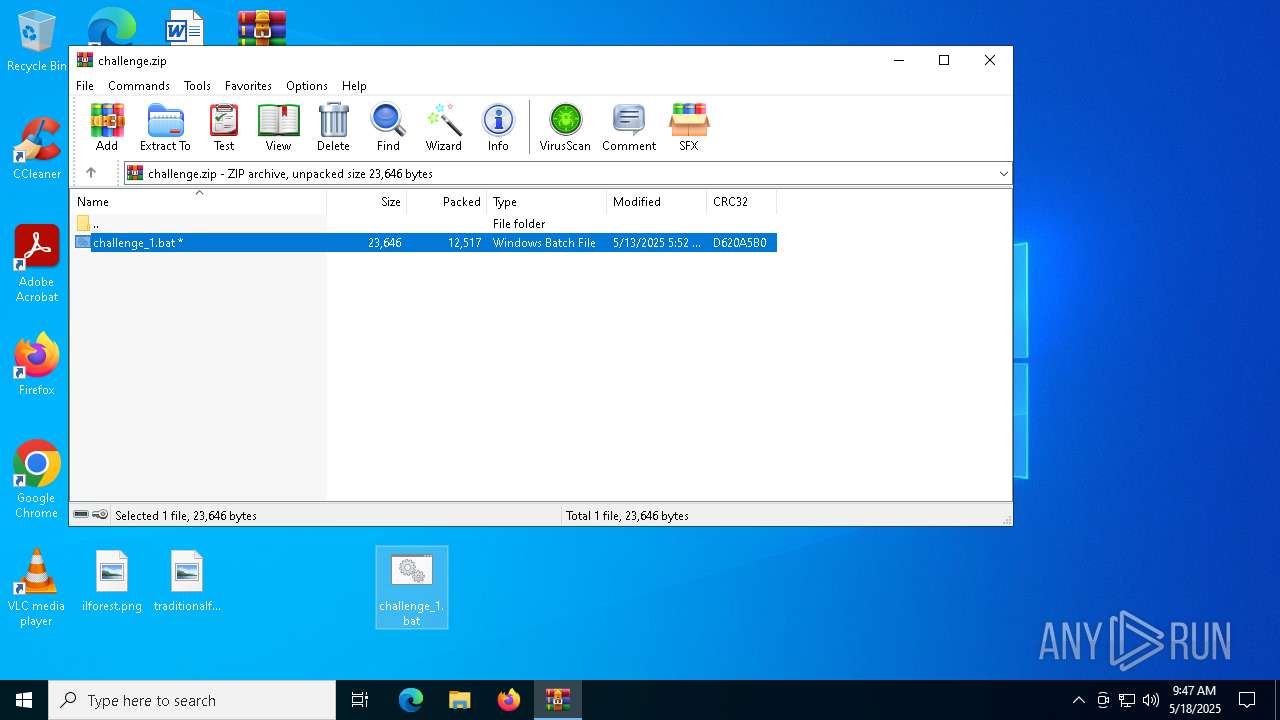
| File name: | challenge.zip |
| Full analysis: | https://app.any.run/tasks/88fb6364-9b10-4050-ac98-89f301b25d7e |
| Verdict: | Malicious activity |
| Analysis date: | May 18, 2025, 09:46:53 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 52F9551DECA942A8A88ED0A619684FAA |
| SHA1: | 4ADB581F7D20B0A51F09AF6E966495BA9BF35E86 |
| SHA256: | B58E493A5E7780611A2A3337448F57EE21A6AF0EA6722674DC80D80F06235275 |
| SSDEEP: | 384:U7g5i/kW5kN4v3P4741m54OmajzzXvcv72:/W+qvf474U54cnXvX |
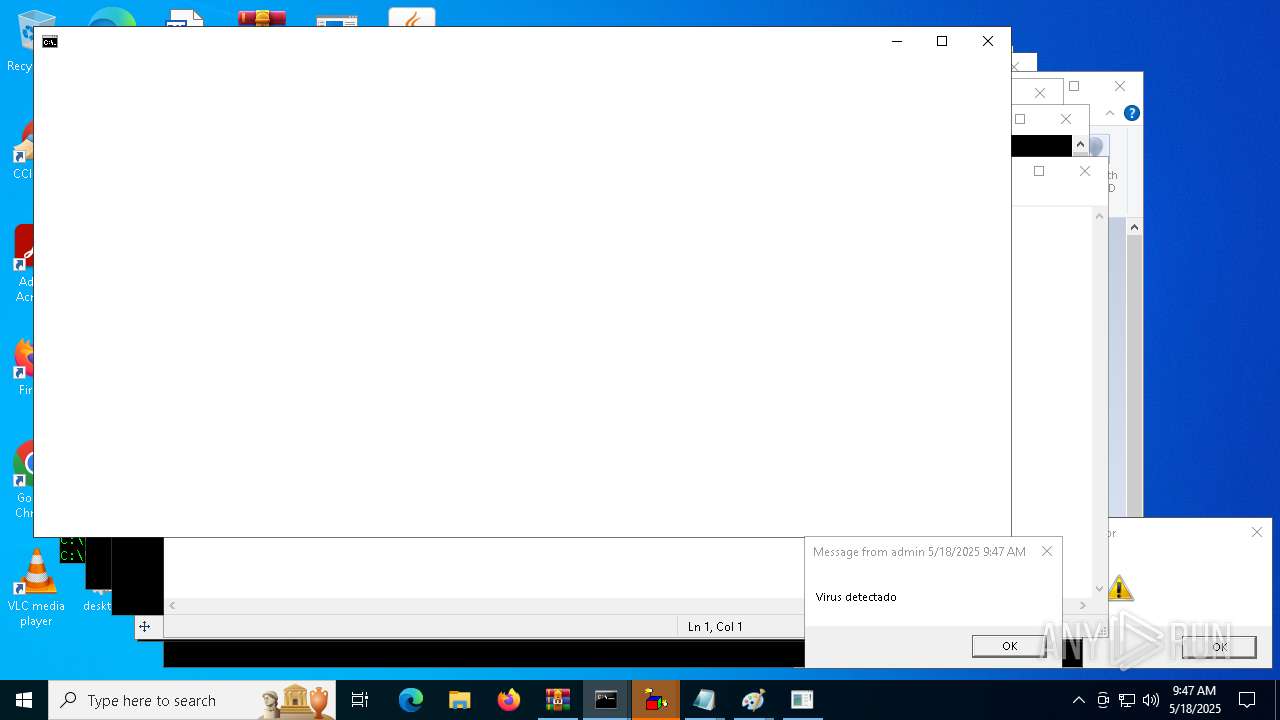
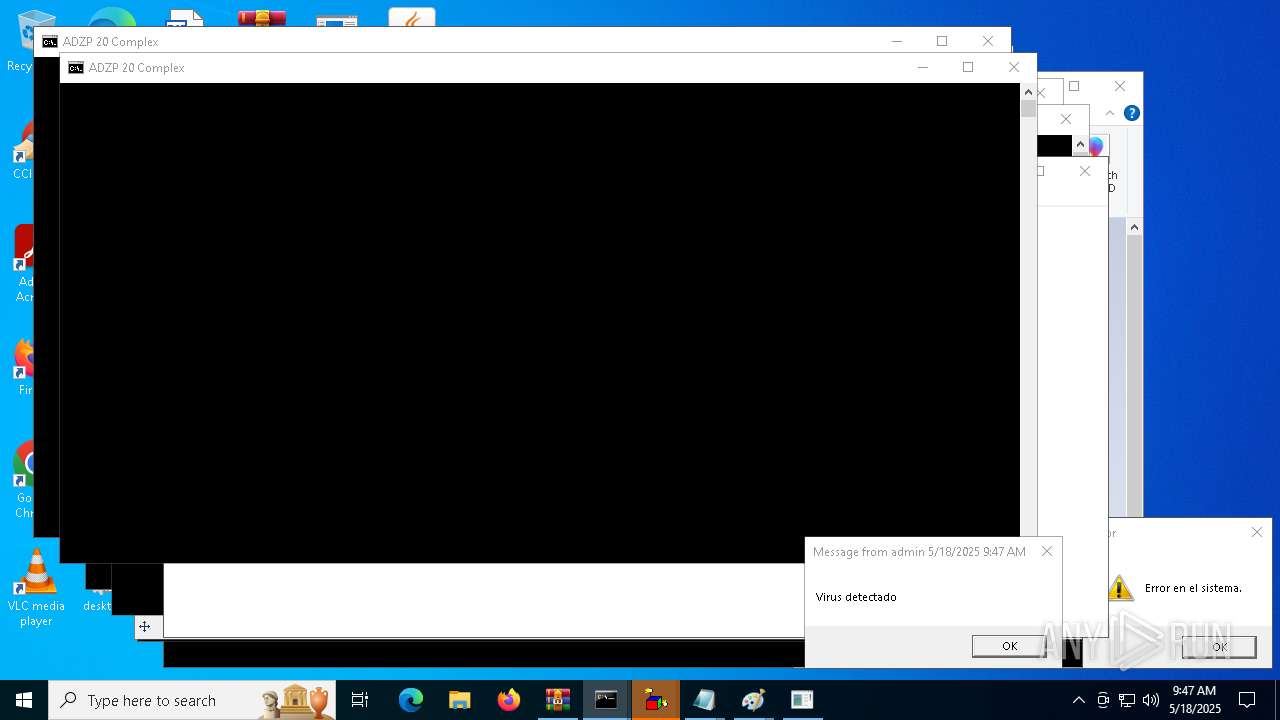
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 300)
Create files in the Startup directory
- cmd.exe (PID: 3956)
Changes the autorun value in the registry
- reg.exe (PID: 4756)
- reg.exe (PID: 8136)
- reg.exe (PID: 8124)
- reg.exe (PID: 7856)
SONIC has been detected
- cmd.exe (PID: 3956)
SUSPICIOUS
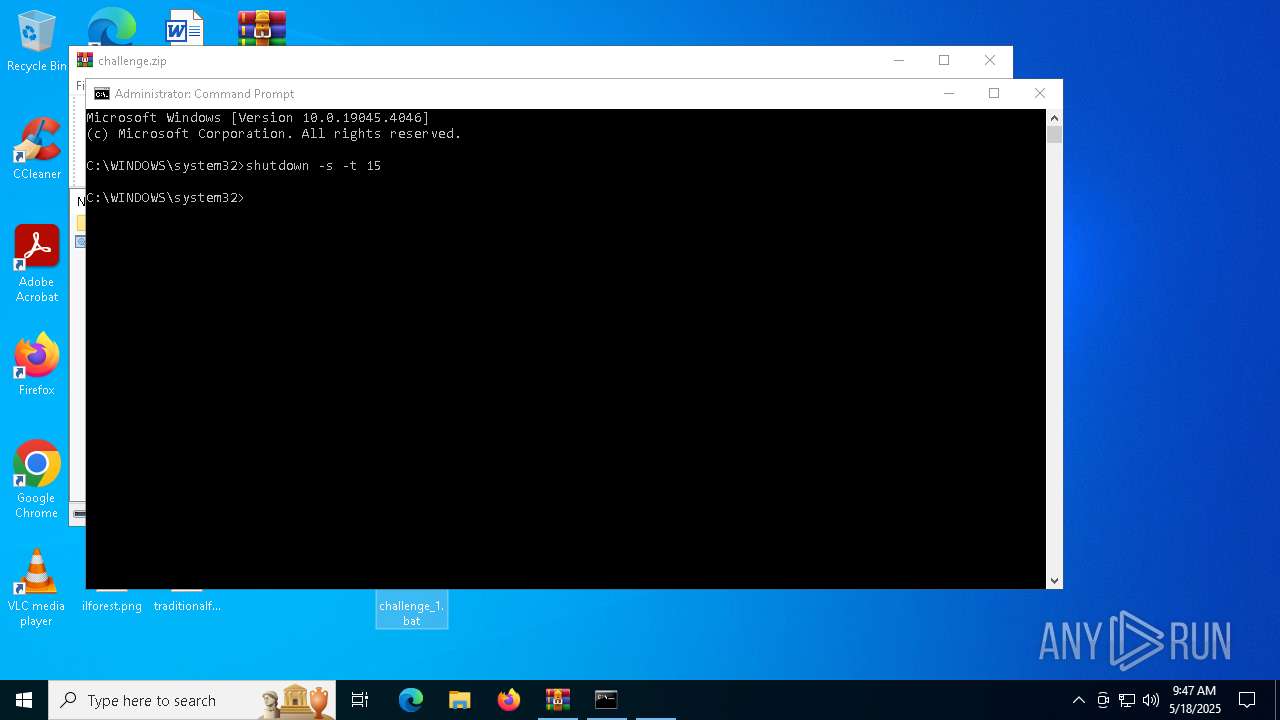
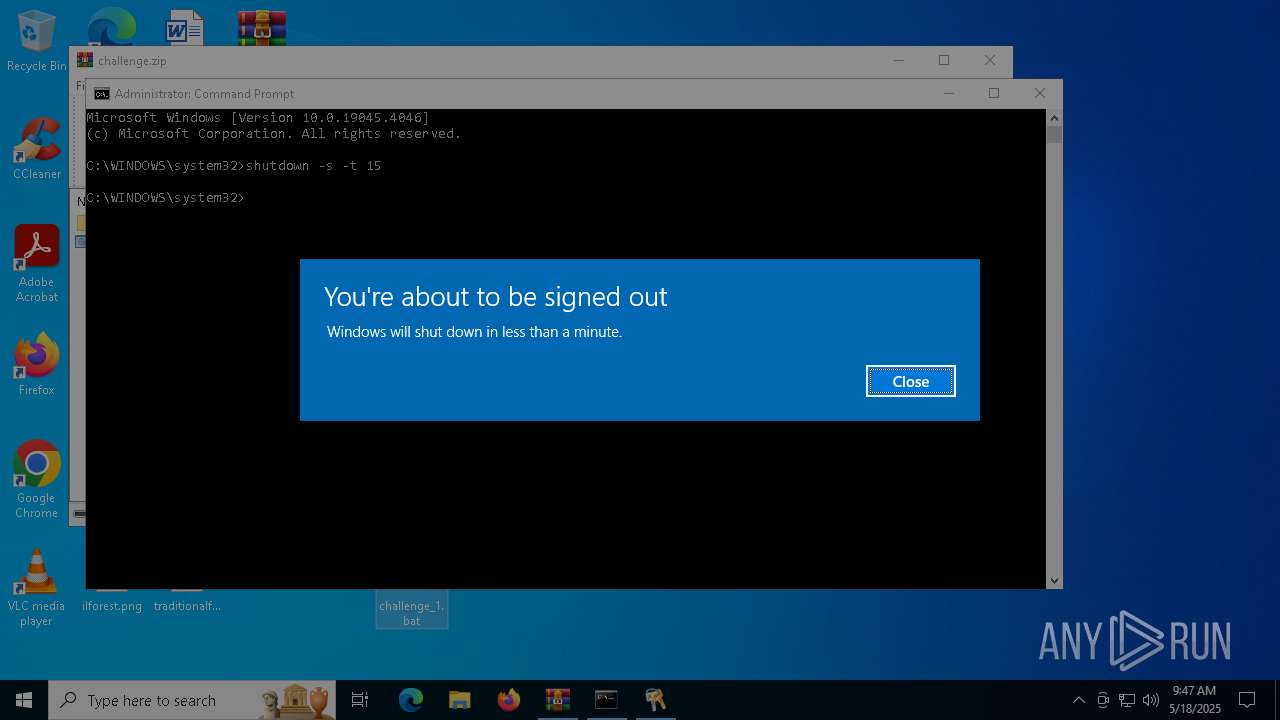
The system shut down or reboot
- cmd.exe (PID: 1276)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 5572)
- cmd.exe (PID: 3956)
- cmd.exe (PID: 7768)
- cmd.exe (PID: 5020)
- cmd.exe (PID: 7484)
- cmd.exe (PID: 8164)
- cmd.exe (PID: 7196)
- cmd.exe (PID: 7972)
- cmd.exe (PID: 7416)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 3956)
- cmd.exe (PID: 5572)
- cmd.exe (PID: 7484)
- cmd.exe (PID: 7196)
- cmd.exe (PID: 7972)
- cmd.exe (PID: 8164)
- cmd.exe (PID: 5020)
- cmd.exe (PID: 7768)
- cmd.exe (PID: 7416)
Decoding a file from Base64 using CertUtil
- cmd.exe (PID: 3956)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 3956)
- cmd.exe (PID: 5020)
- cmd.exe (PID: 7196)
- cmd.exe (PID: 7484)
Executable content was dropped or overwritten
- certutil.exe (PID: 7156)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 3956)
- cmd.exe (PID: 5020)
- cmd.exe (PID: 7484)
- cmd.exe (PID: 7196)
Process uses IPCONFIG to discard the IP address configuration
- cmd.exe (PID: 3956)
- cmd.exe (PID: 5020)
- cmd.exe (PID: 7484)
- cmd.exe (PID: 7196)
The process executes VB scripts
- cmd.exe (PID: 3956)
- cmd.exe (PID: 7484)
- cmd.exe (PID: 7196)
- cmd.exe (PID: 5020)
Executing commands from a ".bat" file
- cmd.exe (PID: 3956)
- cmd.exe (PID: 5020)
- cmd.exe (PID: 7484)
- cmd.exe (PID: 7196)
- cmd.exe (PID: 7416)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3956)
- cmd.exe (PID: 7484)
- cmd.exe (PID: 5020)
- cmd.exe (PID: 7196)
- cmd.exe (PID: 7416)
Application launched itself
- cmd.exe (PID: 3956)
- cmd.exe (PID: 5020)
- cmd.exe (PID: 7484)
- cmd.exe (PID: 7196)
- cmd.exe (PID: 7416)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 3956)
- cmd.exe (PID: 5020)
- cmd.exe (PID: 7484)
- cmd.exe (PID: 7196)
Uses NETSH.EXE to change the status of the firewall
- cmd.exe (PID: 3956)
The process checks if it is being run in the virtual environment
- icacls.exe (PID: 7616)
INFO
Manual execution by a user
- cmd.exe (PID: 1276)
- cmd.exe (PID: 3956)
Checks supported languages
- Tasksvc.exe (PID: 744)
Reads the computer name
- Tasksvc.exe (PID: 744)
Reads security settings of Internet Explorer
- calc.exe (PID: 7276)
- calc.exe (PID: 4528)
- calc.exe (PID: 7584)
- OpenWith.exe (PID: 8096)
- OpenWith.exe (PID: 8044)
- OpenWith.exe (PID: 7568)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:13 05:52:44 |
| ZipCRC: | 0xd620a5b0 |
| ZipCompressedSize: | 12517 |
| ZipUncompressedSize: | 23646 |
| ZipFileName: | challenge_1.bat |
Total processes
370
Monitored processes
238
Malicious processes
4
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\challenge.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 744 | Tasksvc.exe | C:\Users\admin\Desktop\Tasksvc.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 1088 | rundll32 user32.dll, SwapMouseButton | C:\Windows\System32\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | rundll32 user32.dll, SetCursorPos | C:\Windows\System32\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1276 | "C:\WINDOWS\system32\cmd.exe" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1568 | takeown /f "C:\WINDOWS\System32\winresume.exe" | C:\Windows\System32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Takes ownership of a file Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1912 | WScript ErrorCritico.vbs | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 2552 | WScript Advertencia.vbs | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
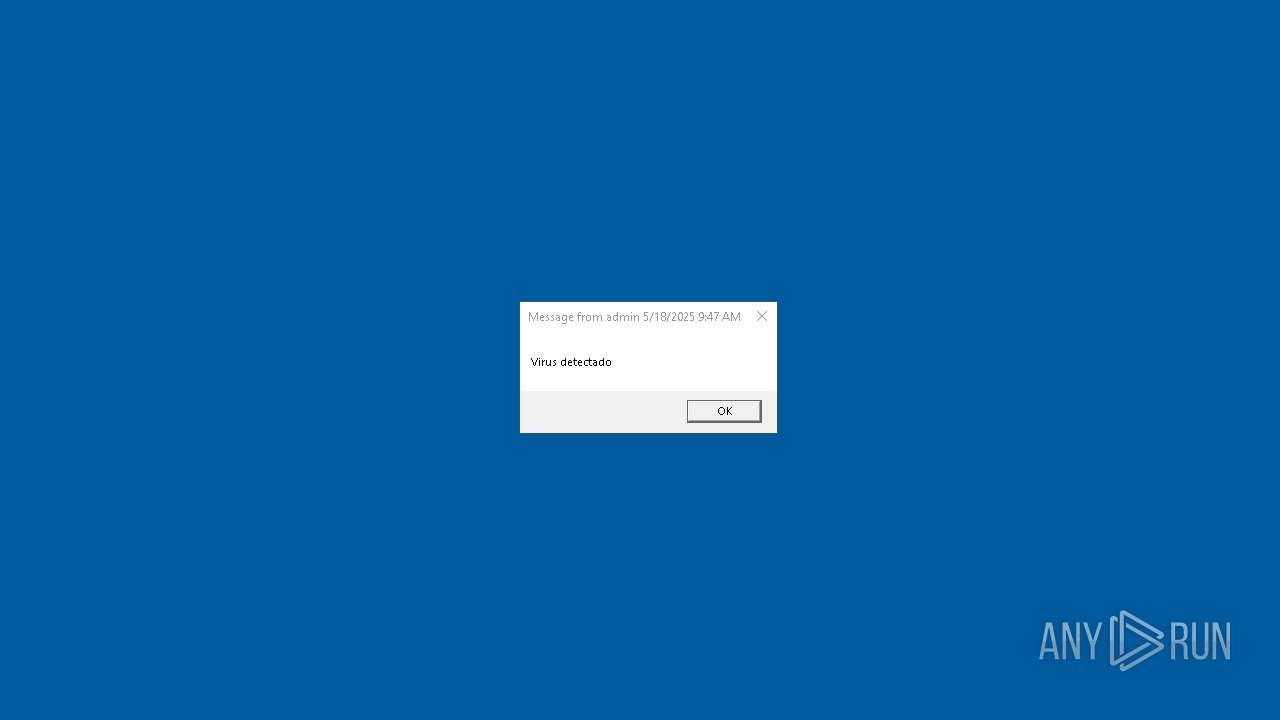
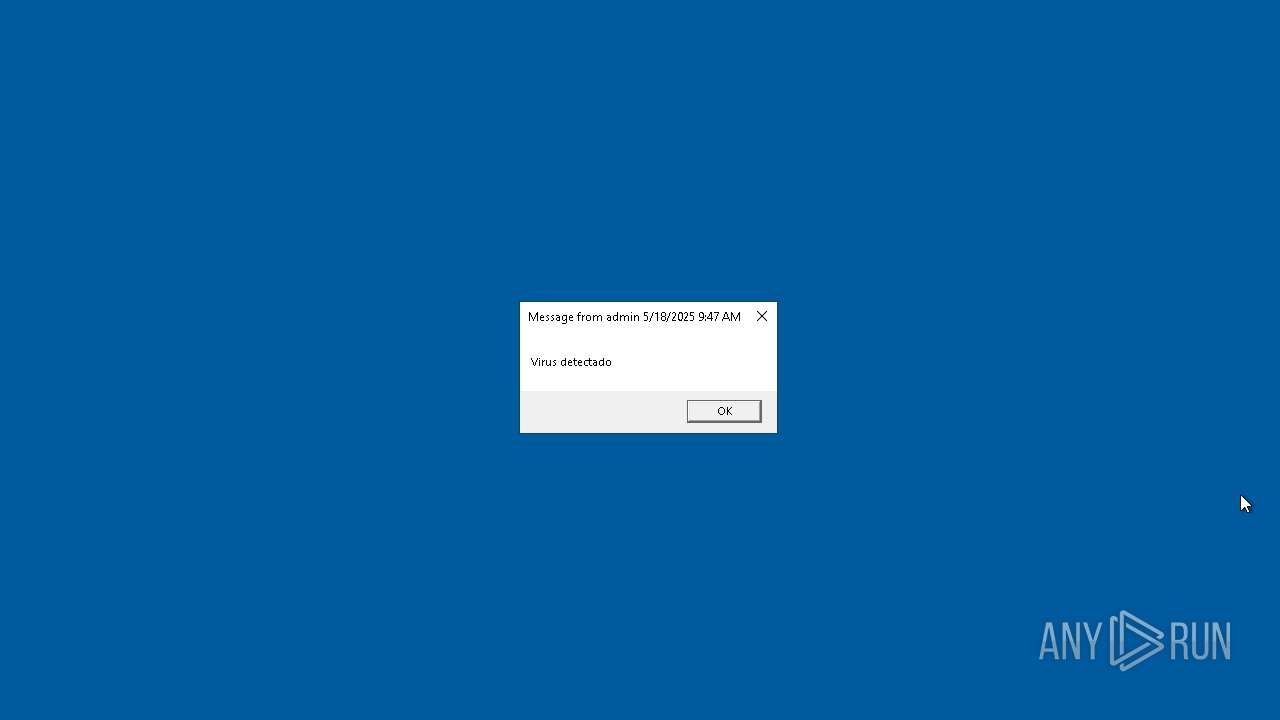
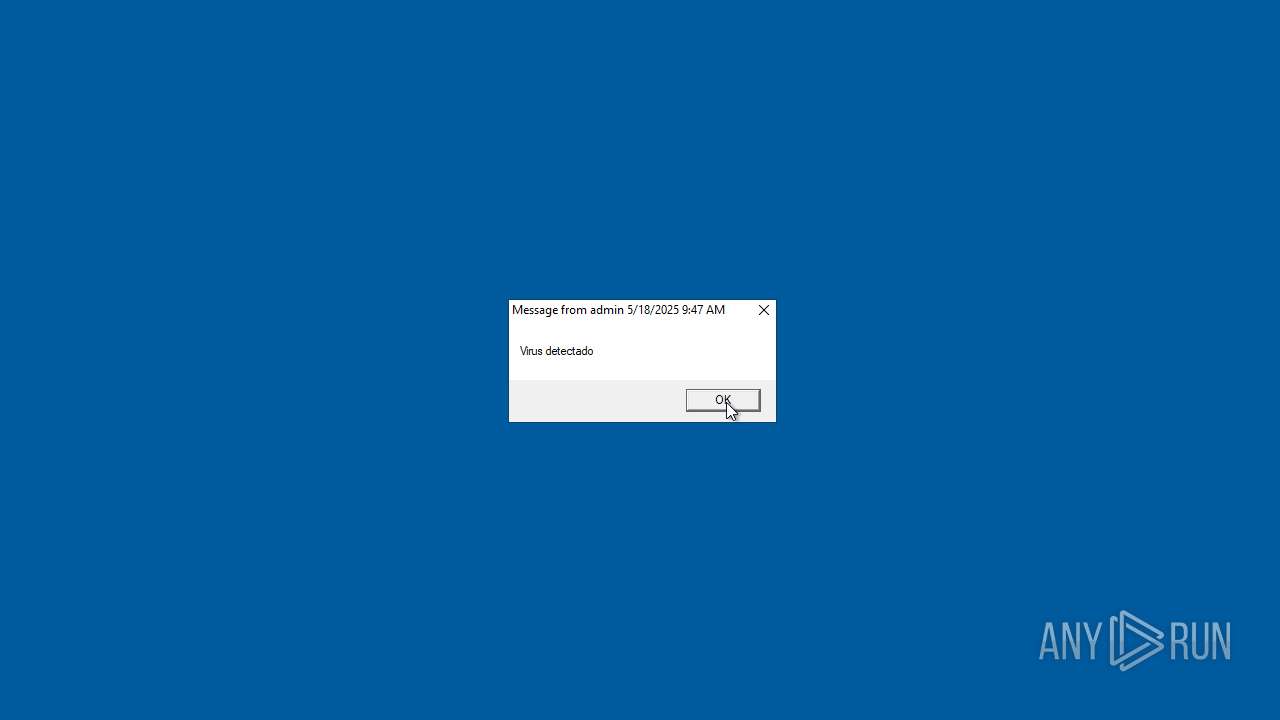
| 2616 | msg * Has sido hackeado! | C:\Windows\System32\msg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Message Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3024 | explorer.exe | C:\Windows\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
27 380
Read events
27 290
Write events
90
Delete events
0
Modification events
| (PID) Process: | (300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\challenge.zip | |||
| (PID) Process: | (300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (4756) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | EthernetKill |
Value: C:\Users\admin\AppData\Local\Temp\EthernetKiller.cmd | |||
Executable files
2
Suspicious files
0
Text files
24
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3956 | cmd.exe | C:\Users\admin\Desktop\Taskdl.bat | text | |
MD5:9905E5A33C6EDD8EB5F59780AFBF74DE | SHA256:C134B2F85415BA5CFCE3E3FE4745688335745A9BB22152AC8F5C77F190D8AEE3 | |||
| 3956 | cmd.exe | C:\Users\admin\Desktop\Advertencia.vbs | text | |
MD5:08121EA7E3B2EB7EDFC85252B937AAEB | SHA256:31CD4463ECC62DC846DBAEE0A5446D4BF11100BEFF1B01AE88E234B6C29329C2 | |||
| 3956 | cmd.exe | C:\Users\admin\Desktop\ErrorCritico.vbs | text | |
MD5:08121EA7E3B2EB7EDFC85252B937AAEB | SHA256:31CD4463ECC62DC846DBAEE0A5446D4BF11100BEFF1B01AE88E234B6C29329C2 | |||
| 300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb300.43386\challenge_1.bat | text | |
MD5:39830FCB4FFB54FEAAF9A659C07ACED3 | SHA256:D13E2C505021D99FD969A85F1FD530066E48ABDCA9161166D38D7593C8EF275D | |||
| 3956 | cmd.exe | C:\Users\admin\Desktop\Taskse.exe | text | |
MD5:523E98DDFC769CDED3270A59BBDCE3BC | SHA256:256B3E85E92CE2FA4D5910286F86892B797222FD4880EF76AF4A467050A2B941 | |||
| 3956 | cmd.exe | C:\Users\admin\Desktop\Autorun.inf | text | |
MD5:9A9FED65AE5AECB2E2723DCCF0F0B34E | SHA256:B9EB9A01994285B8A10189321D0CF6055AD92AE659D6603F7D1FE835F39CA1D2 | |||
| 3956 | cmd.exe | C:\Users\admin\Desktop\Virus.dll | text | |
MD5:2333EEBD2ABCF14BD375F410B414894C | SHA256:4AC5133D9958374C5E4A250CFAE5645C31984B50205A423A47B2A2D8AC6BE071 | |||
| 3956 | cmd.exe | C:\Users\admin\Desktop\Virus.com | text | |
MD5:4E41B674F8EF8CF2012EE14BAAB6F8FB | SHA256:6E873072B66344577E74522918670959181BD0AF626FDC45E39F4630A8EF72C8 | |||
| 3956 | cmd.exe | C:\Users\admin\Desktop\Virus.ini | text | |
MD5:0DA3FB67CF67763AD3E1A8CC0C3E71F0 | SHA256:8A634603DE0147F793D1ABBC9E42BDC42098A712B16941609A4504288A082D6B | |||
| 3956 | cmd.exe | C:\Users\admin\Desktop\Virus.reg | text | |
MD5:0E3AA27843A450BC9D3D946302688BE6 | SHA256:DAB84F0135C6112A8A8DBB24733962E5D67C5038C899882F9F4C5E20715E1DAD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
31
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.8:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5008 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5008 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.8:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.5:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
th.bing.com |
| whitelisted |