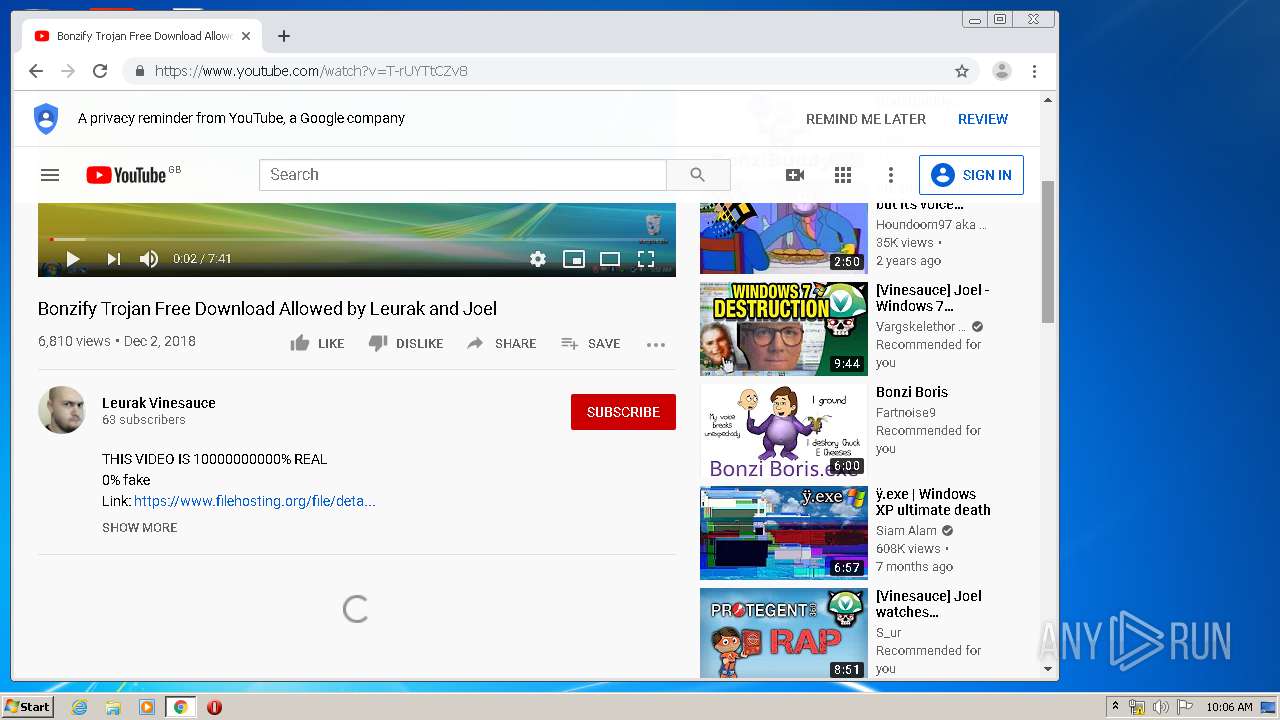
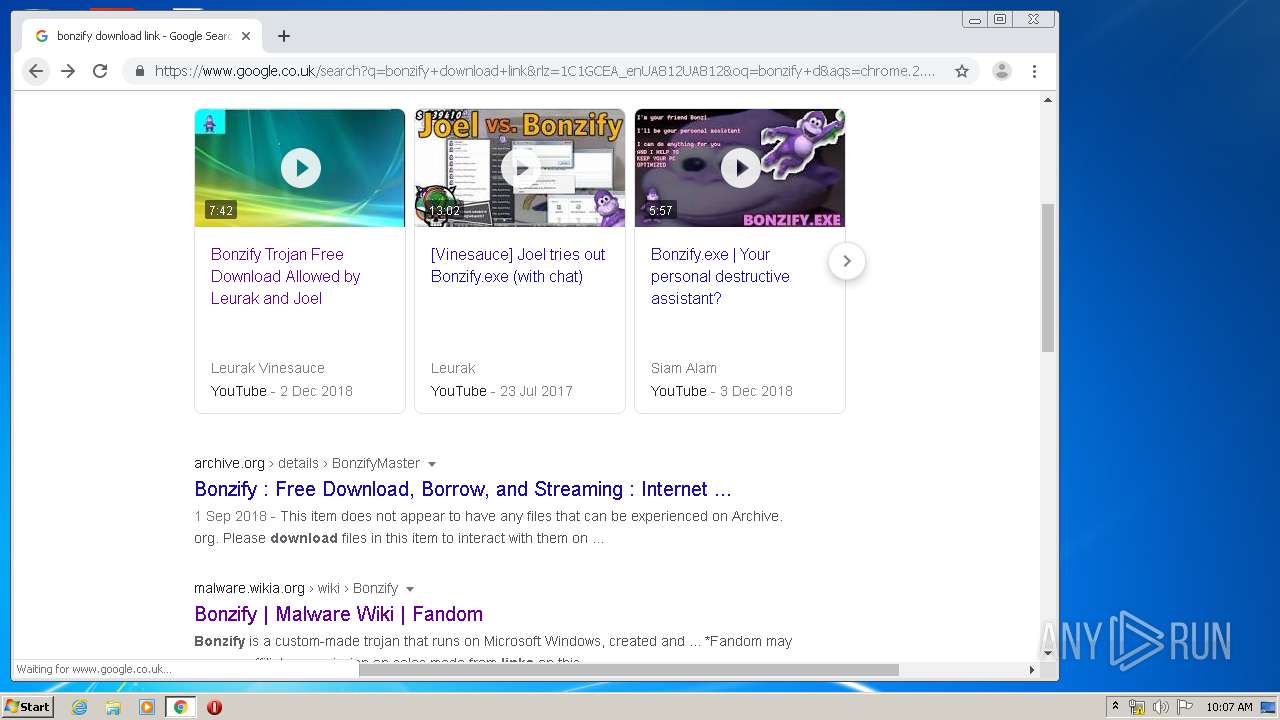
| URL: | https://web.archive.org/web/20040804124508/http:/www.youareanidiot.org/ |
| Full analysis: | https://app.any.run/tasks/05a3ce46-ef93-4192-b13c-553e81ccd3d7 |
| Verdict: | Malicious activity |
| Analysis date: | May 31, 2020, 09:04:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | A3D841EF4E8D65E26D7BA47081858E6D |
| SHA1: | 8492B94996B907B98F12F0C9C5049300796482B5 |
| SHA256: | B58DC149D5C50EF996BA20B8BA443EB26FED34295A6589E9178AA8A92F0A3C05 |
| SSDEEP: | 3:N8RQXxXJevRz3KN3dU+dpQK5:2GhX8BWKS |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executed via COM
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 184)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 3000)
Modifies files in Chrome extension folder
- chrome.exe (PID: 1824)
INFO
Application launched itself
- iexplore.exe (PID: 2152)
- chrome.exe (PID: 1824)
Reads Internet Cache Settings
- iexplore.exe (PID: 2152)
- iexplore.exe (PID: 2472)
Changes internet zones settings
- iexplore.exe (PID: 2152)
Creates files in the user directory
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 3000)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 184)
Reads internet explorer settings
- iexplore.exe (PID: 2472)
Manual execution by user
- chrome.exe (PID: 1824)
Reads the hosts file
- chrome.exe (PID: 1824)
- chrome.exe (PID: 2640)
Reads settings of System Certificates
- iexplore.exe (PID: 2472)
- chrome.exe (PID: 2640)
- iexplore.exe (PID: 2152)
Changes settings of System certificates
- iexplore.exe (PID: 2152)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2152)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
88
Monitored processes
48
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 184 | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 26.0 r0 Exit code: 0 Version: 26,0,0,131 Modules
| |||||||||||||||
| 664 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1000,14118925843190170289,6970264640353944167,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=915772898675298252 --mojo-platform-channel-handle=4264 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 824 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1000,14118925843190170289,6970264640353944167,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=16349844619149485636 --renderer-client-id=31 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1884 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 832 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1000,14118925843190170289,6970264640353944167,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9836341362545727808 --renderer-client-id=19 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3876 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 936 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1000,14118925843190170289,6970264640353944167,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7406085385019287584 --renderer-client-id=42 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3676 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 964 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1000,14118925843190170289,6970264640353944167,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=2032886215666077776 --mojo-platform-channel-handle=3520 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1016 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1000,14118925843190170289,6970264640353944167,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=558748603948168592 --mojo-platform-channel-handle=4640 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1196 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1000,14118925843190170289,6970264640353944167,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=3492489878496826216 --mojo-platform-channel-handle=4208 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1356 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1000,14118925843190170289,6970264640353944167,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=13252374590645394462 --renderer-client-id=32 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2052 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1524 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1000,14118925843190170289,6970264640353944167,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=1911878386990973763 --mojo-platform-channel-handle=4108 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
7 465
Read events
2 149
Write events
3 589
Delete events
1 727
Modification events
| (PID) Process: | (2152) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 2571832568 | |||
| (PID) Process: | (2152) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30816042 | |||
| (PID) Process: | (2152) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2152) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2152) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2152) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2152) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2152) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2152) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2152) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
212
Text files
249
Unknown types
39
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2472 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabA12A.tmp | — | |
MD5:— | SHA256:— | |||
| 2472 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarA12B.tmp | — | |
MD5:— | SHA256:— | |||
| 2152 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2472 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EB2C4AB8B68FFA4B7733A9139239A396_D76DB901EE986B889F30D8CC06229E2D | binary | |
MD5:— | SHA256:— | |||
| 2472 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EB2C4AB8B68FFA4B7733A9139239A396_D76DB901EE986B889F30D8CC06229E2D | der | |
MD5:— | SHA256:— | |||
| 2472 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\banner-styles[1].css | text | |
MD5:— | SHA256:— | |||
| 2472 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\223DE96EE265046957A660ED7C9DD9E7_EFF9B9BA98DEAA773F261FA85A0B1771 | der | |
MD5:— | SHA256:— | |||
| 2472 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\223DE96EE265046957A660ED7C9DD9E7_EFF9B9BA98DEAA773F261FA85A0B1771 | binary | |
MD5:— | SHA256:— | |||
| 2472 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\playback.bundle[1].js | text | |
MD5:— | SHA256:— | |||
| 2472 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\www.youareanidiot[1].htm | html | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
157
DNS requests
103
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2640 | chrome.exe | GET | 204 | 172.217.29.67:80 | http://csi.gstatic.com/csi?v=3&s=gapi_module&action=gapi_iframes__googleapis_cli12&it=mli.15,mei.5&tbsrt=887&tran=15&e=abc_l0,abc_m0,abc_pgapi_iframes__googleapis_cli12,abc_u0&rt= | US | — | — | whitelisted |
2640 | chrome.exe | GET | 302 | 172.217.23.142:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjY5QUFXTEQwc2RPVXhRY3picjhxblh1dw/7619.603.0.2_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 525 b | whitelisted |
2472 | iexplore.exe | GET | 200 | 192.124.249.41:80 | http://ocsp.godaddy.com//MEQwQjBAMD4wPDAJBgUrDgMCGgUABBTkIInKBAzXkF0Qh0pel3lfHJ9GPAQU0sSw0pHUTBFxs2HLPaH%2B3ahq1OMCAxvnFQ%3D%3D | US | der | 1.66 Kb | whitelisted |
2640 | chrome.exe | GET | 304 | 2.21.78.252:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | unknown | compressed | 57.0 Kb | whitelisted |
2152 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2472 | iexplore.exe | GET | 200 | 192.124.249.24:80 | http://ocsp.godaddy.com//MEQwQjBAMD4wPDAJBgUrDgMCGgUABBTkIInKBAzXkF0Qh0pel3lfHJ9GPAQU0sSw0pHUTBFxs2HLPaH%2B3ahq1OMCAxvnFQ%3D%3D | US | der | 1.66 Kb | whitelisted |
2472 | iexplore.exe | GET | 200 | 192.124.249.41:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | US | der | 1.69 Kb | whitelisted |
2152 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2640 | chrome.exe | GET | 302 | 172.217.23.142:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 520 b | whitelisted |
2640 | chrome.exe | GET | 200 | 74.125.4.203:80 | http://r5---sn-aigzrner.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjY5QUFXTEQwc2RPVXhRY3picjhxblh1dw/7619.603.0.2_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mh=Qx&mip=185.217.117.39&mm=28&mn=sn-aigzrner&ms=nvh&mt=1590915852&mv=m&mvi=4&pl=25&shardbypass=yes | US | crx | 816 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2472 | iexplore.exe | 207.241.233.214:443 | web.archive.org | Internet Archive | US | suspicious |
2472 | iexplore.exe | 192.124.249.41:80 | ocsp.godaddy.com | Sucuri | US | suspicious |
2472 | iexplore.exe | 192.124.249.24:80 | ocsp.godaddy.com | Sucuri | US | suspicious |
2152 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2472 | iexplore.exe | 207.241.224.2:443 | archive.org | Internet Archive | US | malicious |
2472 | iexplore.exe | 207.241.225.95:443 | analytics.archive.org | Internet Archive | US | unknown |
2152 | iexplore.exe | 207.241.233.214:443 | web.archive.org | Internet Archive | US | suspicious |
2640 | chrome.exe | 172.217.21.195:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2640 | chrome.exe | 216.58.208.35:443 | www.google.com.ua | Google Inc. | US | whitelisted |
2640 | chrome.exe | 216.58.212.141:443 | accounts.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
web.archive.org |
| whitelisted |
ocsp.godaddy.com |
| whitelisted |
archive.org |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
analytics.archive.org |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com.ua |
| whitelisted |
fonts.googleapis.com |
| whitelisted |