| File name: | 607c020ccd8e87bd7fd91dab66479fe0.exe |
| Full analysis: | https://app.any.run/tasks/234ea5a2-9e49-4950-a73a-fd0709d43193 |
| Verdict: | Malicious activity |
| Analysis date: | December 04, 2023, 11:37:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 607C020CCD8E87BD7FD91DAB66479FE0 |
| SHA1: | 21002F1D6D8F026CDA8AB2C4001EEED6E981B330 |
| SHA256: | B58D7685ECCA1A16F4702A50E623B41CA47422AA9CE3781FE422E752EC52B76B |
| SSDEEP: | 12288:5V5lAvYHb82Mx2YXVR8nLo20llVSZr5utkY9yKwrjr:5VPAvYHb82MAYXVKnLohl/SZdutkY9yL |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- 607c020ccd8e87bd7fd91dab66479fe0.exe (PID: 2644)
Reads the Internet Settings
- 607c020ccd8e87bd7fd91dab66479fe0.exe (PID: 2644)
Reads security settings of Internet Explorer
- 607c020ccd8e87bd7fd91dab66479fe0.exe (PID: 2644)
Reads settings of System Certificates
- 607c020ccd8e87bd7fd91dab66479fe0.exe (PID: 2644)
Checks Windows Trust Settings
- 607c020ccd8e87bd7fd91dab66479fe0.exe (PID: 2644)
Reads Internet Explorer settings
- 607c020ccd8e87bd7fd91dab66479fe0.exe (PID: 2644)
INFO
Create files in a temporary directory
- 607c020ccd8e87bd7fd91dab66479fe0.exe (PID: 2644)
Reads the computer name
- 607c020ccd8e87bd7fd91dab66479fe0.exe (PID: 2644)
- wmpnscfg.exe (PID: 2544)
Checks supported languages
- 607c020ccd8e87bd7fd91dab66479fe0.exe (PID: 2644)
- wmpnscfg.exe (PID: 2544)
Checks proxy server information
- 607c020ccd8e87bd7fd91dab66479fe0.exe (PID: 2644)
Reads the machine GUID from the registry
- 607c020ccd8e87bd7fd91dab66479fe0.exe (PID: 2644)
Creates files or folders in the user directory
- 607c020ccd8e87bd7fd91dab66479fe0.exe (PID: 2644)
Manual execution by a user
- wmpnscfg.exe (PID: 2544)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (38.2) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (37.5) |
| .dll | | | Win32 Dynamic Link Library (generic) (9.2) |
| .exe | | | Win32 Executable (generic) (6.3) |
| .exe | | | Win16/32 Executable Delphi generic (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:20 00:22:17+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 364544 |
| InitializedDataSize: | 8192 |
| UninitializedDataSize: | 921600 |
| EntryPoint: | 0x13aaf0 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.8.0.0 |
| ProductVersionNumber: | 3.8.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Windows, Chinese (Simplified) |
| CompanyName: | 桂林老兵站 |
| FileDescription: | 网站安全检测工具 |
| FileVersion: | 3.8.0.0 |
| InternalName: | 桂林老兵站 |
| LegalCopyright: | www.gxgl.com&www.gxgl.net |
| LegalTrademarks: | - |
| OriginalFileName: | - |
| ProductName: | WebTool |
| ProductVersion: | 3.8.0.0 |
| Comments: | 主要用于网站的安全检测。 |
Total processes
38
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2544 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2644 | "C:\Users\admin\AppData\Local\Temp\607c020ccd8e87bd7fd91dab66479fe0.exe" | C:\Users\admin\AppData\Local\Temp\607c020ccd8e87bd7fd91dab66479fe0.exe | explorer.exe | ||||||||||||
User: admin Company: 桂林老兵站 Integrity Level: MEDIUM Description: 网站安全检测工具 Exit code: 0 Version: 3.8.0.0 Modules
| |||||||||||||||
Total events
10 585
Read events
10 555
Write events
29
Delete events
1
Modification events
| (PID) Process: | (2644) 607c020ccd8e87bd7fd91dab66479fe0.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2644) 607c020ccd8e87bd7fd91dab66479fe0.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2644) 607c020ccd8e87bd7fd91dab66479fe0.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2644) 607c020ccd8e87bd7fd91dab66479fe0.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2644) 607c020ccd8e87bd7fd91dab66479fe0.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2644) 607c020ccd8e87bd7fd91dab66479fe0.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2644) 607c020ccd8e87bd7fd91dab66479fe0.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2644) 607c020ccd8e87bd7fd91dab66479fe0.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005A010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2644) 607c020ccd8e87bd7fd91dab66479fe0.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad\{FCC67766-6201-4AD1-A6B8-2F4553C93D47} |
| Operation: | write | Name: | WpadDecisionReason |
Value: 1 | |||
| (PID) Process: | (2644) 607c020ccd8e87bd7fd91dab66479fe0.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad\{FCC67766-6201-4AD1-A6B8-2F4553C93D47} |
| Operation: | write | Name: | WpadDecision |
Value: 0 | |||
Executable files
0
Suspicious files
13
Text files
62
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2644 | 607c020ccd8e87bd7fd91dab66479fe0.exe | C:\Users\admin\AppData\Local\Temp\Wconfig | text | |
MD5:5259E286959F286CC7591B24E7BB39E3 | SHA256:82415B70C6CC267226221D10BFE048C2446B70311D9956DA8F7983FBA2289786 | |||
| 2644 | 607c020ccd8e87bd7fd91dab66479fe0.exe | C:\Users\admin\AppData\Local\Temp\WebPath | text | |
MD5:32F7AE12C3C164ACD6BE3EE4A27DF10E | SHA256:588F30B0312B23E29724AE3718EB9B8DFDEE22FBA8AE50A0528DE8629F1D1566 | |||
| 2644 | 607c020ccd8e87bd7fd91dab66479fe0.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\6XZKW1NI.htm | html | |
MD5:D4B691CD9D99117B2EA34586D3E7EEB8 | SHA256:2178EEDD5723A6AC22E94EC59BDCD99229C87F3623753F5E199678242F0E90DE | |||
| 2644 | 607c020ccd8e87bd7fd91dab66479fe0.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\2VRSUH11.txt | text | |
MD5:68F1BBB99314E509D66F581D74A5ED3F | SHA256:A71963E183BECB7BE489B0485FCBAADED6BCFC2F6B912F21F2D89977454E3B96 | |||
| 2644 | 607c020ccd8e87bd7fd91dab66479fe0.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | der | |
MD5:AC89A852C2AAA3D389B2D2DD312AD367 | SHA256:0B720E19270C672F9B6E0EC40B468AC49376807DE08A814573FE038779534F45 | |||
| 2644 | 607c020ccd8e87bd7fd91dab66479fe0.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:264599C2F0E79D712D78E3B7AB1EDA7D | SHA256:0F11C0F75D737B2BAEF6701380166BCA719CA189C4F54495F92999161C416643 | |||
| 2644 | 607c020ccd8e87bd7fd91dab66479fe0.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:5D01960BFB443A039A24C10C568C4F2C | SHA256:46D6019043089190D69E15DBADF4D7512D22E340A6791B4C87C449E20A1D967D | |||
| 2644 | 607c020ccd8e87bd7fd91dab66479fe0.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\F2DDCD2B5F37625B82E81F4976CEE400_8FF5BE4204C5F704E3914BEF4952C317 | binary | |
MD5:030ECDE6BAE2A89FF5F53E4F1E6102F8 | SHA256:CB8ED24CF106108D4EE05549F8DB94CEB623DFCF6BF98AADE1031837CB95B0B5 | |||
| 2644 | 607c020ccd8e87bd7fd91dab66479fe0.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\MYVHLMBP.txt | text | |
MD5:9B148E863D73FCDA00E7B4948F75A667 | SHA256:C08A04FFB96DF963E32018C2D5A995A529D935862D57A39221F3554F6F6CAD1C | |||
| 2644 | 607c020ccd8e87bd7fd91dab66479fe0.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_9487BC0D4381A7CDEB9A8CC43F66D27C | binary | |
MD5:C6DE5238E22DC528C1A4D14DDFF90764 | SHA256:6386BC1692827128A46C01B954EBF2D5C2300987F0F1B2E0FC024FA27CB1D264 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
29
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
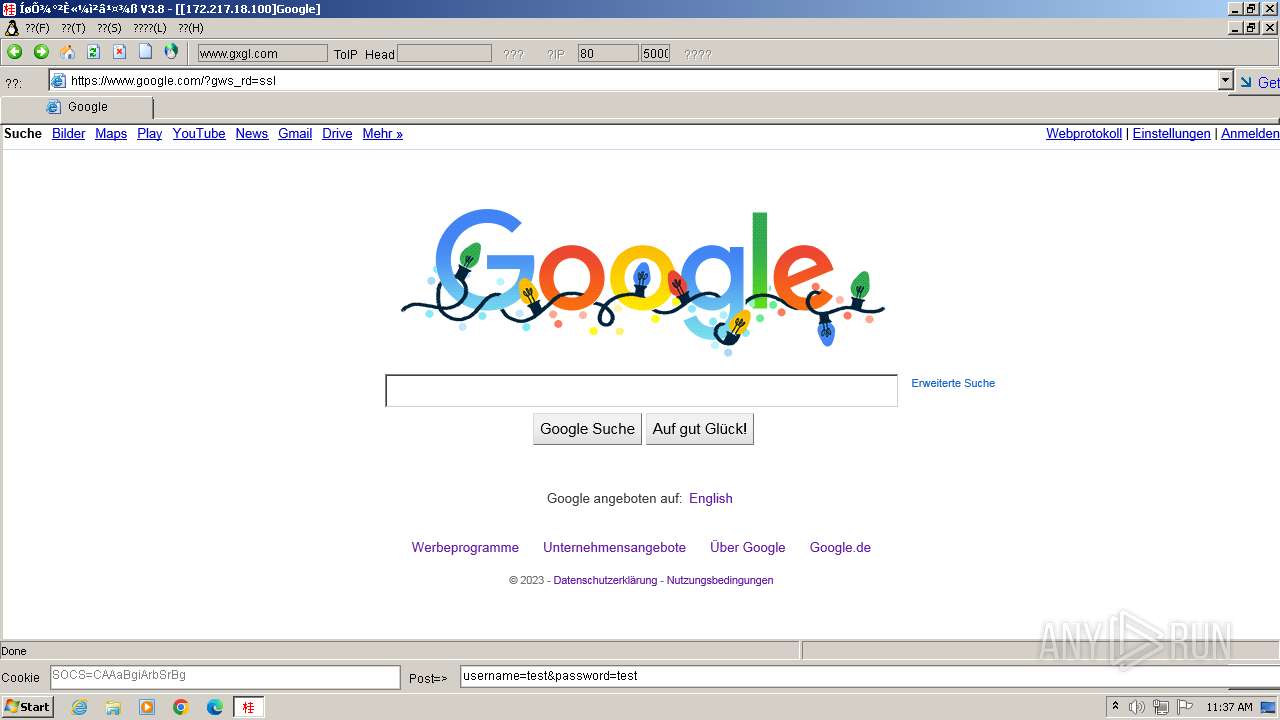
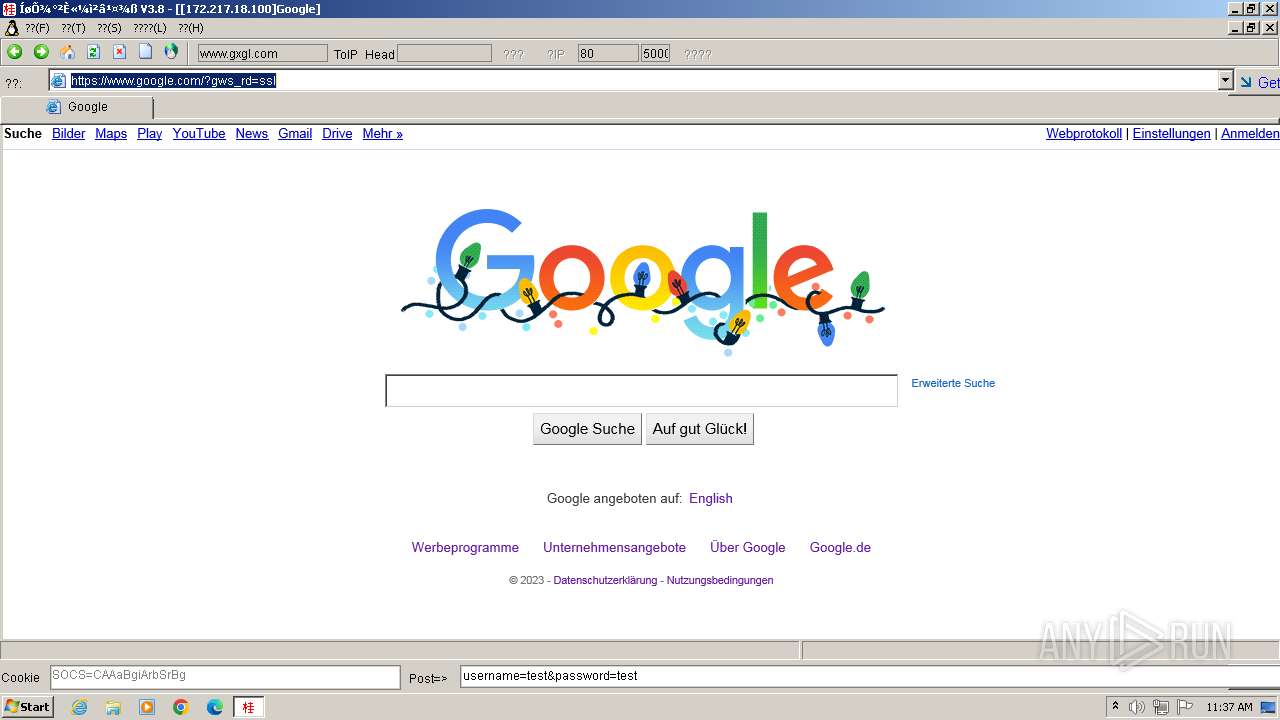
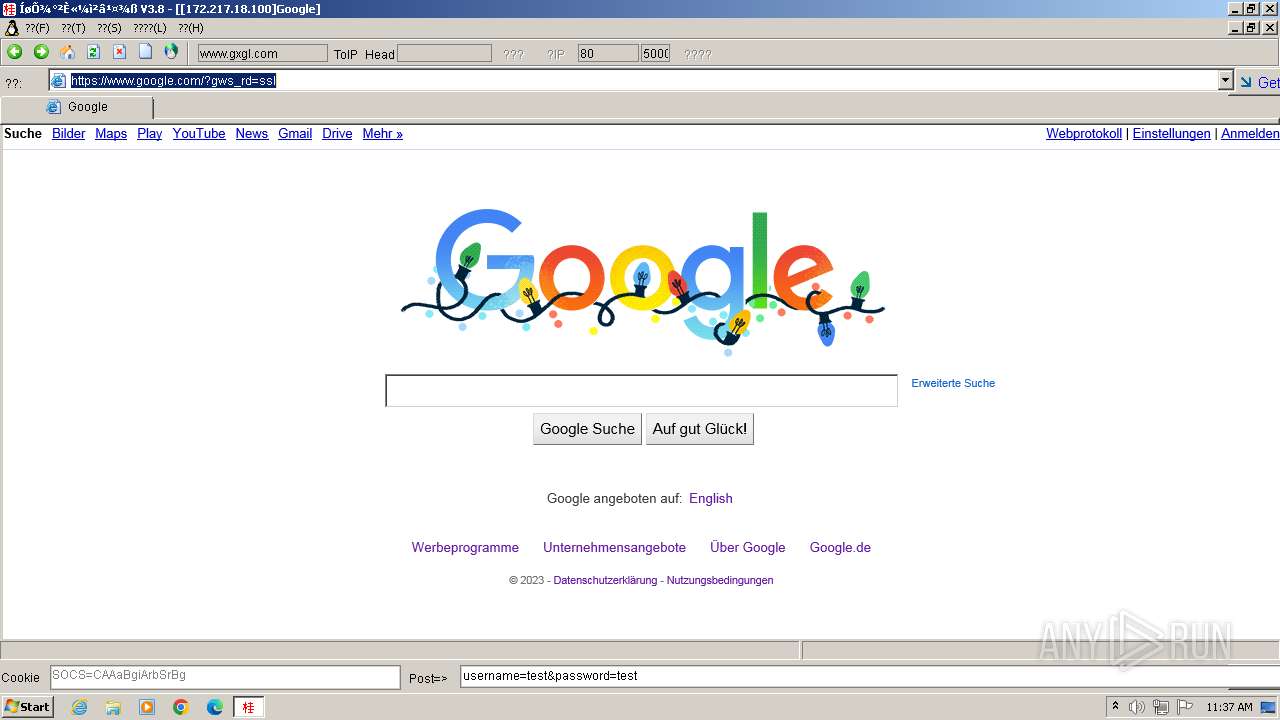
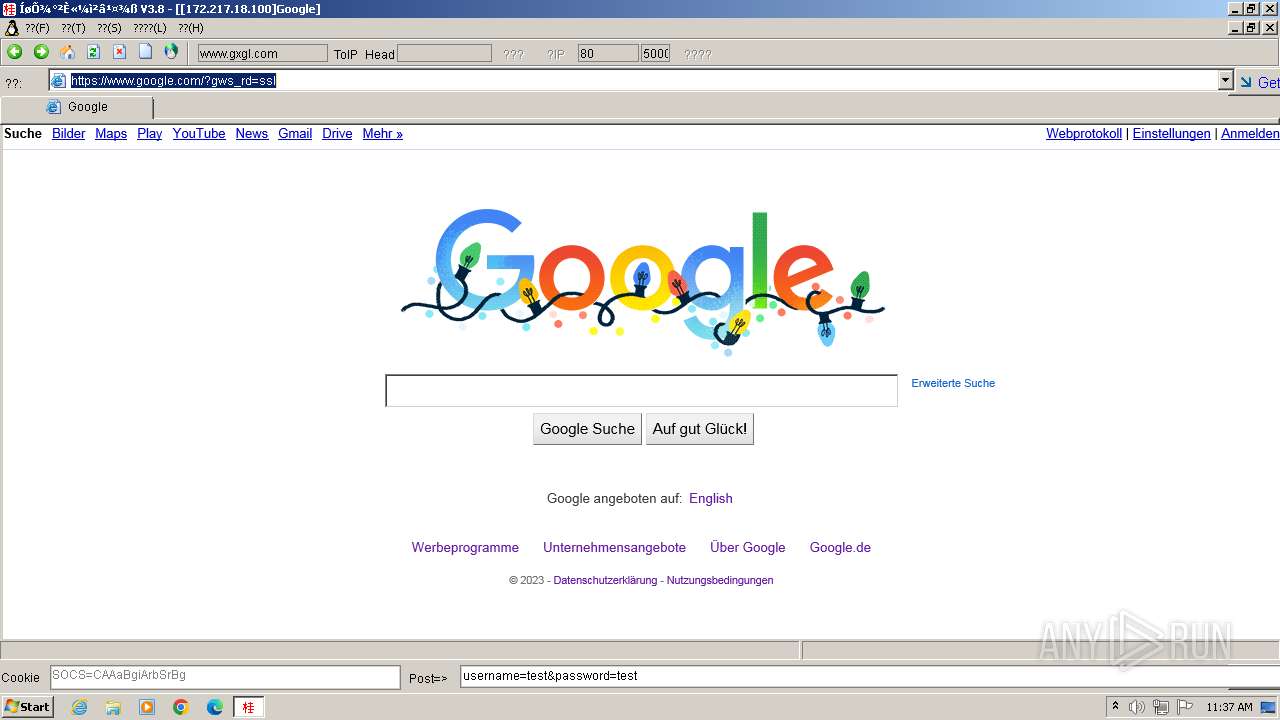
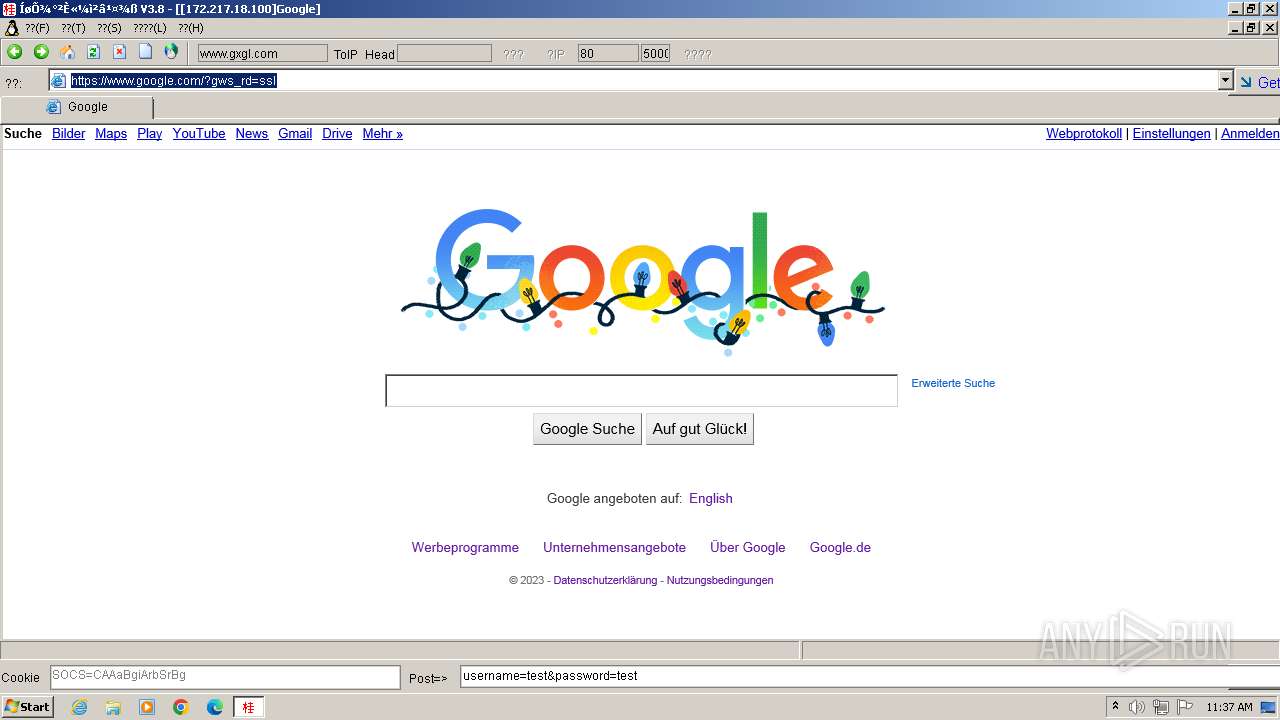
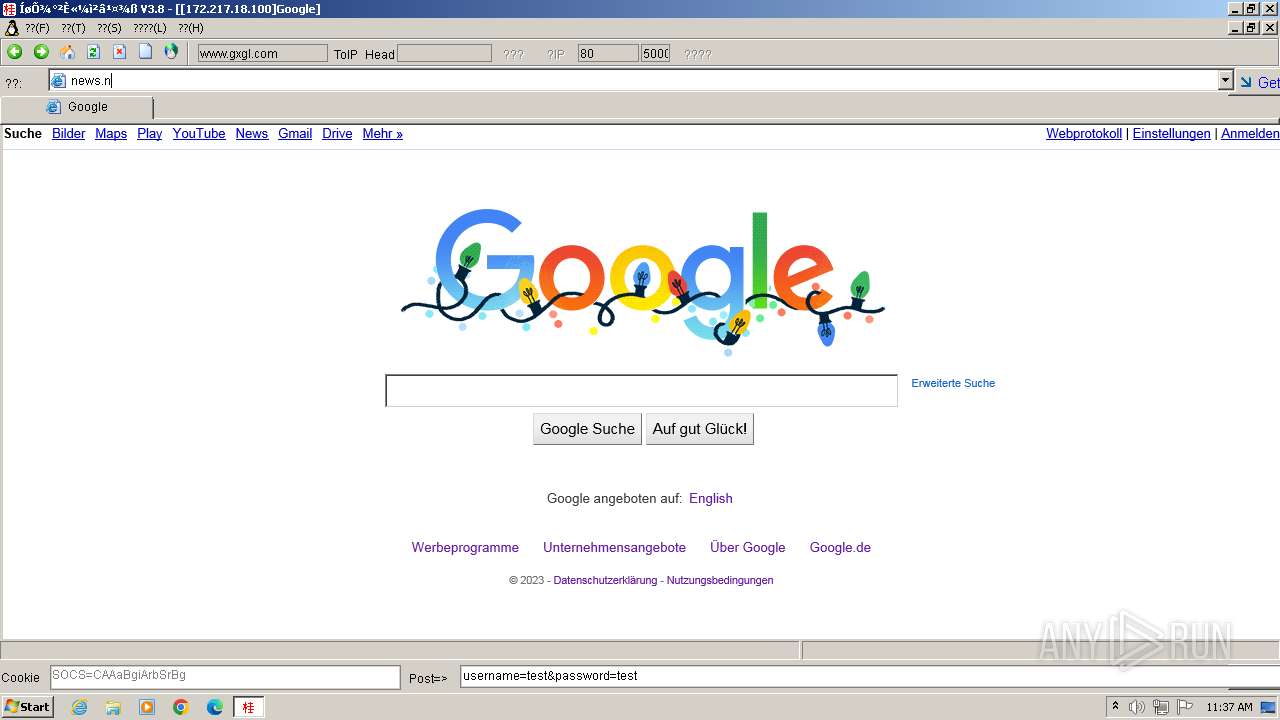
2644 | 607c020ccd8e87bd7fd91dab66479fe0.exe | GET | 302 | 172.217.18.100:80 | http://www.google.com/ | unknown | html | 231 b | unknown |
2644 | 607c020ccd8e87bd7fd91dab66479fe0.exe | GET | 301 | 142.250.186.46:80 | http://google.com/ | unknown | html | 219 b | unknown |
2644 | 607c020ccd8e87bd7fd91dab66479fe0.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c6d67f3a233f651e | unknown | compressed | 4.66 Kb | unknown |
2644 | 607c020ccd8e87bd7fd91dab66479fe0.exe | GET | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
2644 | 607c020ccd8e87bd7fd91dab66479fe0.exe | GET | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
2644 | 607c020ccd8e87bd7fd91dab66479fe0.exe | GET | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEF2rtEA6xK7GEl4nbt8ZZfk%3D | unknown | binary | 471 b | unknown |
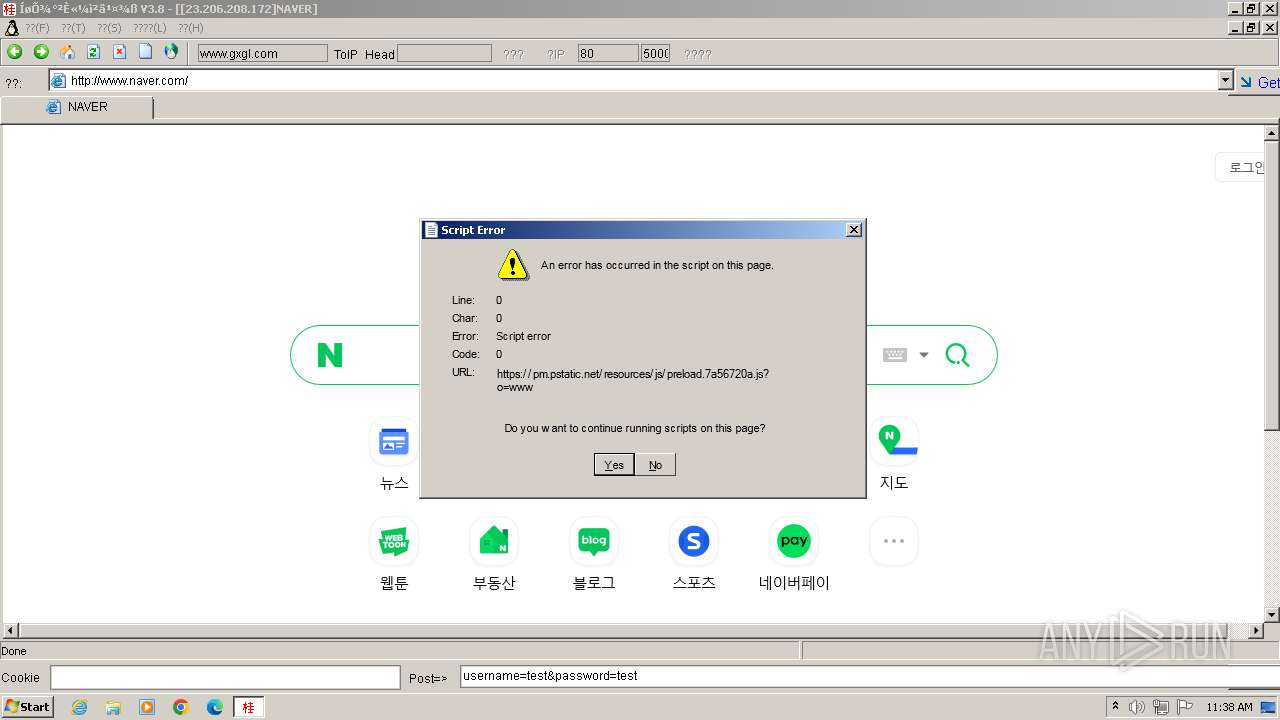
2644 | 607c020ccd8e87bd7fd91dab66479fe0.exe | GET | 302 | 23.206.208.172:80 | http://news.naver.com/ | unknown | — | — | unknown |
2644 | 607c020ccd8e87bd7fd91dab66479fe0.exe | GET | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCLPpgizFvtXApe3cL6kC3u | unknown | binary | 472 b | unknown |
2644 | 607c020ccd8e87bd7fd91dab66479fe0.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAVG%2Fhgj9%2BGUHaOfzhTEYXM%3D | unknown | binary | 471 b | unknown |
2644 | 607c020ccd8e87bd7fd91dab66479fe0.exe | GET | 302 | 23.206.208.172:80 | http://news.naver.com/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2644 | 607c020ccd8e87bd7fd91dab66479fe0.exe | 142.250.186.46:80 | google.com | GOOGLE | US | whitelisted |
2644 | 607c020ccd8e87bd7fd91dab66479fe0.exe | 172.217.18.100:80 | www.google.com | GOOGLE | US | whitelisted |
2644 | 607c020ccd8e87bd7fd91dab66479fe0.exe | 172.217.18.100:443 | www.google.com | GOOGLE | US | whitelisted |
2644 | 607c020ccd8e87bd7fd91dab66479fe0.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2644 | 607c020ccd8e87bd7fd91dab66479fe0.exe | 142.250.186.163:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
2644 | 607c020ccd8e87bd7fd91dab66479fe0.exe | 142.250.184.206:443 | clients1.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.google.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
clients1.google.com |
| whitelisted |
news.naver.com |
| unknown |
ocsp.digicert.com |
| whitelisted |
naver.com |
| unknown |
www.naver.com |
| whitelisted |
ssl.pstatic.net |
| whitelisted |