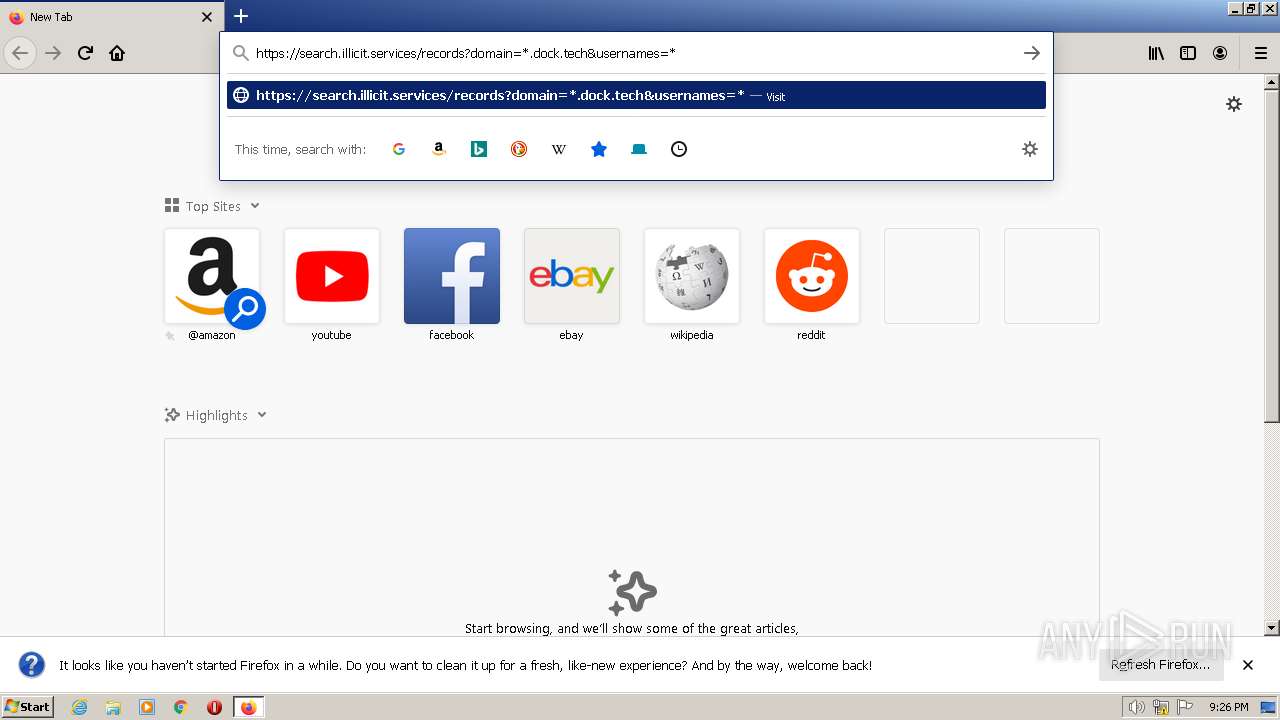
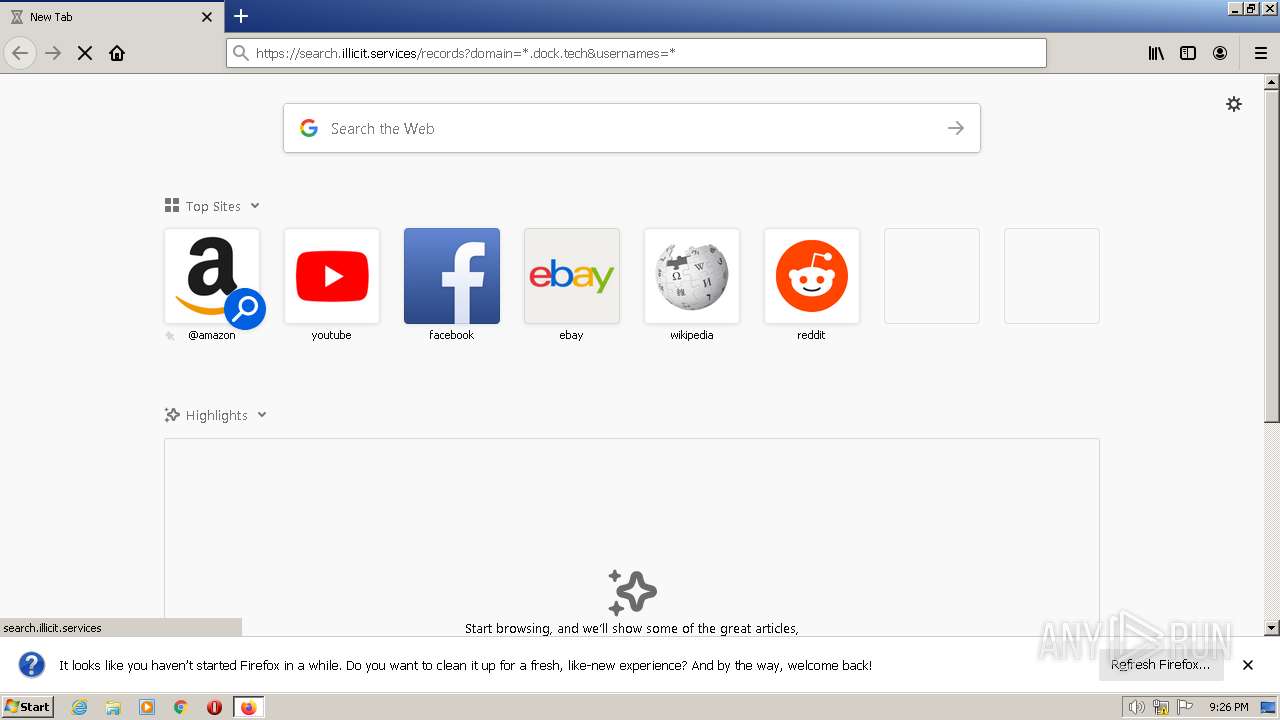
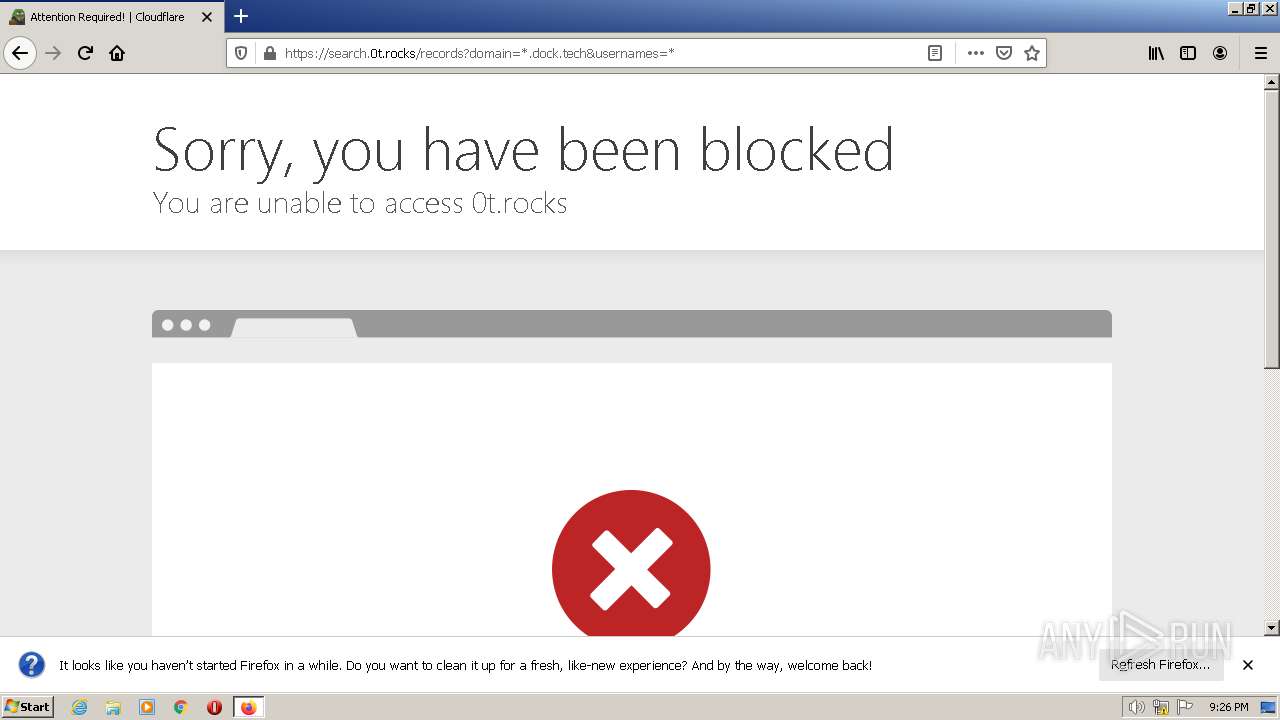
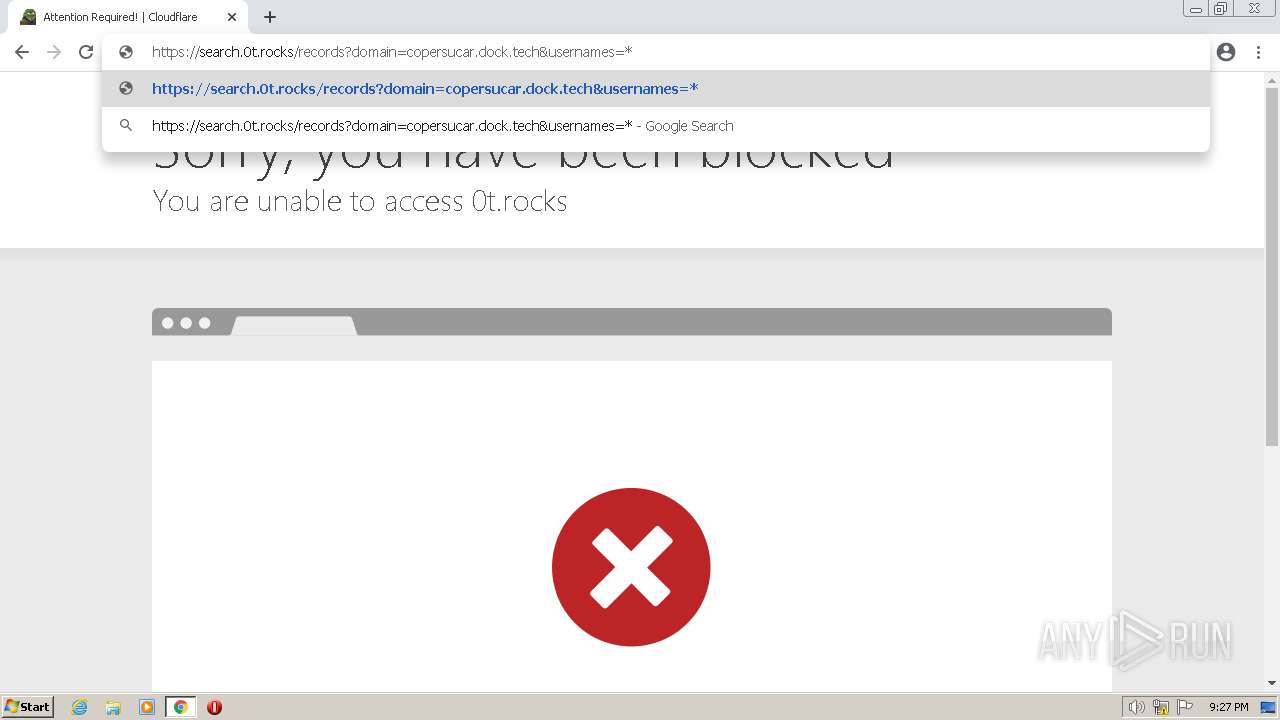
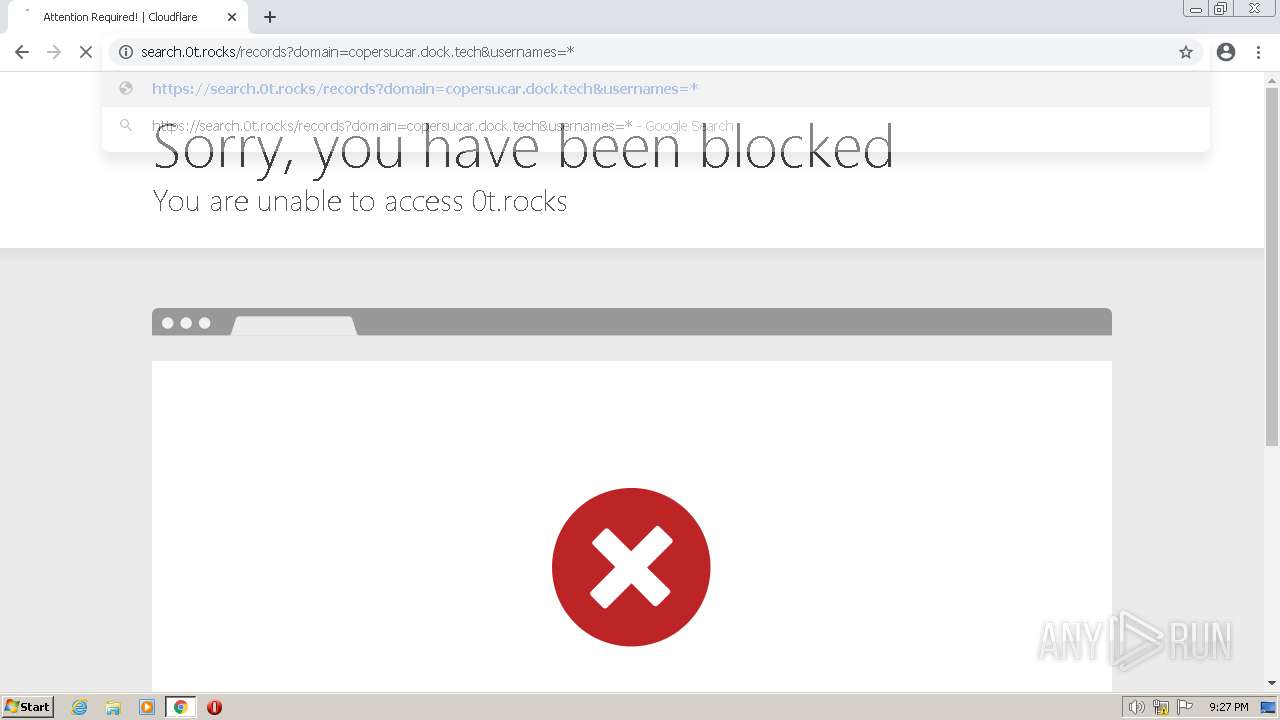
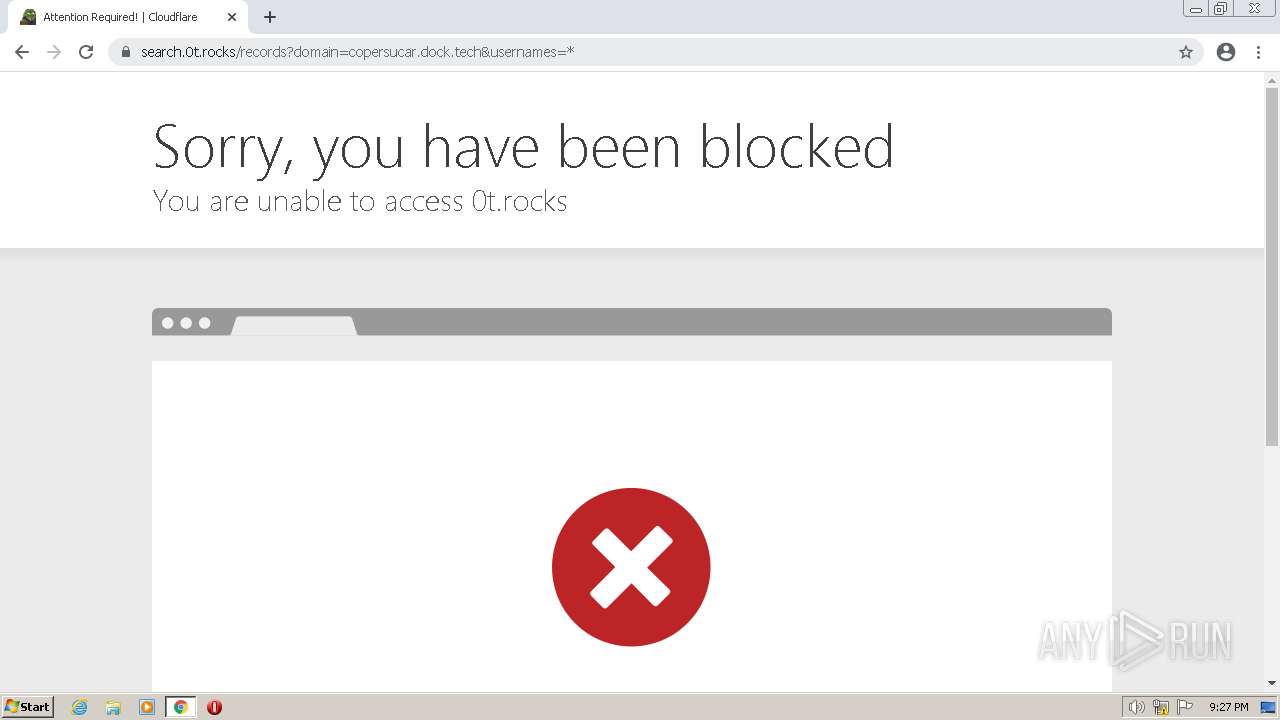
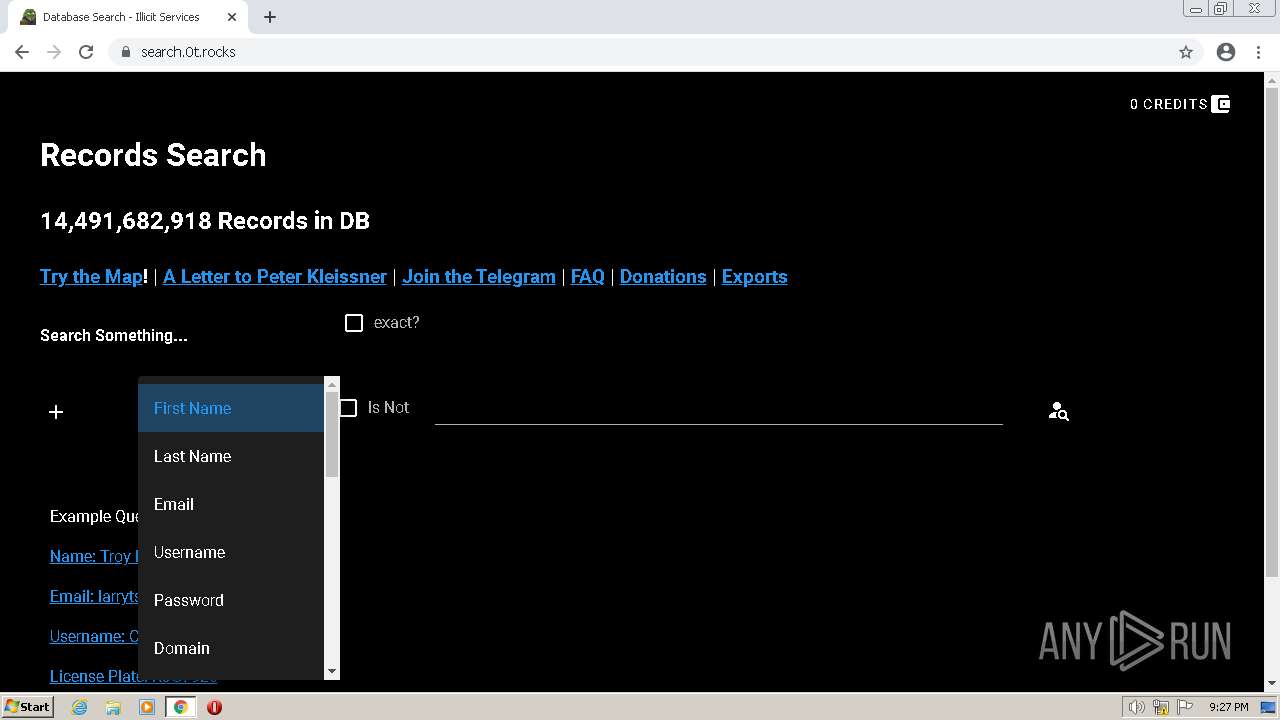
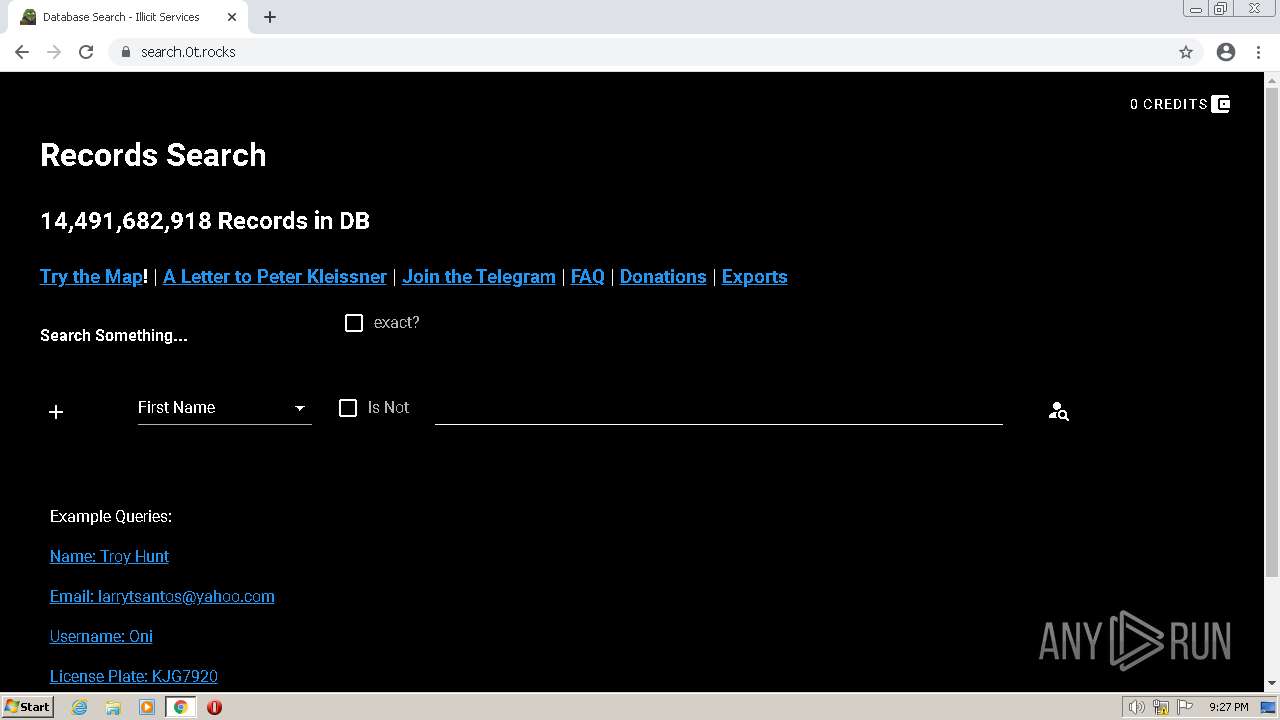
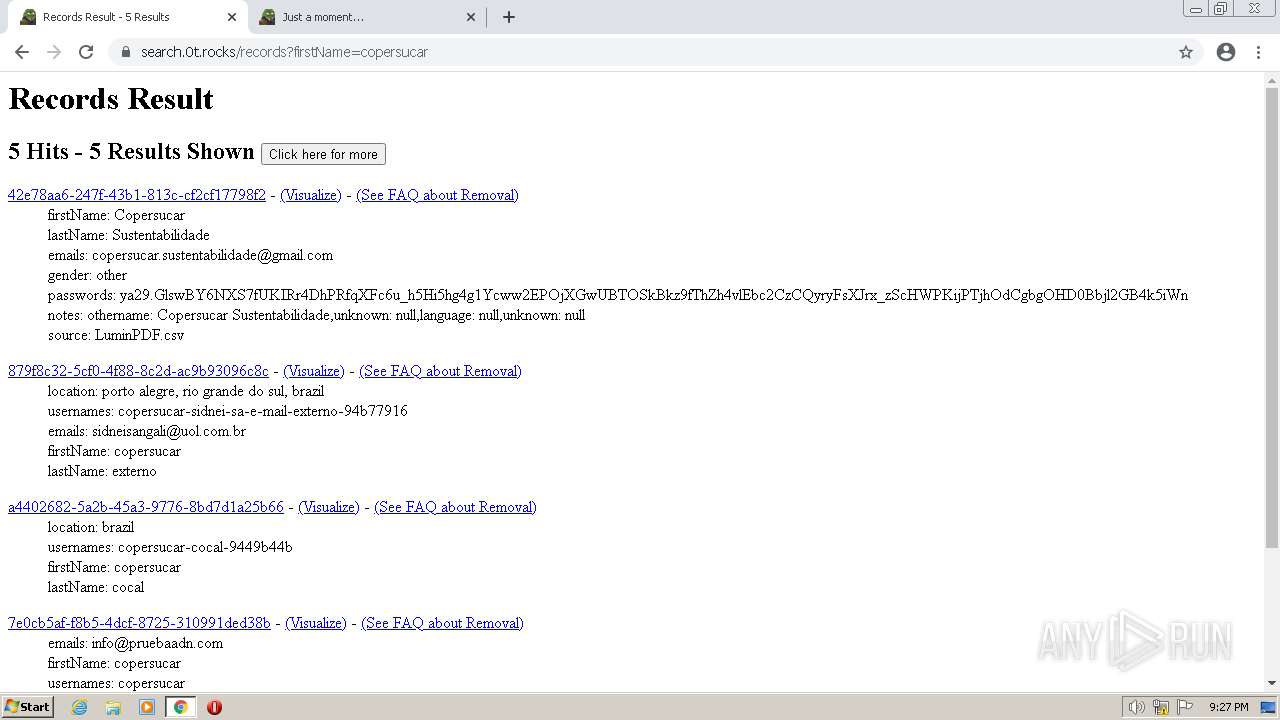
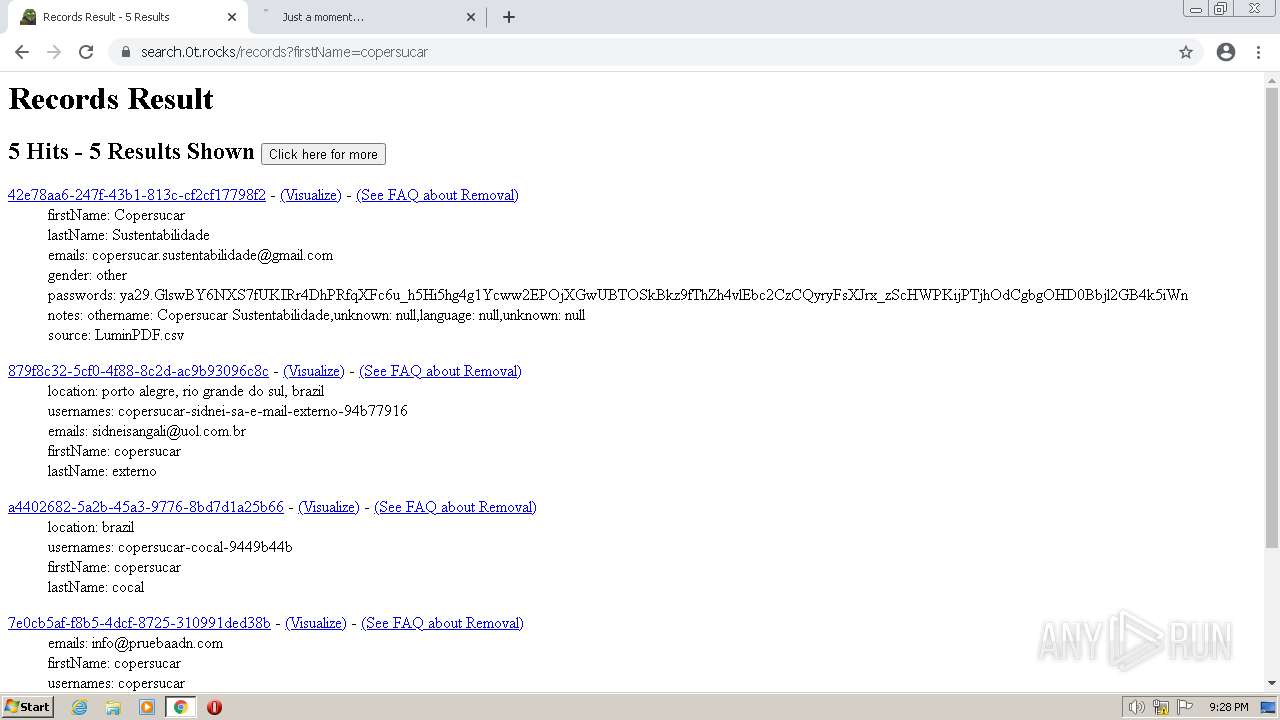
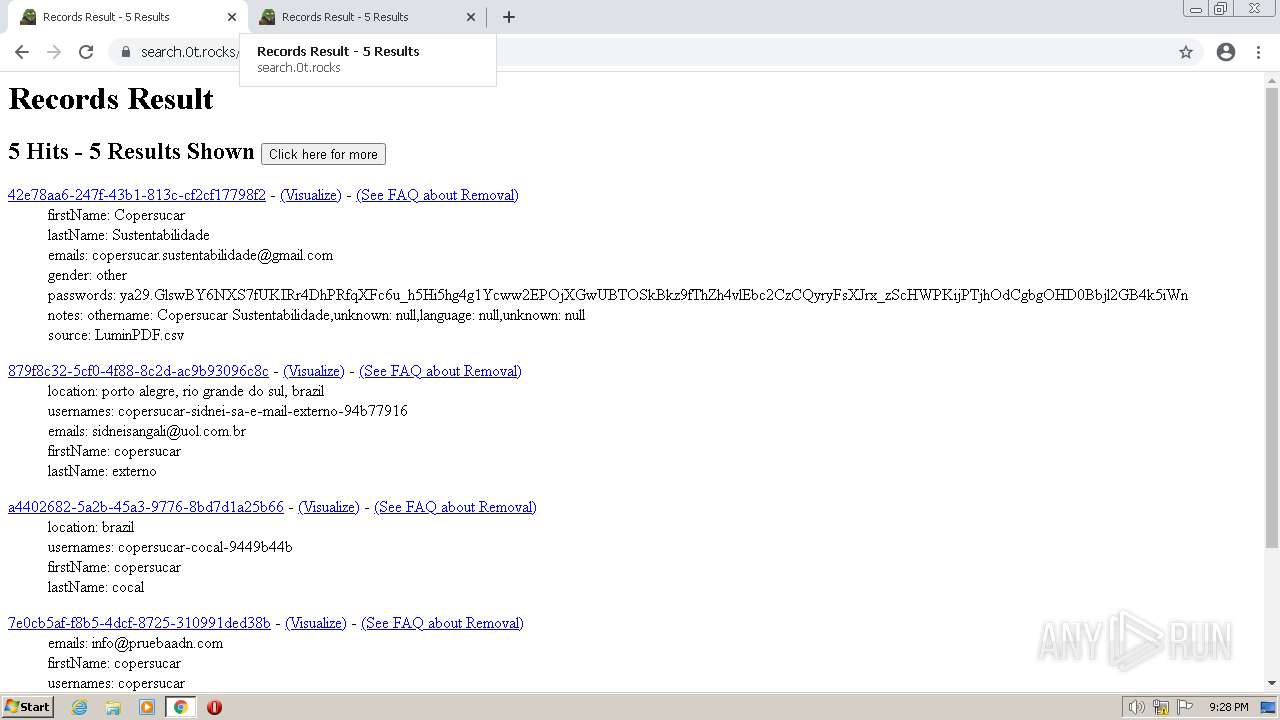
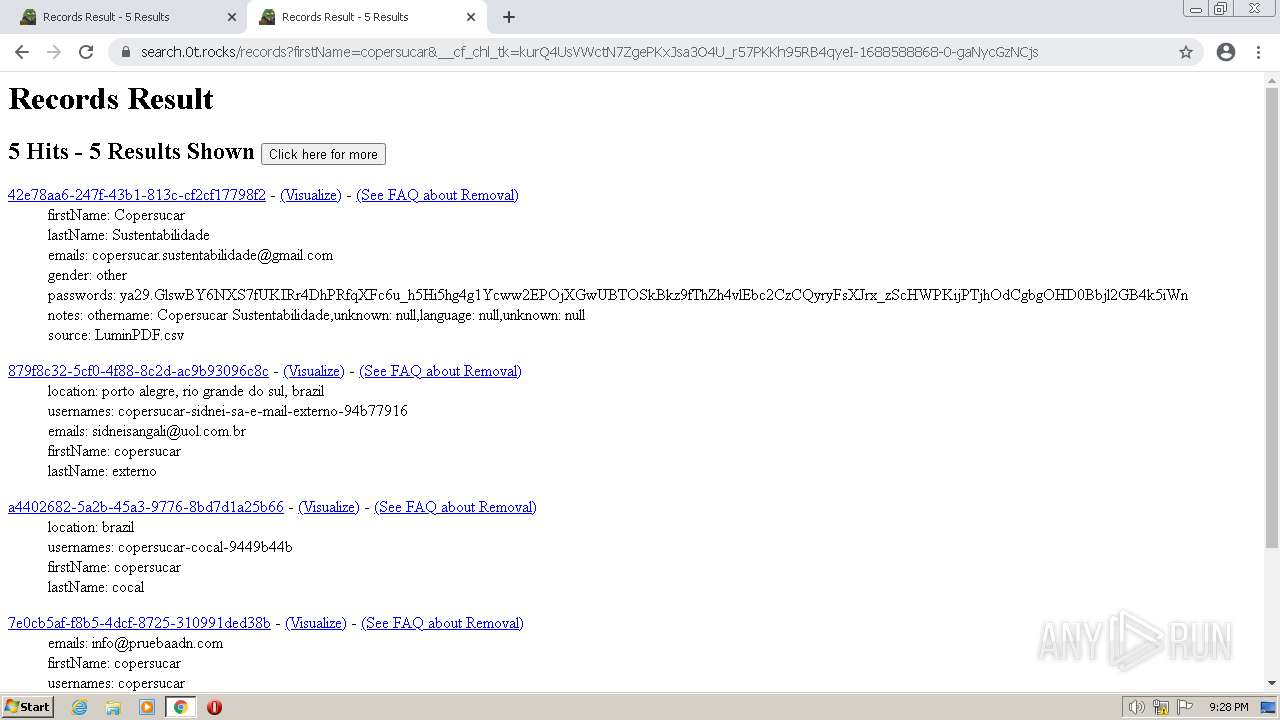
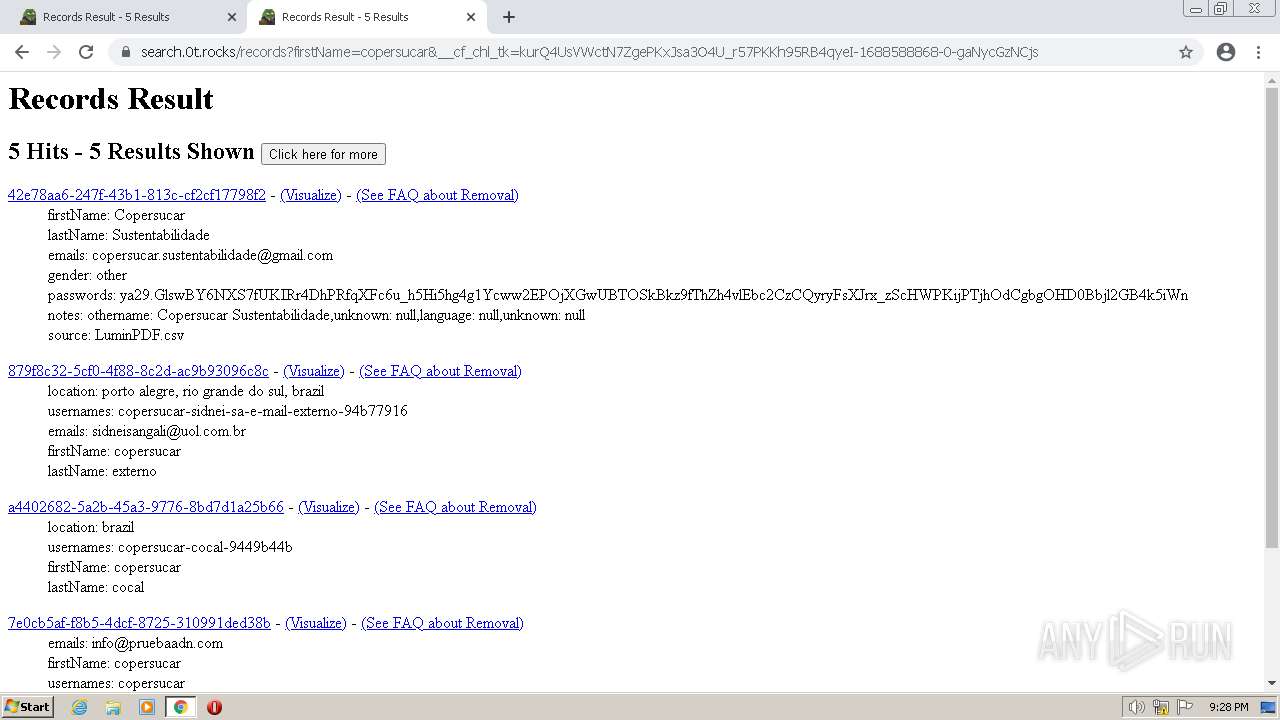
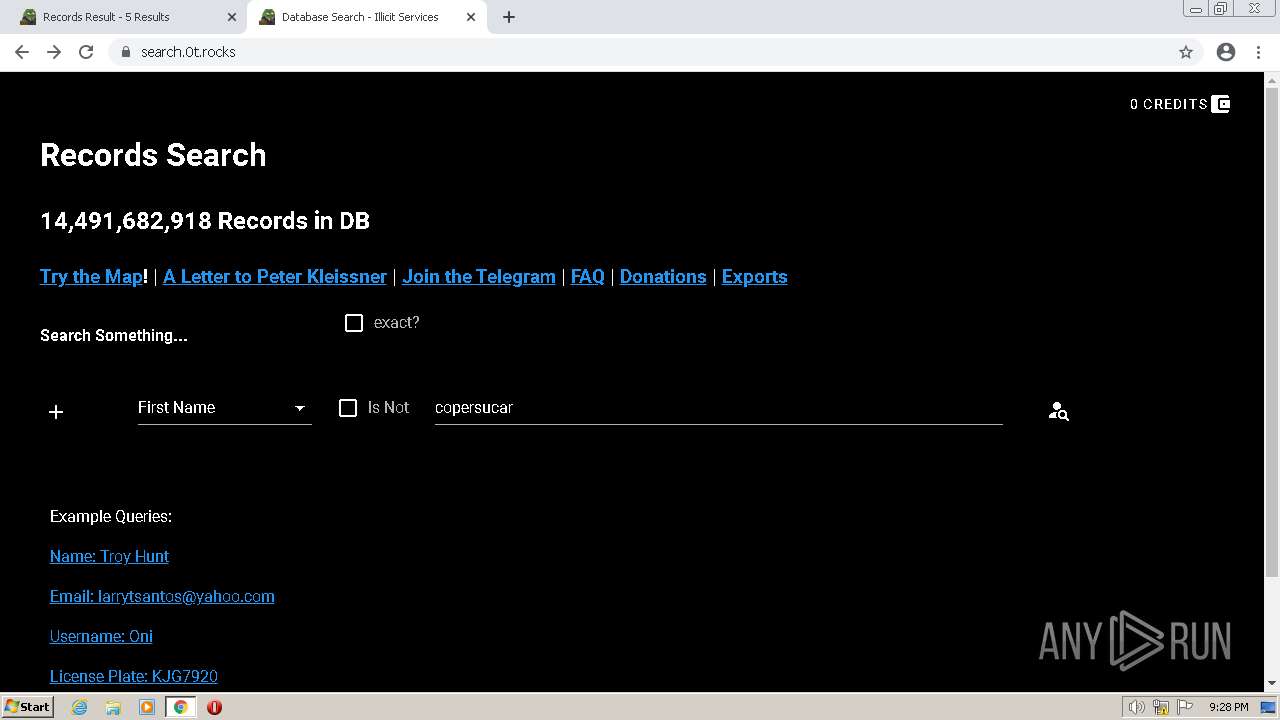
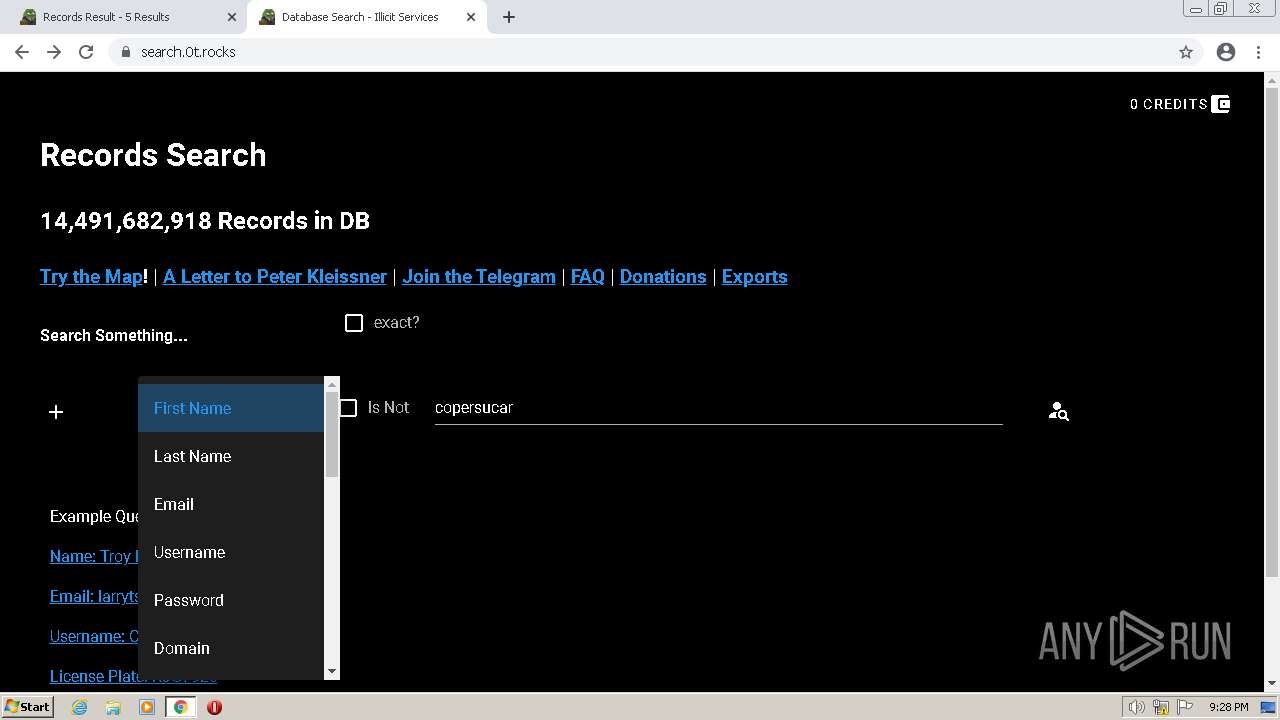
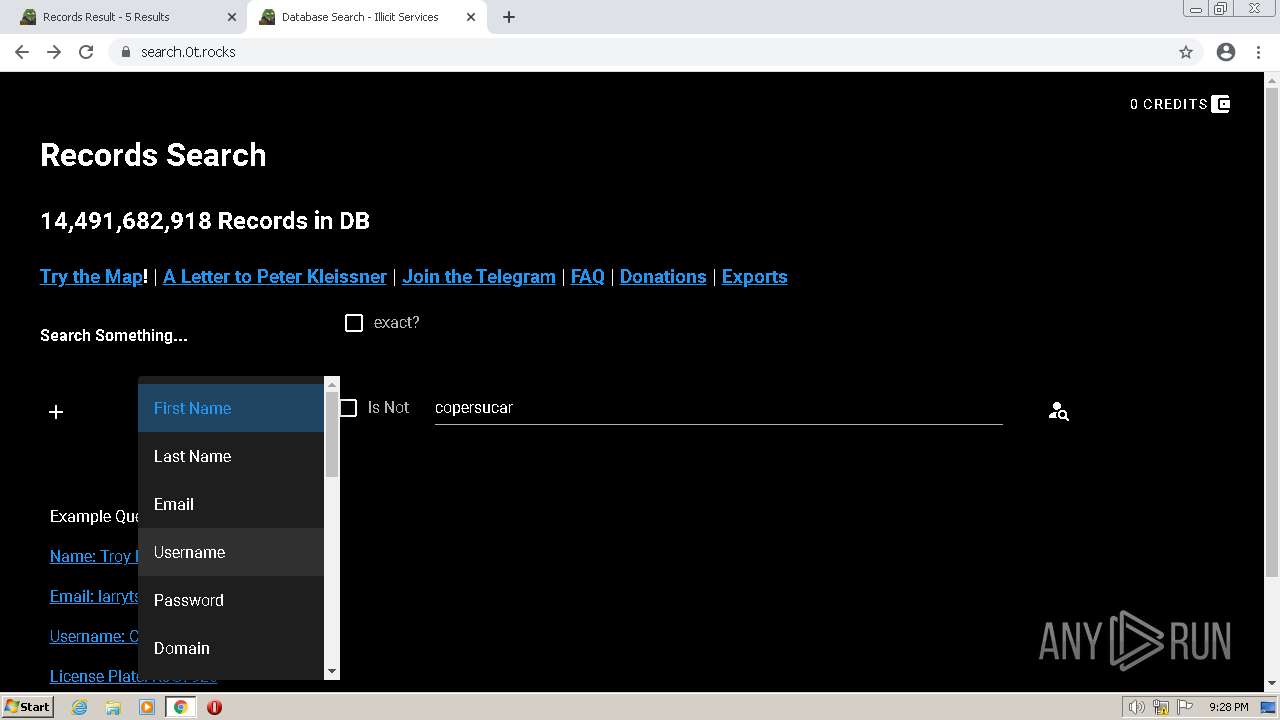
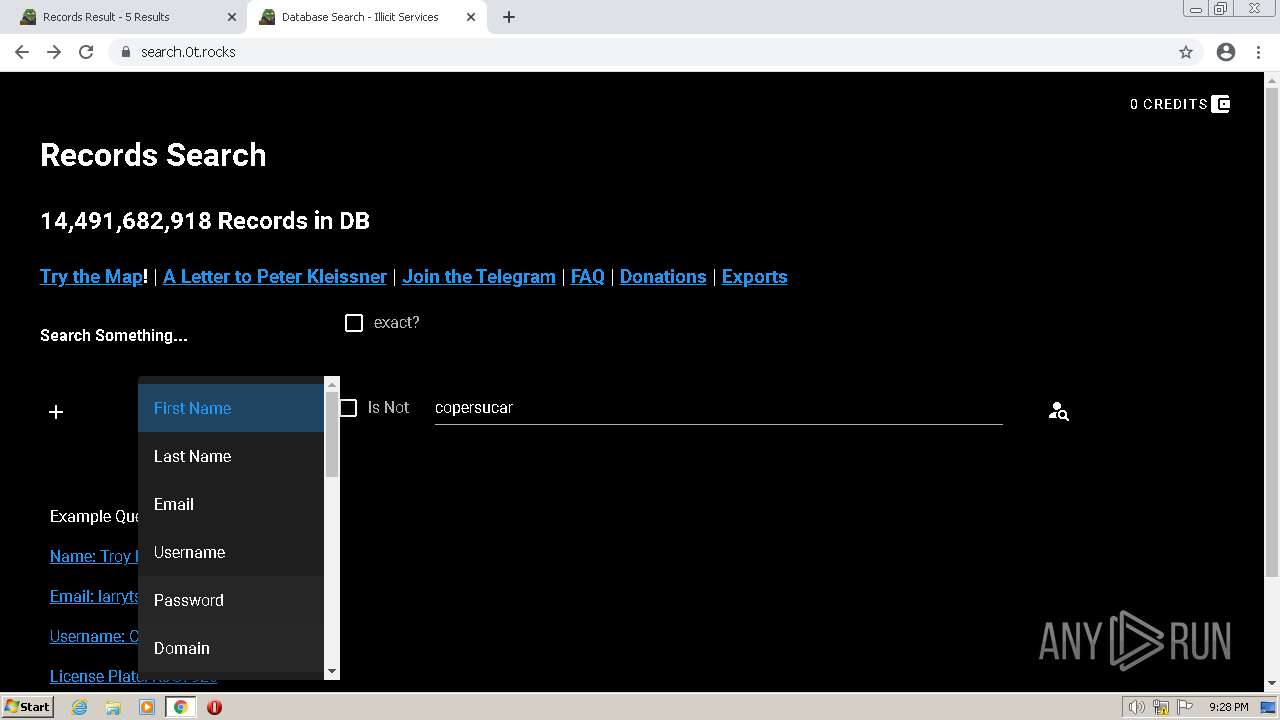
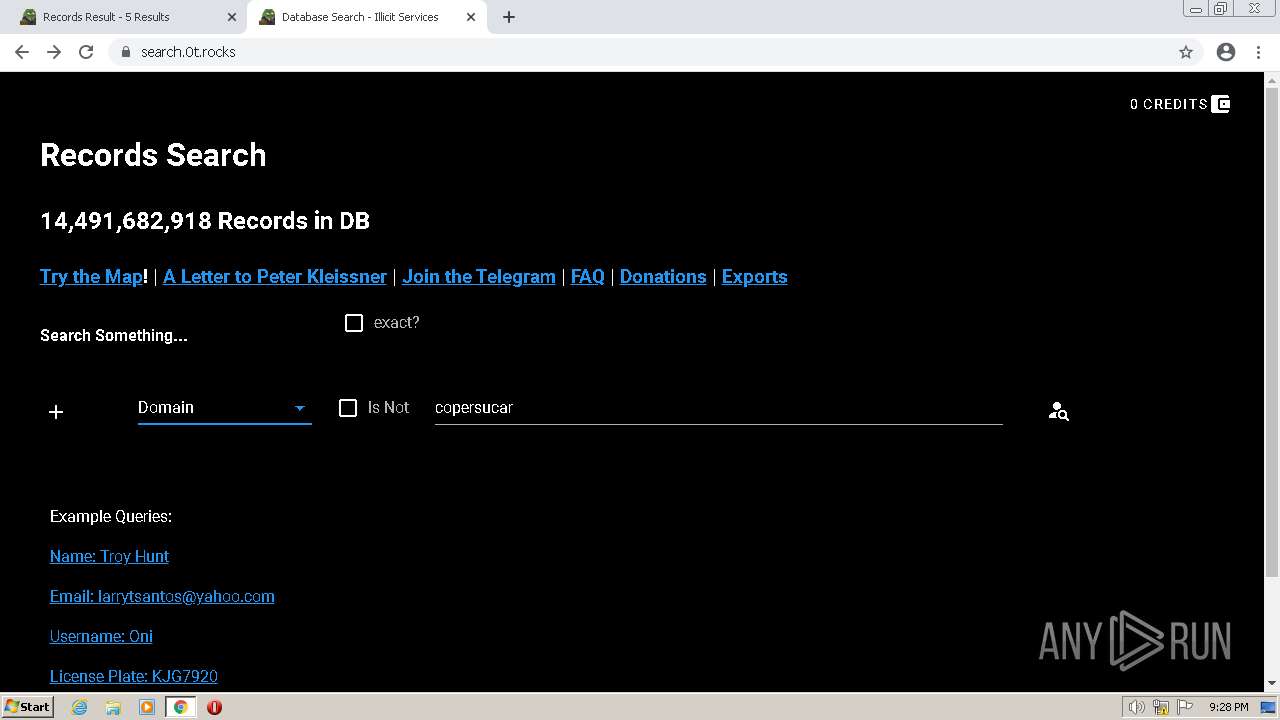
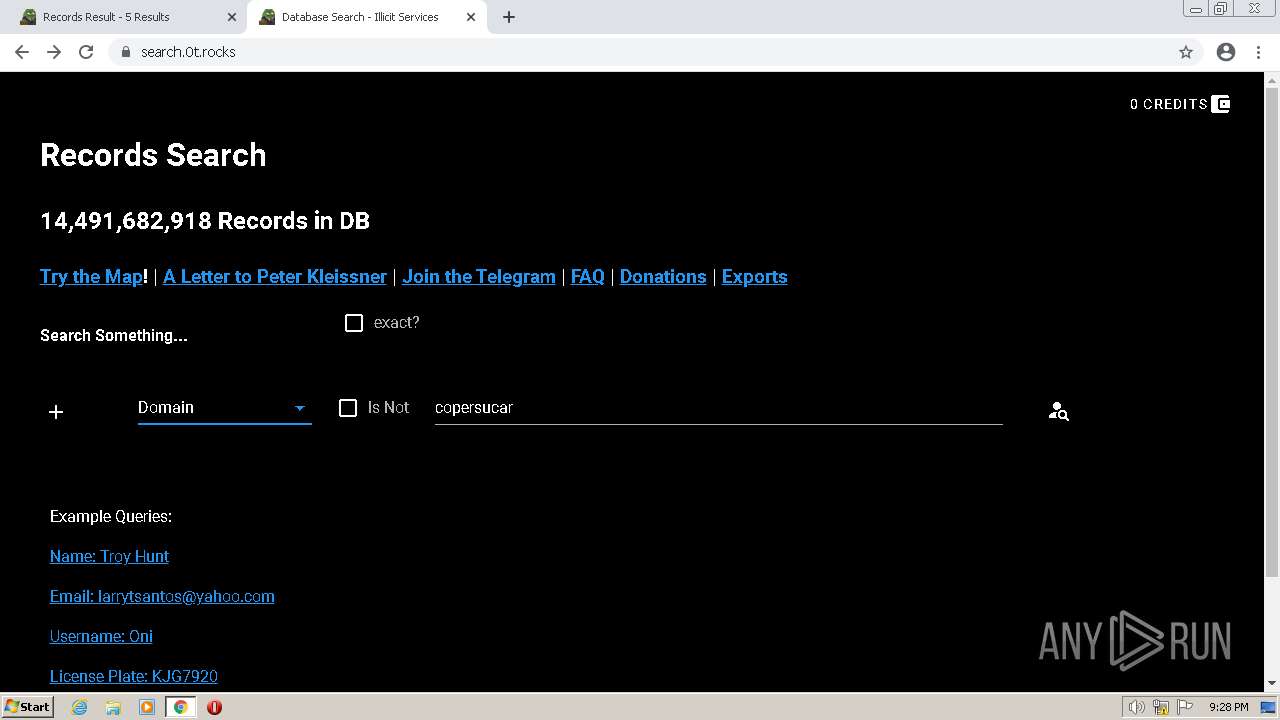
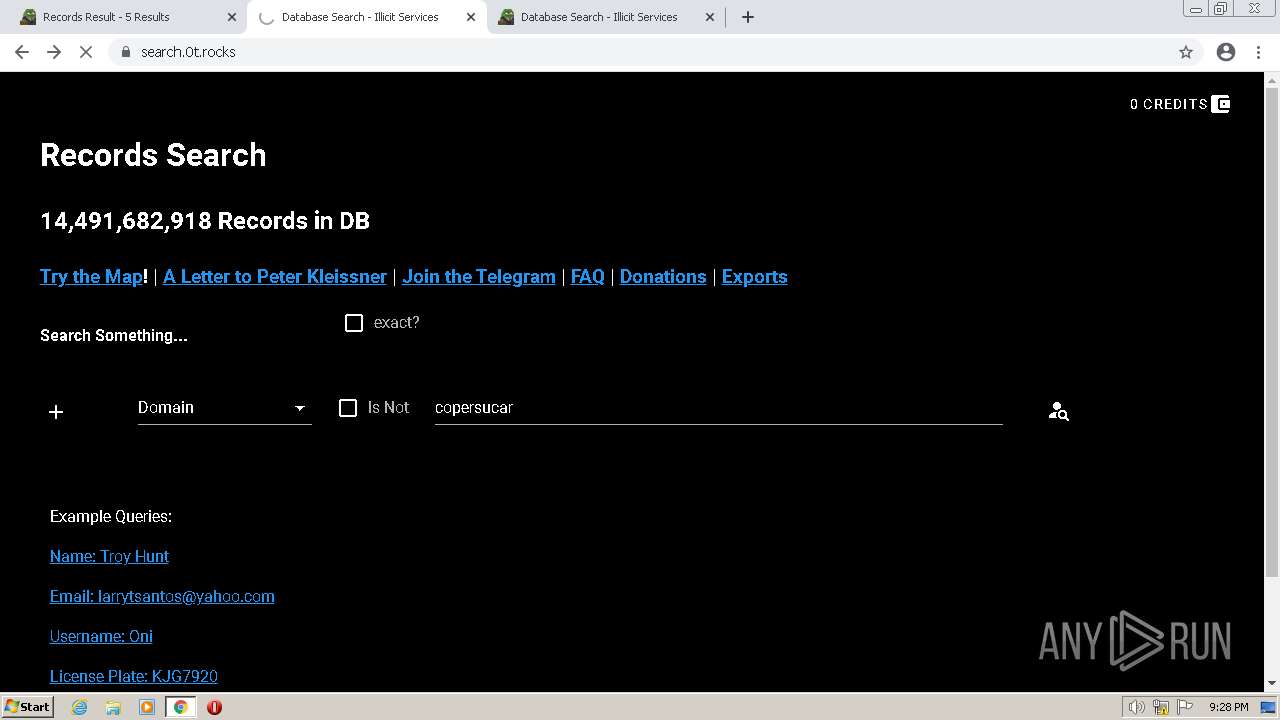
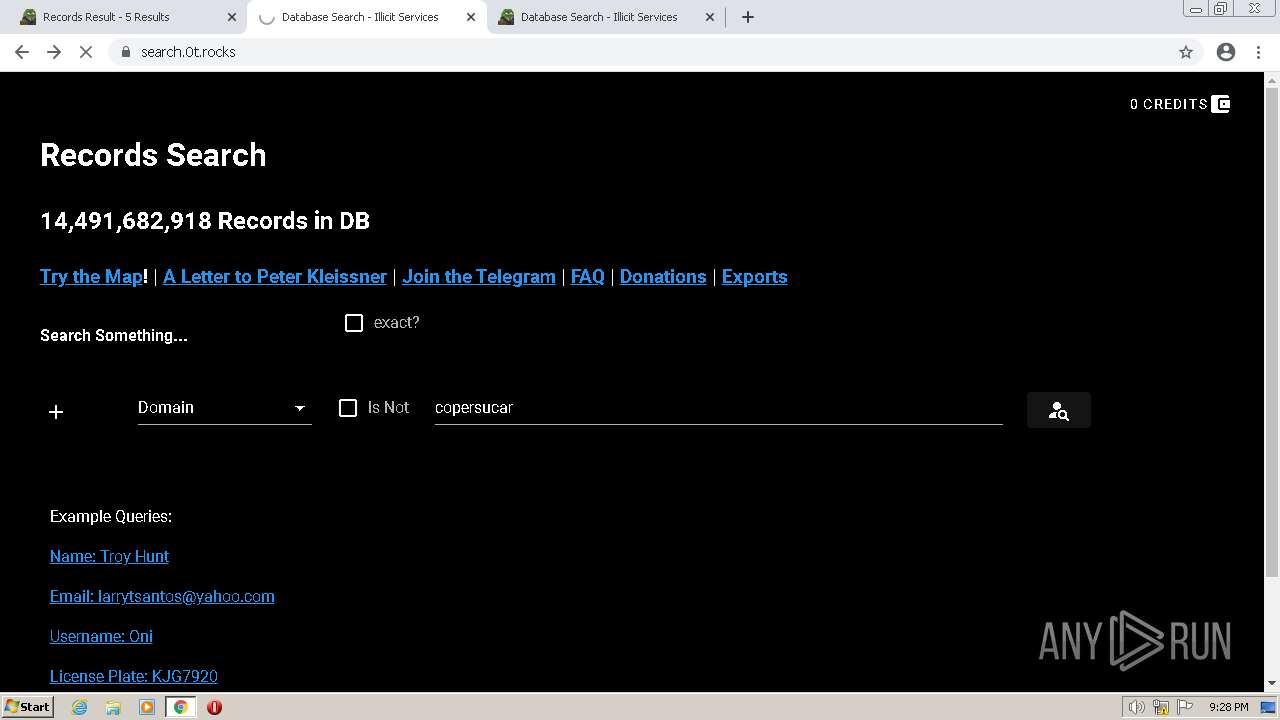
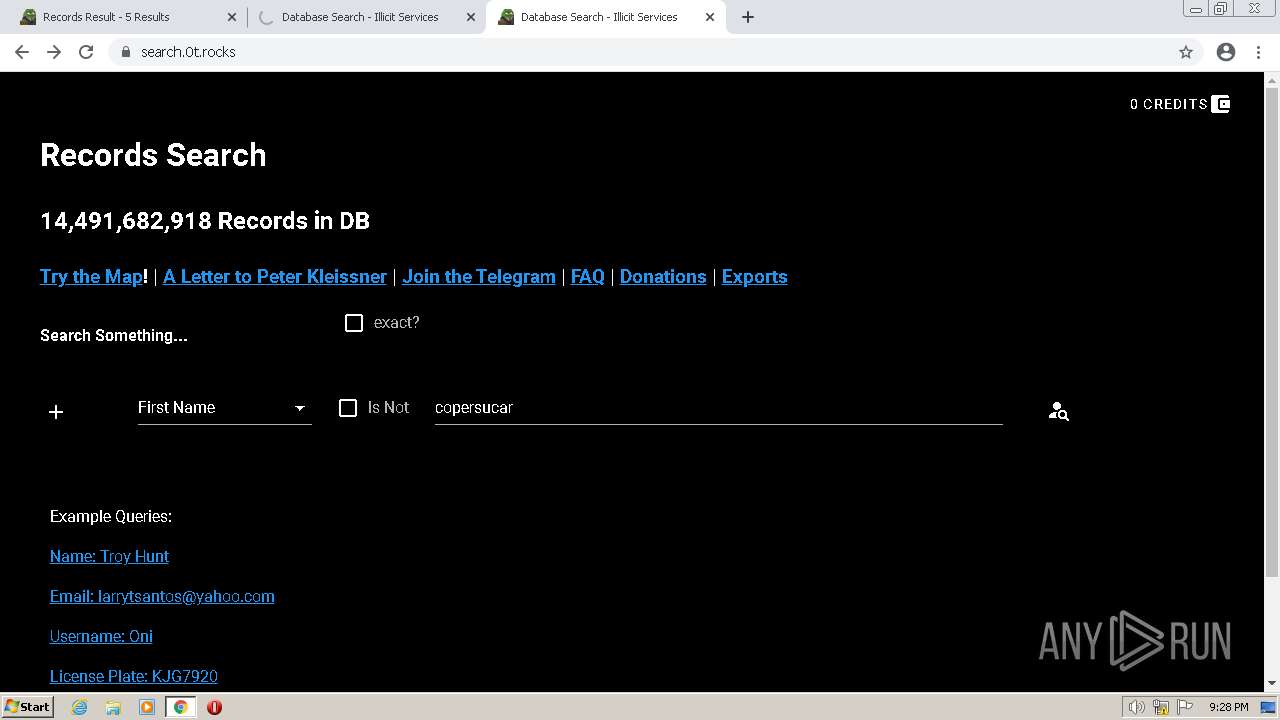
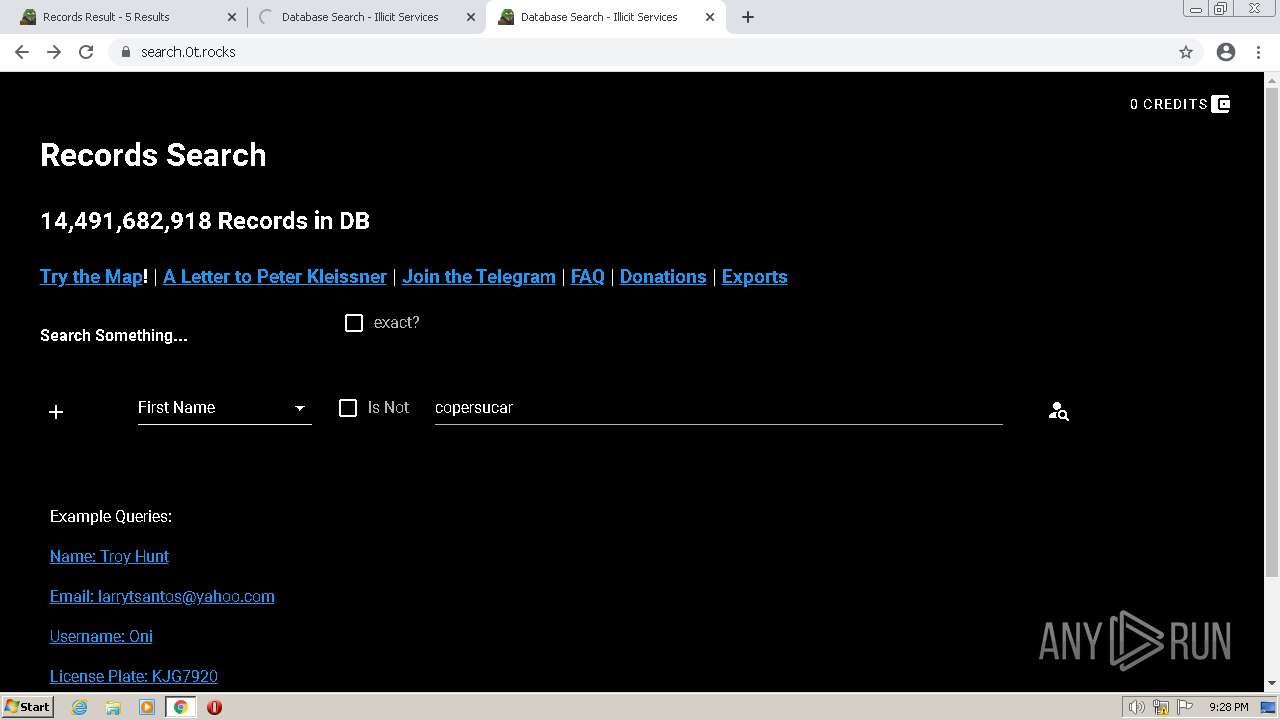
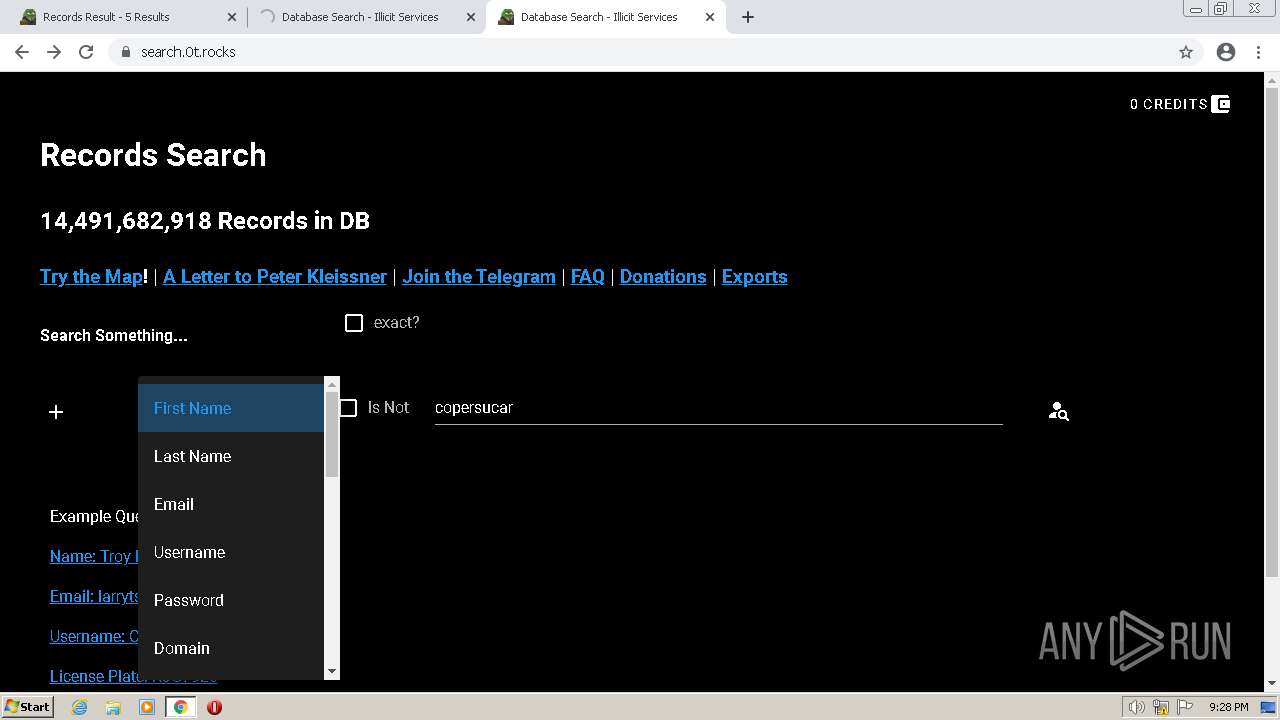
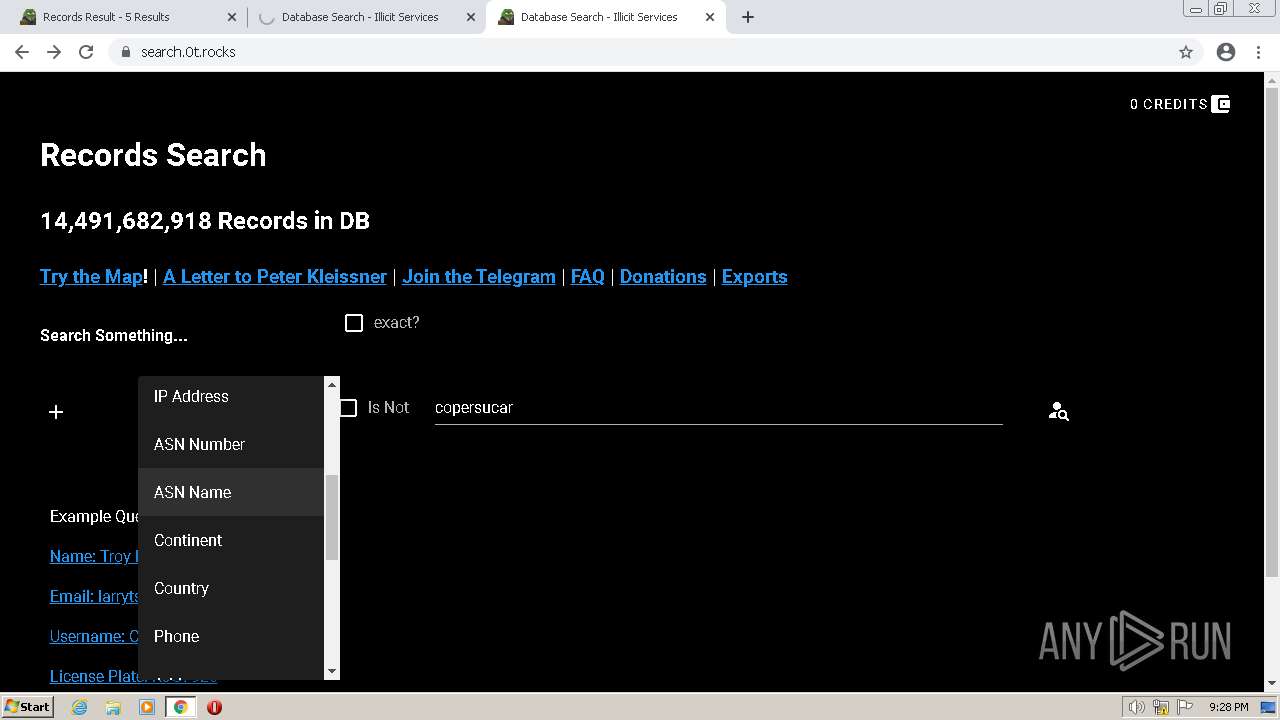
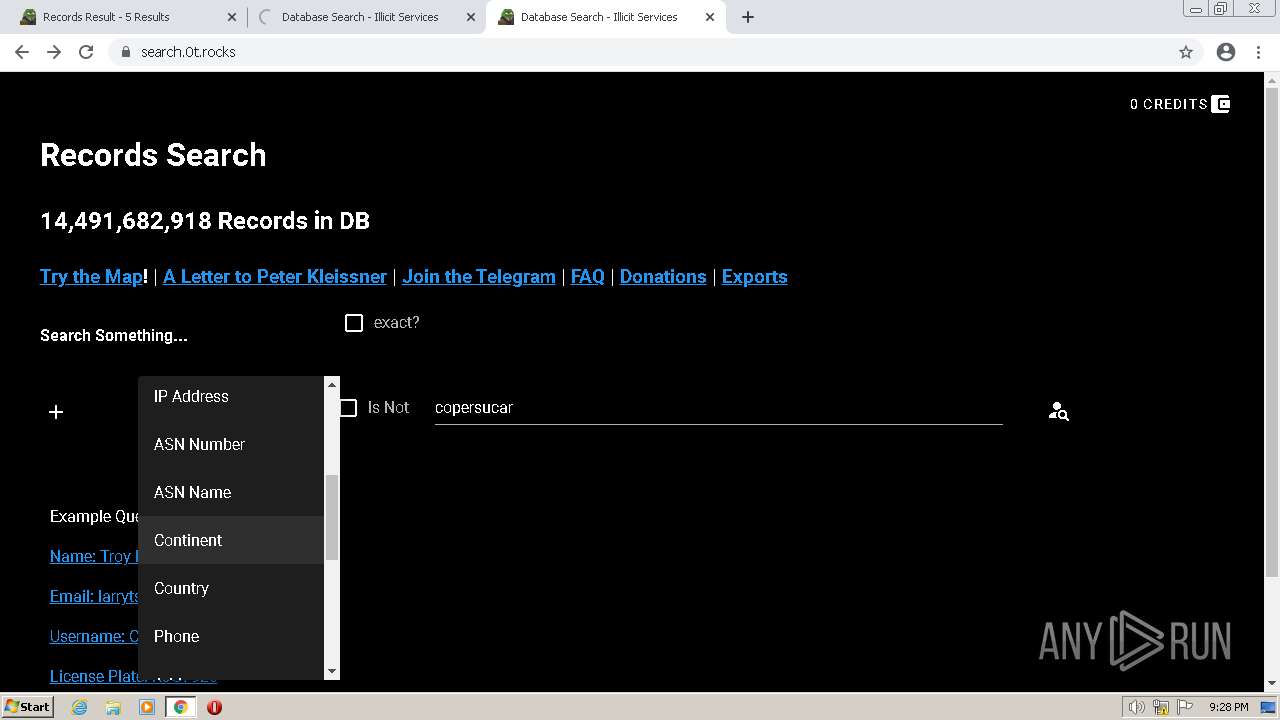
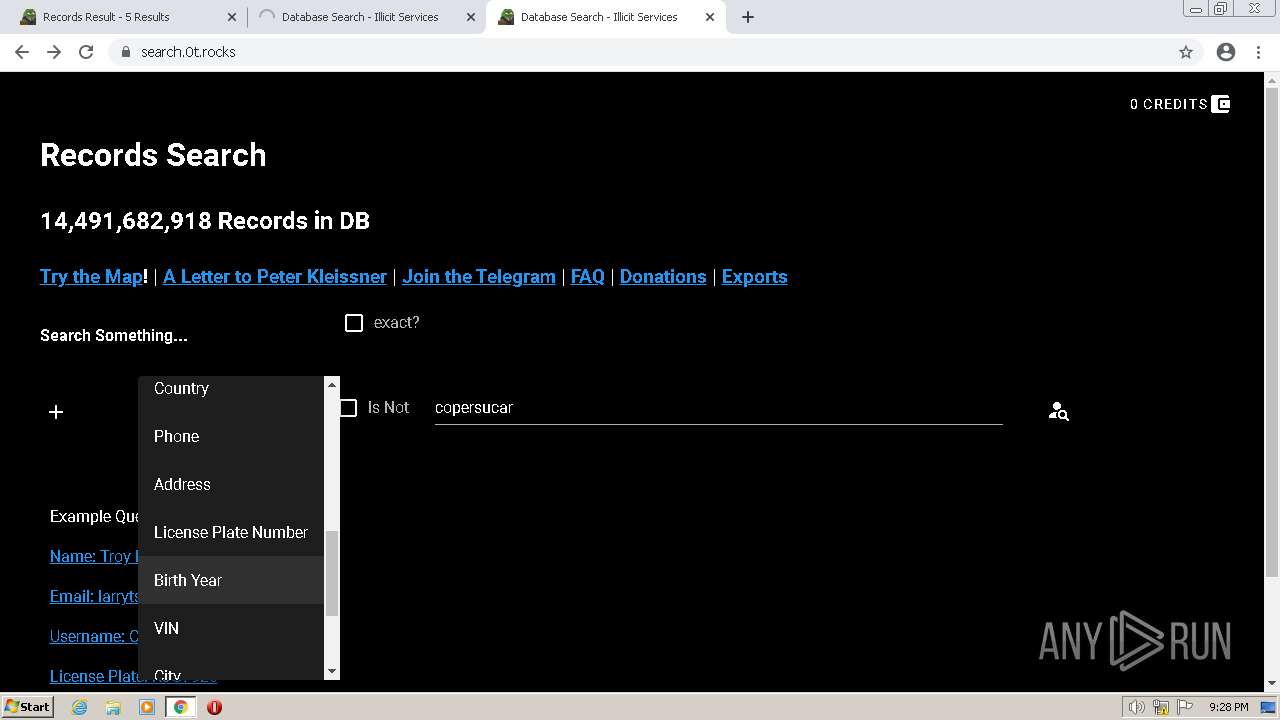
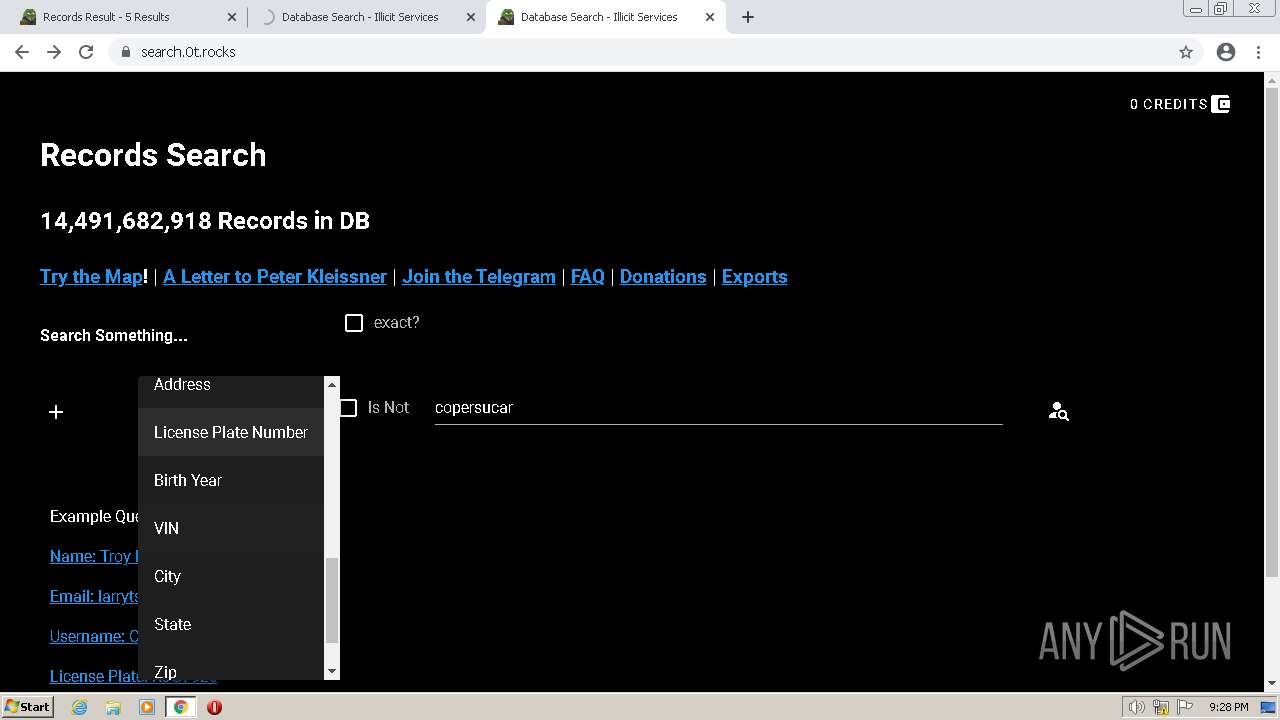
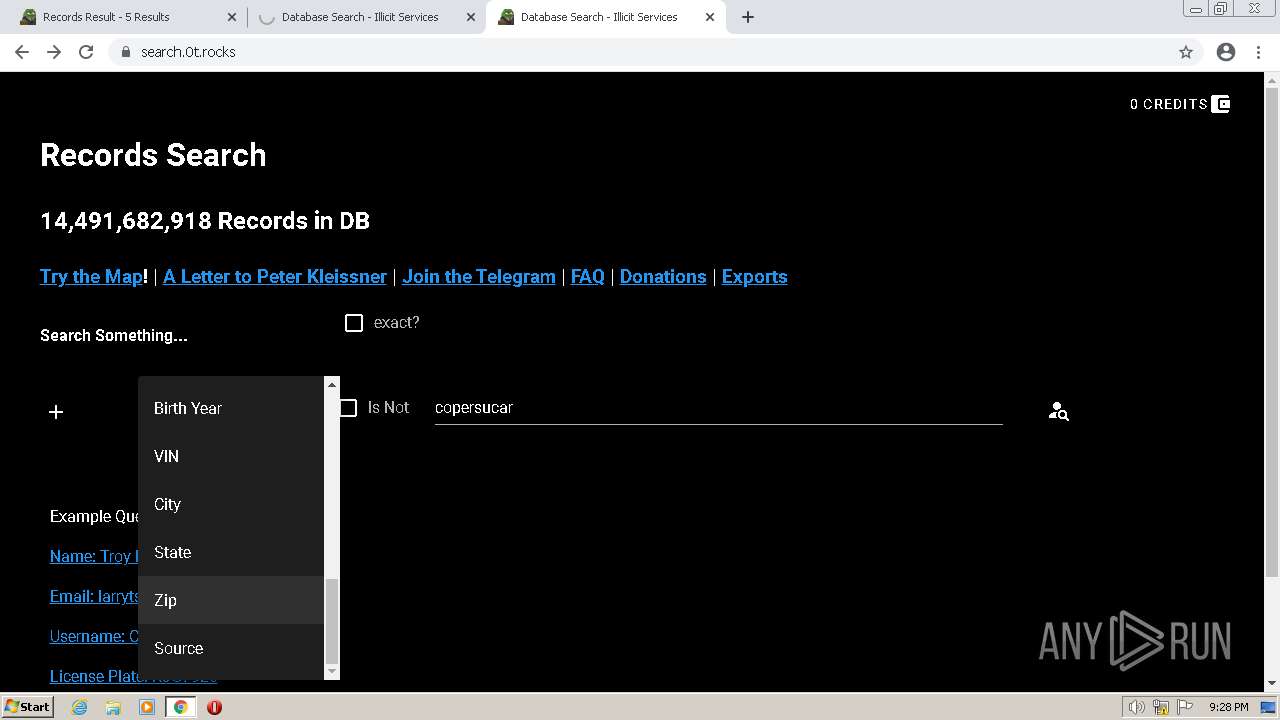
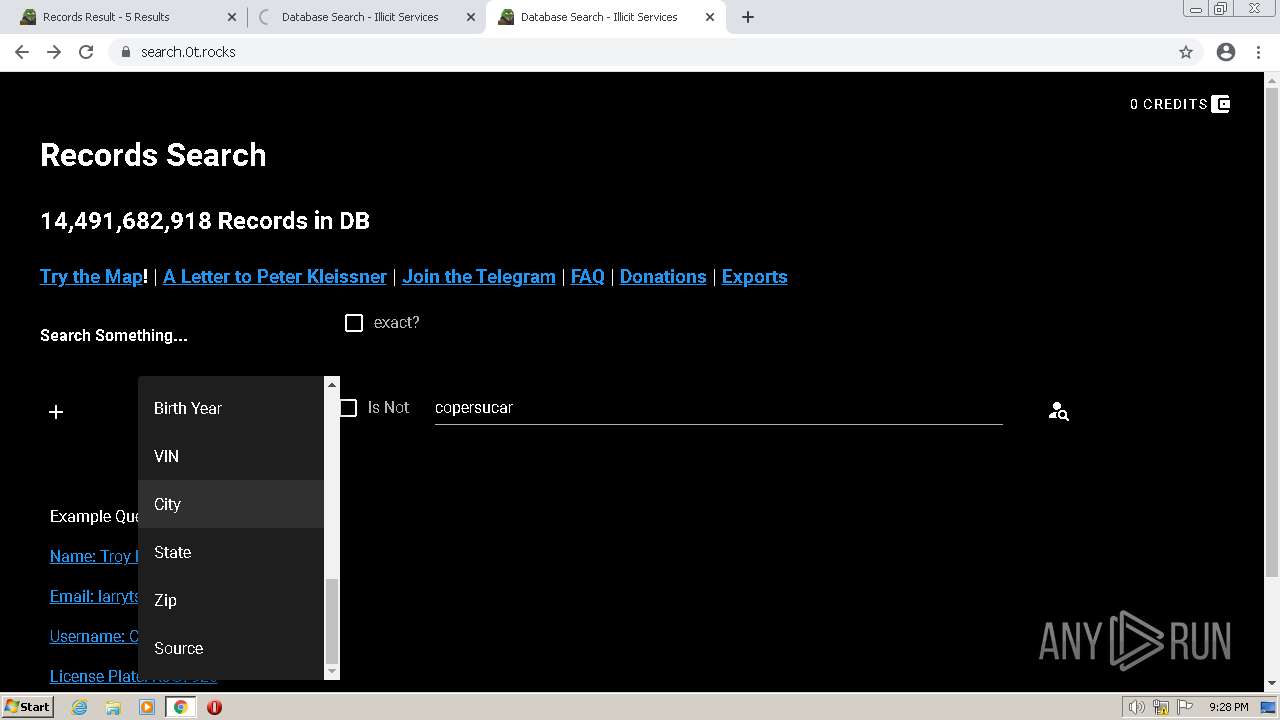
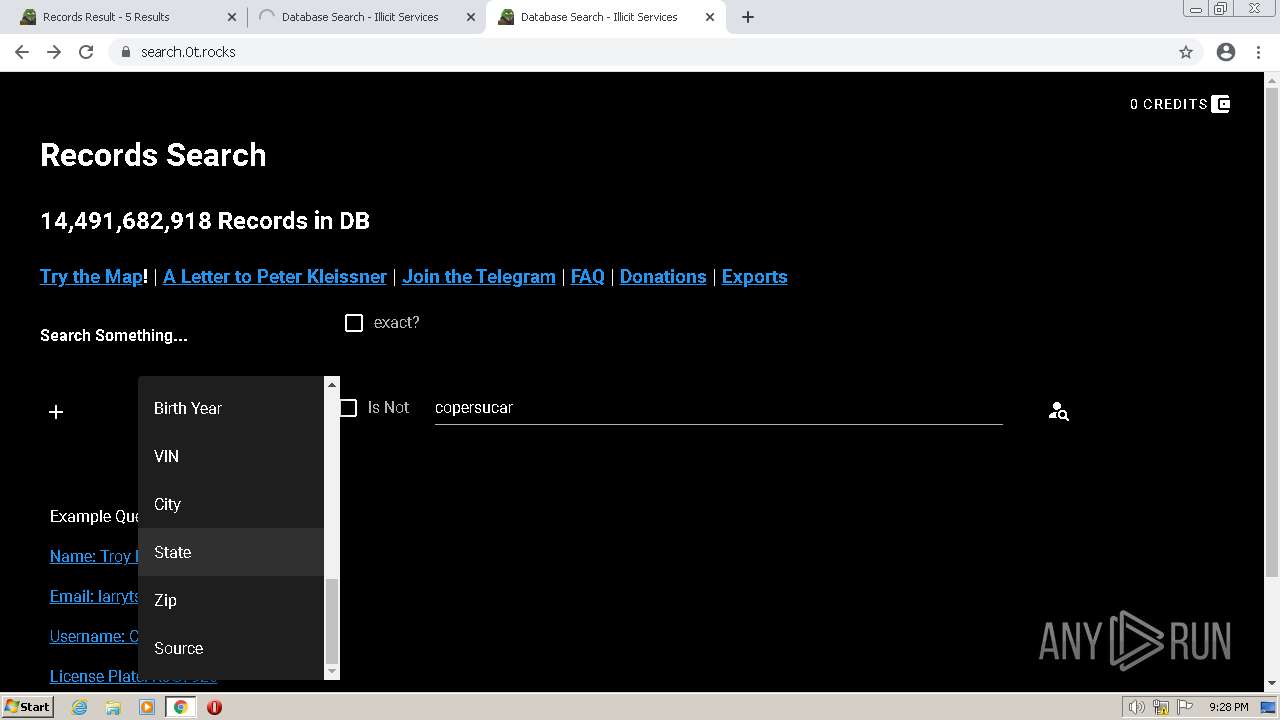
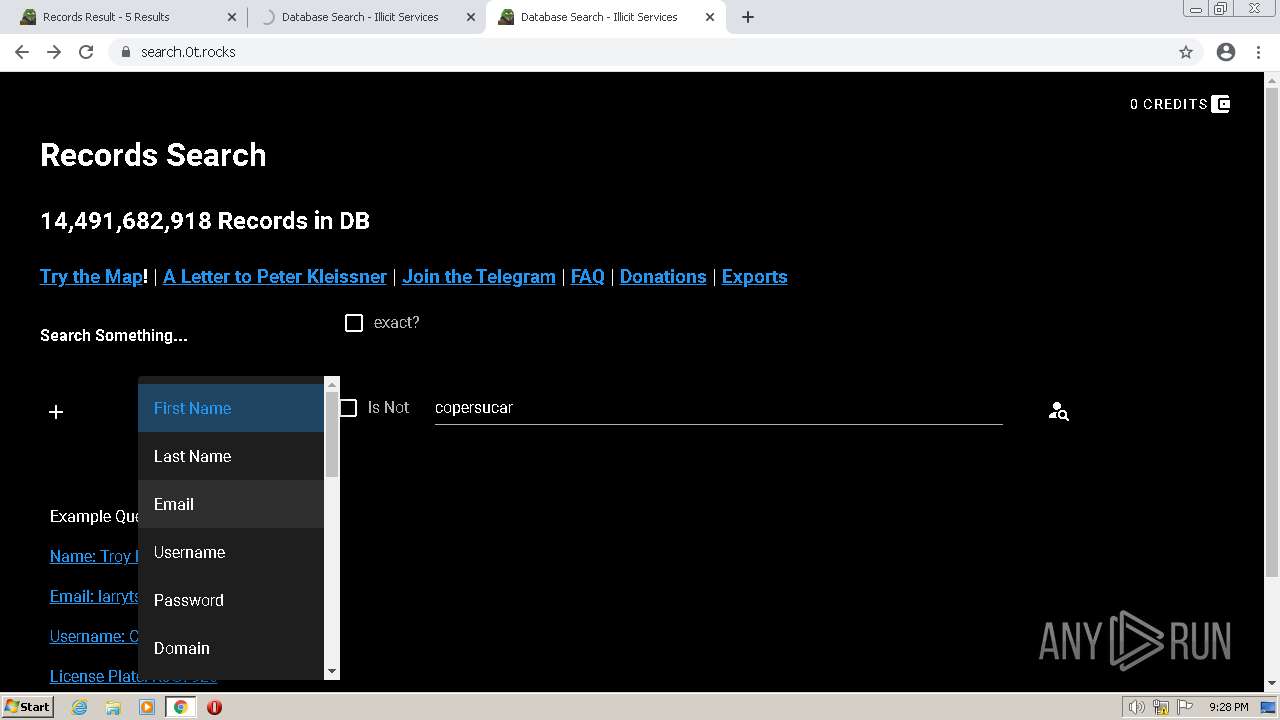
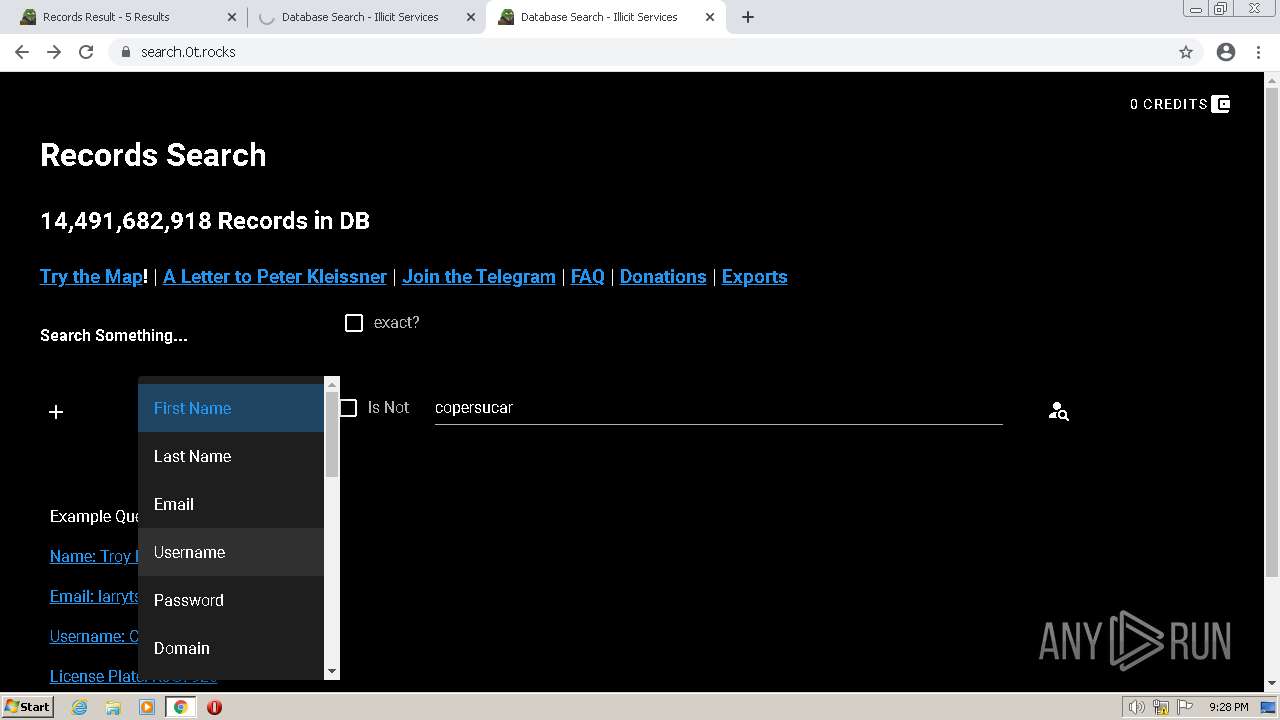
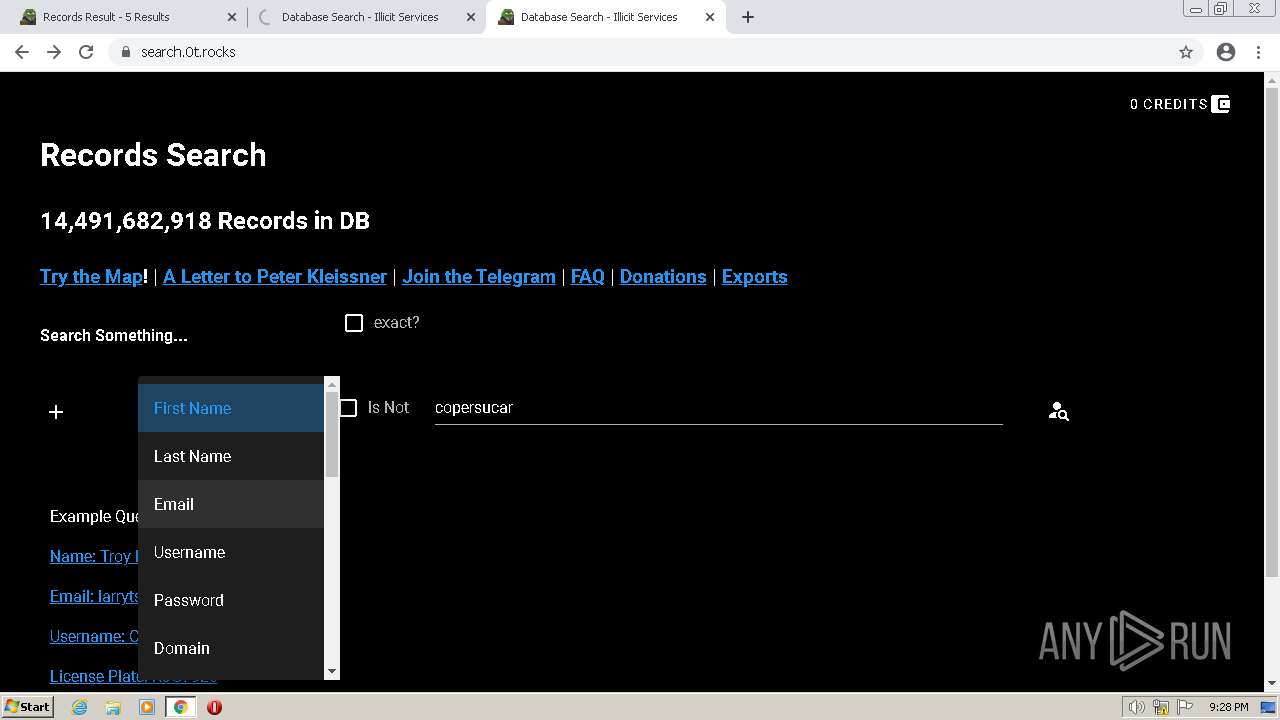
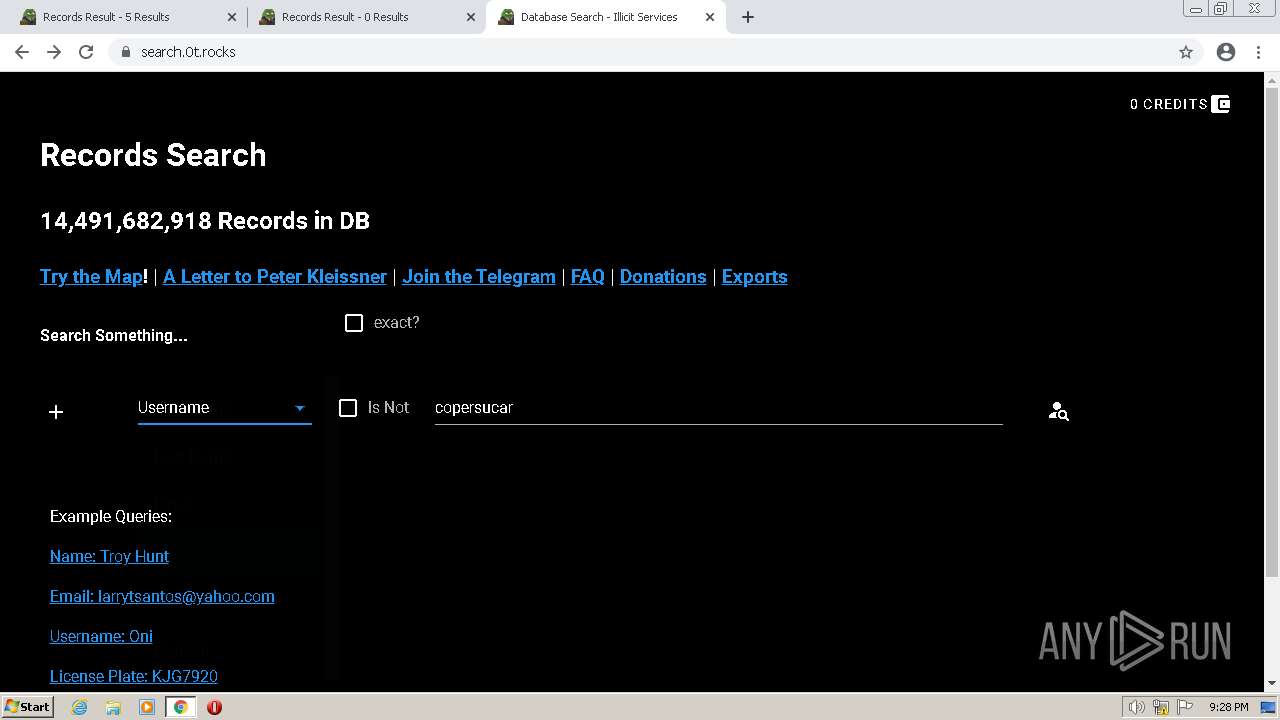
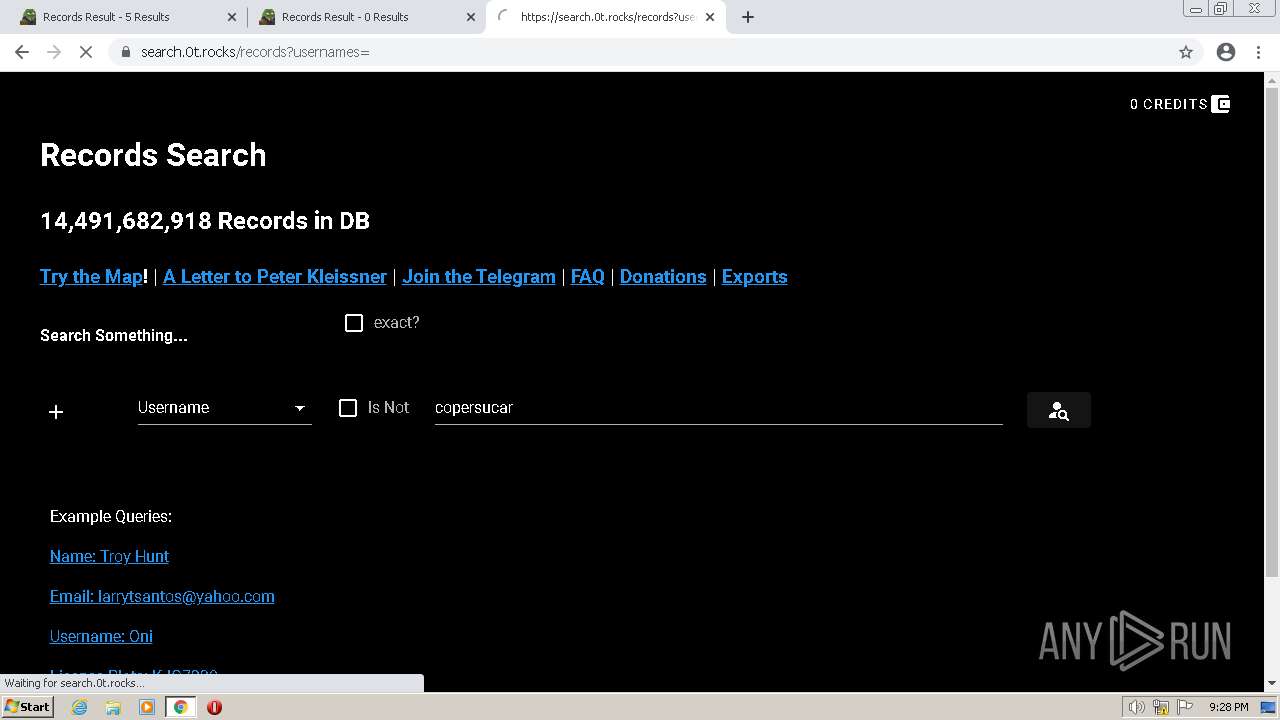
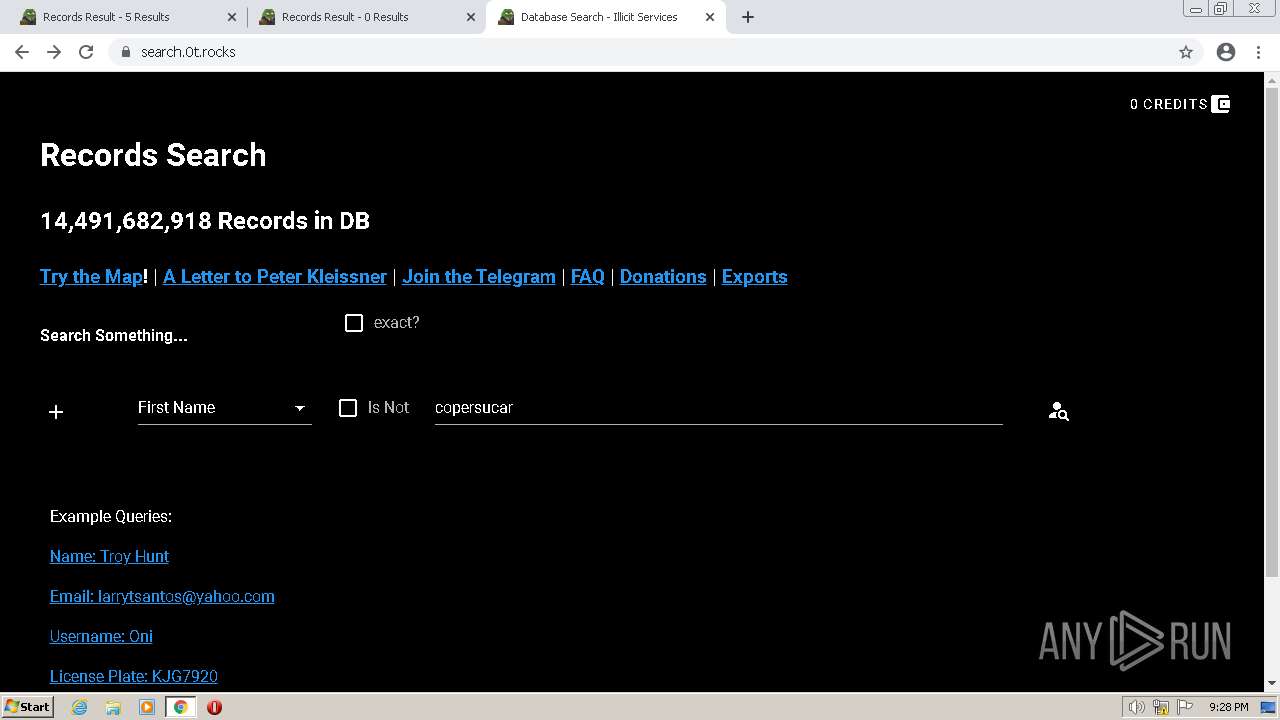
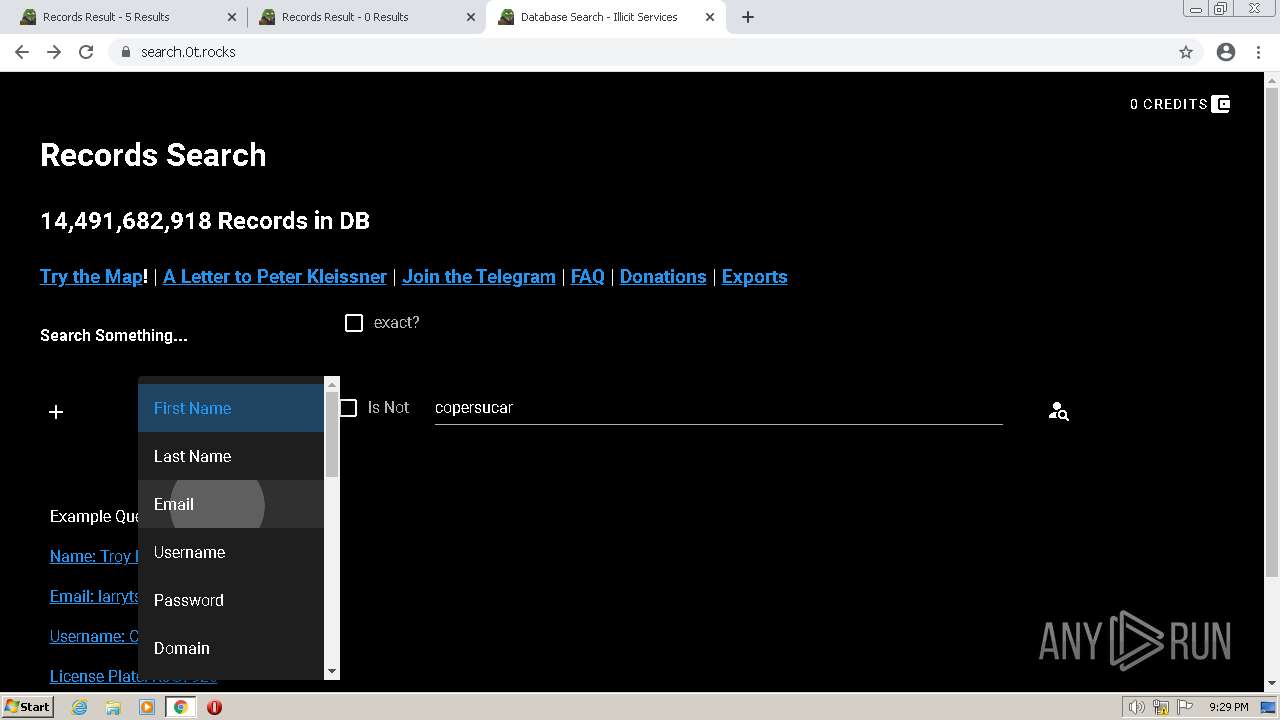
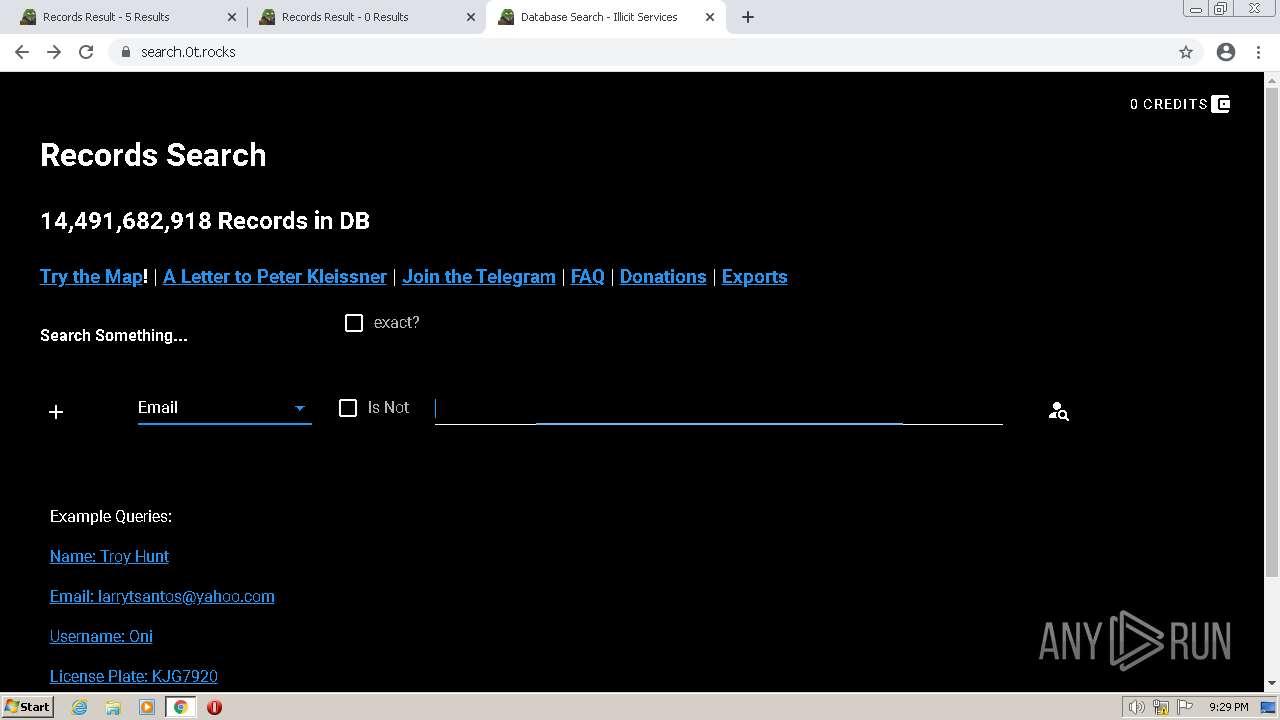
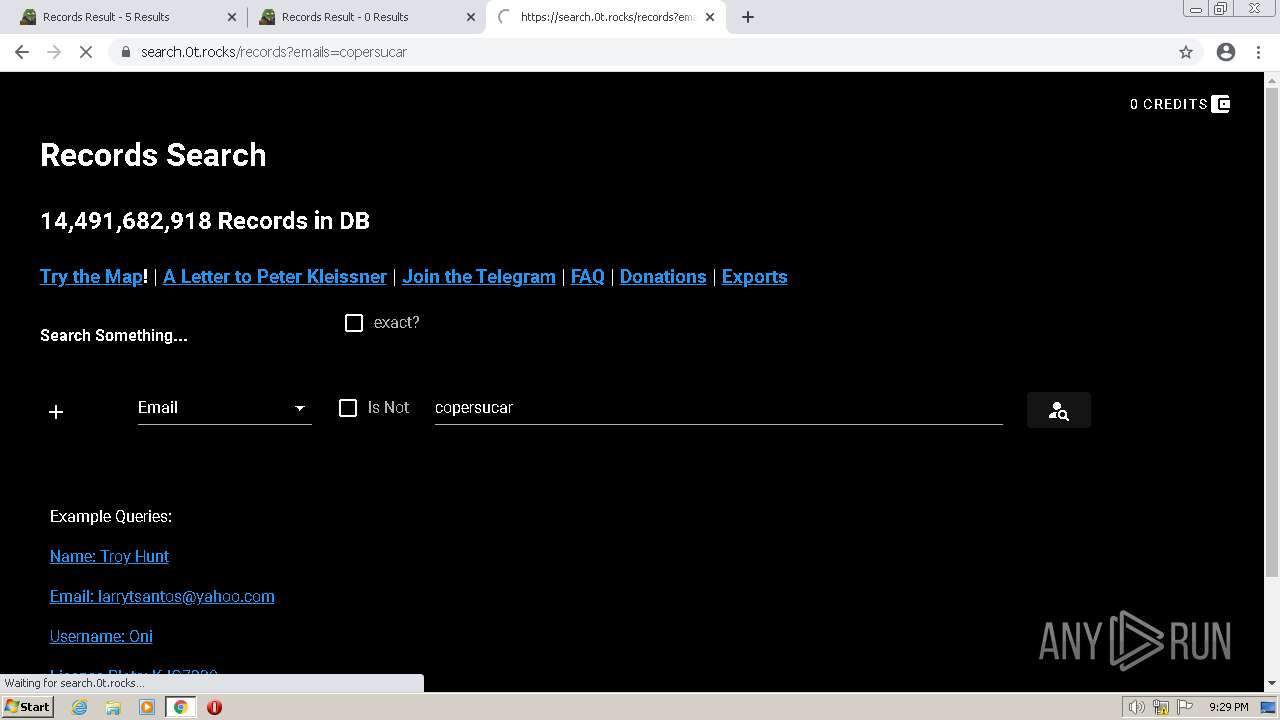
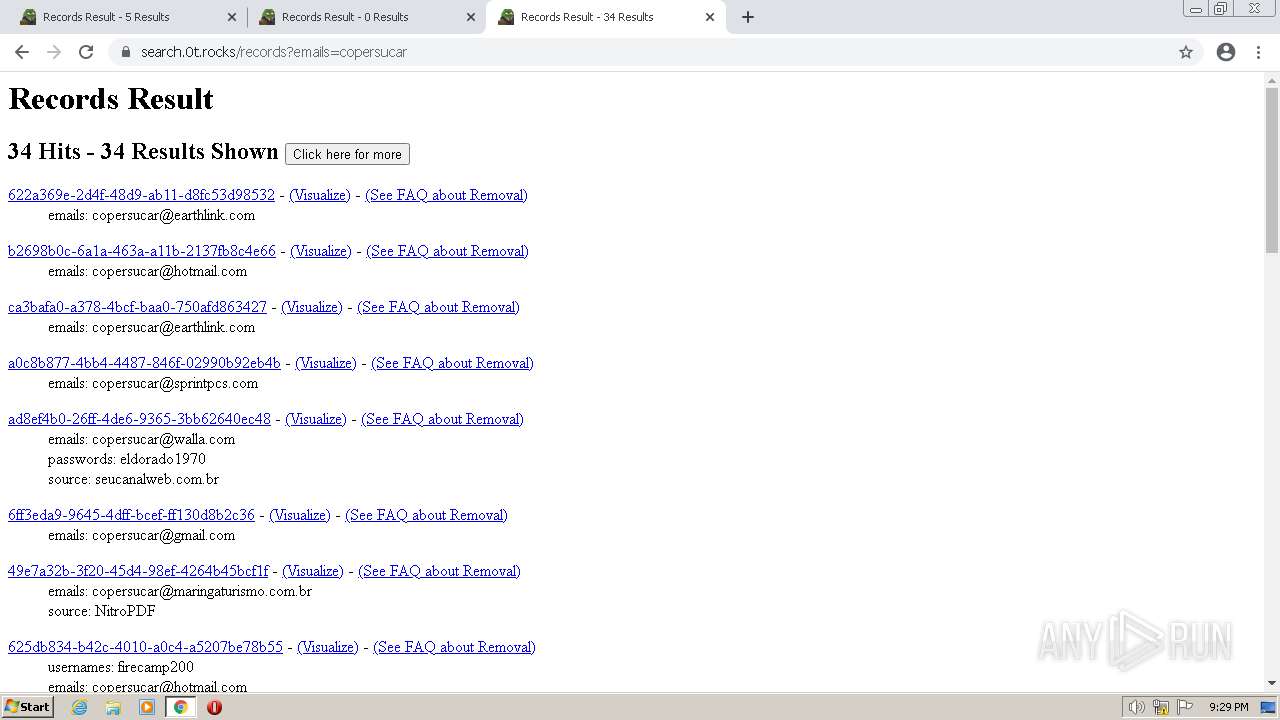
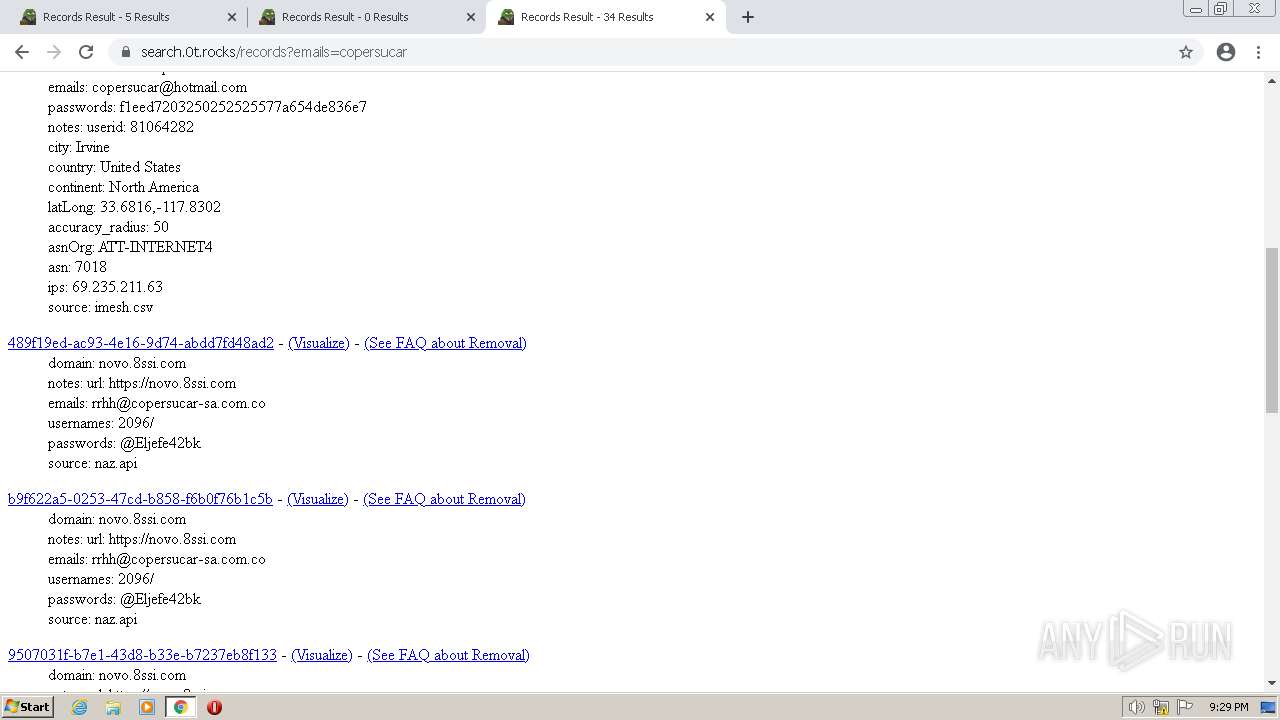
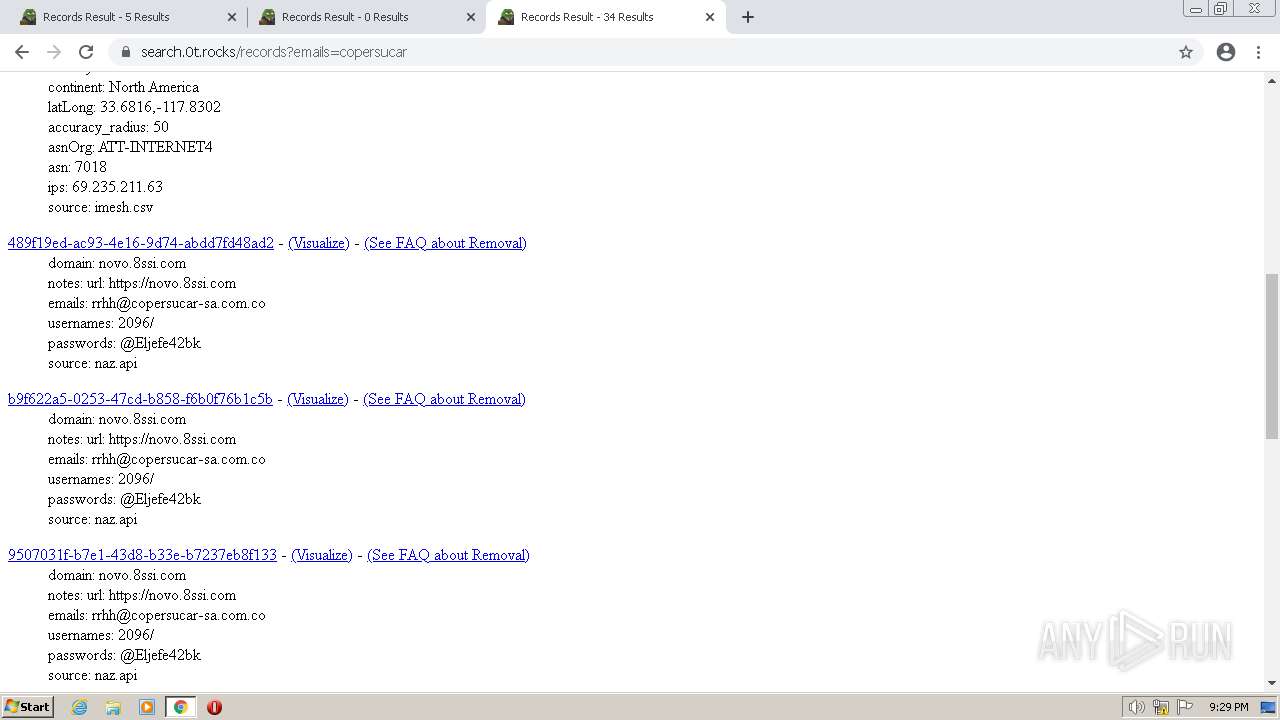
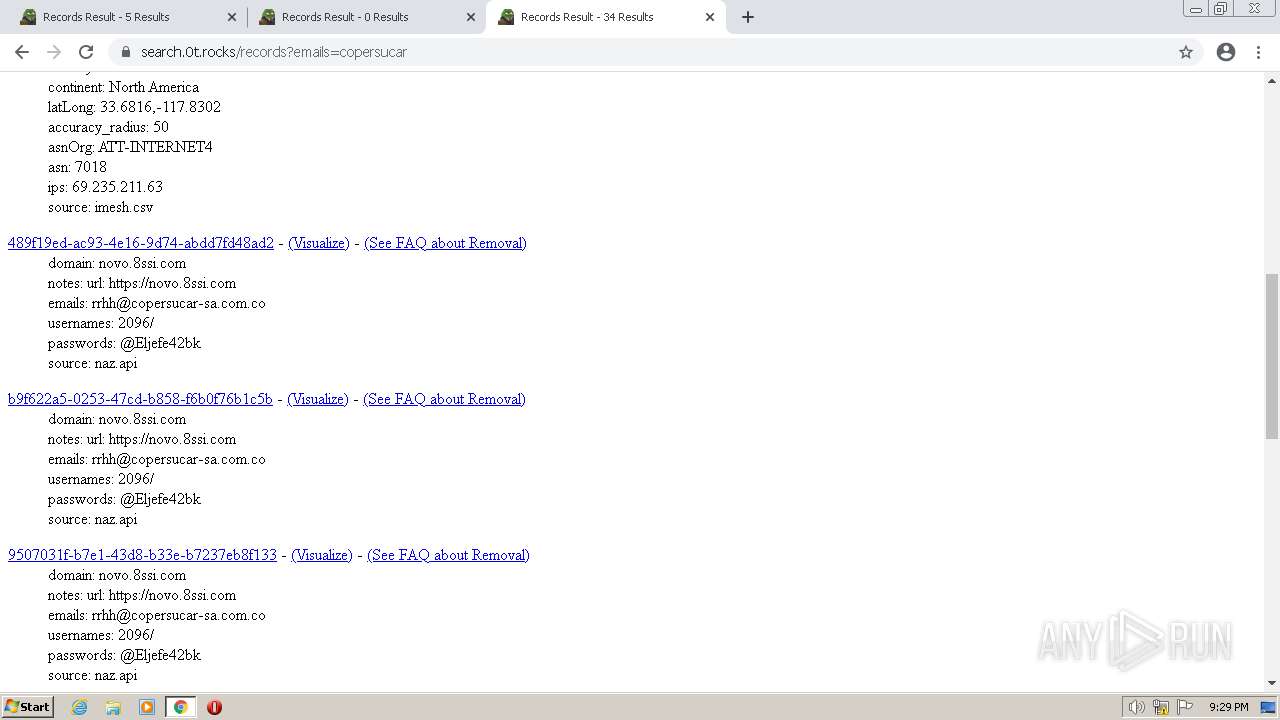
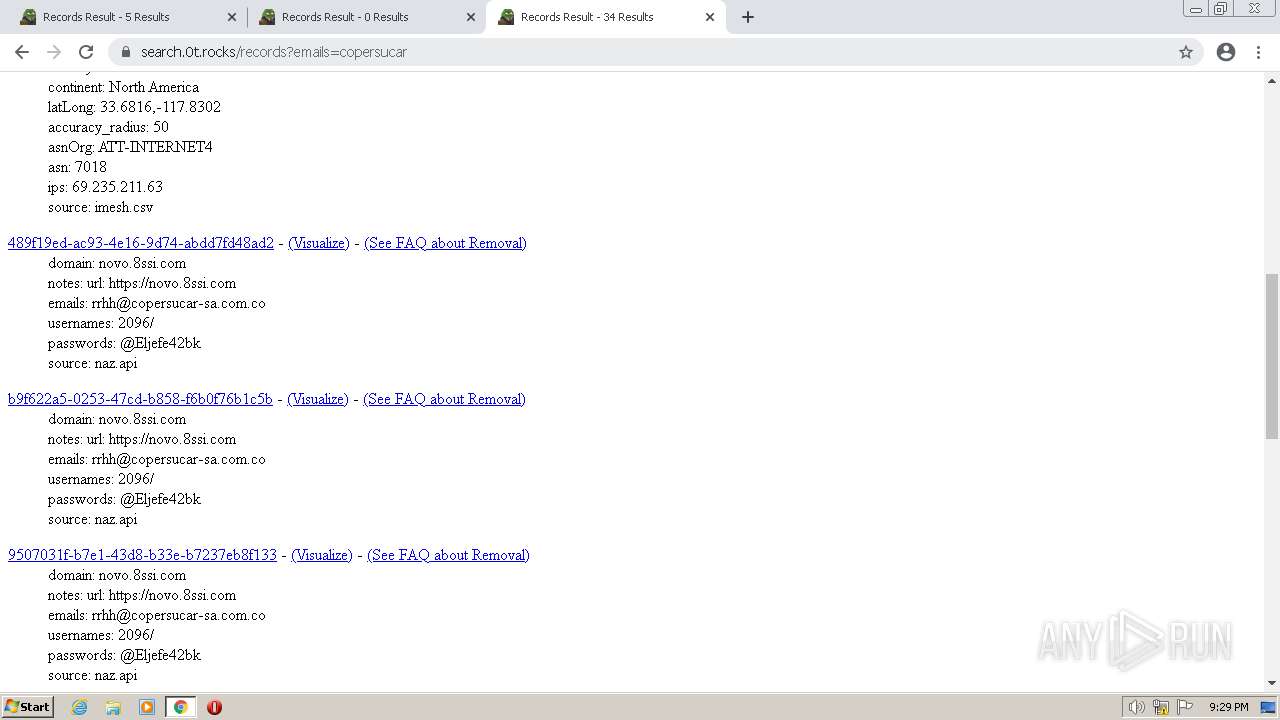
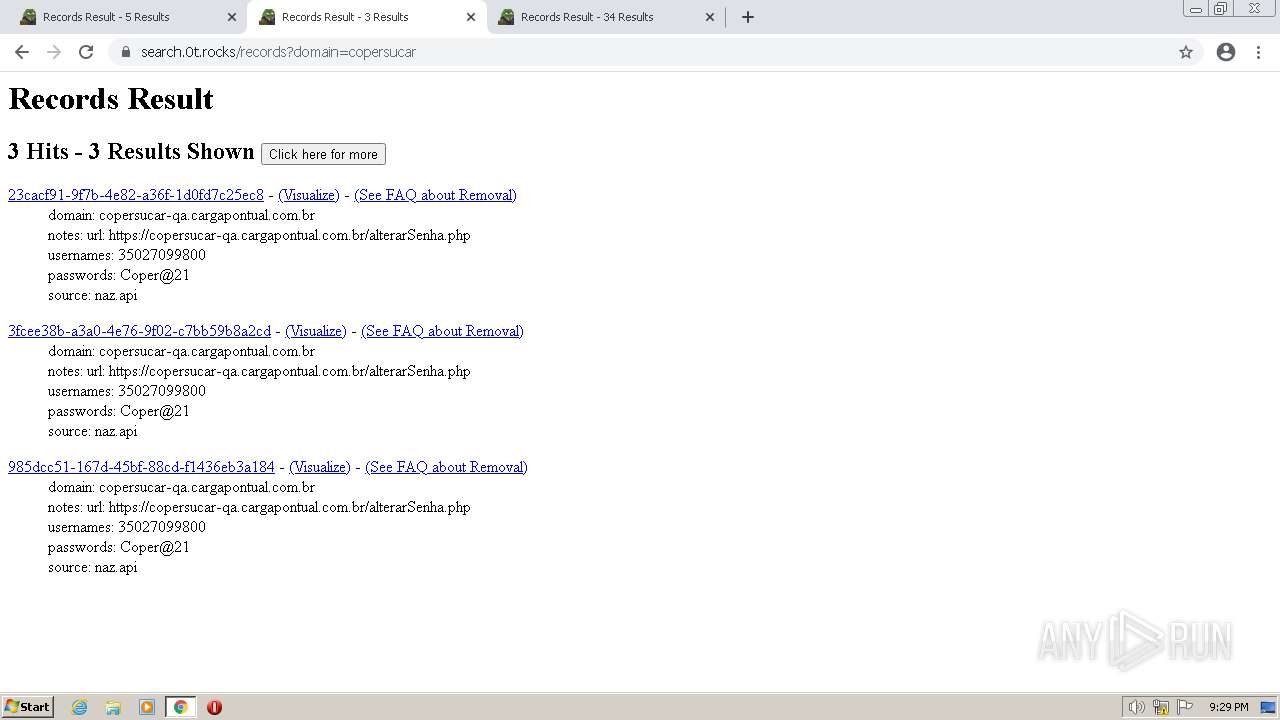
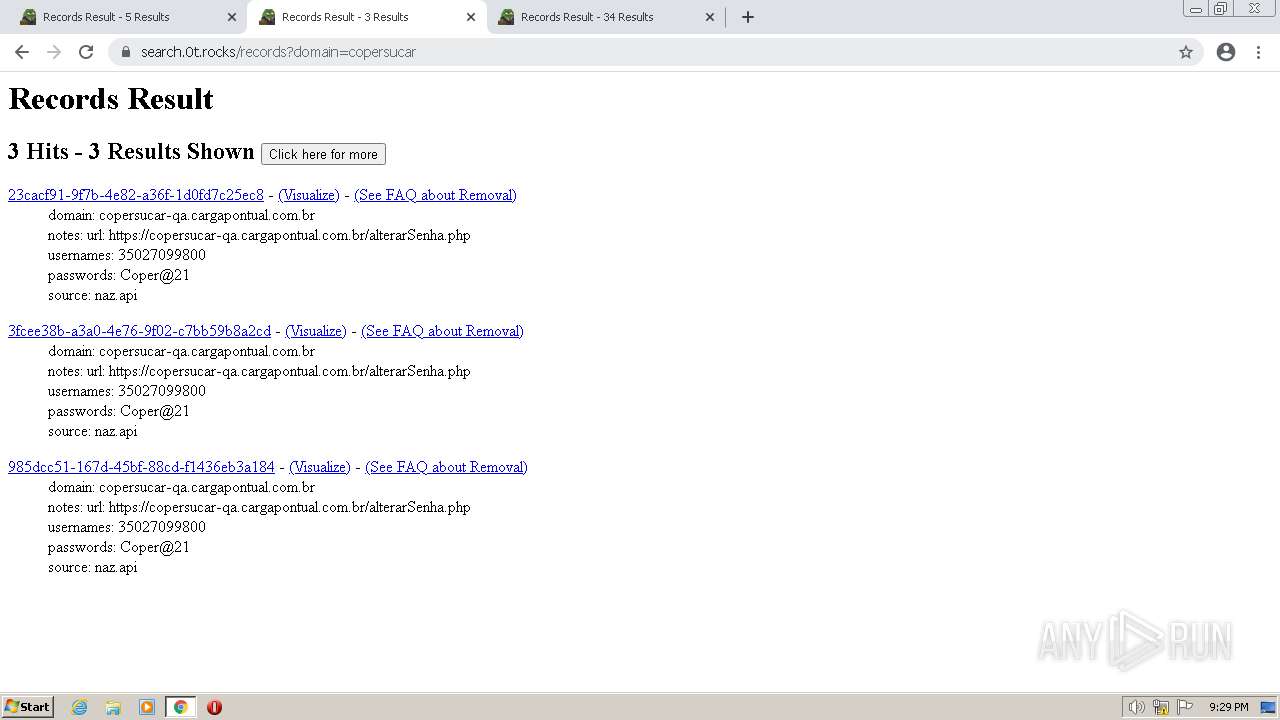
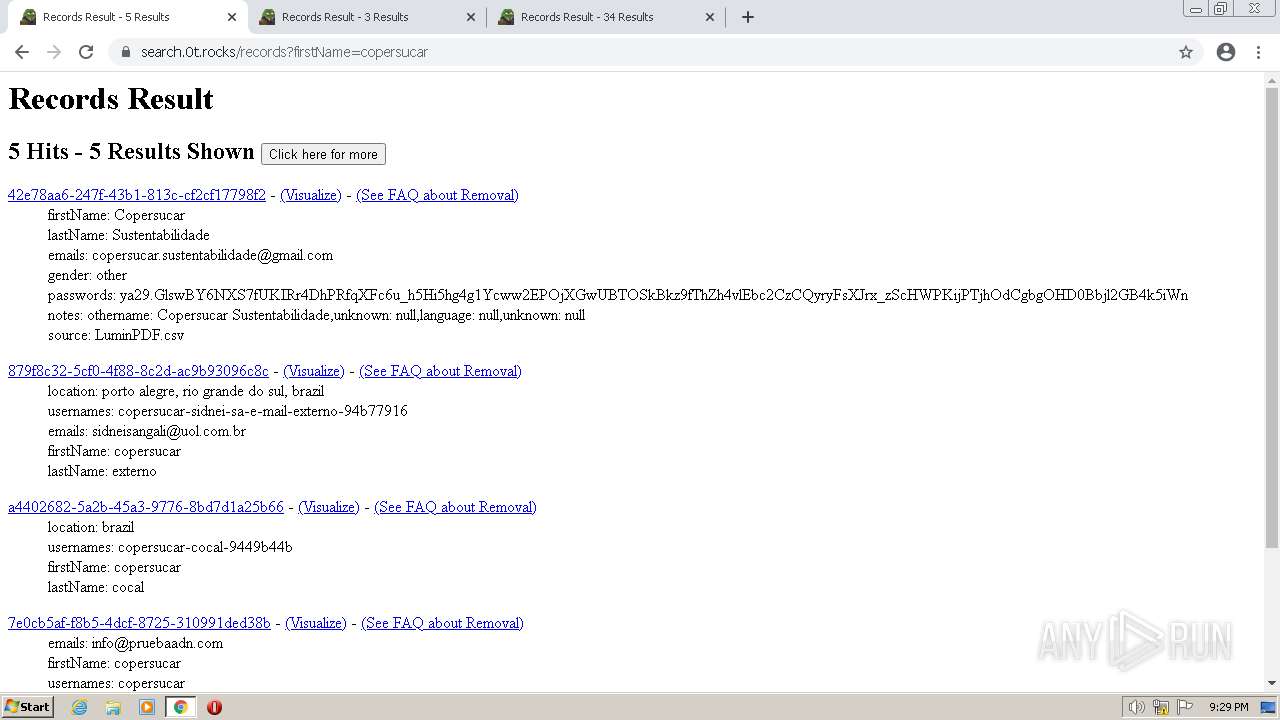
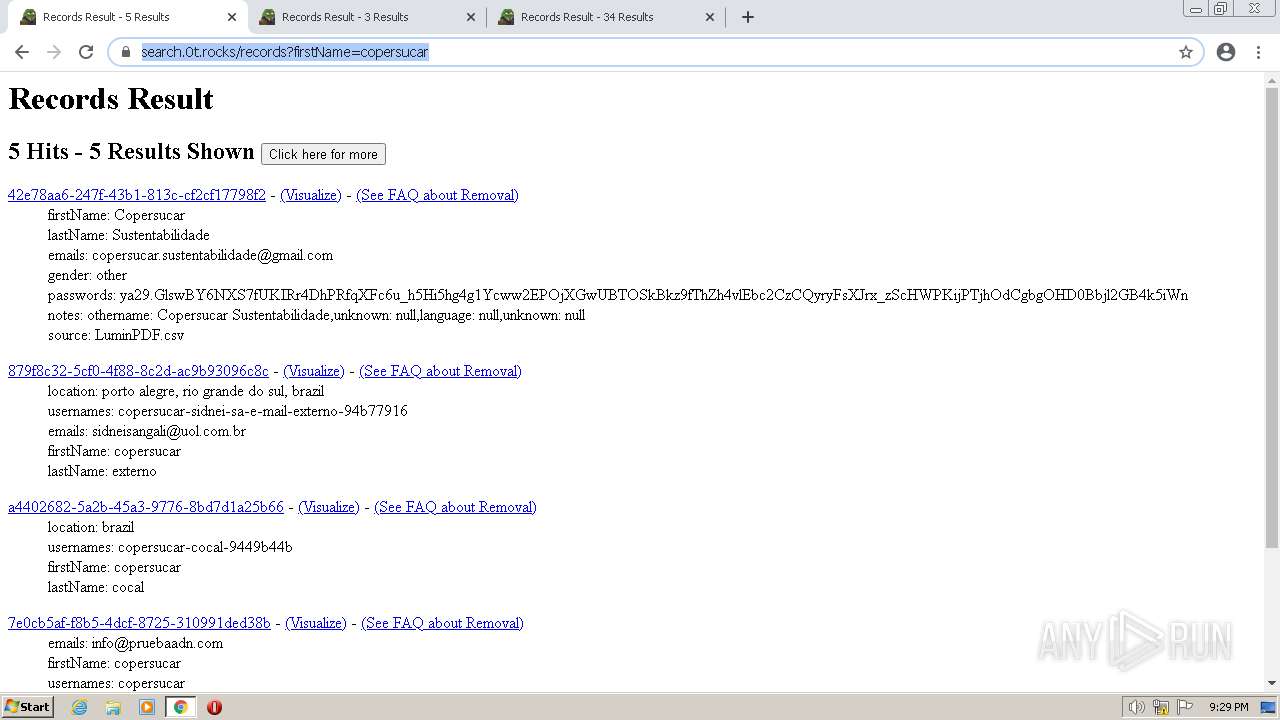
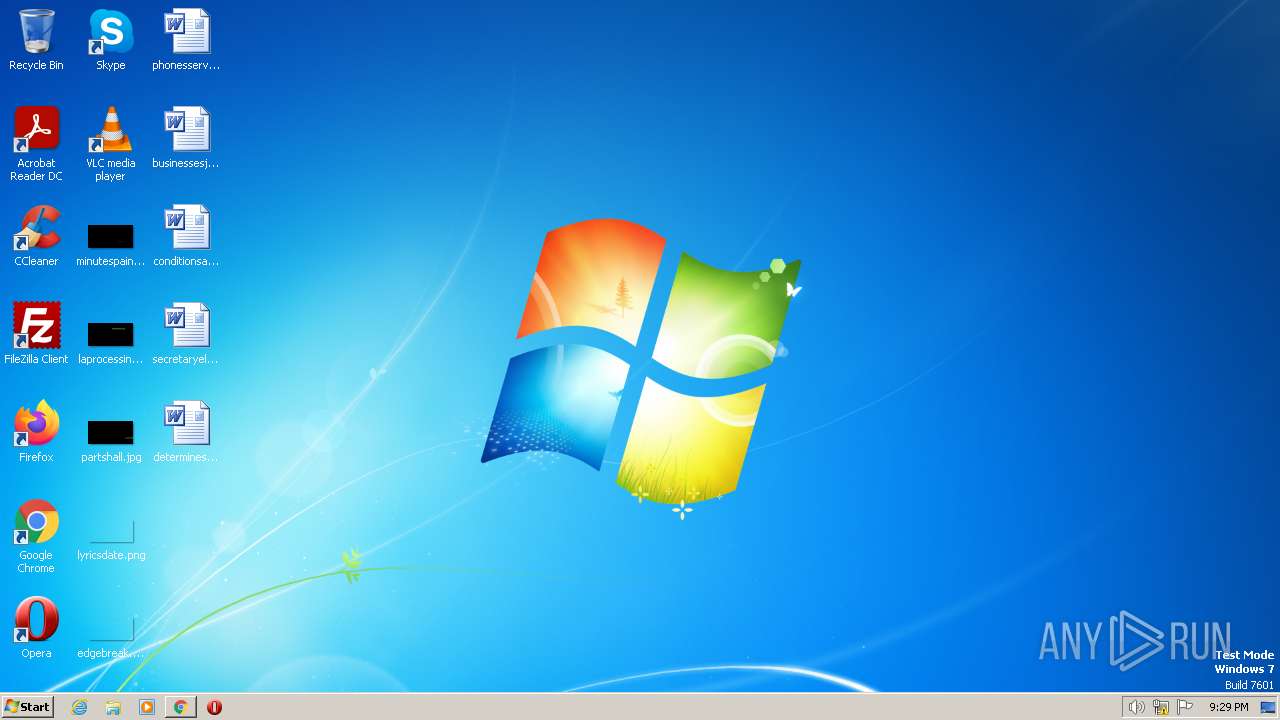
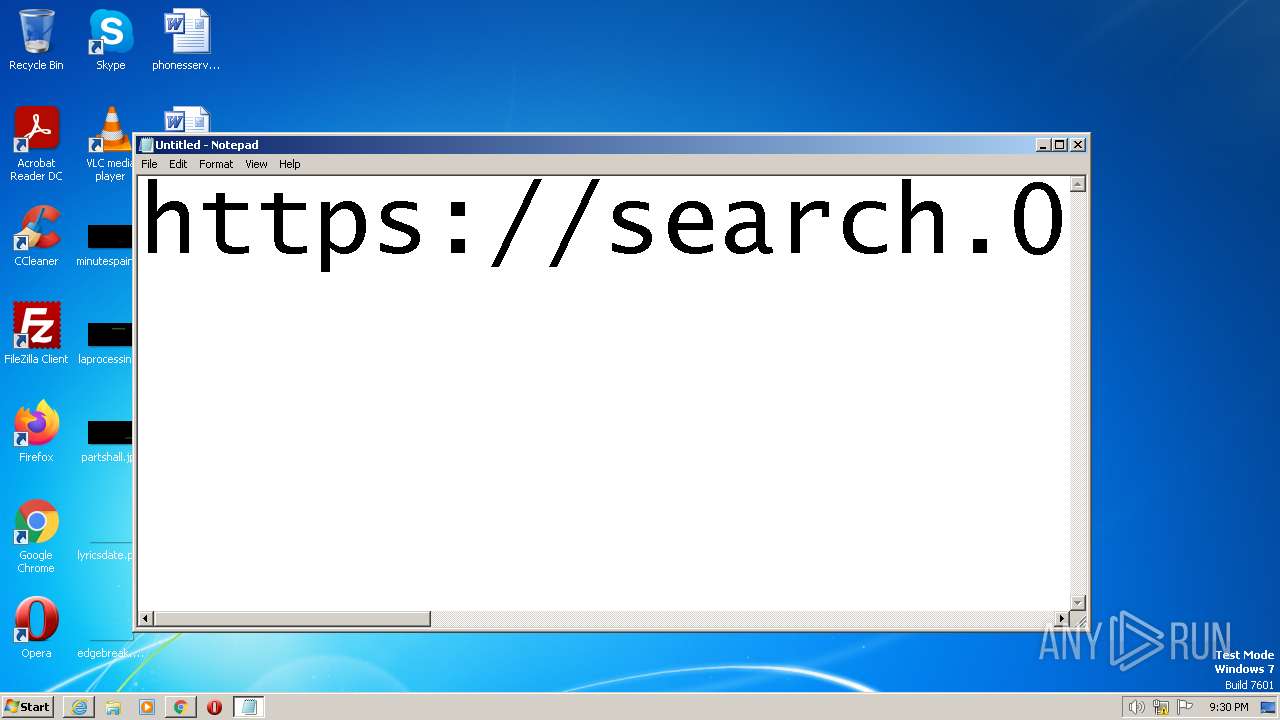
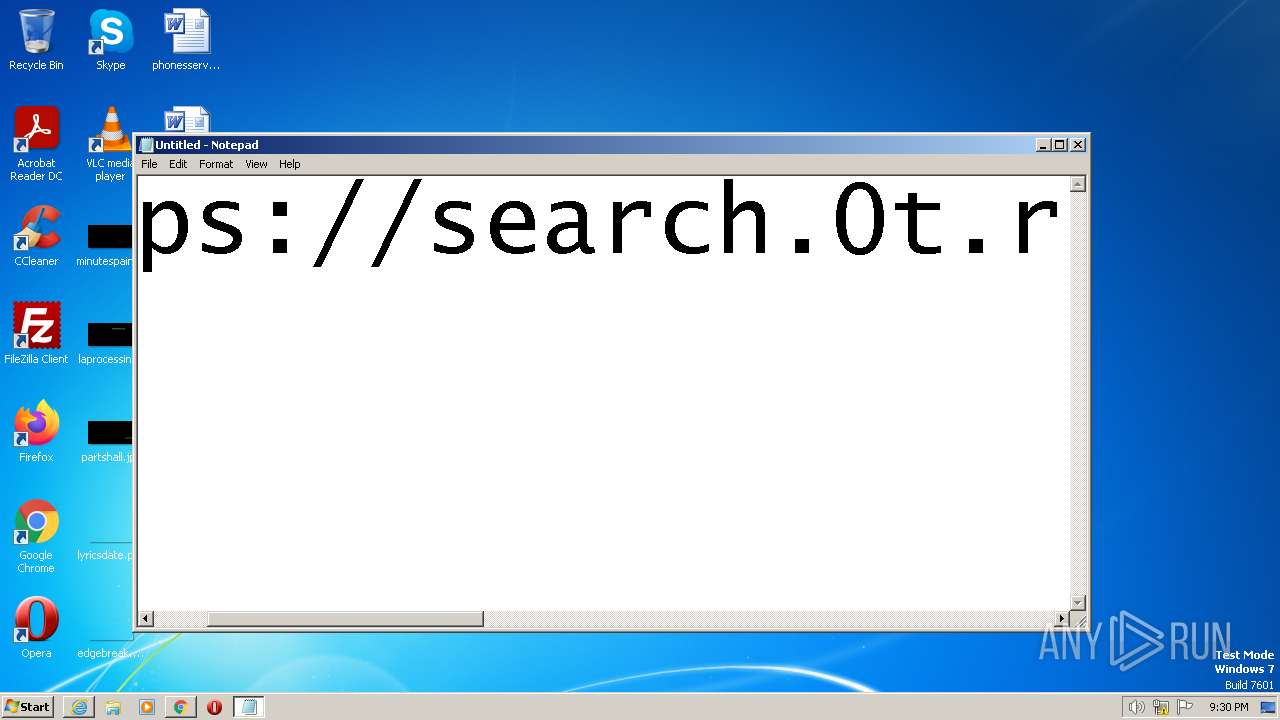
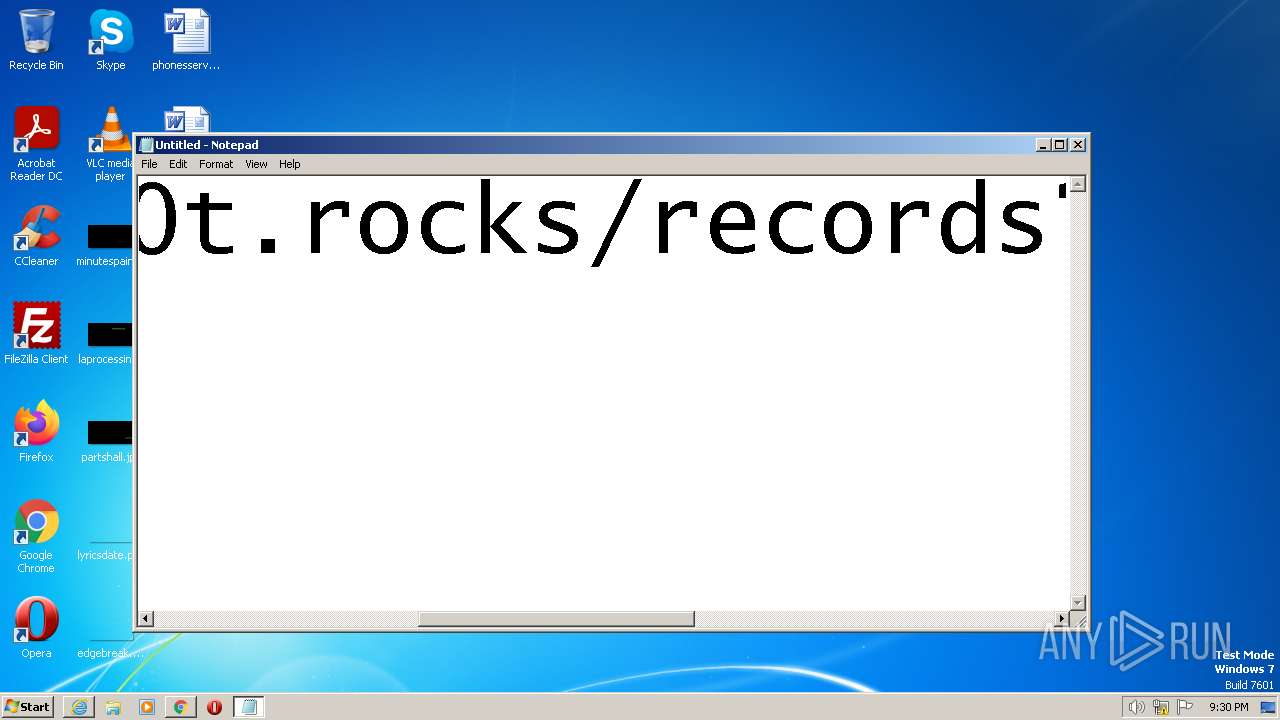
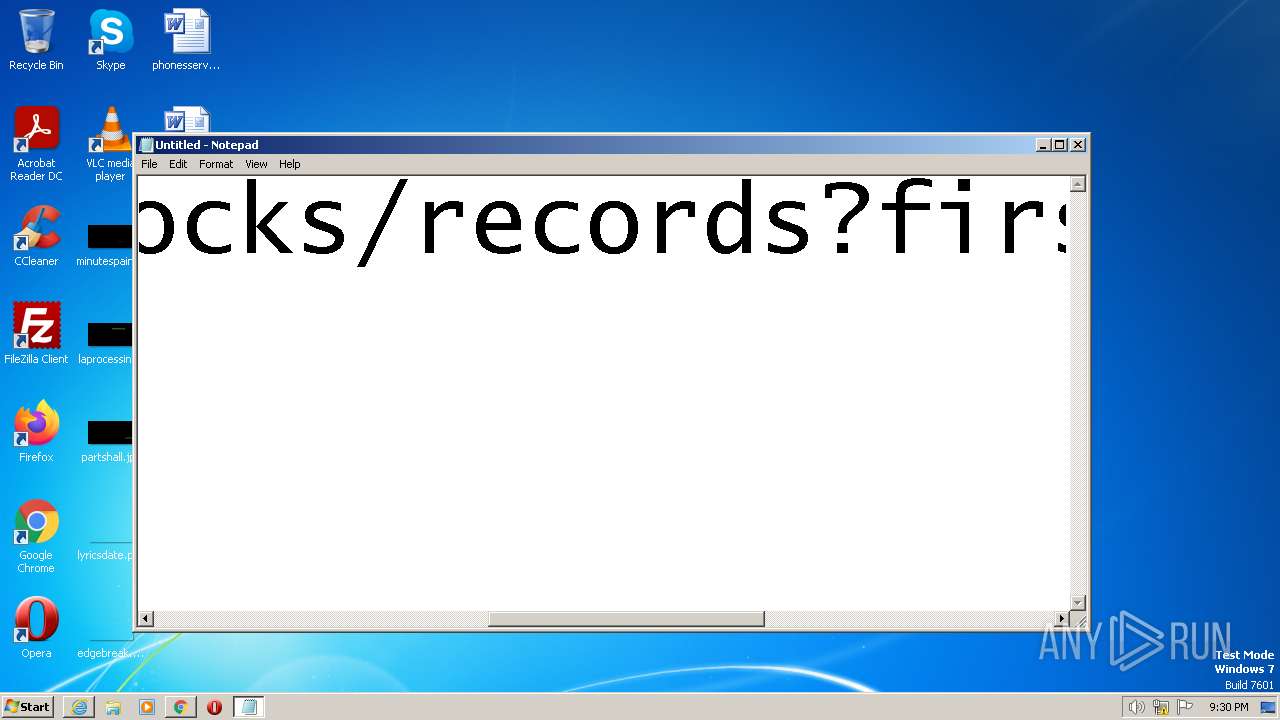
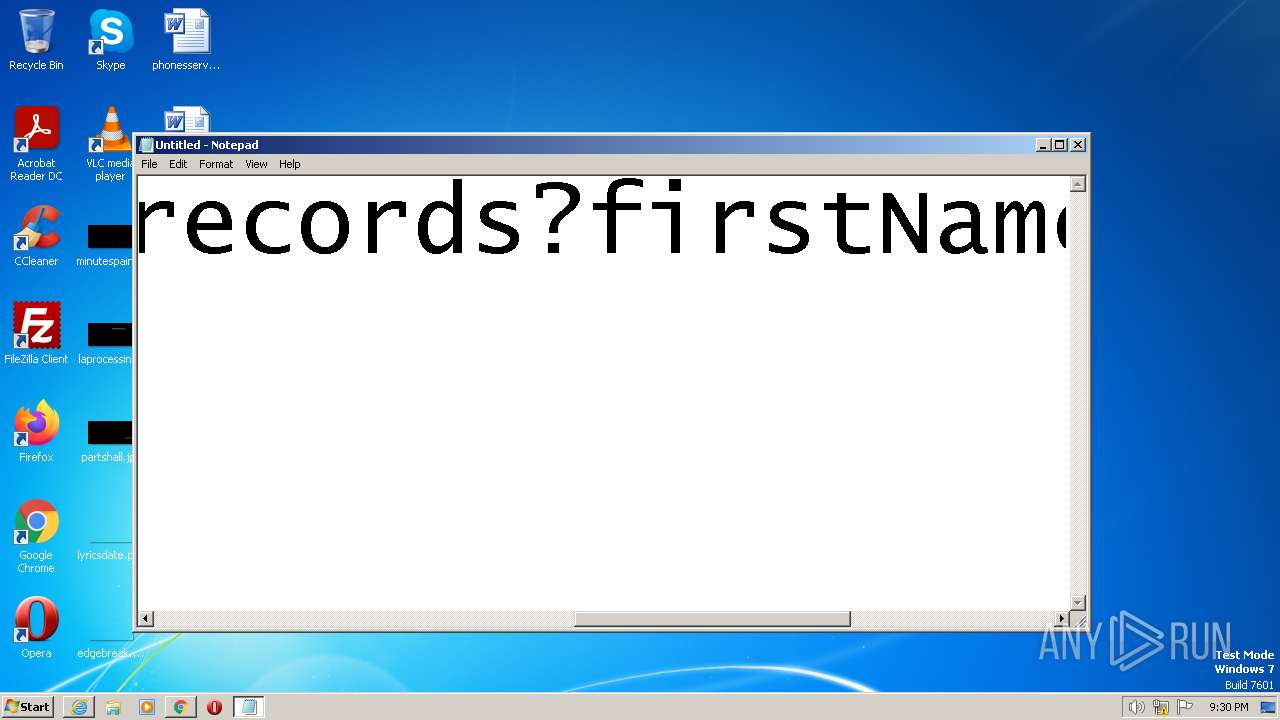
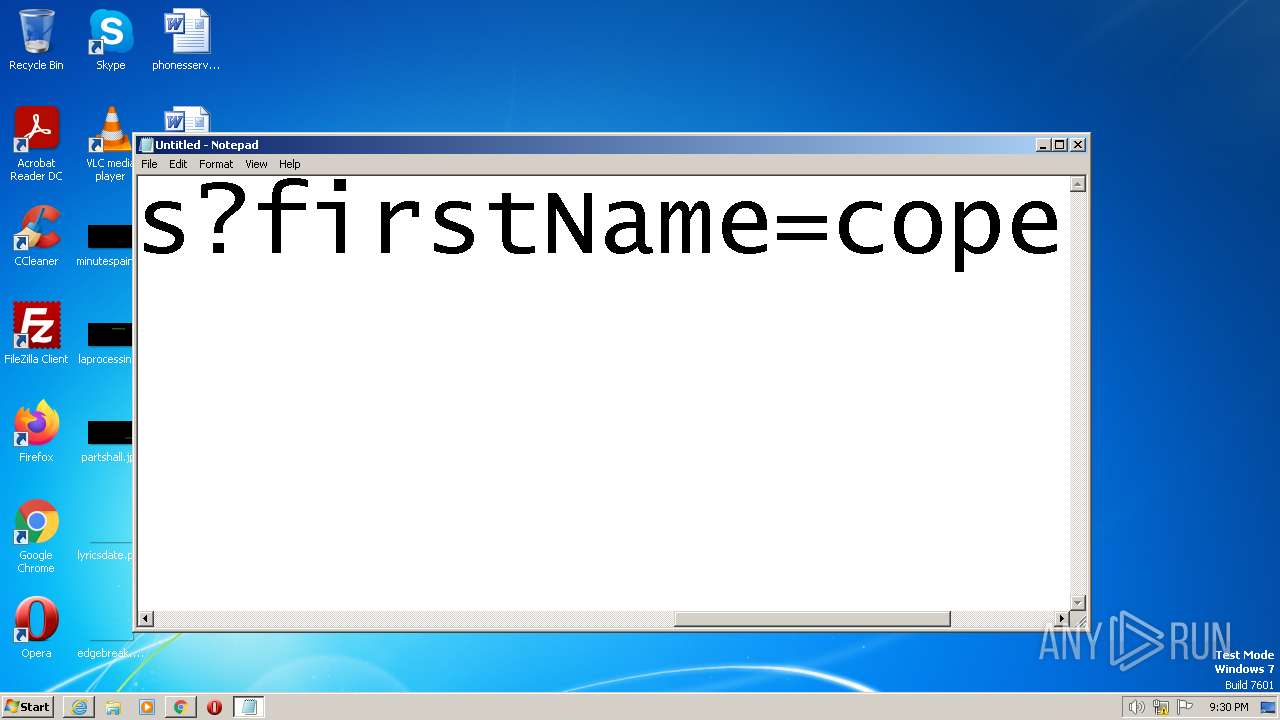
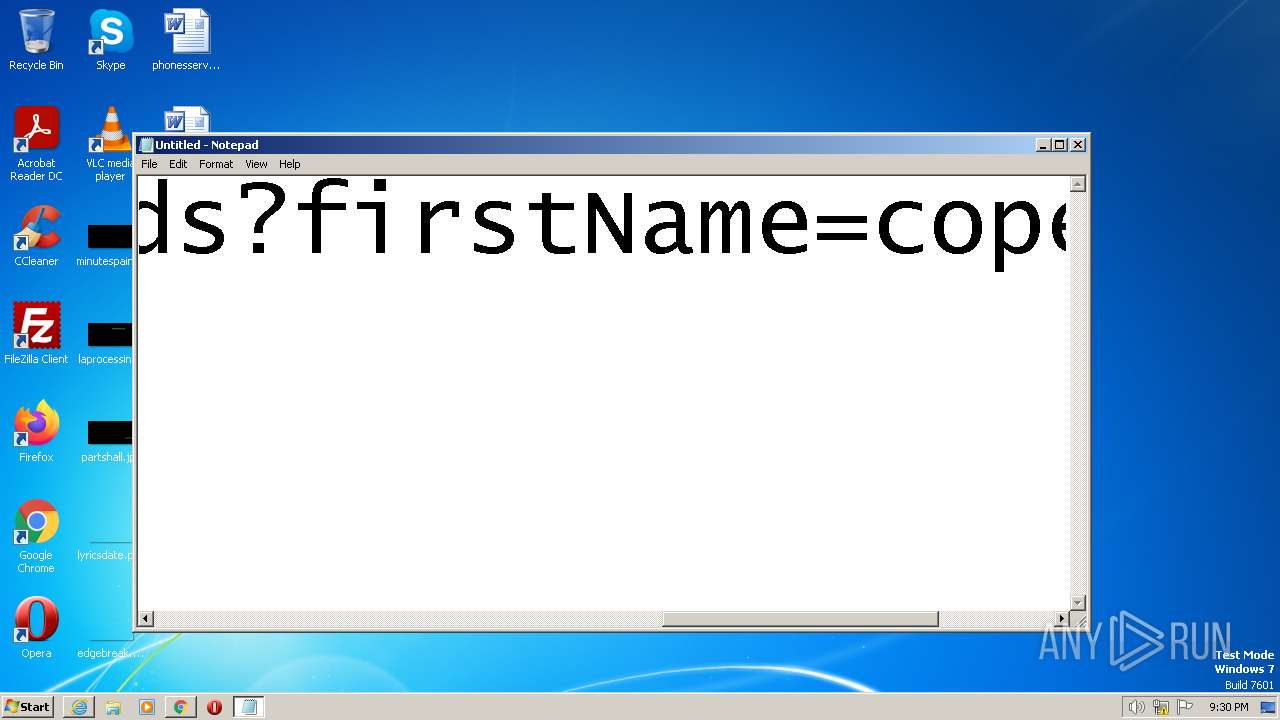
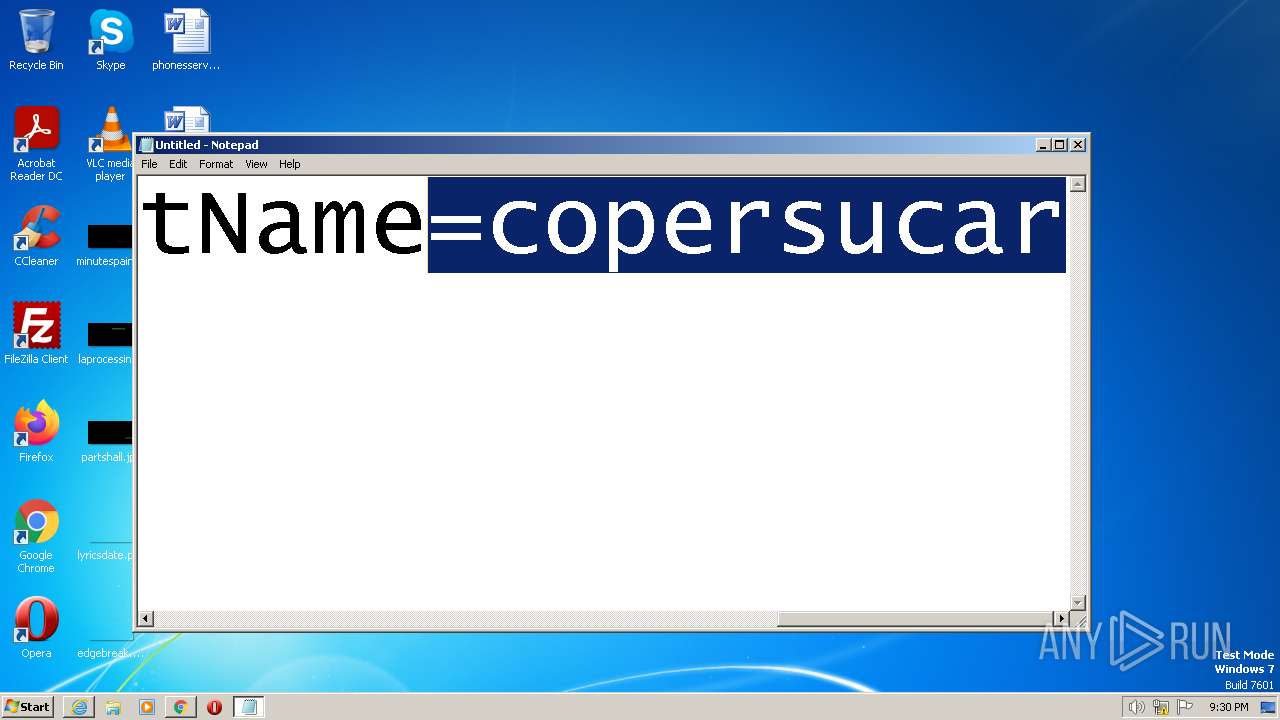
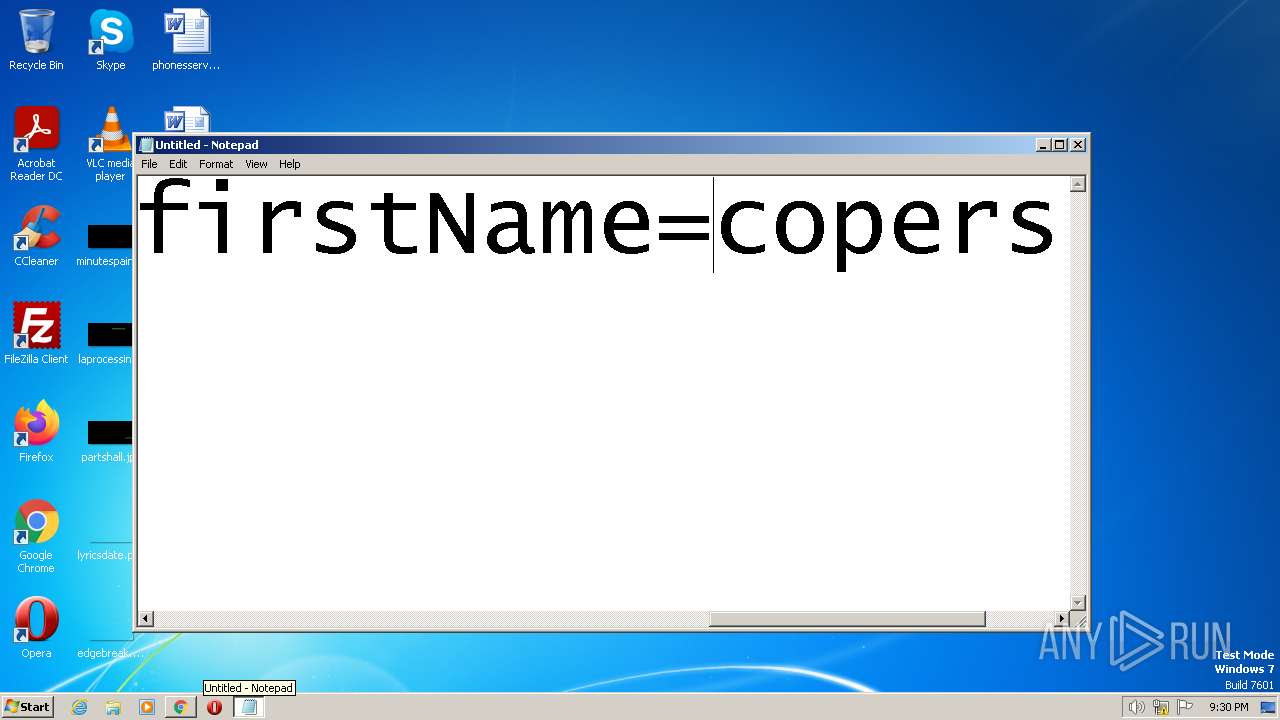
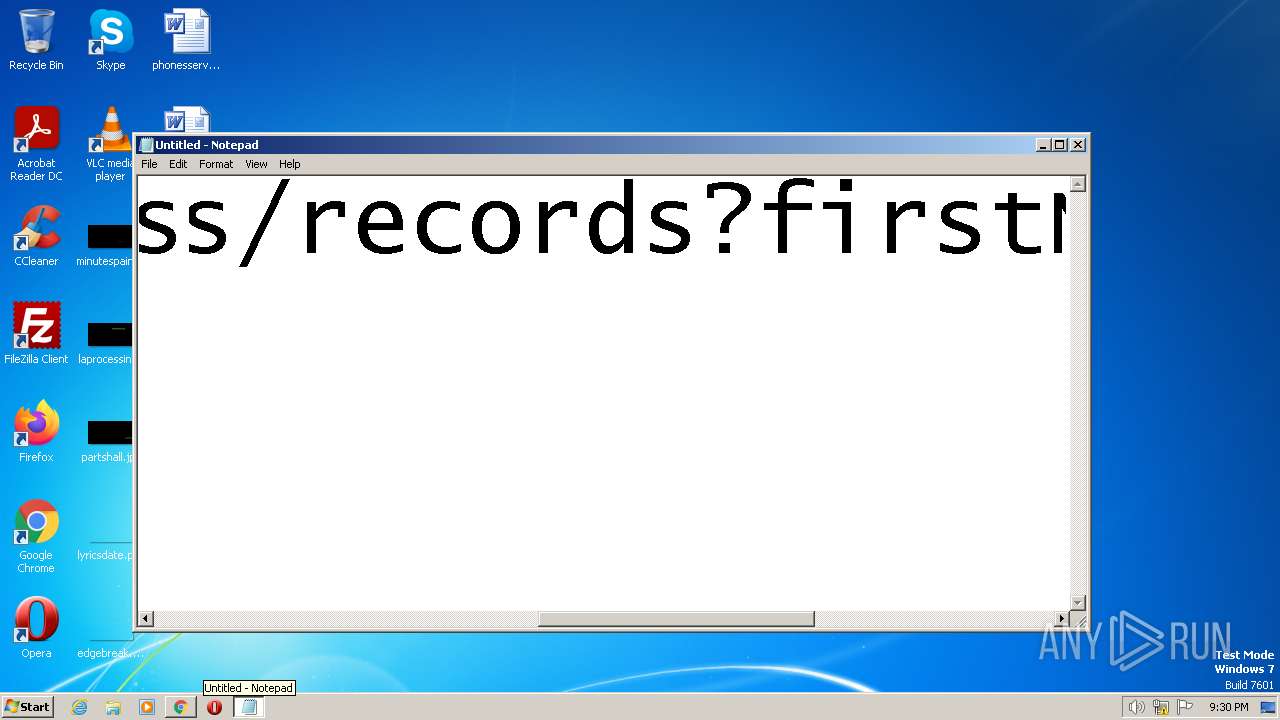
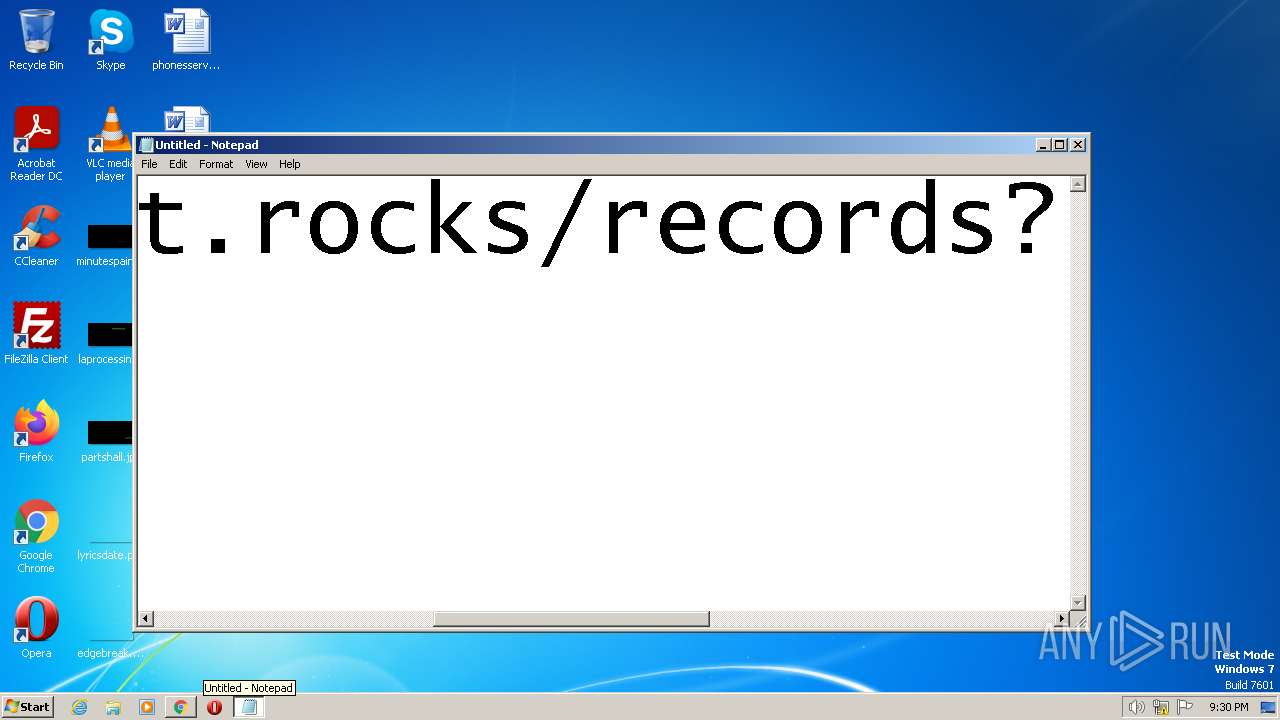
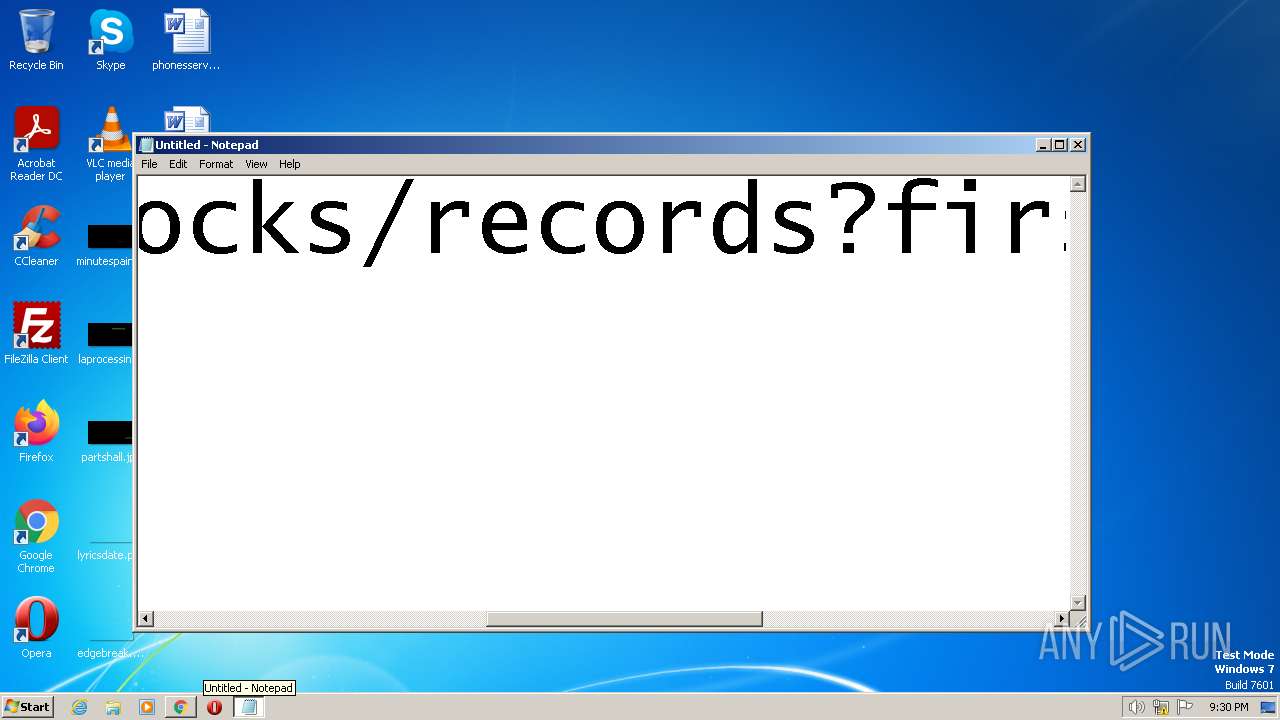
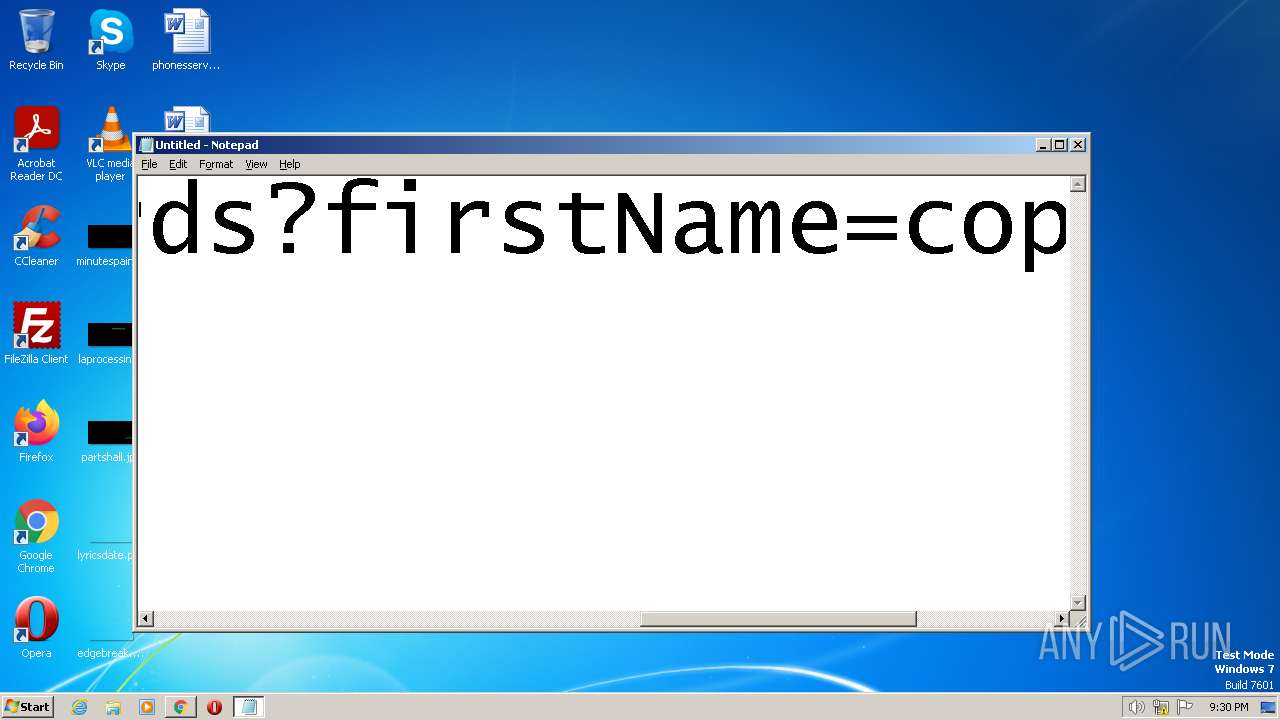
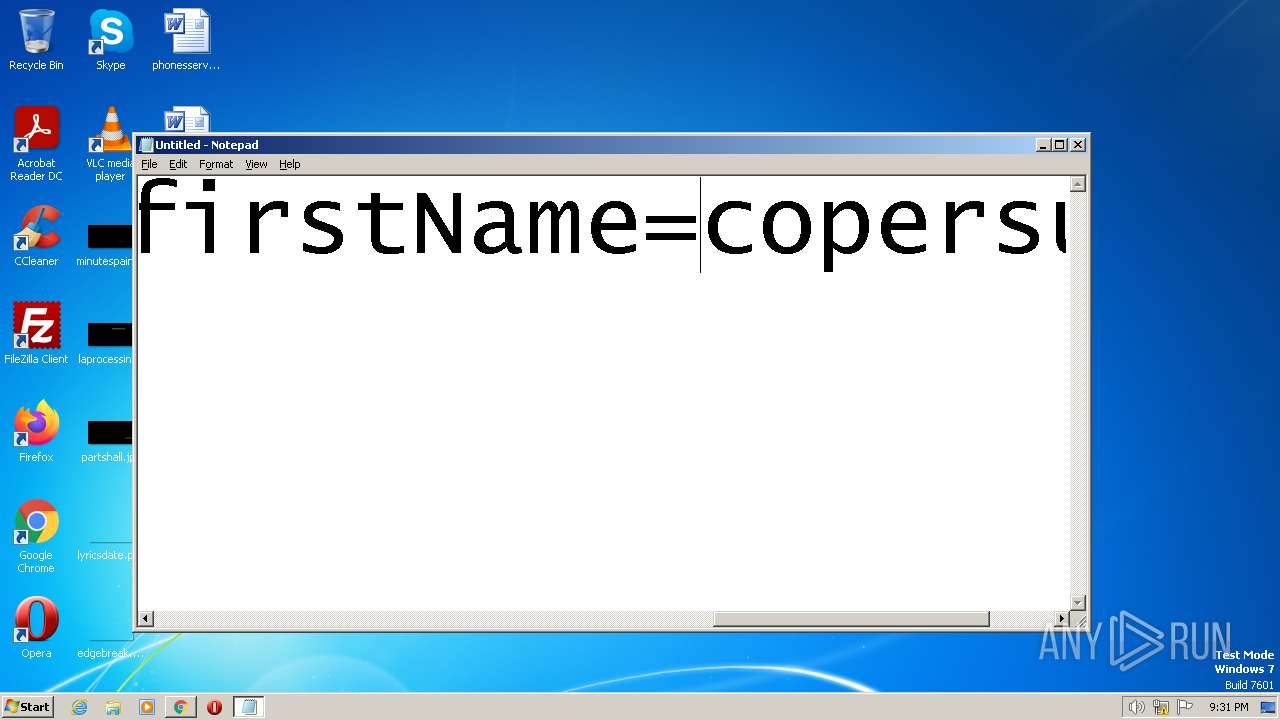
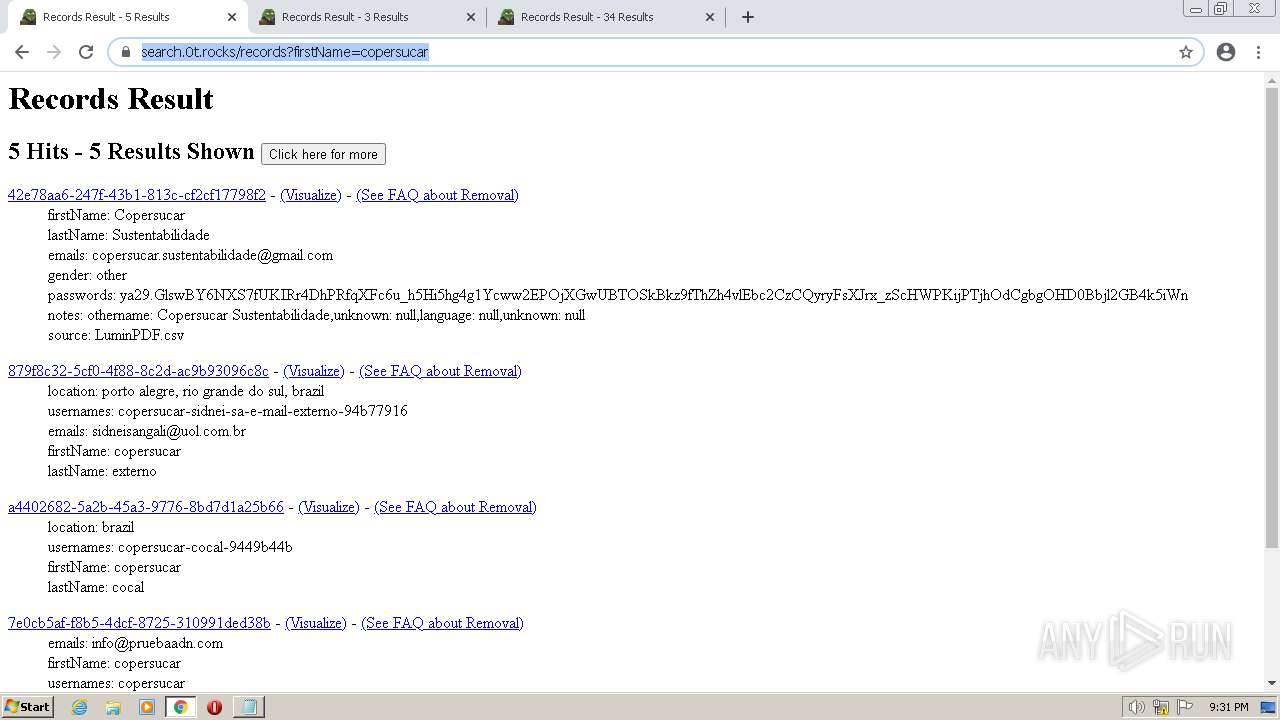
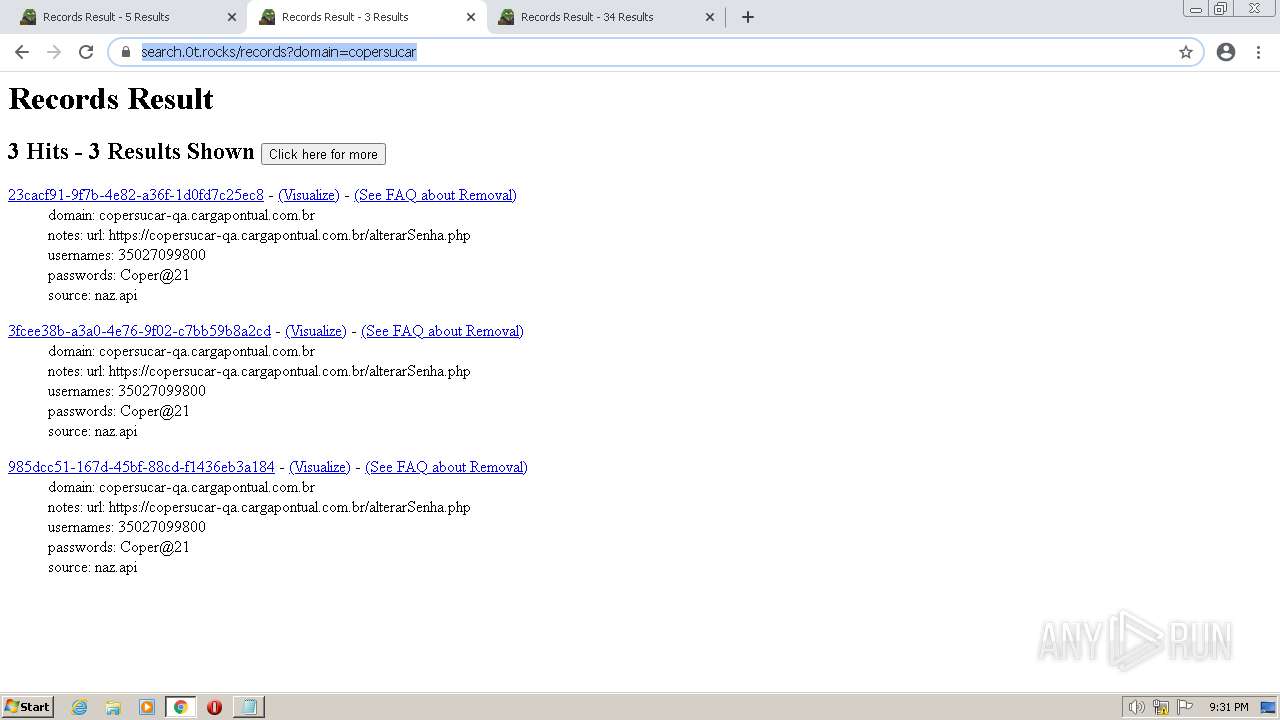
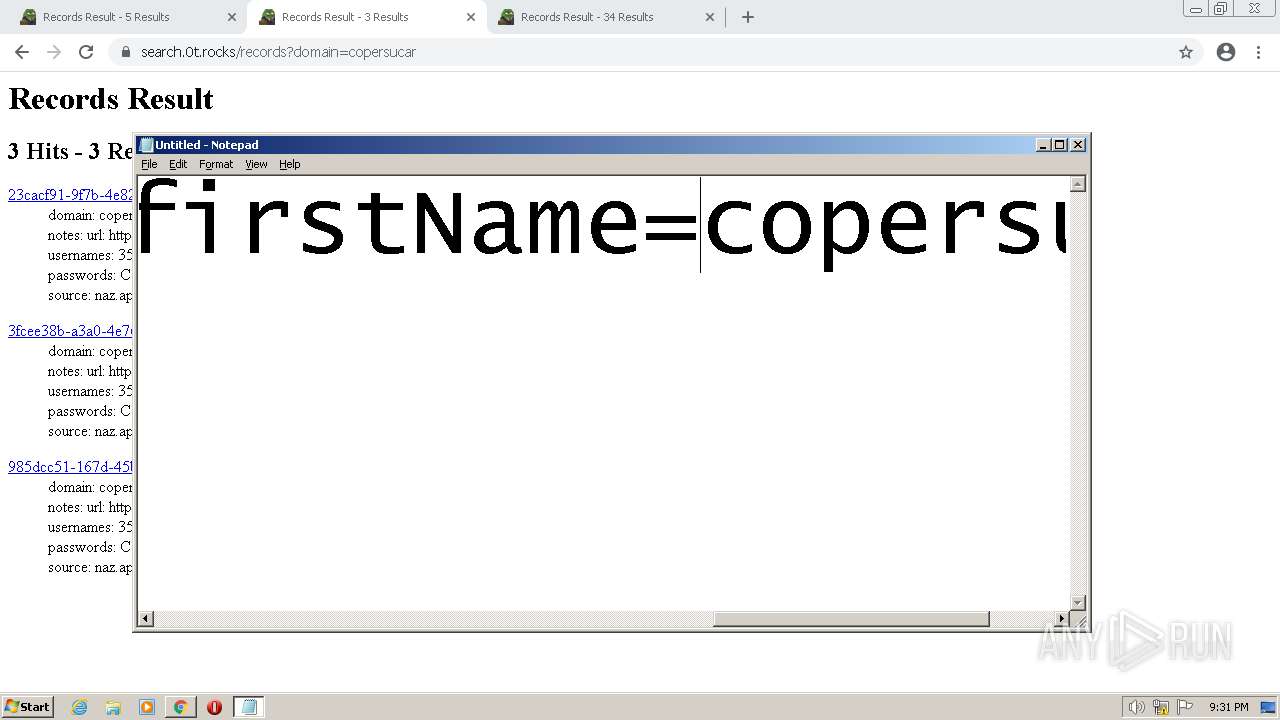
| URL: | https://search.illicit.services/records?domain=*.dock.tech&usernames=* |
| Full analysis: | https://app.any.run/tasks/28683684-8840-45c4-b253-c9dbe232c0cc |
| Verdict: | Malicious activity |
| Analysis date: | July 05, 2023, 20:26:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 96B9252C8BF9AE11C36A0E7B9A1C745F |
| SHA1: | 1047C1C87319ADC7D795E8C6F2868DE2C8BEAFA5 |
| SHA256: | B5800899FD5104C6F7D0845C643039FA1764094B62E5E802F5CC4F92533F754F |
| SSDEEP: | 3:N8N+J+HXs0DyiGSWYPn:2QJ+Hc0tGSWYPn |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 2508)
- firefox.exe (PID: 2468)
- firefox.exe (PID: 1300)
- chrome.exe (PID: 1464)
The process checks LSA protection
- dllhost.exe (PID: 2020)
Manual execution by a user
- firefox.exe (PID: 2468)
- notepad.exe (PID: 2680)
- chrome.exe (PID: 1464)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
84
Monitored processes
47
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 796 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1012,1858281152426602050,5166571607949373763,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --use-gl=swiftshader-webgl --mojo-platform-channel-handle=1116 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 944 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1012,1858281152426602050,5166571607949373763,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --mojo-platform-channel-handle=1032 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 956 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1012,1858281152426602050,5166571607949373763,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3048 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1100 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,1858281152426602050,5166571607949373763,131072 --enable-features=PasswordImport --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2268 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1172 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="1300.0.1204805435\1651435838" -parentBuildID 20201112153044 -prefsHandle 1124 -prefMapHandle 1116 -prefsLen 1 -prefMapSize 238726 -appdir "C:\Program Files\Mozilla Firefox\browser" - 1300 "\\.\pipe\gecko-crash-server-pipe.1300" 1224 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 1 Version: 83.0 Modules
| |||||||||||||||
| 1300 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 1396 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="1300.6.1357545923\1551580202" -childID 1 -isForBrowser -prefsHandle 4836 -prefMapHandle 4832 -prefsLen 181 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 1300 "\\.\pipe\gecko-crash-server-pipe.1300" 4848 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 1464 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1584 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="1300.13.700943593\861009711" -childID 2 -isForBrowser -prefsHandle 2516 -prefMapHandle 2512 -prefsLen 6644 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 1300 "\\.\pipe\gecko-crash-server-pipe.1300" 1416 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 1596 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1012,1858281152426602050,5166571607949373763,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3124 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
35 467
Read events
35 246
Write events
212
Delete events
9
Modification events
| (PID) Process: | (2508) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2508) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2508) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2508) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2508) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2508) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2508) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2508) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2508) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2508) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
10
Suspicious files
271
Text files
191
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1300 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 3580 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:509AA92CBA599B40A8A0B13196A753B1 | SHA256:EE325B9626236C7D51641A0986DB27020973FB3C4D4B06B41BA8D0AC0883B1F7 | |||
| 2508 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\{35A09685-1B72-11EE-B2B4-12A9866C77DE}.dat | binary | |
MD5:7EAF14CD088E652CBC49A17727D37ADE | SHA256:B39C7A2F106444D50EF7169FAB7D24406852487C6A382BC3547BDC3F53257624 | |||
| 2508 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{35A09684-1B72-11EE-B2B4-12A9866C77DE}.dat | binary | |
MD5:A7CD22DEF4302D3A1484D4F23E7FA0F2 | SHA256:B6732FBC39AB5E714CC486694DF599894980A8D08F090762493BCAA8E0E19397 | |||
| 2508 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\RecoveryStore.{42C873D0-1D90-11EB-BA2C-12A9866C77DE}.dat | binary | |
MD5:3F11AA373C4568EA053C52BCE361B10C | SHA256:F017F9D0BB48A5ADA7B2B23492B0D9E6DE858AB4606BD7488D67296F94E9031F | |||
| 2508 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF0C3BA88E51A26F48.TMP | binary | |
MD5:1F1BB46D6F9E7A84D2FC153D47E6CEEC | SHA256:31197F3EE95DBBC7C914703A0866A77D2E4ACB82900F6C3CB8F2645321F5F21A | |||
| 1300 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2508 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{2C0DA51F-1B72-11EE-B2B4-12A9866C77DE}.dat | binary | |
MD5:7803556556E6FD3B6ECFBBE784112E2E | SHA256:27DD93DCF4D96E44F9E5947A6DF74A0B574810695D265DAB85F6399DCE93ACCA | |||
| 1300 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:994A33896BB41A278A315D0D796422B6 | SHA256:54EC50A20FFF8CC016710E49437CF6A11D3FE5EE7B28C185E4A9AAFEE2908B63 | |||
| 1300 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
39
TCP/UDP connections
119
DNS requests
93
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1300 | firefox.exe | GET | — | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | US | — | — | whitelisted |
3224 | chrome.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | binary | 242 Kb | whitelisted |
3224 | chrome.exe | GET | 200 | 67.27.234.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?89b1dff44d6295c4 | US | compressed | 62.3 Kb | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
1300 | firefox.exe | POST | 200 | 95.101.54.130:80 | http://e1.o.lencr.org/ | DE | binary | 345 b | whitelisted |
852 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjg0QUFYSnN4MFUtaEQwNDZqVGRkVkFmZw/1.0.6.0_aemomkdncapdnfajjbbcbdebjljbpmpj.crx | US | binary | 3.40 Kb | whitelisted |
1300 | firefox.exe | POST | 200 | 95.101.54.123:80 | http://r3.o.lencr.org/ | DE | der | 503 b | shared |
852 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | US | binary | 8.49 Kb | whitelisted |
852 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | US | binary | 3.40 Kb | whitelisted |
852 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjg0QUFYSnN4MFUtaEQwNDZqVGRkVkFmZw/1.0.6.0_aemomkdncapdnfajjbbcbdebjljbpmpj.crx | US | binary | 3.40 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
820 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3580 | iexplore.exe | 172.67.70.102:443 | search.illicit.services | CLOUDFLARENET | US | unknown |
3580 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3580 | iexplore.exe | 142.250.185.227:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
2508 | iexplore.exe | 2.16.241.144:443 | www.bing.com | Akamai International B.V. | DE | suspicious |
3580 | iexplore.exe | 104.26.7.232:443 | search.illicit.services | CLOUDFLARENET | US | unknown |
1300 | firefox.exe | 52.34.120.119:443 | location.services.mozilla.com | AMAZON-02 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
search.illicit.services |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.pki.goog |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
firefox.settings.services.mozilla.com |
| whitelisted |
prod.remote-settings.prod.webservices.mozgcp.net |
| whitelisted |