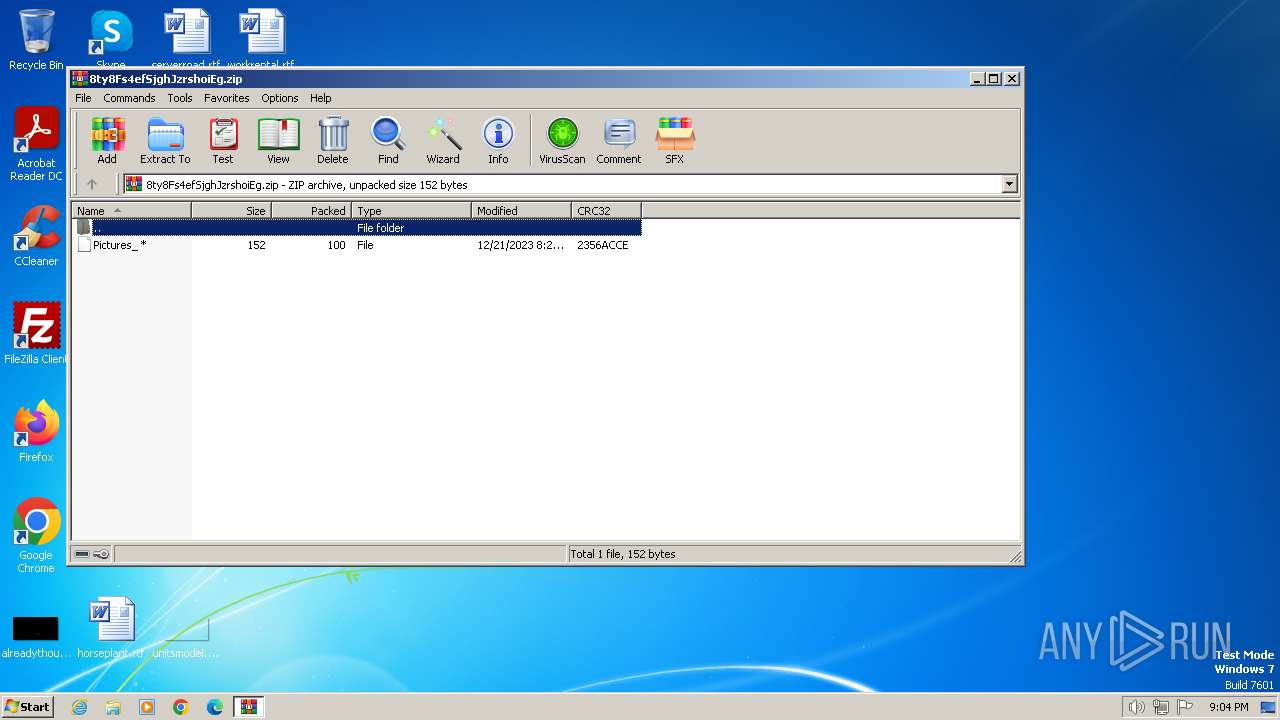
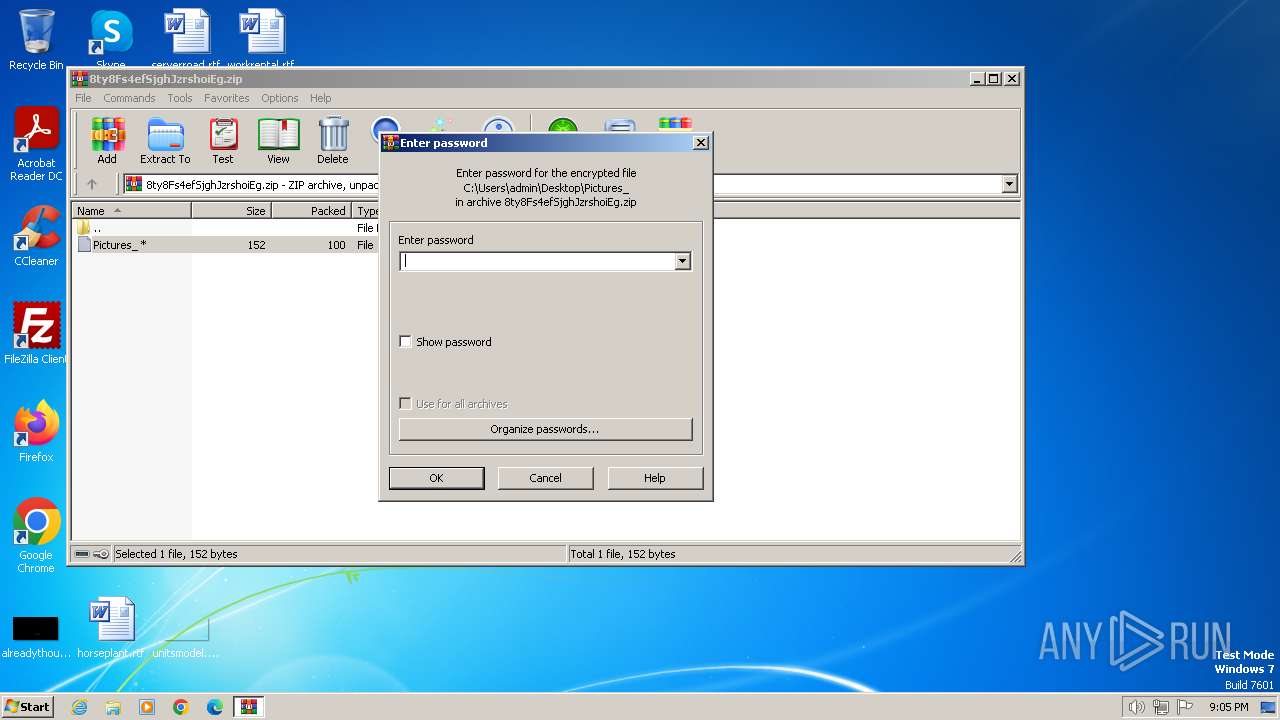
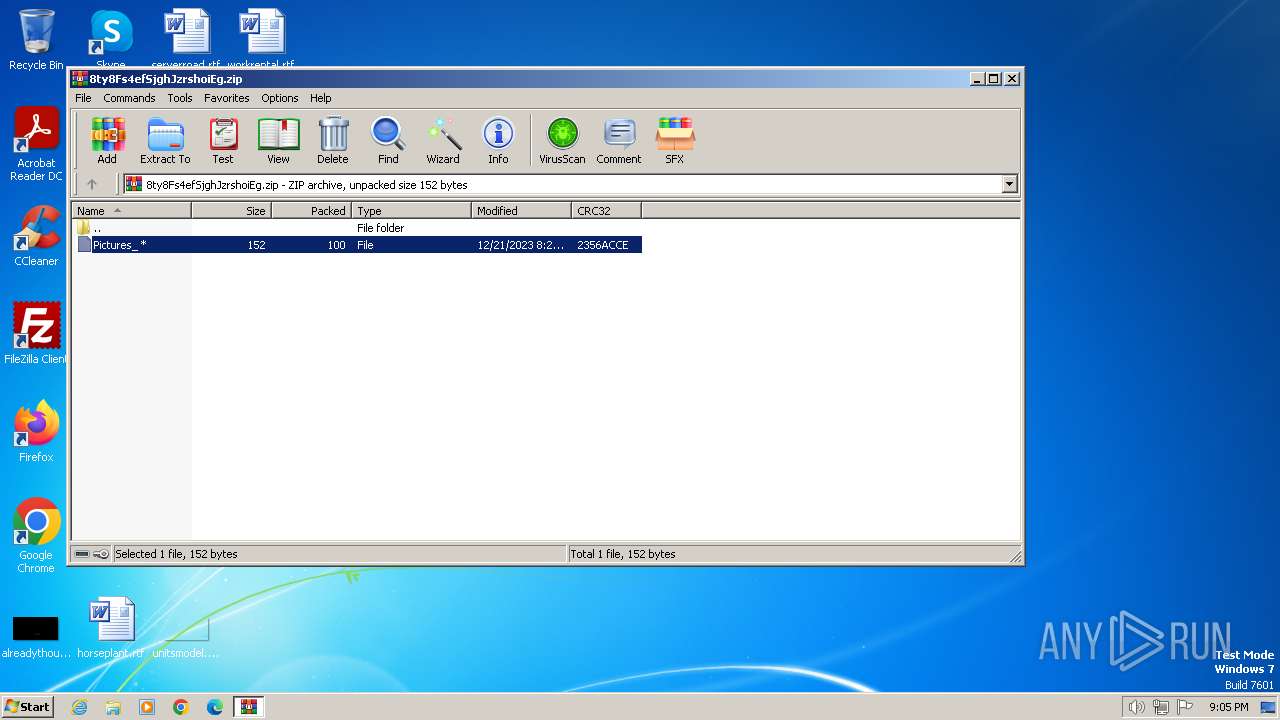
| File name: | 8ty8Fs4efSjghJzrshoiEg.zip |
| Full analysis: | https://app.any.run/tasks/4a182875-58a4-4c91-bd18-ccf9acdab510 |
| Verdict: | Malicious activity |
| Analysis date: | December 21, 2023, 21:04:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 6F23E0630A081B58EE77F9963E5CD261 |
| SHA1: | A5A815DBE47B32F13CF265BEFC2BA32AB25791D2 |
| SHA256: | B577D7111AE4BFEA8C85CB3D89C6152AD6A07C01CC331A64F6151749B37591AE |
| SSDEEP: | 6:5juu4IHlfcKv5zmShVGoGx1NjXnHu7kVzW/Cxxuu4IJBt+lU5:5juu4IHlfc0wUkx3nAgzW/Cx4u4IJLaM |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Internet Settings
- rundll32.exe (PID: 2300)
- rundll32.exe (PID: 696)
- rundll32.exe (PID: 2968)
- rundll32.exe (PID: 2788)
- rundll32.exe (PID: 3048)
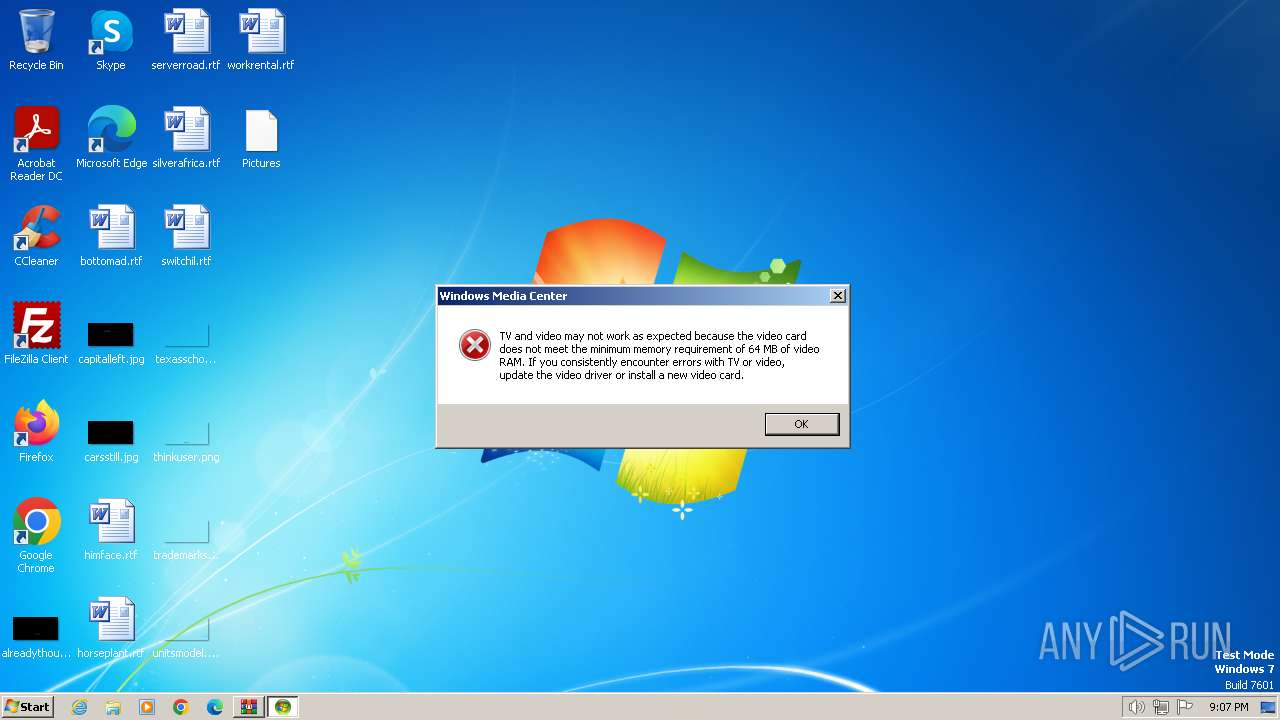
- ehshell.exe (PID: 2508)
- wmplayer.exe (PID: 2460)
- rundll32.exe (PID: 2960)
- rundll32.exe (PID: 1556)
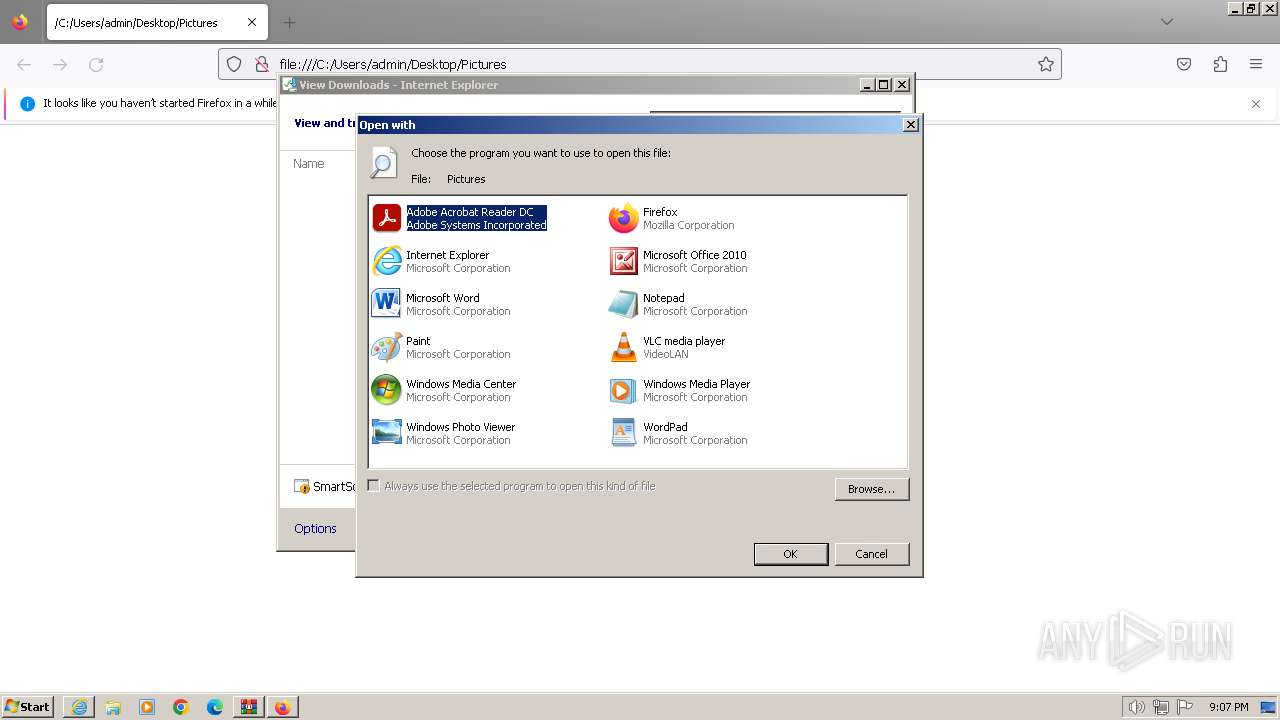
Uses RUNDLL32.EXE to load library
- iexplore.exe (PID: 2316)
INFO
Manual execution by a user
- rundll32.exe (PID: 1380)
- rundll32.exe (PID: 696)
- rundll32.exe (PID: 2300)
- iexplore.exe (PID: 2316)
- rundll32.exe (PID: 2968)
- rundll32.exe (PID: 3048)
- ehtray.exe (PID: 3484)
- rundll32.exe (PID: 2960)
- rundll32.exe (PID: 1556)
- ehtray.exe (PID: 3424)
Creates files in the program directory
- ehshell.exe (PID: 2508)
- ehrecvr.exe (PID: 2304)
- ehshell.exe (PID: 2312)
Application launched itself
- AcroRd32.exe (PID: 2096)
- RdrCEF.exe (PID: 1232)
- firefox.exe (PID: 2944)
- firefox.exe (PID: 3032)
- iexplore.exe (PID: 2316)
Checks supported languages
- ehshell.exe (PID: 2508)
- wmplayer.exe (PID: 2460)
- ehrecvr.exe (PID: 2304)
- ehsched.exe (PID: 3564)
- ehtray.exe (PID: 3484)
- ehsched.exe (PID: 3508)
- ehrec.exe (PID: 4040)
- ehshell.exe (PID: 2312)
- ehtray.exe (PID: 3424)
- ehrec.exe (PID: 1528)
- vlc.exe (PID: 3604)
Reads the computer name
- ehshell.exe (PID: 2508)
- wmplayer.exe (PID: 2460)
- ehrecvr.exe (PID: 2304)
- ehsched.exe (PID: 3564)
- ehtray.exe (PID: 3484)
- ehrec.exe (PID: 4040)
- ehshell.exe (PID: 2312)
- ehsched.exe (PID: 3508)
- ehtray.exe (PID: 3424)
- vlc.exe (PID: 3604)
- ehrec.exe (PID: 1528)
Reads the machine GUID from the registry
- ehshell.exe (PID: 2508)
- wmplayer.exe (PID: 2460)
- ehrecvr.exe (PID: 2304)
- ehsched.exe (PID: 3564)
- ehtray.exe (PID: 3484)
- ehrec.exe (PID: 4040)
- ehshell.exe (PID: 2312)
- ehsched.exe (PID: 3508)
- ehtray.exe (PID: 3424)
- ehrec.exe (PID: 1528)
Process checks computer location settings
- ehshell.exe (PID: 2508)
- ehshell.exe (PID: 2312)
- wmplayer.exe (PID: 2460)
Reads Environment values
- ehshell.exe (PID: 2508)
- wmplayer.exe (PID: 2460)
Executes as Windows Service
- ehrecvr.exe (PID: 2304)
- ehsched.exe (PID: 3564)
- ehsched.exe (PID: 3508)
Creates files or folders in the user directory
- ehshell.exe (PID: 2508)
- wmplayer.exe (PID: 2460)
Checks proxy server information
- wmplayer.exe (PID: 2460)
Drops the executable file immediately after the start
- ehrec.exe (PID: 4040)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:12:21 15:24:38 |
| ZipCRC: | 0x2356acce |
| ZipCompressedSize: | 100 |
| ZipUncompressedSize: | 152 |
| ZipFileName: | Pictures_ |
Total processes
86
Monitored processes
44
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 572 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3032.7.1495773830\353587962" -childID 6 -isForBrowser -prefsHandle 4084 -prefMapHandle 4120 -prefsLen 34225 -prefMapSize 244195 -jsInitHandle 884 -jsInitLen 240908 -parentBuildID 20230710165010 -appDir "C:\Program Files\Mozilla Firefox\browser" - {a6b8e479-8fc9-4633-83b0-d2c37f075280} 3032 "\\.\pipe\gecko-crash-server-pipe.3032" 3944 18386c90 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
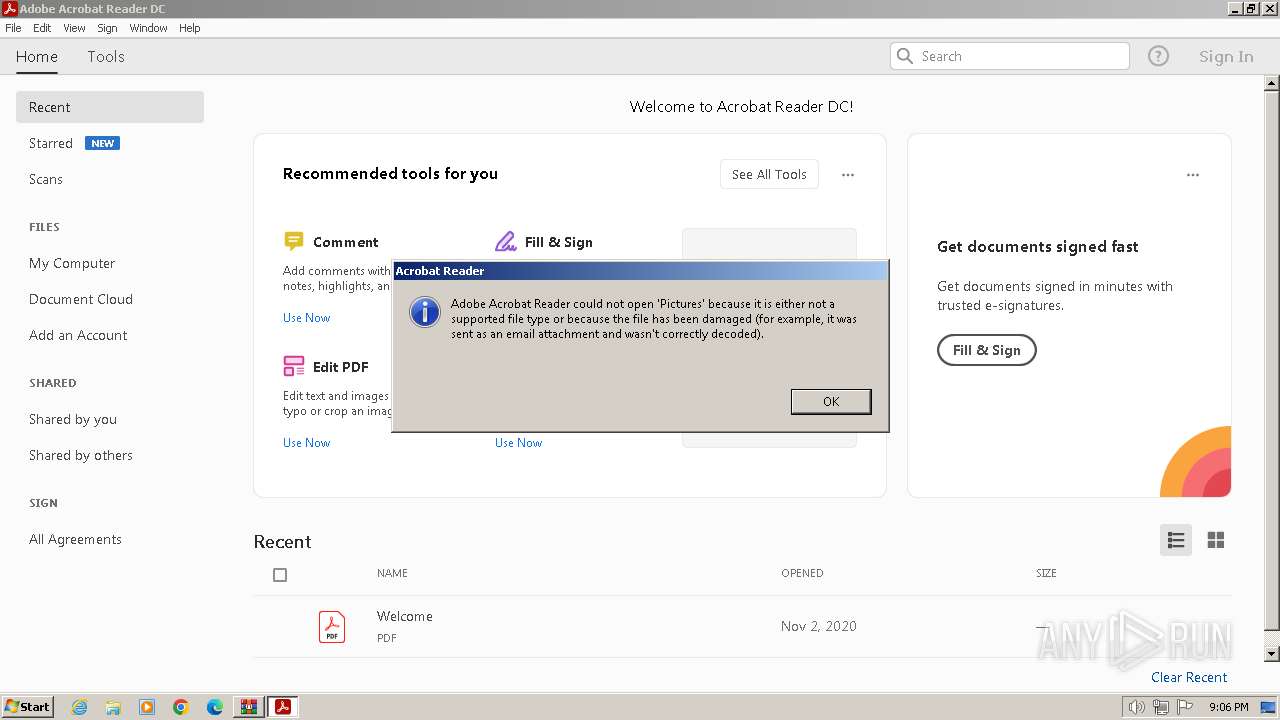
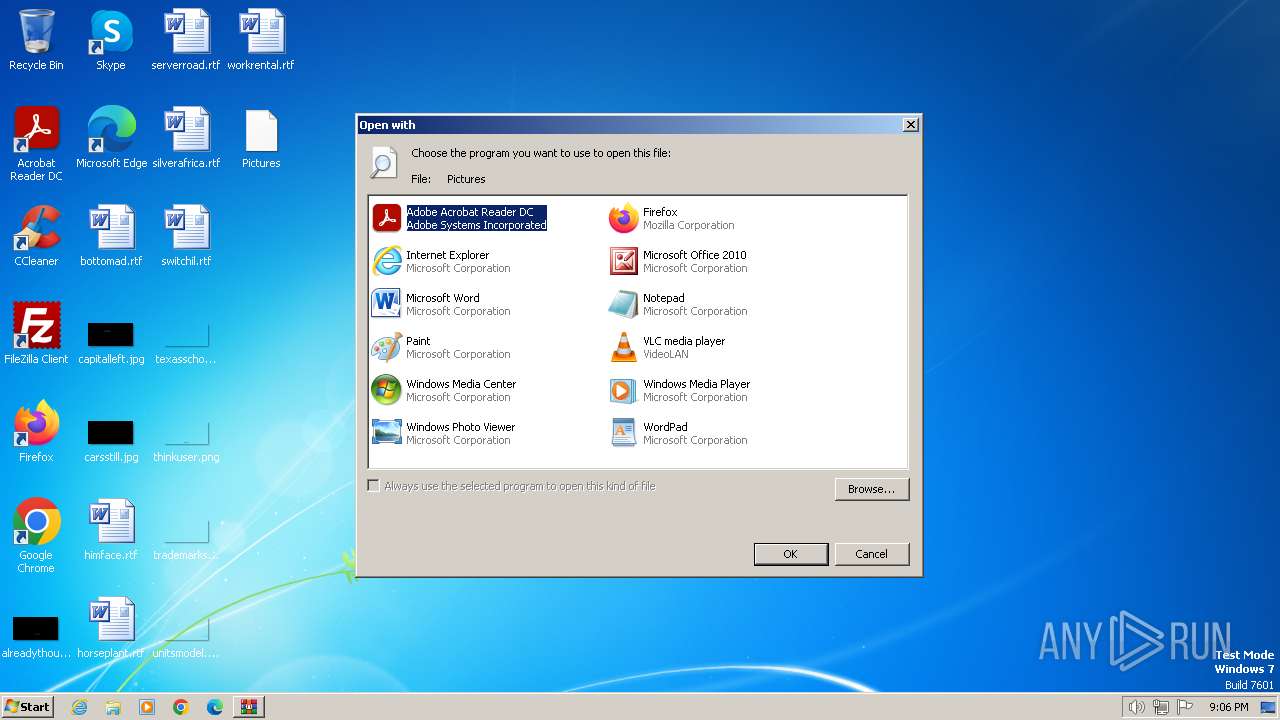
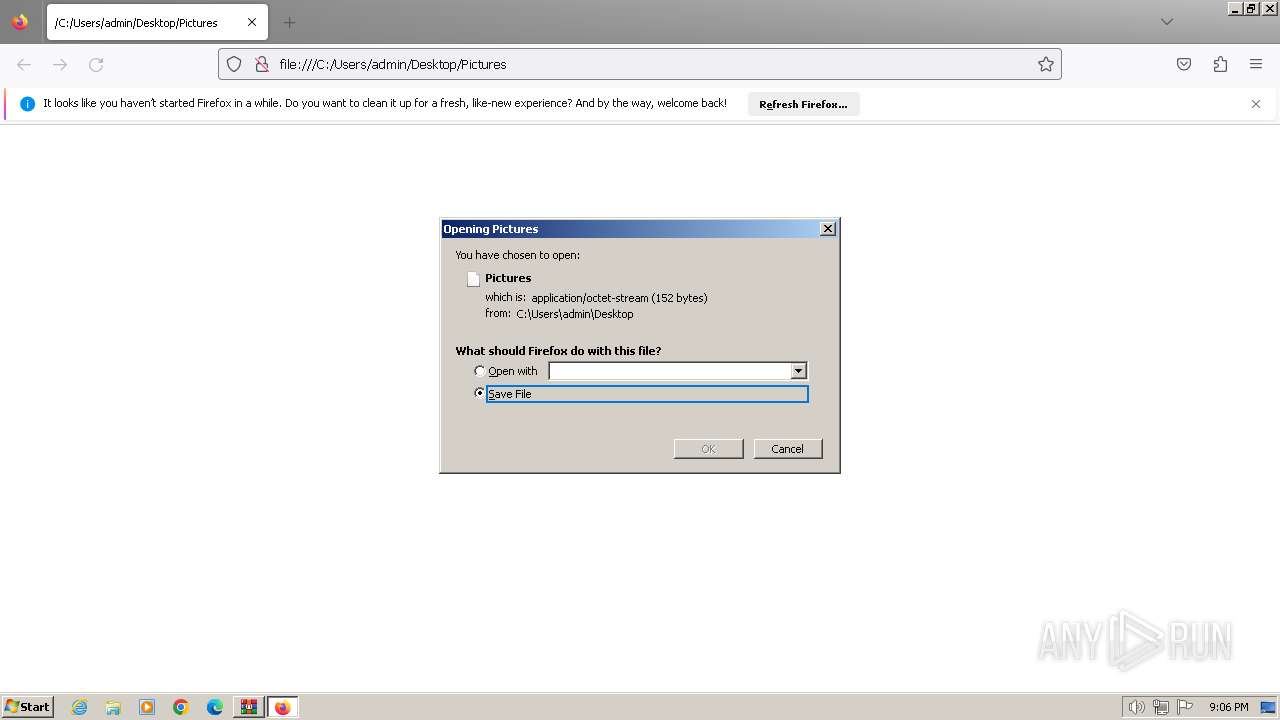
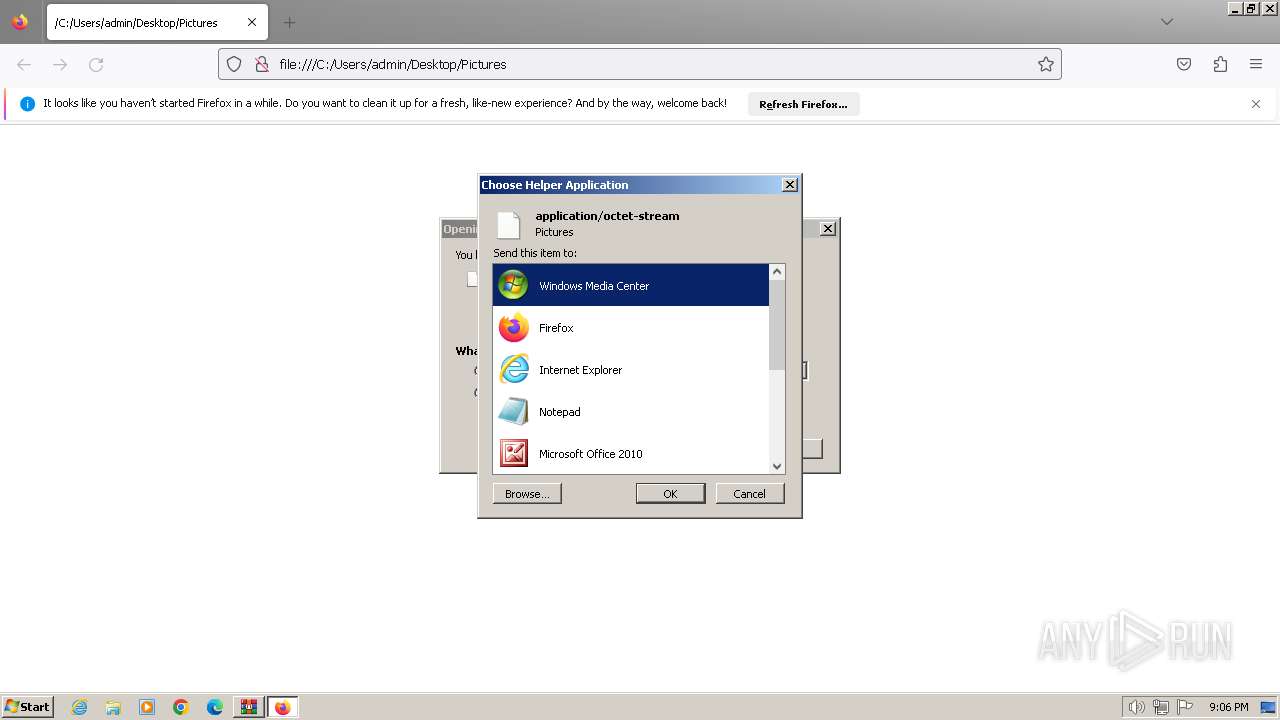
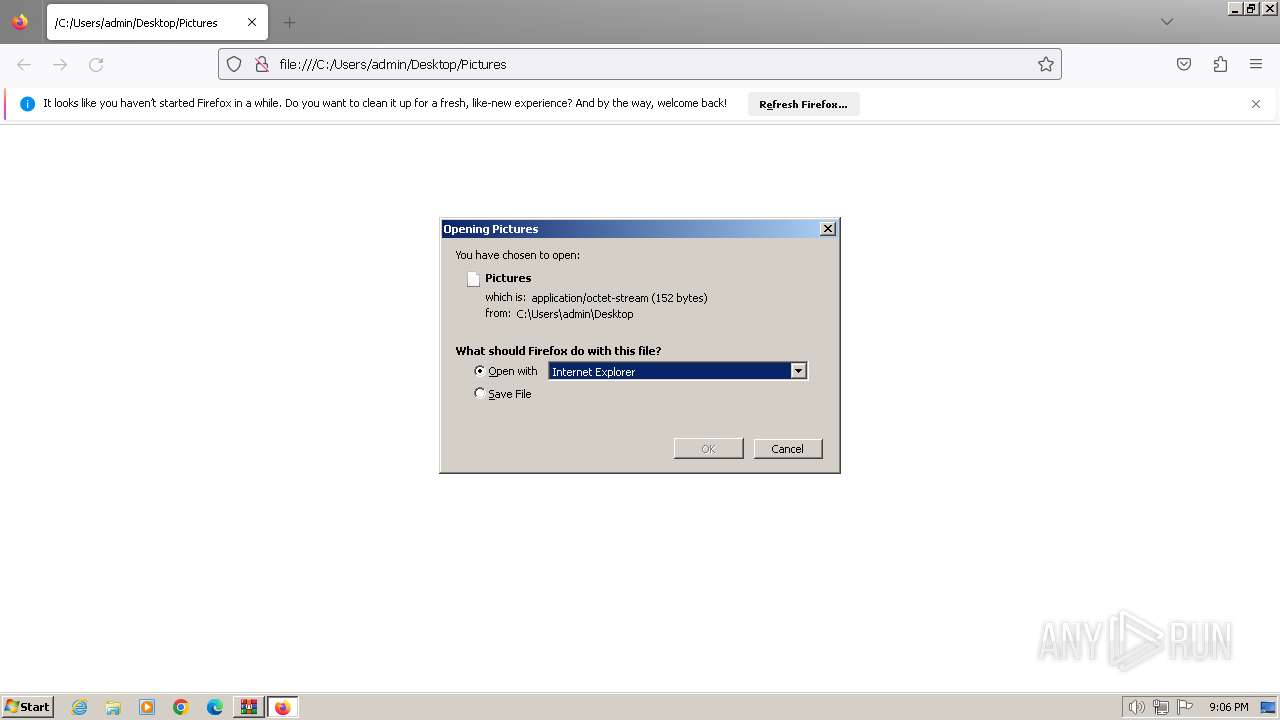
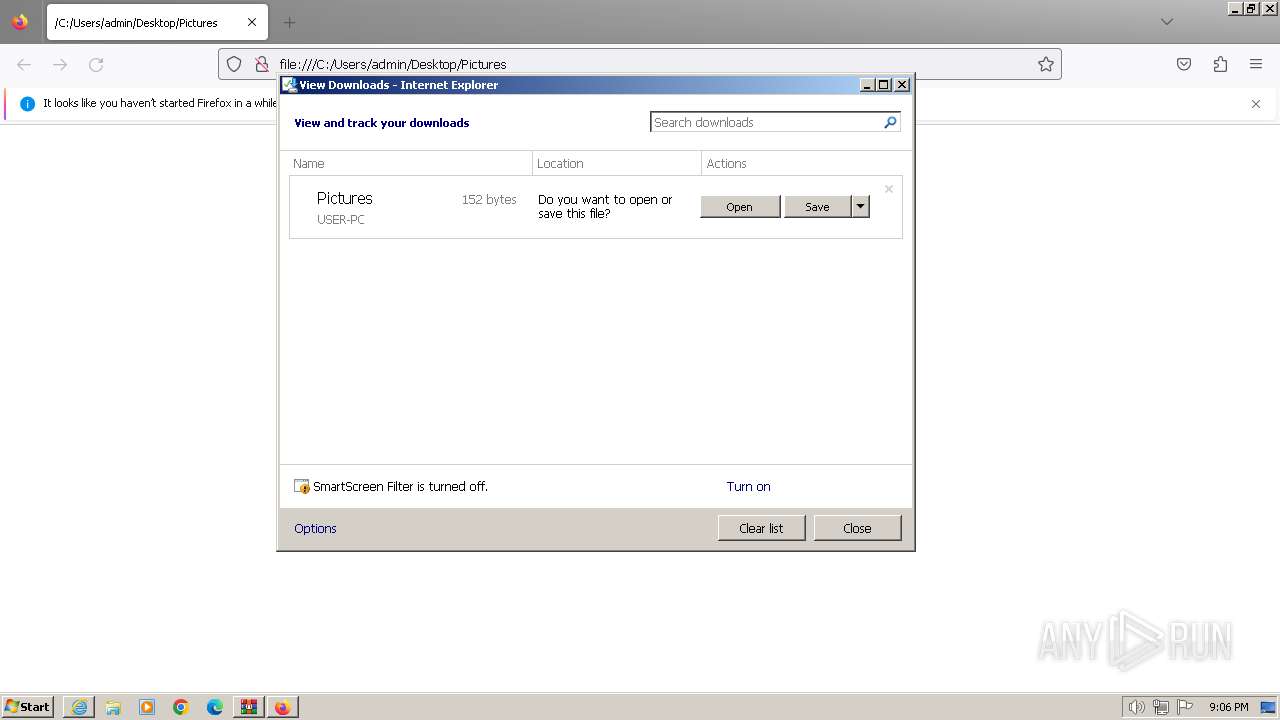
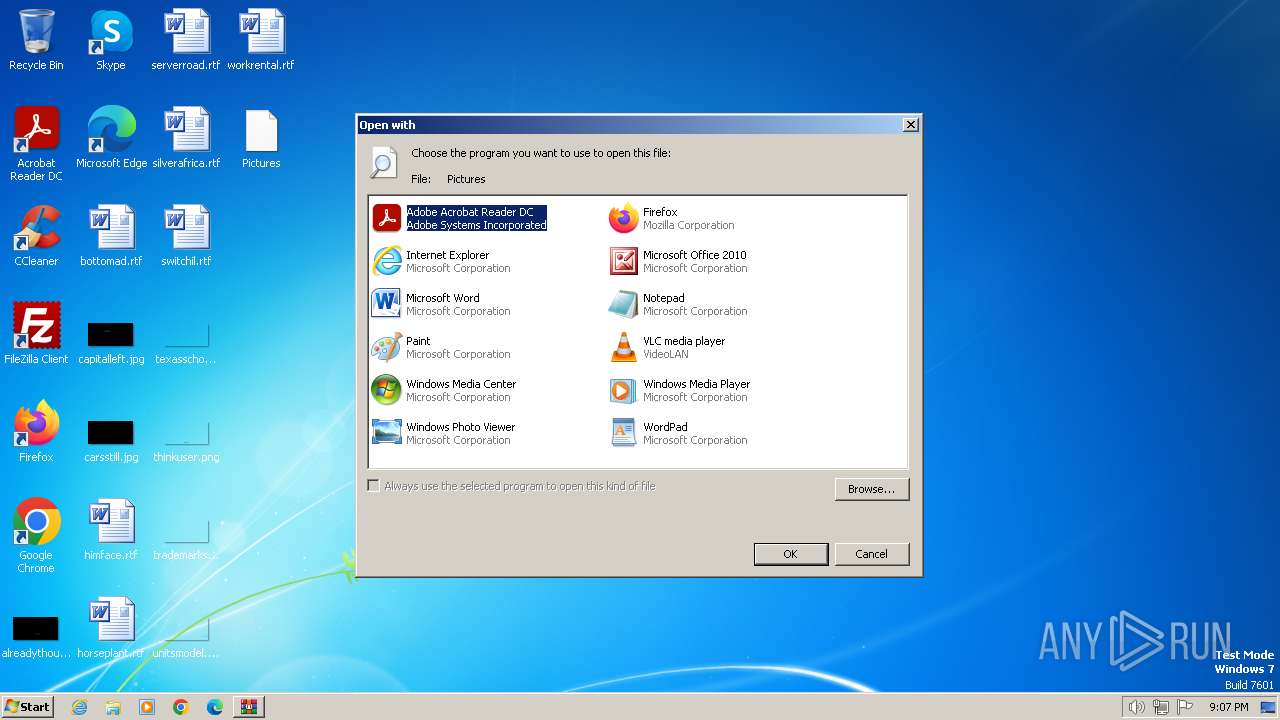
| 696 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\Pictures | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 908 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1156,14637910537695706829,13029155377920505168,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7153866409666336749 --renderer-client-id=7 --mojo-platform-channel-handle=2364 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1044 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1232 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16514043 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1380 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\Pictures | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1432 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\8ty8Fs4efSjghJzrshoiEg.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1528 | C:\Windows\ehome\ehRec.exe -Embedding | C:\Windows\ehome\ehrec.exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Media Center Host Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1556 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1156,14637910537695706829,13029155377920505168,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=11983651020904617462 --renderer-client-id=2 --mojo-platform-channel-handle=1164 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1556 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\Pictures | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
39 797
Read events
38 595
Write events
943
Delete events
259
Modification events
| (PID) Process: | (1432) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1432) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1432) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1432) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1432) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (1432) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1432) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1432) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1432) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1380) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
3
Suspicious files
222
Text files
39
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1232 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\febb41df4ea2b63a_0 | binary | |
MD5:B117A1365EDE2EF970FF60A6F616C01E | SHA256:3EF753CB7EA5E5A03EFE2C4861496AFF3E3D43BB2E47B83057F91C8BC33DC787 | |||
| 1232 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\560e9c8bff5008d8_0 | binary | |
MD5:B70A3BAE97BF907C272614728B5C7090 | SHA256:4EA5757B7EA3538B38E1ED9D4C46DE228255860472061CE6740A302BF7AB4C67 | |||
| 1232 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\2a426f11fd8ebe18_0 | binary | |
MD5:42FDDE11CBF03C6B16807E0353CD96B8 | SHA256:51AF611F4D2ED706D7845200AC99FE5ECF2D99ACAE76413485C9E28AC4769A4E | |||
| 1232 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\8e417e79df3bf0e9_0 | binary | |
MD5:22C0022E42DAC044FC16A6135867F4CD | SHA256:474DF04A0B8F5F3368CE4767485E1352C39110D586DB3D497219028492EE1B9A | |||
| 1232 | RdrCEF.exe | — | ||
MD5:— | SHA256:— | |||
| 1232 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\72d9f526d2e2e7c8_0 | binary | |
MD5:2A3B9087BB8B9B818E6831909B593486 | SHA256:548F6B41C3A08FDC9478875883E010BE8B99BE378910C89FEC9006C6886BBE45 | |||
| 1232 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\f941376b2efdd6e6_0 | binary | |
MD5:76D1C57C8F53D24CF2903155D9689A86 | SHA256:9AE7349AD226842FF76C615AEB3481AC3DB9D8FC8B0BFE9B65C3EF3BBFF67679 | |||
| 2336 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Reader\Files\TESTING | mp3 | |
MD5:DC84B0D741E5BEAE8070013ADDCC8C28 | SHA256:81FF65EFC4487853BDB4625559E69AB44F19E0F5EFBD6D5B2AF5E3AB267C8E06 | |||
| 1232 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\86b8040b7132b608_0 | binary | |
MD5:D8DDA53E566A89BF2A736D9429B658C8 | SHA256:F9747EDA2580D9704B7D53F2A7E088525004777CF77690225BBB0E5DDA81726C | |||
| 1232 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\983b7a3da8f39a46_0 | binary | |
MD5:95C0DF025F7F31F1F9F4F9CE92762B1B | SHA256:395E0F746B87A7A10067EAFEBD01AC4D44827703B8D50153B327C1A80DC1BE8E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
56
DNS requests
203
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3032 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | text | 90 b | unknown |
2096 | AcroRd32.exe | GET | — | 2.16.2.154:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?120fad9c75deed2b | unknown | — | — | unknown |
3032 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | text | 8 b | unknown |
3032 | firefox.exe | POST | 200 | 2.16.2.73:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
3032 | firefox.exe | POST | 200 | 2.16.2.73:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
3032 | firefox.exe | POST | 200 | 2.16.2.73:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
3032 | firefox.exe | POST | 200 | 2.16.2.73:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
3032 | firefox.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | binary | 471 b | unknown |
3032 | firefox.exe | POST | 200 | 2.16.2.73:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
3032 | firefox.exe | POST | 200 | 2.16.2.73:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1232 | RdrCEF.exe | 23.73.140.157:443 | geo2.adobe.com | AKAMAI-AS | CZ | unknown |
1232 | RdrCEF.exe | 34.237.241.83:443 | p13n.adobe.io | AMAZON-AES | US | unknown |
1232 | RdrCEF.exe | 2.23.8.158:443 | armmf.adobe.com | AKAMAI-AS | CZ | unknown |
2096 | AcroRd32.exe | 23.44.215.48:443 | acroipm2.adobe.com | Akamai International B.V. | CZ | unknown |
2096 | AcroRd32.exe | 2.16.2.154:80 | ctldl.windowsupdate.com | Akamai International B.V. | CZ | whitelisted |
3032 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
3032 | firefox.exe | 52.86.78.173:443 | spocs.getpocket.com | AMAZON-AES | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
geo2.adobe.com |
| whitelisted |
p13n.adobe.io |
| whitelisted |
armmf.adobe.com |
| whitelisted |
acroipm2.adobe.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| shared |
firefox.settings.services.mozilla.com |
| whitelisted |
safebrowsing.googleapis.com |
| unknown |
Threats
Process | Message |
|---|---|
ehshell.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
ehshell.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
ehshell.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
ehshell.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
ehshell.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
ehshell.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
ehshell.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
ehshell.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
ehshell.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
ehshell.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|