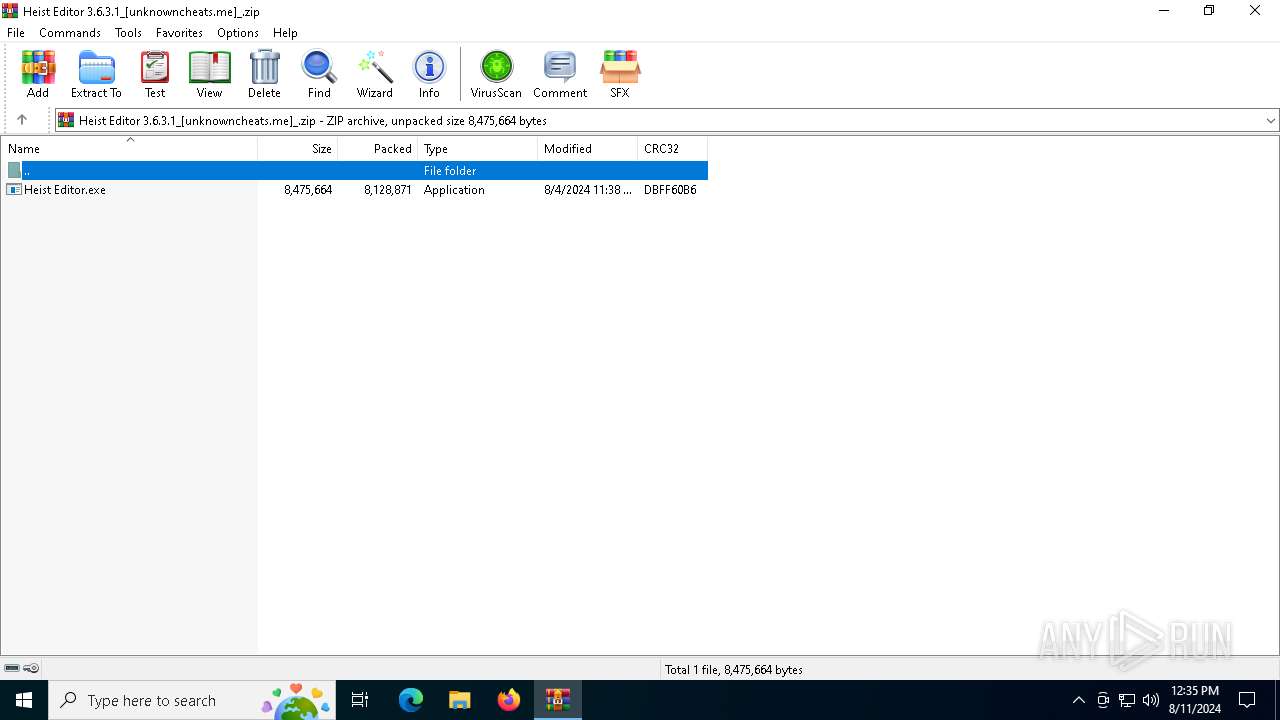
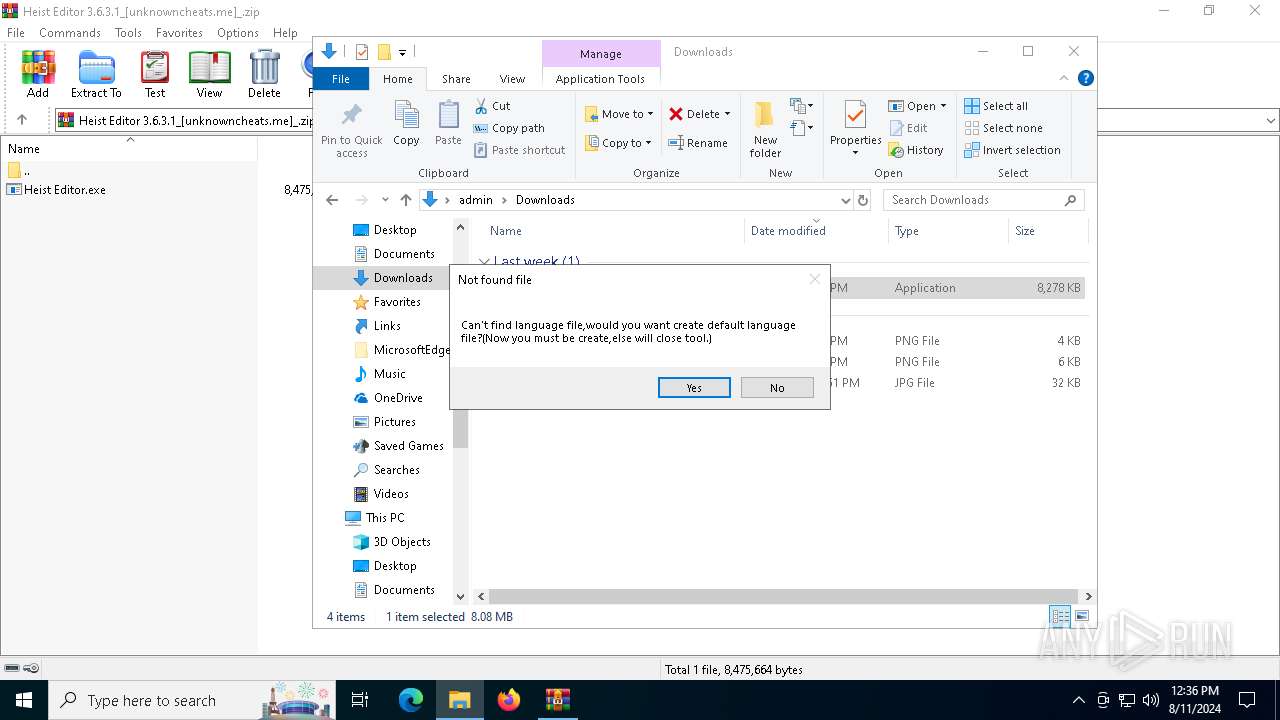
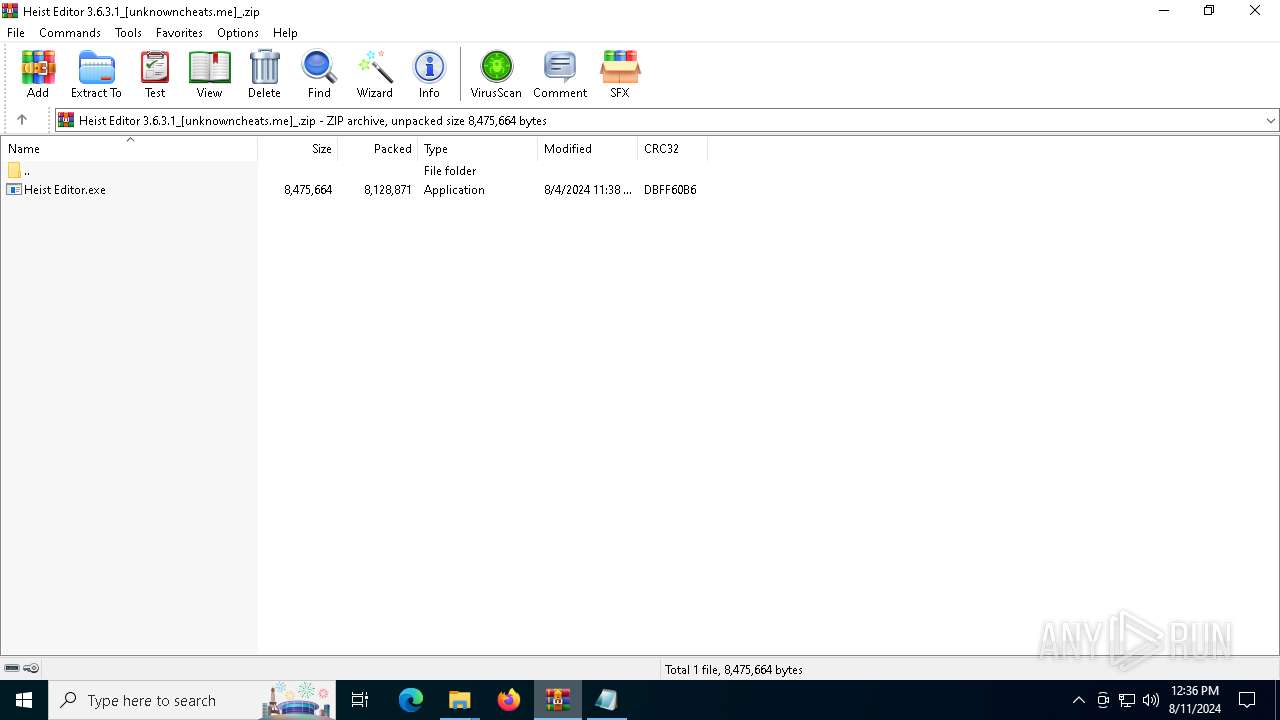
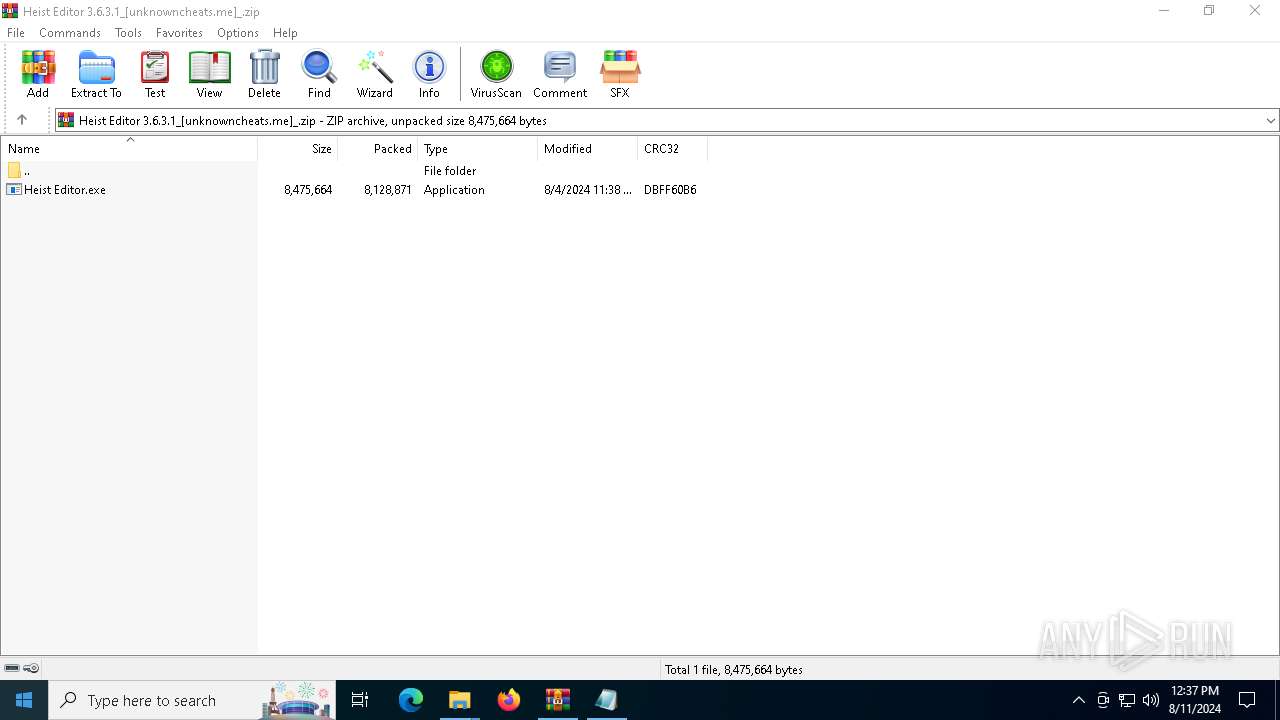
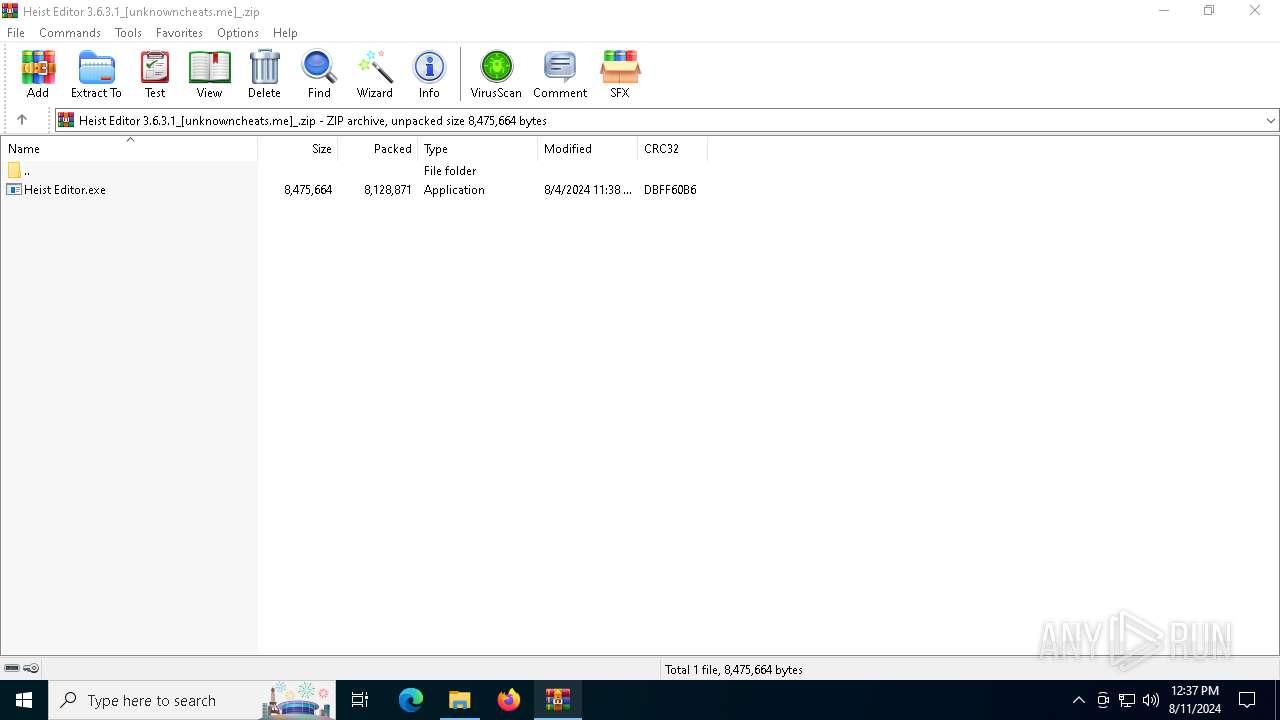
| File name: | Heist Editor 3.6.3.1_[unknowncheats.me]_.zip |
| Full analysis: | https://app.any.run/tasks/9582421f-ce2c-4dac-b2d9-e6babb1dc4ad |
| Verdict: | Malicious activity |
| Analysis date: | August 11, 2024, 12:35:46 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 0517600B2C90A946D034E374850117D3 |
| SHA1: | 0A7EEDA36865E058C3218331991E73089C763F49 |
| SHA256: | B56D1DF8F0E8516A37CF2FA45C14337A7AE737185349E943A5B4EDE3CC6ACC16 |
| SSDEEP: | 98304:TVOWyk4USfPDzcq0QFI5ycaCJdDsSPBffbJuh67SUpZ2wwwJ7umXEJm1sxticLkh:+r6jCTGwEnBmEZq+iVI |
MALICIOUS
No malicious indicators.SUSPICIOUS
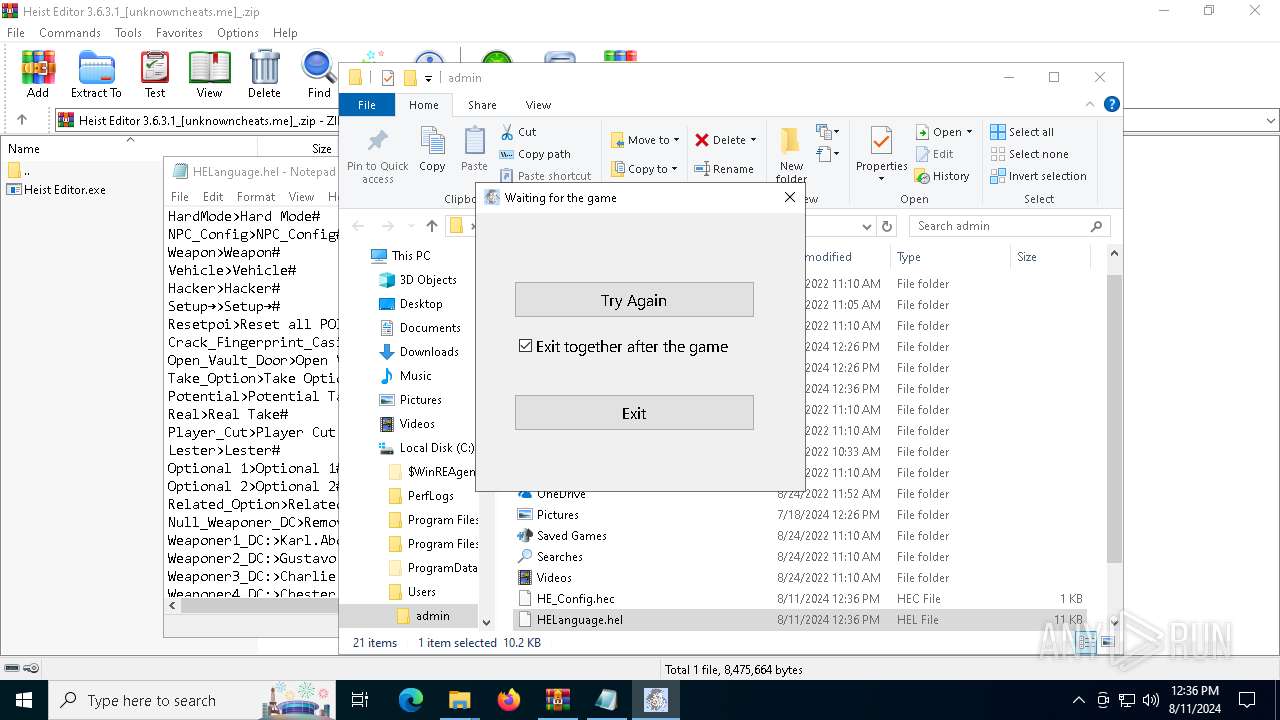
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6588)
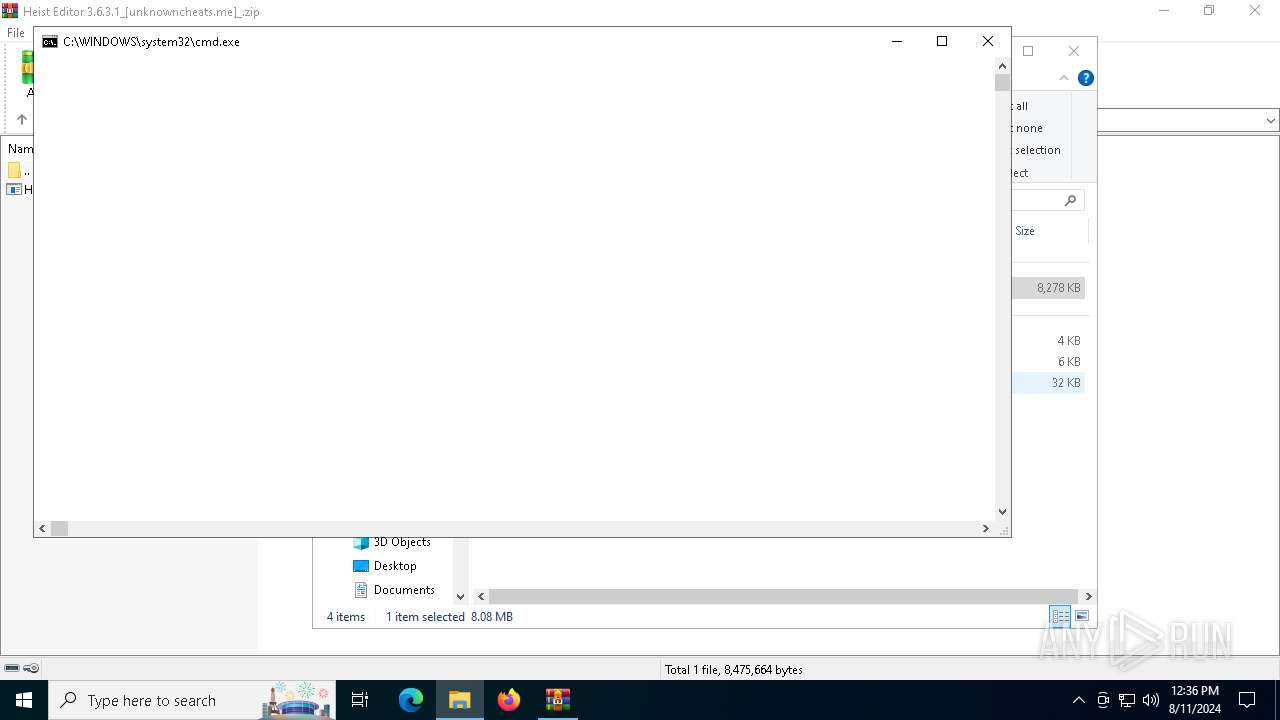
Starts CMD.EXE for commands execution
- Heist Editor.exe (PID: 6820)
Reads the BIOS version
- Heist Editor.exe (PID: 6820)
- Heist Editor.exe (PID: 6416)
Creates file in the systems drive root
- explorer.exe (PID: 5196)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6588)
Manual execution by a user
- Heist Editor.exe (PID: 6768)
- Heist Editor.exe (PID: 6820)
- mspaint.exe (PID: 3356)
- Heist Editor.exe (PID: 5472)
- Heist Editor.exe (PID: 6416)
Process checks whether UAC notifications are on
- Heist Editor.exe (PID: 6820)
- Heist Editor.exe (PID: 6416)
Checks supported languages
- Heist Editor.exe (PID: 6820)
- TextInputHost.exe (PID: 6796)
- Heist Editor.exe (PID: 6416)
Reads the computer name
- Heist Editor.exe (PID: 6820)
- TextInputHost.exe (PID: 6796)
- Heist Editor.exe (PID: 6416)
Reads security settings of Internet Explorer
- notepad.exe (PID: 3044)
- explorer.exe (PID: 5196)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:08:04 23:38:16 |
| ZipCRC: | 0xdbff60b6 |
| ZipCompressedSize: | 8128871 |
| ZipUncompressedSize: | 8475664 |
| ZipFileName: | Heist Editor.exe |
Total processes
148
Monitored processes
15
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1104 | explorer /select,C:\Users\admin\HELanguage.hel | C:\Windows\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3044 | notepad C:\Users\admin\HELanguage.hel | C:\Windows\System32\notepad.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3356 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Downloads\exchangeenergy.png" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3520 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5196 | C:\WINDOWS\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5472 | "C:\Users\admin\Downloads\Heist Editor.exe" | C:\Users\admin\Downloads\Heist Editor.exe | — | explorer.exe | |||||||||||
User: admin Company: Верный Integrity Level: MEDIUM Description: Heist Editor Exit code: 3221226540 Version: 3.6.3.1 Modules
| |||||||||||||||
| 6416 | "C:\Users\admin\Downloads\Heist Editor.exe" | C:\Users\admin\Downloads\Heist Editor.exe | explorer.exe | ||||||||||||
User: admin Company: Верный Integrity Level: HIGH Description: Heist Editor Exit code: 0 Version: 3.6.3.1 Modules
| |||||||||||||||
| 6428 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6444 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
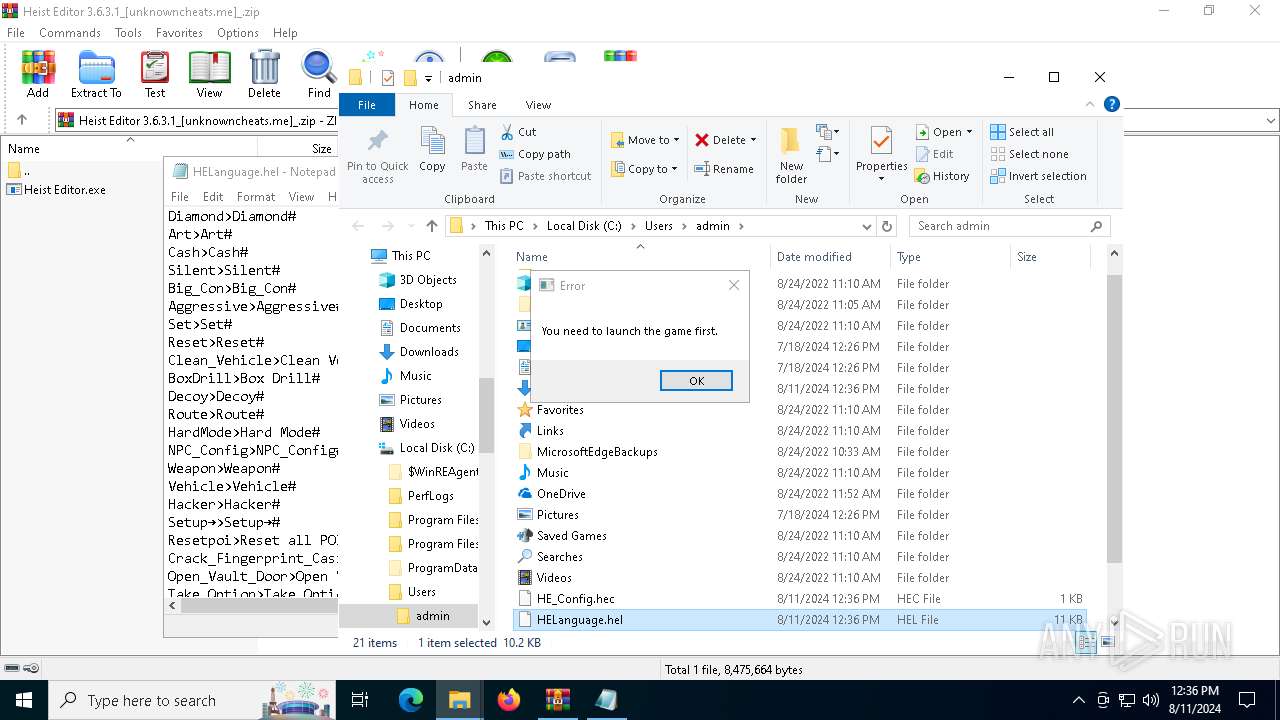
| 6484 | C:\WINDOWS\system32\cmd.exe /c start notepad C:\Users\admin\HELanguage.hel | C:\Windows\System32\cmd.exe | — | Heist Editor.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
19 837
Read events
19 737
Write events
98
Delete events
2
Modification events
| (PID) Process: | (6588) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6588) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6588) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6588) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Heist Editor 3.6.3.1_[unknowncheats.me]_.zip | |||
| (PID) Process: | (6588) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6588) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6588) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6588) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6588) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads | |||
| (PID) Process: | (5196) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
Executable files
1
Suspicious files
1
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6820 | Heist Editor.exe | C:\Users\admin\HE_Config.hec | abr | |
MD5:094ACB45FE35409F4F9FA34365CDA714 | SHA256:DEAE8F9D469A291E3D2E0FD8606153E6D29C3560A32786043E7FE0557955195E | |||
| 6588 | WinRAR.exe | C:\Users\admin\Downloads\Heist Editor.exe | executable | |
MD5:722C7B30ABD2600EF7B7AFF5FC6448D1 | SHA256:56D8C2773E25A737299BD511F795F5E3F9FD4A81A93DEB68D22C56285AA0121C | |||
| 6820 | Heist Editor.exe | C:\Users\admin\HEModel.hem | text | |
MD5:5D1A149F3203D84BD7A15C0F33398732 | SHA256:77FFF2B08F004F4CB4D695063E4F08D55271A5AD93273391E9A9E47C32B7E190 | |||
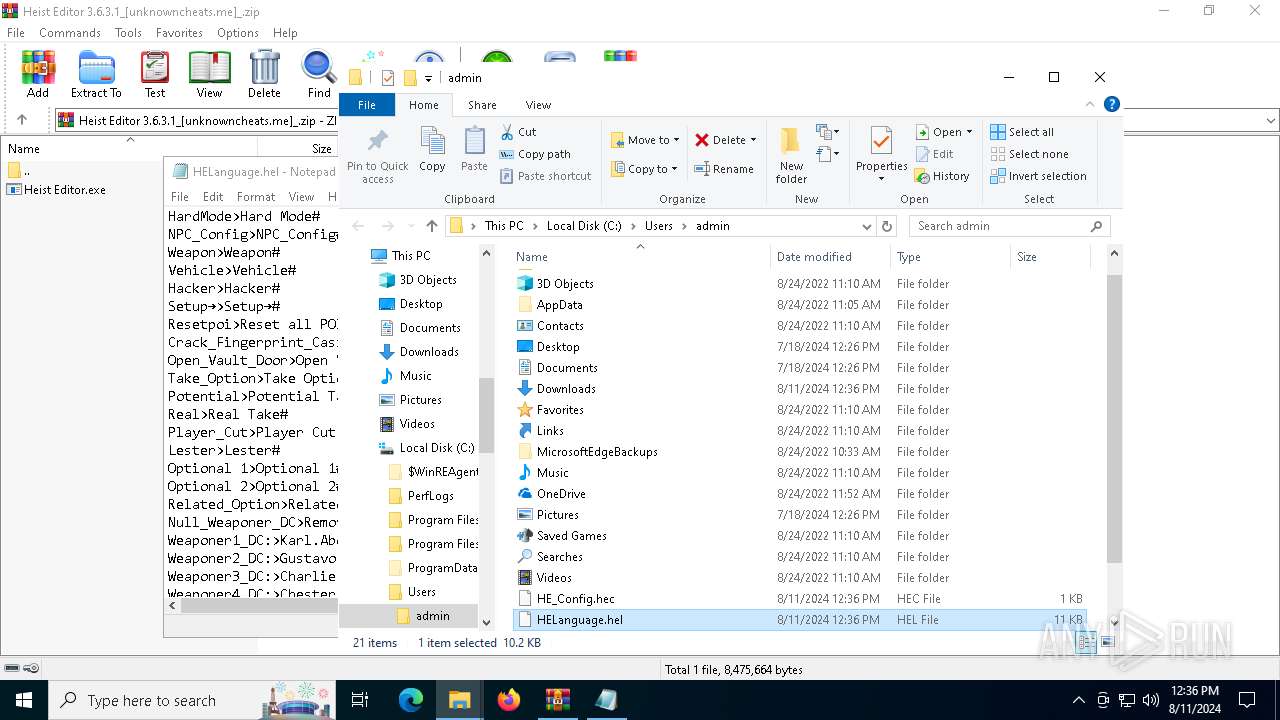
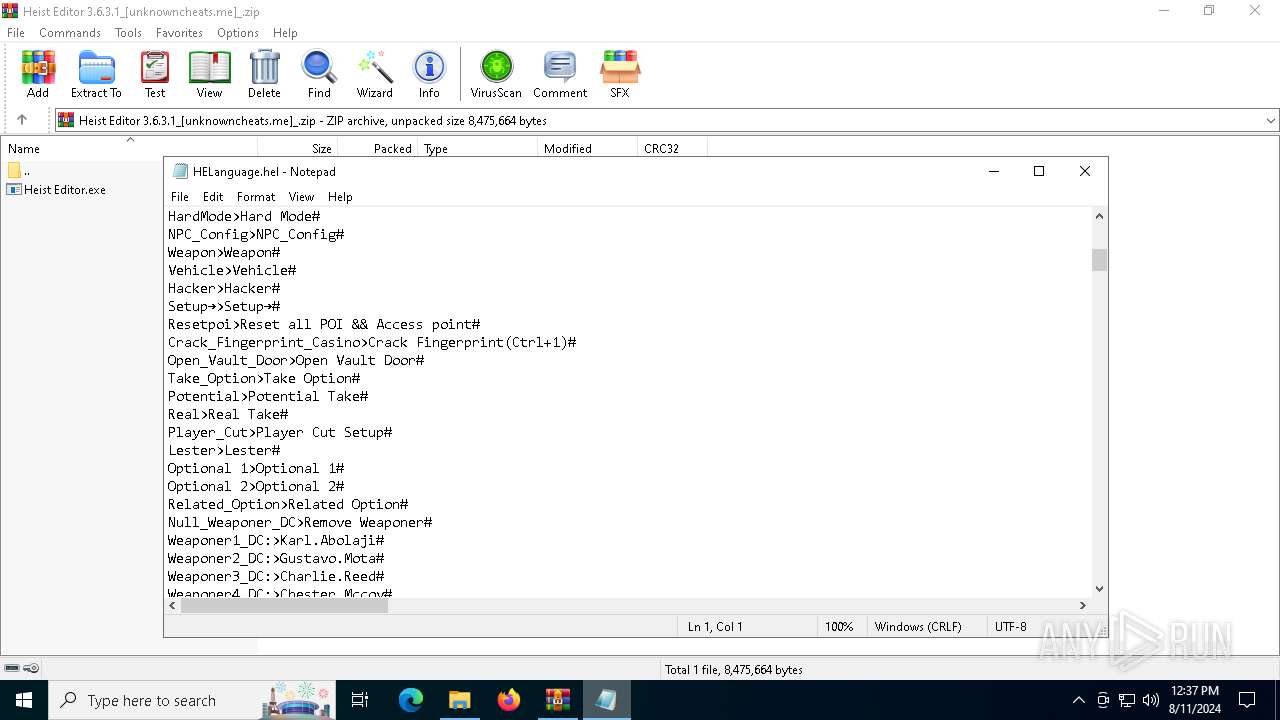
| 6820 | Heist Editor.exe | C:\Users\admin\HELanguage.hel | text | |
MD5:E48671F08C254445AAB192942DBF6059 | SHA256:7C642B8A501C94CD614F1178B2D11E3D39557AE5A26BD8E17E6C2A29F7790BCC | |||
| 6820 | Heist Editor.exe | C:\Users\admin\HEVehicle.hev | text | |
MD5:CF7F9AEE23075A7915CB46CC438C794B | SHA256:FBFA926CC6ACE7C9EBD9C4EC2003370E21AA2D580E624EAA262045CB034C85DE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
41
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6900 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6956 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
300 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
300 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4056 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
532 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4056 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5336 | SearchApp.exe | 204.79.197.200:443 | www.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |