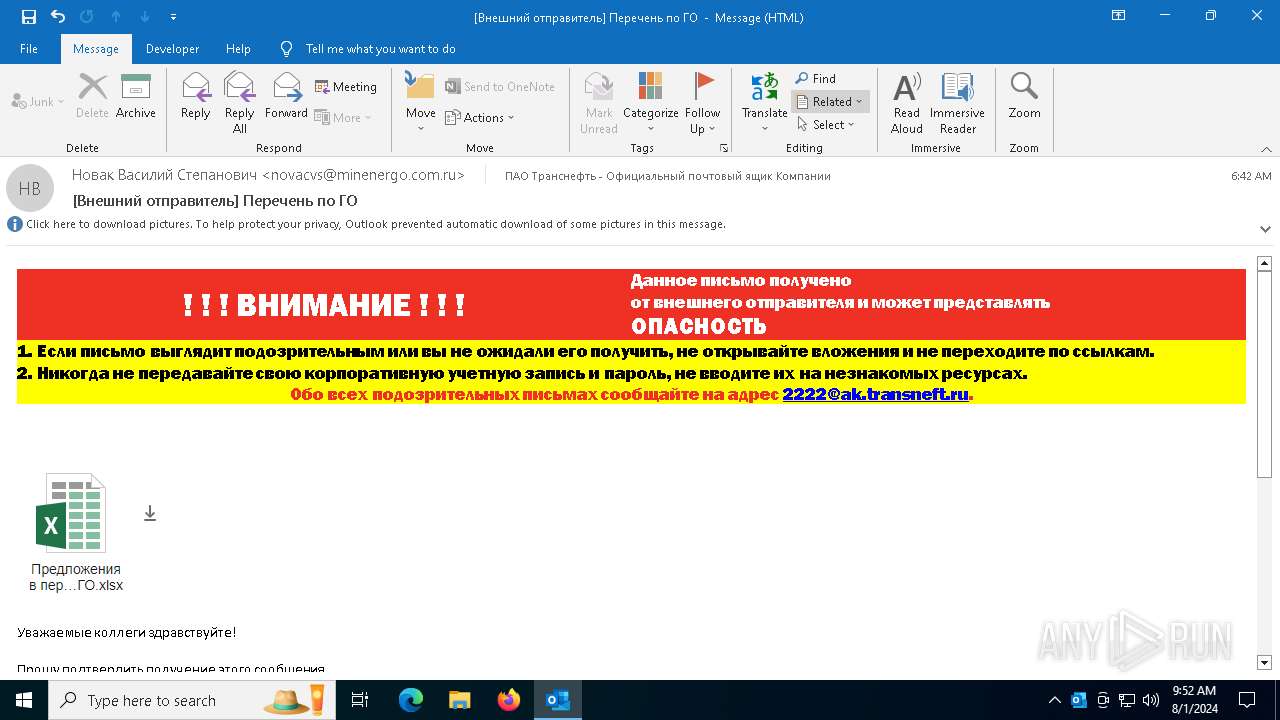
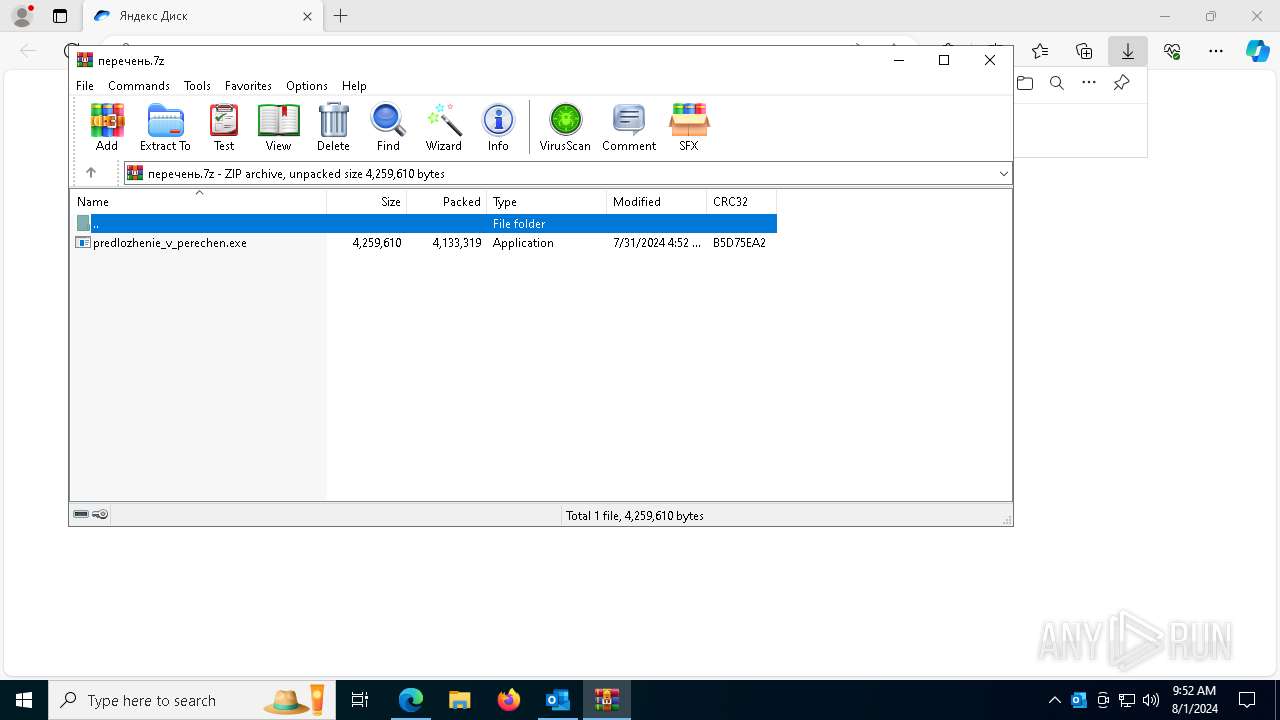
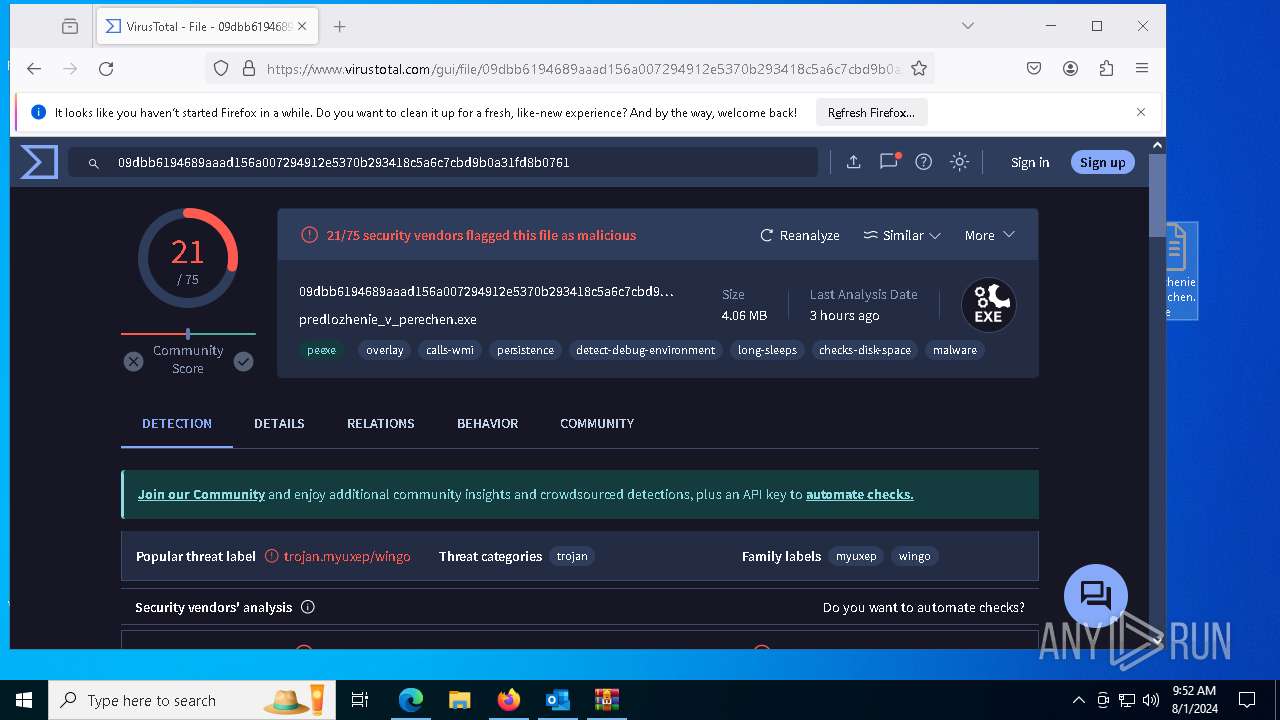
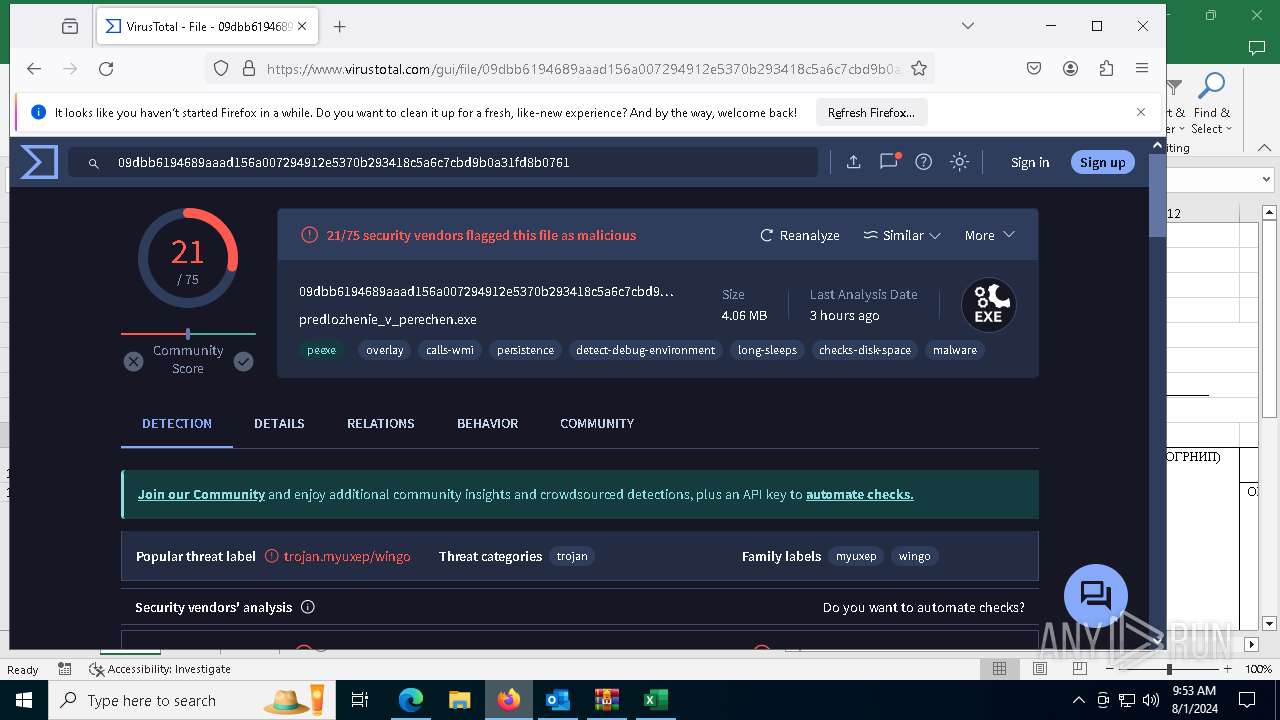
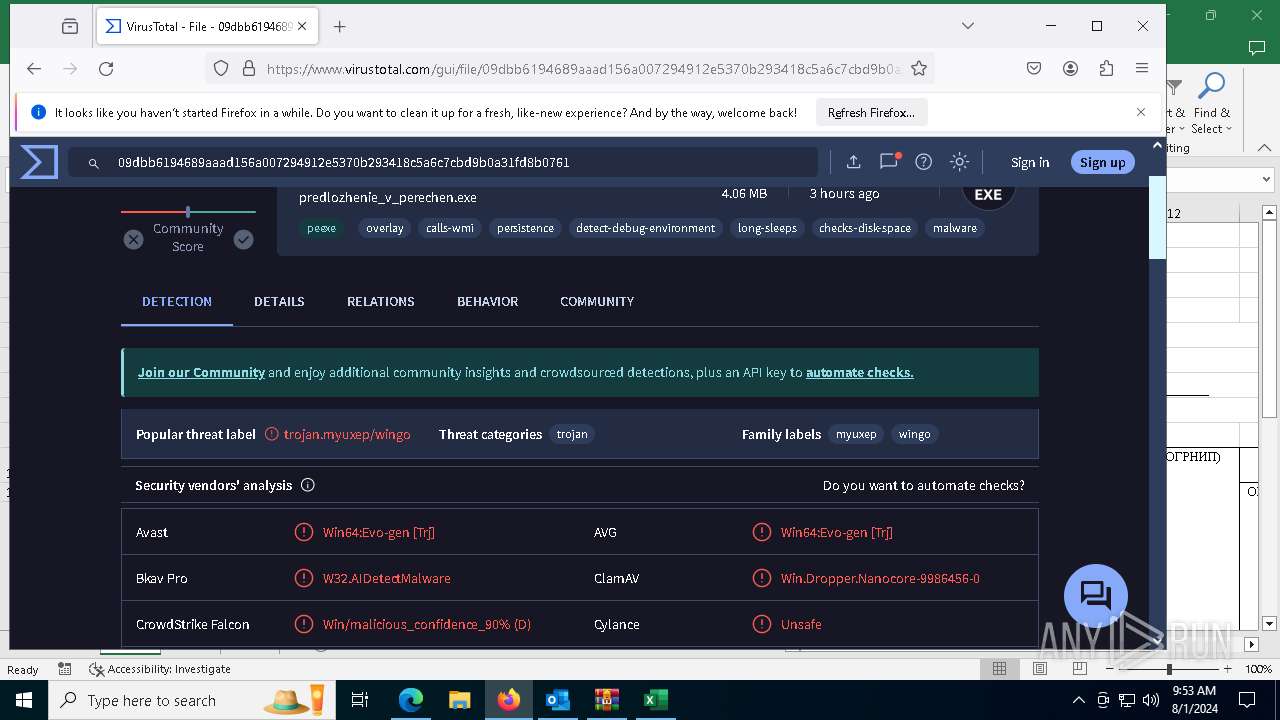
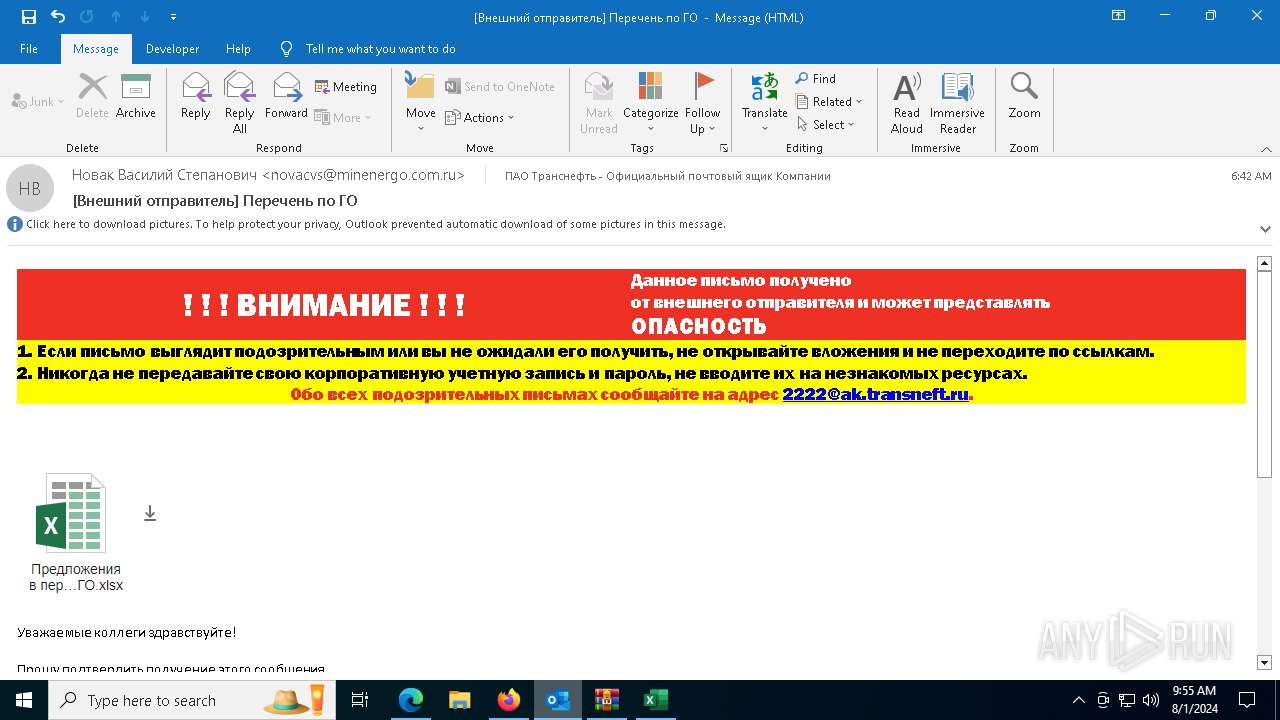
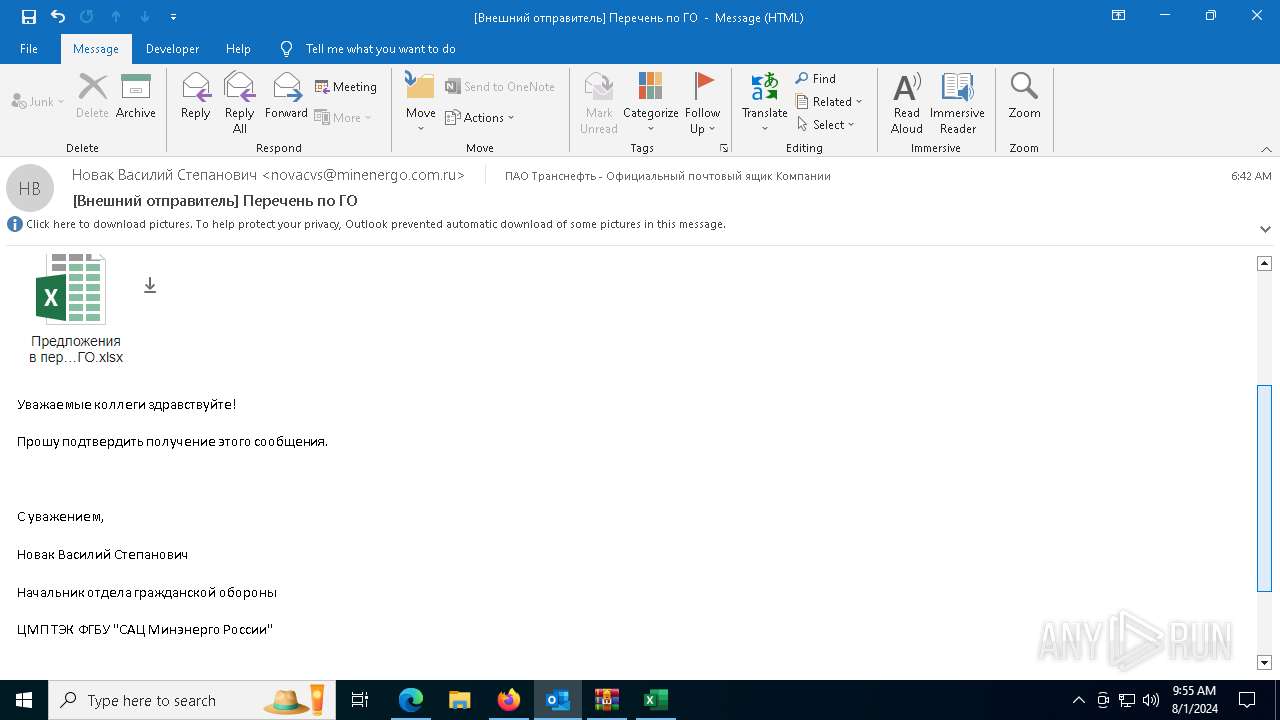
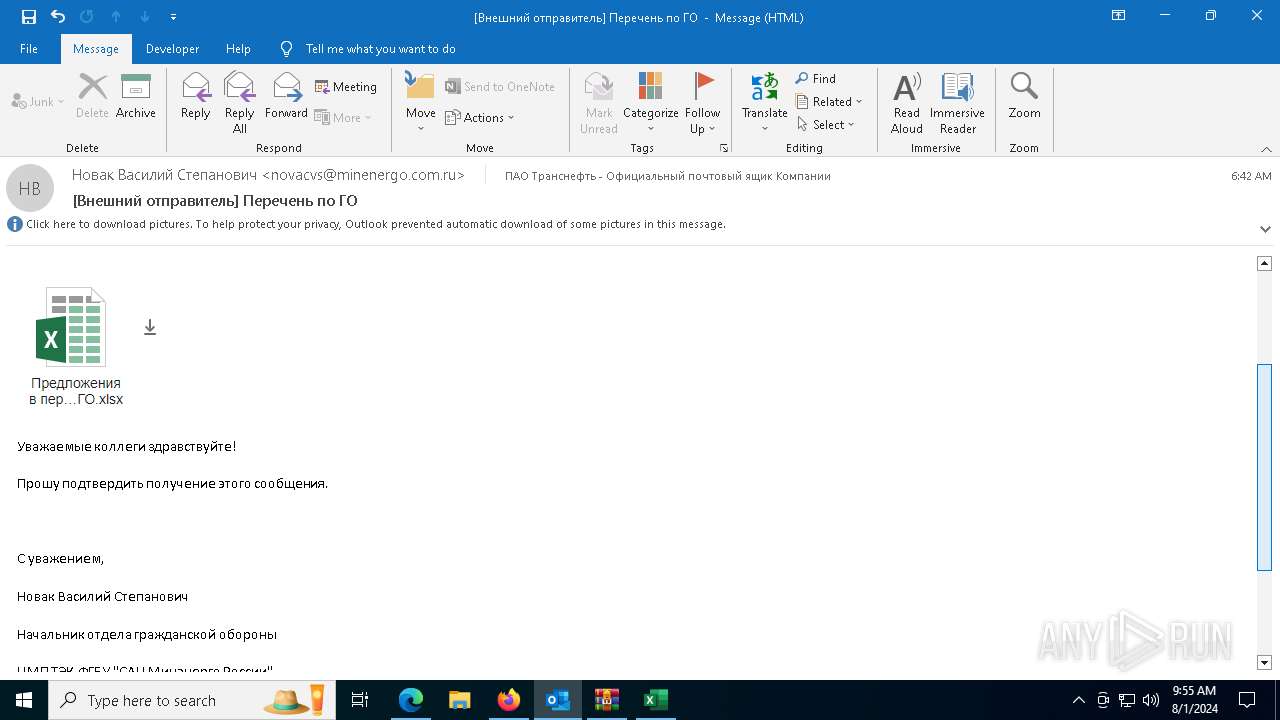
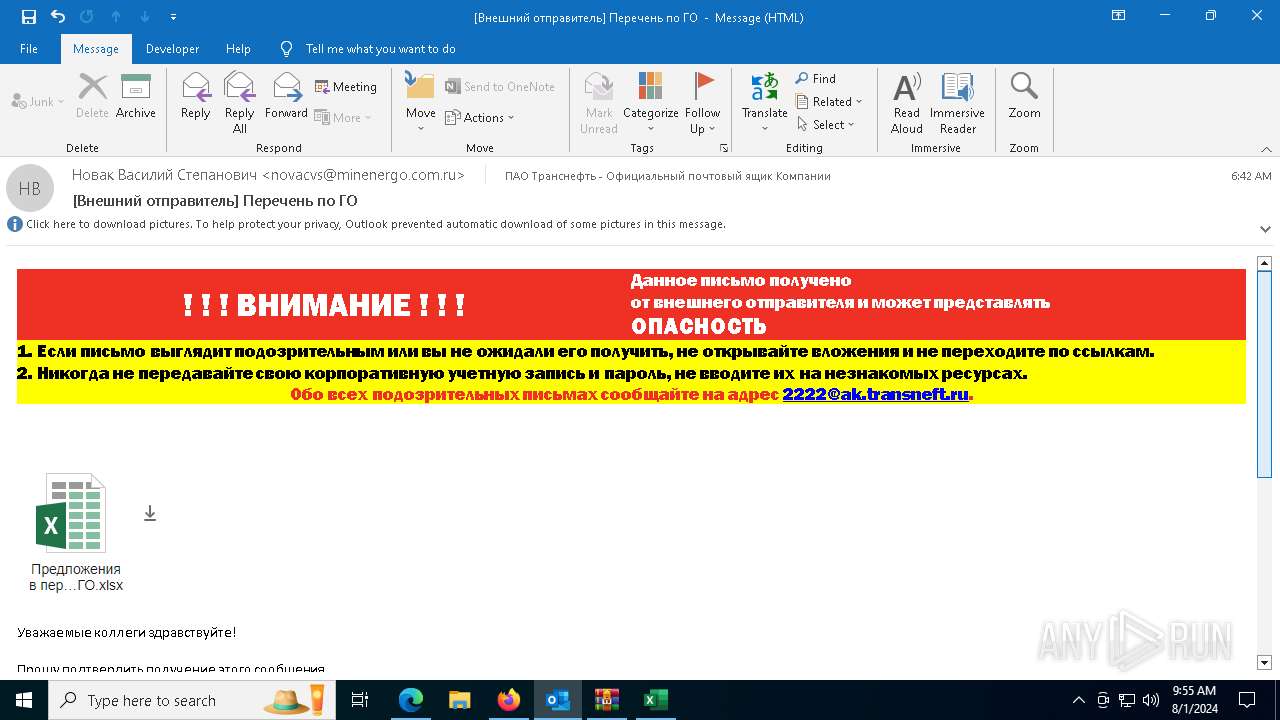
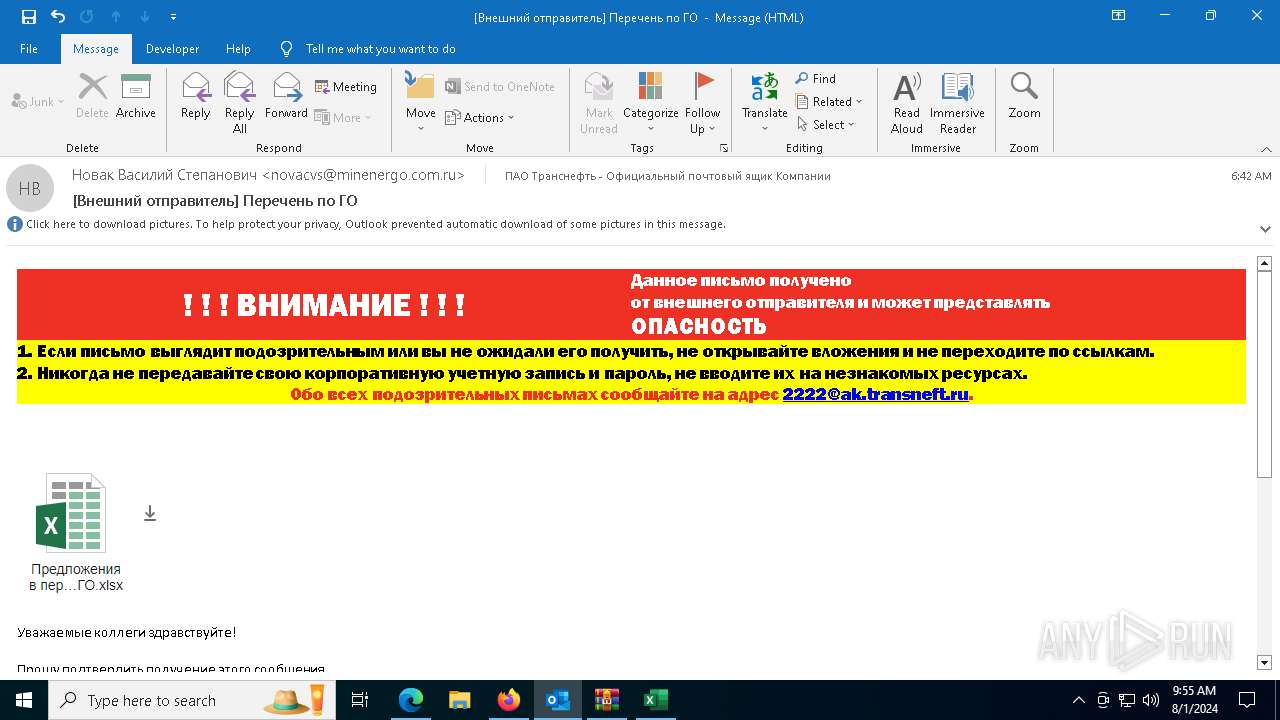
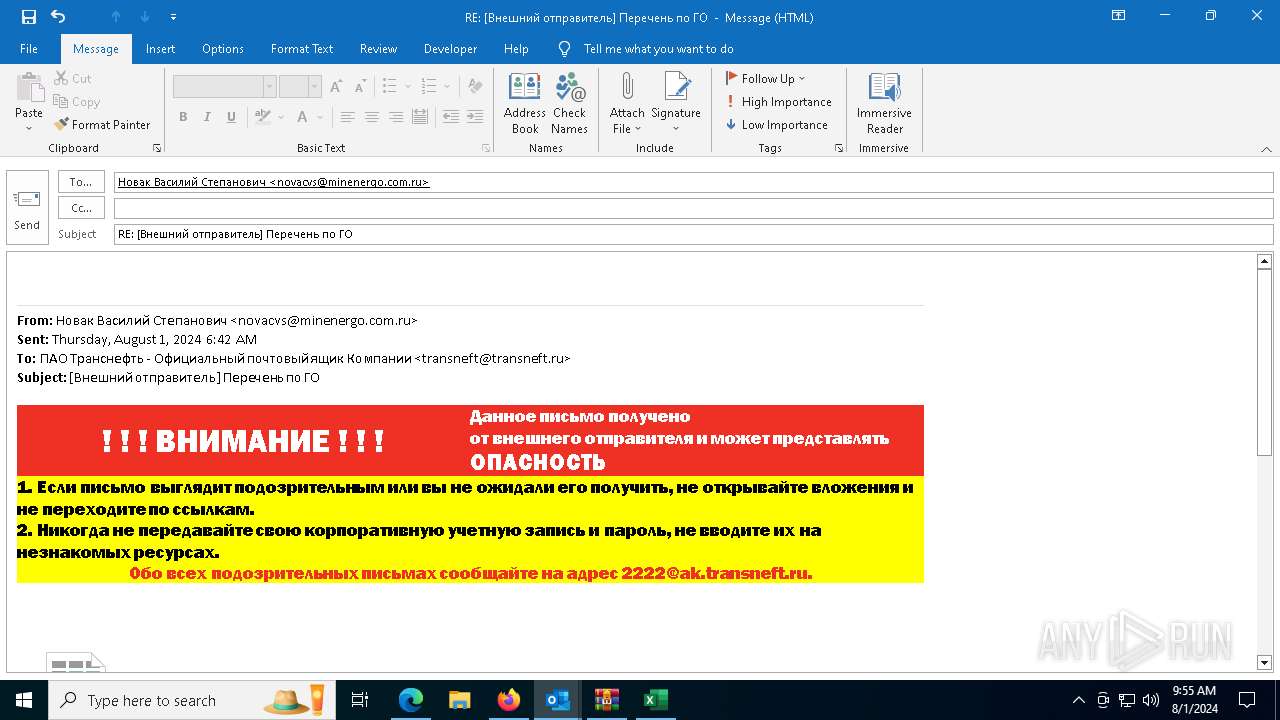
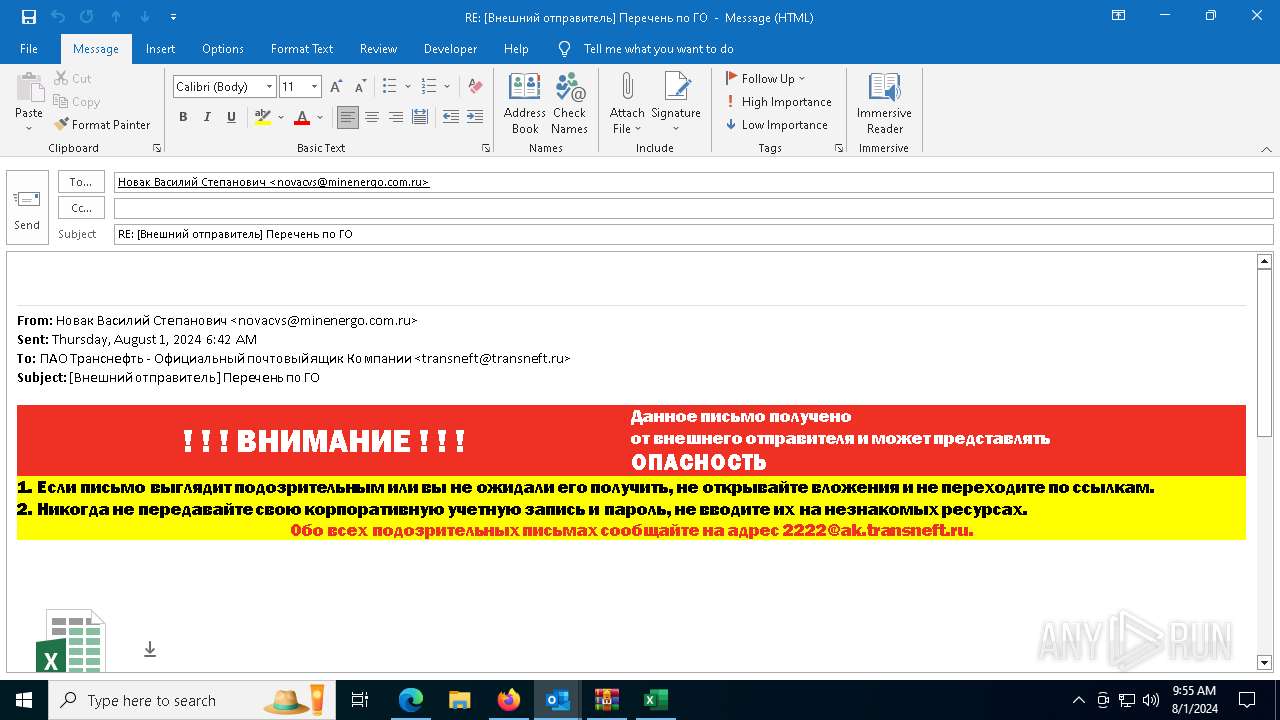
| File name: | Внешний отправитель Перечень по ГО.msg |
| Full analysis: | https://app.any.run/tasks/a88f6bbc-7626-4393-b718-6cb822287240 |
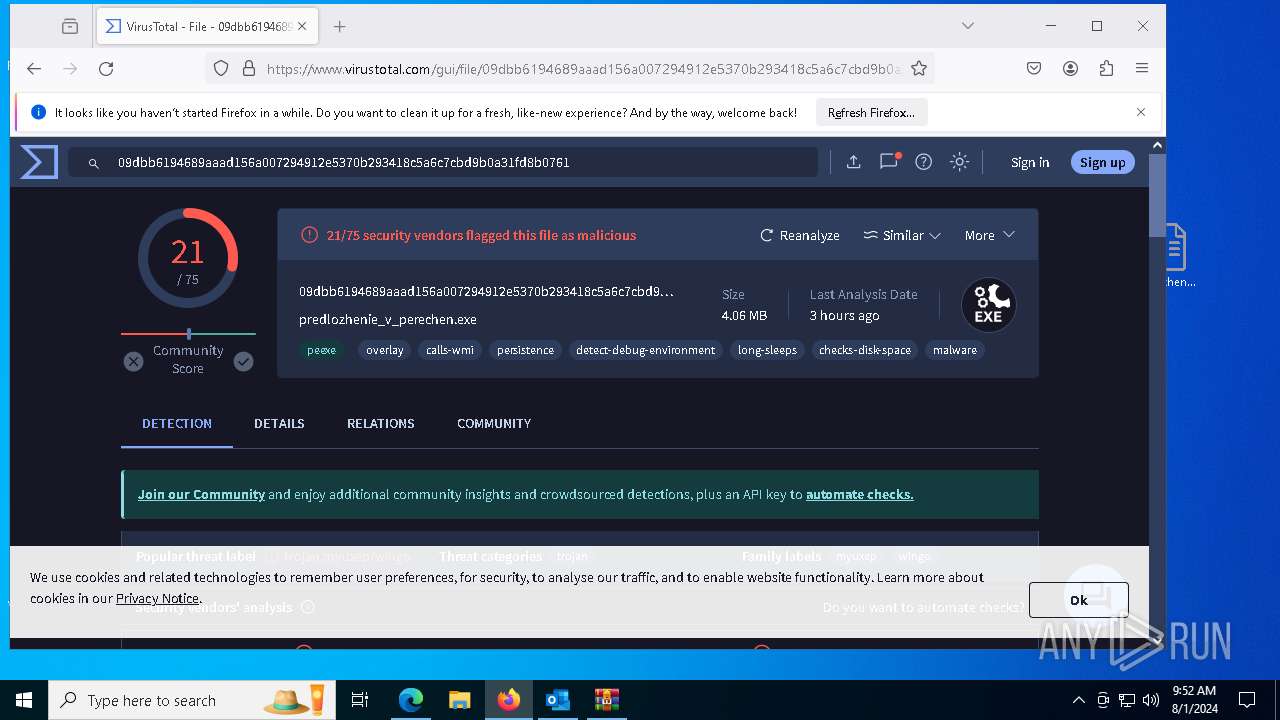
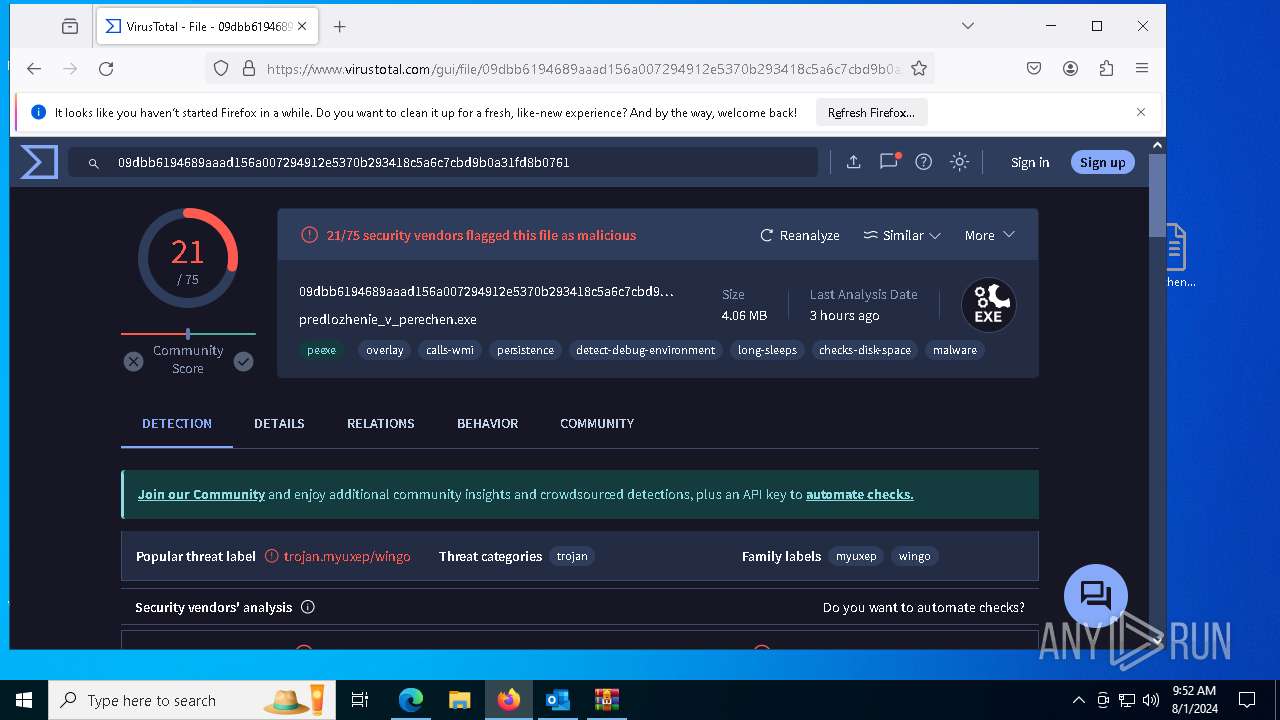
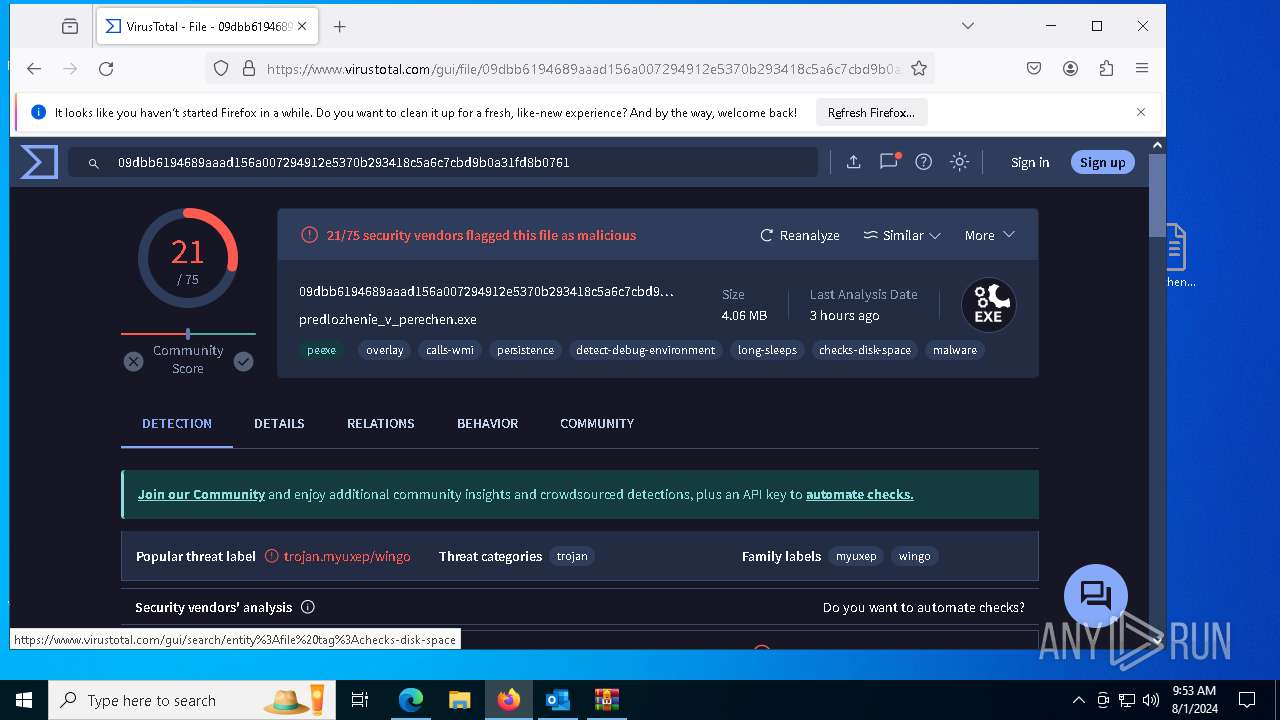
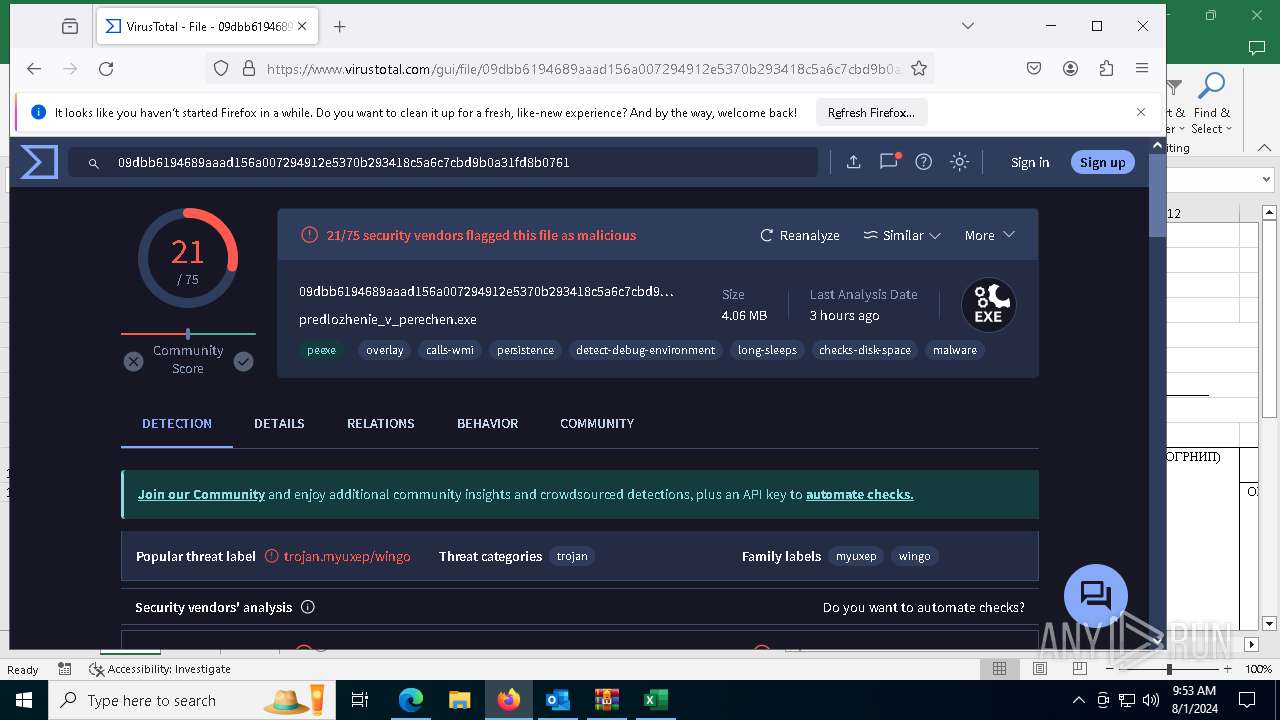
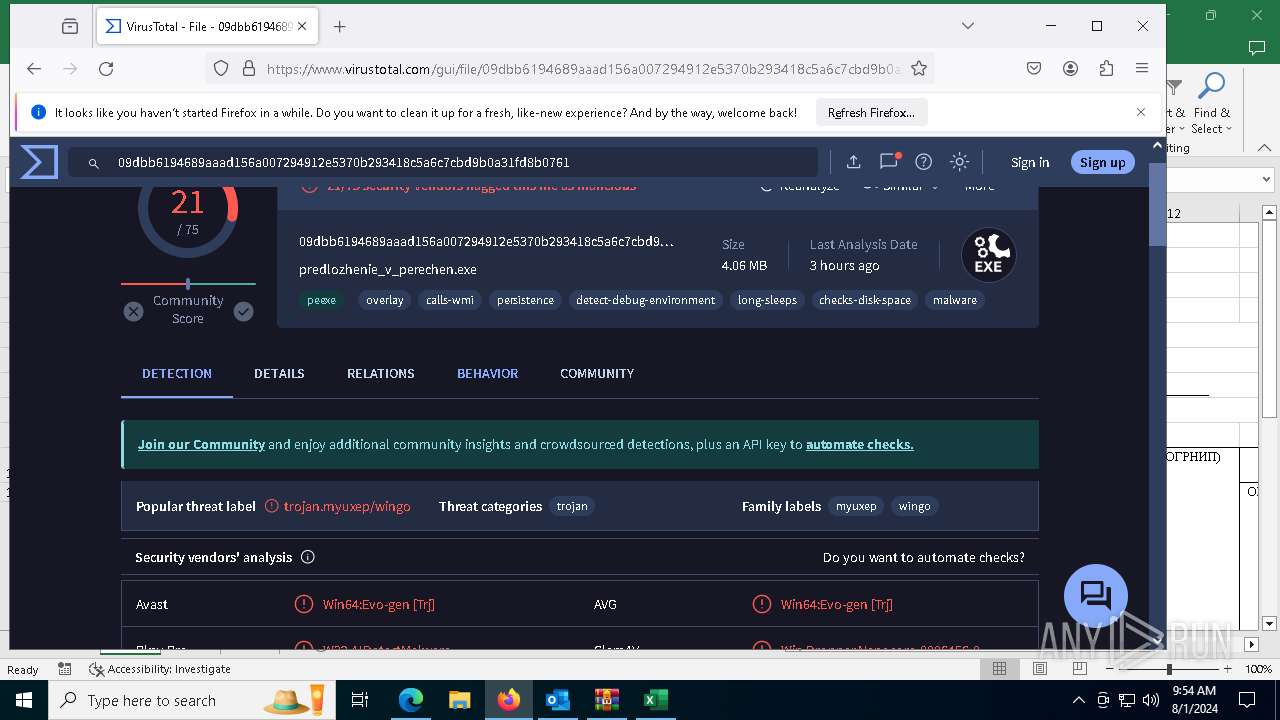
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | August 01, 2024, 09:51:51 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 0FC5F421BD56AE6CC1E704A2F7C52FEC |
| SHA1: | 43A1E1825BD7844A95C3187E6E08693275D64F18 |
| SHA256: | B5697E68CB1457421AB0076C48A0A840D798845857AA2F4BCA0378E251A1576D |
| SSDEEP: | 768:P44e/E9Tvu3QHcyqgvGKTsKBLkqUjyzG:Pf2AHcyqgvpL |
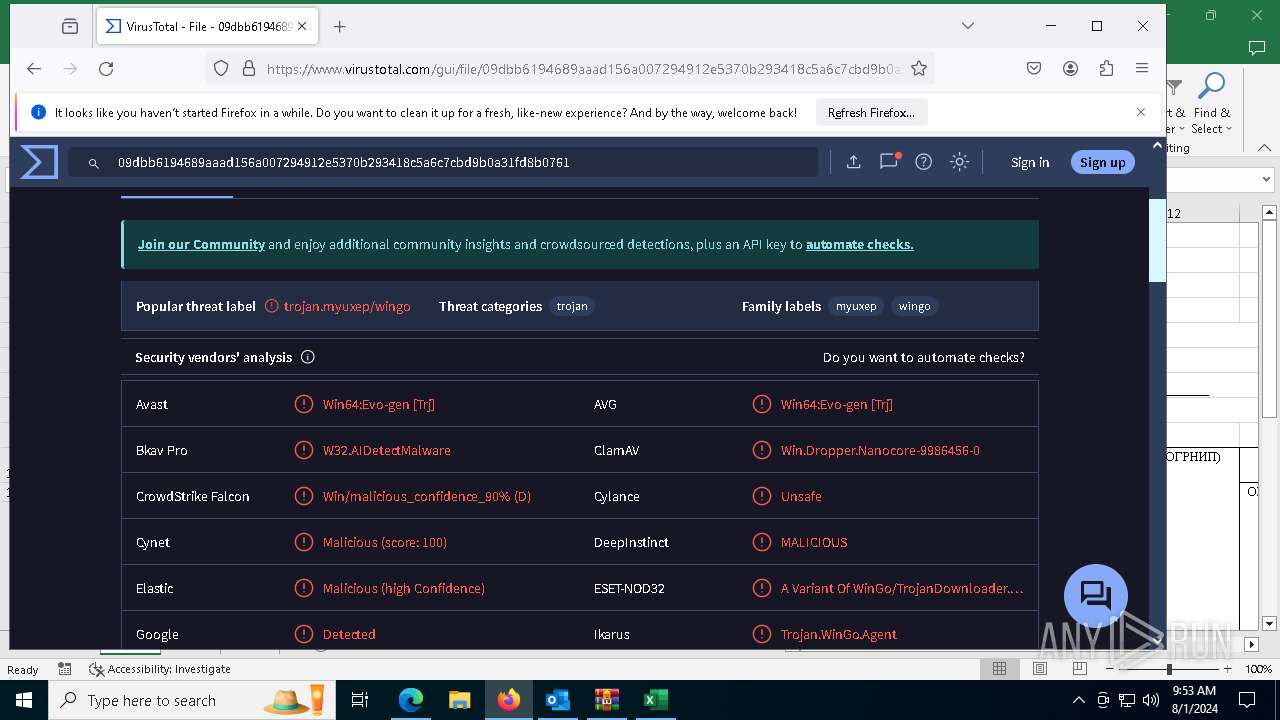
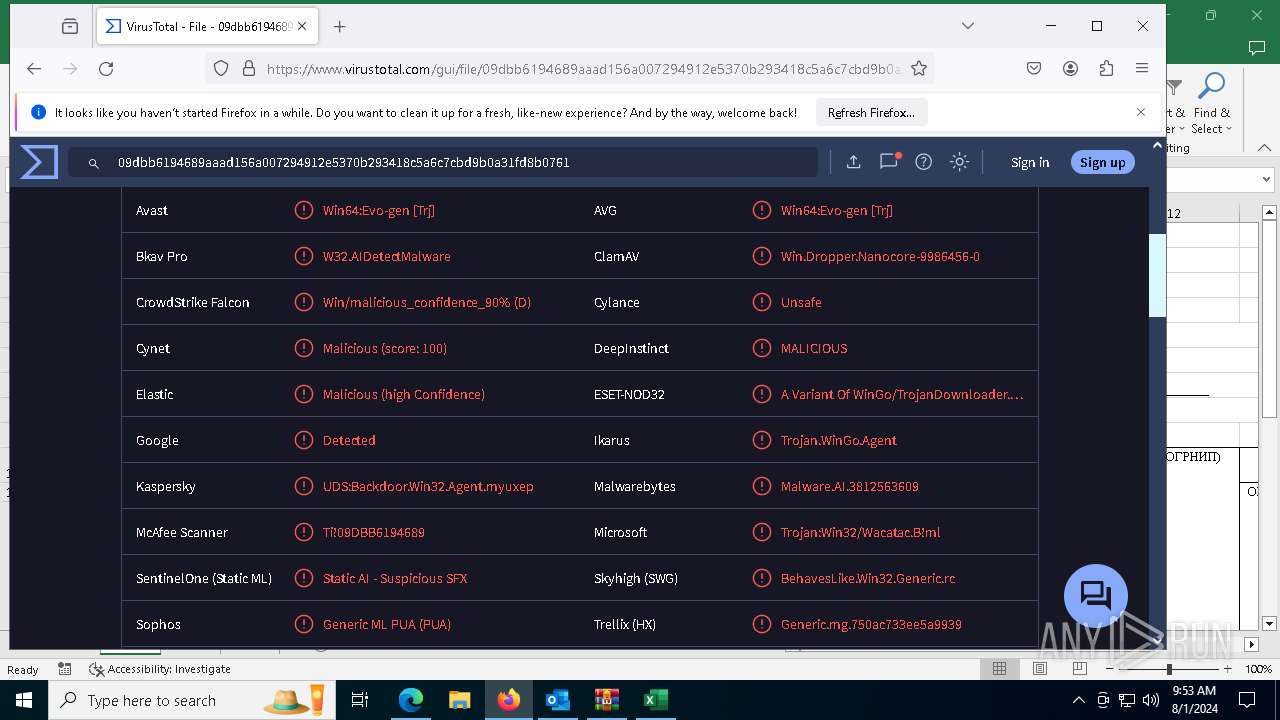
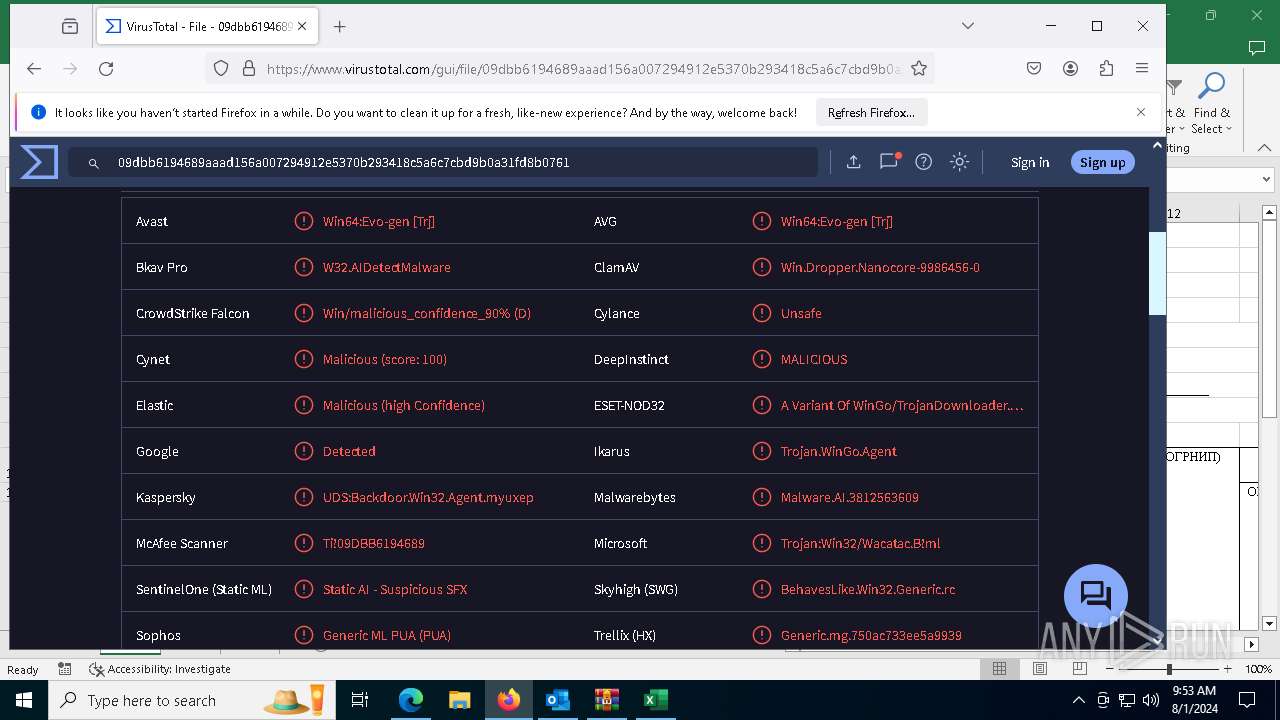
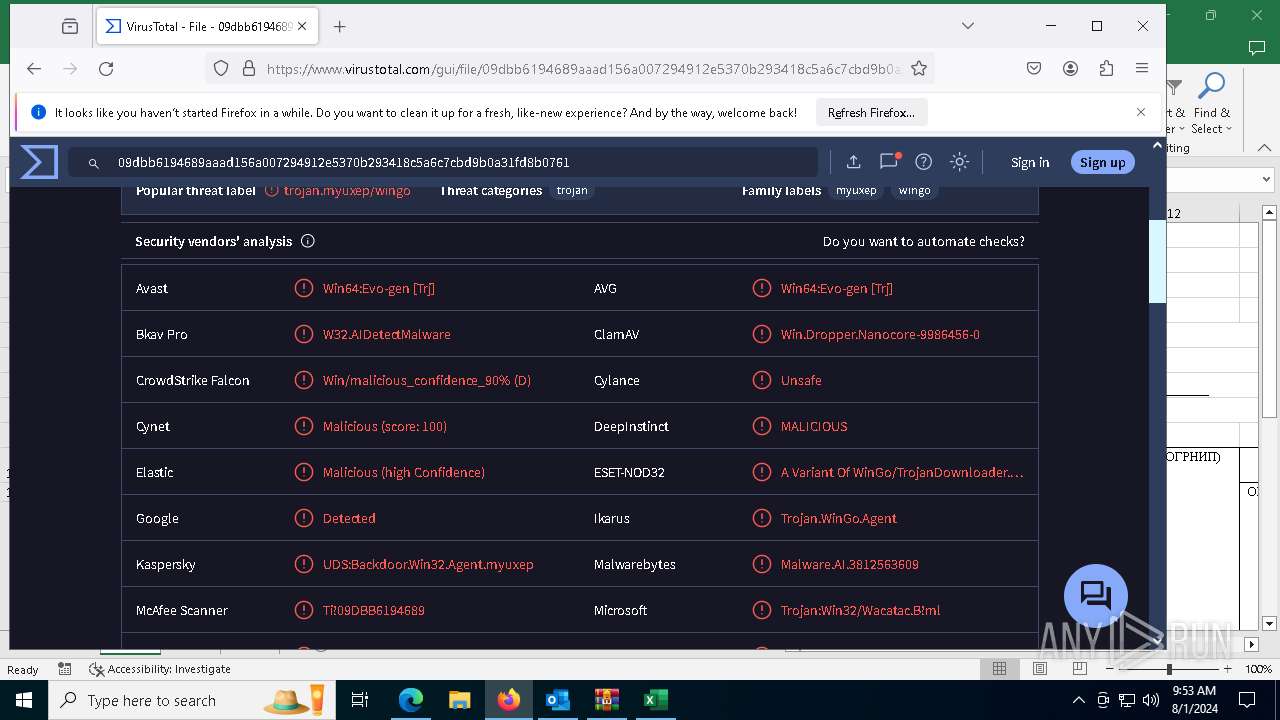
MALICIOUS
Drops the executable file immediately after the start
- predlozhenie_v_perechen.exe (PID: 7208)
- file.exe (PID: 2768)
- csc.exe (PID: 7000)
- System.exe (PID: 6580)
Adds path to the Windows Defender exclusion list
- nopuralte.exe (PID: 1076)
DcRAT is detected
- file.exe (PID: 2768)
- System.exe (PID: 6580)
Changes the autorun value in the registry
- file.exe (PID: 2768)
Changes the login/logoff helper path in the registry
- file.exe (PID: 2768)
Connects to the CnC server
- System.exe (PID: 6580)
DARKCRYSTAL has been detected (SURICATA)
- System.exe (PID: 6580)
DCRAT has been detected (YARA)
- System.exe (PID: 6580)
Steals credentials from Web Browsers
- System.exe (PID: 6580)
Actions looks like stealing of personal data
- System.exe (PID: 6580)
SUSPICIOUS
Executable content was dropped or overwritten
- predlozhenie_v_perechen.exe (PID: 7208)
- file.exe (PID: 2768)
- csc.exe (PID: 7000)
- System.exe (PID: 6580)
Reads security settings of Internet Explorer
- predlozhenie_v_perechen.exe (PID: 7208)
- nopuralte.exe (PID: 8688)
- file.exe (PID: 2768)
- msedge.exe (PID: 8076)
Reads the date of Windows installation
- predlozhenie_v_perechen.exe (PID: 7208)
- nopuralte.exe (PID: 8688)
- file.exe (PID: 2768)
- msedge.exe (PID: 8076)
Starts POWERSHELL.EXE for commands execution
- nopuralte.exe (PID: 1076)
Application launched itself
- nopuralte.exe (PID: 8688)
Script adds exclusion path to Windows Defender
- nopuralte.exe (PID: 1076)
Detected use of alternative data streams (AltDS)
- powershell.exe (PID: 8364)
Adds/modifies Windows certificates
- nopuralte.exe (PID: 1076)
The process creates files with name similar to system file names
- file.exe (PID: 2768)
Executed via WMI
- schtasks.exe (PID: 7264)
- schtasks.exe (PID: 8696)
- schtasks.exe (PID: 2424)
- schtasks.exe (PID: 8000)
- schtasks.exe (PID: 8800)
- schtasks.exe (PID: 8732)
- schtasks.exe (PID: 7128)
- schtasks.exe (PID: 6564)
- schtasks.exe (PID: 8100)
- schtasks.exe (PID: 2876)
- schtasks.exe (PID: 7764)
- schtasks.exe (PID: 3672)
- schtasks.exe (PID: 3548)
- schtasks.exe (PID: 6684)
- schtasks.exe (PID: 6512)
- schtasks.exe (PID: 5492)
- schtasks.exe (PID: 4024)
- schtasks.exe (PID: 7392)
Process drops legitimate windows executable
- file.exe (PID: 2768)
Starts CMD.EXE for commands execution
- file.exe (PID: 2768)
Starts application with an unusual extension
- cmd.exe (PID: 8796)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 8796)
Executing commands from a ".bat" file
- file.exe (PID: 2768)
Loads DLL from Mozilla Firefox
- System.exe (PID: 6580)
Sets XML DOM element text (SCRIPT)
- splwow64.exe (PID: 8608)
INFO
Reads Microsoft Office registry keys
- msedge.exe (PID: 7252)
- firefox.exe (PID: 8008)
- predlozhenie_v_perechen.exe (PID: 7208)
The process uses the downloaded file
- msedge.exe (PID: 8184)
- msedge.exe (PID: 7252)
- WinRAR.exe (PID: 6400)
Checks supported languages
- TextInputHost.exe (PID: 2992)
- identity_helper.exe (PID: 7980)
- predlozhenie_v_perechen.exe (PID: 7208)
- nopuralte.exe (PID: 8688)
- nopuralte.exe (PID: 1076)
- file.exe (PID: 2768)
- csc.exe (PID: 7212)
- cvtres.exe (PID: 1044)
- csc.exe (PID: 7000)
- cvtres.exe (PID: 8108)
- csc.exe (PID: 6792)
- csc.exe (PID: 4024)
- cvtres.exe (PID: 8528)
- cvtres.exe (PID: 6516)
- chcp.com (PID: 7892)
- System.exe (PID: 6580)
- msedge.exe (PID: 8076)
- msedge.exe.exe (PID: 8144)
Reads the computer name
- identity_helper.exe (PID: 7980)
- TextInputHost.exe (PID: 2992)
- predlozhenie_v_perechen.exe (PID: 7208)
- nopuralte.exe (PID: 8688)
- nopuralte.exe (PID: 1076)
- file.exe (PID: 2768)
- System.exe (PID: 6580)
- msedge.exe (PID: 8076)
- msedge.exe.exe (PID: 8144)
Reads Environment values
- identity_helper.exe (PID: 7980)
- file.exe (PID: 2768)
- System.exe (PID: 6580)
- msedge.exe.exe (PID: 8144)
Drops the executable file immediately after the start
- msedge.exe (PID: 7252)
- WinRAR.exe (PID: 6400)
- firefox.exe (PID: 8008)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6400)
- firefox.exe (PID: 8008)
Manual execution by a user
- firefox.exe (PID: 7680)
- predlozhenie_v_perechen.exe (PID: 7208)
Application launched itself
- firefox.exe (PID: 7680)
- msedge.exe (PID: 7252)
- firefox.exe (PID: 8008)
Process checks computer location settings
- predlozhenie_v_perechen.exe (PID: 7208)
- nopuralte.exe (PID: 8688)
- file.exe (PID: 2768)
- msedge.exe (PID: 8076)
Create files in a temporary directory
- predlozhenie_v_perechen.exe (PID: 7208)
- file.exe (PID: 2768)
- cvtres.exe (PID: 1044)
- cvtres.exe (PID: 8108)
- cvtres.exe (PID: 6516)
- cvtres.exe (PID: 8528)
- System.exe (PID: 6580)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 8364)
- powershell.exe (PID: 6784)
Reads the software policy settings
- nopuralte.exe (PID: 1076)
Reads the machine GUID from the registry
- nopuralte.exe (PID: 1076)
- file.exe (PID: 2768)
- csc.exe (PID: 7212)
- csc.exe (PID: 7000)
- csc.exe (PID: 6792)
- csc.exe (PID: 4024)
- System.exe (PID: 6580)
Creates files in the program directory
- file.exe (PID: 2768)
- csc.exe (PID: 7000)
- csc.exe (PID: 6792)
- csc.exe (PID: 4024)
Creates files or folders in the user directory
- csc.exe (PID: 7212)
Checks proxy server information
- System.exe (PID: 6580)
Disables trace logs
- System.exe (PID: 6580)
Found Base64 encoded reference to WMI classes (YARA)
- System.exe (PID: 6580)
.NET Reactor protector has been detected
- System.exe (PID: 6580)
Reads security settings of Internet Explorer
- splwow64.exe (PID: 8608)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
DcRat
(PID) Process(6580) System.exe
C2 (1)http://strepsils.top/VideoVm_requestMultiTestLocal.php
Options
PluginConfigs
0{SYSTEMDRIVE}/Users/
1false
2false
3true
4true
5true
6true
7false
8true
9true
10true
11true
12true
13true
14true
Version5.0.1
C2 (1)http://strepsils.top/VideoVm_requestMultiTestLocal.php
Options
PluginConfigs
0{SYSTEMDRIVE}/Users/
1false
2false
3true
4true
5true
6true
7false
8true
9true
10true
11true
12true
13true
14true
Version5.0.1
PluginsTVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAAKX/2QAAAAAAAAAAOAAIiALAQgAAEYBAAAGAAAAAAAA7mUBAAAgAAAAgAEAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAADAAQAAAgAAm0ACAAMAQIUA...
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
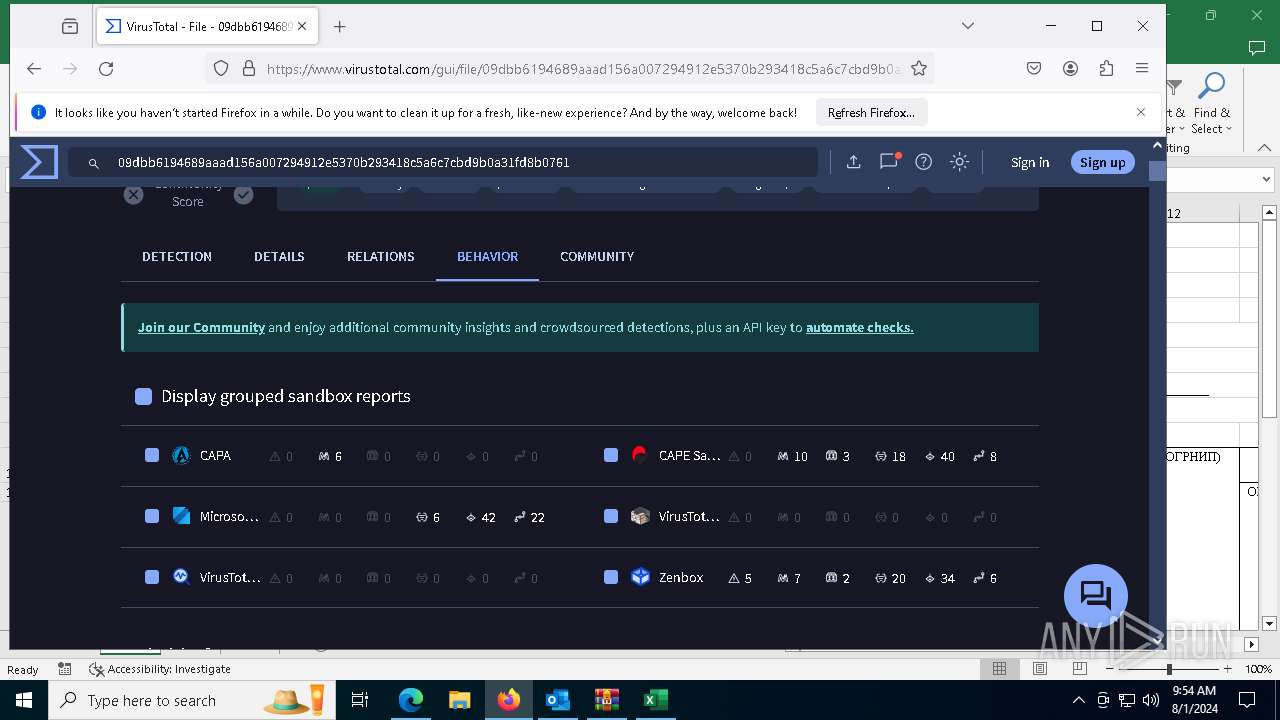
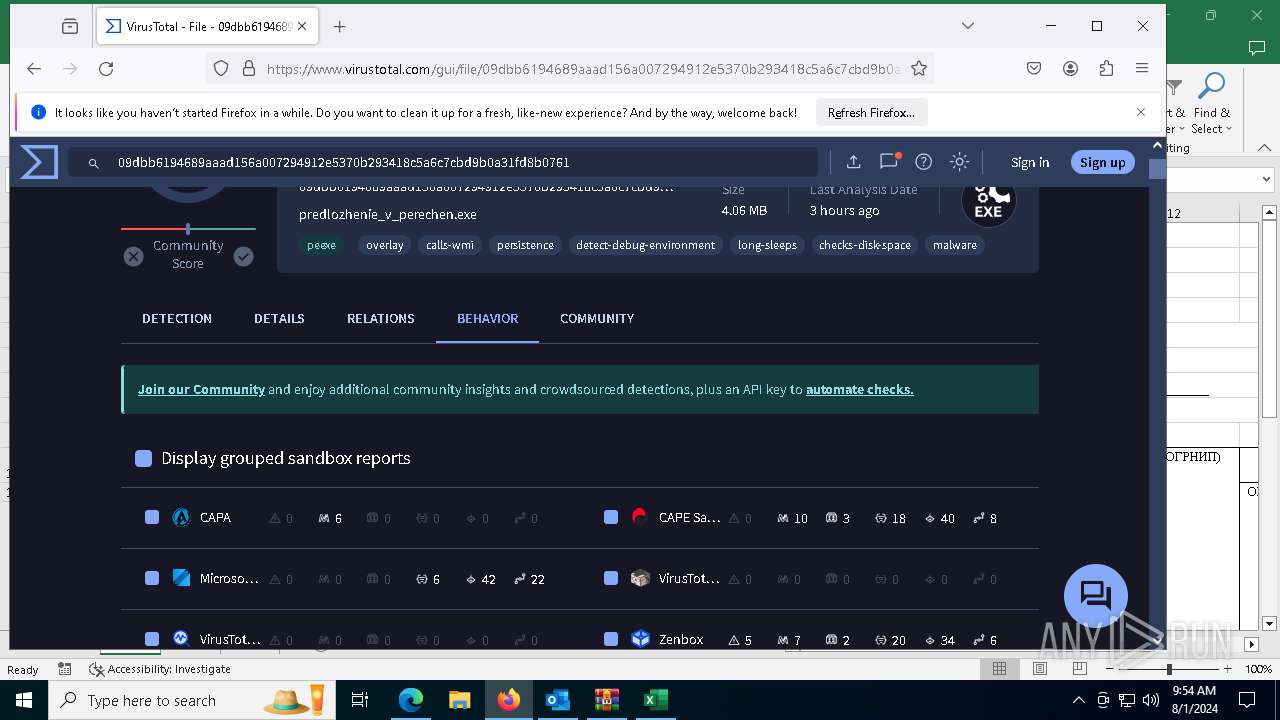
Total processes
238
Monitored processes
99
Malicious processes
9
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 252 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2296 -parentBuildID 20240213221259 -prefsHandle 2288 -prefMapHandle 2284 -prefsLen 30537 -prefMapSize 244343 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {ac93de45-b1f4-4f7e-955a-21ddf102ab2d} 8008 "\\.\pipe\gecko-crash-server-pipe.8008" 2456f180f10 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1044 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES7BDE.tmp" "c:\Users\admin\AppData\Local\Microsoft\OneDrive\CSCEF657F7B9A9F478A858B89922760FDC3.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
| 1076 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5992 --field-trial-handle=2388,i,17509114796308366242,7063480979053263767,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1076 | "C:\Users\admin\AppData\Local\Temp\nopuralte.exe" | C:\Users\admin\AppData\Local\Temp\nopuralte.exe | nopuralte.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1812 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "F8BD40B7-1542-4A0F-9305-D9117CC5F650" "22BDB8FF-88EF-41FA-BE3D-72FC844E0C7C" "6848" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2396 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1832 -parentBuildID 20240213221259 -prefsHandle 1864 -prefMapHandle 1856 -prefsLen 30537 -prefMapSize 244343 -appDir "C:\Program Files\Mozilla Firefox\browser" - {405b5b00-d0de-41bf-96c5-76ca77babf4a} 8008 "\\.\pipe\gecko-crash-server-pipe.8008" 2457bae5710 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2424 | schtasks.exe /create /tn "System" /sc ONLOGON /tr "'C:\found.000\dir_00000002.chk\System.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2768 | C:\Users\admin\Desktop\file.exe | C:\Users\admin\Desktop\file.exe | nopuralte.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.2.7.1277 Modules
| |||||||||||||||
| 2876 | schtasks.exe /create /tn "fontdrvhostf" /sc MINUTE /mo 8 /tr "'C:\Program Files (x86)\Opera\fontdrvhost.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
88 360
Read events
86 621
Write events
1 545
Delete events
194
Modification events
| (PID) Process: | (6848) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (6848) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\6848 |
| Operation: | write | Name: | 0 |
Value: 0B0E10532BD0CD3E7F0F478855A564681C728C230046B797C3A087FFB8ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511C035D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (6848) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (6848) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (6848) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6848) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (6848) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (6848) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (6848) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (6848) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
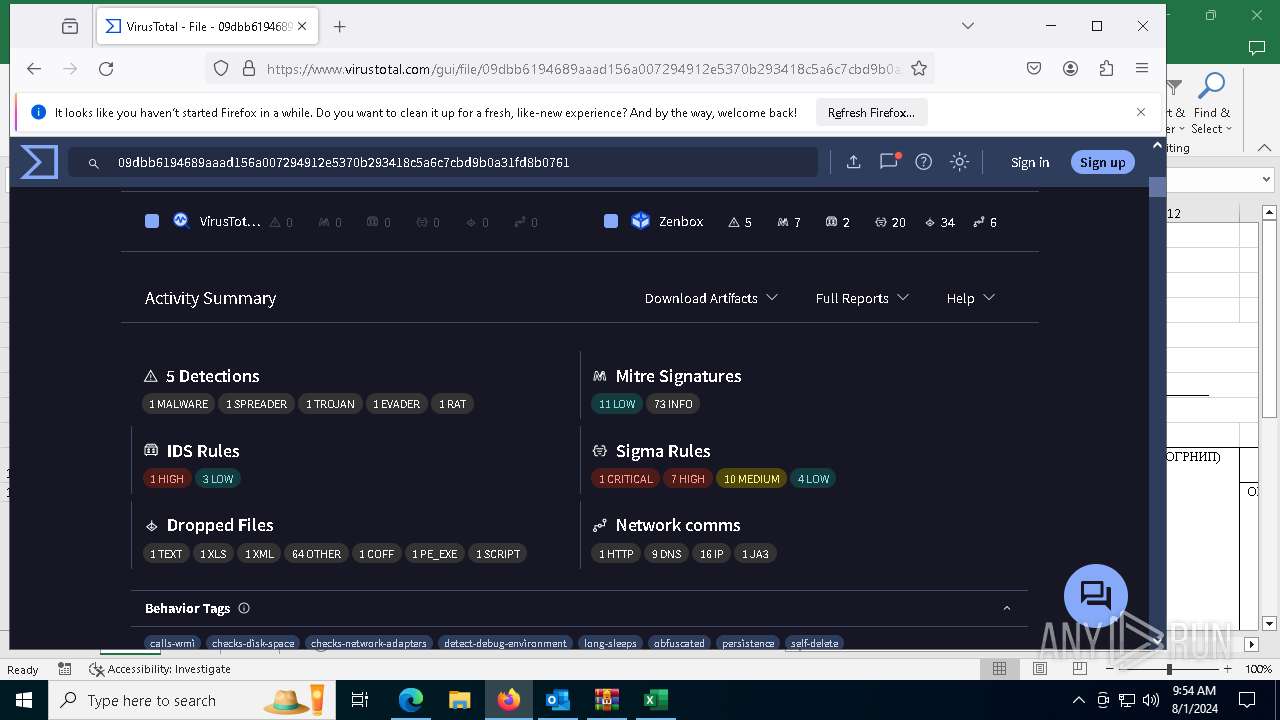
Executable files
18
Suspicious files
398
Text files
148
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6848 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 6848 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:B1C2A62715B156D6905C86DDAB5EE981 | SHA256:0BF0A7EA76A6AF3098FEB73A568EAB7DC96BB6EB0093ACB4D6BC495C23486A8F | |||
| 7252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RFe82d8.TMP | — | |
MD5:— | SHA256:— | |||
| 7252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6848 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:A9A10843A2B01C572FDB066E892843C7 | SHA256:5374F2262A9D5B9049DC66436B8DAC364745488E51F4E7EA56CB82FCA9EEA40D | |||
| 6848 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\27CC7A3E-0FFA-4C90-A1FD-89D9BB0801BE | xml | |
MD5:CE6CBC638E857156AEE75AECED4D9DE8 | SHA256:62A0238B0405325698A2215D26F3BCF83B8A79A9AD73618FB3B1257579A5C415 | |||
| 7252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RFe82e7.TMP | — | |
MD5:— | SHA256:— | |||
| 6848 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | binary | |
MD5:A47BAA1ADC222D3D555E173B0B81375E | SHA256:73B283F1C58BD31A52CD81EFB509D09EF0973912050BA7CF834017747478CC22 | |||
| 7252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6848 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:FAD6F380995B1EB33BA20E71BC576CA3 | SHA256:22DC24626E7BBDBE05A8004DDCAD41875E79DBD95142408B4099055F20FADAD7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
180
TCP/UDP connections
197
DNS requests
265
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6848 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5300 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6520 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6556 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6848 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
8008 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
8008 | firefox.exe | POST | 200 | 2.16.241.8:80 | http://r11.o.lencr.org/ | unknown | — | — | unknown |
8008 | firefox.exe | POST | 200 | 142.250.186.163:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
8008 | firefox.exe | POST | 200 | 2.16.241.15:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4100 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1116 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5336 | SearchApp.exe | 104.126.37.178:443 | www.bing.com | Akamai International B.V. | DE | unknown |
— | — | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5300 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7484 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
7484 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2256 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
6580 | System.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
6580 | System.exe | A Network Trojan was detected | ET MALWARE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
6580 | System.exe | A Network Trojan was detected | REMOTE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
6580 | System.exe | Misc activity | SUSPICIOUS [ANY.RUN] Possible DarkCrystal Rat Encrypted Connection |
6580 | System.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
6580 | System.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
Process | Message |
|---|---|
msedge.exe | [0801/095345.661:WARNING:device_ticket.cc(151)] Timed out waiting for device ticket. Canceling async operation.
|
msedge.exe | [0801/095347.348:ERROR:filesystem_win.cc(128)] GetFileAttributes C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\attachments\b551a0d7-c149-4578-9fc5-02c0ef78e1dc: The system cannot find the file specified. (0x2)
|
msedge.exe | [0801/095347.348:ERROR:filesystem_win.cc(128)] GetFileAttributes C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\attachments\b551a0d7-c149-4578-9fc5-02c0ef78e1dc: The system cannot find the file specified. (0x2)
|
msedge.exe | [0801/095347.395:ERROR:filesystem_win.cc(128)] GetFileAttributes C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\attachments\b551a0d7-c149-4578-9fc5-02c0ef78e1dc: The system cannot find the file specified. (0x2)
|
msedge.exe | [0801/095347.395:ERROR:filesystem_win.cc(128)] GetFileAttributes C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\attachments\b551a0d7-c149-4578-9fc5-02c0ef78e1dc: The system cannot find the file specified. (0x2)
|
msedge.exe | [0801/095409.931:ERROR:filesystem_win.cc(128)] GetFileAttributes C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\attachments\2796ed85-a752-4903-9803-58a13df9ac61: The system cannot find the file specified. (0x2)
|
msedge.exe | [0801/095409.931:ERROR:filesystem_win.cc(128)] GetFileAttributes C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\attachments\b551a0d7-c149-4578-9fc5-02c0ef78e1dc: The system cannot find the file specified. (0x2)
|
msedge.exe | [0801/095409.931:ERROR:filesystem_win.cc(128)] GetFileAttributes C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\attachments\b551a0d7-c149-4578-9fc5-02c0ef78e1dc: The system cannot find the file specified. (0x2)
|
msedge.exe | [0801/095409.931:ERROR:filesystem_win.cc(128)] GetFileAttributes C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\attachments\2796ed85-a752-4903-9803-58a13df9ac61: The system cannot find the file specified. (0x2)
|
msedge.exe | [0801/095409.931:ERROR:filesystem_win.cc(128)] GetFileAttributes C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\attachments\b551a0d7-c149-4578-9fc5-02c0ef78e1dc: The system cannot find the file specified. (0x2)
|