| File name: | Zemana.AntiMalware.Setup.exe |
| Full analysis: | https://app.any.run/tasks/2783a922-a6db-4caa-b2e7-3820a5b16ba3 |
| Verdict: | Malicious activity |
| Analysis date: | June 09, 2024, 20:50:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 048EA3233E0E7611AB414684583C1421 |
| SHA1: | 026E20BACA271CBFEA44FA2CE6F3E405CA5D263D |
| SHA256: | B548F01428CB26A5870602E8018ADBCE814DD2ED53A6B1F74C3B3B7BF23FA965 |
| SSDEEP: | 98304:e+QqZ8f+RYeWUC1k/lyeacDiV1eJ5X40iS0Tfya8+L/GIuBMJMEbCIkFIDUw67HG:xziahJqry7VR2/Mttleqhc/9+DQiW |
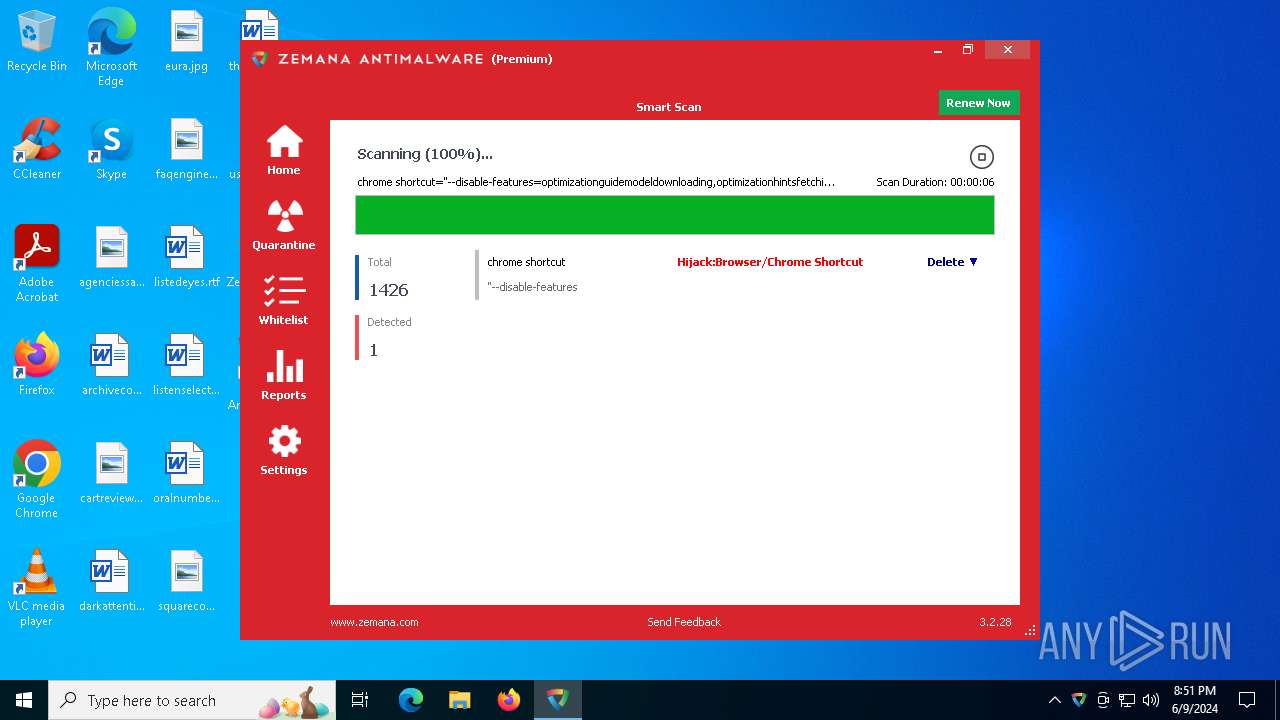
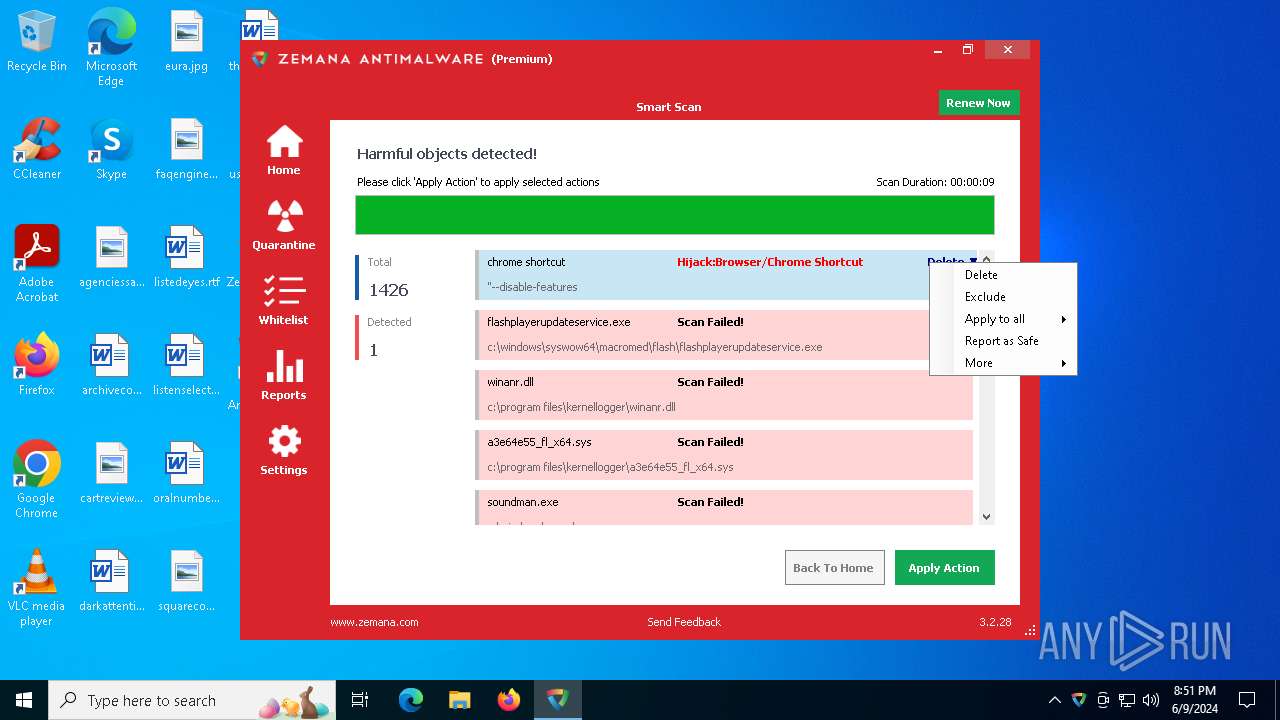
MALICIOUS
Drops the executable file immediately after the start
- Zemana.AntiMalware.Setup.exe (PID: 6504)
- Zemana.AntiMalware.Setup.exe (PID: 6616)
- Zemana.AntiMalware.Setup.tmp (PID: 6656)
Creates a writable file in the system directory
- Zemana.AntiMalware.Setup.tmp (PID: 6656)
Registers / Runs the DLL via REGSVR32.EXE
- Zemana.AntiMalware.Setup.tmp (PID: 6656)
Uses Task Scheduler to run other applications
- Zemana.AntiMalware.Setup.tmp (PID: 6656)
- AntiMalware.exe (PID: 7124)
Steals credentials from Web Browsers
- AntiMalware.exe (PID: 7124)
Actions looks like stealing of personal data
- AntiMalware.exe (PID: 7124)
Scans artifacts that could help determine the target
- AntiMalware.exe (PID: 7124)
SUSPICIOUS
Executable content was dropped or overwritten
- Zemana.AntiMalware.Setup.exe (PID: 6616)
- Zemana.AntiMalware.Setup.tmp (PID: 6656)
- Zemana.AntiMalware.Setup.exe (PID: 6504)
Reads the Windows owner or organization settings
- Zemana.AntiMalware.Setup.tmp (PID: 6656)
Creates files in the driver directory
- Zemana.AntiMalware.Setup.tmp (PID: 6656)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 7040)
Drops a system driver (possible attempt to evade defenses)
- Zemana.AntiMalware.Setup.tmp (PID: 6656)
Process drops legitimate windows executable
- Zemana.AntiMalware.Setup.tmp (PID: 6656)
Adds/modifies Windows certificates
- AntiMalware.exe (PID: 7124)
Reads security settings of Internet Explorer
- AntiMalware.exe (PID: 7124)
- Zemana.AntiMalware.Setup.tmp (PID: 6536)
The process verifies whether the antivirus software is installed
- AntiMalware.exe (PID: 7124)
Read startup parameters
- AntiMalware.exe (PID: 7124)
Reads the date of Windows installation
- Zemana.AntiMalware.Setup.tmp (PID: 6536)
Reads Microsoft Outlook installation path
- AntiMalware.exe (PID: 7124)
Reads Internet Explorer settings
- AntiMalware.exe (PID: 7124)
Checks Windows Trust Settings
- AntiMalware.exe (PID: 7124)
INFO
Create files in a temporary directory
- Zemana.AntiMalware.Setup.tmp (PID: 6656)
- Zemana.AntiMalware.Setup.exe (PID: 6504)
- Zemana.AntiMalware.Setup.exe (PID: 6616)
- AntiMalware.exe (PID: 7124)
Checks supported languages
- Zemana.AntiMalware.Setup.tmp (PID: 6656)
- Zemana.AntiMalware.Setup.exe (PID: 6504)
- Zemana.AntiMalware.Setup.tmp (PID: 6536)
- AntiMalware.exe (PID: 7124)
- Zemana.AntiMalware.Setup.exe (PID: 6616)
Reads the computer name
- Zemana.AntiMalware.Setup.tmp (PID: 6656)
- AntiMalware.exe (PID: 7124)
- Zemana.AntiMalware.Setup.tmp (PID: 6536)
Process checks computer location settings
- Zemana.AntiMalware.Setup.tmp (PID: 6536)
Creates files or folders in the user directory
- Zemana.AntiMalware.Setup.tmp (PID: 6656)
- AntiMalware.exe (PID: 7124)
Creates files in the program directory
- Zemana.AntiMalware.Setup.tmp (PID: 6656)
- AntiMalware.exe (PID: 7124)
Creates a software uninstall entry
- Zemana.AntiMalware.Setup.tmp (PID: 6656)
Reads the machine GUID from the registry
- AntiMalware.exe (PID: 7124)
Reads Environment values
- AntiMalware.exe (PID: 7124)
Disables trace logs
- AntiMalware.exe (PID: 7124)
Checks proxy server information
- AntiMalware.exe (PID: 7124)
Reads CPU info
- AntiMalware.exe (PID: 7124)
Process checks Internet Explorer phishing filters
- AntiMalware.exe (PID: 7124)
Reads the software policy settings
- AntiMalware.exe (PID: 7124)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (51.8) |
|---|---|---|
| .exe | | | InstallShield setup (20.3) |
| .exe | | | Win32 EXE PECompact compressed (generic) (19.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.1) |
| .exe | | | Win32 Executable (generic) (2.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:11:15 09:48:30+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741376 |
| InitializedDataSize: | 38400 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.2.28.0 |
| ProductVersionNumber: | 3.2.28.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Zemana Ltd. |
| FileDescription: | Advanced Malware Protection |
| FileVersion: | 3.2.28 |
| LegalCopyright: | Copyright 2017 |
| OriginalFileName: | |
| ProductName: | Advanced Malware Protection |
| ProductVersion: | 3.2.28 |
Total processes
131
Monitored processes
13
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4080 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4288 | "schtasks.exe" /CREATE /F /TN "AMSkipUAC" /XML "C:\Program Files (x86)\Zemana\AntiMalware\data\AMSkipUAC" | C:\Windows\SysWOW64\schtasks.exe | — | AntiMalware.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4480 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6172 | "schtasks.exe" /CREATE /F /TN "AMSkipUAC" /XML "C:\Program Files (x86)\Zemana\AntiMalware\data\AMSkipUAC" | C:\Windows\SysWOW64\schtasks.exe | — | AntiMalware.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6504 | "C:\Users\admin\Desktop\Zemana.AntiMalware.Setup.exe" | C:\Users\admin\Desktop\Zemana.AntiMalware.Setup.exe | explorer.exe | ||||||||||||
User: admin Company: Zemana Ltd. Integrity Level: MEDIUM Description: Advanced Malware Protection Exit code: 0 Version: 3.2.28 Modules
| |||||||||||||||
| 6536 | "C:\Users\admin\AppData\Local\Temp\is-8981J.tmp\Zemana.AntiMalware.Setup.tmp" /SL5="$401DE,13025042,780800,C:\Users\admin\Desktop\Zemana.AntiMalware.Setup.exe" | C:\Users\admin\AppData\Local\Temp\is-8981J.tmp\Zemana.AntiMalware.Setup.tmp | — | Zemana.AntiMalware.Setup.exe | |||||||||||
User: admin Company: Zemana Ltd. Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 6616 | "C:\Users\admin\Desktop\Zemana.AntiMalware.Setup.exe" /SPAWNWND=$301F6 /NOTIFYWND=$401DE | C:\Users\admin\Desktop\Zemana.AntiMalware.Setup.exe | Zemana.AntiMalware.Setup.tmp | ||||||||||||
User: admin Company: Zemana Ltd. Integrity Level: HIGH Description: Advanced Malware Protection Exit code: 0 Version: 3.2.28 Modules
| |||||||||||||||
| 6656 | "C:\Users\admin\AppData\Local\Temp\is-2H670.tmp\Zemana.AntiMalware.Setup.tmp" /SL5="$502A8,13025042,780800,C:\Users\admin\Desktop\Zemana.AntiMalware.Setup.exe" /SPAWNWND=$301F6 /NOTIFYWND=$401DE | C:\Users\admin\AppData\Local\Temp\is-2H670.tmp\Zemana.AntiMalware.Setup.tmp | Zemana.AntiMalware.Setup.exe | ||||||||||||
User: admin Company: Zemana Ltd. Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 6936 | "C:\WINDOWS\system32\regsvr32.exe" /s "C:\Program Files (x86)\Zemana\AntiMalware\AM_ShellExt64.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | Zemana.AntiMalware.Setup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7040 | /s "C:\Program Files (x86)\Zemana\AntiMalware\AM_ShellExt64.dll" | C:\Windows\System32\regsvr32.exe | — | regsvr32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
36 264
Read events
36 060
Write events
193
Delete events
11
Modification events
| (PID) Process: | (6656) Zemana.AntiMalware.Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion |
| Operation: | write | Name: | CUID |
Value: 123B235C41148C76422FA6 | |||
| (PID) Process: | (6656) Zemana.AntiMalware.Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\ZmnGlobalSDK |
| Operation: | write | Name: | CUID |
Value: 123B235C41148C76422FA6 | |||
| (PID) Process: | (6656) Zemana.AntiMalware.Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\amsdk\Instances |
| Operation: | write | Name: | DefaultInstance |
Value: AMSDKDefaultFilter | |||
| (PID) Process: | (6656) Zemana.AntiMalware.Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\amsdk\Instances\AMSDKDefaultFilter |
| Operation: | write | Name: | Altitude |
Value: 80682 | |||
| (PID) Process: | (6656) Zemana.AntiMalware.Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\amsdk\Instances\AMSDKDefaultFilter |
| Operation: | write | Name: | Flags |
Value: 0 | |||
| (PID) Process: | (6656) Zemana.AntiMalware.Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\CrashControl |
| Operation: | write | Name: | CrashDumpEnabled |
Value: 3 | |||
| (PID) Process: | (6656) Zemana.AntiMalware.Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\ZmnGlobalSDK |
| Operation: | write | Name: | PartnerId |
Value: 2 | |||
| (PID) Process: | (6656) Zemana.AntiMalware.Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\ZmnGlobalSDK |
| Operation: | write | Name: | AM_SelectedLang |
Value: x0409 | |||
| (PID) Process: | (6656) Zemana.AntiMalware.Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\ZmnGlobalSDK |
| Operation: | write | Name: | AM_InstallPath |
Value: C:\Program Files (x86)\Zemana\AntiMalware | |||
| (PID) Process: | (6656) Zemana.AntiMalware.Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\ZmnGlobalSDK |
| Operation: | write | Name: | AM_ShellIconPath |
Value: C:\Program Files (x86)\Zemana\AntiMalware\res\2.ico | |||
Executable files
33
Suspicious files
55
Text files
62
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6504 | Zemana.AntiMalware.Setup.exe | C:\Users\admin\AppData\Local\Temp\is-8981J.tmp\Zemana.AntiMalware.Setup.tmp | executable | |
MD5:EA91A08C1EB0733BB797BB6458F01FB9 | SHA256:C0C7E61F5D7F57F14F6741D38514D265B48DCCC267303D17B8195B1548736590 | |||
| 6656 | Zemana.AntiMalware.Setup.tmp | C:\WINDOWS\system32\drivers\amsdk.sys | executable | |
MD5:A83639773C1BD96A2953EA64A82FF863 | SHA256:9C394DCAB9F711E2BF585EDF0D22D2210843885917D409EE56F22A4C24AD225E | |||
| 6656 | Zemana.AntiMalware.Setup.tmp | C:\Program Files (x86)\Zemana\AntiMalware\is-JF43M.tmp | executable | |
MD5:048EA3233E0E7611AB414684583C1421 | SHA256:B548F01428CB26A5870602E8018ADBCE814DD2ED53A6B1F74C3B3B7BF23FA965 | |||
| 6656 | Zemana.AntiMalware.Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-QEN8F.tmp\2.rtf | text | |
MD5:D8F67DA37A0AF157E6D5065AD335D15B | SHA256:B6A8596D7D5A2A2B4A8AD4027E697619350FAB83083B9261C34E63C9F7CD29DE | |||
| 6656 | Zemana.AntiMalware.Setup.tmp | C:\Program Files (x86)\Zemana\AntiMalware\Setup.exe | executable | |
MD5:048EA3233E0E7611AB414684583C1421 | SHA256:B548F01428CB26A5870602E8018ADBCE814DD2ED53A6B1F74C3B3B7BF23FA965 | |||
| 6616 | Zemana.AntiMalware.Setup.exe | C:\Users\admin\AppData\Local\Temp\is-2H670.tmp\Zemana.AntiMalware.Setup.tmp | executable | |
MD5:EA91A08C1EB0733BB797BB6458F01FB9 | SHA256:C0C7E61F5D7F57F14F6741D38514D265B48DCCC267303D17B8195B1548736590 | |||
| 6656 | Zemana.AntiMalware.Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-QEN8F.tmp\Partners.ini | ini | |
MD5:8FF384084F33F06A3952FC12FF75D1E6 | SHA256:CA10CD00B06593F4CE25839742289F78E3962BD0450A803479A989FA744CF269 | |||
| 6656 | Zemana.AntiMalware.Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-QEN8F.tmp\AMSDKCore399001.dll | executable | |
MD5:BD1CD3CB27C3687F70789C96BD324381 | SHA256:2C63C9035A5794423FCF360A685C321C0D1A4E72C4DCA4C66A87D7A2157D3BB5 | |||
| 6656 | Zemana.AntiMalware.Setup.tmp | C:\Program Files (x86)\Zemana\AntiMalware\AntiMalware.exe | executable | |
MD5:75CD10A49F0743FE04B5B282D9F7A5CE | SHA256:E64091F1796AEE4900EA972DC2403CC649FACE1D7A1BF76911528EDEBD6BEF1A | |||
| 6656 | Zemana.AntiMalware.Setup.tmp | C:\Program Files (x86)\Zemana\AntiMalware\is-RAMUA.tmp | executable | |
MD5:EA91A08C1EB0733BB797BB6458F01FB9 | SHA256:C0C7E61F5D7F57F14F6741D38514D265B48DCCC267303D17B8195B1548736590 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
46
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4540 | RUXIMICS.exe | GET | 200 | 2.22.57.219:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
5140 | MoUsoCoreWorker.exe | GET | 200 | 23.216.155.66:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5504 | svchost.exe | GET | 200 | 23.216.155.66:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
— | — | GET | 200 | 208.109.191.195:443 | https://zam-ai.zemana.com/api/client/settings/123B235C41148C76422FA6/2/2/3002028/ | unknown | — | — | unknown |
5140 | MoUsoCoreWorker.exe | GET | — | 2.22.57.219:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
5504 | svchost.exe | GET | 200 | 2.22.57.219:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
— | — | GET | 301 | 192.168.1.2:443 | https://zam-cloud.zemana.com/api/scan-post-feedback?culture=en-US&isFree=False | unknown | — | — | unknown |
7124 | AntiMalware.exe | GET | 200 | 17.253.57.200:80 | http://captive.apple.com/hotspot-detect.html | unknown | — | — | unknown |
7124 | AntiMalware.exe | GET | 200 | 17.253.57.200:80 | http://captive.apple.com/hotspot-detect.html | unknown | — | — | unknown |
— | — | GET | 200 | 208.109.191.195:443 | https://zam-ai.zemana.com/api/client/settings/123B235C41148C76422FA6/2/2/3002028/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4364 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5504 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4540 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5140 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5140 | MoUsoCoreWorker.exe | 23.216.155.66:80 | crl.microsoft.com | Akamai International B.V. | IE | unknown |
5504 | svchost.exe | 23.216.155.66:80 | crl.microsoft.com | Akamai International B.V. | IE | unknown |
5140 | MoUsoCoreWorker.exe | 2.22.57.219:80 | www.microsoft.com | AKAMAI-AS | FR | unknown |
5504 | svchost.exe | 2.22.57.219:80 | www.microsoft.com | AKAMAI-AS | FR | unknown |
4540 | RUXIMICS.exe | 2.22.57.219:80 | www.microsoft.com | AKAMAI-AS | FR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
zam-ai.zemana.com |
| whitelisted |
check.zemana.com |
| whitelisted |
zam-cloud.zemana.com |
| unknown |
connect.zemana.com |
| unknown |
captive.apple.com |
| whitelisted |
dl12.zemana.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
AntiMalware.exe | AMLogger: 2024-06-09 20:51:12,992 [INFO ] [1] [Zemana.AntiMalware.UI.Program.Main] Line: 54 - ################################# SYSTEM INITIALIZED #################################
|
AntiMalware.exe | AMLogger: 2024-06-09 20:51:13,117 [INFO ] [1] [Zemana.AntiMalware.UI.Program.Main] Line: 55 - v3.2.28 is launching...
|
AntiMalware.exe | AMLogger: 2024-06-09 20:51:13,289 [INFO ] [1] [Zemana.AntiMalware.UI.Services.CommandHandler.CreateOrShowRunningUIInstance] Line: 234 - ================= Running command C:\Program Files (x86)\Zemana\AntiMalware\AntiMalware.exe /SL5=$502A8,13025042,780800,C:\Users\admin\Desktop\Zemana.AntiMalware.Setup.exe /SPAWNWND=$301F6 /NOTIFYWND=$401DE /INSTALLER /SELECTEDLANG x0409 /AUTOSTART /AUTOUPLOAD =================
|
AntiMalware.exe | AMLogger: 2024-06-09 20:51:14,023 [DEBUG] [1] [Zemana.AntiMalware.Core.Localization.Translator.Initialize] Line: 59 - Initializing translator... ActiveLanguageCode:
|
AntiMalware.exe | AMLogger: 2024-06-09 20:51:14,023 [DEBUG] [1] [Zemana.AntiMalware.Core.Localization.Translator.Initialize] Line: 72 - Language file path: C:\Program Files (x86)\Zemana\AntiMalware\Languages\Arabic.json
|
AntiMalware.exe | AMLogger: 2024-06-09 20:51:14,039 [DEBUG] [1] [Zemana.AntiMalware.Core.Localization.Translator.Initialize] Line: 81 - Is translation null: False
|
AntiMalware.exe | AMLogger: 2024-06-09 20:51:14,039 [DEBUG] [1] [Zemana.AntiMalware.Core.Localization.Translator.Initialize] Line: 72 - Language file path: C:\Program Files (x86)\Zemana\AntiMalware\Languages\Korean.json
|
AntiMalware.exe | AMLogger: 2024-06-09 20:51:14,039 [DEBUG] [1] [Zemana.AntiMalware.Core.Localization.Translator.Initialize] Line: 81 - Is translation null: False
|
AntiMalware.exe | AMLogger: 2024-06-09 20:51:14,039 [DEBUG] [1] [Zemana.AntiMalware.Core.Localization.Translator.Initialize] Line: 81 - Is translation null: False
|
AntiMalware.exe | AMLogger: 2024-06-09 20:51:14,039 [DEBUG] [1] [Zemana.AntiMalware.Core.Localization.Translator.Initialize] Line: 81 - Is translation null: False
|