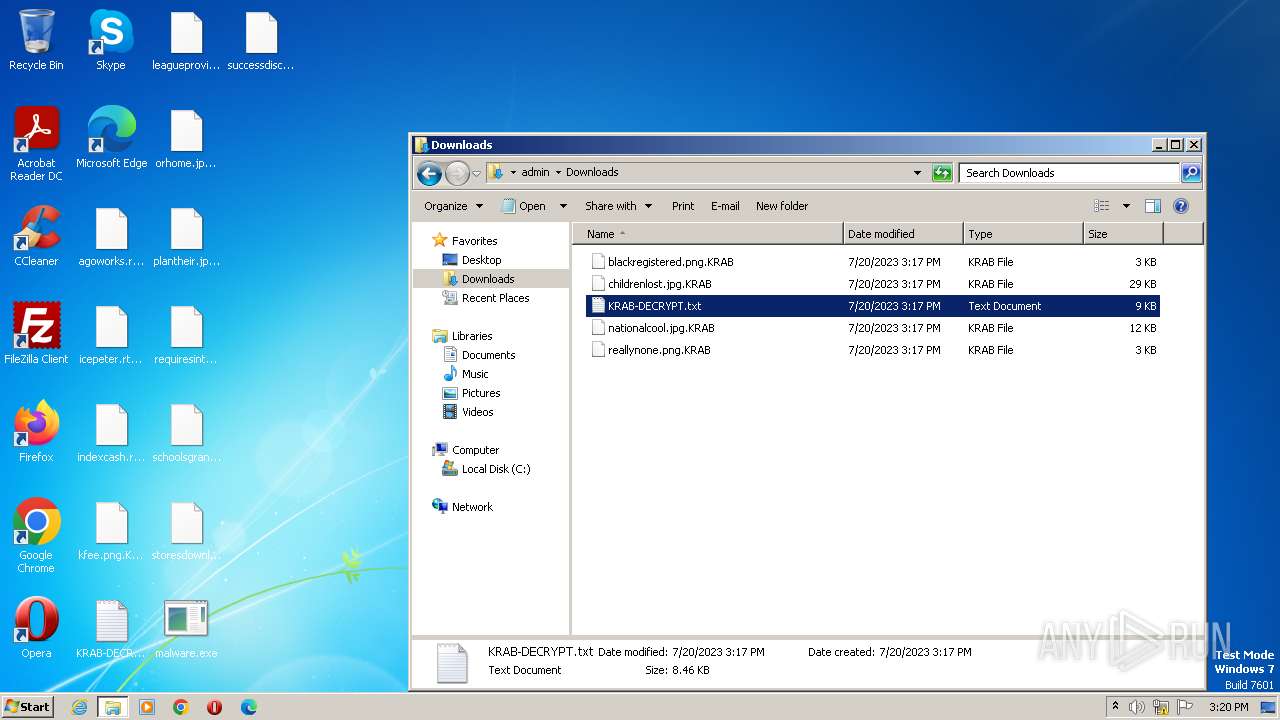
| File name: | malware.exe |
| Full analysis: | https://app.any.run/tasks/47ddac92-bc77-4384-adf0-8cb6da2db70e |
| Verdict: | Malicious activity |
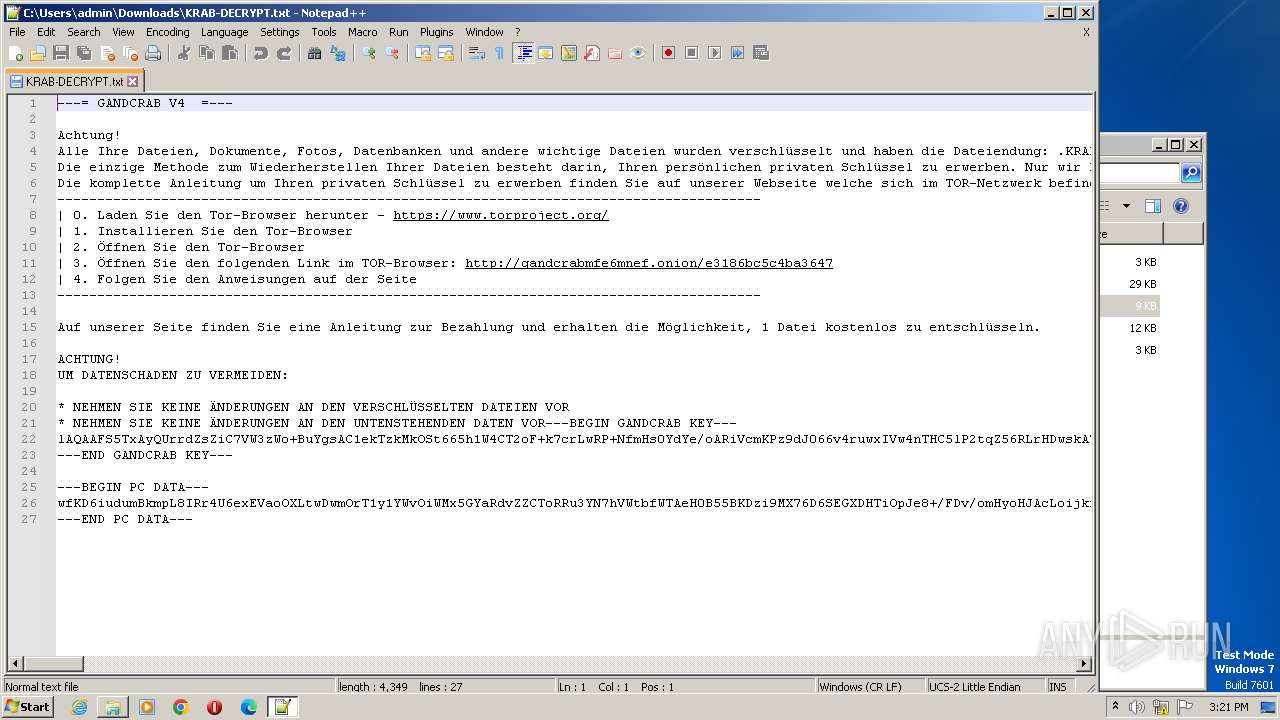
| Threats: | GandCrab is probably one of the most famous Ransomware. A Ransomware is a malware that asks the victim to pay money in order to restore access to encrypted files. If the user does not cooperate the files are forever lost. |
| Analysis date: | July 20, 2023, 14:17:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 35D03057D02E656FFE148BBB2523E0C7 |
| SHA1: | 3FF49986FD966A3157BE5B82B5FD02575E99E4BC |
| SHA256: | B535D4DC180F666DE891979E5D9D090C27D1EB0F252423C0B1911F1F0B9FC5B2 |
| SSDEEP: | 3072:x3iPmbqzPrLd+9zUhGed8tzm0OofBB61pqnevTglfap0PBNe8mFNTXaCm:x3iRLXd+9wEedAzNOoJB9nevT8CqEFN |
MALICIOUS
Writes a file to the Word startup folder
- malware.exe (PID: 4052)
Connects to the CnC server
- malware.exe (PID: 4052)
GANDCRAB was detected
- malware.exe (PID: 4052)
Steals credentials from Web Browsers
- malware.exe (PID: 4052)
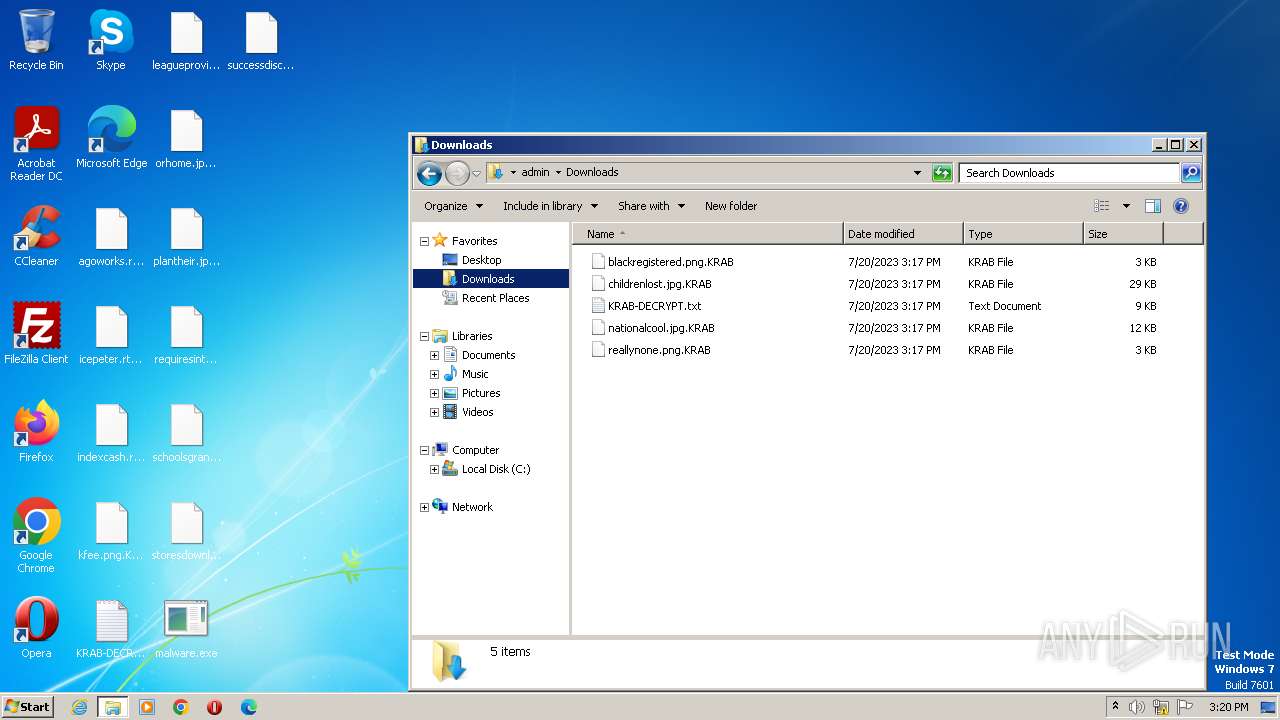
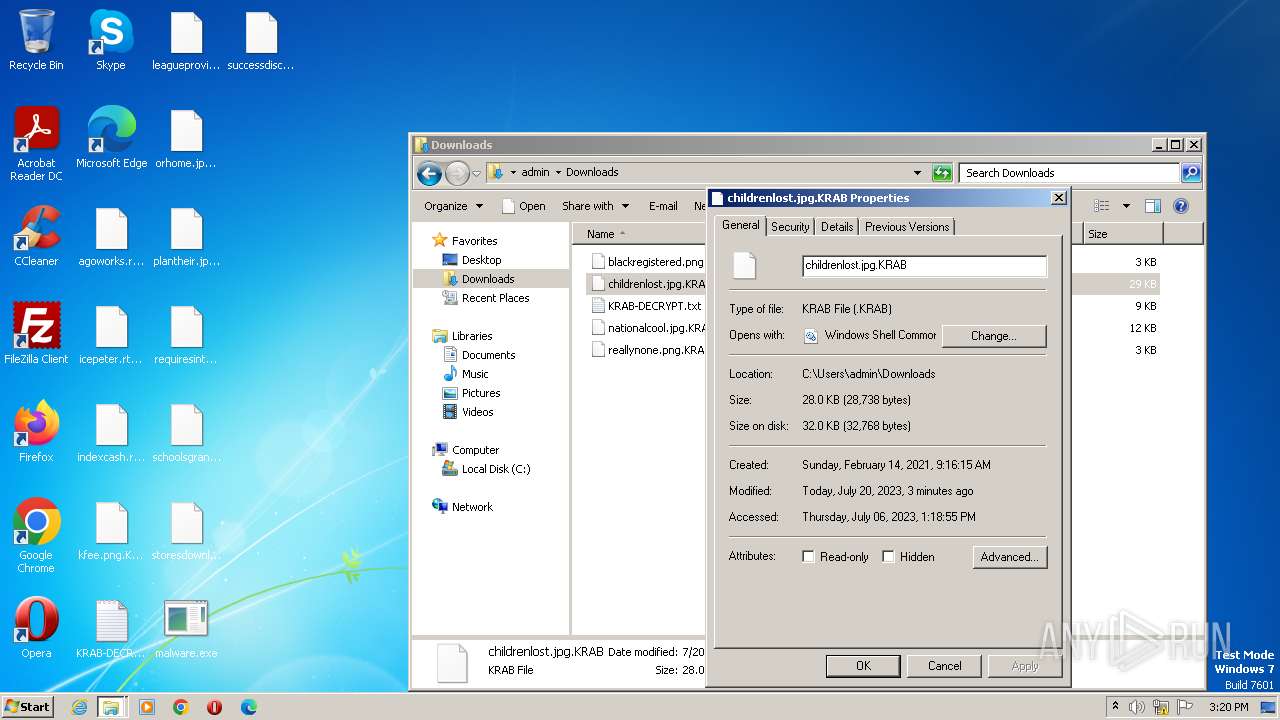
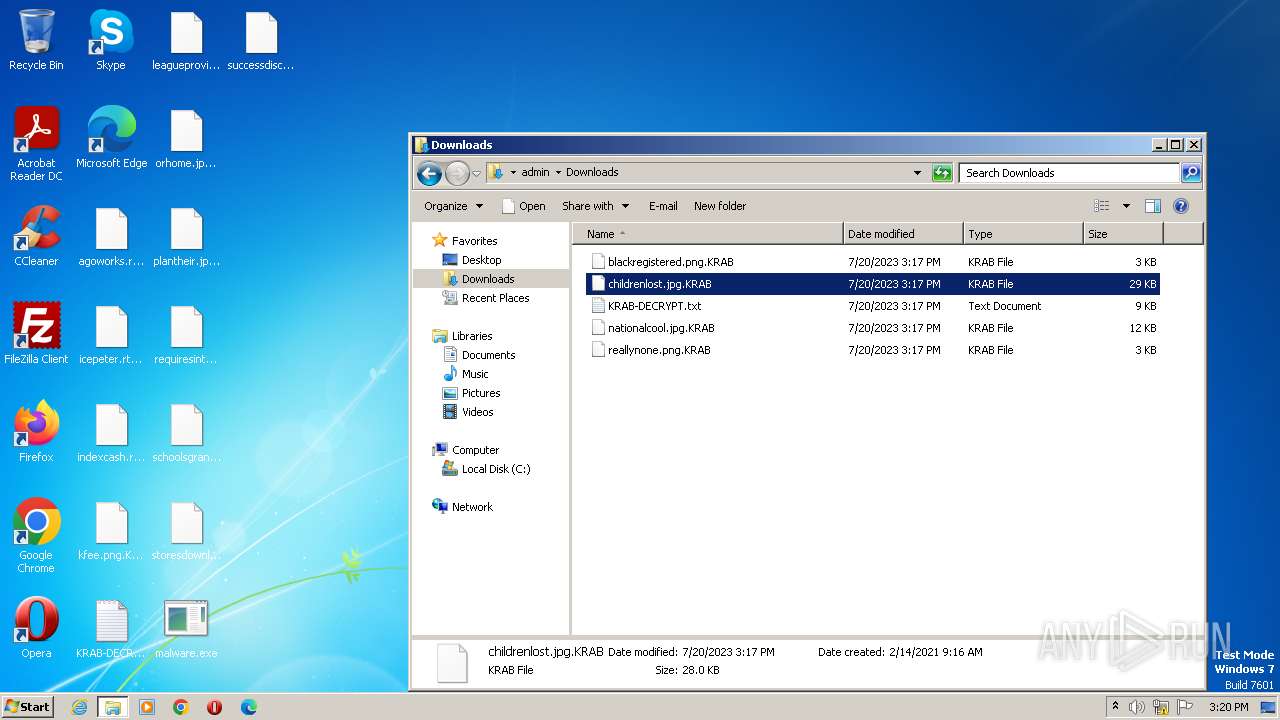
Renames files like ransomware
- malware.exe (PID: 4052)
Deletes shadow copies
- malware.exe (PID: 4052)
Actions looks like stealing of personal data
- malware.exe (PID: 4052)
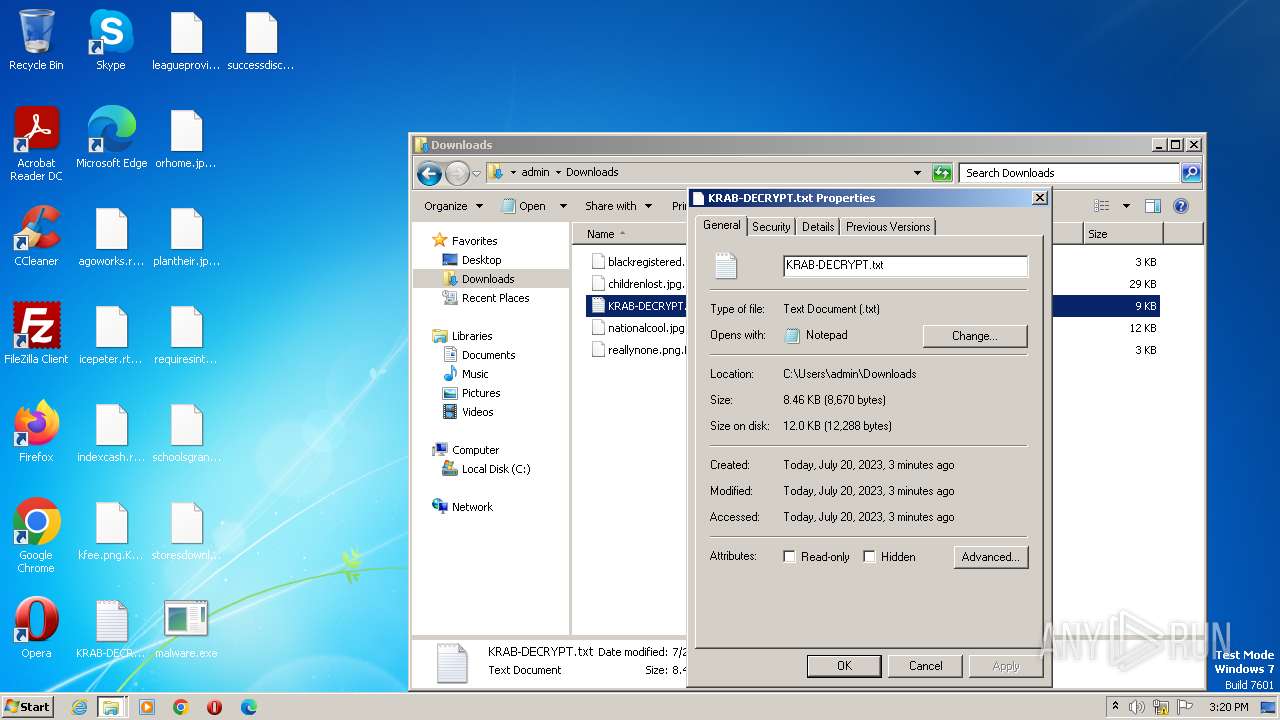
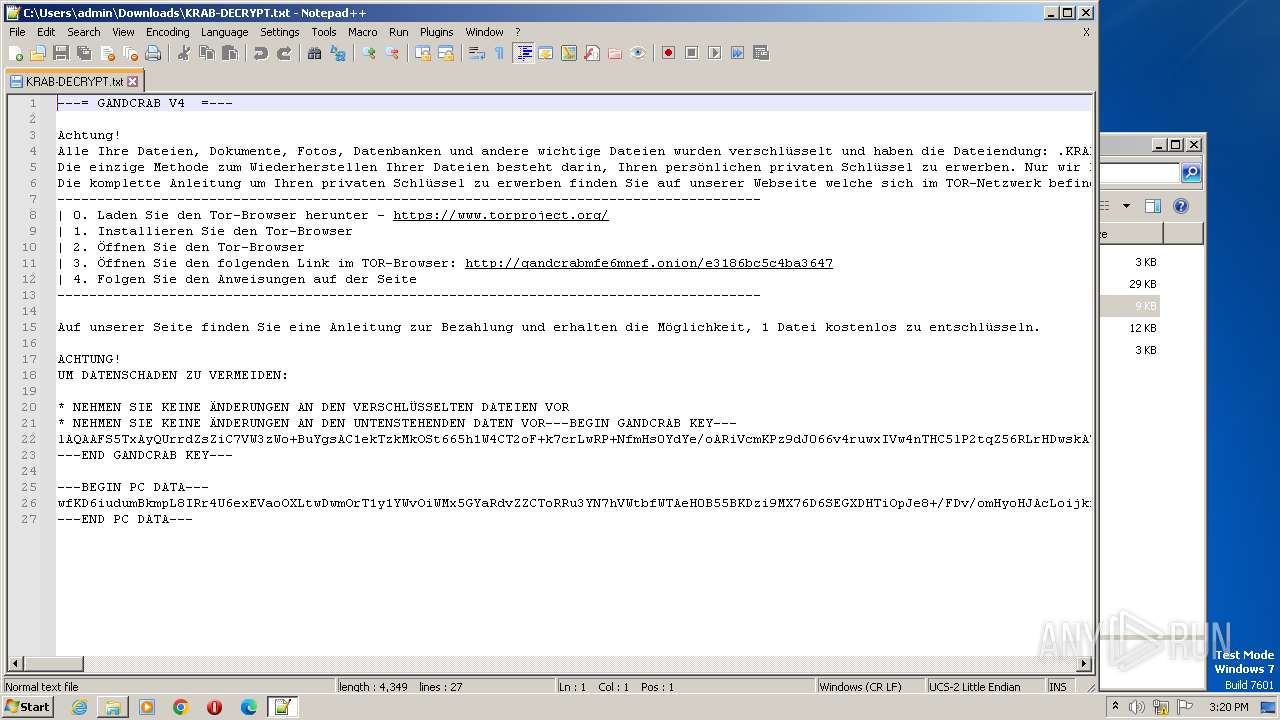
Gandcrab ransom note is found
- malware.exe (PID: 4052)
- malware.exe (PID: 4052)
SUSPICIOUS
Reads the Internet Settings
- malware.exe (PID: 4052)
- WMIC.exe (PID: 2852)
Reads browser cookies
- malware.exe (PID: 4052)
Creates files like ransomware instruction
- malware.exe (PID: 4052)
Reads security settings of Internet Explorer
- malware.exe (PID: 4052)
Reads settings of System Certificates
- malware.exe (PID: 4052)
Checks Windows Trust Settings
- malware.exe (PID: 4052)
INFO
Reads Environment values
- malware.exe (PID: 4052)
Checks supported languages
- malware.exe (PID: 4052)
- wmpnscfg.exe (PID: 1580)
Reads the computer name
- malware.exe (PID: 4052)
- wmpnscfg.exe (PID: 1580)
Reads product name
- malware.exe (PID: 4052)
Reads the machine GUID from the registry
- malware.exe (PID: 4052)
- wmpnscfg.exe (PID: 1580)
The process checks LSA protection
- malware.exe (PID: 4052)
- WMIC.exe (PID: 2852)
- wmpnscfg.exe (PID: 1580)
- explorer.exe (PID: 2892)
- notepad++.exe (PID: 3588)
Reads CPU info
- malware.exe (PID: 4052)
Checks proxy server information
- malware.exe (PID: 4052)
Creates files or folders in the user directory
- malware.exe (PID: 4052)
Manual execution by a user
- wmpnscfg.exe (PID: 1580)
- explorer.exe (PID: 2892)
- notepad++.exe (PID: 3588)
Dropped object may contain TOR URL's
- malware.exe (PID: 4052)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| CharacterSet: | Unknown (77B0) |
|---|---|
| LanguageCode: | Unknown (3436) |
| FileSubtype: | - |
| ObjectFileType: | VxD |
| FileOS: | Unknown (0x588891) |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 12.0.0.0 |
| FileVersionNumber: | 11.0.0.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 5.1 |
| ImageVersion: | - |
| OSVersion: | 5.1 |
| EntryPoint: | 0x4955 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 110080 |
| CodeSize: | 147456 |
| LinkerVersion: | 10 |
| PEType: | PE32 |
| ImageFileCharacteristics: | Executable, 32-bit |
| TimeStamp: | 2017:05:12 01:51:11+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 12-May-2017 01:51:11 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000F0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 12-May-2017 01:51:11 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00023F95 | 0x00024000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 7.58057 |
.rdata | 0x00025000 | 0x0000652A | 0x00006600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.85165 |
.data | 0x0002C000 | 0x000040A8 | 0x00002200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.20509 |
.rsrc | 0x00031000 | 0x0000F450 | 0x0000F600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.45224 |
.reloc | 0x00041000 | 0x00001D2C | 0x00001E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 4.82363 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 2.86432 | 184 | UNKNOWN | UNKNOWN | RT_VERSION |
199 | 4.07191 | 23560 | UNKNOWN | UNKNOWN | RT_BITMAP |
201 | 6.21639 | 29736 | UNKNOWN | UNKNOWN | RT_BITMAP |
234 | 5.96011 | 5072 | UNKNOWN | UNKNOWN | RT_BITMAP |
1235 | 4.99297 | 2720 | UNKNOWN | UNKNOWN | RT_BITMAP |
Imports
ADVAPI32.dll |
KERNEL32.dll |
Total processes
53
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1580 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2492 | "C:\Program Files\Notepad++\updater\gup.exe" -v7.91 | C:\Program Files\Notepad++\updater\GUP.exe | notepad++.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: WinGup for Notepad++ Exit code: 4294967295 Version: 5.11 Modules
| |||||||||||||||
| 2852 | "C:\Windows\system32\wbem\wmic.exe" shadowcopy delete | C:\Windows\System32\wbem\WMIC.exe | — | malware.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 2147749908 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2892 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3588 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Downloads\KRAB-DECRYPT.txt" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 4052 | "C:\Users\admin\Desktop\malware.exe" | C:\Users\admin\Desktop\malware.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
21 429
Read events
21 378
Write events
48
Delete events
3
Modification events
| (PID) Process: | (4052) malware.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (4052) malware.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000047010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4052) malware.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4052) malware.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4052) malware.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4052) malware.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (4052) malware.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4052) malware.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1580) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{AC937D25-B615-4205-BB48-654BA316074B}\{66B7EE32-9FD6-46A2-8B87-22C2FDCDB325} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1580) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{AC937D25-B615-4205-BB48-654BA316074B} |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
0
Suspicious files
978
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4052 | malware.exe | C:\Users\admin\AppData\KRAB-DECRYPT.txt | binary | |
MD5:96E2807F5AAC20FFB171ACE14BC30A72 | SHA256:9E6F03AB44EE572DCA68480B8F28937922430CF00CFBEBC0B7CA283993613DF1 | |||
| 4052 | malware.exe | C:\$Recycle.Bin\S-1-5-21-1302019708-1500728564-335382590-1000\KRAB-DECRYPT.txt | binary | |
MD5:96E2807F5AAC20FFB171ACE14BC30A72 | SHA256:9E6F03AB44EE572DCA68480B8F28937922430CF00CFBEBC0B7CA283993613DF1 | |||
| 4052 | malware.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\KRAB-DECRYPT.txt | binary | |
MD5:96E2807F5AAC20FFB171ACE14BC30A72 | SHA256:9E6F03AB44EE572DCA68480B8F28937922430CF00CFBEBC0B7CA283993613DF1 | |||
| 4052 | malware.exe | C:\Users\admin\.oracle_jre_usage\KRAB-DECRYPT.txt | binary | |
MD5:96E2807F5AAC20FFB171ACE14BC30A72 | SHA256:9E6F03AB44EE572DCA68480B8F28937922430CF00CFBEBC0B7CA283993613DF1 | |||
| 4052 | malware.exe | C:\MSOCache\KRAB-DECRYPT.txt | binary | |
MD5:96E2807F5AAC20FFB171ACE14BC30A72 | SHA256:9E6F03AB44EE572DCA68480B8F28937922430CF00CFBEBC0B7CA283993613DF1 | |||
| 4052 | malware.exe | C:\Users\admin\AppData\Roaming\KRAB-DECRYPT.txt | binary | |
MD5:96E2807F5AAC20FFB171ACE14BC30A72 | SHA256:9E6F03AB44EE572DCA68480B8F28937922430CF00CFBEBC0B7CA283993613DF1 | |||
| 4052 | malware.exe | C:\Users\admin\AppData\Roaming\Adobe\KRAB-DECRYPT.txt | binary | |
MD5:96E2807F5AAC20FFB171ACE14BC30A72 | SHA256:9E6F03AB44EE572DCA68480B8F28937922430CF00CFBEBC0B7CA283993613DF1 | |||
| 4052 | malware.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\JSCache\GlobData.KRAB | binary | |
MD5:C4212656728008B20AC0EC60C42DC491 | SHA256:C188E4D4C34BDB99CF02FFD4DA75F0171697A9B75D5FD13ED65690C09B19DFAB | |||
| 4052 | malware.exe | C:\Users\admin\KRAB-DECRYPT.txt | binary | |
MD5:96E2807F5AAC20FFB171ACE14BC30A72 | SHA256:9E6F03AB44EE572DCA68480B8F28937922430CF00CFBEBC0B7CA283993613DF1 | |||
| 4052 | malware.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\KRAB-DECRYPT.txt | binary | |
MD5:96E2807F5AAC20FFB171ACE14BC30A72 | SHA256:9E6F03AB44EE572DCA68480B8F28937922430CF00CFBEBC0B7CA283993613DF1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
37
DNS requests
16
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4052 | malware.exe | GET | — | 15.188.254.247:80 | http://www.macartegrise.eu/ | FR | — | — | malicious |
4052 | malware.exe | GET | — | 107.178.223.183:80 | http://www.poketeg.com/ | US | — | — | malicious |
4052 | malware.exe | POST | — | 104.155.138.21:80 | http://www.poketeg.com/news/assets/dezumo.gif | US | — | — | malicious |
4052 | malware.exe | POST | — | 204.11.56.48:80 | http://www.billerimpex.com/uploads/tmp/dehemo.png | VG | — | — | whitelisted |
4052 | malware.exe | POST | 301 | 15.188.254.247:80 | http://www.macartegrise.eu/data/image/hekerufuhe.jpg | FR | — | — | malicious |
4052 | malware.exe | GET | 200 | 52.222.161.89:80 | http://s.ss2.us/r.crl | US | der | 486 b | whitelisted |
4052 | malware.exe | POST | — | 204.11.56.48:80 | http://www.billerimpex.com/uploads/tmp/dehemo.png | VG | — | — | whitelisted |
4052 | malware.exe | GET | 403 | 204.11.56.48:80 | http://www.billerimpex.com/ | VG | html | 272 b | whitelisted |
4052 | malware.exe | POST | — | 104.155.138.21:80 | http://perovaphoto.ru/data/image/esmeke.jpg | US | — | — | malicious |
4052 | malware.exe | GET | 200 | 108.156.0.231:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | binary | 2.02 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4052 | malware.exe | 204.11.56.48:80 | www.billerimpex.com | ULTRADDOS | VG | malicious |
4052 | malware.exe | 15.188.254.247:80 | www.macartegrise.eu | AMAZON-02 | FR | unknown |
3204 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4052 | malware.exe | 35.181.103.121:443 | www.macartegrise.eu | AMAZON-02 | FR | unknown |
4052 | malware.exe | 15.188.254.247:443 | www.macartegrise.eu | AMAZON-02 | FR | unknown |
4052 | malware.exe | 108.156.0.68:80 | o.ss2.us | AMAZON-02 | US | unknown |
4052 | malware.exe | 8.253.95.121:80 | ctldl.windowsupdate.com | LEVEL3 | US | suspicious |
4052 | malware.exe | 52.222.161.89:80 | s.ss2.us | AMAZON-02 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.billerimpex.com |
| whitelisted |
www.macartegrise.eu |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
o.ss2.us |
| whitelisted |
s.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
crl.rootca1.amazontrust.com |
| whitelisted |
ocsp.r2m01.amazontrust.com |
| whitelisted |
crl.r2m01.amazontrust.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4052 | malware.exe | Malware Command and Control Activity Detected | ET MALWARE [eSentire] Win32/GandCrab v4/5 Ransomware CnC Activity |
4052 | malware.exe | Malware Command and Control Activity Detected | ET MALWARE [eSentire] Win32/GandCrab v4/5 Ransomware CnC Activity |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\plugins\Config\nppPluginList.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|