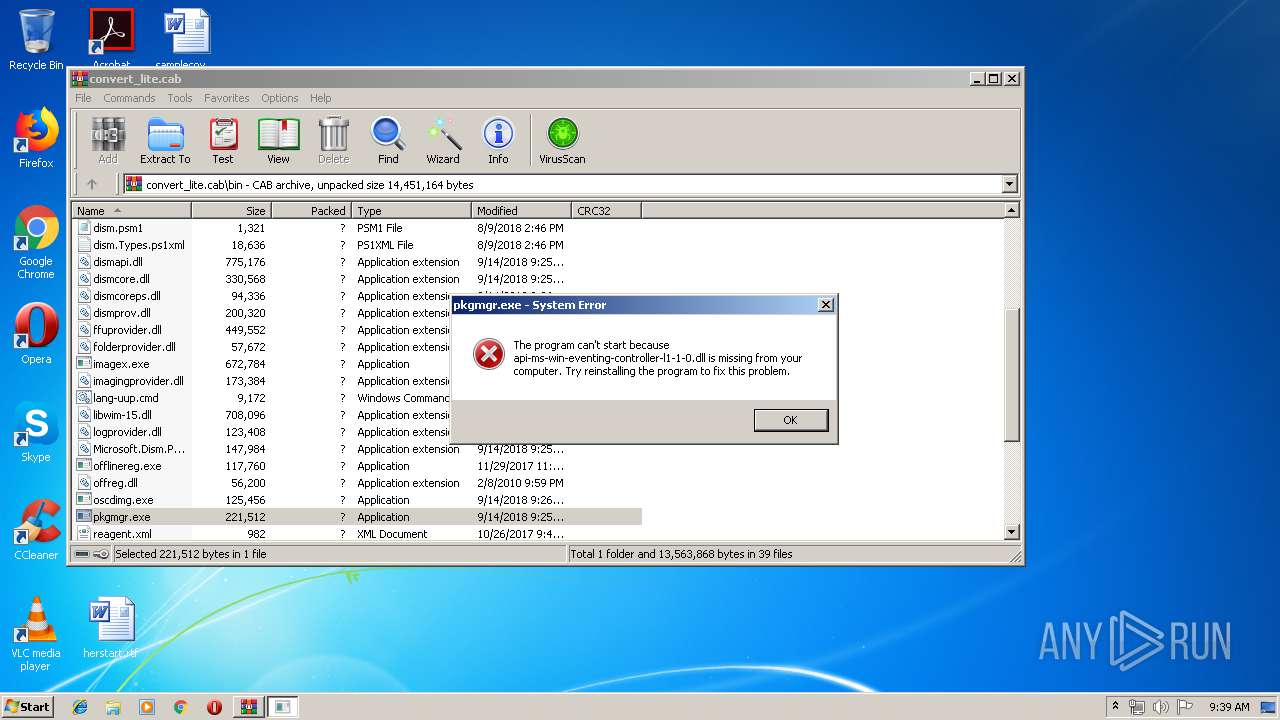
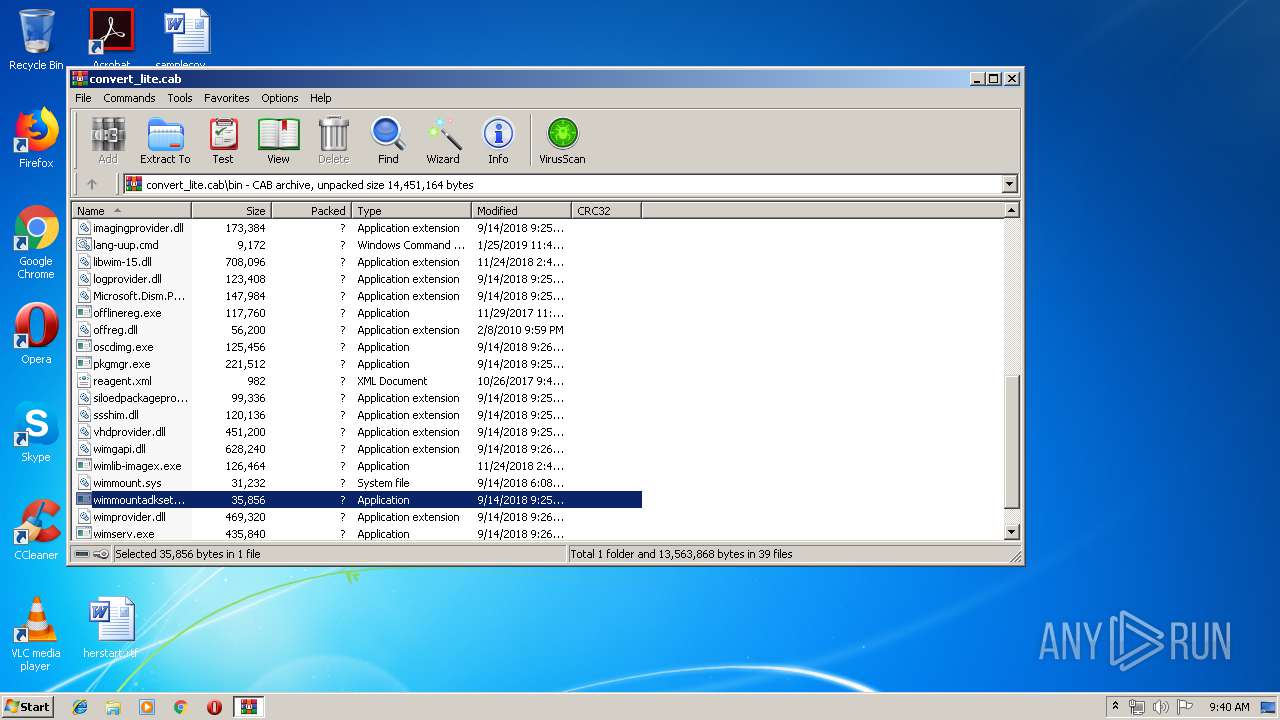
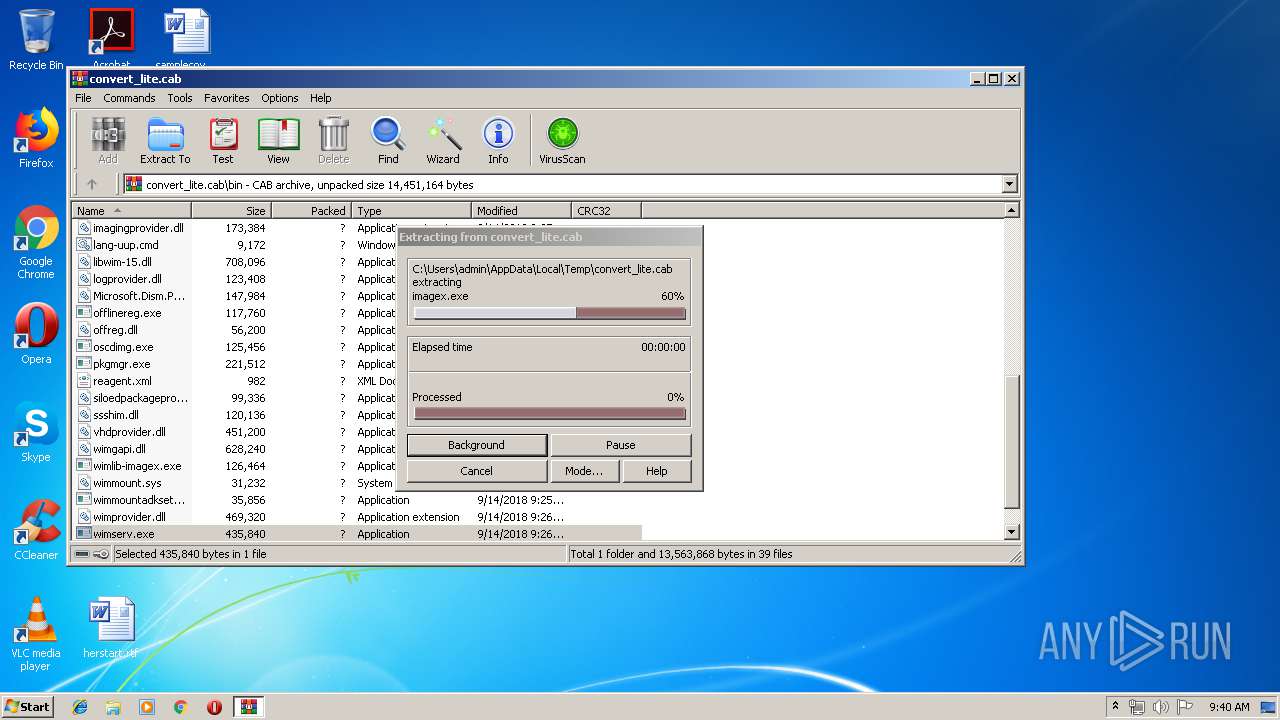
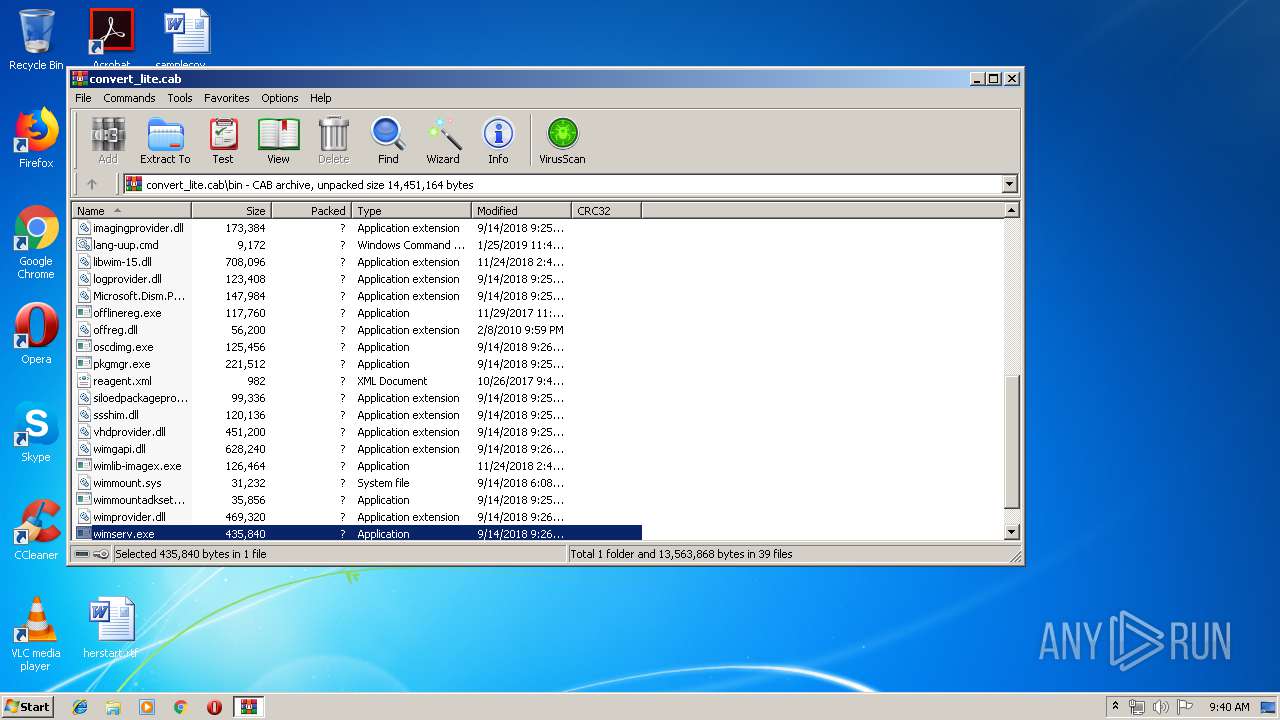
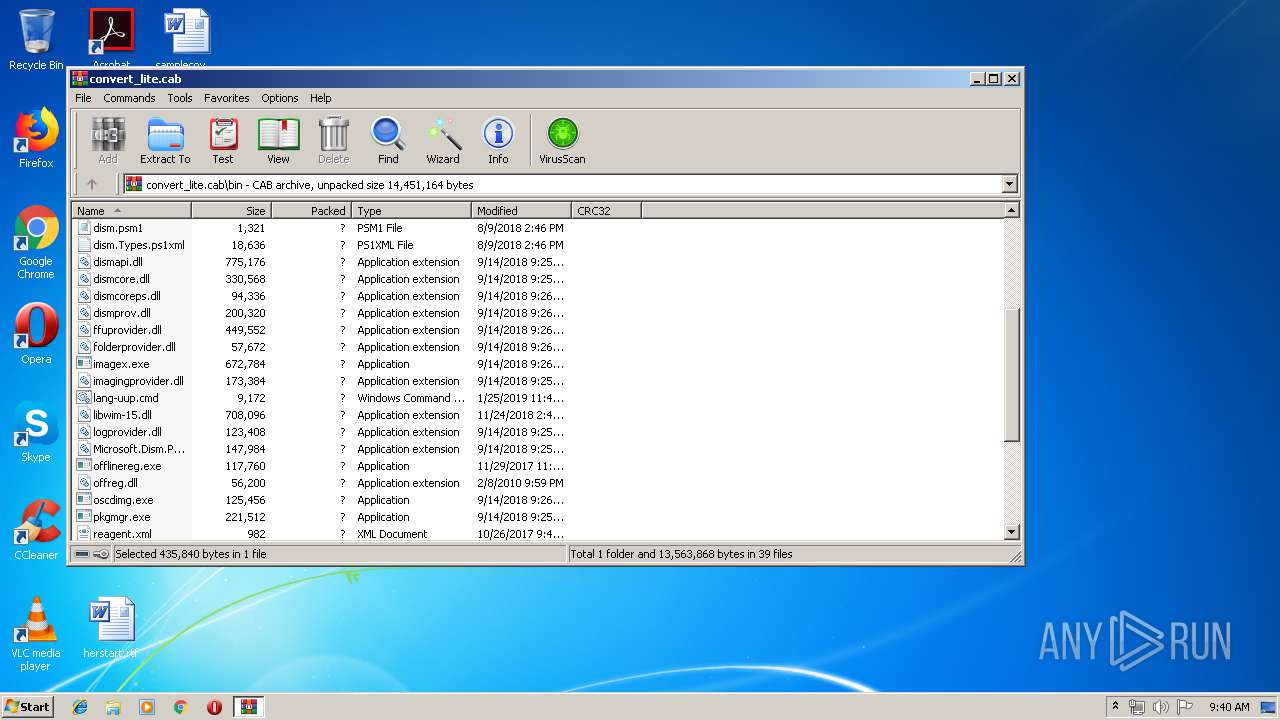
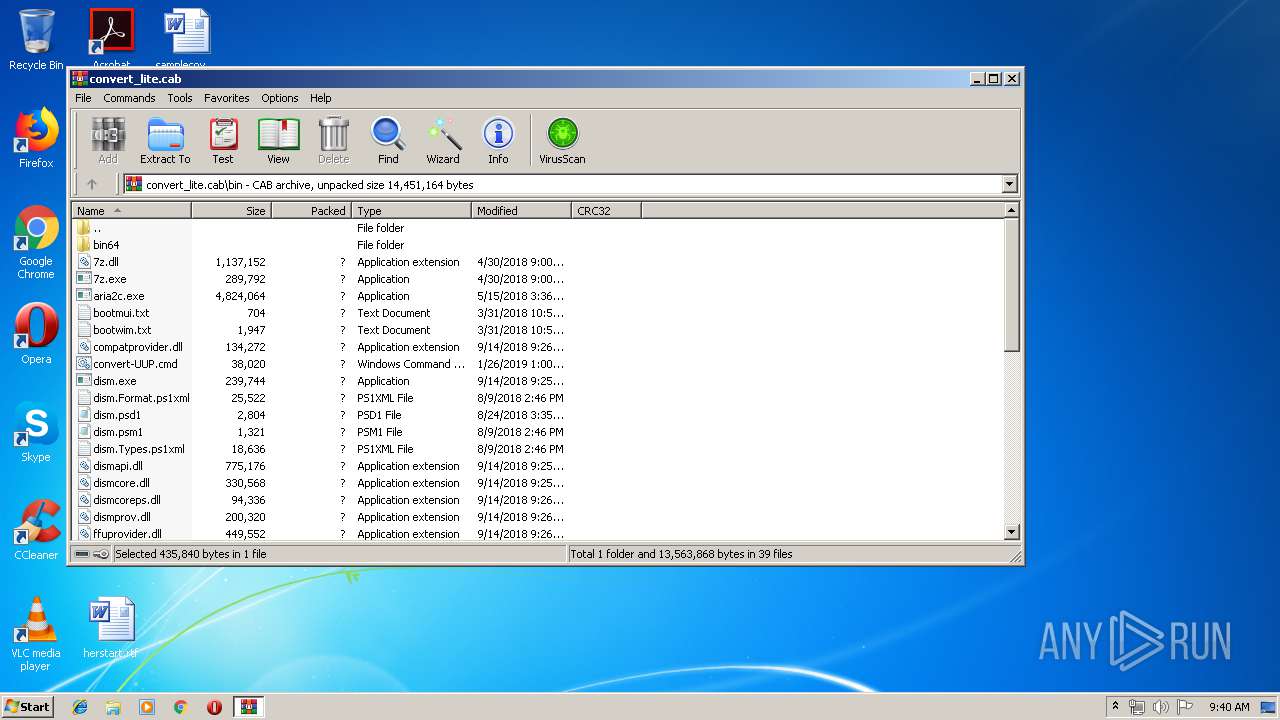
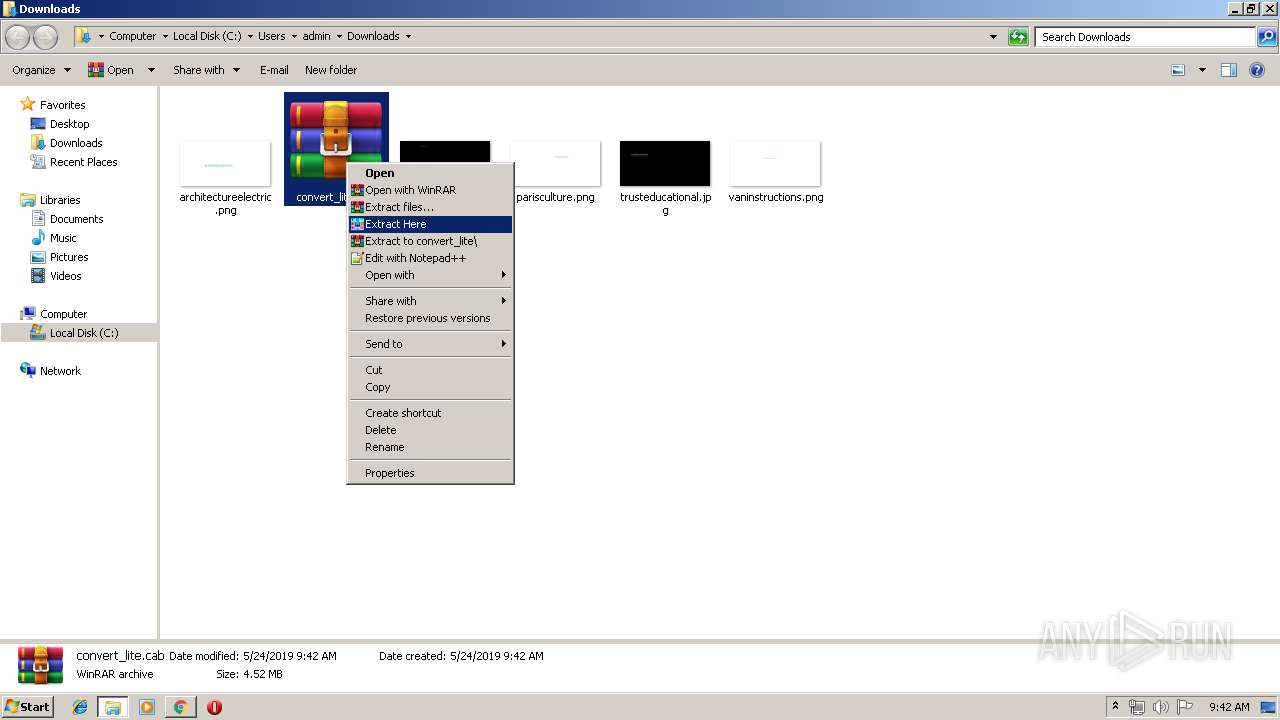
| download: | convert_lite.cab |
| Full analysis: | https://app.any.run/tasks/53c86dbf-f9d8-4492-bd02-63140a1253e8 |
| Verdict: | Malicious activity |
| Analysis date: | May 24, 2019, 08:38:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-cab-compressed |
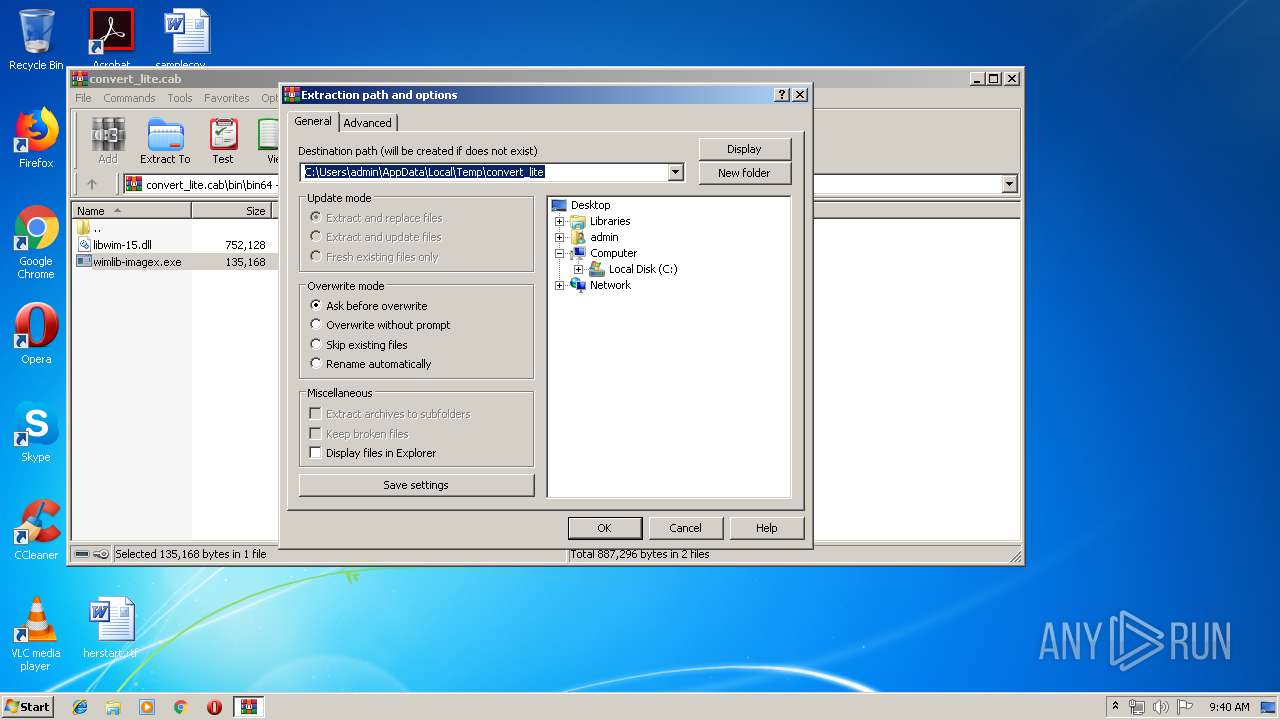
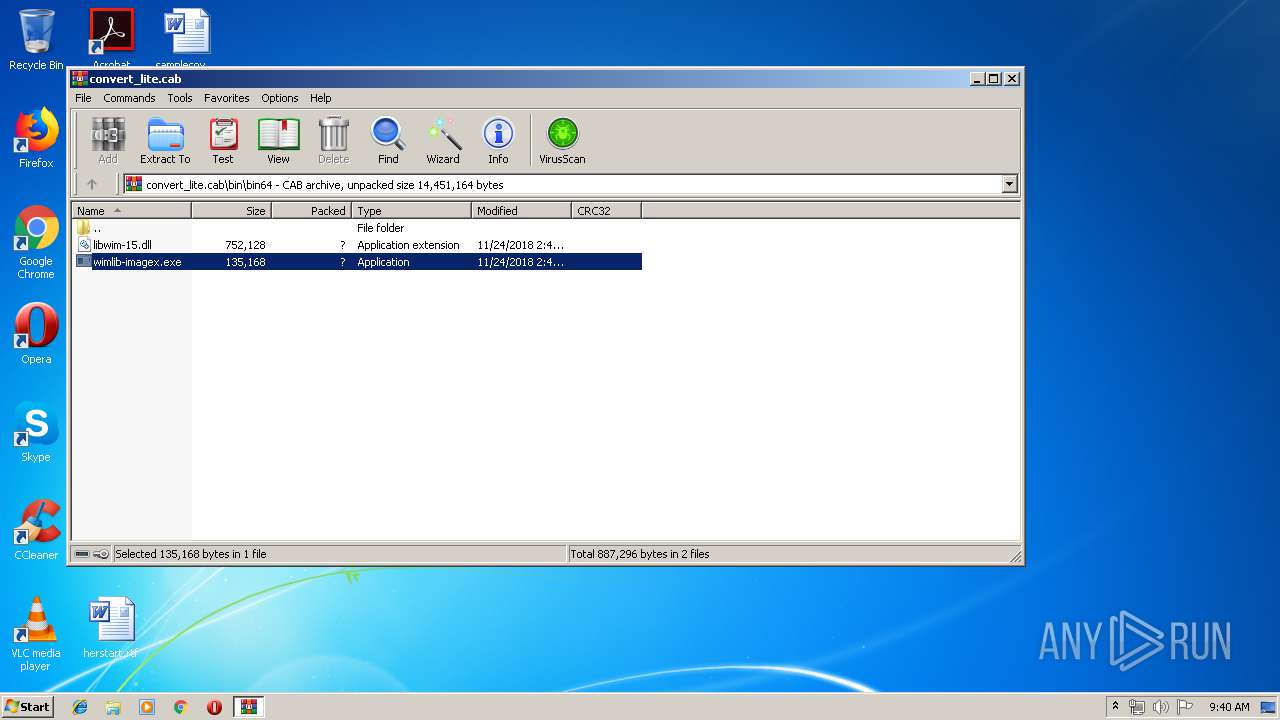
| File info: | Microsoft Cabinet archive data, 4746424 bytes, 41 files |
| MD5: | 6665F15BF8841CAFFE4CF1C8349AE4FA |
| SHA1: | E7C4FEB463148AAE7F8D0CF5582B99C08A9E5030 |
| SHA256: | B52F48FFF0AE1B41BA2B2C5AC7E0C6851830B983AD48E1A9A0E296B6853869F1 |
| SSDEEP: | 98304:wJuzOnftmiaF/CoyTj/0lR4+HNV4zFYxDJyE1rPcnwa5s6wN3gNDFo:wZftm3m/0jfTnDJyEFcl5nwgXo |
MALICIOUS
Application was dropped or rewritten from another process
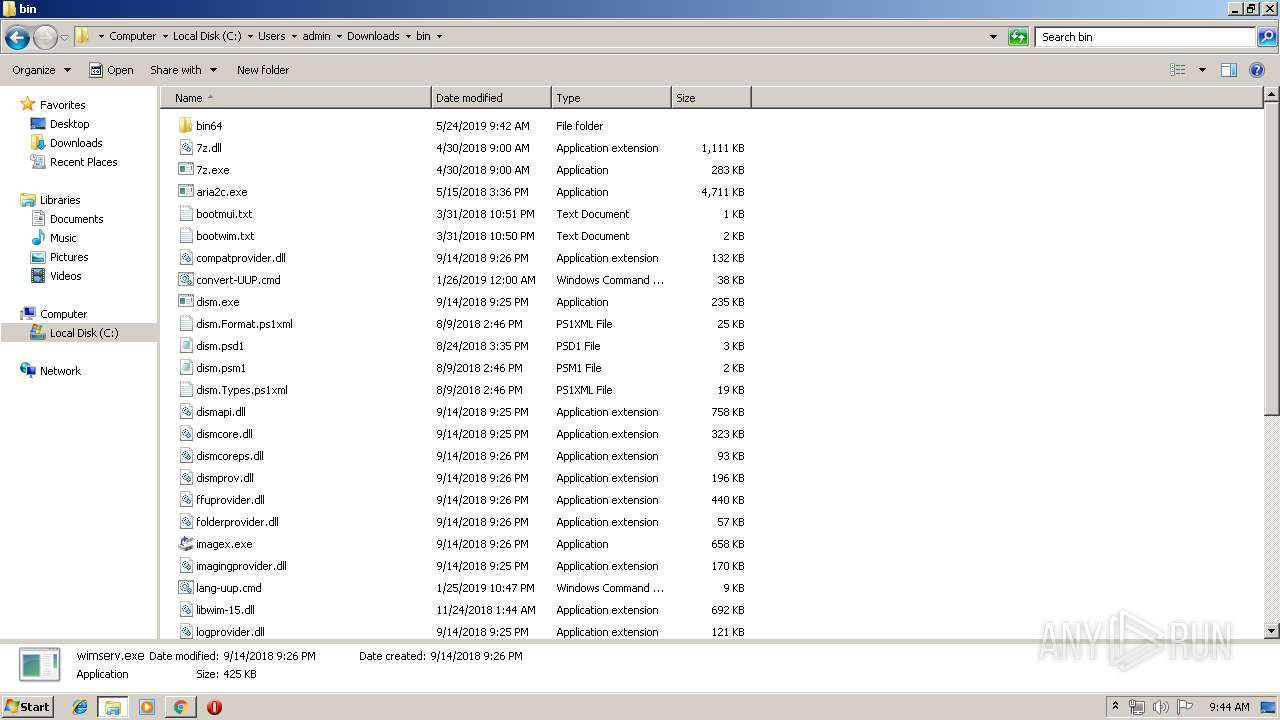
- aria2c.exe (PID: 3016)
- imagex.exe (PID: 2292)
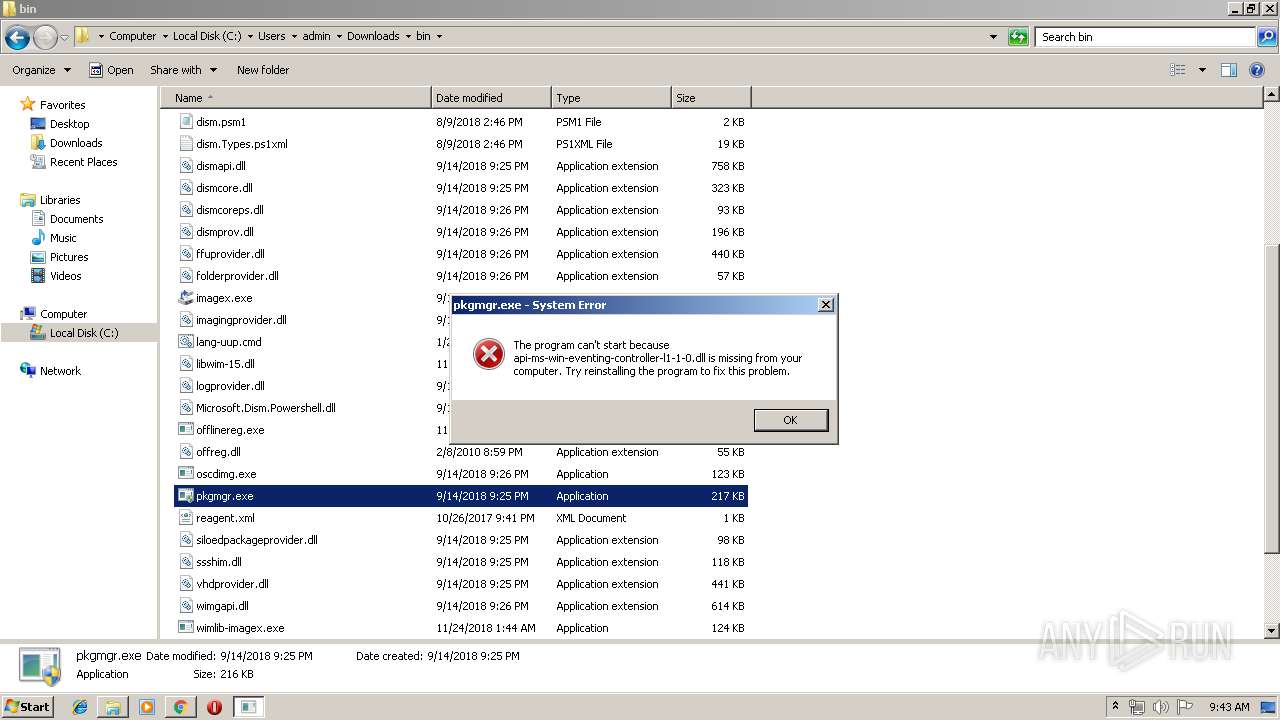
- pkgmgr.exe (PID: 2680)
- dism.exe (PID: 2236)
- 7z.exe (PID: 3556)
- oscdimg.exe (PID: 300)
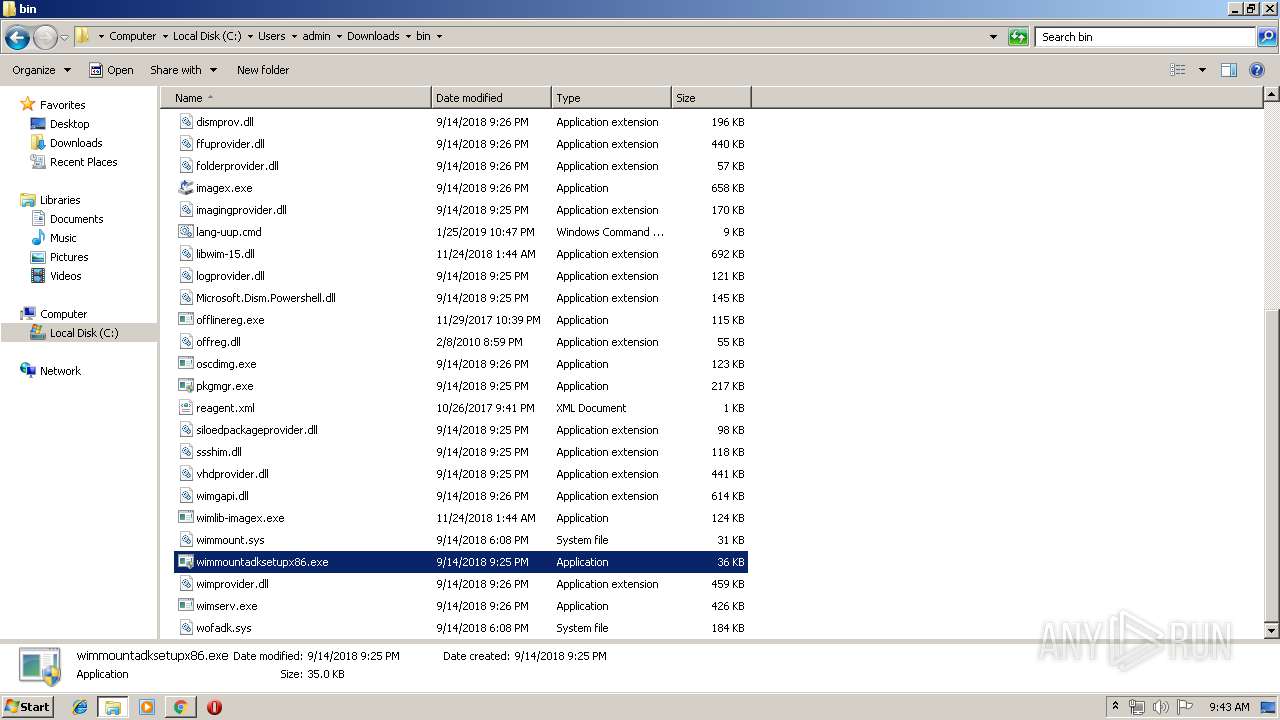
- wimmountadksetupx86.exe (PID: 636)
- offlinereg.exe (PID: 3400)
- wimlib-imagex.exe (PID: 1260)
- pkgmgr.exe (PID: 2168)
- wimserv.exe (PID: 2632)
- wimmountadksetupx86.exe (PID: 2148)
- 7z.exe (PID: 1824)
- 7z.exe (PID: 1920)
- dism.exe (PID: 1888)
- offlinereg.exe (PID: 2704)
- dism.exe (PID: 2600)
- oscdimg.exe (PID: 3896)
- pkgmgr.exe (PID: 3224)
- wimlib-imagex.exe (PID: 3428)
- pkgmgr.exe (PID: 2468)
- wimmountadksetupx86.exe (PID: 1520)
- wimmountadksetupx86.exe (PID: 3724)
- wimserv.exe (PID: 2236)
- aria2c.exe (PID: 3332)
- aria2c.exe (PID: 2300)
- imagex.exe (PID: 1496)
Loads dropped or rewritten executable
- dism.exe (PID: 2236)
- wimlib-imagex.exe (PID: 1260)
- SearchProtocolHost.exe (PID: 1704)
- dism.exe (PID: 1888)
- dism.exe (PID: 2600)
- wimlib-imagex.exe (PID: 3428)
- explorer.exe (PID: 2044)
SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 1004)
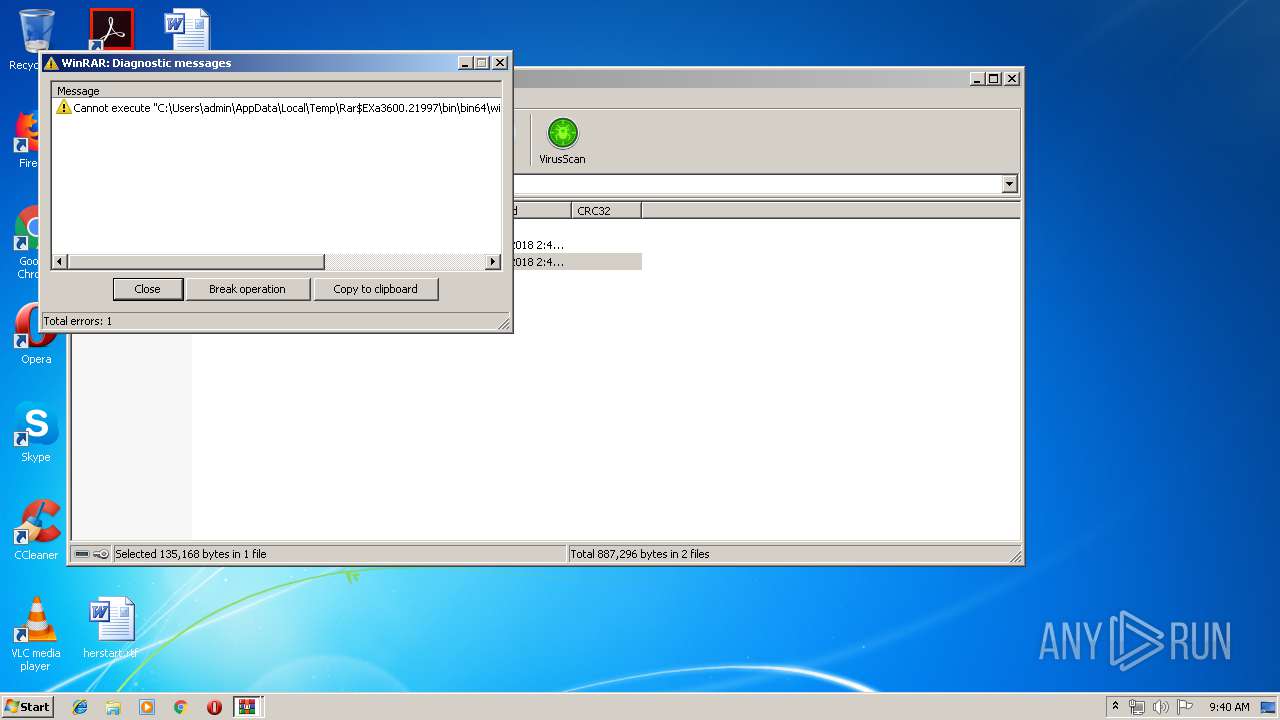
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2748)
- WinRAR.exe (PID: 3600)
INFO
Application launched itself
- chrome.exe (PID: 1004)
Reads Internet Cache Settings
- chrome.exe (PID: 1004)
Manual execution by user
- chrome.exe (PID: 1004)
- WinRAR.exe (PID: 2748)
- 7z.exe (PID: 1824)
- dism.exe (PID: 2600)
- aria2c.exe (PID: 2300)
- dism.exe (PID: 1888)
- aria2c.exe (PID: 3332)
- 7z.exe (PID: 1920)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .cab | | | Microsoft Cabinet Archive (100) |
|---|
Total processes
131
Monitored processes
61
Malicious processes
9
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=972,1103087453622406580,15721761924195644747,131072 --enable-features=PasswordImport --service-pipe-token=8014625435041075771 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8014625435041075771 --renderer-client-id=3 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1872 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 300 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3600.19463\bin\oscdimg.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3600.19463\bin\oscdimg.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft CD/DVD Premastering Utility Exit code: 1 Version: 2.56 Modules
| |||||||||||||||
| 636 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3600.20391\bin\wimmountadksetupx86.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3600.20391\bin\wimmountadksetupx86.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WimMount setup Exit code: 87 Version: 10.0.17763.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1004 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1048 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=972,1103087453622406580,15721761924195644747,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=15129211275144390490 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=15129211275144390490 --renderer-client-id=8 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2480 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1212 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=972,1103087453622406580,15721761924195644747,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=9303306243186981320 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9303306243186981320 --renderer-client-id=24 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3896 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1256 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=972,1103087453622406580,15721761924195644747,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=727631989464877983 --mojo-platform-channel-handle=4532 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1260 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3600.20238\bin\wimlib-imagex.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3600.20238\bin\wimlib-imagex.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 2 Modules
| |||||||||||||||
| 1356 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=972,1103087453622406580,15721761924195644747,131072 --enable-features=PasswordImport --service-pipe-token=3453943213151318990 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=3453943213151318990 --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1992 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1456 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=972,1103087453622406580,15721761924195644747,131072 --enable-features=PasswordImport --service-pipe-token=16003947335206362236 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=16003947335206362236 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2128 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
Total events
4 078
Read events
3 371
Write events
702
Delete events
5
Modification events
| (PID) Process: | (3600) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3600) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3600) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3600) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\convert_lite.cab | |||
| (PID) Process: | (3600) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3600) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3600) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3600) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2044) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.cab\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
| (PID) Process: | (2044) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.cab\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
Executable files
385
Suspicious files
49
Text files
322
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3600 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3600.16970\bin\bootmui.txt | text | |
MD5:— | SHA256:— | |||
| 3600 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3600.16970\bin\convert-UUP.cmd | text | |
MD5:— | SHA256:— | |||
| 3600 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3600.16970\bin\bootwim.txt | text | |
MD5:— | SHA256:— | |||
| 3600 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3600.16970\bin\dism.exe | executable | |
MD5:— | SHA256:— | |||
| 3600 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3600.16970\bin\imagex.exe | executable | |
MD5:— | SHA256:— | |||
| 3600 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3600.16970\bin\aria2c.exe | executable | |
MD5:3885ADC6619A8257C8B42DFA7349CE11 | SHA256:3EB8712B0DB6BA466F8AFE1BF606983FE8341C941BDFCADC07068288C7CA5A9C | |||
| 3600 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3600.16970\bin\7z.dll | executable | |
MD5:04E4F293970589EAD1DC19FC8BE60C92 | SHA256:6CD22F513CE36B4727BB6C353C58182C7CC8A14CBE3EEFDCA85C2A25906A0077 | |||
| 3600 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3600.16970\bin\dism.Format.ps1xml | text | |
MD5:22E53D0E44212AFFE536AD0C658953CC | SHA256:0476E8C703EC695CC4CDBA62D795A546DB567ADA3C916AEFB7473937D1E6C256 | |||
| 3600 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3600.16970\bin\7z.exe | executable | |
MD5:77E556CDFDC5C592F5C46DB4127C6F4C | SHA256:034ECA579F68B44F8F41294D8C9DAC96F032C57DEE0877095DA47913060DFF84 | |||
| 3600 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3600.16970\bin\dismcoreps.dll | executable | |
MD5:8BDA6E3379AB78A80B78C89E47113A48 | SHA256:FF71A1E0C8553ED8D28F7B2FD25BF1035892737878D7C6928D39469238FF25C4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
26
DNS requests
28
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1004 | chrome.exe | GET | 302 | 216.58.207.46:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 506 b | whitelisted |
1004 | chrome.exe | GET | 200 | 209.85.226.6:80 | http://r1---sn-5hnekn76.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=185.104.185.243&mm=28&mn=sn-5hnekn76&ms=nvh&mt=1558687188&mv=m&pl=24&shardbypass=yes | US | crx | 842 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1004 | chrome.exe | 216.58.207.67:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
1004 | chrome.exe | 172.217.16.206:443 | clients1.google.com | Google Inc. | US | whitelisted |
1004 | chrome.exe | 216.58.208.35:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
1004 | chrome.exe | 172.217.16.142:443 | apis.google.com | Google Inc. | US | whitelisted |
1004 | chrome.exe | 216.58.207.74:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
1004 | chrome.exe | 172.217.22.109:443 | accounts.google.com | Google Inc. | US | whitelisted |
— | — | 216.58.207.46:80 | redirector.gvt1.com | Google Inc. | US | whitelisted |
— | — | 216.58.207.33:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
1004 | chrome.exe | 216.58.207.35:443 | www.google.com.ua | Google Inc. | US | whitelisted |
1004 | chrome.exe | 8.8.8.8:53 | — | Google Inc. | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
www.google.com.ua |
| whitelisted |
accounts.google.com |
| shared |
clients1.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
www.google.com |
| malicious |
www.google.fr |
| whitelisted |
fonts.googleapis.com |
| whitelisted |