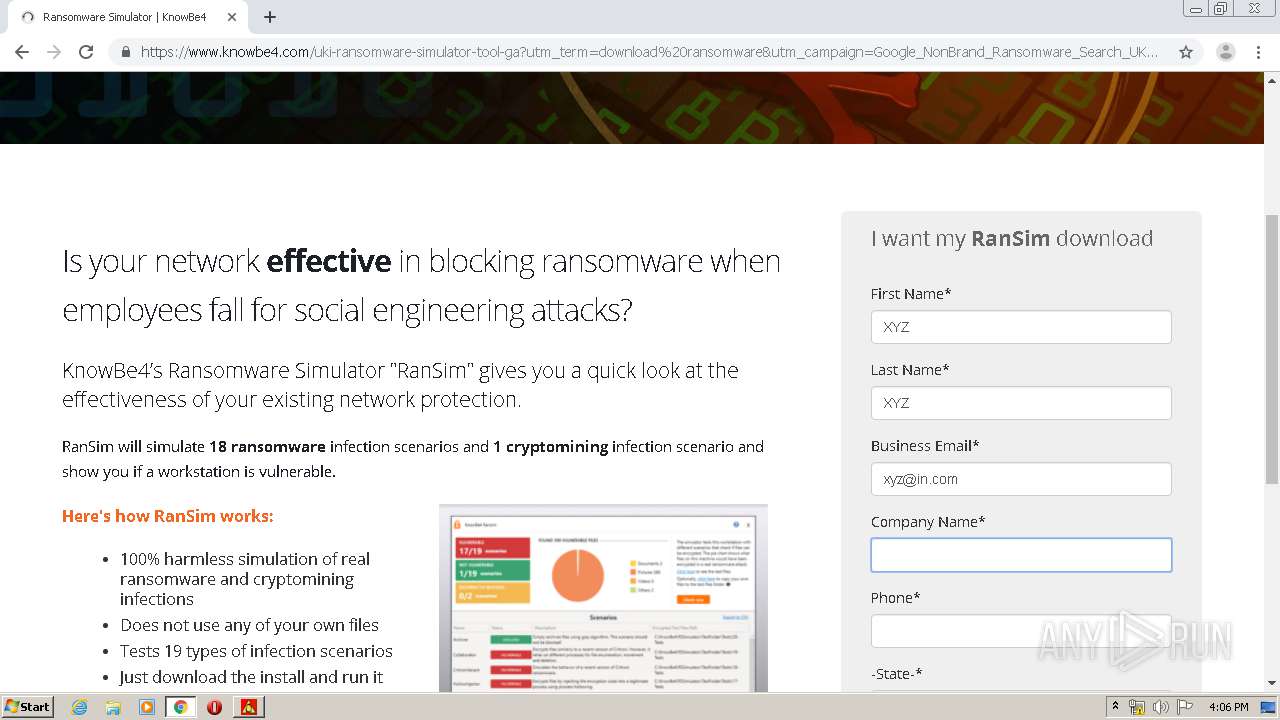
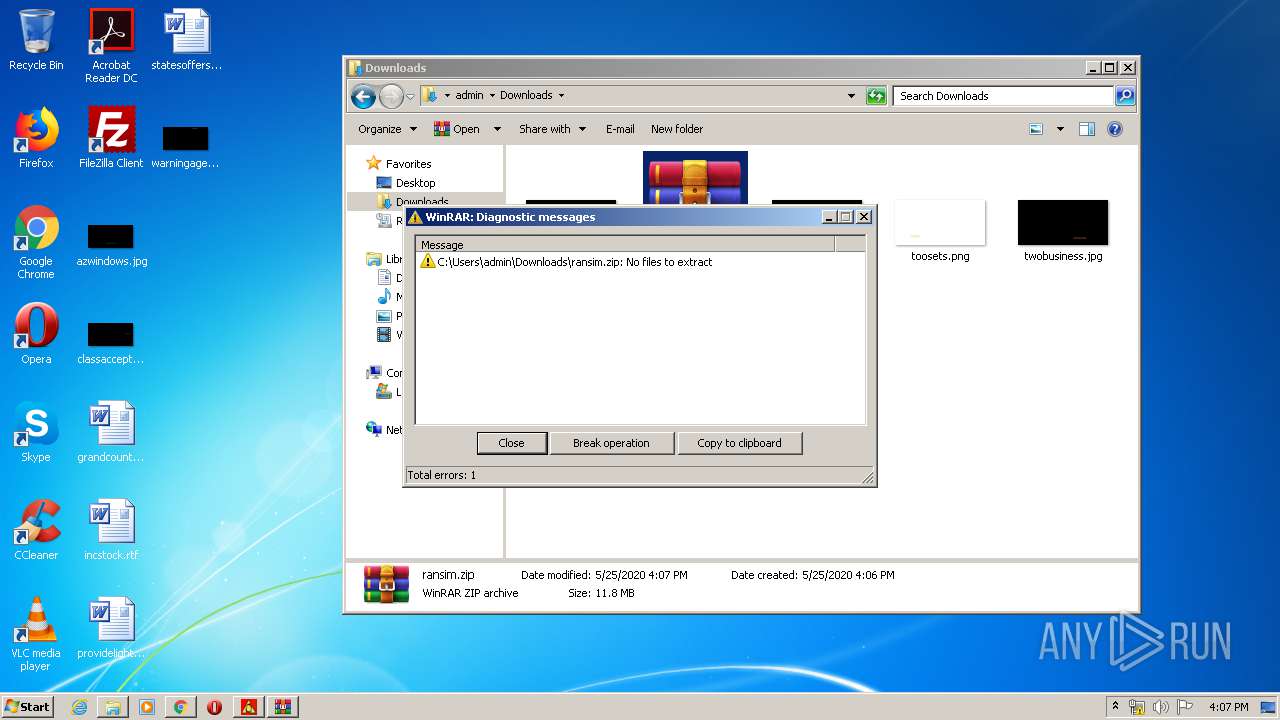
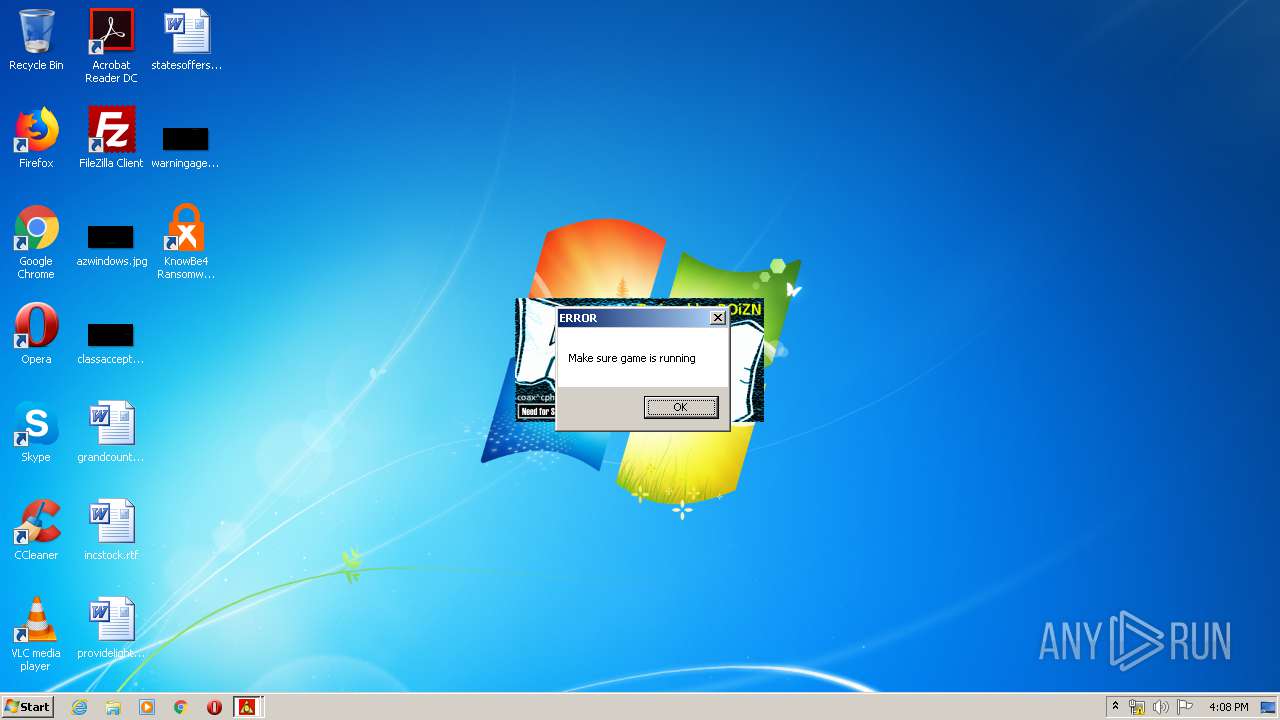
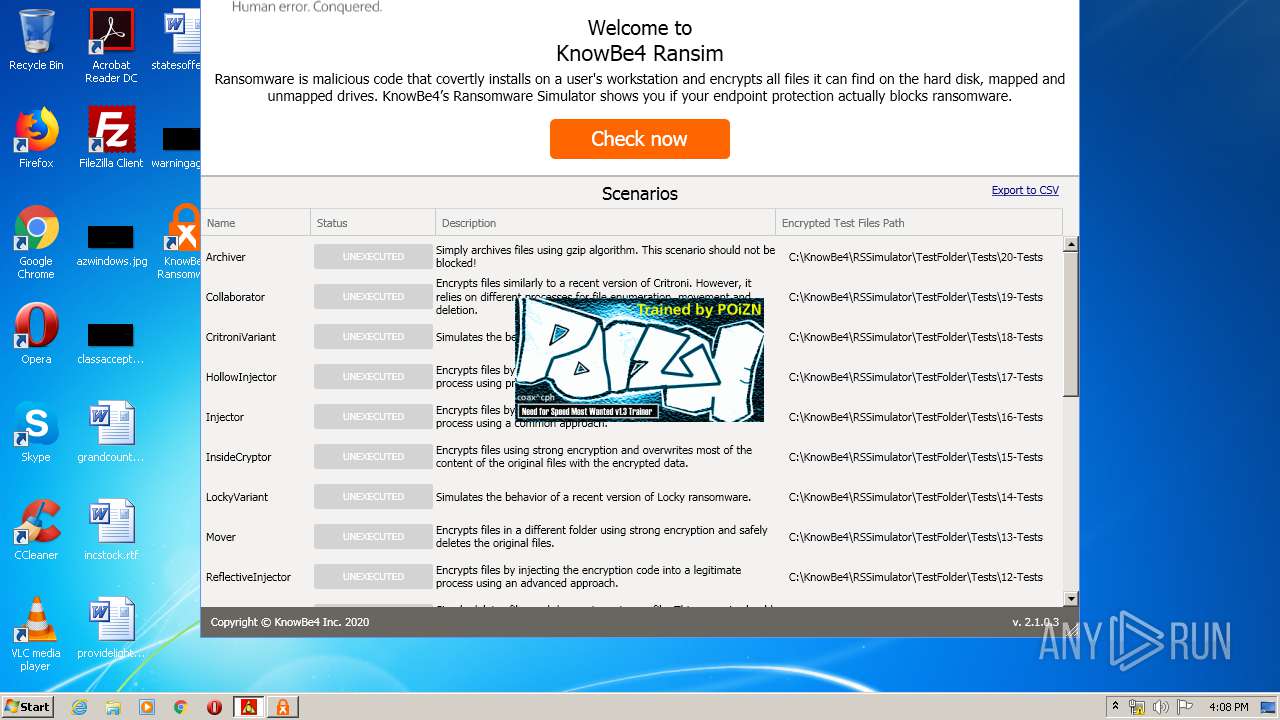
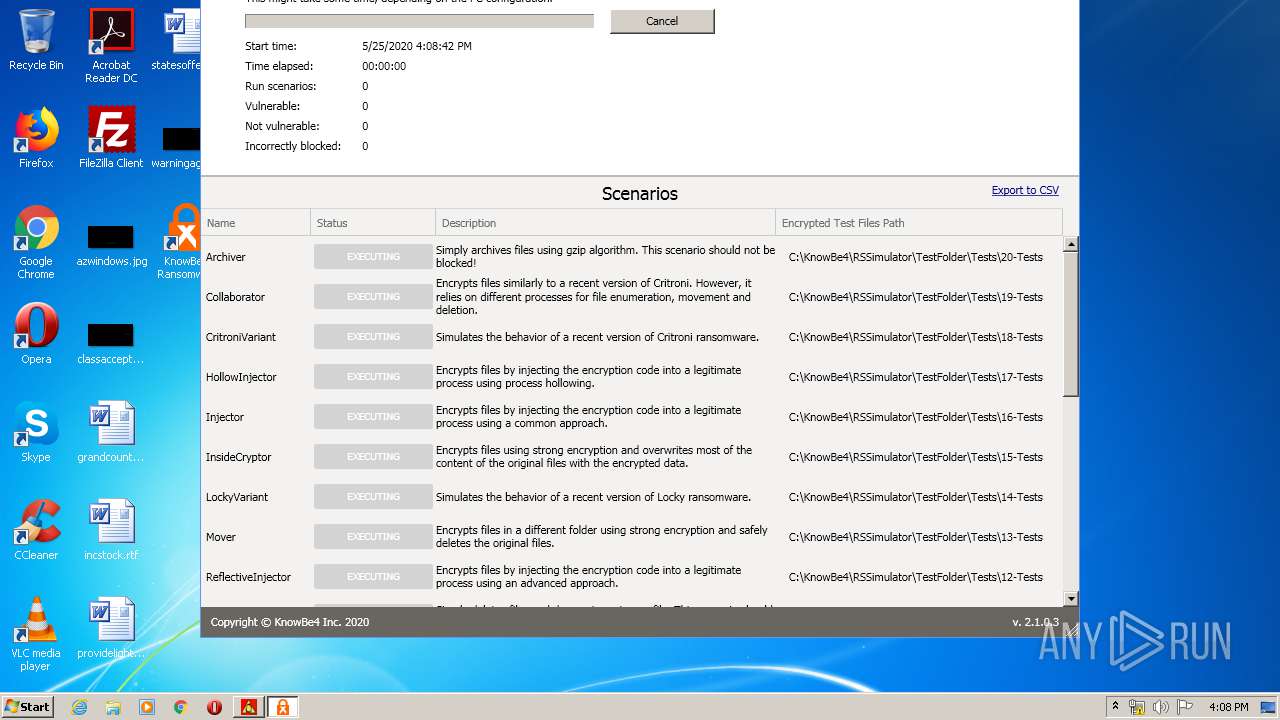
| File name: | pzn-nfst.exe |
| Full analysis: | https://app.any.run/tasks/edb9a737-212c-4bd7-b9c8-62841e3ba69b |
| Verdict: | Malicious activity |
| Analysis date: | May 25, 2020, 15:03:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | MS-DOS executable, MZ for MS-DOS |
| MD5: | 9B5C55CD0BB53A42B6E333A52A7C552D |
| SHA1: | B52CB332631B449DE46CF49A0A1BBC6743828B7F |
| SHA256: | B5296CF0EB22FBA6E2F68D0C9DE9EF7845F330F7C611A0D60007AA87E270C62A |
| SSDEEP: | 768:9qdwGP49jpGjStTWNFTL4eUOQtTMZSivMo/W:QOGA9DtqvTPmMZSgO |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1987:09:11 03:35:02+02:00 |
| PEType: | PE32 |
| LinkerVersion: | - |
| CodeSize: | 5120 |
| InitializedDataSize: | 101376 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2445e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 11-Sep-1987 01:35:02 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0x4550 |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x014C |
| Checksum: | 0x0002 |
| Initial IP value: | 0x5346 |
| Initial CS value: | 0x2147 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x010B |
| OEM information: | 0x0000 |
| Address of NE header: | 0x0000000C |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 2 |
| Time date stamp: | 11-Sep-1987 01:35:02 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
0x0001D000 | 0x00008000 | 0x00007557 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.8746 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 3.90062 | 2216 | UNKNOWN | English - United States | RT_ICON |
500 | 1.91924 | 20 | UNKNOWN | English - United States | RT_GROUP_ICON |
Imports
KERNEL32.dll |
Total processes
34
Monitored processes
1
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
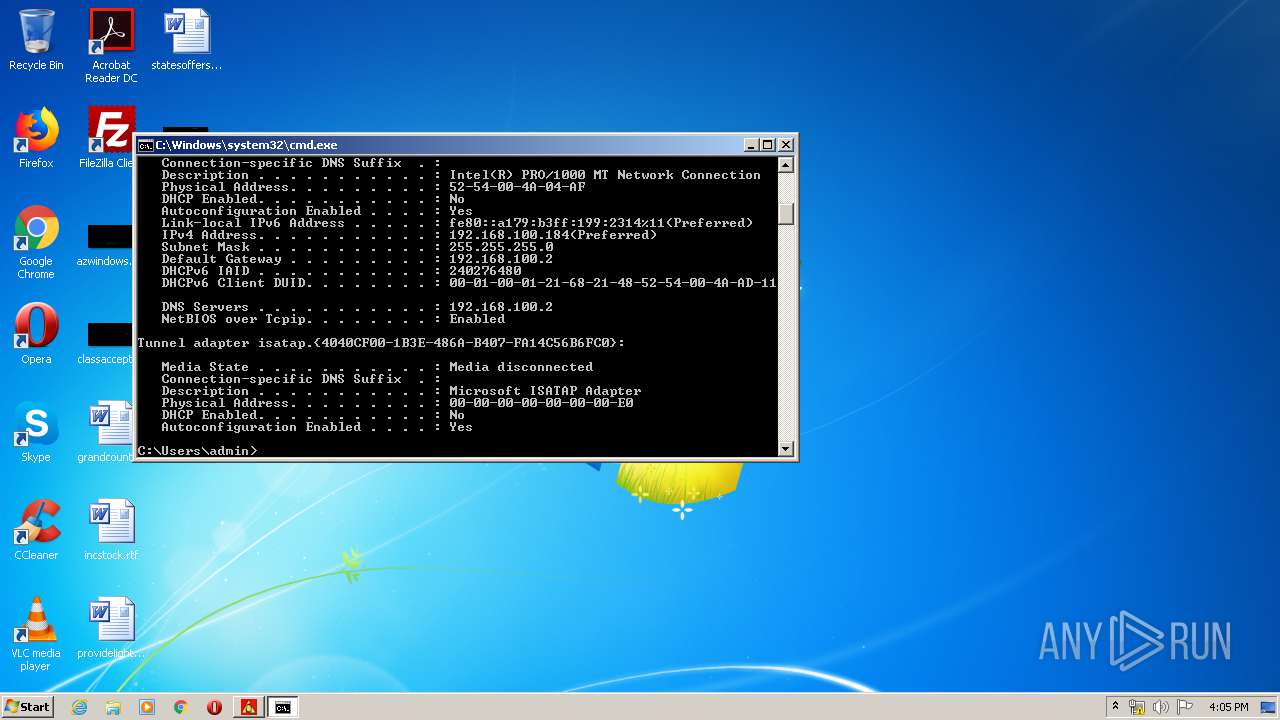
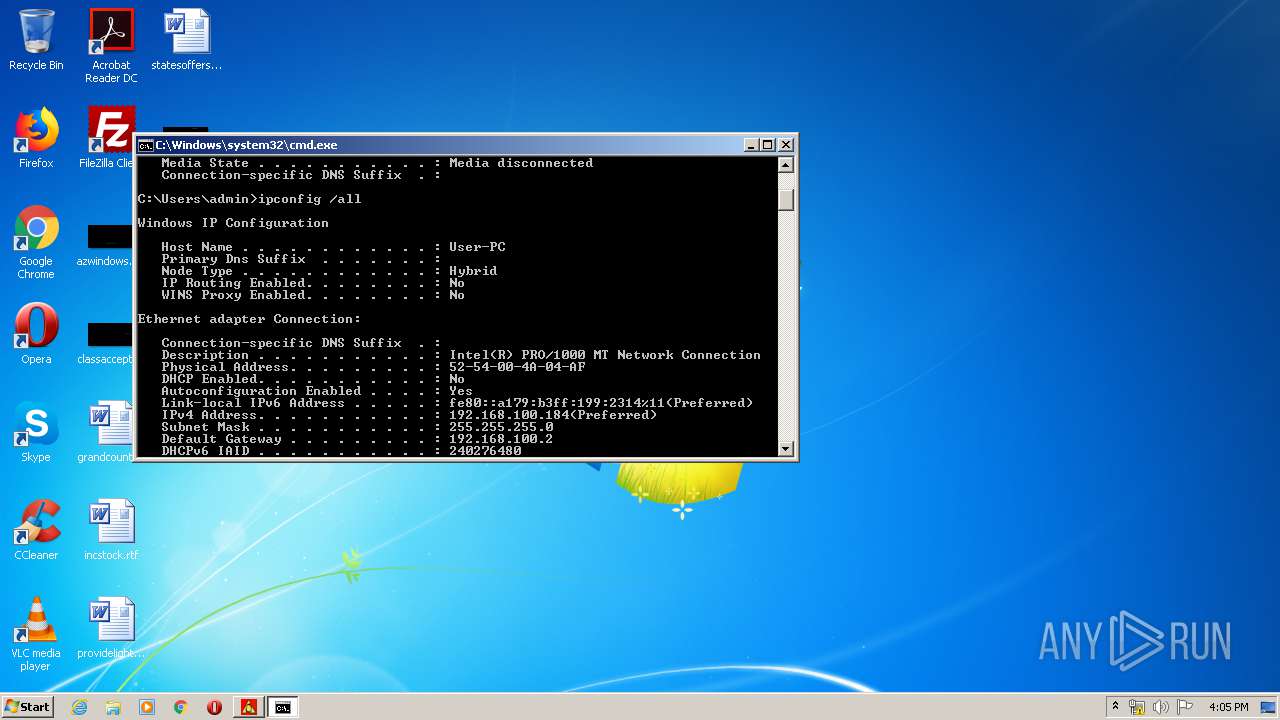
| 2572 | "C:\Users\admin\AppData\Local\Temp\pzn-nfst.exe" | C:\Users\admin\AppData\Local\Temp\pzn-nfst.exe | — | explorer.exe |
User: admin Integrity Level: MEDIUM Exit code: 0 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
127
DNS requests
103
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 173.194.5.185:80 | http://r3---sn-aigl6n7z.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjY5QUFXTEQwc2RPVXhRY3picjhxblh1dw/7619.603.0.2_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mh=Qx&mip=185.217.117.55&mm=28&mn=sn-aigl6n7z&ms=nvh&mt=1590419053&mv=m&mvi=2&pl=25&shardbypass=yes | US | crx | 816 Kb | whitelisted |
— | — | GET | 302 | 172.217.21.238:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjY5QUFXTEQwc2RPVXhRY3picjhxblh1dw/7619.603.0.2_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 525 b | whitelisted |
— | — | GET | 200 | 173.194.183.73:80 | http://r4---sn-aigl6ned.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx?cms_redirect=yes&mh=QJ&mip=185.217.117.55&mm=28&mn=sn-aigl6ned&ms=nvh&mt=1590419053&mv=m&mvi=3&pl=25&shardbypass=yes | US | crx | 293 Kb | whitelisted |
— | — | GET | 302 | 172.217.21.238:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 520 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 172.217.16.195:443 | www.google.com.ua | Google Inc. | US | whitelisted |
— | — | 172.217.16.138:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
— | — | 172.217.22.99:443 | www.gstatic.com | Google Inc. | US | whitelisted |
— | — | 216.58.212.174:443 | apis.google.com | Google Inc. | US | whitelisted |
— | — | 172.217.22.110:443 | ogs.google.com.ua | Google Inc. | US | whitelisted |
— | — | 216.58.207.35:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
— | — | 216.58.212.164:443 | www.google.com | Google Inc. | US | whitelisted |
— | — | 172.217.22.67:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
— | — | 172.217.23.174:443 | clients2.google.com | Google Inc. | US | whitelisted |
— | — | 173.194.183.73:80 | r4---sn-aigl6ned.gvt1.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com.ua |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
ogs.google.com.ua |
| whitelisted |
www.google.com |
| malicious |
www.google.co.uk |
| whitelisted |