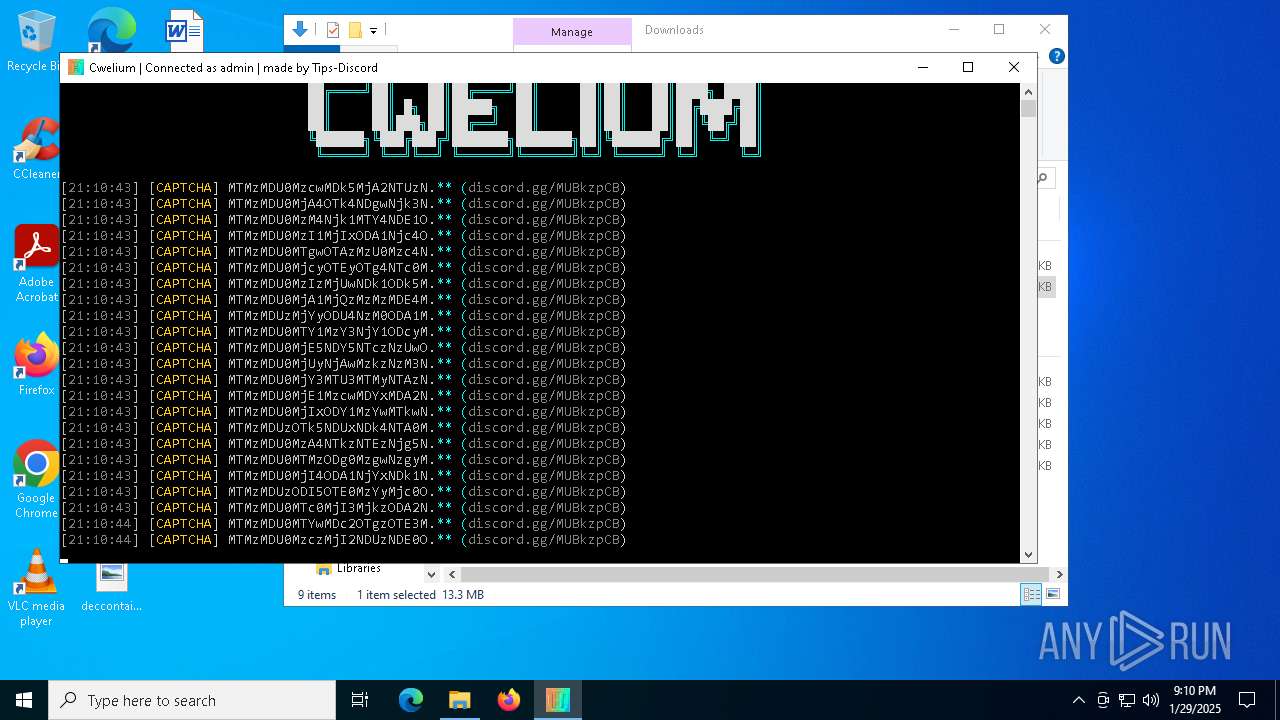
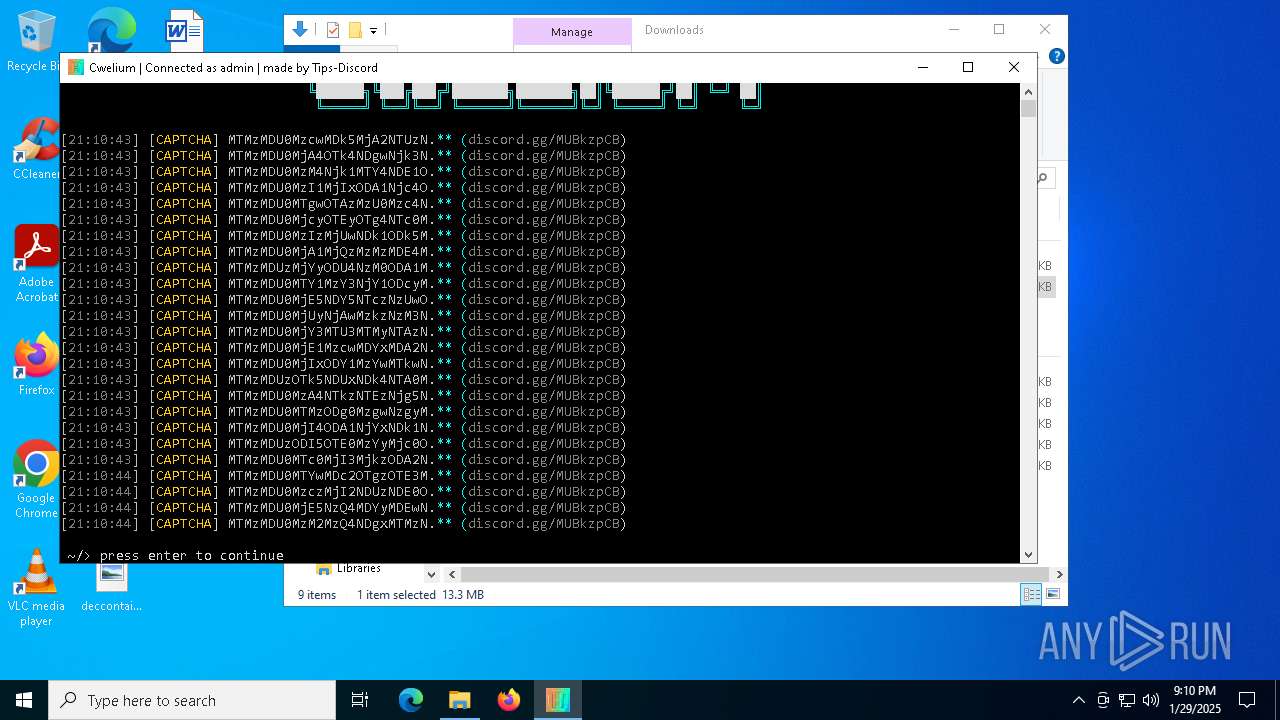
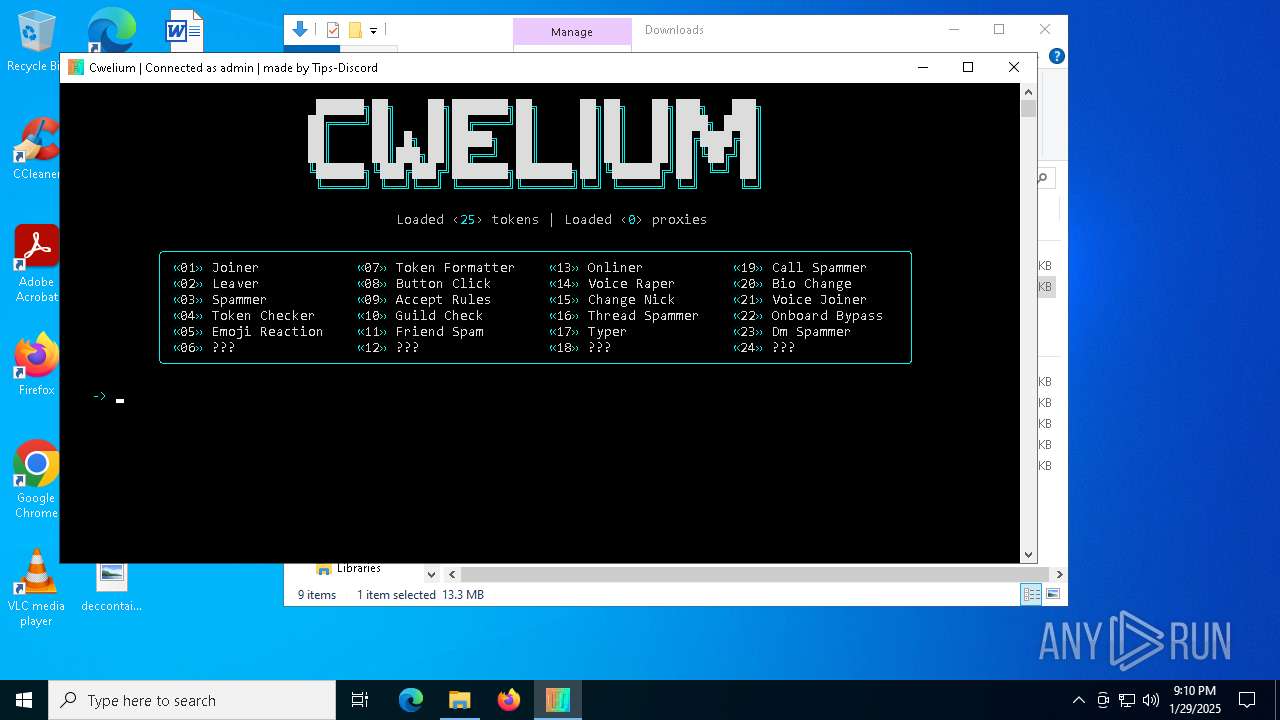
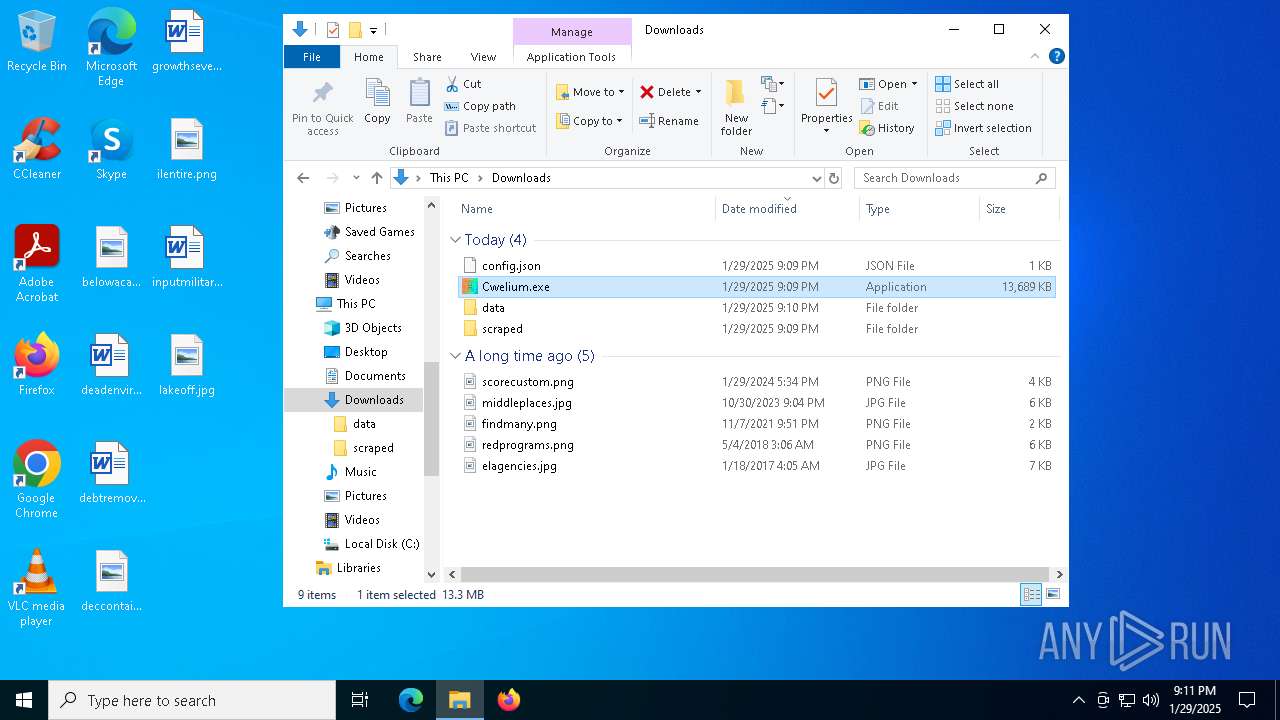
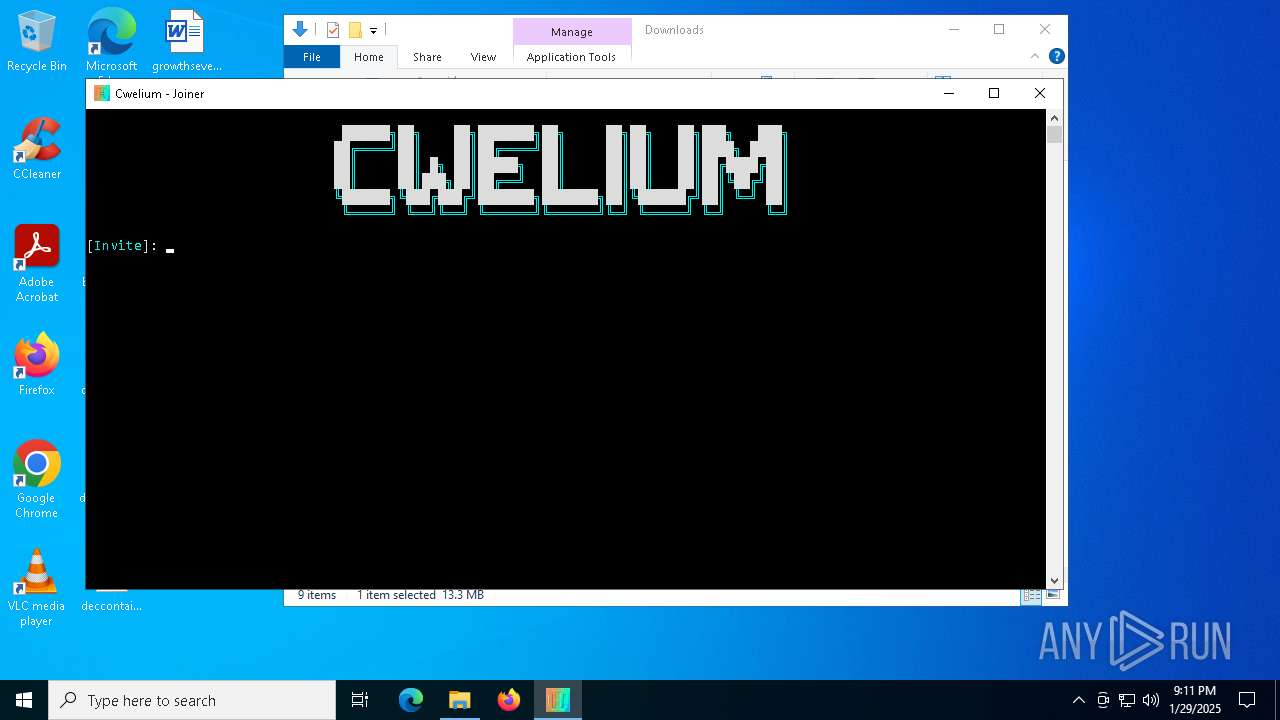
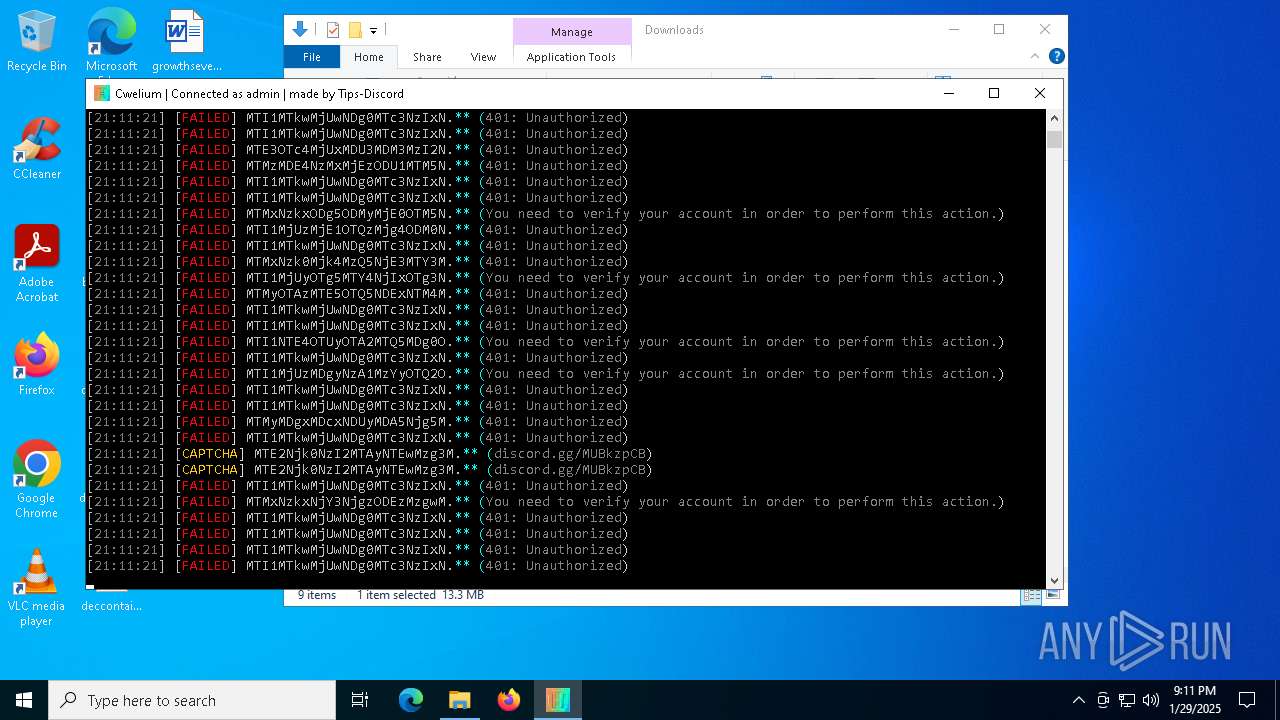
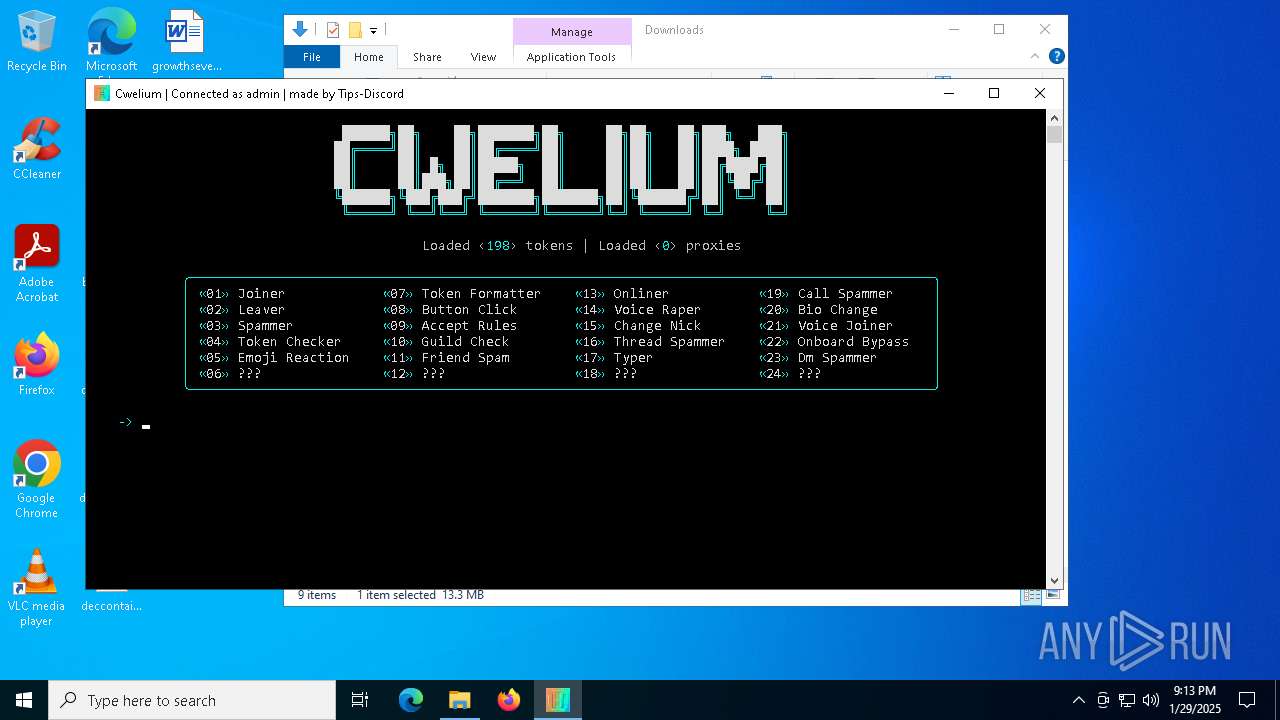
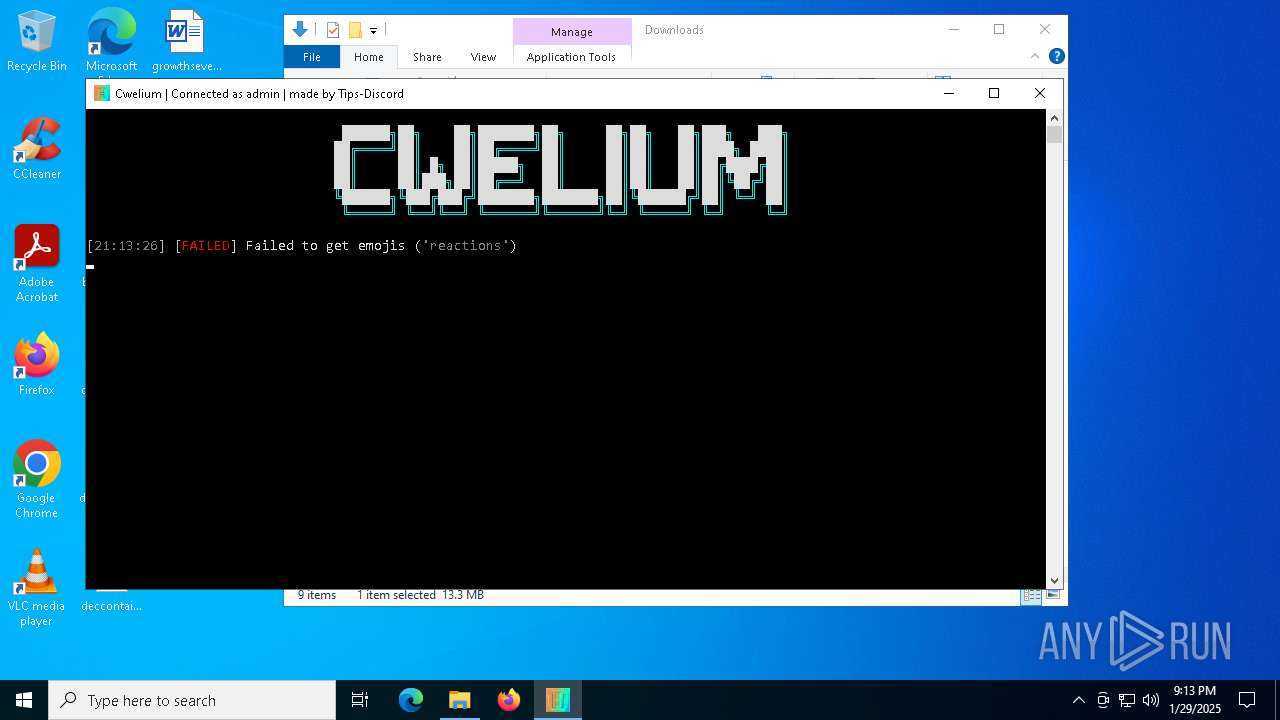
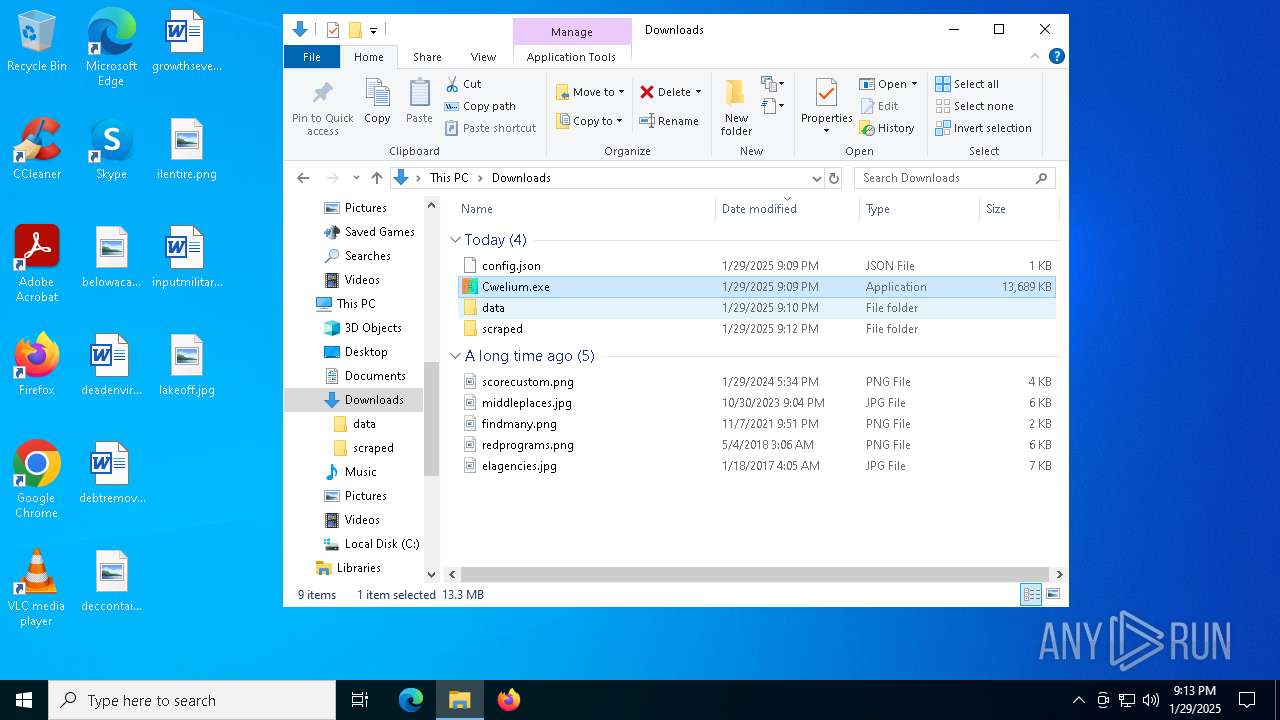
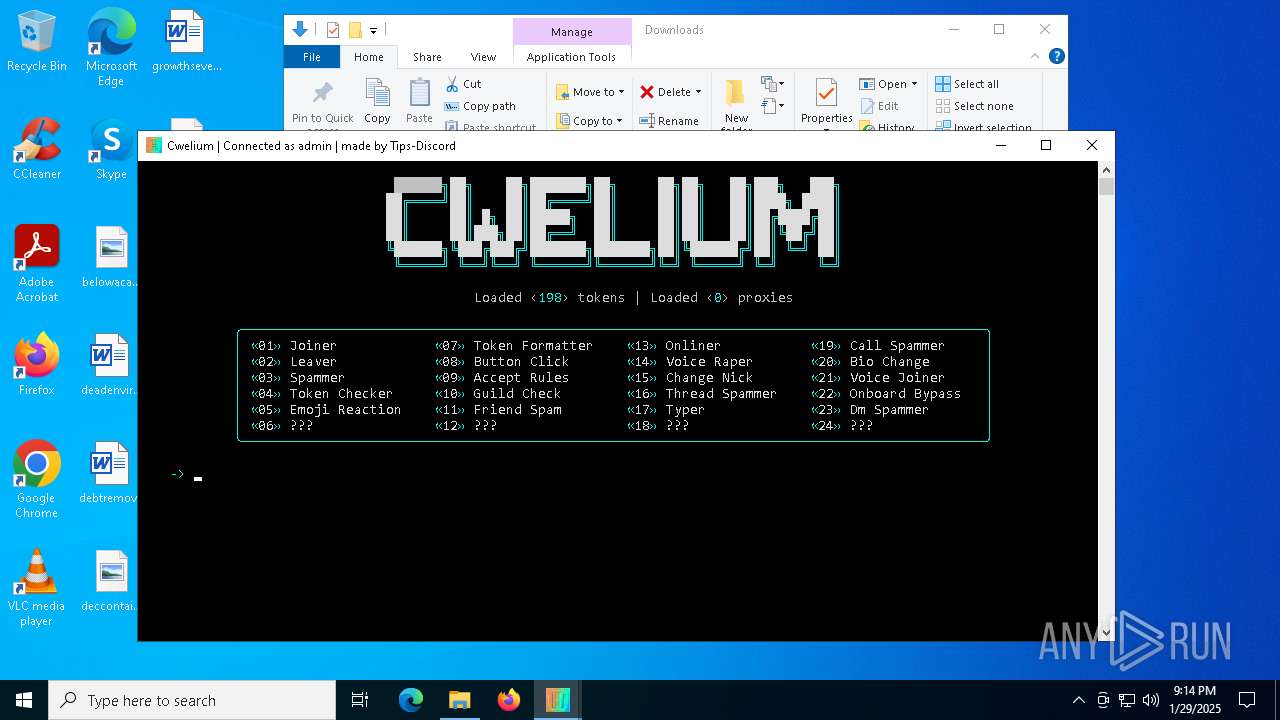
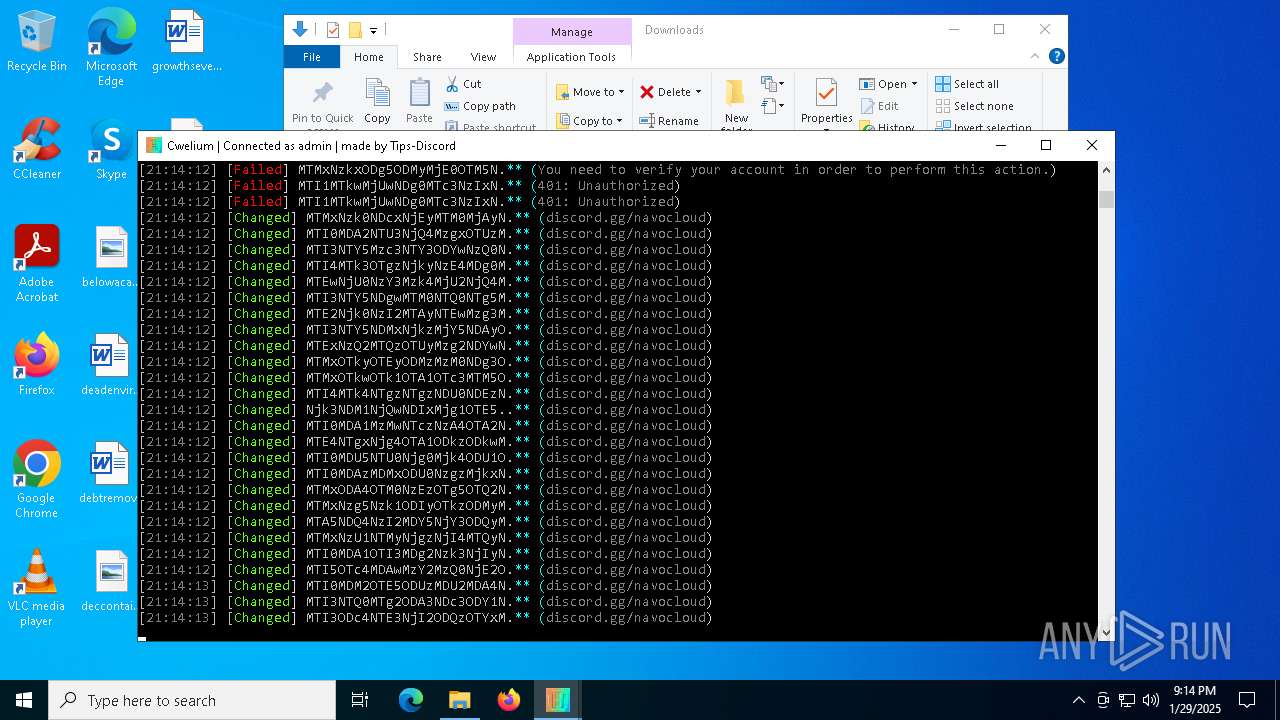
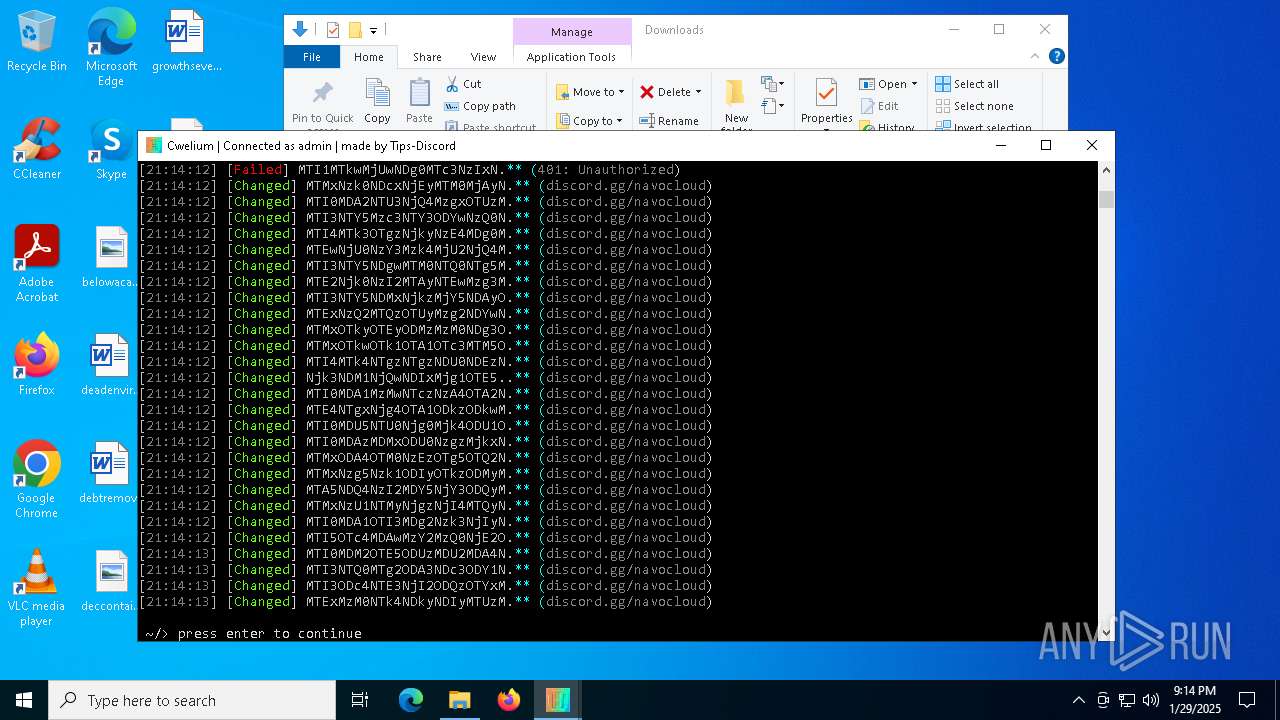
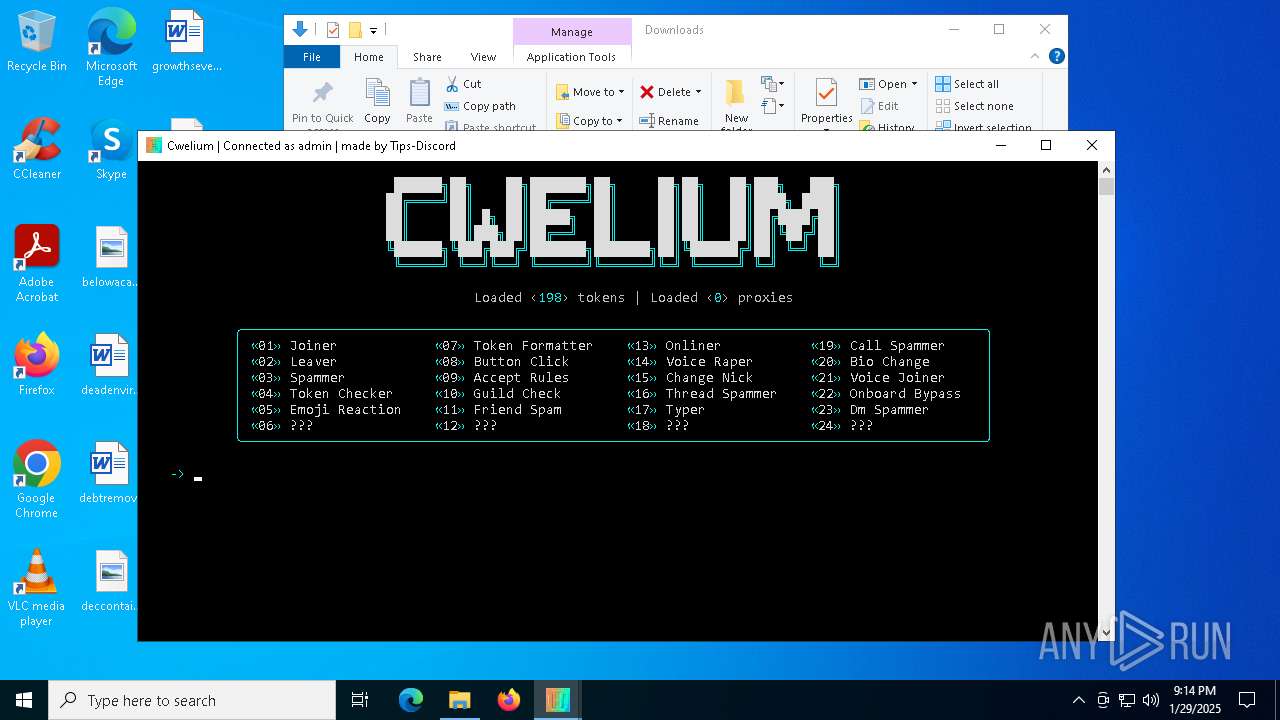
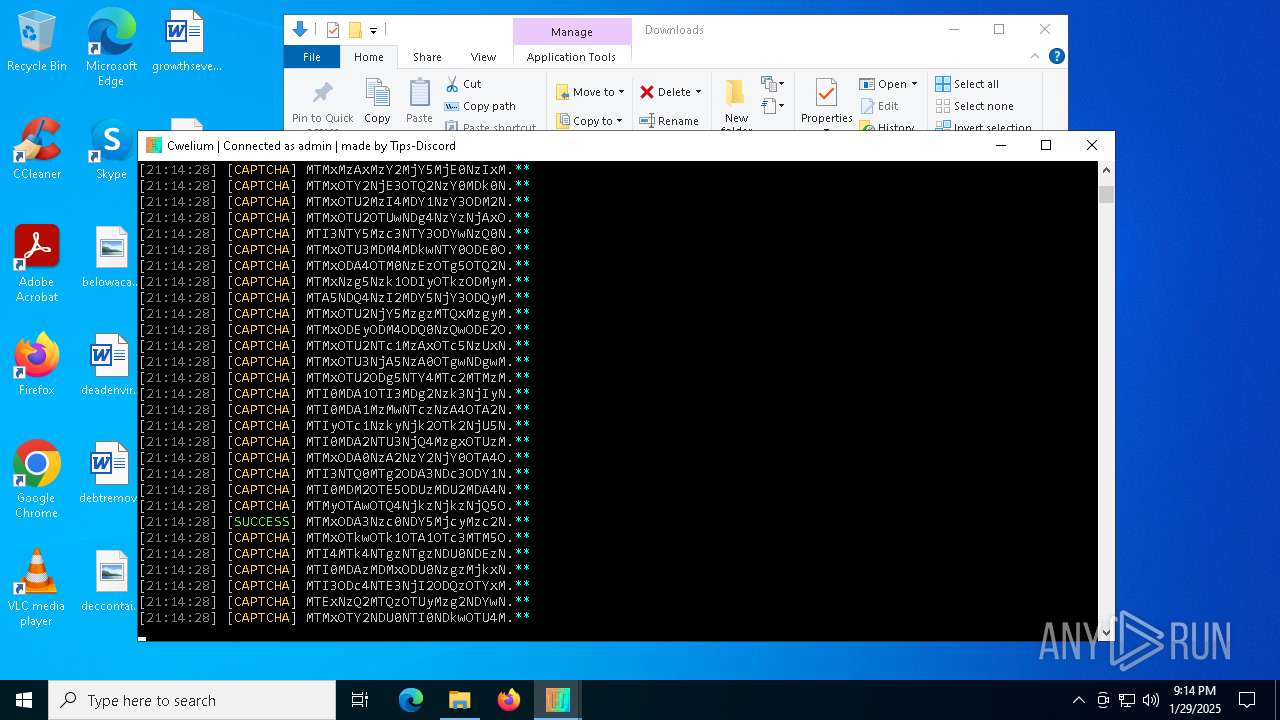
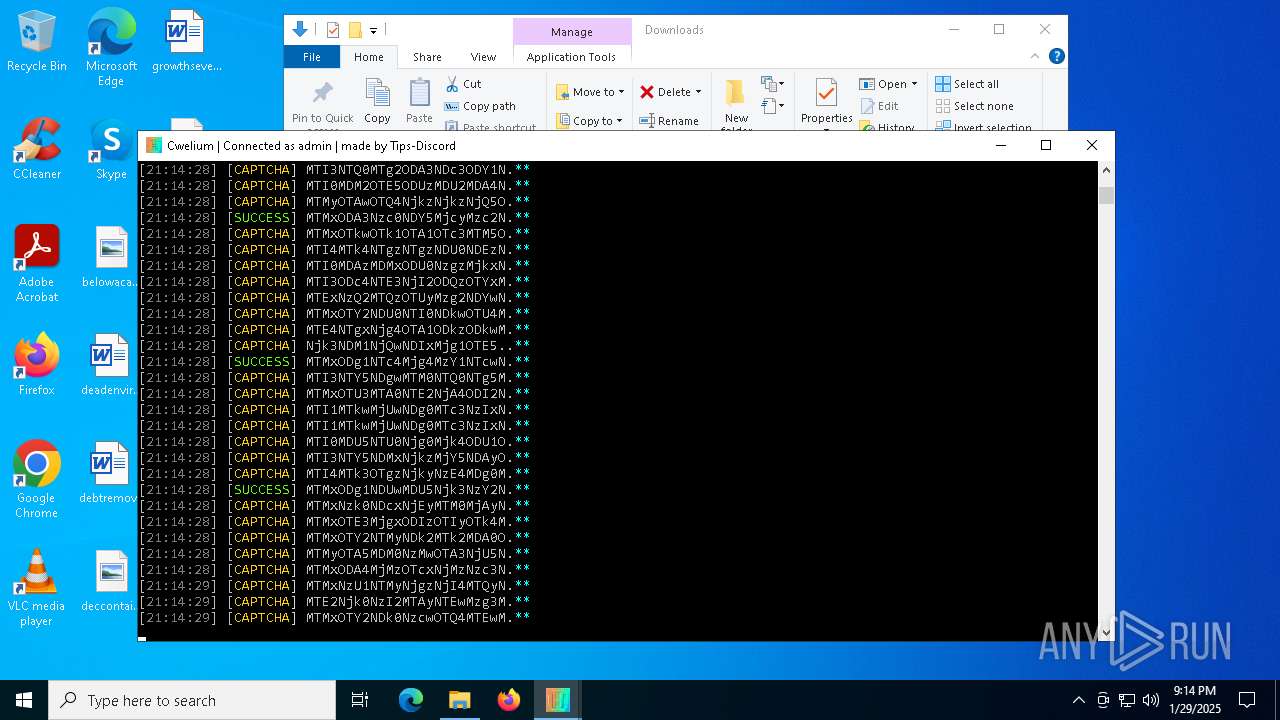
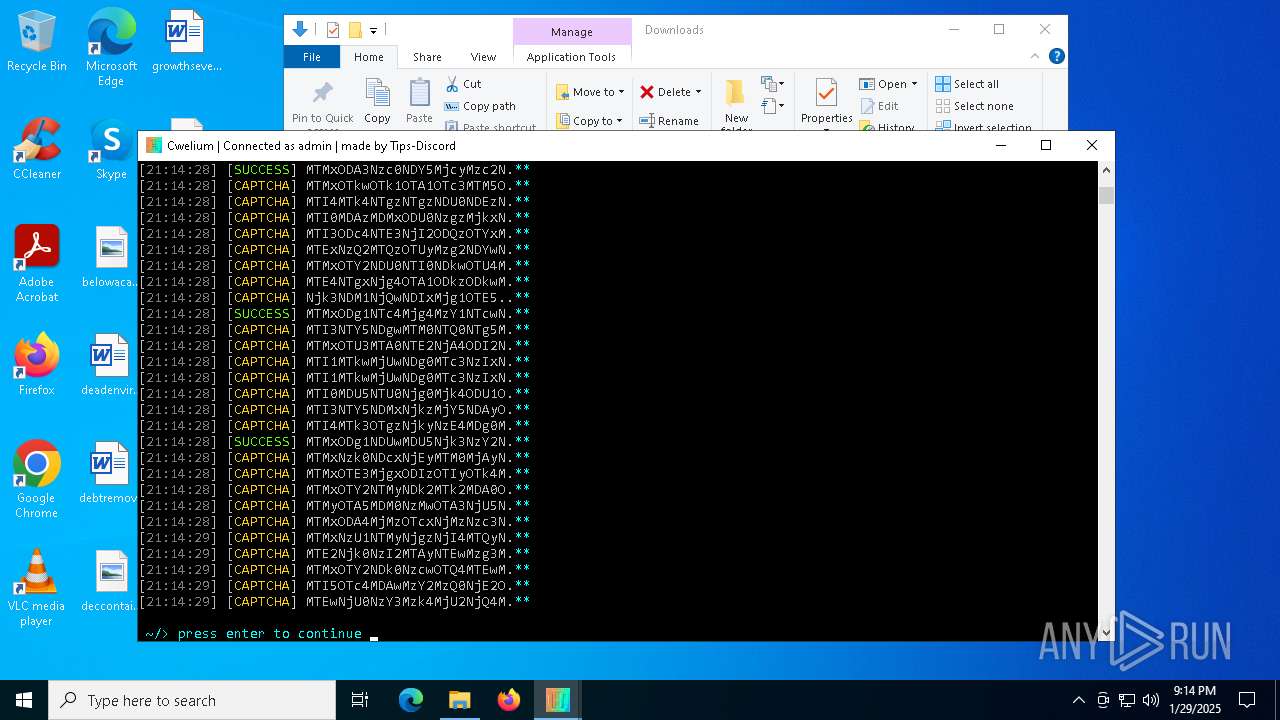
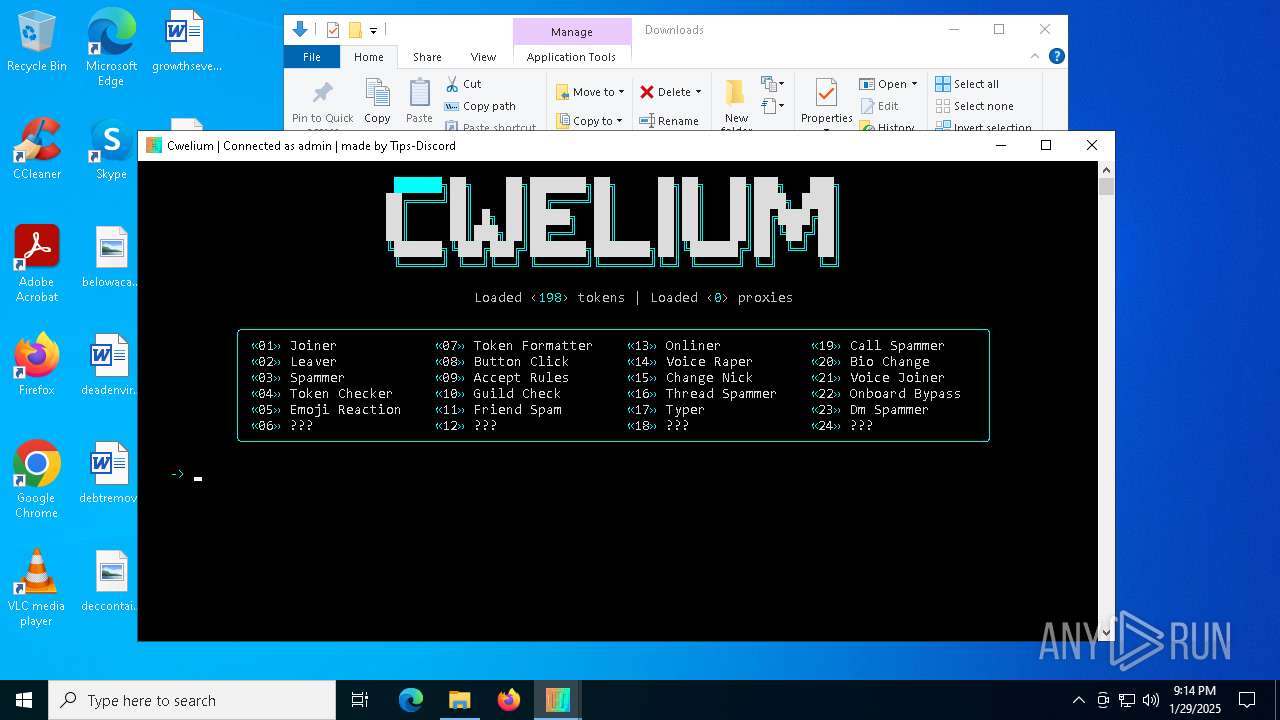
| File name: | Cwelium.exe |
| Full analysis: | https://app.any.run/tasks/342d9d4c-c2a1-4314-8032-493b686b8810 |
| Verdict: | Malicious activity |
| Analysis date: | January 29, 2025, 21:09:33 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64 (stripped to external PDB), for MS Windows, 12 sections |
| MD5: | 1970691985CFA519E5D7CD4D318DA84D |
| SHA1: | F26399239532055CB0FF59E5F05E5790AADD6C60 |
| SHA256: | B52721BF53C98AF2059C7B0AA4CB0255AF0B1ABE89B0630DD3FC5FAA0D331BD9 |
| SSDEEP: | 196608:B8Hy4tQu/8YmtRBYkB0No4mfPjOauAITPFrm:BwyWQCyRBYkBGLGiauRm |
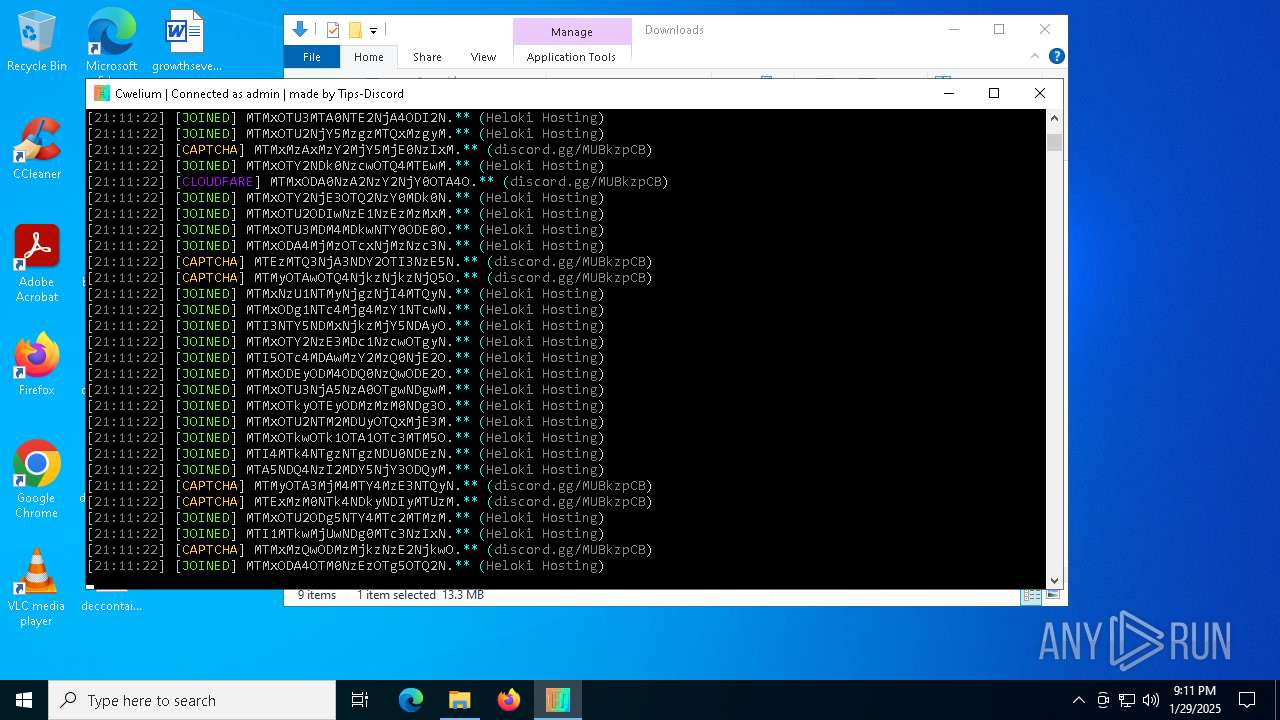
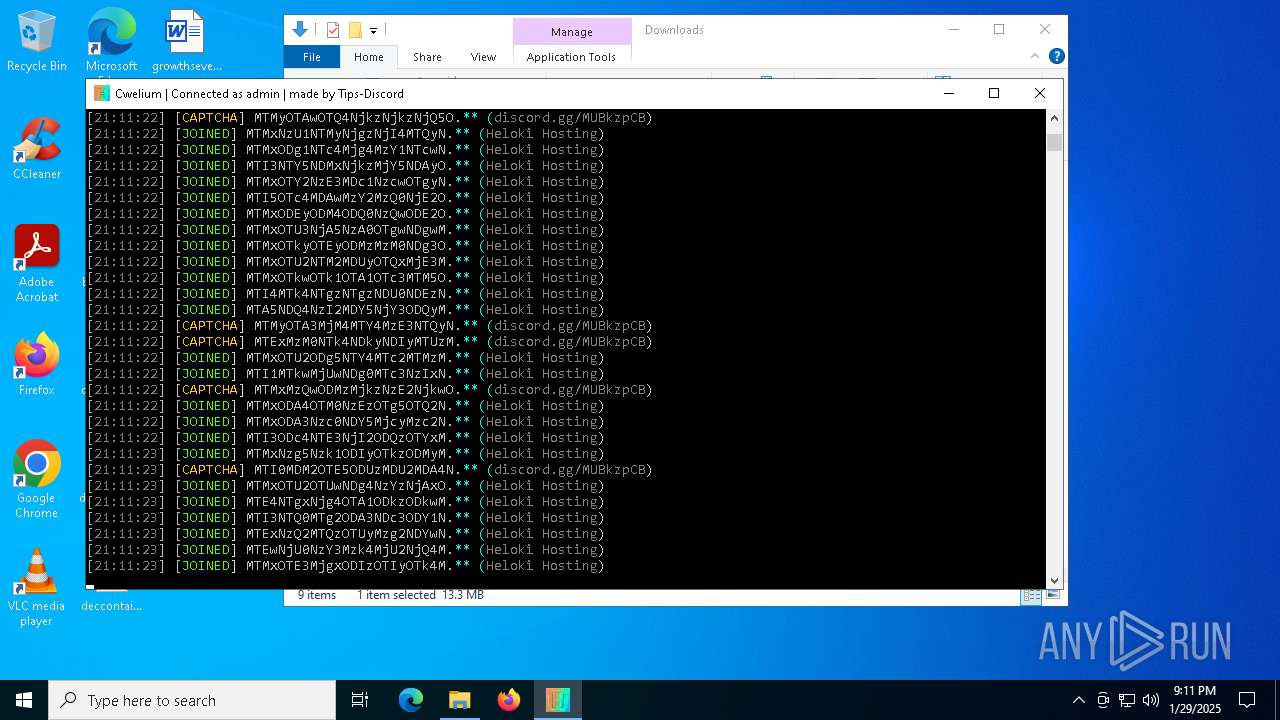
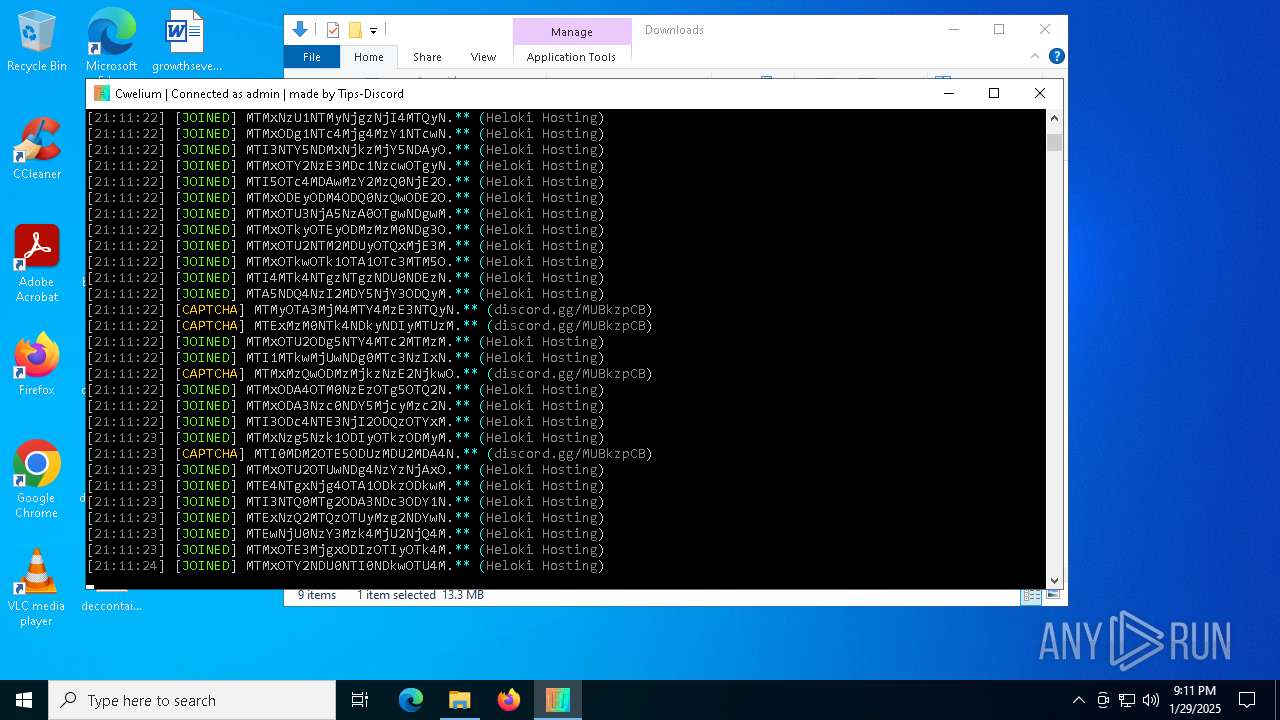
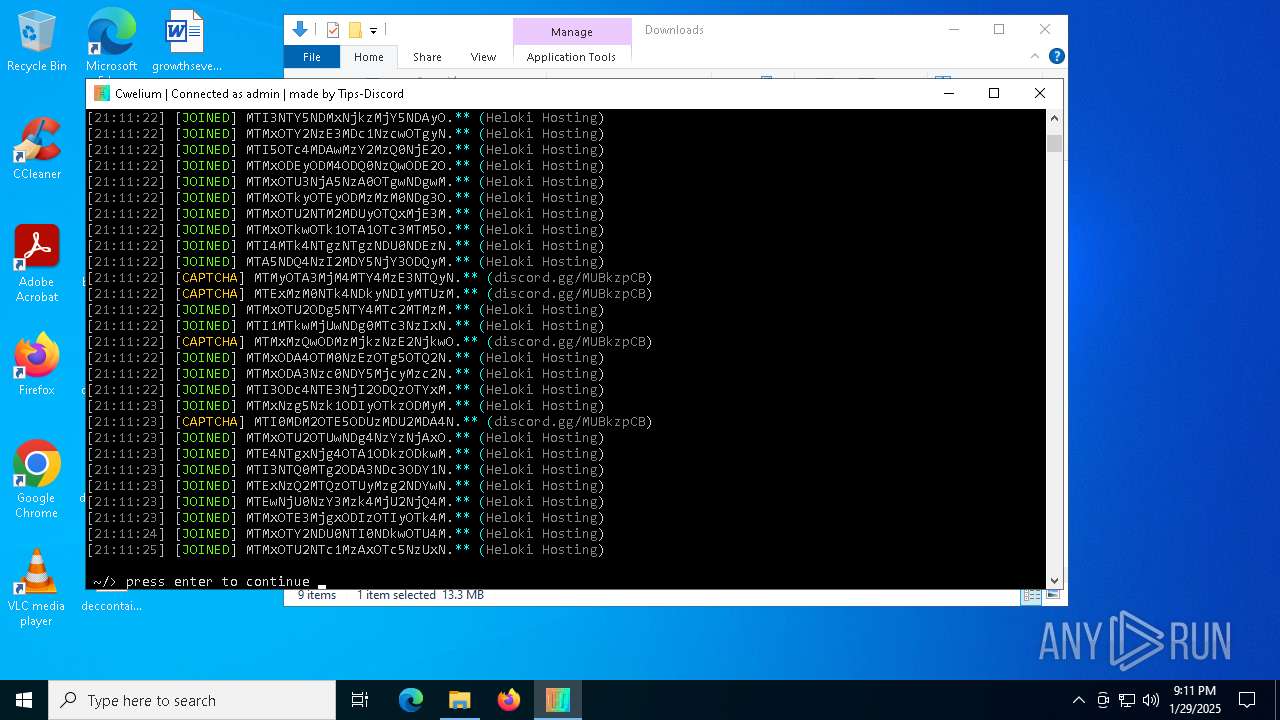
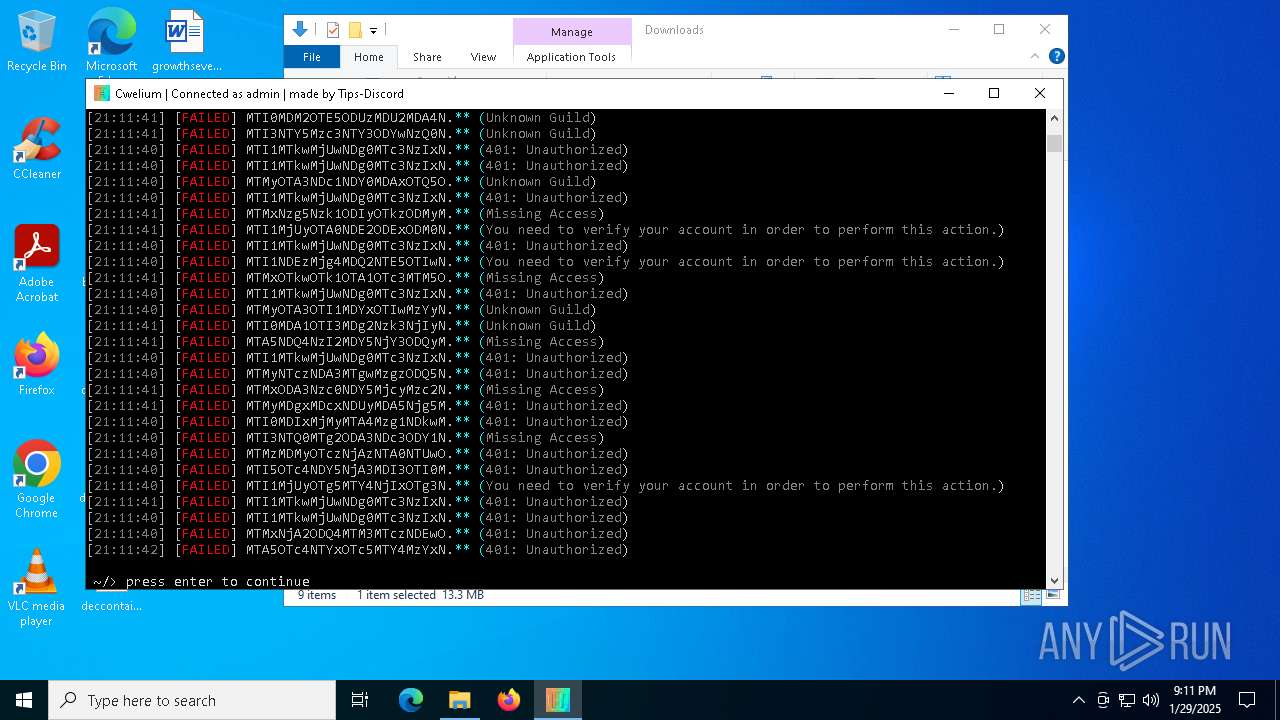
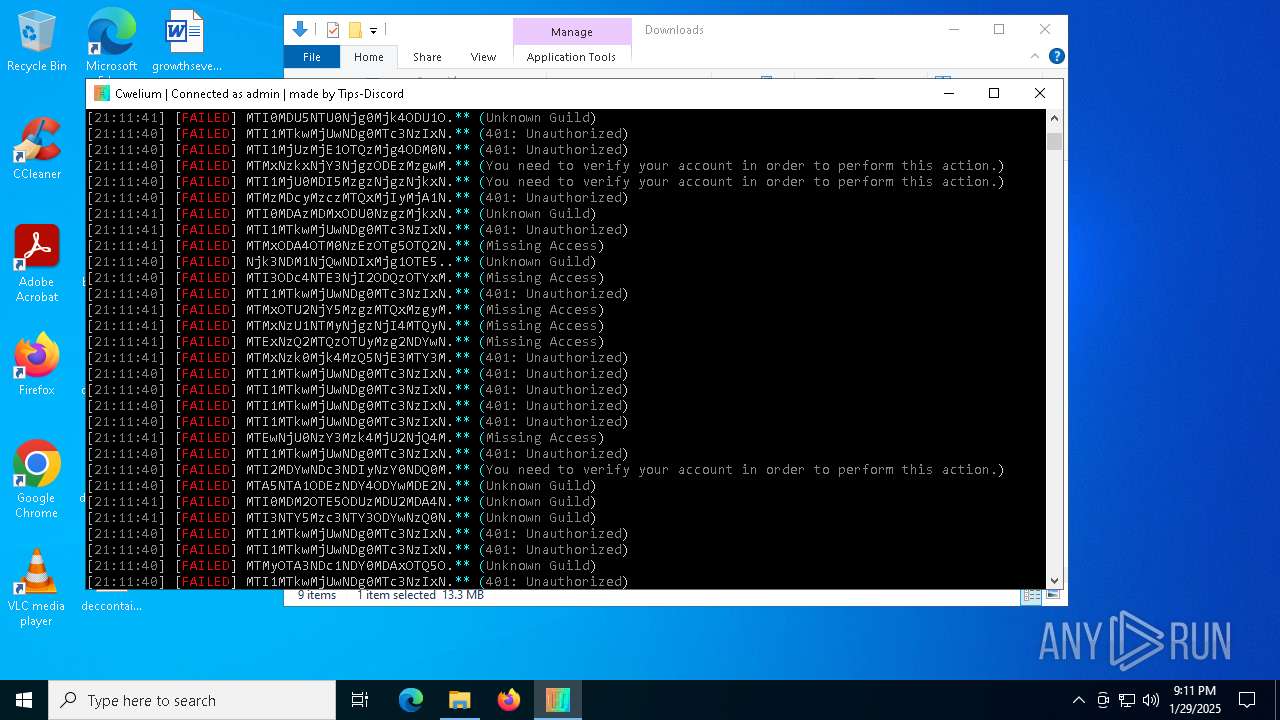
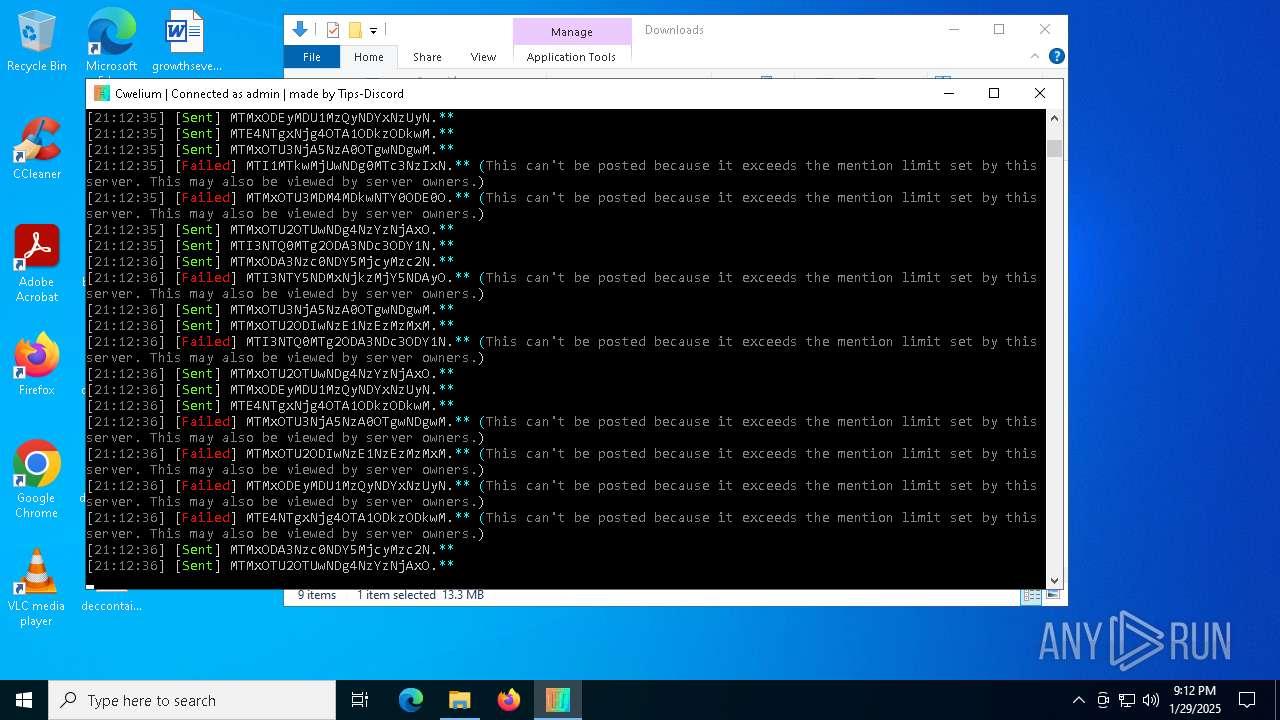
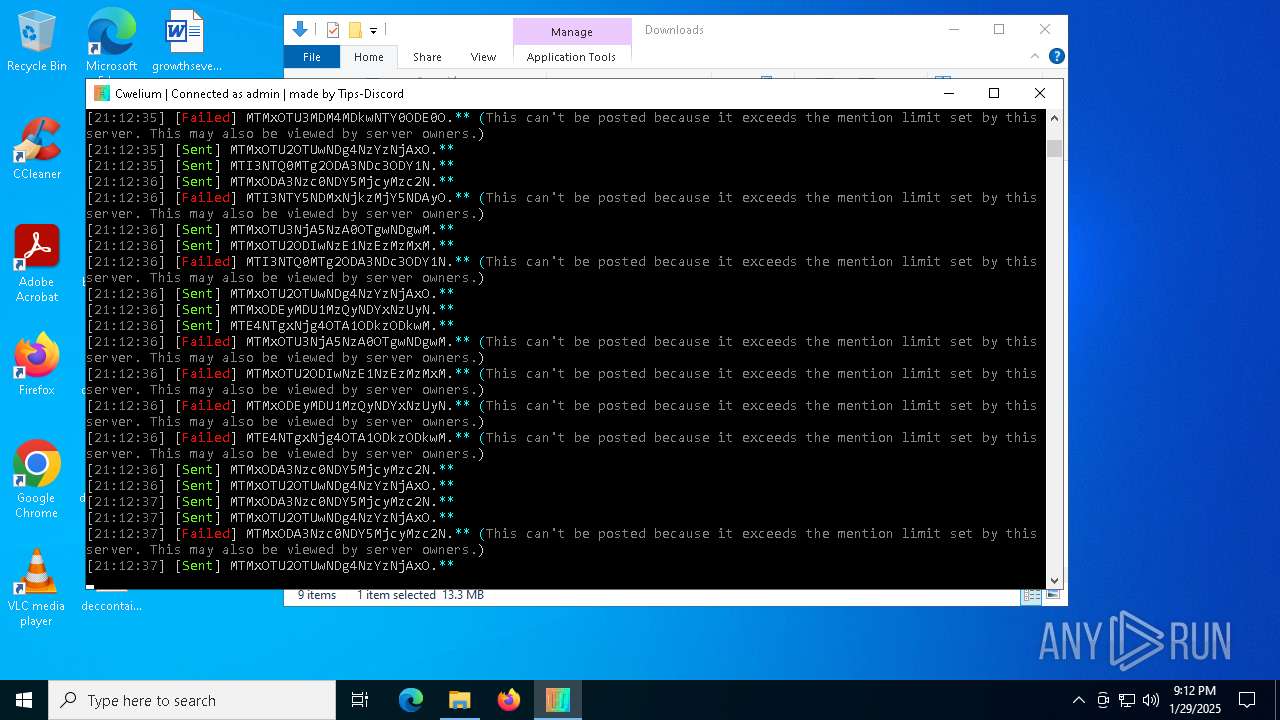
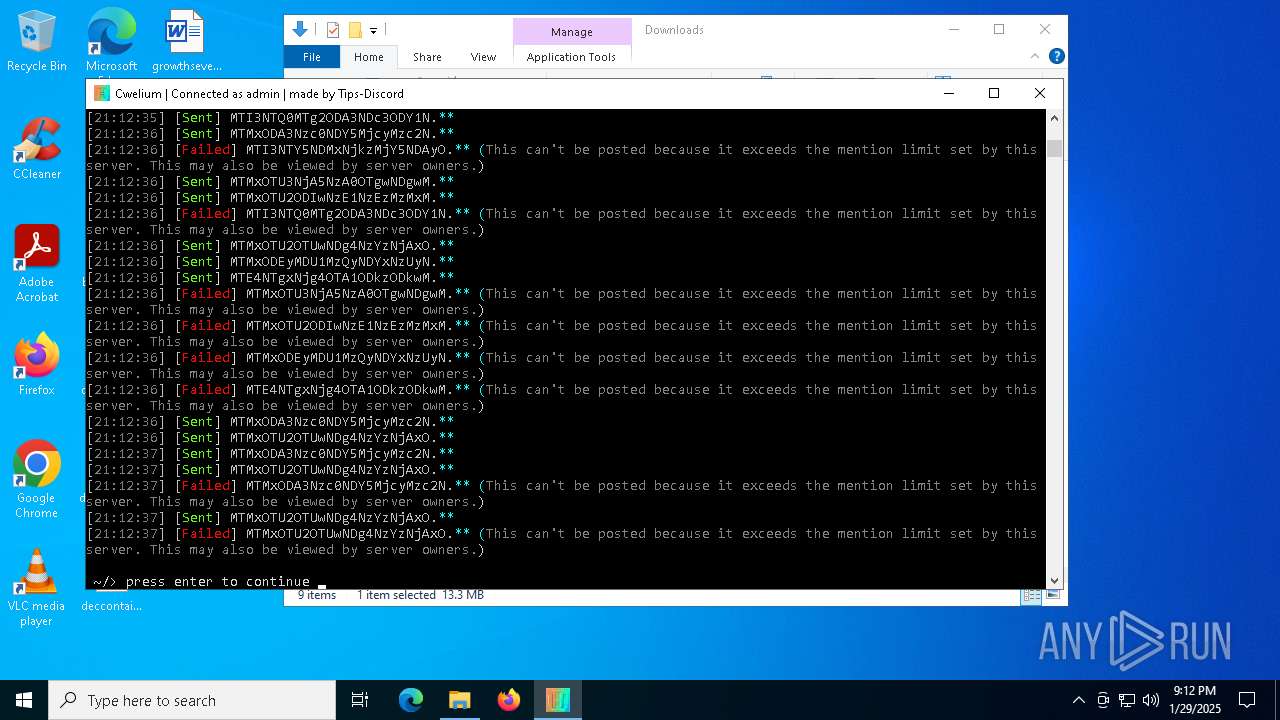
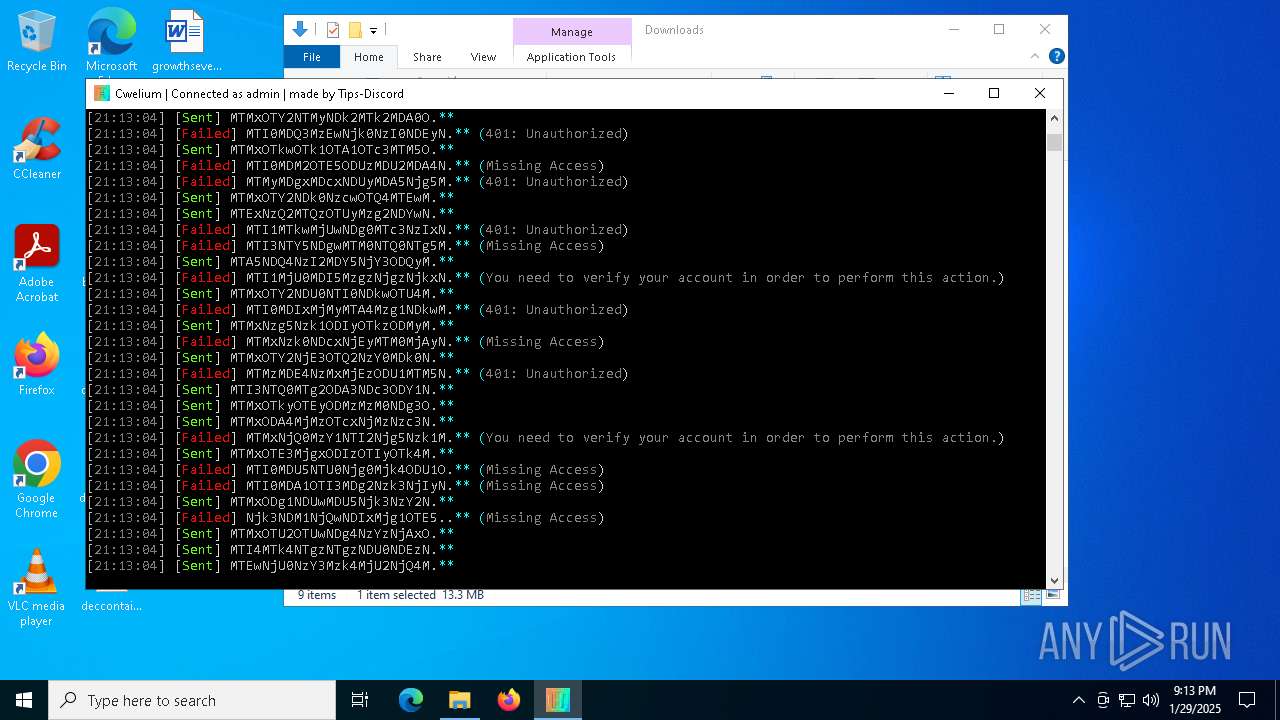
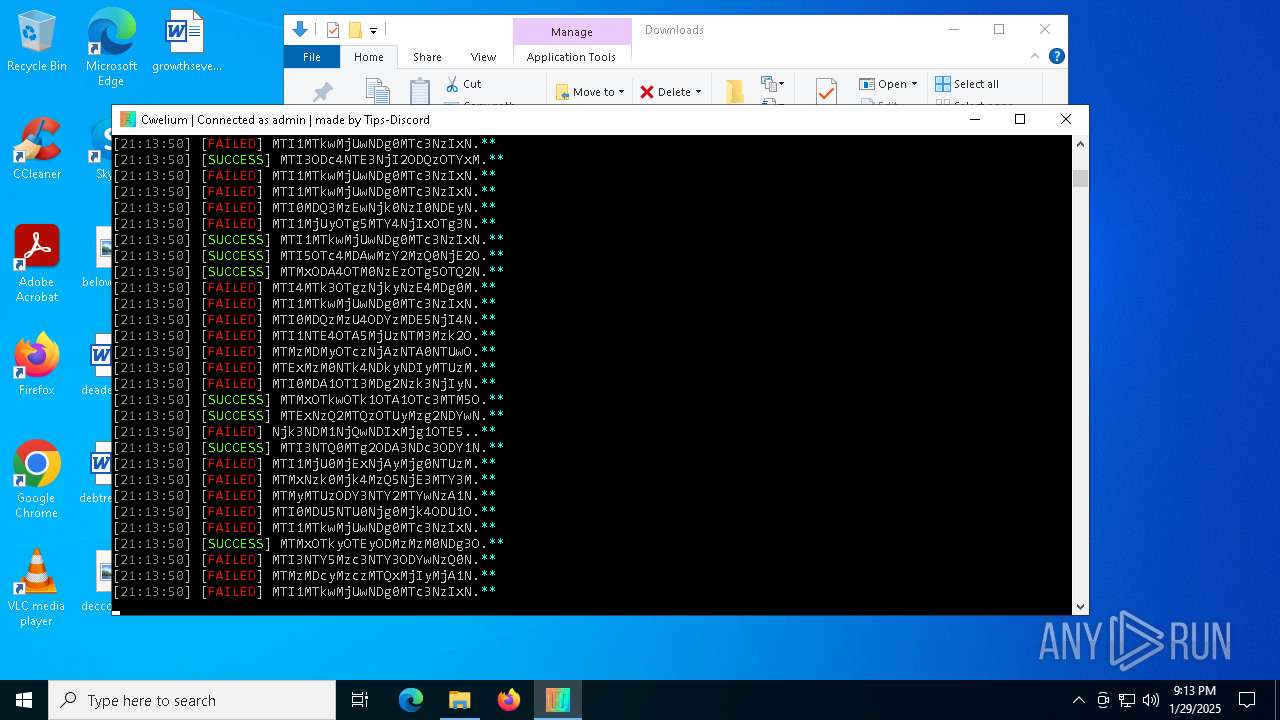
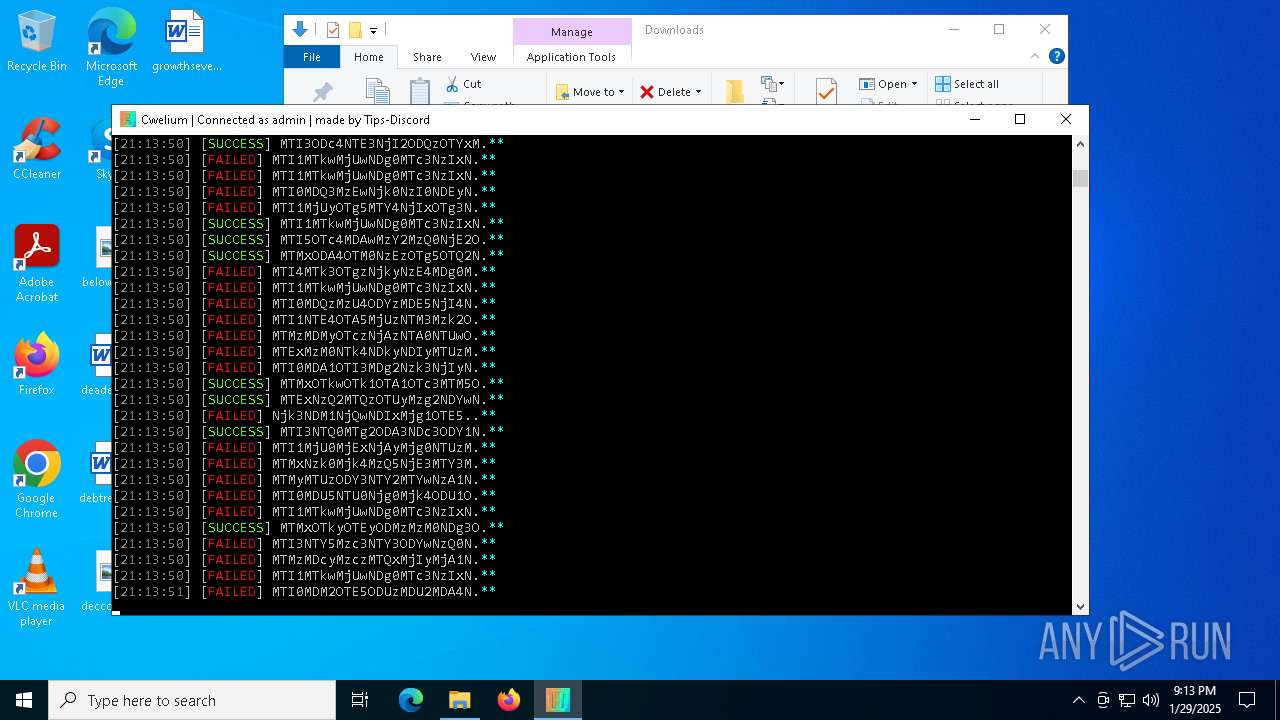
MALICIOUS
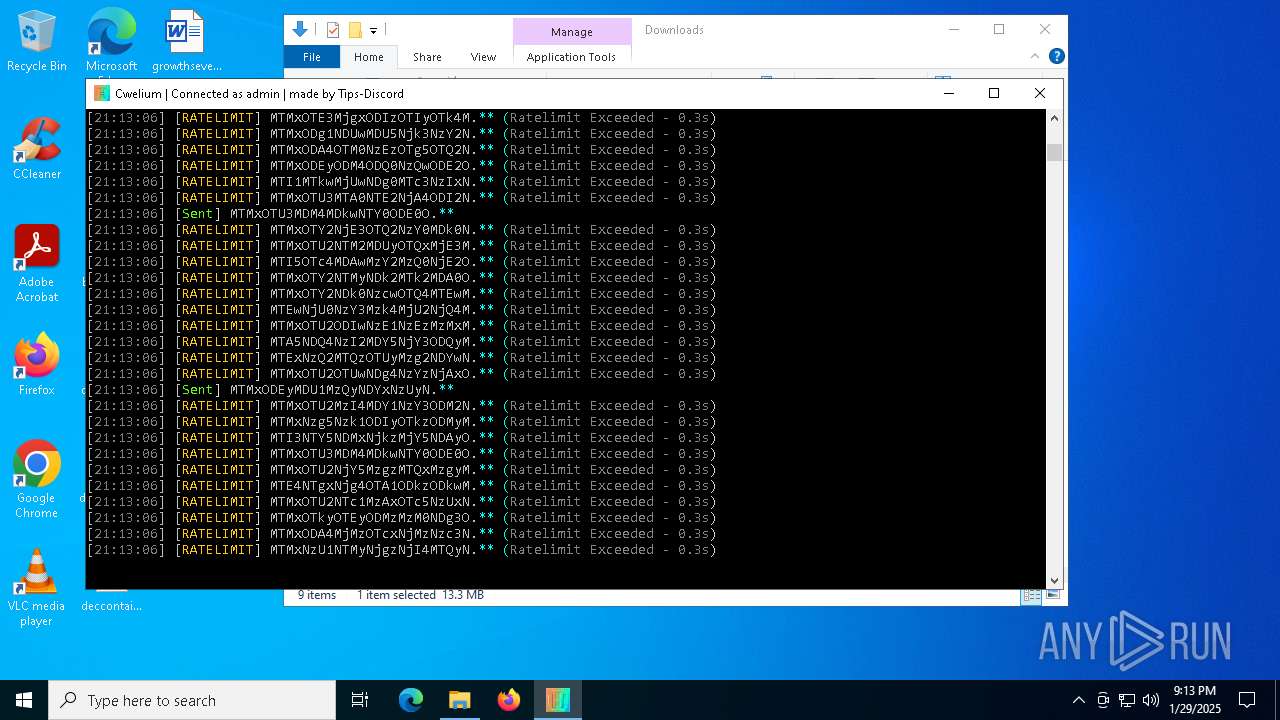
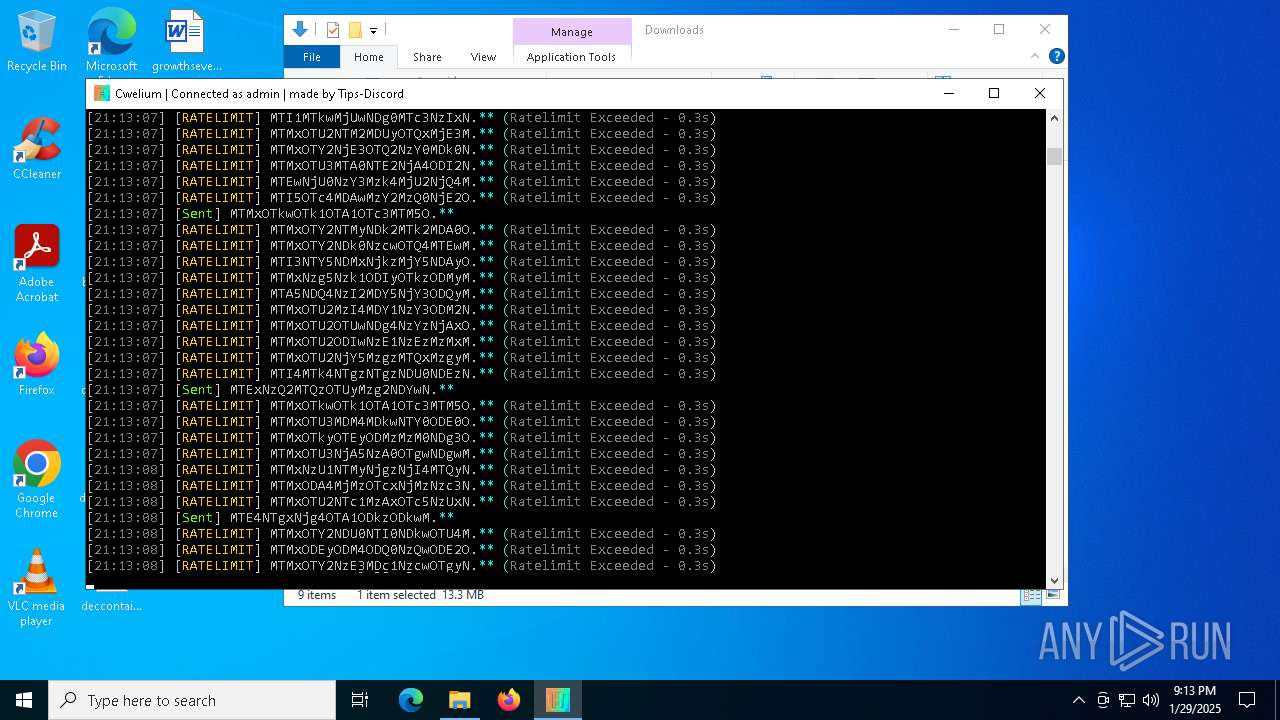
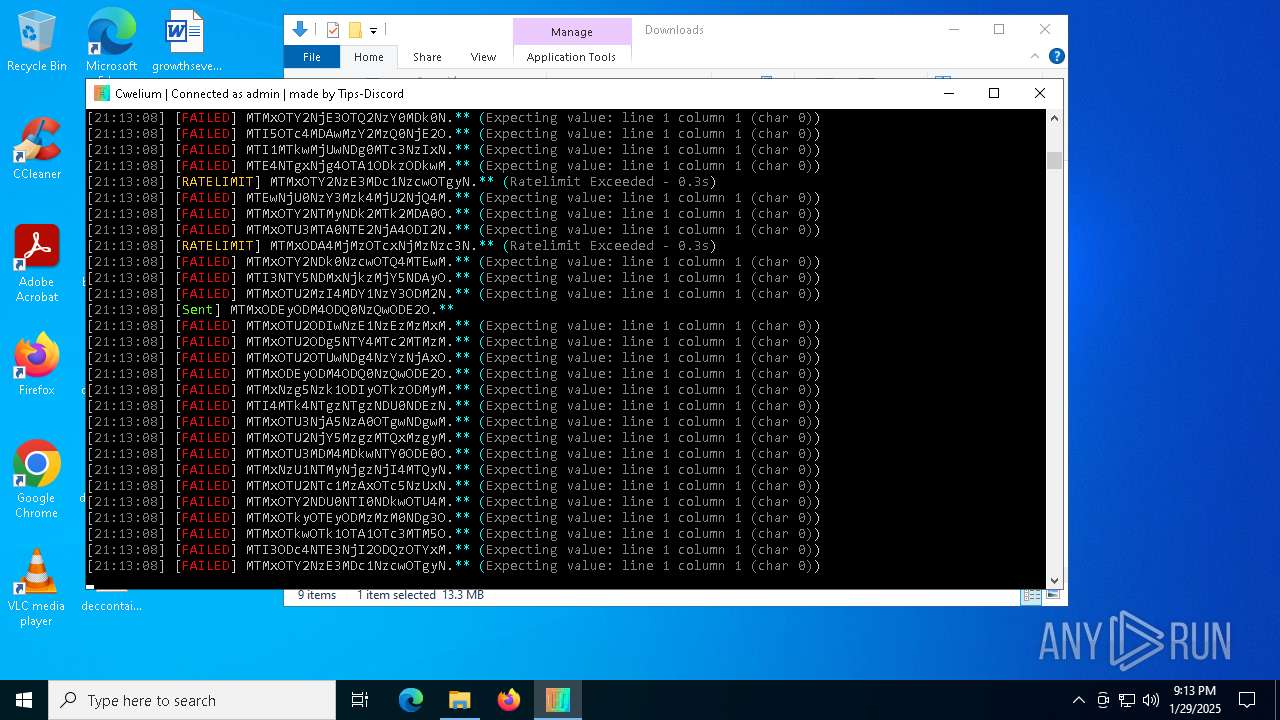
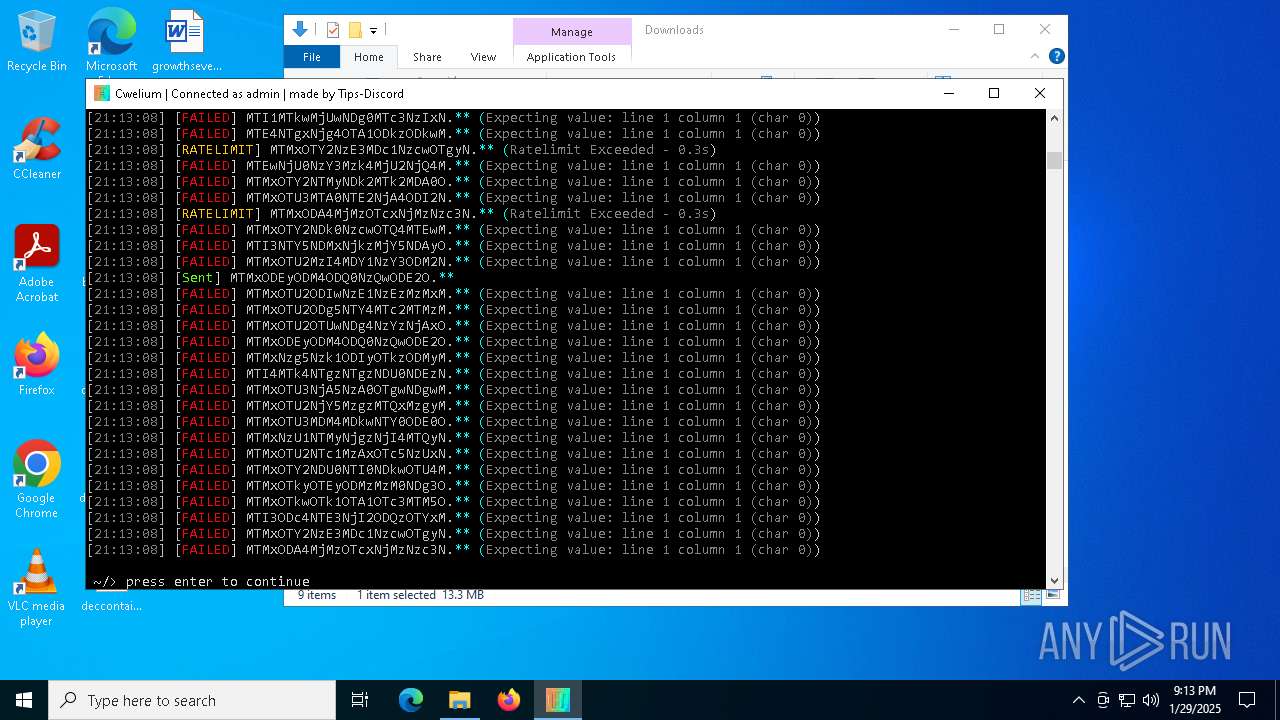
TROX has been detected
- Cwelium.exe (PID: 6288)
- Cwelium.exe (PID: 3620)
- Cwelium.exe (PID: 5736)
- Cwelium.exe (PID: 6732)
- Cwelium.exe (PID: 4516)
SUSPICIOUS
Process drops python dynamic module
- Cwelium.exe (PID: 6288)
- Cwelium.exe (PID: 3620)
- Cwelium.exe (PID: 6732)
- Cwelium.exe (PID: 5736)
- Cwelium.exe (PID: 4516)
Executable content was dropped or overwritten
- Cwelium.exe (PID: 6288)
- Cwelium.exe (PID: 3620)
- Cwelium.exe (PID: 6732)
- Cwelium.exe (PID: 5736)
- Cwelium.exe (PID: 4516)
Starts CMD.EXE for commands execution
- Cwelium.exe (PID: 6376)
- Cwelium.exe (PID: 5460)
- Cwelium.exe (PID: 876)
- Cwelium.exe (PID: 4604)
- Cwelium.exe (PID: 6348)
Loads Python modules
- Cwelium.exe (PID: 6376)
- Cwelium.exe (PID: 5460)
- Cwelium.exe (PID: 6348)
- Cwelium.exe (PID: 876)
- Cwelium.exe (PID: 4604)
Reads security settings of Internet Explorer
- Cwelium.exe (PID: 6288)
- Cwelium.exe (PID: 3620)
- Cwelium.exe (PID: 6732)
INFO
Create files in a temporary directory
- Cwelium.exe (PID: 6288)
- Cwelium.exe (PID: 3620)
- Cwelium.exe (PID: 6732)
- Cwelium.exe (PID: 5736)
- Cwelium.exe (PID: 4516)
Checks supported languages
- Cwelium.exe (PID: 6288)
- Cwelium.exe (PID: 6376)
- Cwelium.exe (PID: 3620)
- Cwelium.exe (PID: 5460)
- Cwelium.exe (PID: 6732)
- Cwelium.exe (PID: 876)
- Cwelium.exe (PID: 5736)
- Cwelium.exe (PID: 4516)
- Cwelium.exe (PID: 4604)
- Cwelium.exe (PID: 6348)
Reads the computer name
- Cwelium.exe (PID: 6376)
- Cwelium.exe (PID: 6288)
- Cwelium.exe (PID: 5460)
- Cwelium.exe (PID: 3620)
- Cwelium.exe (PID: 6348)
- Cwelium.exe (PID: 876)
- Cwelium.exe (PID: 6732)
Checks proxy server information
- Cwelium.exe (PID: 6376)
- Cwelium.exe (PID: 5460)
- Cwelium.exe (PID: 876)
- Cwelium.exe (PID: 4604)
- Cwelium.exe (PID: 6348)
Manual execution by a user
- Cwelium.exe (PID: 3620)
- Cwelium.exe (PID: 6732)
- Cwelium.exe (PID: 5736)
- Cwelium.exe (PID: 4516)
Reads the machine GUID from the registry
- Cwelium.exe (PID: 5460)
- Cwelium.exe (PID: 876)
- Cwelium.exe (PID: 6348)
- Cwelium.exe (PID: 4604)
Reads the software policy settings
- Cwelium.exe (PID: 5460)
- Cwelium.exe (PID: 876)
- Cwelium.exe (PID: 6348)
- Cwelium.exe (PID: 4604)
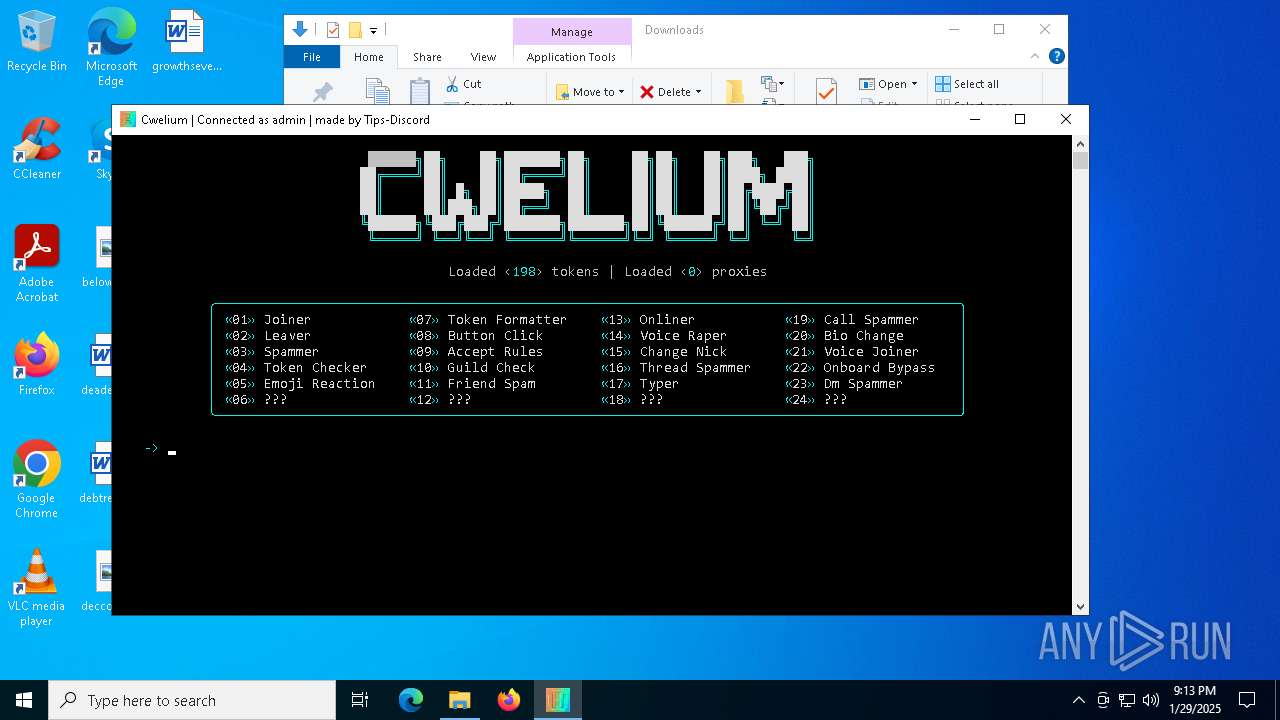
Application based on Golang
- Cwelium.exe (PID: 5460)
The sample compiled with english language support
- Cwelium.exe (PID: 5736)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:12:13 18:03:21+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Large address aware, No debug |
| PEType: | PE32+ |
| LinkerVersion: | 2.43 |
| CodeSize: | 113152 |
| InitializedDataSize: | 14016000 |
| UninitializedDataSize: | 146944 |
| EntryPoint: | 0x1125 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 1.1.2.0 |
| ProductVersionNumber: | 1.1.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
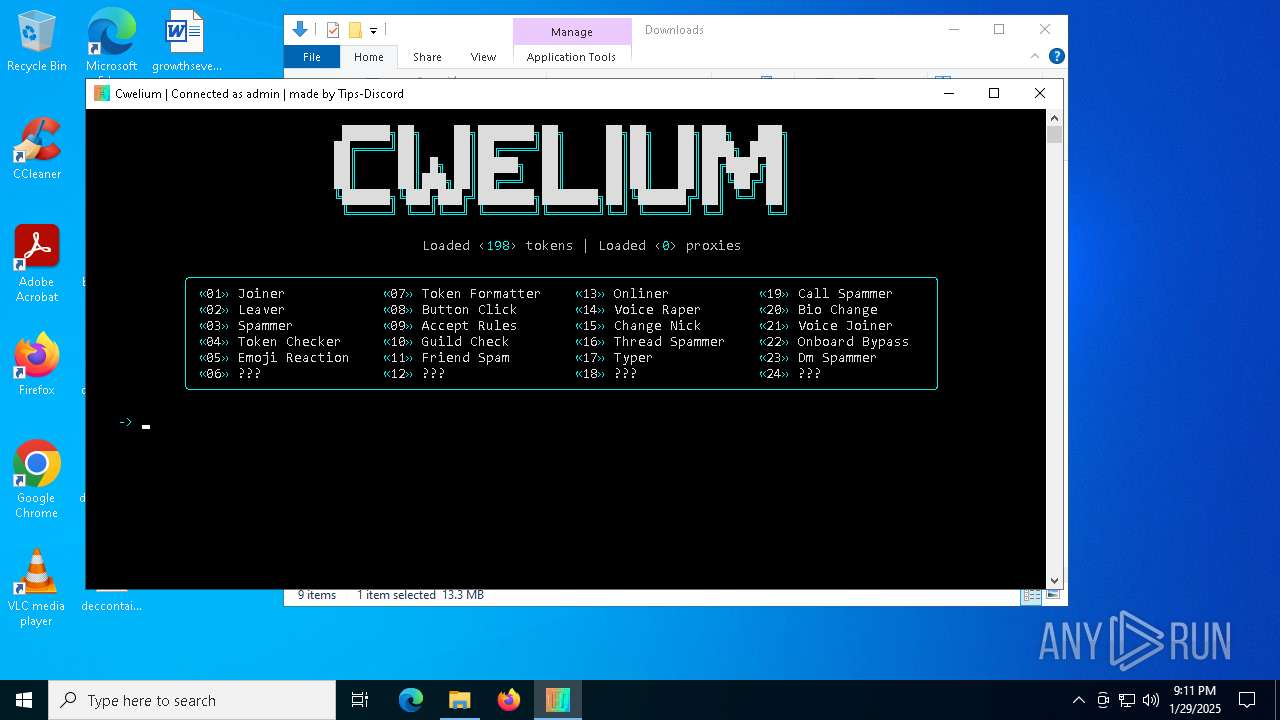
| CompanyName: | Cwelium inc. |
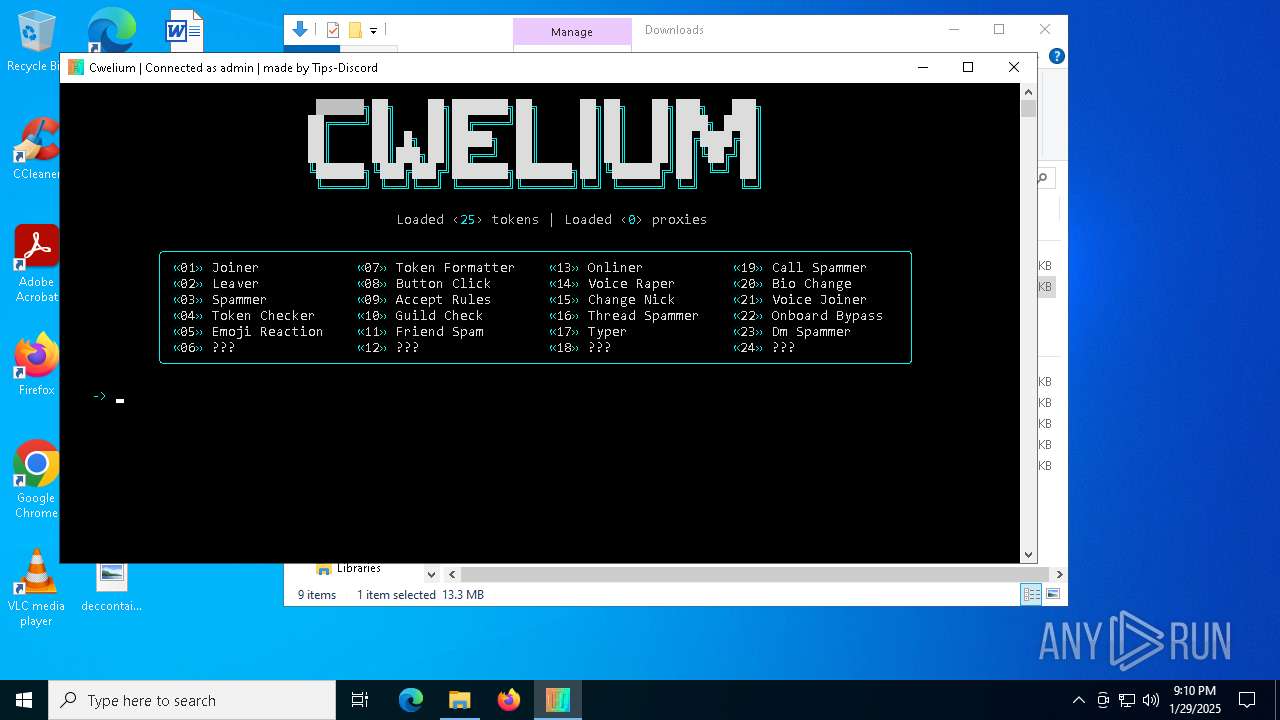
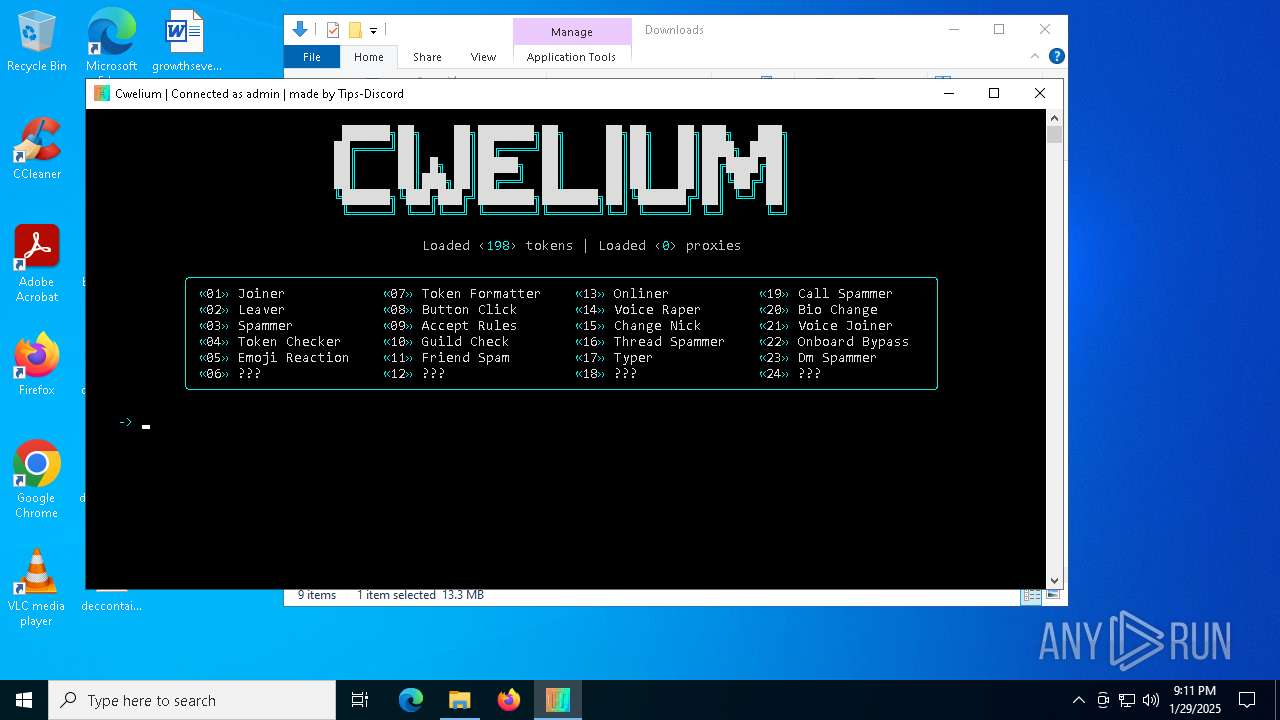
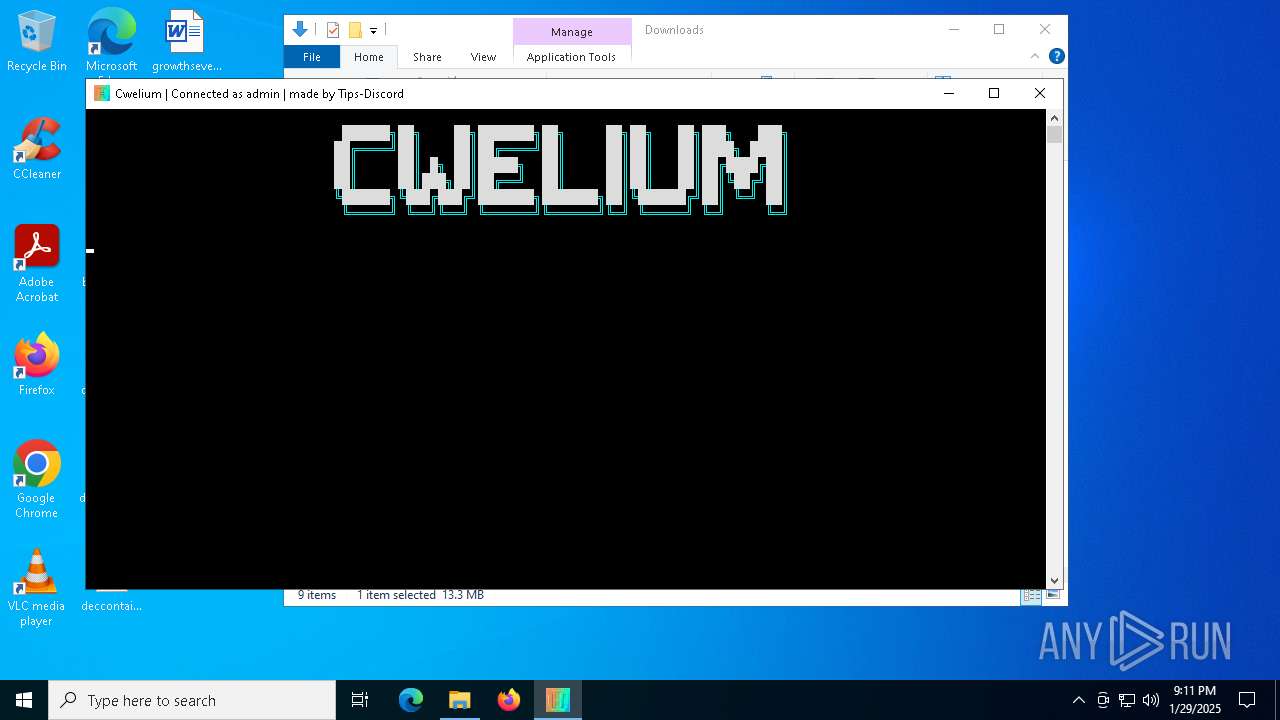
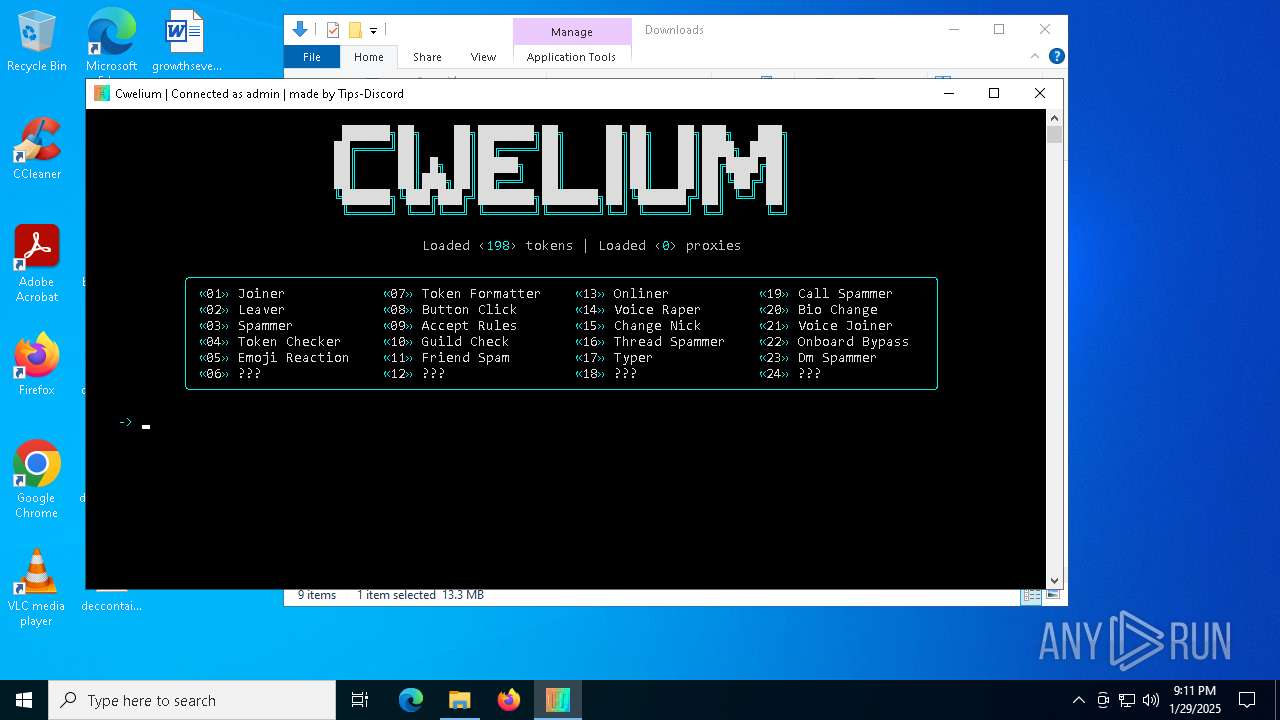
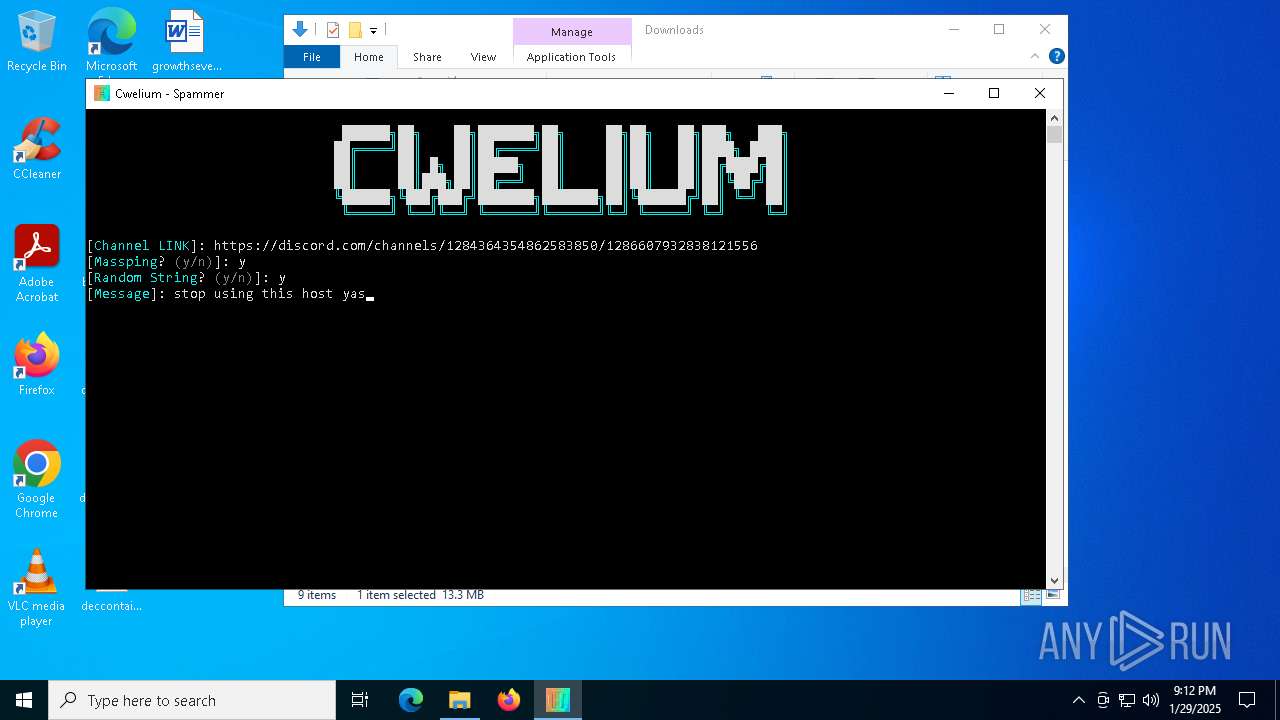
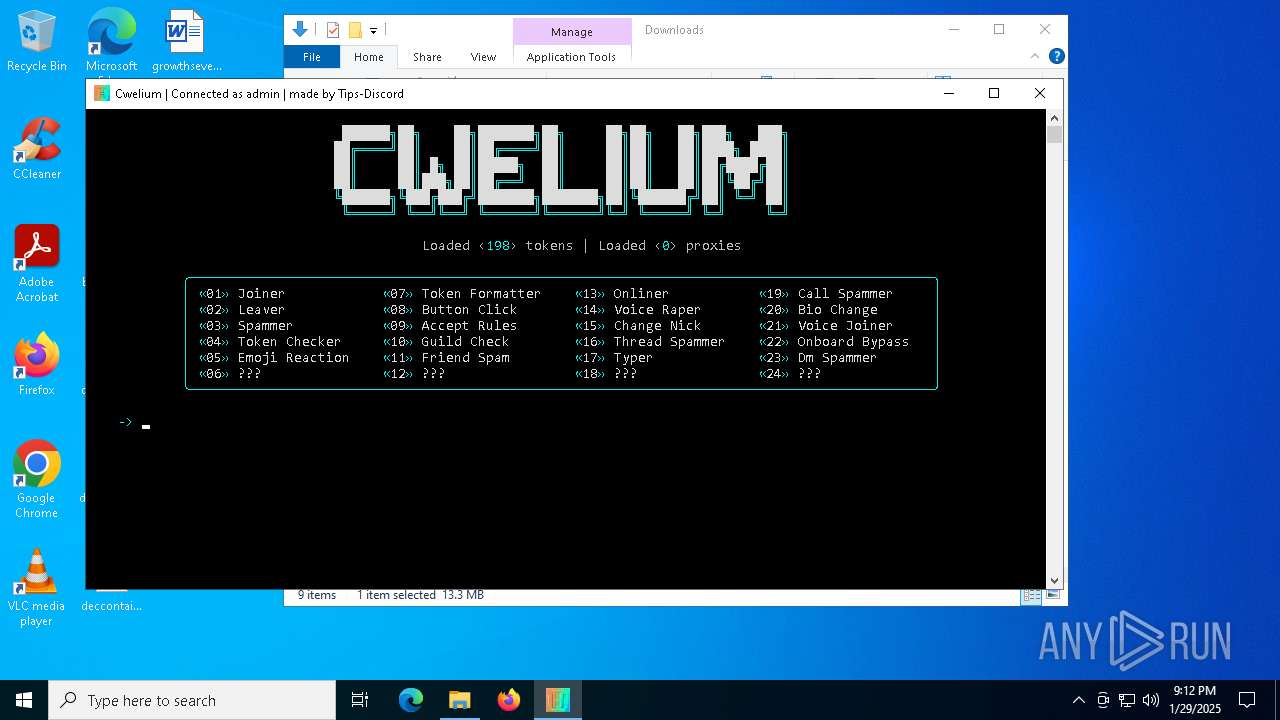
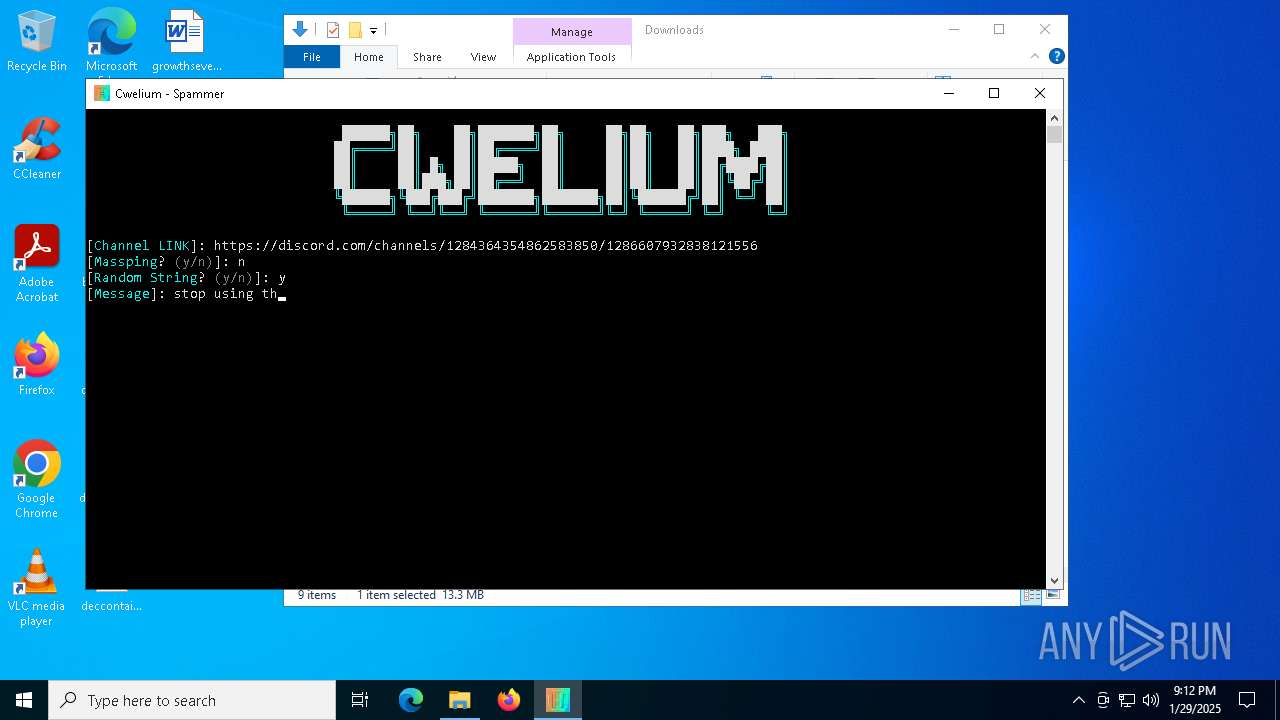
| FileDescription: | Cwelium Discord Raider |
| LegalCopyright: | Copyright (c) 2024 Cwelium Inc. All rights reserved. |
| ProductVersion: | 1.1.0.0 |
| FileVersion: | 1.1.2.0 |
| OriginalFileName: | Cwelium.exe |
| InternalName: | Cwelium |
| ProductName: | Cwelium |
Total processes
218
Monitored processes
90
Malicious processes
5
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 396 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | Cwelium.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 848 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | Cwelium.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 876 | C:\Users\admin\Downloads\Cwelium.exe | C:\Users\admin\AppData\Local\Temp\onefile_6732_133826586768335067\Cwelium.exe | Cwelium.exe | ||||||||||||
User: admin Company: Cwelium inc. Integrity Level: MEDIUM Description: Cwelium Discord Raider Exit code: 1 Version: 1.1.2.0 Modules
| |||||||||||||||
| 1016 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | Cwelium.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1200 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | Cwelium.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1200 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | Cwelium.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1544 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | Cwelium.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1596 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | Cwelium.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2012 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | Cwelium.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2280 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | Cwelium.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
18 835
Read events
18 835
Write events
0
Delete events
0
Modification events
Executable files
125
Suspicious files
1
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6288 | Cwelium.exe | C:\Users\admin\AppData\Local\Temp\onefile_6288_133826585811933499\_ctypes.pyd | executable | |
MD5:5377AB365C86BBCDD998580A79BE28B4 | SHA256:6C5F31BEF3FDBFF31BEAC0B1A477BE880DDA61346D859CF34CA93B9291594D93 | |||
| 6288 | Cwelium.exe | C:\Users\admin\AppData\Local\Temp\onefile_6288_133826585811933499\libssl-3.dll | executable | |
MD5:4FF168AAA6A1D68E7957175C8513F3A2 | SHA256:2E4D35B681A172D3298CAF7DC670451BE7A8BA27C26446EFC67470742497A950 | |||
| 6288 | Cwelium.exe | C:\Users\admin\AppData\Local\Temp\onefile_6288_133826585811933499\_lzma.pyd | executable | |
MD5:9E94FAC072A14CA9ED3F20292169E5B2 | SHA256:A46189C5BD0302029847FED934F481835CB8D06470EA3D6B97ADA7D325218A9F | |||
| 6288 | Cwelium.exe | C:\Users\admin\AppData\Local\Temp\onefile_6288_133826585811933499\vcruntime140_1.dll | executable | |
MD5:F8DFA78045620CF8A732E67D1B1EB53D | SHA256:A113F192195F245F17389E6ECBED8005990BCB2476DDAD33F7C4C6C86327AFE5 | |||
| 6288 | Cwelium.exe | C:\Users\admin\AppData\Local\Temp\onefile_6288_133826585811933499\python3.dll | executable | |
MD5:5EACE36402143B0205635818363D8E57 | SHA256:25A39E721C26E53BEC292395D093211BBA70465280ACFA2059FA52957EC975B2 | |||
| 6288 | Cwelium.exe | C:\Users\admin\AppData\Local\Temp\onefile_6288_133826585811933499\unicodedata.pyd | executable | |
MD5:A8ED52A66731E78B89D3C6C6889C485D | SHA256:BF669344D1B1C607D10304BE47D2A2FB572E043109181E2C5C1038485AF0C3D7 | |||
| 6288 | Cwelium.exe | C:\Users\admin\AppData\Local\Temp\onefile_6288_133826585811933499\Cwelium.exe | executable | |
MD5:1FBE480FC647D999B76FE1835E55612F | SHA256:C5D7C530FC4569B5E239BC9D6153421A4D61F8C9E4B88713535345B4CB84603B | |||
| 6288 | Cwelium.exe | C:\Users\admin\AppData\Local\Temp\onefile_6288_133826585811933499\_hashlib.pyd | executable | |
MD5:A25BC2B21B555293554D7F611EAA75EA | SHA256:43ACECDC00DD5F9A19B48FF251106C63C975C732B9A2A7B91714642F76BE074D | |||
| 6288 | Cwelium.exe | C:\Users\admin\AppData\Local\Temp\onefile_6288_133826585811933499\_decimal.pyd | executable | |
MD5:7AE94F5A66986CBC1A2B3C65A8D617F3 | SHA256:DA8BB3D54BBBA20D8FA6C2FD0A4389AEC80AB6BD490B0ABEF5BD65097CBC0DA4 | |||
| 6288 | Cwelium.exe | C:\Users\admin\AppData\Local\Temp\onefile_6288_133826585811933499\_bz2.pyd | executable | |
MD5:30F396F8411274F15AC85B14B7B3CD3D | SHA256:CB15D6CC7268D3A0BD17D9D9CEC330A7C1768B1C911553045C73BC6920DE987F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
51
DNS requests
22
Threats
18
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3884 | svchost.exe | GET | 200 | 2.16.164.81:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7164 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3884 | svchost.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7164 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2408 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3884 | svchost.exe | 2.16.164.81:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
3884 | svchost.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | unknown |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
5064 | SearchApp.exe | 2.21.65.132:443 | www.bing.com | Akamai International B.V. | NL | unknown |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1176 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| unknown |
www.microsoft.com |
| unknown |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| unknown |
login.live.com |
| unknown |
go.microsoft.com |
| unknown |
discord.com |
| unknown |
settings-win.data.microsoft.com |
| unknown |
slscr.update.microsoft.com |
| unknown |
fe3cr.delivery.mp.microsoft.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
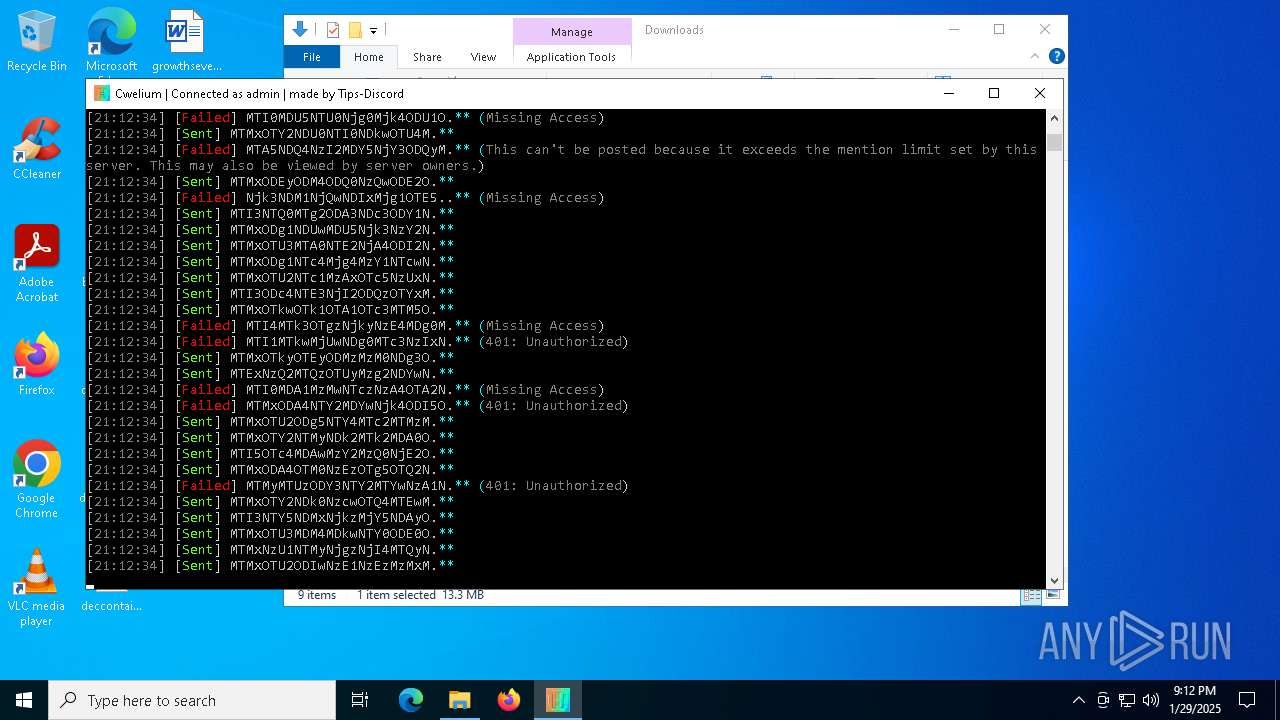
2192 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
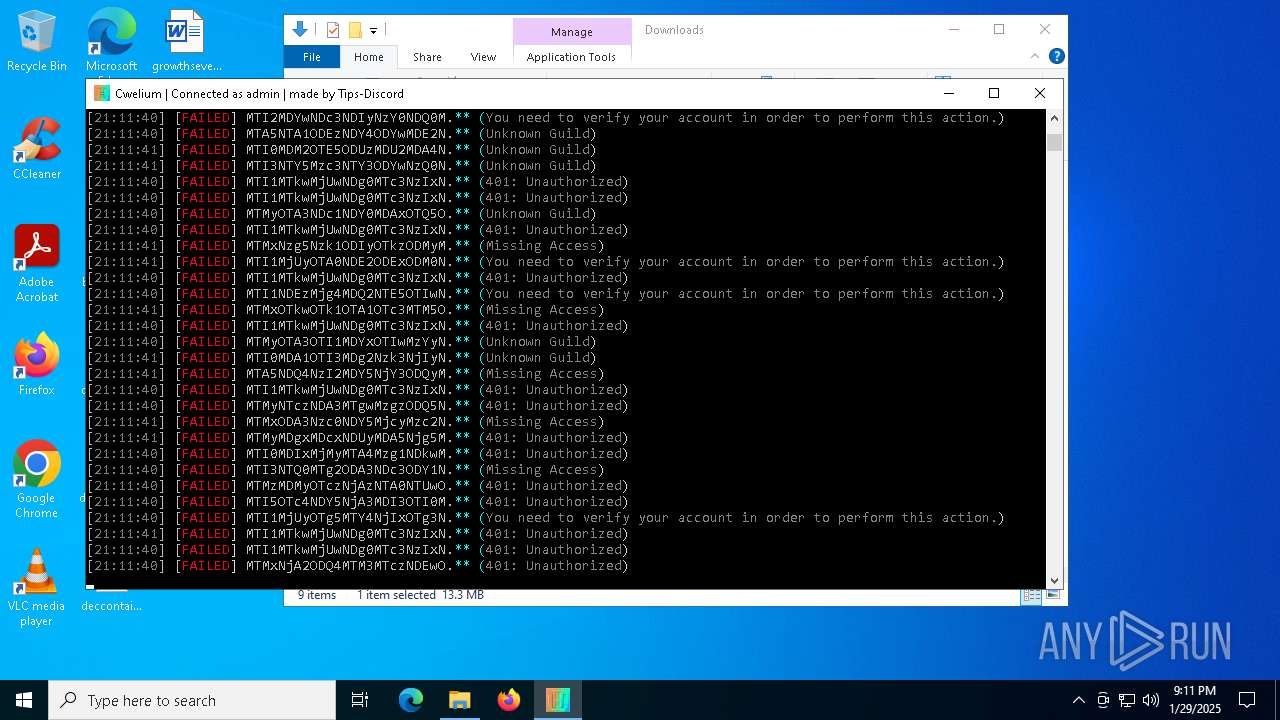
6376 | Cwelium.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
5460 | Cwelium.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
5460 | Cwelium.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
876 | Cwelium.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
876 | Cwelium.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
876 | Cwelium.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
876 | Cwelium.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
876 | Cwelium.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
876 | Cwelium.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |