| File name: | b50d83820a5704522fee59164d7bc69bea5c834ebd9be7fd8ad35b040910807f |
| Full analysis: | https://app.any.run/tasks/bc37caf7-5cb2-4fd2-82c3-41fdc4d7d6de |
| Verdict: | Malicious activity |
| Analysis date: | February 28, 2020, 02:02:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (DLL) (GUI) Intel 80386, for MS Windows |
| MD5: | AB95209E7CF8EB2079E50B503C296E8B |
| SHA1: | 8F93F250CDF406C1E1D93809754E369C9AB139CA |
| SHA256: | B50D83820A5704522FEE59164D7BC69BEA5C834EBD9BE7FD8AD35B040910807F |
| SSDEEP: | 6144:YrDmCDfEXR6x6RAntistIlz+gyhAOpJLY+ozz1noZVWZuRmh:YWCDfEXY6RAntlNgYLR2n96mh |
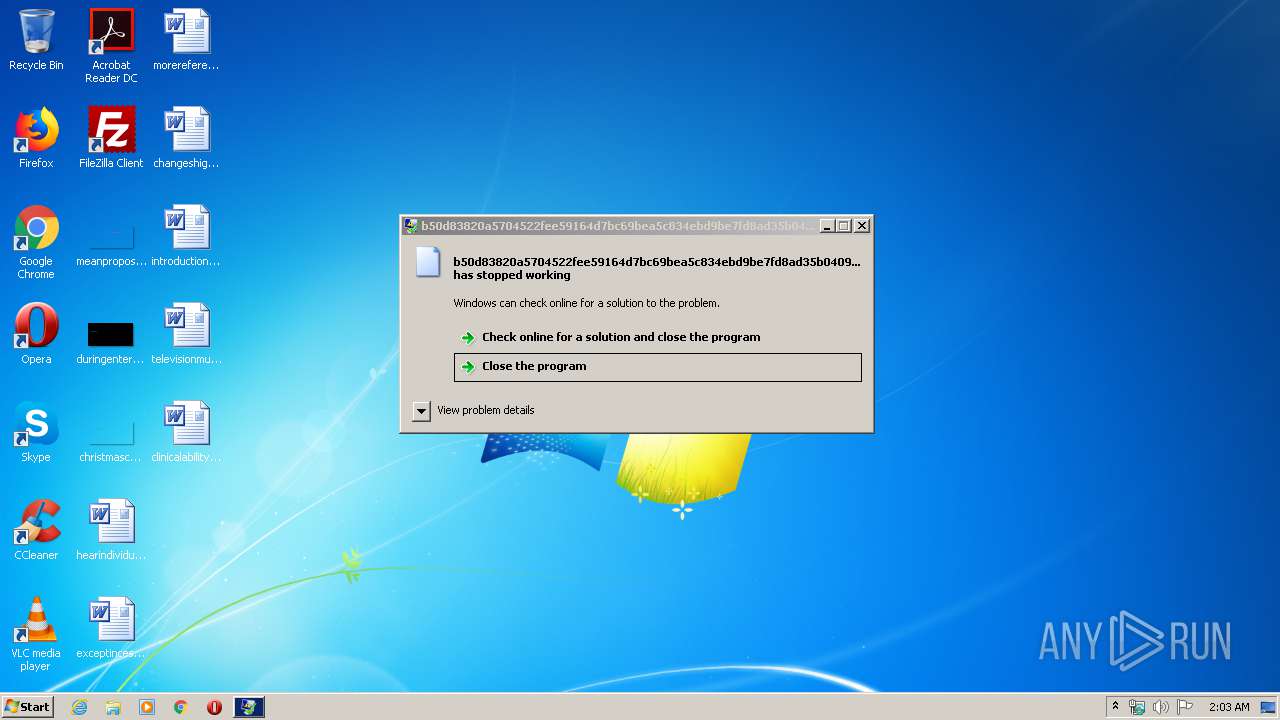
MALICIOUS
Loads dropped or rewritten executable
- WerFault.exe (PID: 3284)
- svchost.exe (PID: 860)
- explorer.exe (PID: 372)
- rundll32.exe (PID: 3168)
SUSPICIOUS
Uses RUNDLL32.EXE to load library
- explorer.exe (PID: 372)
- cmd.exe (PID: 3692)
Starts CMD.EXE for commands execution
- explorer.exe (PID: 372)
Reads Internet Cache Settings
- rundll32.exe (PID: 3168)
Connects to server without host name
- rundll32.exe (PID: 3168)
INFO
Loads main object executable
- rundll32.exe (PID: 3240)
Manual execution by user
- explorer.exe (PID: 2628)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:12:11 10:05:40+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 174080 |
| InitializedDataSize: | 162304 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xdb51 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 11-Dec-2018 09:05:40 |
| Detected languages: |
|
| Debug artifacts: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 11-Dec-2018 09:05:40 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0002A7D6 | 0x0002A800 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.68326 |
.rdata | 0x0002C000 | 0x00011AFC | 0x00011C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.6178 |
.data | 0x0003E000 | 0x00013478 | 0x00012600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 6.66057 |
.rsrc | 0x00052000 | 0x000001E0 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.71141 |
.reloc | 0x00053000 | 0x00002554 | 0x00002600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.52343 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
2 | 4.91161 | 381 | UNKNOWN | English - United States | RT_MANIFEST |
Imports
KERNEL32.dll |
Exports
Title | Ordinal | Address |
|---|---|---|
displayAsciiArt | 1 | 0x00009010 |
displayChunkNames | 2 | 0x00008D00 |
displayFilterTypes | 3 | 0x00009280 |
displayPNGInfo | 4 | 0x00008720 |
get_shellcode | 5 | 0x00009800 |
main | 6 | 0x00009830 |
Total processes
41
Monitored processes
7
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 372 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 860 | C:\Windows\system32\svchost.exe -k netsvcs | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2628 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3168 | rundll32 b50d83820a5704522fee59164d7bc69bea5c834ebd9be7fd8ad35b040910807f.exe main | C:\Windows\system32\rundll32.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3240 | "C:\Windows\System32\rundll32.exe" "C:\Users\admin\b50d83820a5704522fee59164d7bc69bea5c834ebd9be7fd8ad35b040910807f.exe", displayAsciiArt | C:\Windows\System32\rundll32.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 3221225477 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3284 | C:\Windows\system32\WerFault.exe -u -p 3240 -s 168 | C:\Windows\system32\WerFault.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3692 | "cmd.exe" /s /k pushd "C:\Users\admin" | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
731
Read events
348
Write events
383
Delete events
0
Modification events
| (PID) Process: | (372) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (372) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | @"%windir%\System32\ie4uinit.exe",-738 |
Value: Start Internet Explorer without ActiveX controls or browser extensions. | |||
| (PID) Process: | (372) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | @%windir%\Explorer.exe,-312 |
Value: Play and manage games on your computer. | |||
| (PID) Process: | (372) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.lnk\OpenWithProgids |
| Operation: | write | Name: | lnkfile |
Value: | |||
| (PID) Process: | (372) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | {S38OS404-1Q43-42S2-9305-67QR0O28SP23}\rkcybere.rkr |
Value: 000000000B00000018000000868F0F00000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFFD0553644DBEDD50100000000 | |||
| (PID) Process: | (372) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000400000004F000000E1B725000B00000018000000868F0F007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E006500780065000000E72FC477822EC477B8F9D1765102000060000000B7B34E7002000000800200000000000014DC82070BA07476F0AE3706E06F0F02800200000D0000002F000000AF020000F0AE370634DC82074319D2769FB13706009E10035E000000F0AE3706E06F0F02AF020000B8F9D176C0271002C027100244DC82076419D276E06F0F02009E1003DCE08207BF43D276E06F0F020000000000000000FFFFFFFF000000000000000000000000009E1003189E1003009E1003429E10030000000000000000000000000000D27600D81A0310AF100328E18207BF43D27600D81A030000000000000000FFFFFFFF00000000000000000000000010AF100328AF100310AF100352AF10036B1C0000AD077100E8DC820733ABC477AD2F3FBA070C0000102700001B000000065602001CDD8207F8AAC47706560200AD0771003CDD8207603F1102BCDD820700000000A4010000150200001B000000030000000200000044DD8207FDE1C375E40700003CDD8207E40702001C00020003001B0015021B00D0553644DBEDD5016CDD820757C1D57658DD8207BCDD820762C1D576E407020005001C000B00000018000000868F0F007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E006500780065000000E72FC477822EC477B8F9D1765102000060000000B7B34E7002000000800200000000000014DC82070BA07476F0AE3706E06F0F02800200000D0000002F000000AF020000F0AE370634DC82074319D2769FB13706009E10035E000000F0AE3706E06F0F02AF020000B8F9D176C0271002C027100244DC82076419D276E06F0F02009E1003DCE08207BF43D276E06F0F020000000000000000FFFFFFFF000000000000000000000000009E1003189E1003009E1003429E10030000000000000000000000000000D27600D81A0310AF100328E18207BF43D27600D81A030000000000000000FFFFFFFF00000000000000000000000010AF100328AF100310AF100352AF10036B1C0000AD077100E8DC820733ABC477AD2F3FBA070C0000102700001B000000065602001CDD8207F8AAC47706560200AD0771003CDD8207603F1102BCDD820700000000A4010000150200001B000000030000000200000044DD8207FDE1C375E40700003CDD8207E40702001C00020003001B0015021B00D0553644DBEDD5016CDD820757C1D57658DD8207BCDD820762C1D576E407020005001C000B00000018000000868F0F007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E006500780065000000E72FC477822EC477B8F9D1765102000060000000B7B34E7002000000800200000000000014DC82070BA07476F0AE3706E06F0F02800200000D0000002F000000AF020000F0AE370634DC82074319D2769FB13706009E10035E000000F0AE3706E06F0F02AF020000B8F9D176C0271002C027100244DC82076419D276E06F0F02009E1003DCE08207BF43D276E06F0F020000000000000000FFFFFFFF000000000000000000000000009E1003189E1003009E1003429E10030000000000000000000000000000D27600D81A0310AF100328E18207BF43D27600D81A030000000000000000FFFFFFFF00000000000000000000000010AF100328AF100310AF100352AF10036B1C0000AD077100E8DC820733ABC477AD2F3FBA070C0000102700001B000000065602001CDD8207F8AAC47706560200AD0771003CDD8207603F1102BCDD820700000000A4010000150200001B000000030000000200000044DD8207FDE1C375E40700003CDD8207E40702001C00020003001B0015021B00D0553644DBEDD5016CDD820757C1D57658DD8207BCDD820762C1D576E407020005001C00 | |||
| (PID) Process: | (372) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | {9R3995NO-1S9P-4S13-O827-48O24O6P7174}\GnfxOne\Jvaqbjf Rkcybere.yax |
Value: 000000000B000000000000000A000000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFFC09F3844DBEDD50100000000 | |||
| (PID) Process: | (372) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 000000002200000000000000210000000B000000000000000A0000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C00570069006E0064006F007700730020004500780070006C006F007200650072002E006C006E006B0000000000000014DC82070BA07476F0AE3706E06F0F02800200000D0000002F000000AF020000F0AE370634DC82074319D2769FB13706009E10035E000000F0AE3706E06F0F02AF020000B8F9D176C0271002C027100244DC82076419D276E06F0F02009E1003DCE08207BF43D276E06F0F020000000000000000FFFFFFFF000000000000000000000000009E1003189E1003009E1003429E10030000000000000000000000000000D27600D81A0310AF100328E18207BF43D27600D81A030000000000000000FFFFFFFF00000000000000000000000010AF100328AF100310AF100352AF10036B1C0000BC077100E8DC820733ABC477BC2F3FBA070C0000102700001B000000065602001CDD8207F8AAC47706560200BC0771003CDD8207484A1102BCDD820700000000A4010000240200001B000000030000000200000044DD8207FDE1C375E40700003CDD8207E40702001C00020003001B0024021B00C09F3844DBEDD5016CDD820757C1D57658DD8207BCDD820762C1D576E407020005001C000B000000000000000A0000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C00570069006E0064006F007700730020004500780070006C006F007200650072002E006C006E006B0000000000000014DC82070BA07476F0AE3706E06F0F02800200000D0000002F000000AF020000F0AE370634DC82074319D2769FB13706009E10035E000000F0AE3706E06F0F02AF020000B8F9D176C0271002C027100244DC82076419D276E06F0F02009E1003DCE08207BF43D276E06F0F020000000000000000FFFFFFFF000000000000000000000000009E1003189E1003009E1003429E10030000000000000000000000000000D27600D81A0310AF100328E18207BF43D27600D81A030000000000000000FFFFFFFF00000000000000000000000010AF100328AF100310AF100352AF10036B1C0000BC077100E8DC820733ABC477BC2F3FBA070C0000102700001B000000065602001CDD8207F8AAC47706560200BC0771003CDD8207484A1102BCDD820700000000A4010000240200001B000000030000000200000044DD8207FDE1C375E40700003CDD8207E40702001C00020003001B0024021B00C09F3844DBEDD5016CDD820757C1D57658DD8207BCDD820762C1D576E407020005001C000B000000000000000A0000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C00570069006E0064006F007700730020004500780070006C006F007200650072002E006C006E006B0000000000000014DC82070BA07476F0AE3706E06F0F02800200000D0000002F000000AF020000F0AE370634DC82074319D2769FB13706009E10035E000000F0AE3706E06F0F02AF020000B8F9D176C0271002C027100244DC82076419D276E06F0F02009E1003DCE08207BF43D276E06F0F020000000000000000FFFFFFFF000000000000000000000000009E1003189E1003009E1003429E10030000000000000000000000000000D27600D81A0310AF100328E18207BF43D27600D81A030000000000000000FFFFFFFF00000000000000000000000010AF100328AF100310AF100352AF10036B1C0000BC077100E8DC820733ABC477BC2F3FBA070C0000102700001B000000065602001CDD8207F8AAC47706560200BC0771003CDD8207484A1102BCDD820700000000A4010000240200001B000000030000000200000044DD8207FDE1C375E40700003CDD8207E40702001C00020003001B0024021B00C09F3844DBEDD5016CDD820757C1D57658DD8207BCDD820762C1D576E407020005001C00 | |||
| (PID) Process: | (372) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | {9R3995NO-1S9P-4S13-O827-48O24O6P7174}\GnfxOne\Jvaqbjf Rkcybere.yax |
Value: 000000000B000000000000000B000000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFFC09F3844DBEDD50100000000 | |||
| (PID) Process: | (372) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 000000002200000000000000220000000B000000000000000B0000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C00570069006E0064006F007700730020004500780070006C006F007200650072002E006C006E006B0000006C006E006B0000000000000014DC82070BA07476F0AE3706E06F0F02800200000D0000002F000000AF020000F0AE370634DC82074319D2769FB13706009E10035E000000F0AE3706E06F0F02AF020000B8F9D176C0271002C027100244DC82076419D276E06F0F02009E1003DCE08207BF43D276E06F0F020000000000000000FFFFFFFF000000000000000000000000009E1003189E1003009E1003429E10030000000000000000000000000000D27600D81A0310AF100328E18207BF43D27600D81A030000000000000000FFFFFFFF00000000000000000000000010AF100328AF100310AF100352AF10036B1C0000BC077100E8DC820733ABC477BC2F3FBA070C0000102700001B000000065602001CDD8207F8AAC47706560200BC0771003CDD8207484A1102BCDD820700000000A40100007CDD0000C0606BAD2CDD82078291D2767CDD820730DD82072795D27600000000D44E110258DD8207CD94D276D44E110204DE8207484A1102E194D27600000000484A110204DE820760DD82070B000000000000000B0000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C00570069006E0064006F007700730020004500780070006C006F007200650072002E006C006E006B0000006C006E006B0000000000000014DC82070BA07476F0AE3706E06F0F02800200000D0000002F000000AF020000F0AE370634DC82074319D2769FB13706009E10035E000000F0AE3706E06F0F02AF020000B8F9D176C0271002C027100244DC82076419D276E06F0F02009E1003DCE08207BF43D276E06F0F020000000000000000FFFFFFFF000000000000000000000000009E1003189E1003009E1003429E10030000000000000000000000000000D27600D81A0310AF100328E18207BF43D27600D81A030000000000000000FFFFFFFF00000000000000000000000010AF100328AF100310AF100352AF10036B1C0000BC077100E8DC820733ABC477BC2F3FBA070C0000102700001B000000065602001CDD8207F8AAC47706560200BC0771003CDD8207484A1102BCDD820700000000A40100007CDD0000C0606BAD2CDD82078291D2767CDD820730DD82072795D27600000000D44E110258DD8207CD94D276D44E110204DE8207484A1102E194D27600000000484A110204DE820760DD82070B000000000000000B0000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C00570069006E0064006F007700730020004500780070006C006F007200650072002E006C006E006B0000006C006E006B0000000000000014DC82070BA07476F0AE3706E06F0F02800200000D0000002F000000AF020000F0AE370634DC82074319D2769FB13706009E10035E000000F0AE3706E06F0F02AF020000B8F9D176C0271002C027100244DC82076419D276E06F0F02009E1003DCE08207BF43D276E06F0F020000000000000000FFFFFFFF000000000000000000000000009E1003189E1003009E1003429E10030000000000000000000000000000D27600D81A0310AF100328E18207BF43D27600D81A030000000000000000FFFFFFFF00000000000000000000000010AF100328AF100310AF100352AF10036B1C0000BC077100E8DC820733ABC477BC2F3FBA070C0000102700001B000000065602001CDD8207F8AAC47706560200BC0771003CDD8207484A1102BCDD820700000000A40100007CDD0000C0606BAD2CDD82078291D2767CDD820730DD82072795D27600000000D44E110258DD8207CD94D276D44E110204DE8207484A1102E194D27600000000484A110204DE820760DD8207 | |||
Executable files
0
Suspicious files
5
Text files
0
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 860 | svchost.exe | C:\Windows\SoftwareDistribution\DataStore\DataStore.edb | — | |
MD5:— | SHA256:— | |||
| 860 | svchost.exe | C:\Windows\appcompat\programs\RecentFileCache.bcf | txt | |
MD5:— | SHA256:— | |||
| 3284 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\rundll32.exe.3240.dmp | dmp | |
MD5:— | SHA256:— | |||
| 3284 | WerFault.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WER\ReportArchive\AppCrash_rundll32.exe_b50_8f2642348cb645f92bb0c8ed71e63c8f5585f_0c729553\Report.wer | binary | |
MD5:— | SHA256:— | |||
| 860 | svchost.exe | C:\Windows\SoftwareDistribution\DataStore\Logs\edb.chk | binary | |
MD5:— | SHA256:— | |||
| 860 | svchost.exe | C:\Windows\SoftwareDistribution\DataStore\Logs\edb.log | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
13
DNS requests
0
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3168 | rundll32.exe | POST | — | 45.67.231.169:80 | http://45.67.231.169/ | unknown | — | — | unknown |
3168 | rundll32.exe | POST | — | 45.67.231.169:80 | http://45.67.231.169/ | unknown | — | — | unknown |
3168 | rundll32.exe | POST | — | 193.228.52.57:80 | http://193.228.52.57/ | AT | — | — | unknown |
3168 | rundll32.exe | POST | — | 193.228.52.57:80 | http://193.228.52.57/ | AT | — | — | unknown |
3168 | rundll32.exe | POST | — | 45.67.231.169:80 | http://45.67.231.169/ | unknown | — | — | unknown |
3168 | rundll32.exe | POST | — | 193.228.52.57:80 | http://193.228.52.57/ | AT | — | — | unknown |
3168 | rundll32.exe | POST | — | 45.67.231.169:80 | http://45.67.231.169/ | unknown | — | — | unknown |
3168 | rundll32.exe | POST | — | 45.67.231.169:80 | http://45.67.231.169/ | unknown | — | — | unknown |
3168 | rundll32.exe | POST | — | 45.67.231.169:80 | http://45.67.231.169/ | unknown | — | — | unknown |
3168 | rundll32.exe | POST | — | 193.228.52.57:80 | http://193.228.52.57/ | AT | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3168 | rundll32.exe | 45.67.231.169:80 | — | — | — | unknown |
3168 | rundll32.exe | 193.228.52.57:80 | — | — | AT | unknown |