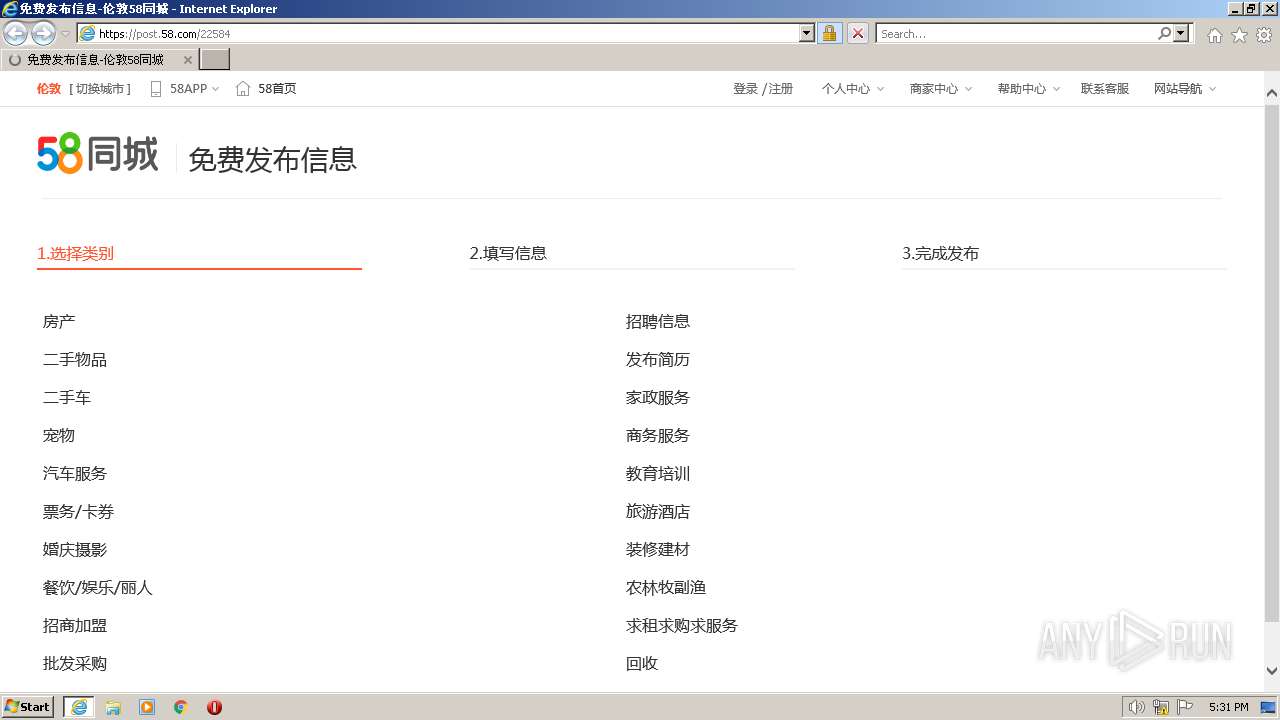
| URL: | https://post.58.com |
| Full analysis: | https://app.any.run/tasks/33e22b67-88e6-4d53-8fb7-e16e28ad33e0 |
| Verdict: | Malicious activity |
| Analysis date: | June 20, 2023, 16:30:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | B3A6AD4AFA433C6888752EF55206EAAA |
| SHA1: | 5ADEEAFF76CCBB8496CC7FEE08E2D01F7452E131 |
| SHA256: | B4F786A75C402FE8452FCA15DCD0E155C70AA59FC0D1A5E3A07F920FA50A1AC8 |
| SSDEEP: | 3:N8OC:2OC |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 1008)
The process uses the downloaded file
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 3348)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
41
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1008 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://post.58.com" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2644 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1008 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3348 | C:\Windows\system32\Macromed\Flash\FlashUtil32_32_0_0_453_ActiveX.exe -Embedding | C:\Windows\System32\Macromed\Flash\FlashUtil32_32_0_0_453_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 32.0 r0 Exit code: 0 Version: 32,0,0,453 Modules
| |||||||||||||||
Total events
20 929
Read events
20 813
Write events
112
Delete events
4
Modification events
| (PID) Process: | (1008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (1008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (1008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (1008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1008) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
62
Text files
89
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2644 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 2644 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\349D186F1CB5682FA0194D4F3754EF36_5CF06D1C7E0DD67BC0AF8842F6720BCA | binary | |
MD5:BC2309F33641247EB436F0321BEA0CD5 | SHA256:0FD8971A8B28F60A2FE3828E0F572140414E7E8F8BFB8E660C1CFE877D0DBE0B | |||
| 2644 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:30A72C71D9173534BB930A6EDB439243 | SHA256:18136E3C2421E780D80E5B463C1AFCABAB77BA0215F9FA308C52FF8C1B52BFE5 | |||
| 2644 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\349D186F1CB5682FA0194D4F3754EF36_EEF528AD7517EEF440A4023E7C0294E0 | binary | |
MD5:94B6D7791B65C0521A65406074B995DC | SHA256:F0D5BDC21059D1C4A546CACA6927CF06DB34F53FDB5F38C0CDF16FADE48E5AD8 | |||
| 2644 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\ComponentsLoader_v20230504110709[1].js | text | |
MD5:E69F1A6DCDFF19902ED7D00F90918D38 | SHA256:751BBB9632A0F21D1A4C6A4DB674CC8860A40219366368380C0E3EAF6D2027C0 | |||
| 2644 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\22584[1].htm | html | |
MD5:1E8EBAAD103D93AF05F1441069EAA656 | SHA256:8D2AA994E080C033D4CEB70D0CEF8FD0A18765E9DD7708E9FE2B2F677CF6C64E | |||
| 2644 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\DNLK2JAZ.htm | html | |
MD5:4AC9E703939DBD661639CD5E01E70EA6 | SHA256:C638A503BA76619736944A5A9E97BDCFFDF58F30F051C635A124D3290A1D2EED | |||
| 2644 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\es5-shim.min[1].js | text | |
MD5:8183A6498EA74AC1906E38293814035E | SHA256:EDB48406D115BC1C57CD5018A616496516D6296908C08A83AF948F29745D7E6D | |||
| 2644 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B039FEA45CB4CC4BBACFC013C7C55604_50D7940D5D3FEDD8634D83074C7A46A3 | binary | |
MD5:4D0585FE60658B8BFA933ED4B793BDC7 | SHA256:E72DC6427EC51258E2EA1259C86B96F766E1AA84E14CE7C0C603B0CE0E399DBD | |||
| 2644 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\logo-o[1].png | image | |
MD5:9C987C7EEA4DEF87124B581492392389 | SHA256:DBBF049737E9C5BE22382A0123FBE4785131CA6B5DA0540F0CD4CB07D7DE7910 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
113
DNS requests
38
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2644 | iexplore.exe | GET | — | 104.18.21.226:80 | http://ocsp.globalsign.com/gsrsaovsslca2018/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBRrcGT%2BanRD3C1tW3nsrKeuXC7DPwQU%2BO9%2F8s14Z6jeb48kjYjxhwMCs%2BsCDDiMjVH447tH8EfGWQ%3D%3D | US | — | — | whitelisted |
2644 | iexplore.exe | GET | 200 | 104.18.21.226:80 | http://ocsp2.globalsign.com/rootr3/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCDQHuXyId%2FGI71DM6hVc%3D | US | der | 1.40 Kb | whitelisted |
1008 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | binary | 1.47 Kb | whitelisted |
1008 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
1008 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | binary | 1.47 Kb | whitelisted |
2644 | iexplore.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/rootr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCDQHuXxad%2F5c1K2Rl1mo%3D | US | binary | 1.41 Kb | whitelisted |
2644 | iexplore.exe | GET | 200 | 163.181.56.157:80 | http://ocsp.digicert.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbJNRrm8KxusAb7DCqnMkE%3D | US | binary | 471 b | whitelisted |
1008 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEALnkXH7gCHpP%2BLZg4NMUMA%3D | US | binary | 471 b | whitelisted |
2644 | iexplore.exe | GET | 200 | 163.181.56.157:80 | http://ocsp.digicert.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQhnxEBNL9LgIhfSsTcHsrTt204QgQURNnISjOO01KNp5KUYR%2BayKW37MsCEAKkCO%2FNVFmpdj6tg5BH5d4%3D | US | binary | 471 b | whitelisted |
2644 | iexplore.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | US | binary | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2644 | iexplore.exe | 42.187.161.231:443 | post.58.com | Shenzhen Tencent Computer Systems Company Limited | CN | unknown |
568 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2644 | iexplore.exe | 152.195.133.24:80 | ctldl.windowsupdate.com | EDGECAST | US | malicious |
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2644 | iexplore.exe | 104.18.21.226:80 | ocsp.globalsign.com | CLOUDFLARENET | — | shared |
2644 | iexplore.exe | 203.205.239.154:443 | mp.weixin.qq.com | Tencent Building, Kejizhongyi Avenue | HK | unknown |
1008 | iexplore.exe | 2.18.66.177:443 | www.bing.com | Akamai International B.V. | GB | unknown |
2644 | iexplore.exe | 42.187.161.138:443 | tracklog.58.com | Shenzhen Tencent Computer Systems Company Limited | CN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
post.58.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
ocsp2.globalsign.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.globalsign.com |
| whitelisted |
c.58cdn.com.cn |
| suspicious |
j2.58cdn.com.cn |
| suspicious |
j1.58cdn.com.cn |
| suspicious |