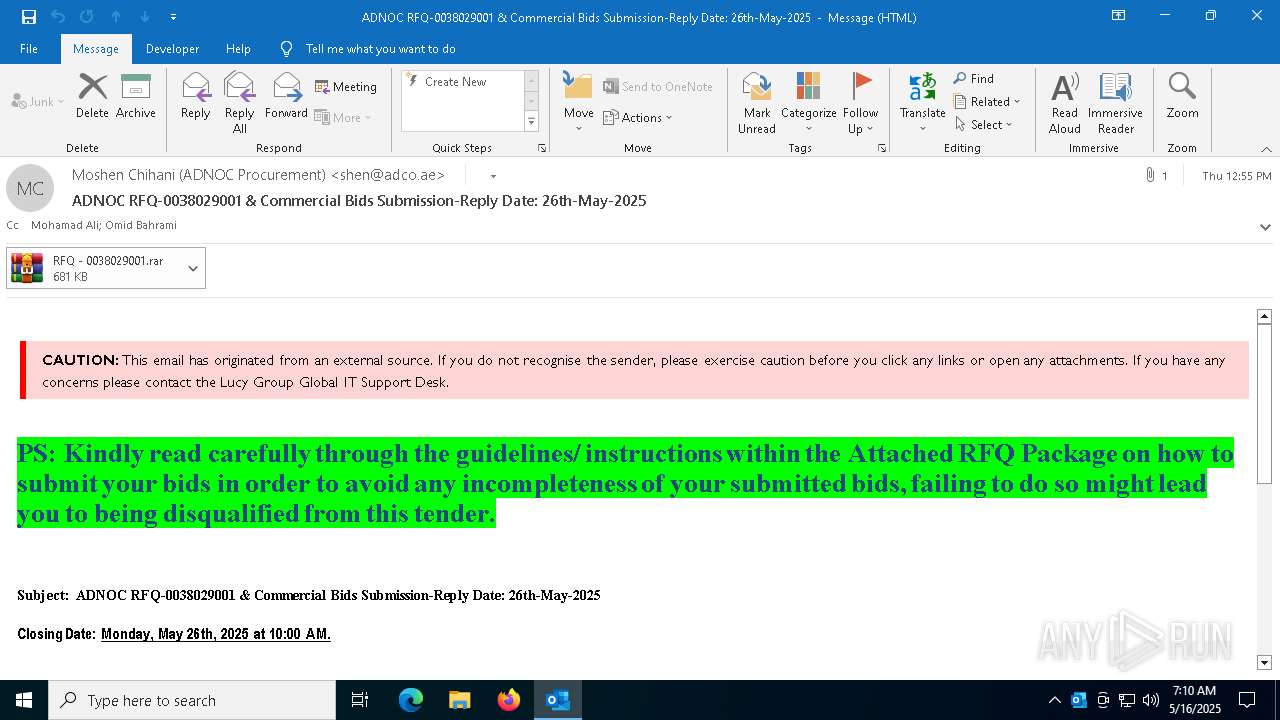
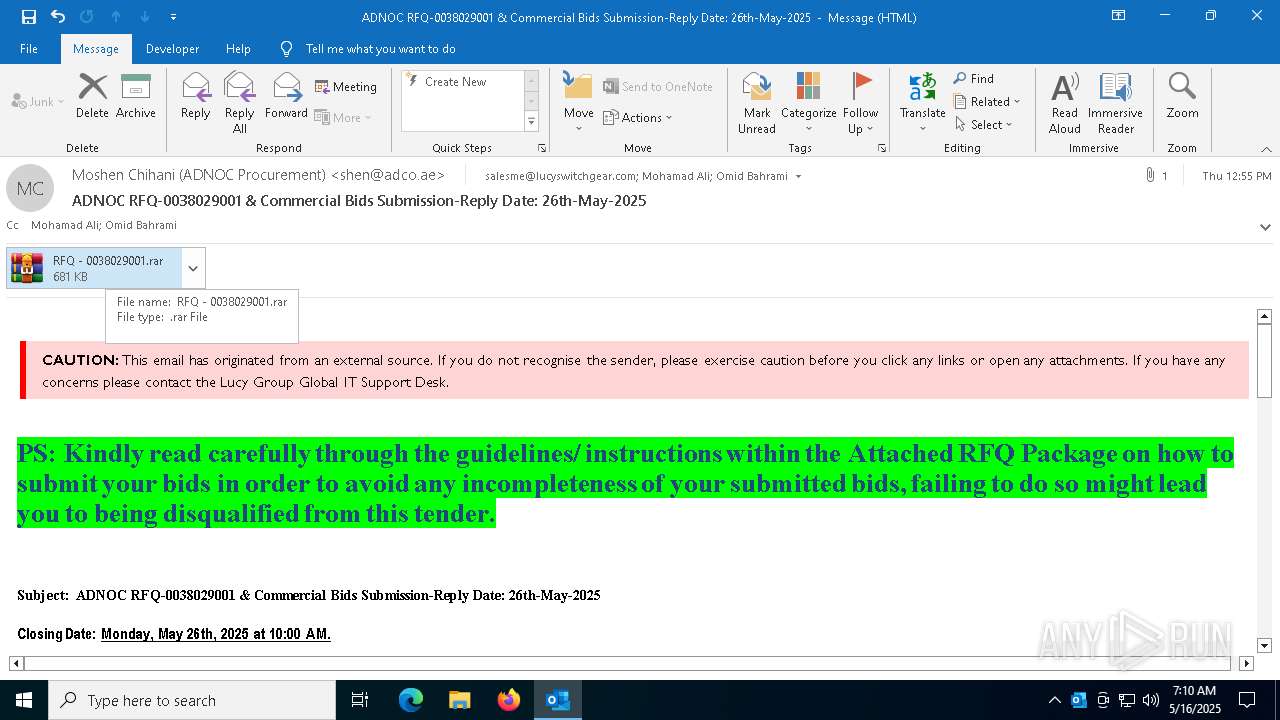
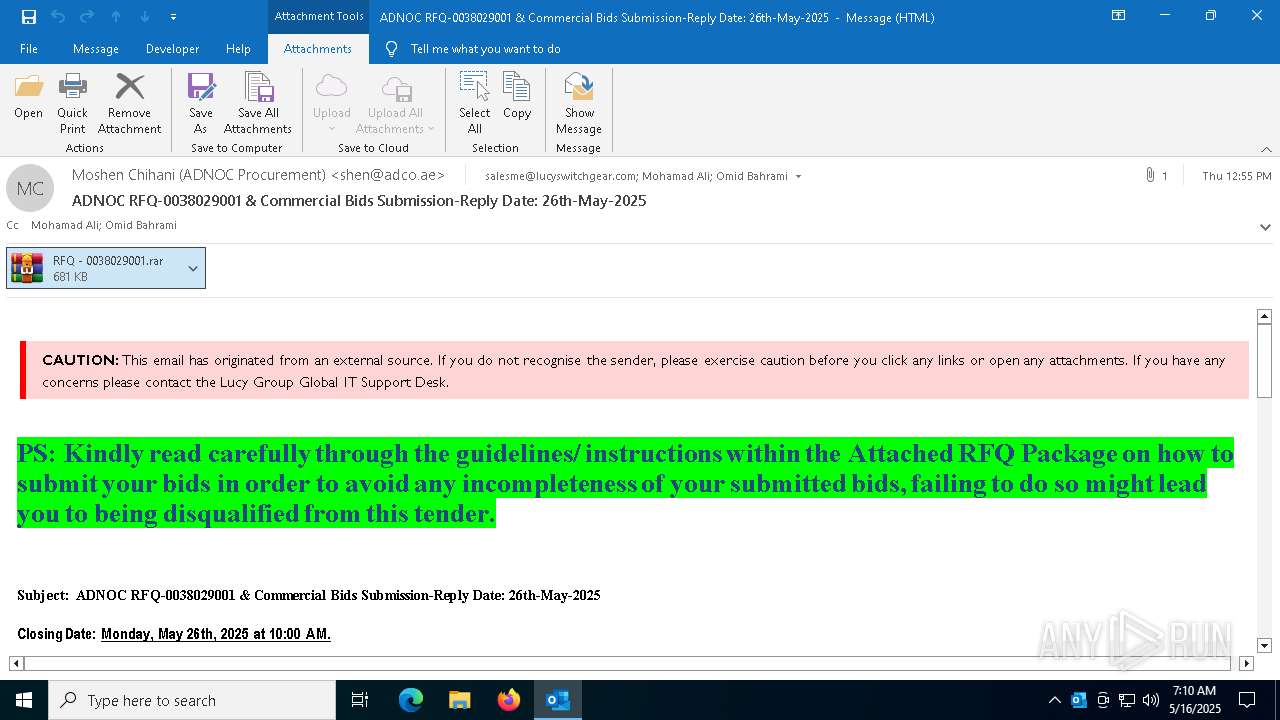
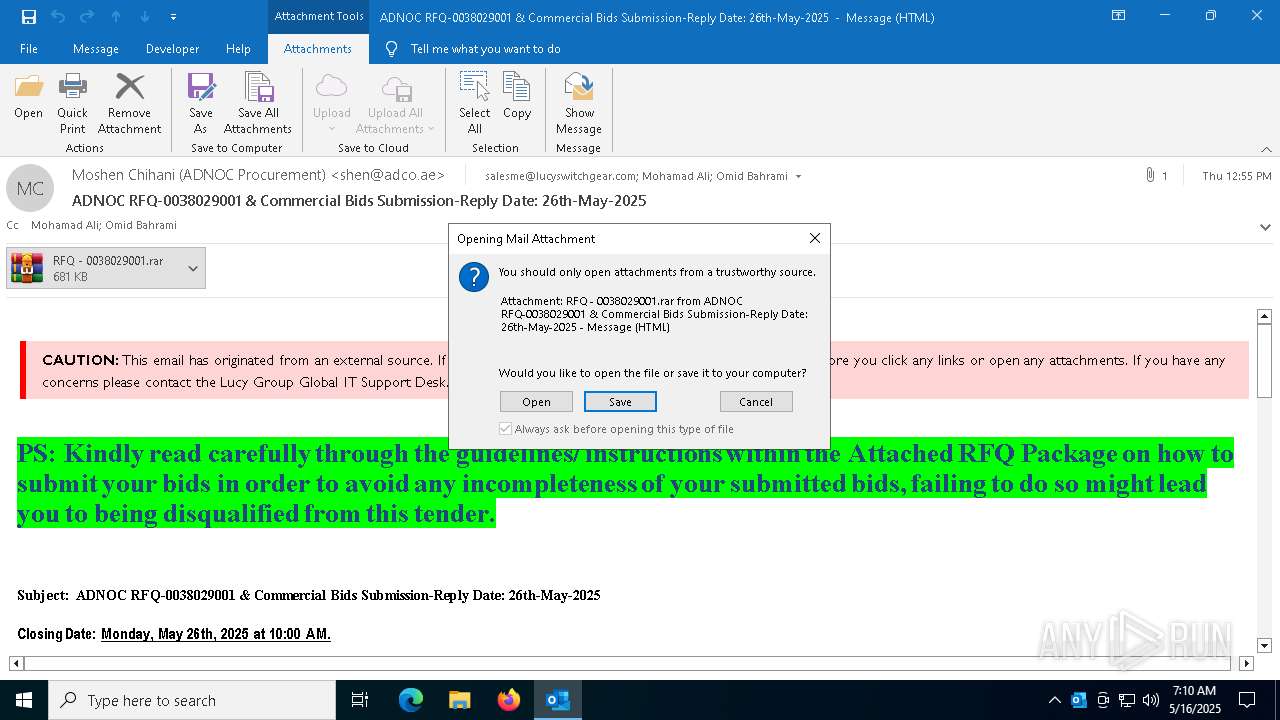
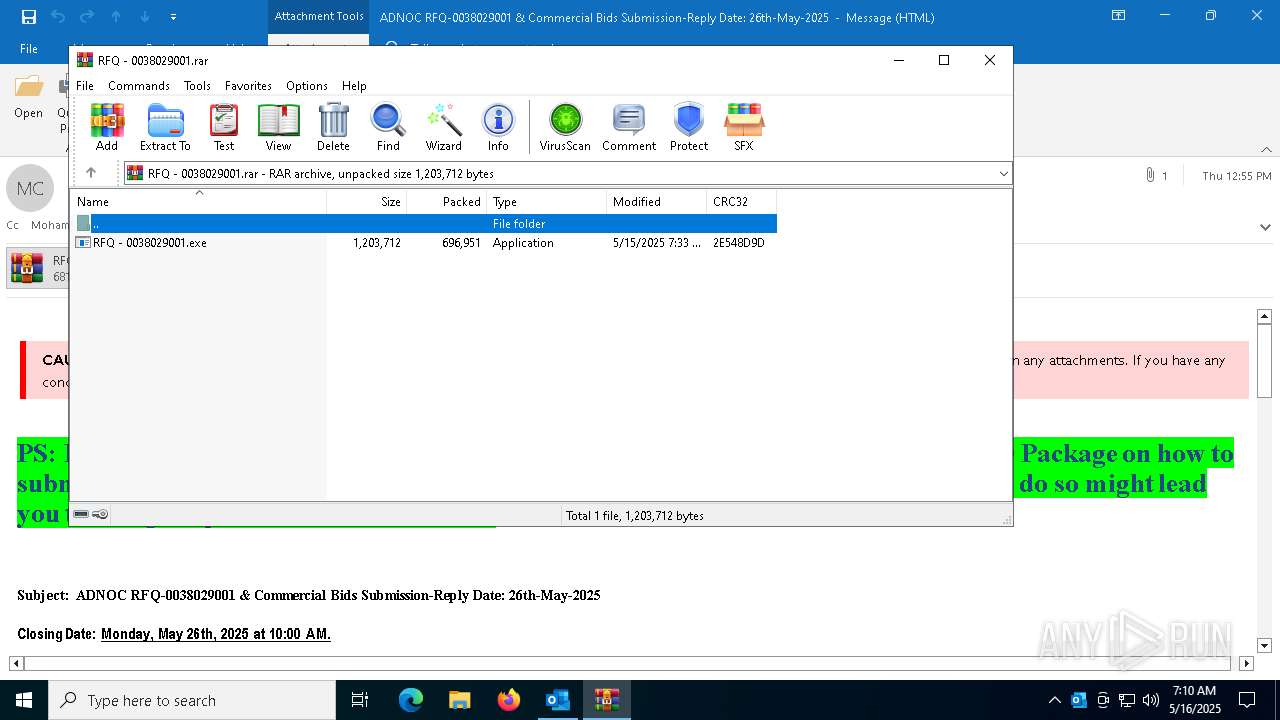
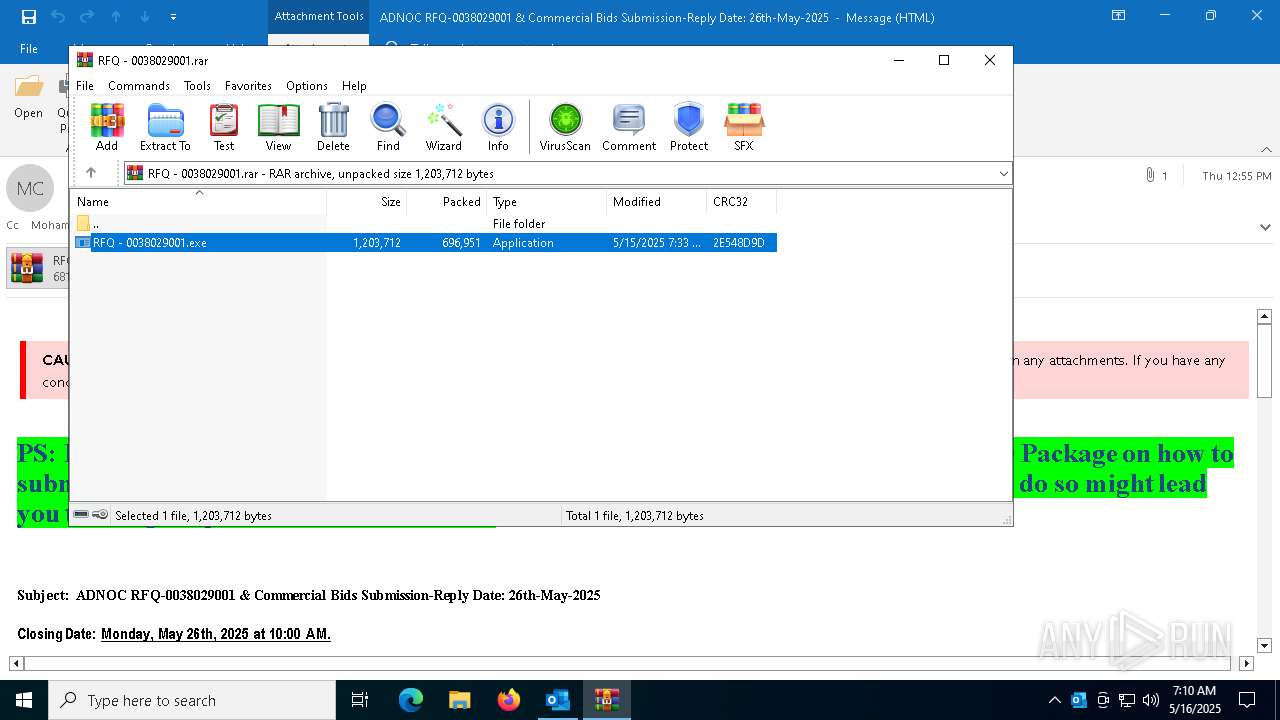
| File name: | 251f689c-49c7-d6ad-ed12-43401ecc7965.eml |
| Full analysis: | https://app.any.run/tasks/ff059217-614d-4d4e-bef8-398011205e73 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 07:10:12 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with CRLF line terminators |
| MD5: | 8FDE8002A271EC4B3FDD363C71F48627 |
| SHA1: | 55C26EFB0F8EAD3B222C4ACBF665E34F2A1CB30B |
| SHA256: | B4DC8DFF2EBA9E568B3805D7C315E37DFC7546316E25812014F37D5205B6DA00 |
| SSDEEP: | 24576:puuP74kUvoDhwNyPz9TSViheWrnUmxXqZl0:kuKyPhQm0Y |
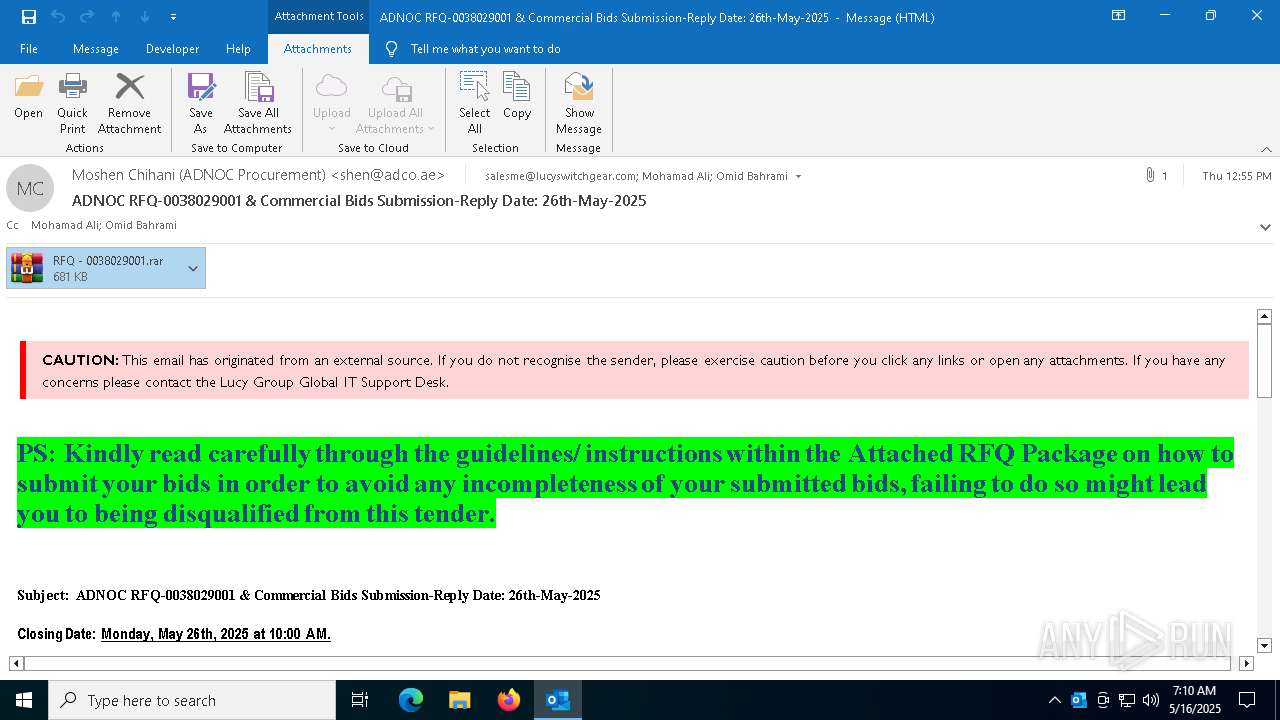
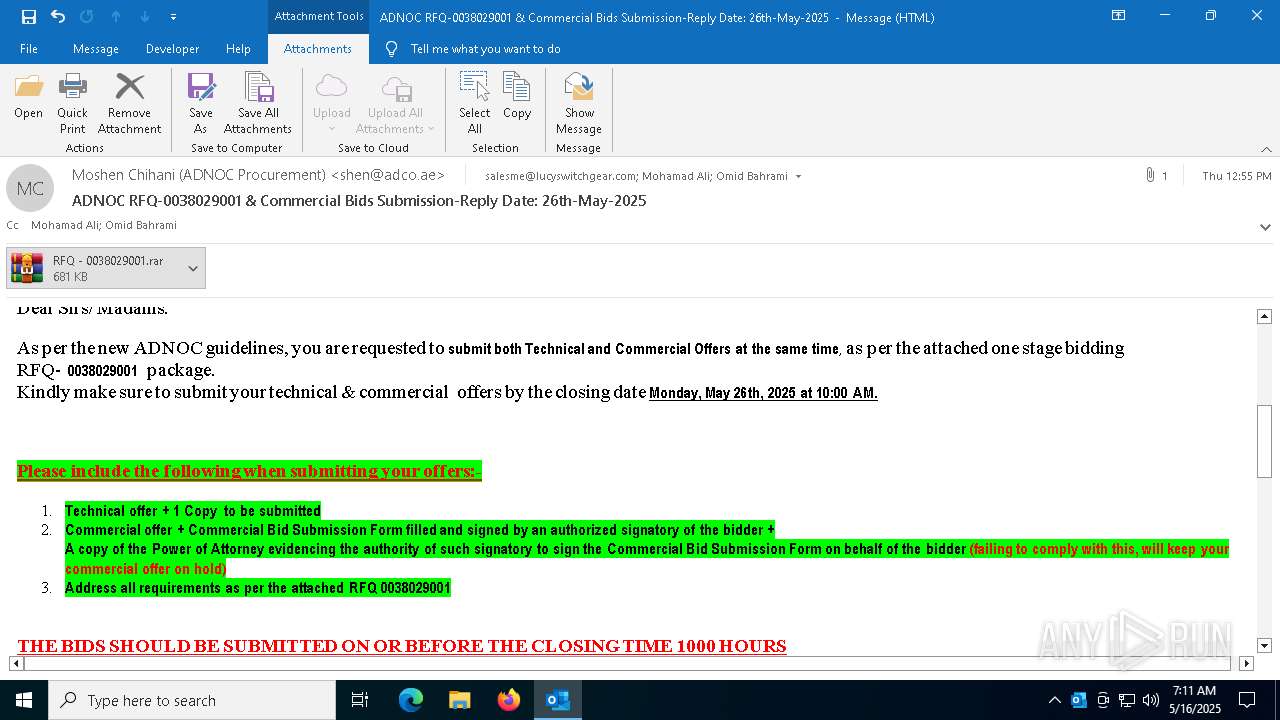
MALICIOUS
Generic archive extractor
- OUTLOOK.EXE (PID: 7192)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 8172)
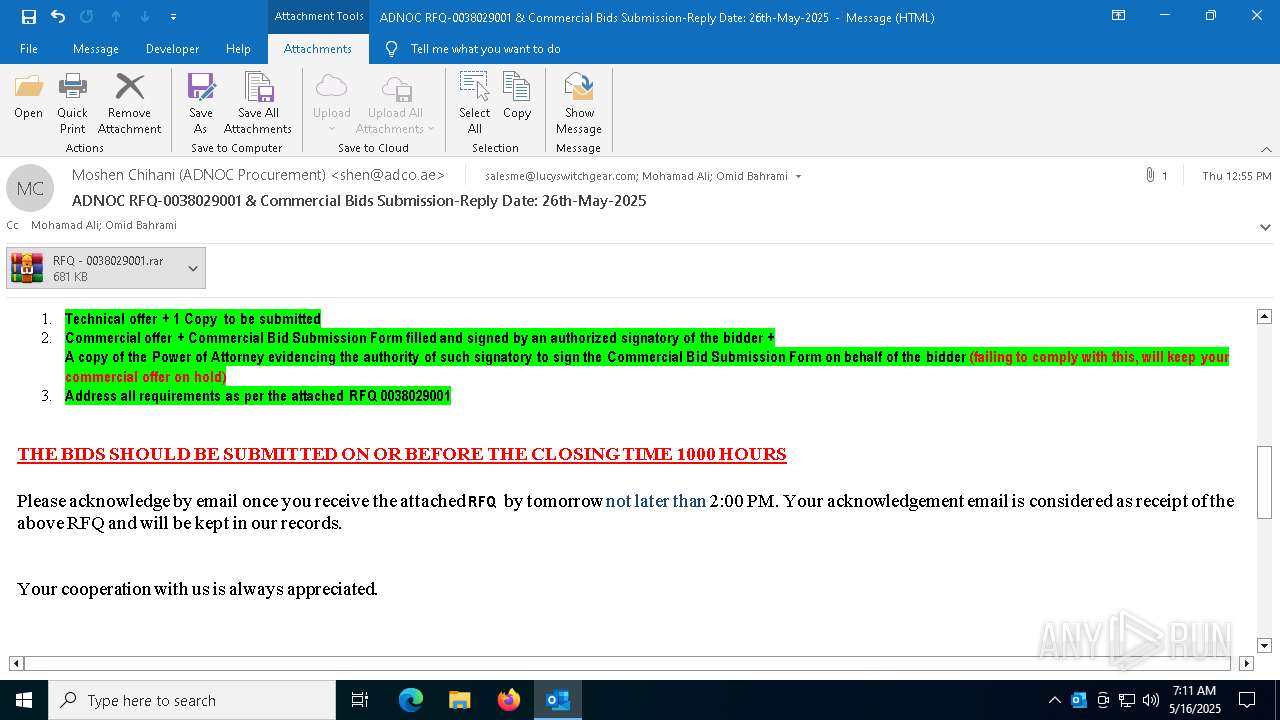
Executes application which crashes
- RFQ - 0038029001.exe (PID: 5504)
- RFQ - 0038029001.exe (PID: 7204)
INFO
The sample compiled with english language support
- OUTLOOK.EXE (PID: 7192)
- WinRAR.exe (PID: 8172)
Reads mouse settings
- RFQ - 0038029001.exe (PID: 5504)
- RFQ - 0038029001.exe (PID: 7204)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 8172)
Checks supported languages
- RFQ - 0038029001.exe (PID: 5504)
- RFQ - 0038029001.exe (PID: 7204)
Create files in a temporary directory
- RFQ - 0038029001.exe (PID: 5504)
- RFQ - 0038029001.exe (PID: 7204)
Creates files or folders in the user directory
- WerFault.exe (PID: 6644)
- WerFault.exe (PID: 1852)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
144
Monitored processes
9
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1852 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 7204 -s 720 | C:\Windows\SysWOW64\WerFault.exe | — | RFQ - 0038029001.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3900 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa8172.25051\RFQ - 0038029001.exe" | C:\Windows\SysWOW64\svchost.exe | — | RFQ - 0038029001.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 5504 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa8172.25051\RFQ - 0038029001.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa8172.25051\RFQ - 0038029001.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 5960 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa8172.25584\RFQ - 0038029001.exe" | C:\Windows\SysWOW64\svchost.exe | — | RFQ - 0038029001.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 6644 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 5504 -s 652 | C:\Windows\SysWOW64\WerFault.exe | — | RFQ - 0038029001.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7192 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml C:\Users\admin\AppData\Local\Temp\251f689c-49c7-d6ad-ed12-43401ecc7965.eml | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 7204 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa8172.25584\RFQ - 0038029001.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa8172.25584\RFQ - 0038029001.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 7800 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "B2B46FC5-8449-4E28-99EA-93FEEEA98A9D" "0FBF68CF-5C21-45C5-A26A-8040593DE227" "7192" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 8172 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\U8VKDK3B\RFQ - 0038029001.rar" | C:\Program Files\WinRAR\WinRAR.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
17 120
Read events
15 970
Write events
1 029
Delete events
121
Modification events
| (PID) Process: | (7192) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (7192) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\7192 |
| Operation: | write | Name: | 0 |
Value: 0B0E10056F0D17242D1445BBAEC45C726C2EFC230046AA9BB7BC99C6F1ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C5119838D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (7192) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (7192) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (7192) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7192) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (7192) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (7192) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (7192) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (7192) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
2
Suspicious files
19
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7192 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 7192 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\E305573D-125E-45C1-BFE1-91EDB2AB25AF | xml | |
MD5:20956021FA7A30632C677F78641B1959 | SHA256:65EB5B583A4480B664D8C3D1B68FC33CBE8D9EA30C654DC769EBD8B37A6A75CB | |||
| 7192 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:19540895F487CEAB47FCDD46B894F3A5 | SHA256:F2B4DC2F46FBDF8FB2FDBD0ECA4D725748264F8201186163454CD34EFC0BDE5E | |||
| 7192 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\olkCA76.tmp | binary | |
MD5:CACB8A8F8EAF593AC41194578F5F29A4 | SHA256:8A434A3088C8C6969713E8E58966A2091B3B2028CA9F54D08DE64E4AAC9E761D | |||
| 7192 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\U8VKDK3B\RFQ - 0038029001 (002).rar:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 7192 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_TableViewPreviewPrefs_2_4F8DD71AA01CFF439A7FF77657D0A038.dat | xml | |
MD5:0E092DB99AEE99FDFF9B5B222C732CFD | SHA256:D1614AD99ADED9F6F5C1BE7FE7FFA5124BD04A526580DA3818EA8A954E852AA6 | |||
| 6644 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_RFQ - 0038029001_dd41ce1d3ff380183b277010f12696dcc3a0af5_b8a896f0_1e69a354-0157-4723-893b-d9a6c4d774b2\Report.wer | — | |
MD5:— | SHA256:— | |||
| 7192 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\U8VKDK3B\RFQ - 0038029001.rar | compressed | |
MD5:06B3DC02B4F4B79AA986DD1BE3845043 | SHA256:0077A797FCE8F0E6745298FC104148A5CC1953BF43328E5DFD4EDB69B0142B97 | |||
| 7192 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:C85465FD7CE3B46A785E3F8952E826DE | SHA256:022DA201B9E7F1640CC86856A6DB8B595D2361D4E3CD83F7B0B6B0727B65F544 | |||
| 7192 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:9C94C95F8906444CE6526BB6982C362B | SHA256:229ADC643EB49812F7F0DBC27D7846D55E3B98F4D82266365BC88E66033A7AA8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
29
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.20.245.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7192 | OUTLOOK.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7192 | OUTLOOK.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5728 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5728 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.20.245.139:80 | crl.microsoft.com | Akamai International B.V. | SE | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7192 | OUTLOOK.EXE | 52.109.76.240:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |