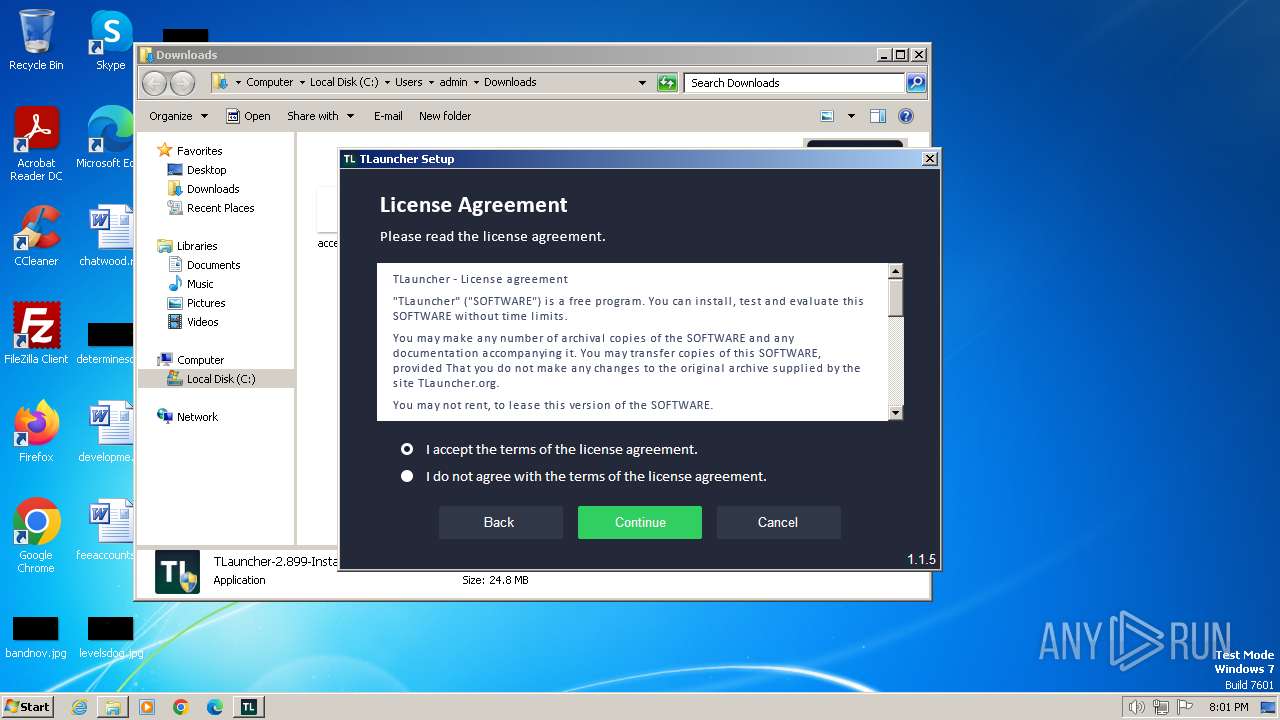
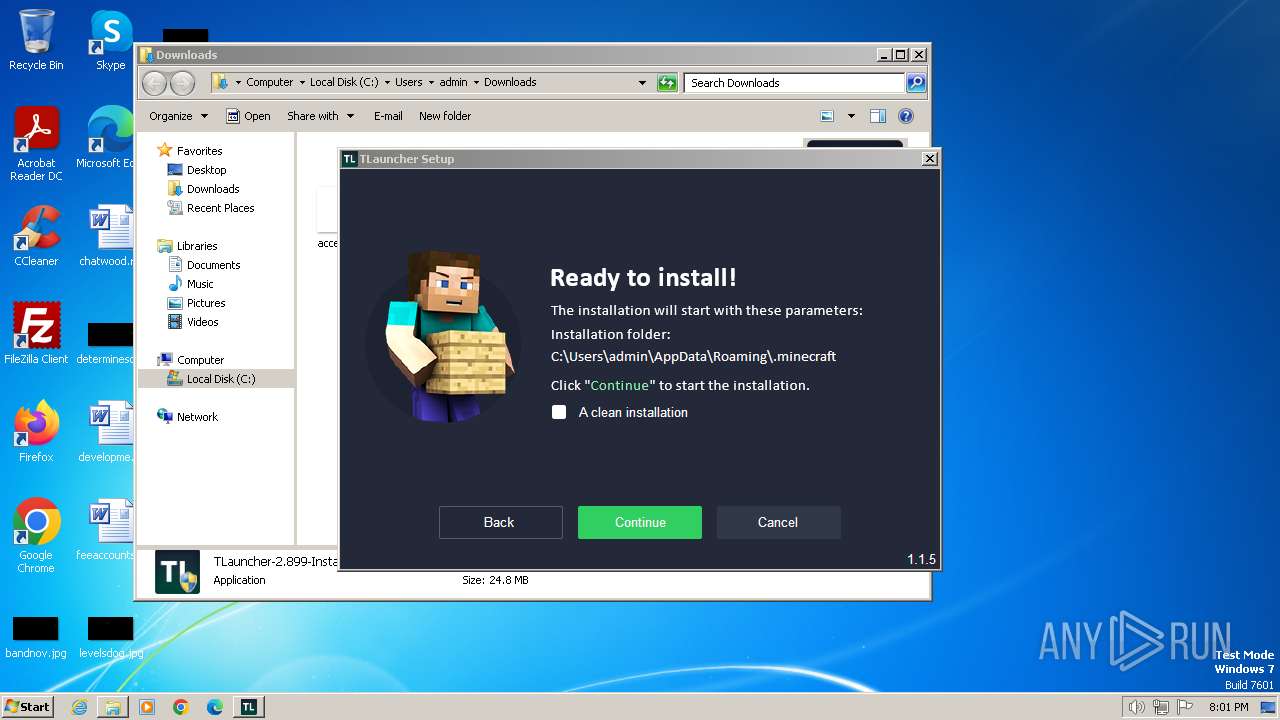
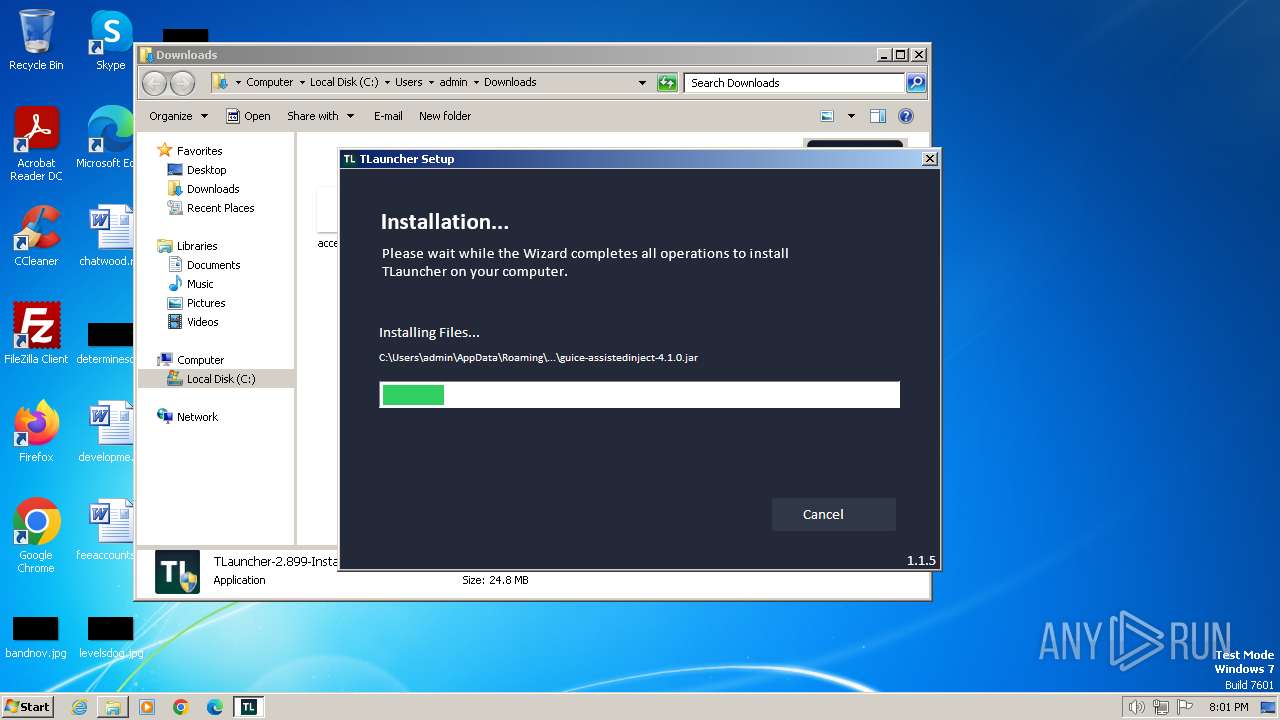
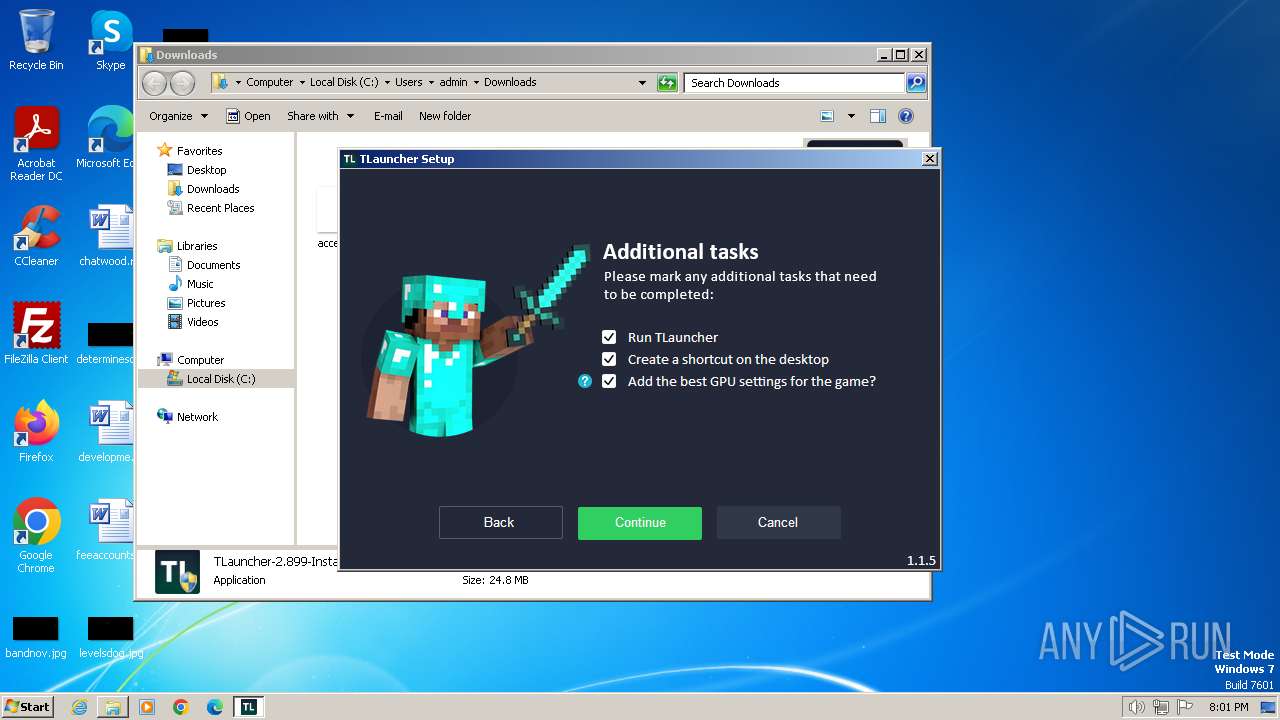
| URL: | https://tlauncher.org/installer |
| Full analysis: | https://app.any.run/tasks/f62f8292-6026-45bd-8d7b-060d90af053f |
| Verdict: | Malicious activity |
| Analysis date: | February 23, 2024, 19:59:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | F5818708A23ED11C618056110D380758 |
| SHA1: | 54790604A2BD759EBCCAF7CCE7EFB49CE24FCEAA |
| SHA256: | B4C6549734FB3075A2AE0A3ED4106A25D1A79981A00321E959B20FDE6B4644BD |
| SSDEEP: | 3:N8BEeLu5MiqOXn:2K5kOXn |
MALICIOUS
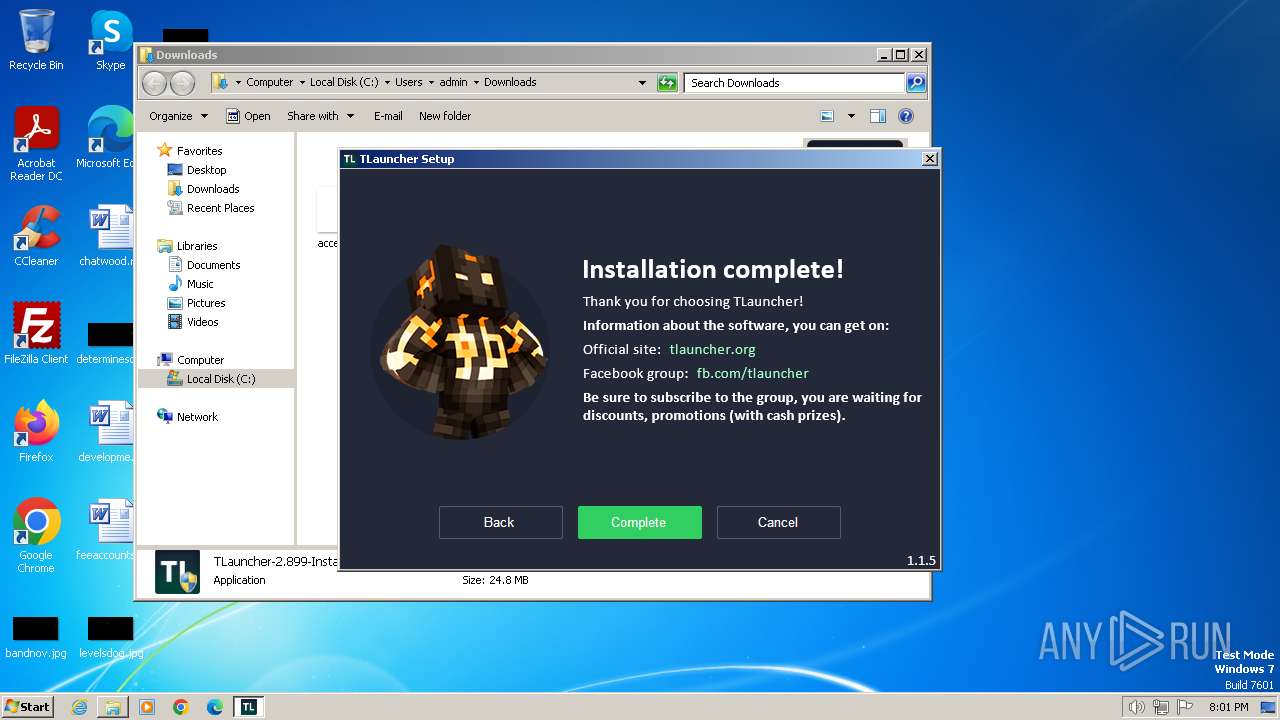
Drops the executable file immediately after the start
- TLauncher-2.899-Installer-1.1.5.exe (PID: 1576)
- BrowserInstaller.exe (PID: 2776)
- irsetup.exe (PID: 2244)
- javaw.exe (PID: 1804)
- javaw.exe (PID: 2424)
Actions looks like stealing of personal data
- irsetup.exe (PID: 2244)
SUSPICIOUS
Executable content was dropped or overwritten
- TLauncher-2.899-Installer-1.1.5.exe (PID: 1576)
- irsetup.exe (PID: 2244)
- BrowserInstaller.exe (PID: 2776)
- javaw.exe (PID: 1804)
- javaw.exe (PID: 2424)
Reads security settings of Internet Explorer
- TLauncher-2.899-Installer-1.1.5.exe (PID: 1576)
- irsetup.exe (PID: 2244)
- BrowserInstaller.exe (PID: 2776)
- irsetup.exe (PID: 3296)
Checks for Java to be installed
- irsetup.exe (PID: 2244)
- TLauncher.exe (PID: 3596)
Reads the Windows owner or organization settings
- irsetup.exe (PID: 2244)
- irsetup.exe (PID: 3296)
Checks Windows Trust Settings
- irsetup.exe (PID: 2244)
- irsetup.exe (PID: 3296)
Reads settings of System Certificates
- irsetup.exe (PID: 2244)
- irsetup.exe (PID: 3296)
- dxdiag.exe (PID: 324)
Reads the Internet Settings
- irsetup.exe (PID: 2244)
- BrowserInstaller.exe (PID: 2776)
- TLauncher-2.899-Installer-1.1.5.exe (PID: 1576)
- irsetup.exe (PID: 3296)
- WMIC.exe (PID: 968)
- WMIC.exe (PID: 3072)
- WMIC.exe (PID: 1484)
- WMIC.exe (PID: 1644)
Adds/modifies Windows certificates
- irsetup.exe (PID: 2244)
Reads Microsoft Outlook installation path
- irsetup.exe (PID: 2244)
Creates a software uninstall entry
- irsetup.exe (PID: 2244)
Reads Internet Explorer settings
- irsetup.exe (PID: 2244)
Starts CMD.EXE for commands execution
- javaw.exe (PID: 1804)
- javaw.exe (PID: 2424)
Starts application with an unusual extension
- cmd.exe (PID: 1928)
- cmd.exe (PID: 3140)
- cmd.exe (PID: 2772)
- cmd.exe (PID: 3616)
- cmd.exe (PID: 3068)
- cmd.exe (PID: 2360)
- cmd.exe (PID: 3732)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 1928)
- cmd.exe (PID: 3140)
Process drops legitimate windows executable
- javaw.exe (PID: 1804)
- javaw.exe (PID: 2424)
The process drops C-runtime libraries
- javaw.exe (PID: 1804)
- javaw.exe (PID: 2424)
Uses ICACLS.EXE to modify access control lists
- javaw.exe (PID: 2424)
Process requests binary or script from the Internet
- javaw.exe (PID: 2424)
Uses WMIC.EXE to obtain CPU information
- cmd.exe (PID: 2772)
Creates/Modifies COM task schedule object
- dxdiag.exe (PID: 324)
Uses WMIC.EXE to obtain quick Fix Engineering (patches) data
- cmd.exe (PID: 3732)
The process creates files with name similar to system file names
- javaw.exe (PID: 2424)
INFO
Application launched itself
- firefox.exe (PID: 4052)
- firefox.exe (PID: 3656)
Executable content was dropped or overwritten
- firefox.exe (PID: 3656)
Drops the executable file immediately after the start
- firefox.exe (PID: 3656)
The process uses the downloaded file
- firefox.exe (PID: 3656)
Manual execution by a user
- TLauncher-2.899-Installer-1.1.5.exe (PID: 1576)
Create files in a temporary directory
- TLauncher-2.899-Installer-1.1.5.exe (PID: 1576)
- irsetup.exe (PID: 2244)
- BrowserInstaller.exe (PID: 2776)
- irsetup.exe (PID: 3296)
- javaw.exe (PID: 1804)
- javaw.exe (PID: 2424)
Checks supported languages
- TLauncher-2.899-Installer-1.1.5.exe (PID: 1576)
- BrowserInstaller.exe (PID: 2776)
- irsetup.exe (PID: 2244)
- irsetup.exe (PID: 3296)
- TLauncher.exe (PID: 3596)
- javaw.exe (PID: 1804)
- chcp.com (PID: 2832)
- chcp.com (PID: 480)
- javaw.exe (PID: 2424)
- chcp.com (PID: 2324)
- chcp.com (PID: 2376)
- chcp.com (PID: 3876)
- chcp.com (PID: 1288)
- chcp.com (PID: 2712)
Reads the computer name
- TLauncher-2.899-Installer-1.1.5.exe (PID: 1576)
- irsetup.exe (PID: 2244)
- BrowserInstaller.exe (PID: 2776)
- irsetup.exe (PID: 3296)
- javaw.exe (PID: 1804)
- javaw.exe (PID: 2424)
Checks proxy server information
- irsetup.exe (PID: 2244)
- irsetup.exe (PID: 3296)
Reads the machine GUID from the registry
- irsetup.exe (PID: 2244)
- irsetup.exe (PID: 3296)
- javaw.exe (PID: 1804)
- javaw.exe (PID: 2424)
Reads the software policy settings
- irsetup.exe (PID: 2244)
- irsetup.exe (PID: 3296)
- dxdiag.exe (PID: 324)
Creates files or folders in the user directory
- irsetup.exe (PID: 2244)
- irsetup.exe (PID: 3296)
- javaw.exe (PID: 1804)
- javaw.exe (PID: 2424)
Creates files in the program directory
- irsetup.exe (PID: 2244)
- javaw.exe (PID: 1804)
- javaw.exe (PID: 2424)
Reads security settings of Internet Explorer
- dxdiag.exe (PID: 324)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
99
Monitored processes
42
Malicious processes
8
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 324 | dxdiag /whql:off /t C:\Users\admin\AppData\Roaming\.minecraft\logs\tlauncher\dxdiag.txt | C:\Windows\System32\dxdiag.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft DirectX Diagnostic Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 448 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3656.7.2011887297\689620520" -childID 6 -isForBrowser -prefsHandle 4248 -prefMapHandle 4252 -prefsLen 29102 -prefMapSize 244195 -jsInitHandle 896 -jsInitLen 240908 -parentBuildID 20230710165010 -appDir "C:\Program Files\Mozilla Firefox\browser" - {1c004622-c233-445f-8ce9-0510ea6b9ad7} 3656 "\\.\pipe\gecko-crash-server-pipe.3656" 4236 18127280 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 480 | chcp 437 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 968 | wmic os get osarchitecture | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1112 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3656.3.1907755092\1574604939" -childID 2 -isForBrowser -prefsHandle 2932 -prefMapHandle 2936 -prefsLen 34225 -prefMapSize 244195 -jsInitHandle 896 -jsInitLen 240908 -parentBuildID 20230710165010 -appDir "C:\Program Files\Mozilla Firefox\browser" - {8adaa44e-c796-4a62-896a-f8e6b874e1cf} 3656 "\\.\pipe\gecko-crash-server-pipe.3656" 2948 16444e00 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 1288 | chcp 437 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1484 | wmic CPU get NAME | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1576 | "C:\Users\admin\Downloads\TLauncher-2.899-Installer-1.1.5.exe" | C:\Users\admin\Downloads\TLauncher-2.899-Installer-1.1.5.exe | explorer.exe | ||||||||||||
User: admin Company: TLauncher Inc. Integrity Level: HIGH Description: TLauncher Setup Exit code: 0 Version: 1.1.5.0 Modules
| |||||||||||||||
| 1596 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3656.5.1655891334\883893472" -childID 4 -isForBrowser -prefsHandle 3900 -prefMapHandle 3880 -prefsLen 29102 -prefMapSize 244195 -jsInitHandle 896 -jsInitLen 240908 -parentBuildID 20230710165010 -appDir "C:\Program Files\Mozilla Firefox\browser" - {e2538c7b-ec4a-4103-ab26-2ecf2caa92ec} 3656 "\\.\pipe\gecko-crash-server-pipe.3656" 3956 18127110 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 1644 | wmic qfe get HotFixID | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
50 881
Read events
50 453
Write events
374
Delete events
54
Modification events
| (PID) Process: | (4052) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: 5A87F54E01000000 | |||
| (PID) Process: | (3656) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: AF68F74E01000000 | |||
| (PID) Process: | (3656) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Installer\308046B0AF4A39CB |
| Operation: | delete value | Name: | installer.taskbarpin.win10.enabled |
Value: | |||
| (PID) Process: | (3656) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 0 | |||
| (PID) Process: | (3656) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (3656) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Theme |
Value: 1 | |||
| (PID) Process: | (3656) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Enabled |
Value: 1 | |||
| (PID) Process: | (3656) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 1 | |||
| (PID) Process: | (3656) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableDefaultBrowserAgent |
Value: 0 | |||
| (PID) Process: | (3656) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|SetDefaultBrowserUserChoice |
Value: 1 | |||
Executable files
391
Suspicious files
351
Text files
986
Unknown types
177
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3656 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:B7A3C61D0C144CC5E166B1E769CA8F8C | SHA256:7FADCB77FFACA6B9E9F15C6F1CD3AAD4C20DCD90FA92429A627A3A7110CA2644 | |||
| 3656 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 3656 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3656 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3656 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3656 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cert9.db-journal | binary | |
MD5:84559E9D373B2F769BEA8FC6E332473B | SHA256:6C69BB3D3AC454B9EA19AC83287CD6505585F14725C84119EE867049204DF3D8 | |||
| 3656 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs-1.js | text | |
MD5:60E0DE9E05EC76C749D80F0D15A81B21 | SHA256:08252FA62CCCCD316474E20CC7317A6B5C932B2C972234318E8CCDA39EC2EF48 | |||
| 3656 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3561288849sdhlie.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3656 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3656 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs.js | text | |
MD5:60E0DE9E05EC76C749D80F0D15A81B21 | SHA256:08252FA62CCCCD316474E20CC7317A6B5C932B2C972234318E8CCDA39EC2EF48 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
33
TCP/UDP connections
157
DNS requests
188
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3656 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | text | 90 b | unknown |
3656 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | text | 8 b | unknown |
3656 | firefox.exe | POST | 200 | 216.58.206.35:80 | http://ocsp.pki.goog/gts1c3 | unknown | binary | 472 b | unknown |
3656 | firefox.exe | POST | 200 | 216.58.206.35:80 | http://ocsp.pki.goog/gts1c3 | unknown | binary | 472 b | unknown |
3656 | firefox.exe | POST | 200 | 95.101.54.216:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
3656 | firefox.exe | POST | 200 | 95.101.54.216:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
3656 | firefox.exe | POST | 200 | 95.101.54.216:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
3656 | firefox.exe | POST | 200 | 95.101.54.139:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
3656 | firefox.exe | POST | 200 | 95.101.54.139:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
3656 | firefox.exe | POST | 200 | 95.101.54.216:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3656 | firefox.exe | 104.20.65.88:443 | tlauncher.org | CLOUDFLARENET | — | unknown |
3656 | firefox.exe | 142.250.184.234:443 | safebrowsing.googleapis.com | — | — | unknown |
3656 | firefox.exe | 95.101.54.139:80 | r3.o.lencr.org | Akamai International B.V. | DE | unknown |
3656 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | unknown |
3656 | firefox.exe | 34.117.237.239:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | unknown |
3656 | firefox.exe | 34.117.188.166:443 | spocs.getpocket.com | GOOGLE-CLOUD-PLATFORM | US | unknown |
3656 | firefox.exe | 216.58.206.35:80 | ocsp.pki.goog | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
tlauncher.org |
| unknown |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| shared |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
gkegw.prod.ads.prod.webservices.mozgcp.net |
| unknown |
r3.o.lencr.org |
| shared |
firefox.settings.services.mozilla.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3656 | firefox.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
3656 | firefox.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
1804 | javaw.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |
1804 | javaw.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |
1804 | javaw.exe | A Network Trojan was detected | ET HUNTING suspicious - gzipped file via JAVA - could be pack200-ed JAR |