| File name: | GetHWID.exe |
| Full analysis: | https://app.any.run/tasks/dbb58aac-6f0d-40b7-b92a-567628473379 |
| Verdict: | Malicious activity |
| Analysis date: | January 09, 2024, 23:46:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | MS-DOS executable PE32 executable (GUI) Intel 80386, for MS Windows, MZ for MS-DOS |
| MD5: | BCCC8EA2A5667905A02A2EDAFD971B05 |
| SHA1: | 1ACE67F78D9E85F66F1F4C58331E5A771A5DC7F5 |
| SHA256: | B4C2B4A922DEBCC5DE5EE7DDD8C24B2FEE6681E2454C2E3B2CBE4191FFC415F1 |
| SSDEEP: | 98304:5cndpeaojAkeMlU5h0LVp17sdEFTqUalcWLWp+cZISDGXVu0rjd2tKM6SrRjyqrM:QNCkfJN5YnZSsE7 |
MALICIOUS
Changes appearance of the Explorer extensions
- explorer.exe (PID: 2020)
- svchost.exe (PID: 492)
Uses Task Scheduler to run other applications
- svchost.exe (PID: 492)
Changes the autorun value in the registry
- svchost.exe (PID: 492)
SUSPICIOUS
Starts application with an unusual extension
- GetHWID.exe (PID: 2064)
The process creates files with name similar to system file names
- icsys.icn.exe (PID: 2416)
- spoolsv.exe (PID: 1392)
Creates or modifies Windows services
- svchost.exe (PID: 492)
INFO
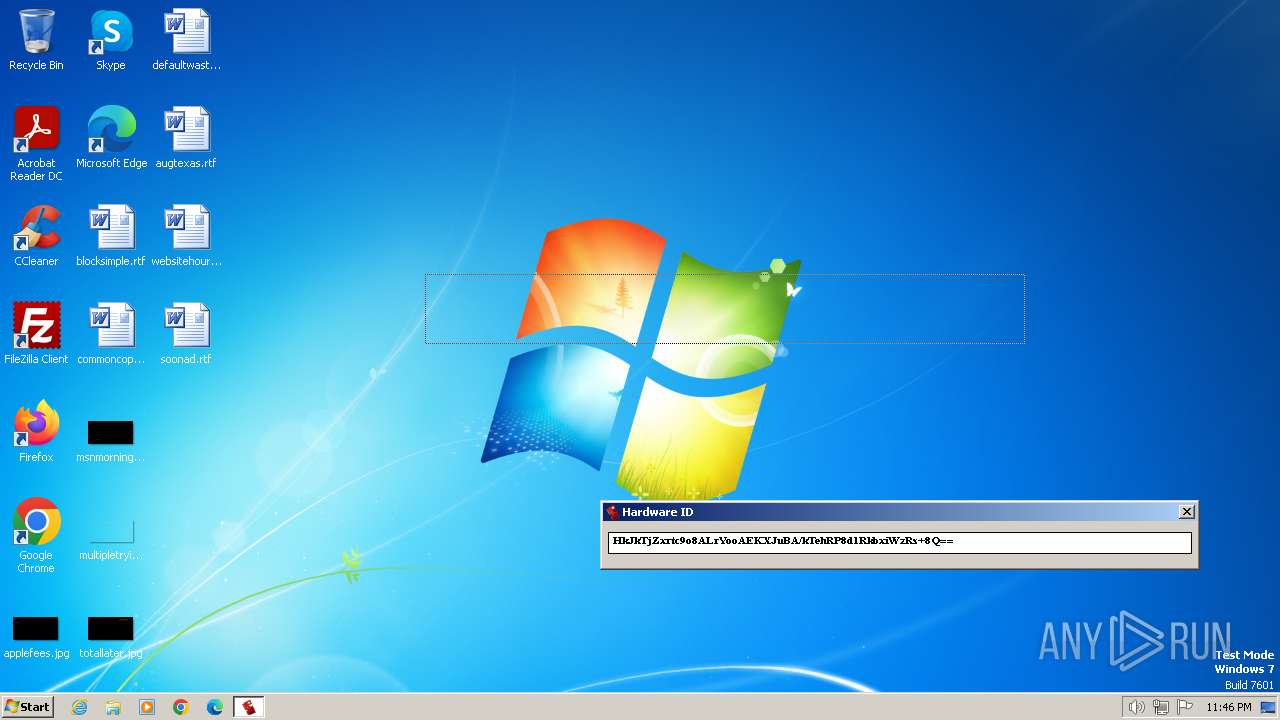
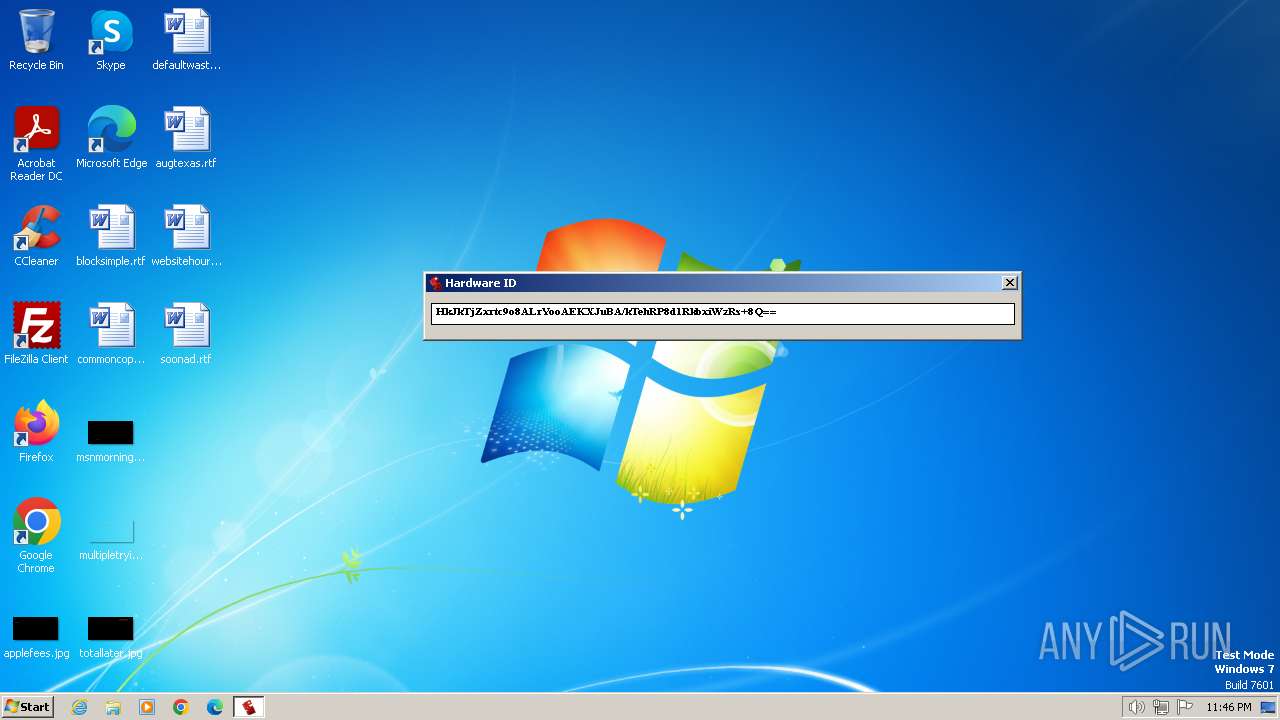
Reads the machine GUID from the registry
- GetHWID.exe (PID: 2064)
- icsys.icn.exe (PID: 2416)
- spoolsv.exe (PID: 1392)
- svchost.exe (PID: 492)
- spoolsv.exe (PID: 268)
- explorer.exe (PID: 2020)
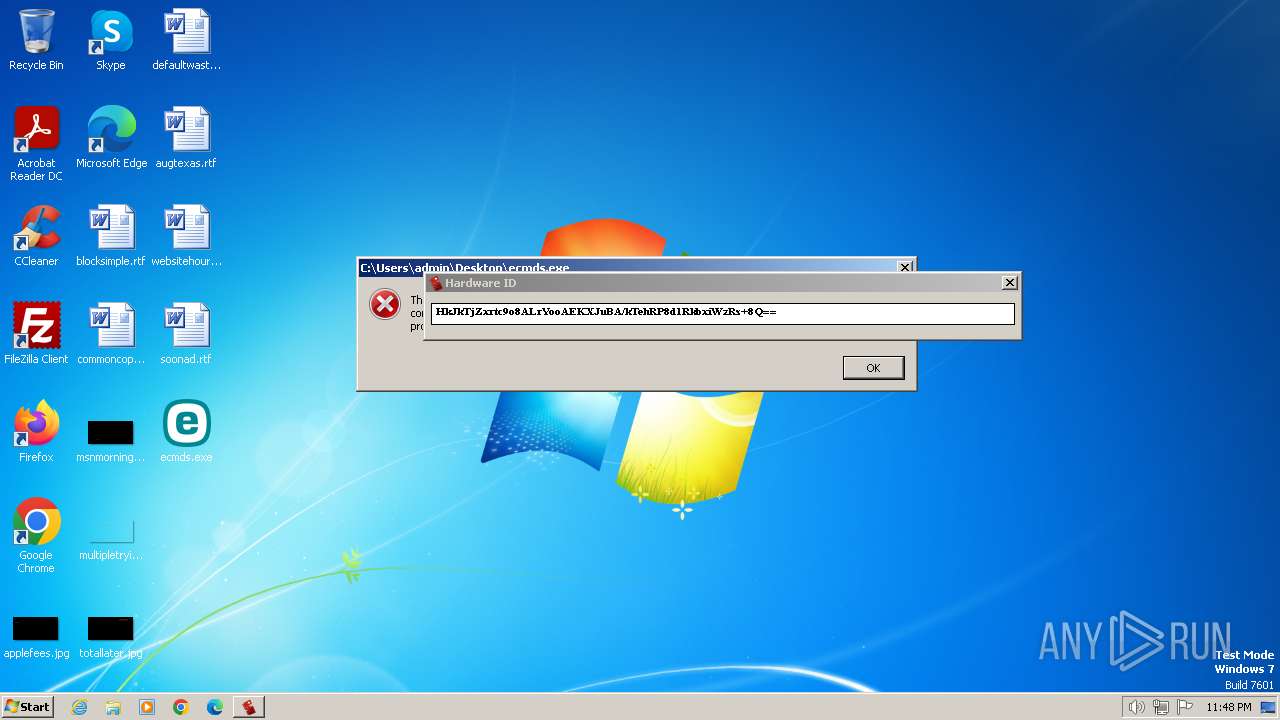
Drops the executable file immediately after the start
- GetHWID.exe (PID: 2064)
- icsys.icn.exe (PID: 2416)
- spoolsv.exe (PID: 1392)
- explorer.exe (PID: 2020)
Checks supported languages
- GetHWID.exe (PID: 2064)
- gethwid.exe (PID: 2408)
- icsys.icn.exe (PID: 2416)
- explorer.exe (PID: 2020)
- svchost.exe (PID: 492)
- spoolsv.exe (PID: 268)
- spoolsv.exe (PID: 1392)
Reads the computer name
- gethwid.exe (PID: 2408)
- svchost.exe (PID: 492)
Starts itself from another location
- GetHWID.exe (PID: 2064)
- icsys.icn.exe (PID: 2416)
- spoolsv.exe (PID: 1392)
- svchost.exe (PID: 492)
- explorer.exe (PID: 2020)
Create files in a temporary directory
- GetHWID.exe (PID: 2064)
- icsys.icn.exe (PID: 2416)
- spoolsv.exe (PID: 1392)
- explorer.exe (PID: 2020)
- svchost.exe (PID: 492)
- spoolsv.exe (PID: 268)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:04:01 09:08:22+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 106496 |
| InitializedDataSize: | 12288 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x290c |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| ProductName: | Project1 |
| FileVersion: | 1 |
| ProductVersion: | 1 |
| InternalName: | TJprojMain |
| OriginalFileName: | TJprojMain.exe |
Total processes
52
Monitored processes
11
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 268 | c:\windows\resources\spoolsv.exe PR | C:\Windows\resources\spoolsv.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 492 | c:\windows\resources\svchost.exe | C:\Windows\resources\svchost.exe | spoolsv.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 696 | schtasks /create /tn "svchost" /tr "c:\windows\resources\svchost.exe" /sc daily /st 23:49 /f | C:\Windows\System32\schtasks.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1392 | c:\windows\resources\spoolsv.exe SE | C:\Windows\resources\spoolsv.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 1504 | schtasks /create /tn "svchost" /tr "c:\windows\resources\svchost.exe" /sc daily /st 23:48 /f | C:\Windows\System32\schtasks.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1732 | schtasks /create /tn "svchost" /tr "c:\windows\resources\svchost.exe" /sc daily /st 23:50 /f | C:\Windows\System32\schtasks.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2020 | c:\windows\resources\themes\explorer.exe | C:\Windows\resources\Themes\explorer.exe | — | icsys.icn.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2040 | "C:\Users\admin\AppData\Local\Temp\GetHWID.exe" | C:\Users\admin\AppData\Local\Temp\GetHWID.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.00 Modules
| |||||||||||||||
| 2064 | "C:\Users\admin\AppData\Local\Temp\GetHWID.exe" | C:\Users\admin\AppData\Local\Temp\GetHWID.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2408 | c:\users\admin\appdata\local\temp\gethwid.exe | C:\Users\admin\AppData\Local\Temp\gethwid.exe | — | GetHWID.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
266
Read events
233
Write events
33
Delete events
0
Modification events
| (PID) Process: | (2416) icsys.icn.exe | Key: | HKEY_CURRENT_USER\Software\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
| (PID) Process: | (492) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Explorer |
Value: c:\windows\resources\themes\explorer.exe RO | |||
| (PID) Process: | (492) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Svchost |
Value: c:\windows\resources\svchost.exe RO | |||
| (PID) Process: | (492) svchost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced |
| Operation: | write | Name: | ShowSuperHidden |
Value: 0 | |||
| (PID) Process: | (2020) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced |
| Operation: | write | Name: | ShowSuperHidden |
Value: 0 | |||
| (PID) Process: | (492) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\Schedule |
| Operation: | write | Name: | Start |
Value: 2 | |||
| (PID) Process: | (492) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\SharedAccess |
| Operation: | write | Name: | Start |
Value: 4 | |||
Executable files
5
Suspicious files
4
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 268 | spoolsv.exe | C:\Users\admin\AppData\Local\Temp\~DF9798C13A558B0569.TMP | binary | |
MD5:3F1E750EA66189C92E45E5BE2676D3A7 | SHA256:2C29A9C6D962EF42DAC5854576B622F565C7F6B303A004BC8A29FDC6AB8E37F5 | |||
| 2020 | explorer.exe | C:\windows\resources\spoolsv.exe | executable | |
MD5:CF20799E2ED1531E00FA98892253D6CB | SHA256:AED4862C0DF38C89333B2347154200B1546F9AC4649F8FDBB8DA438EB99B9C2D | |||
| 2416 | icsys.icn.exe | C:\windows\resources\themes\explorer.exe | executable | |
MD5:A329545F81CDC1244E631E6F630BF41C | SHA256:FF7A3A8D2F600135A65FC43B358CB00FDB609502AC61DA93A4A4807397AD238C | |||
| 2416 | icsys.icn.exe | C:\Users\admin\AppData\Local\Temp\~DF4A418B8FB9160F70.TMP | binary | |
MD5:81A9BD1B6E0E368B3CC68967618E463B | SHA256:7E45889DA7C1E76D25036DF513B19B87DF957BF1A726F9986050FA10254FDCB2 | |||
| 1392 | spoolsv.exe | C:\windows\resources\svchost.exe | executable | |
MD5:F1330DE61F325B974DA07DD8D763A17B | SHA256:FEEAA46D60B38DEA21CCE270CA576CC4148FA036F386ECC8A328ABF5C8F12131 | |||
| 1392 | spoolsv.exe | C:\Users\admin\AppData\Local\Temp\~DF87E144A0FE383724.TMP | binary | |
MD5:3F1E750EA66189C92E45E5BE2676D3A7 | SHA256:2C29A9C6D962EF42DAC5854576B622F565C7F6B303A004BC8A29FDC6AB8E37F5 | |||
| 2064 | GetHWID.exe | C:\Windows\Resources\Themes\icsys.icn.exe | executable | |
MD5:50D9931CD6CD77E7E33192960F3D4403 | SHA256:F482551458DD7E889294ED7EB28F2C74814E50D33E9E479648A119EC1D335395 | |||
| 2064 | GetHWID.exe | C:\users\admin\appdata\local\temp\gethwid.exe | executable | |
MD5:09C8BF93FCE5A30EB46C900FBA0098C6 | SHA256:49BA5A5B7F73631FD856CA205696F19BD332F7F433E49453B105409F9DCAA593 | |||
| 2064 | GetHWID.exe | C:\Users\admin\AppData\Local\Temp\~DF4522F8C5BF51C946.TMP | binary | |
MD5:81A9BD1B6E0E368B3CC68967618E463B | SHA256:7E45889DA7C1E76D25036DF513B19B87DF957BF1A726F9986050FA10254FDCB2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |