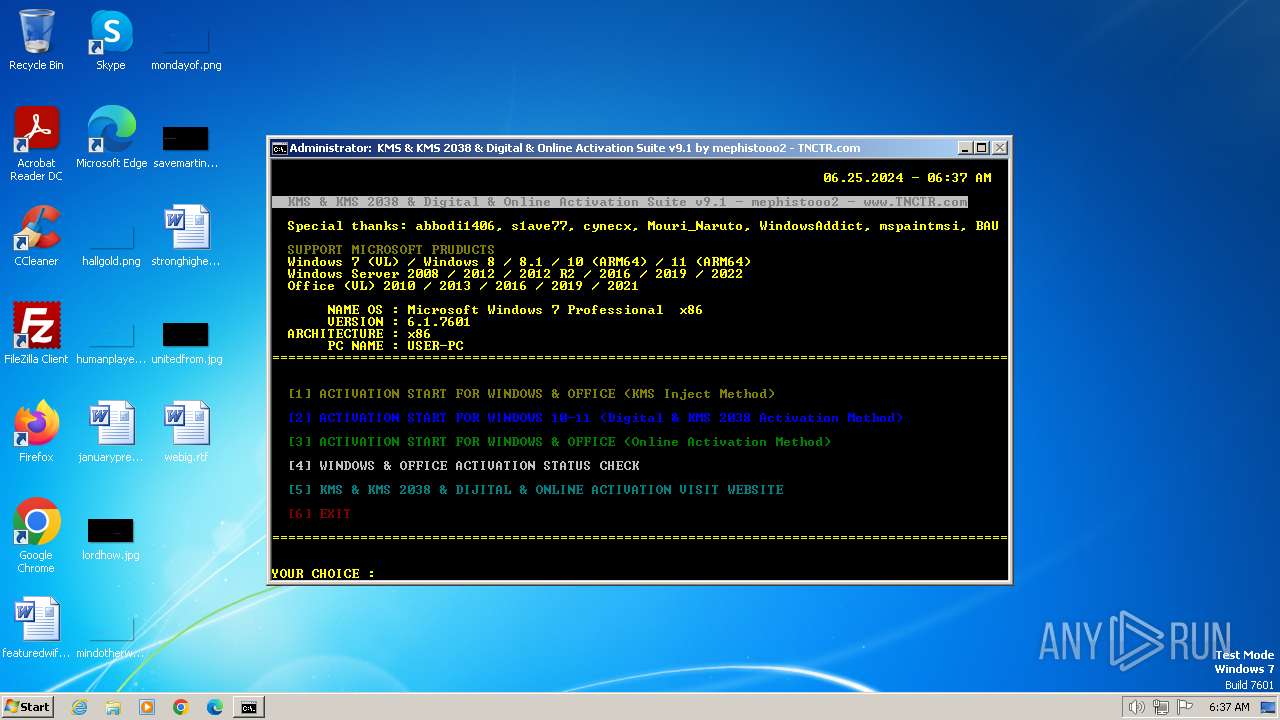
| File name: | KMS_Suite.v9.1.EN.bat |
| Full analysis: | https://app.any.run/tasks/d4e14306-2c01-4460-a541-d77563241a81 |
| Verdict: | Malicious activity |
| Analysis date: | June 25, 2024, 05:37:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with CRLF line terminators |
| MD5: | A1529279D38E87F05888580F79BF7E81 |
| SHA1: | 8D6676A3E9A68CBB47F3D4B5D81C769A6D73DDA3 |
| SHA256: | B4B9CE2E0964DC6823FC795D90C78DB8687836537CA17C0AFCAEDE8C4F3C04FE |
| SSDEEP: | 6144:vlSmZUL9IPt1rnOkF4dHa2ba/z5Np3T02XcTqegEoWwu0Wp61t1EaXKf1obP4XF6:v8/KS66HMFv3wXTqeaWJ0WUj1EjX8 |
MALICIOUS
Starts Visual C# compiler
- powershell.exe (PID: 3204)
Drops the executable file immediately after the start
- csc.exe (PID: 2076)
SUSPICIOUS
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 3400)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 3400)
Uses .NET C# to load dll
- powershell.exe (PID: 3204)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 3400)
- cmd.exe (PID: 3164)
- cmd.exe (PID: 3996)
- cmd.exe (PID: 2424)
- cmd.exe (PID: 4064)
- cmd.exe (PID: 2892)
- cmd.exe (PID: 3824)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 3400)
- cmd.exe (PID: 3164)
- cmd.exe (PID: 3996)
- cmd.exe (PID: 2424)
- cmd.exe (PID: 4064)
- cmd.exe (PID: 2892)
- cmd.exe (PID: 3824)
Executable content was dropped or overwritten
- csc.exe (PID: 2076)
- expand.exe (PID: 3124)
- xcopy.exe (PID: 2900)
Unpacks CAB file
- expand.exe (PID: 3124)
Process drops legitimate windows executable
- xcopy.exe (PID: 2900)
- expand.exe (PID: 3124)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3400)
- powershell.exe (PID: 2840)
- cmd.exe (PID: 3996)
Executing commands from a ".bat" file
- cmd.exe (PID: 3400)
- powershell.exe (PID: 2840)
Application launched itself
- cmd.exe (PID: 3400)
- cmd.exe (PID: 3996)
Powershell scripting: start process
- cmd.exe (PID: 3164)
Reads the Internet Settings
- powershell.exe (PID: 2840)
- cmd.exe (PID: 3996)
- wscript.exe (PID: 764)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 764)
The process executes VB scripts
- cmd.exe (PID: 3996)
Runs shell command (SCRIPT)
- wscript.exe (PID: 764)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 3996)
The executable file from the user directory is run by the CMD process
- center.exe (PID: 3920)
INFO
Manual execution by a user
- wmpnscfg.exe (PID: 3224)
Checks supported languages
- mode.com (PID: 3412)
- wmpnscfg.exe (PID: 3224)
- csc.exe (PID: 2076)
- cvtres.exe (PID: 2348)
- mode.com (PID: 3092)
- mode.com (PID: 2512)
- DisableX.exe (PID: 2532)
- center.exe (PID: 3920)
- mode.com (PID: 2876)
- mode.com (PID: 368)
Reads the computer name
- wmpnscfg.exe (PID: 3224)
Reads the machine GUID from the registry
- csc.exe (PID: 2076)
- cvtres.exe (PID: 2348)
Create files in a temporary directory
- csc.exe (PID: 2076)
- cvtres.exe (PID: 2348)
- expand.exe (PID: 3124)
- xcopy.exe (PID: 2900)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3204)
Drops the executable file immediately after the start
- expand.exe (PID: 3124)
- xcopy.exe (PID: 2900)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
88
Monitored processes
46
Malicious processes
4
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 328 | choice /C:12345678 /N /M "YOUR CHOICE : " | C:\Windows\System32\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Offers the user a choice Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 368 | mode con:cols=84 lines=42 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 764 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\21129\bin\DisableX.vbs" | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 980 | REG QUERY HKU\S-1-5-19\Environment | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1164 | findstr /v /a:7 /R "^f7f81a39-5f63-5b42-9efd-1f13b5431005quot; " [4] WINDOWS & OFFICE ACTIVATION STATUS CHECK" nul | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1196 | choice /C:123456 /N /M "YOUR CHOICE :" | C:\Windows\System32\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Offers the user a choice Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1420 | findstr /v /a:78 /R "^f7f81a39-5f63-5b42-9efd-1f13b5431005quot; " KMS & KMS 2038 & Digital & Online Activation Suite v9.1 - mephistooo2 - www.TNCTR.com" nul | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1428 | C:\Windows\system32\cmd.exe /c "prompt #$H#$E# & echo on & for %b in (1) do rem" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2024 | findstr /v /a:9 /R "^f7f81a39-5f63-5b42-9efd-1f13b5431005quot; " [2] ACTIVATION START FOR WINDOWS 10-11 (Digital & KMS 2038 Activation Method)" nul | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2068 | findstr /v /a:3 /R "^f7f81a39-5f63-5b42-9efd-1f13b5431005quot; " [5] KMS & KMS 2038 & DIJITAL & ONLINE ACTIVATION VISIT WEBSITE" nul | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
20 150
Read events
20 126
Write events
24
Delete events
0
Modification events
| (PID) Process: | (2840) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2840) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2840) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2840) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3996) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3996) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3996) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3996) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (764) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (764) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
28
Suspicious files
18
Text files
45
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3204 | powershell.exe | C:\Users\admin\AppData\Local\Temp\nti4fdoz.30g.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2076 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSC8E8CC25D848448A48E9FED7D76363D6.TMP | binary | |
MD5:E4B31A38136CC0C776CA6DEE5A214929 | SHA256:4368E7184AD1F40484F75907FE5AD126DD6A82E862545D5F0A2B160389741461 | |||
| 2348 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RESEA9B.tmp | binary | |
MD5:CAF63D368E11AE6FF453C4FBE3793E78 | SHA256:52FF3BB8A76964D579B99E5548725D478ED8EEE354B59AF31B28498B2BE63E1A | |||
| 3124 | expand.exe | C:\Users\admin\AppData\Local\Temp\KMS_Suite\bin\DisableX.vbs | text | |
MD5:C2206C9C9B0C97F7C5DB4F473E96E9A3 | SHA256:F1CEC878CD1DB36CA4CCB68296CD47CE039054E2ECE4CD22D9933B90C8625C1F | |||
| 3124 | expand.exe | C:\Users\admin\AppData\Local\Temp\KMS_Suite\KMS_Suite.bat | text | |
MD5:E17010BE52AA4BBA141815926C18E301 | SHA256:2F43CB579C6E40FBD72550B43704CE11C6FDEA78635BB31EE8FFED7F37864E66 | |||
| 3124 | expand.exe | C:\Users\admin\AppData\Local\Temp\KMS_Suite\bin\DisableX.exe | executable | |
MD5:00C9837407663587C69DF18793248D52 | SHA256:09933212238BC7D0CCE57469F9927C0325D5670B21FC7787428574C4A52E5F6D | |||
| 3124 | expand.exe | C:\Users\admin\AppData\Local\Temp\KMS_Suite\bin\center.exe | executable | |
MD5:0A847EAFDDC4529388E1A1B291354CF8 | SHA256:69533D9B66B840B4764F901CD6A502D12453B604617A841F4C2C602FC87DF255 | |||
| 3204 | powershell.exe | C:\Users\admin\AppData\Local\Temp\1 | compressed | |
MD5:67510BD628612052BA1C2560A33BEFC8 | SHA256:EBB5611D9EB6902E0B4DF4197D9628E1C8A56A987946360FC501A51D1DE5E828 | |||
| 3124 | expand.exe | C:\Users\admin\AppData\Local\Temp\KMS_Suite\bin\Digital\Digital_KMS38.bat | text | |
MD5:D7A880AC1D89DECFE79A9E72C6181555 | SHA256:F8FBAF7A6FFE0C24FAEEF62B760129E567F7BE7D73C39887001F34377BF5E3C2 | |||
| 3124 | expand.exe | C:\Users\admin\AppData\Local\Temp\KMS_Suite\bin\Digital\bin\gatherosstate.exe | executable | |
MD5:15CE0753A16DD4F9B9F0F9926DD37C4E | SHA256:028C8FBE58F14753B946475DE9F09A9C7A05FD62E81A1339614C9E138FC2A21D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
12
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?fbe613066ac7852b | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1372 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1372 | svchost.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
1372 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
1060 | svchost.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dns.msftncsi.com |
| shared |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |