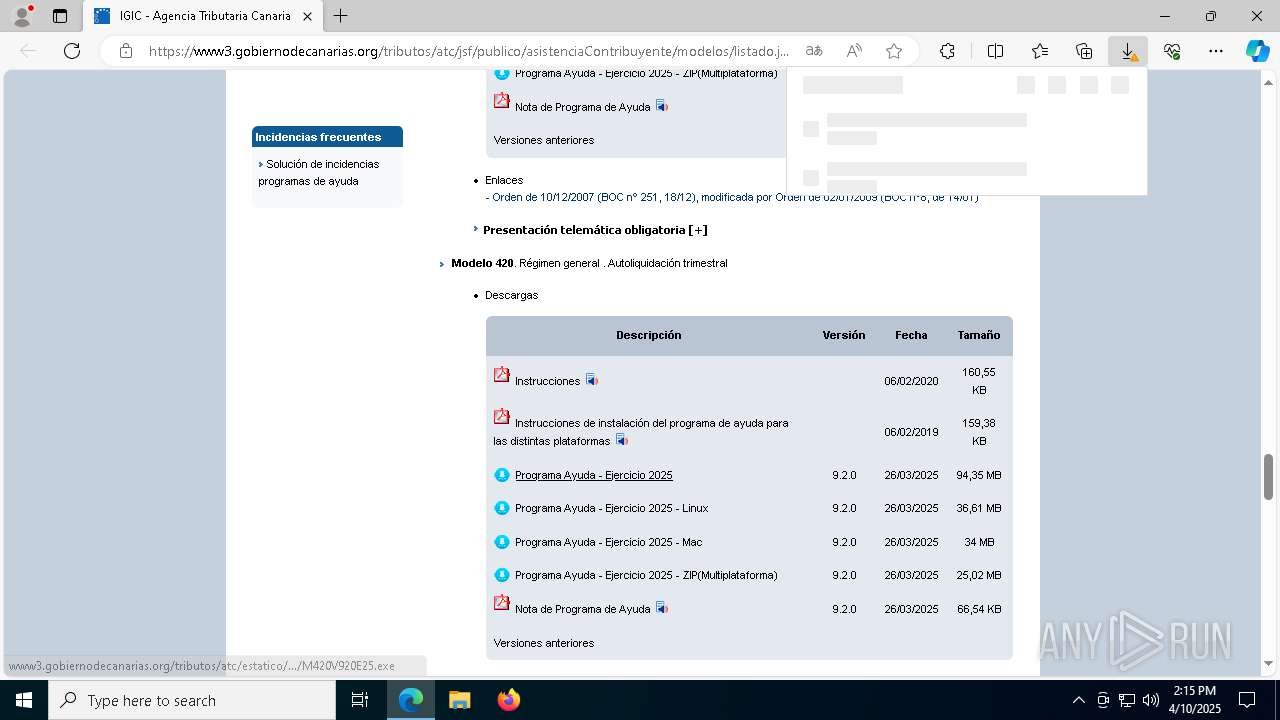
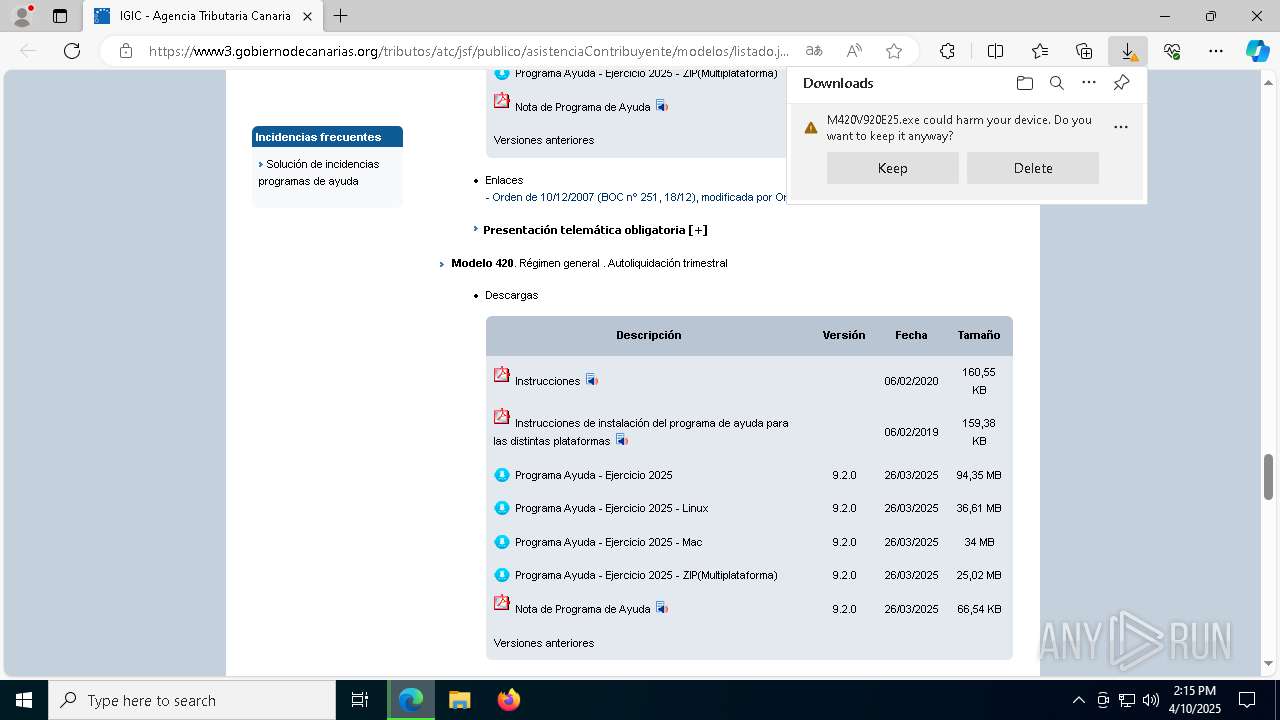
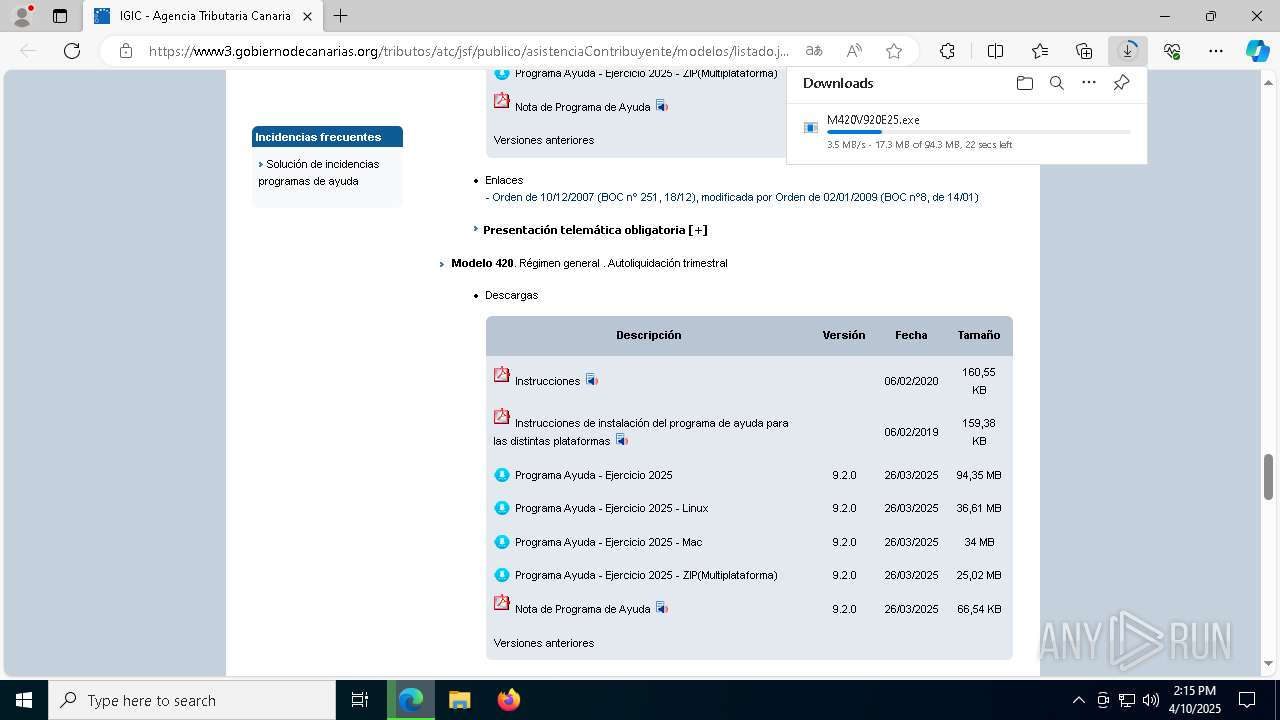
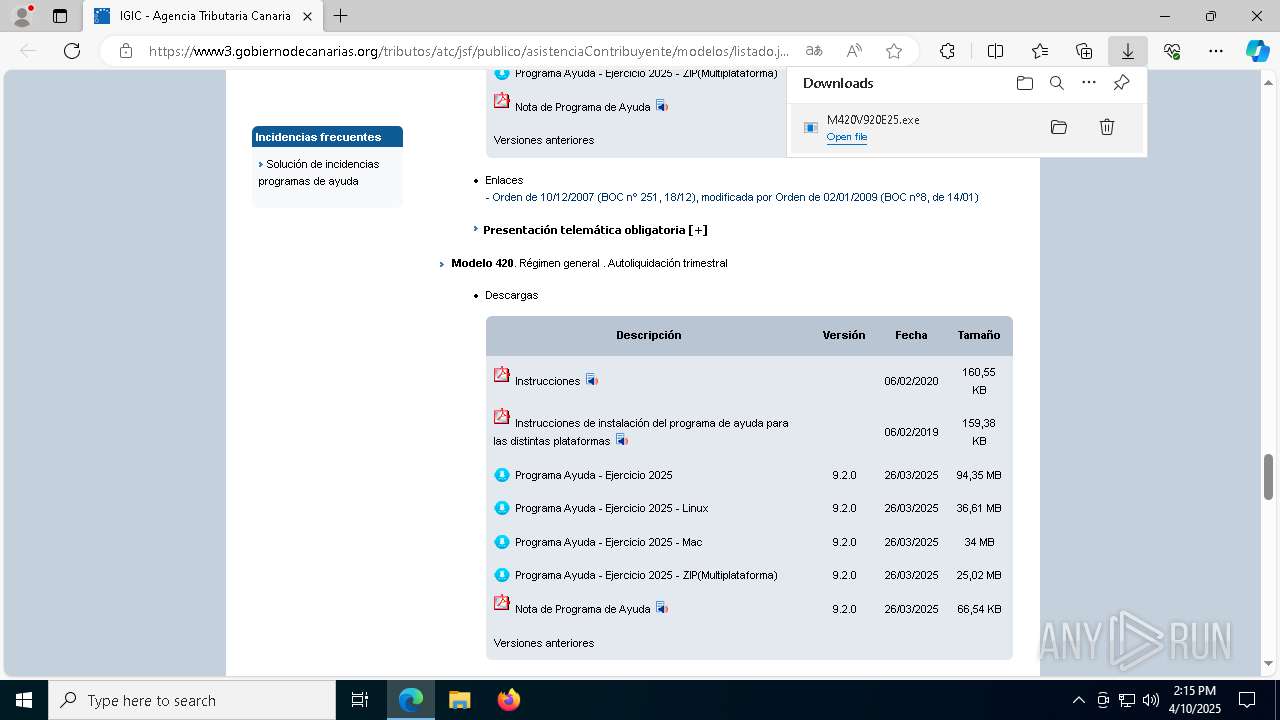
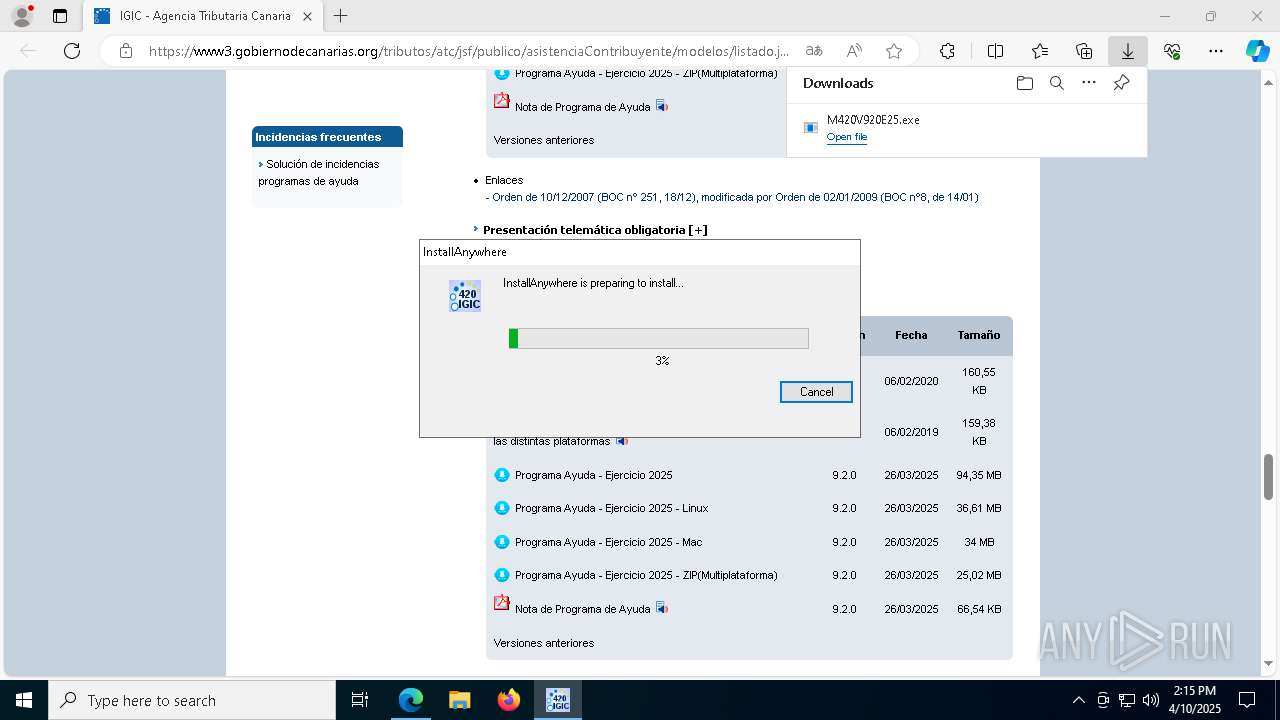
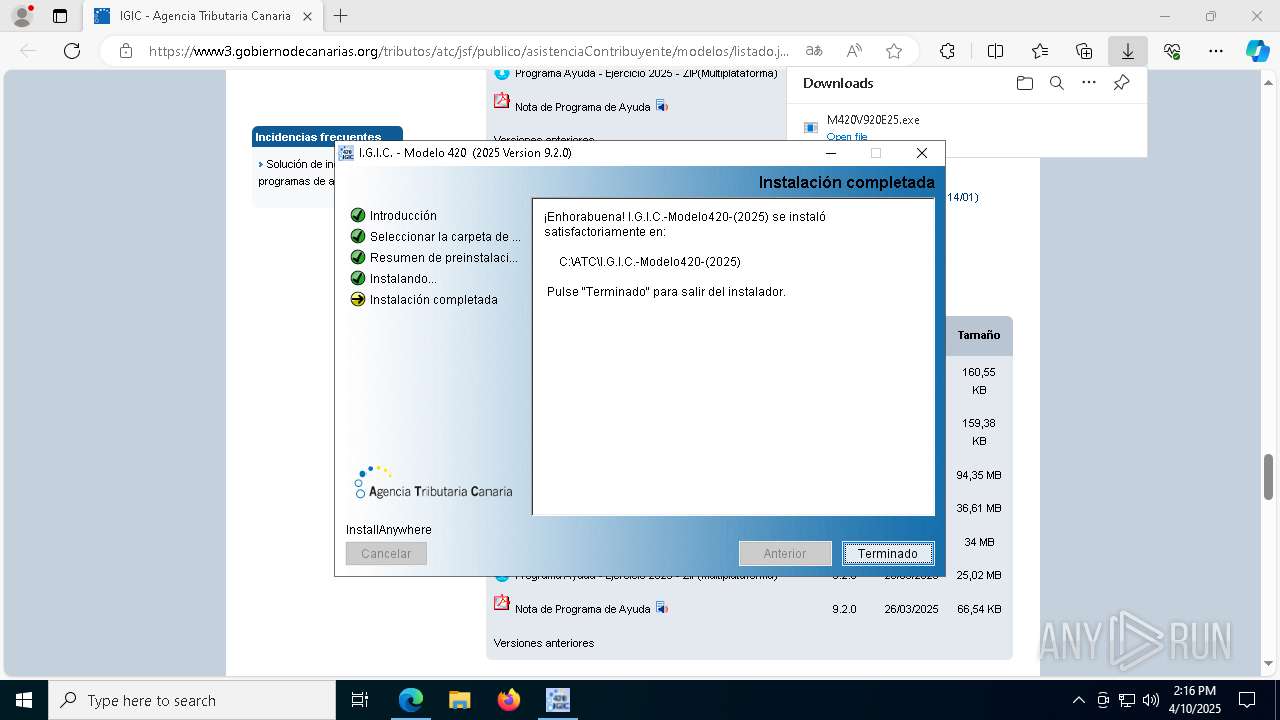
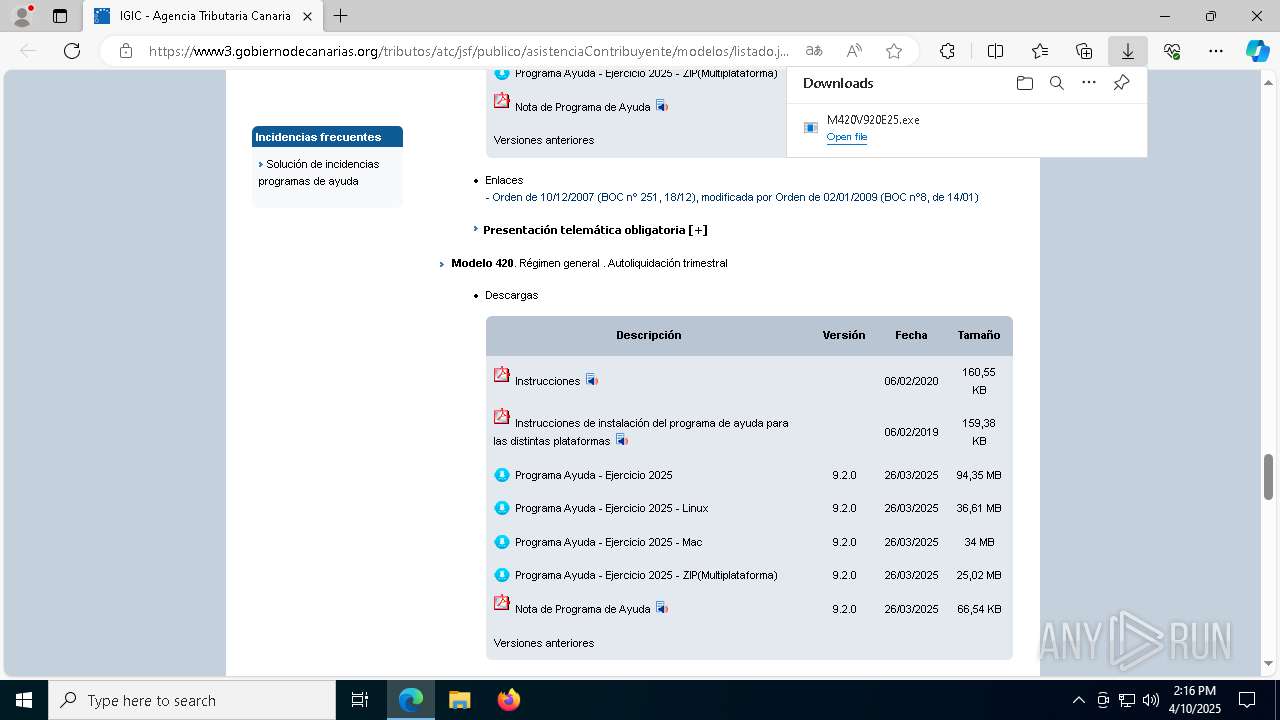
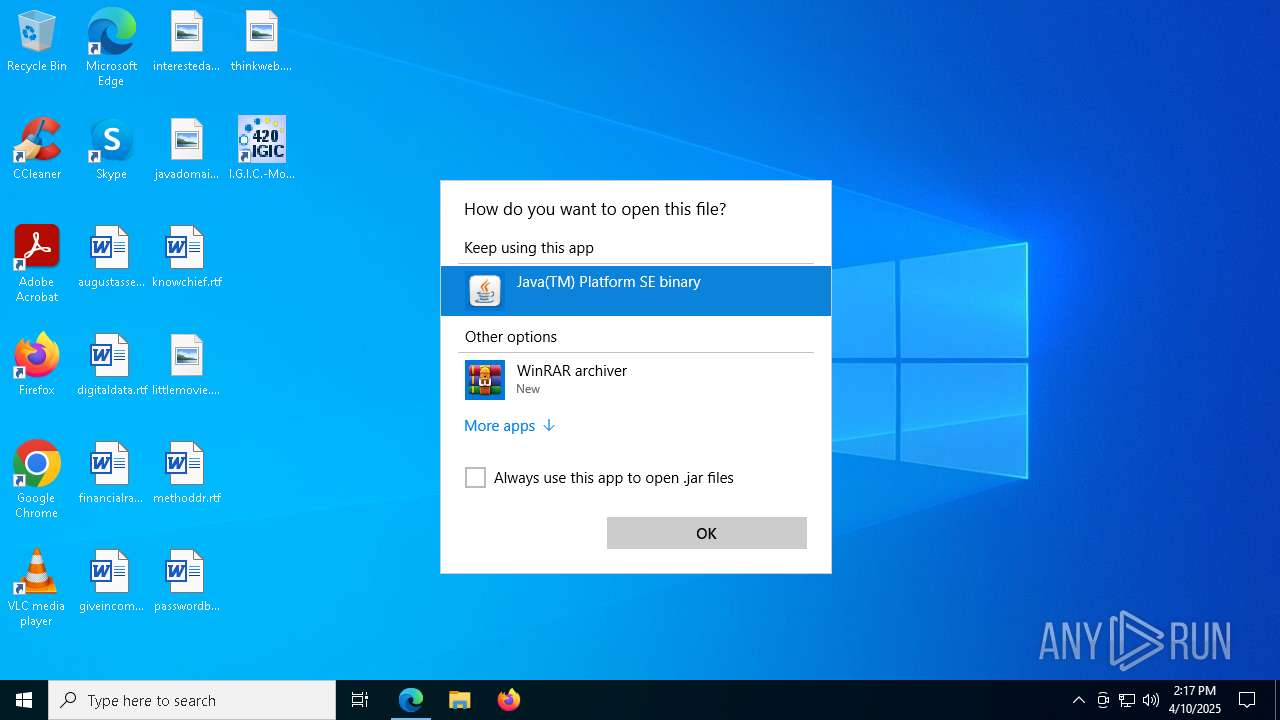
| URL: | https://www3.gobiernodecanarias.org/tributos/atc/jsf/publico/asistenciaContribuyente/modelos/listado.jsp?tributo=IGIC |
| Full analysis: | https://app.any.run/tasks/08fb2d20-ae04-45e7-bb2a-73329690e384 |
| Verdict: | Malicious activity |
| Analysis date: | April 10, 2025, 14:14:49 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | C8940DFFEF365A9B754A9A4CE5FCE65E |
| SHA1: | EE6E0283208E2F51F8E0A472111CB695F8128FD0 |
| SHA256: | B48AD2F91626C7FEA15B25F8C9F7309EF0E6B9DB93F659C576CC515DEB26AC6B |
| SSDEEP: | 3:N8DSWLJhLabFMOIPD/idK/cKLKHw2XILRHwiH:2OMKq/PjidKTL52m9 |
MALICIOUS
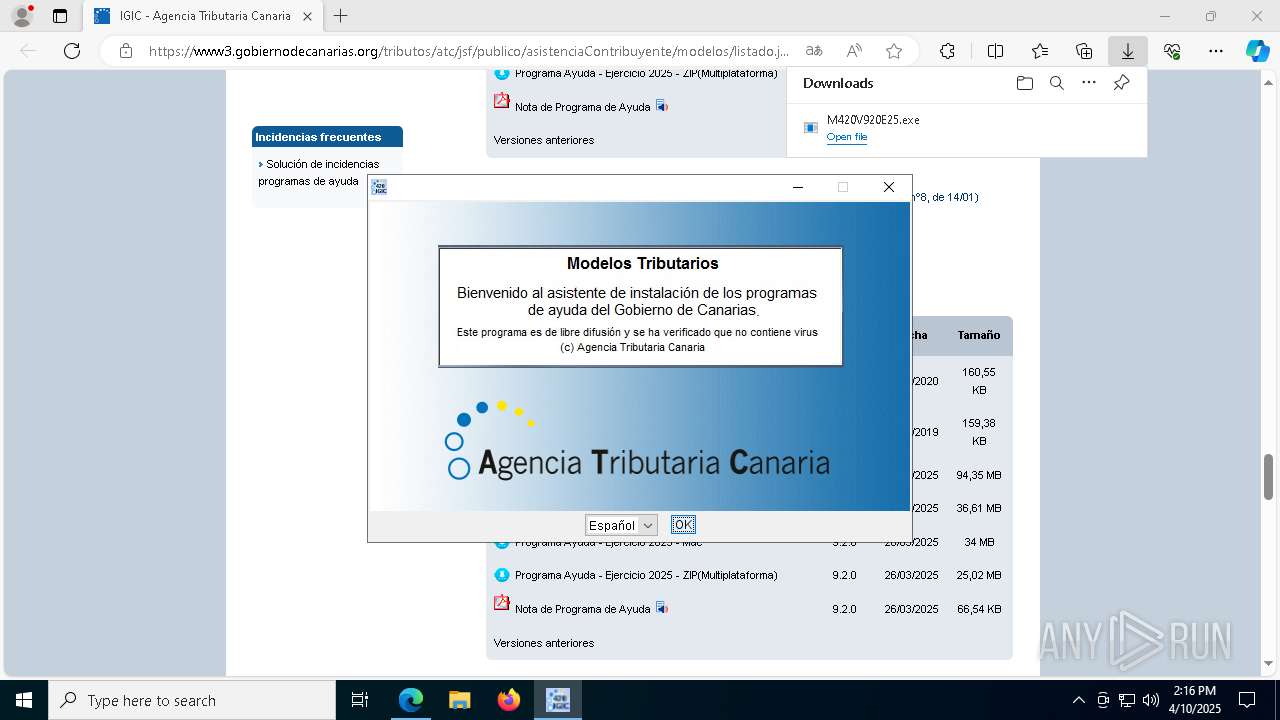
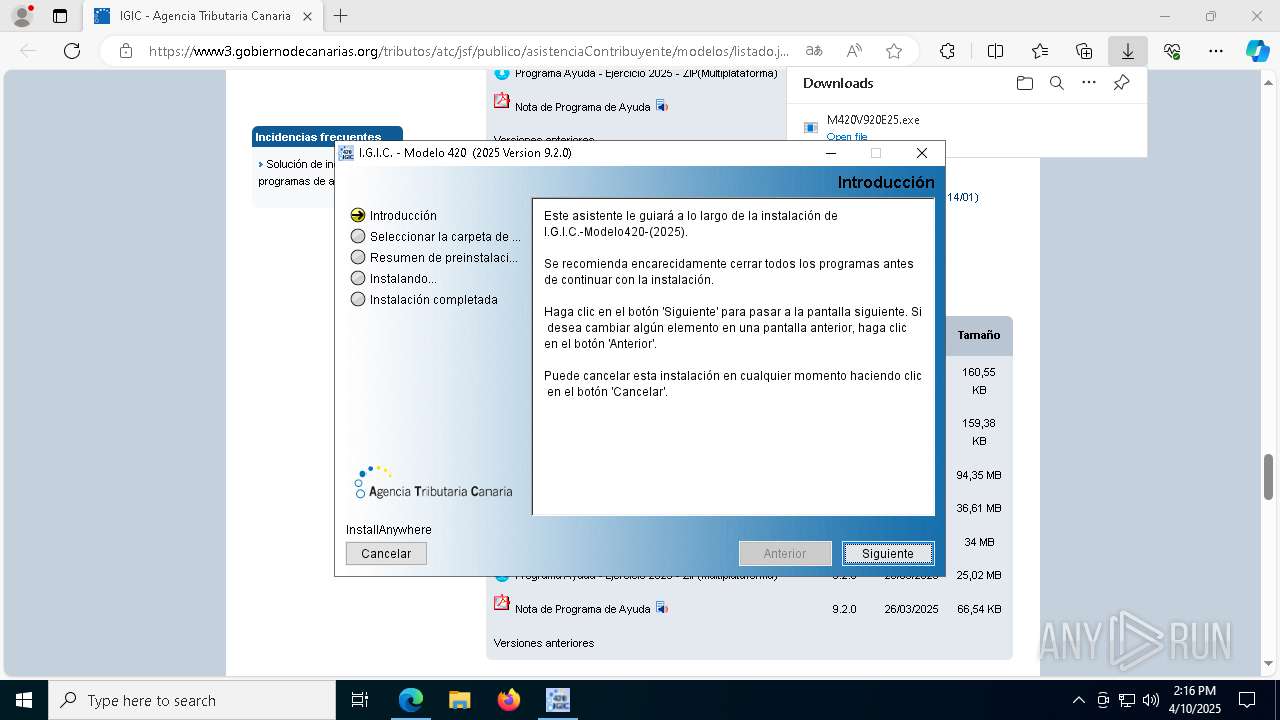
Executing a file with an untrusted certificate
- javaw.exe (PID: 5228)
- win64_32_x64.exe (PID: 7844)
- win64_32_x64.exe (PID: 7928)
- win64_32_x64.exe (PID: 6572)
- win64_32_x64.exe (PID: 5936)
- win64_32_x64.exe (PID: 4572)
- IconChng.exe (PID: 6228)
- remove.exe (PID: 1616)
Changes the autorun value in the registry
- ie4uinit.exe (PID: 8164)
- ie4uinit.exe (PID: 4376)
- ie4uinit.exe (PID: 5972)
- ie4uinit.exe (PID: 7928)
SUSPICIOUS
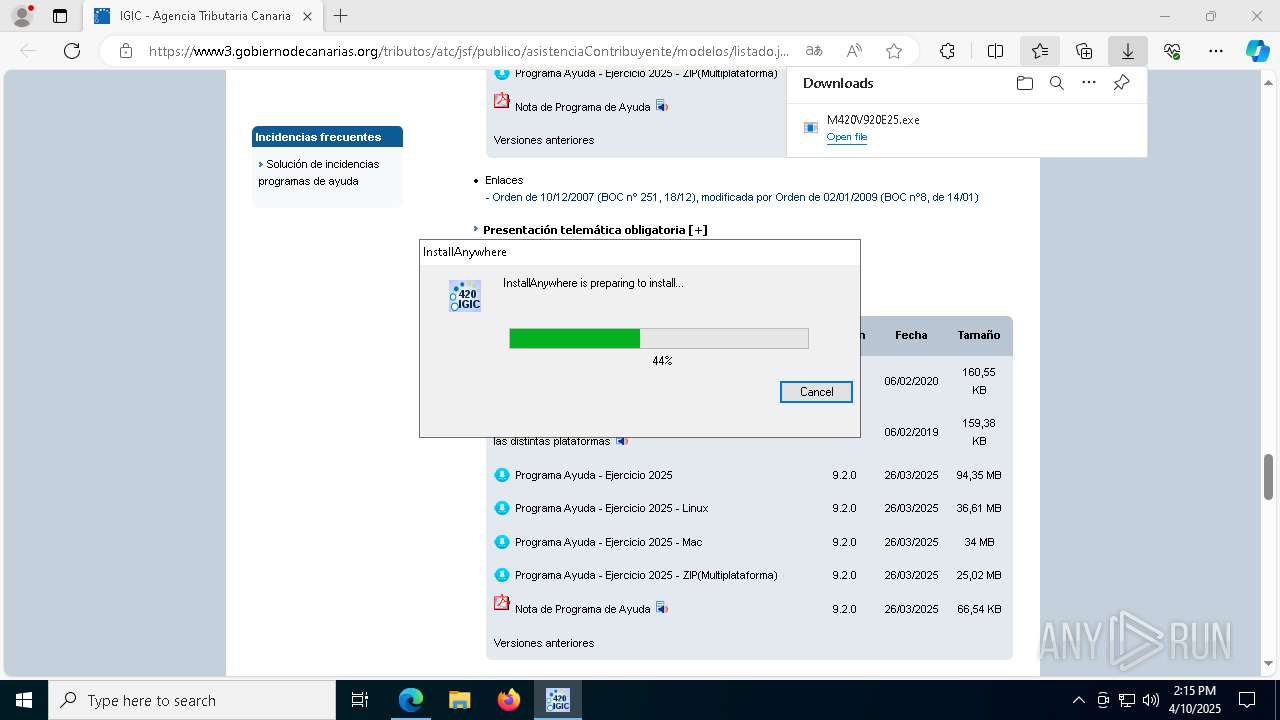
Process drops legitimate windows executable
- M420V920E25.exe (PID: 1812)
- javaw.exe (PID: 5228)
Executable content was dropped or overwritten
- M420V920E25.exe (PID: 1812)
- IconChng.exe (PID: 6228)
- javaw.exe (PID: 5228)
The process drops C-runtime libraries
- M420V920E25.exe (PID: 1812)
- javaw.exe (PID: 5228)
Uses ICACLS.EXE to modify access control lists
- javaw.exe (PID: 5228)
Accesses operating system name via WMI (SCRIPT)
- WMIC.exe (PID: 1676)
- WMIC.exe (PID: 6044)
Uses WMIC.EXE to obtain operating system information
- javaw.exe (PID: 5228)
Uses ATTRIB.EXE to modify file attributes
- javaw.exe (PID: 5228)
There is functionality for taking screenshot (YARA)
- javaw.exe (PID: 5228)
Checks for Java to be installed
- java.exe (PID: 7744)
Creates a software uninstall entry
- javaw.exe (PID: 5228)
INFO
Application launched itself
- msedge.exe (PID: 1512)
Reads Environment values
- identity_helper.exe (PID: 8048)
Autorun file from Downloads
- msedge.exe (PID: 7872)
Reads the computer name
- identity_helper.exe (PID: 8048)
- M420V920E25.exe (PID: 1812)
- javaw.exe (PID: 5228)
- javaw.exe (PID: 4976)
Executable content was dropped or overwritten
- msedge.exe (PID: 1512)
- msedge.exe (PID: 5548)
The sample compiled with english language support
- M420V920E25.exe (PID: 1812)
- javaw.exe (PID: 5228)
- IconChng.exe (PID: 6228)
- msedge.exe (PID: 5548)
Create files in a temporary directory
- M420V920E25.exe (PID: 1812)
- javaw.exe (PID: 5228)
- java.exe (PID: 7744)
- javaw.exe (PID: 4976)
Checks supported languages
- identity_helper.exe (PID: 8048)
- M420V920E25.exe (PID: 208)
- M420V920E25.exe (PID: 1812)
- javaw.exe (PID: 5228)
- win64_32_x64.exe (PID: 7928)
- java.exe (PID: 7744)
- win64_32_x64.exe (PID: 7844)
- win64_32_x64.exe (PID: 6572)
- win64_32_x64.exe (PID: 4572)
- IconChng.exe (PID: 6228)
- win64_32_x64.exe (PID: 5936)
- remove.exe (PID: 1616)
- javaw.exe (PID: 4976)
Creates files in the program directory
- javaw.exe (PID: 5228)
- java.exe (PID: 7744)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 1676)
- WMIC.exe (PID: 8020)
- WMIC.exe (PID: 6044)
- ie4uinit.exe (PID: 4376)
- ie4uinit.exe (PID: 8164)
- ie4uinit.exe (PID: 5972)
- ie4uinit.exe (PID: 7928)
- OpenWith.exe (PID: 2616)
Reads the software policy settings
- slui.exe (PID: 516)
- slui.exe (PID: 6208)
Creates files or folders in the user directory
- ie4uinit.exe (PID: 8164)
- javaw.exe (PID: 5228)
- javaw.exe (PID: 4976)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 2616)
Application based on Java
- javaw.exe (PID: 4976)
Checks proxy server information
- slui.exe (PID: 6208)
Reads the machine GUID from the registry
- javaw.exe (PID: 4976)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
220
Monitored processes
85
Malicious processes
10
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | C:\Users\admin\AppData\Local\Temp\I1744294535\Windows\M420V920E25.exe | C:\Users\admin\AppData\Local\Temp\I1744294535\Windows\M420V920E25.exe | — | M420V920E25.exe | |||||||||||
User: admin Company: Flexera Software Integrity Level: HIGH Description: LaunchAnywhere Exit code: 0 Version: 18, 0, 0, 0 Modules
| |||||||||||||||
| 516 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=28 --mojo-platform-channel-handle=6284 --field-trial-handle=2288,i,8602374458845280950,5596216364666438372,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 896 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | attrib.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1272 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5308 --field-trial-handle=2288,i,8602374458845280950,5596216364666438372,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1272 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_collections.mojom.CollectionsDataManager --lang=en-US --service-sandbox-type=collections --no-appcompat-clear --mojo-platform-channel-handle=3924 --field-trial-handle=2288,i,8602374458845280950,5596216364666438372,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1512 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" "https://www3.gobiernodecanarias.org/tributos/atc/jsf/publico/asistenciaContribuyente/modelos/listado.jsp?tributo=IGIC" | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1568 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6608 --field-trial-handle=2288,i,8602374458845280950,5596216364666438372,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1616 | "C:\Users\admin\AppData\Local\Temp\remove.exe" | C:\Users\admin\AppData\Local\Temp\remove.exe | — | javaw.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1676 | wmic os get name | C:\Windows\SysWOW64\wbem\WMIC.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 783
Read events
10 561
Write events
150
Delete events
72
Modification events
| (PID) Process: | (1512) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1512) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1512) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1512) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (1512) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: F9454E7E03912F00 | |||
| (PID) Process: | (1512) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: D9E8557E03912F00 | |||
| (PID) Process: | (1512) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197458 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {C87C0F9A-E64A-47D4-9E57-39462BE823C4} | |||
| (PID) Process: | (1512) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197458 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {C62FEF10-F45D-4037-A5A1-FAC9D9463C53} | |||
| (PID) Process: | (1512) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197458 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {46E1DB4B-44EE-4E96-BBC7-112FF725D6CF} | |||
| (PID) Process: | (1512) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197458 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {368466F3-5427-4596-BF20-2701A061E200} | |||
Executable files
268
Suspicious files
382
Text files
211
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1512 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10b661.TMP | — | |
MD5:— | SHA256:— | |||
| 1512 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1512 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10b671.TMP | — | |
MD5:— | SHA256:— | |||
| 1512 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1512 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10b661.TMP | — | |
MD5:— | SHA256:— | |||
| 1512 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1512 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10b671.TMP | — | |
MD5:— | SHA256:— | |||
| 1512 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1512 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10b671.TMP | — | |
MD5:— | SHA256:— | |||
| 1512 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
157
DNS requests
87
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1764 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5596 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1744637464&P2=404&P3=2&P4=AVIu6mvpKj3njWo5xi7YA1Qff%2fG%2bbfbQs8OMm6xmzCsDQ2hLiRqmlHtKfFL0gFFfAgGrS%2fNme6%2bwdS9Wd9wGgw%3d%3d | unknown | — | — | whitelisted |
1764 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5596 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1744637464&P2=404&P3=2&P4=AVIu6mvpKj3njWo5xi7YA1Qff%2fG%2bbfbQs8OMm6xmzCsDQ2hLiRqmlHtKfFL0gFFfAgGrS%2fNme6%2bwdS9Wd9wGgw%3d%3d | unknown | — | — | whitelisted |
5596 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1744637464&P2=404&P3=2&P4=AVIu6mvpKj3njWo5xi7YA1Qff%2fG%2bbfbQs8OMm6xmzCsDQ2hLiRqmlHtKfFL0gFFfAgGrS%2fNme6%2bwdS9Wd9wGgw%3d%3d | unknown | — | — | whitelisted |
5596 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1744637464&P2=404&P3=2&P4=AVIu6mvpKj3njWo5xi7YA1Qff%2fG%2bbfbQs8OMm6xmzCsDQ2hLiRqmlHtKfFL0gFFfAgGrS%2fNme6%2bwdS9Wd9wGgw%3d%3d | unknown | — | — | whitelisted |
5596 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1744637464&P2=404&P3=2&P4=AVIu6mvpKj3njWo5xi7YA1Qff%2fG%2bbfbQs8OMm6xmzCsDQ2hLiRqmlHtKfFL0gFFfAgGrS%2fNme6%2bwdS9Wd9wGgw%3d%3d | unknown | — | — | whitelisted |
5596 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1744637464&P2=404&P3=2&P4=AVIu6mvpKj3njWo5xi7YA1Qff%2fG%2bbfbQs8OMm6xmzCsDQ2hLiRqmlHtKfFL0gFFfAgGrS%2fNme6%2bwdS9Wd9wGgw%3d%3d | unknown | — | — | whitelisted |
5596 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1744637464&P2=404&P3=2&P4=AVIu6mvpKj3njWo5xi7YA1Qff%2fG%2bbfbQs8OMm6xmzCsDQ2hLiRqmlHtKfFL0gFFfAgGrS%2fNme6%2bwdS9Wd9wGgw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1512 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7320 | msedge.exe | 13.107.43.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7320 | msedge.exe | 150.171.29.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7320 | msedge.exe | 93.188.136.129:443 | www.gobiernodecanarias.org | Gobierno De Canarias | ES | whitelisted |
7320 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7320 | msedge.exe | 93.188.137.126:443 | www3.gobiernodecanarias.org | Gobierno De Canarias | ES | whitelisted |
7320 | msedge.exe | 13.107.253.45:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7320 | msedge.exe | 23.50.131.74:443 | bzib.nelreports.net | Akamai International B.V. | DE | whitelisted |
7320 | msedge.exe | 104.126.37.161:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| whitelisted |
www3.gobiernodecanarias.org |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
www.gobiernodecanarias.org |
| whitelisted |
www.bing.com |
| whitelisted |
f1-eu.readspeaker.com |
| whitelisted |
cse.google.com |
| whitelisted |