| File name: | 2025-05-25_a597f0f910336931aa0725ec9bef560a_amadey_black-basta_cryptbot_elex_luca-stealer_lynx |
| Full analysis: | https://app.any.run/tasks/ac0dcae5-fae4-4acb-a07f-378ddfbac050 |
| Verdict: | Malicious activity |
| Analysis date: | May 25, 2025, 15:53:32 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | A597F0F910336931AA0725EC9BEF560A |
| SHA1: | B5228DB12F3C76996E8CD8378B115F4971C59363 |
| SHA256: | B483201C1AF77D3E7625AC432DA96829CFBC4824E4C8E07305110C0F064522A8 |
| SSDEEP: | 98304:Q53MvTN5M0vzM8ZBhKCxwxCsuj3ZzeDESpNEzudey8MaTdwt2l4M/yrpKACT7tY/:PbQNp2YuFkgidhOlO |
MALICIOUS
GENERIC has been found (auto)
- rundll32.exe (PID: 7752)
- rundll32.exe (PID: 7200)
- drvinst.exe (PID: 4688)
Changes the autorun value in the registry
- rundll32.exe (PID: 7752)
- rundll32.exe (PID: 7200)
- rundll32.exe (PID: 4448)
- InfDefaultInstall.exe (PID: 7732)
Executing a file with an untrusted certificate
- IDMan.exe (PID: 8004)
- IDMan.exe (PID: 8044)
Starts NET.EXE for service management
- net.exe (PID: 896)
- Uninstall.exe (PID: 8180)
- Uninstall.exe (PID: 5408)
- net.exe (PID: 5984)
- net.exe (PID: 7268)
- net.exe (PID: 7768)
- net.exe (PID: 8156)
- net.exe (PID: 8248)
- net.exe (PID: 8344)
Registers / Runs the DLL via REGSVR32.EXE
- Uninstall.exe (PID: 8180)
- Uninstall.exe (PID: 5408)
SUSPICIOUS
Starts CMD.EXE for commands execution
- rundll32.exe (PID: 7752)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 7772)
Reads security settings of Internet Explorer
- 2025-05-25_a597f0f910336931aa0725ec9bef560a_amadey_black-basta_cryptbot_elex_luca-stealer_lynx.exe (PID: 7496)
- IDMan.exe (PID: 8044)
- IDMan.exe (PID: 8004)
- Uninstall.exe (PID: 8180)
- Uninstall.exe (PID: 5408)
Executable content was dropped or overwritten
- rundll32.exe (PID: 7752)
- IDMan.exe (PID: 8004)
- rundll32.exe (PID: 7200)
- drvinst.exe (PID: 4688)
Drops a system driver (possible attempt to evade defenses)
- rundll32.exe (PID: 7752)
- drvinst.exe (PID: 4688)
- rundll32.exe (PID: 7200)
Creates a software uninstall entry
- rundll32.exe (PID: 7752)
There is functionality for taking screenshot (YARA)
- 2025-05-25_a597f0f910336931aa0725ec9bef560a_amadey_black-basta_cryptbot_elex_luca-stealer_lynx.exe (PID: 7496)
- IDMIntegrator64.exe (PID: 8104)
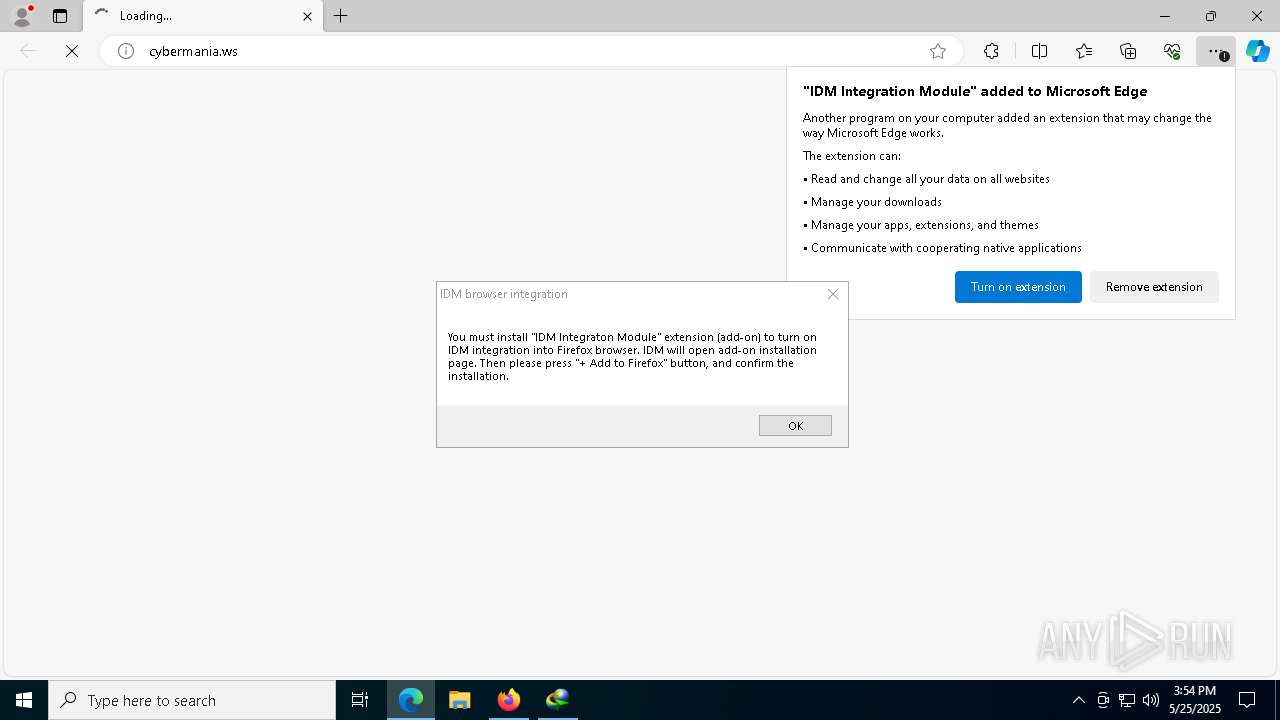
Creates/Modifies COM task schedule object
- IDMIntegrator64.exe (PID: 8116)
- IDMan.exe (PID: 8004)
- regsvr32.exe (PID: 7052)
- regsvr32.exe (PID: 8476)
Uses RUNDLL32.EXE to load library
- Uninstall.exe (PID: 8180)
- Uninstall.exe (PID: 5408)
Creates files in the driver directory
- drvinst.exe (PID: 4688)
Creates or modifies Windows services
- Uninstall.exe (PID: 8180)
- drvinst.exe (PID: 5164)
- drvinst.exe (PID: 7716)
- Uninstall.exe (PID: 5408)
INFO
Checks supported languages
- 2025-05-25_a597f0f910336931aa0725ec9bef560a_amadey_black-basta_cryptbot_elex_luca-stealer_lynx.exe (PID: 7496)
- IDMan.exe (PID: 8044)
- IDMIntegrator64.exe (PID: 8116)
- IDMan.exe (PID: 8004)
- Uninstall.exe (PID: 8180)
- IDMIntegrator64.exe (PID: 8104)
- drvinst.exe (PID: 4688)
- drvinst.exe (PID: 5164)
- drvinst.exe (PID: 7716)
- Uninstall.exe (PID: 5408)
Reads the computer name
- 2025-05-25_a597f0f910336931aa0725ec9bef560a_amadey_black-basta_cryptbot_elex_luca-stealer_lynx.exe (PID: 7496)
- IDMan.exe (PID: 8044)
- IDMan.exe (PID: 8004)
- IDMIntegrator64.exe (PID: 8104)
- Uninstall.exe (PID: 8180)
- drvinst.exe (PID: 4688)
- drvinst.exe (PID: 5164)
- drvinst.exe (PID: 7716)
- Uninstall.exe (PID: 5408)
Create files in a temporary directory
- 2025-05-25_a597f0f910336931aa0725ec9bef560a_amadey_black-basta_cryptbot_elex_luca-stealer_lynx.exe (PID: 7496)
- IDMan.exe (PID: 8004)
- IDMan.exe (PID: 8044)
- rundll32.exe (PID: 7200)
Creates files in the program directory
- rundll32.exe (PID: 7752)
- IDMan.exe (PID: 8004)
The sample compiled with english language support
- rundll32.exe (PID: 7752)
- IDMan.exe (PID: 8004)
- rundll32.exe (PID: 7200)
- drvinst.exe (PID: 4688)
Auto-launch of the file from Registry key
- rundll32.exe (PID: 7752)
- rundll32.exe (PID: 7200)
- rundll32.exe (PID: 4448)
- InfDefaultInstall.exe (PID: 7732)
The sample compiled with russian language support
- rundll32.exe (PID: 7752)
Manual execution by a user
- IDMan.exe (PID: 8044)
- grpconv.exe (PID: 7464)
- wscript.exe (PID: 8716)
- rundll32.exe (PID: 2092)
- wscript.exe (PID: 3800)
- rundll32.exe (PID: 4016)
- rundll32.exe (PID: 2780)
- rundll32.exe (PID: 2552)
Disables trace logs
- IDMan.exe (PID: 8004)
- IDMan.exe (PID: 8044)
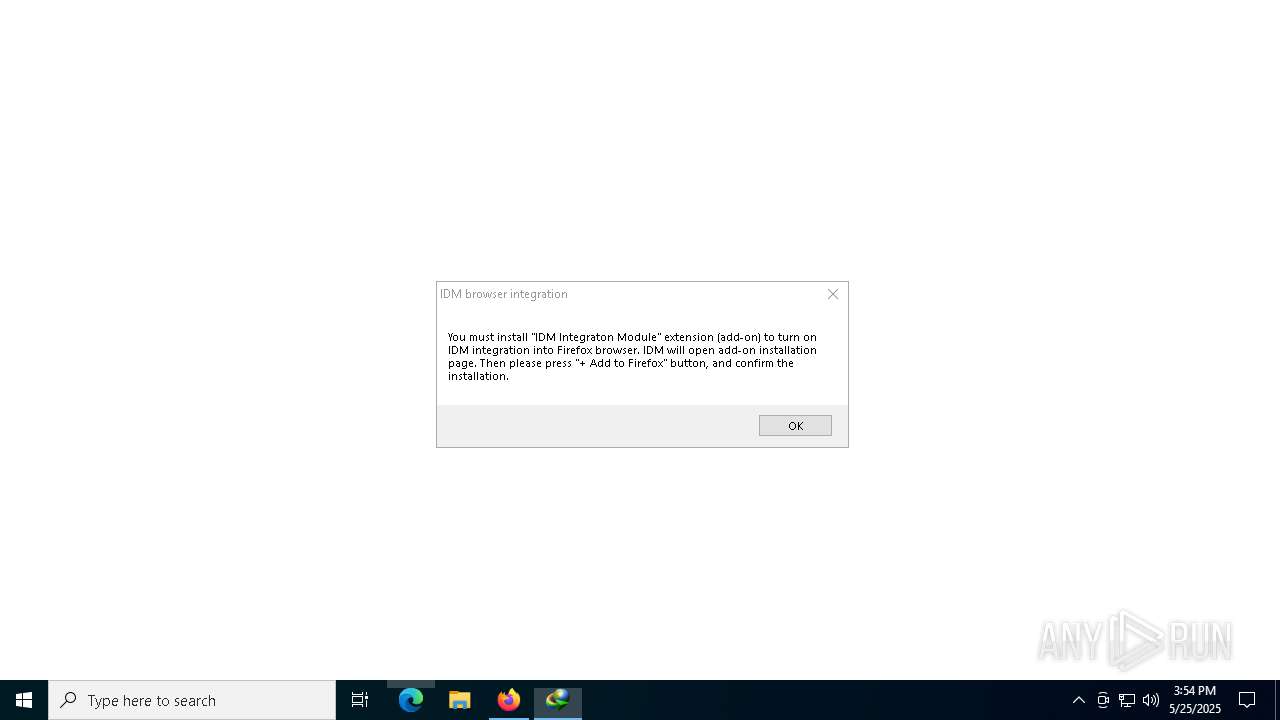
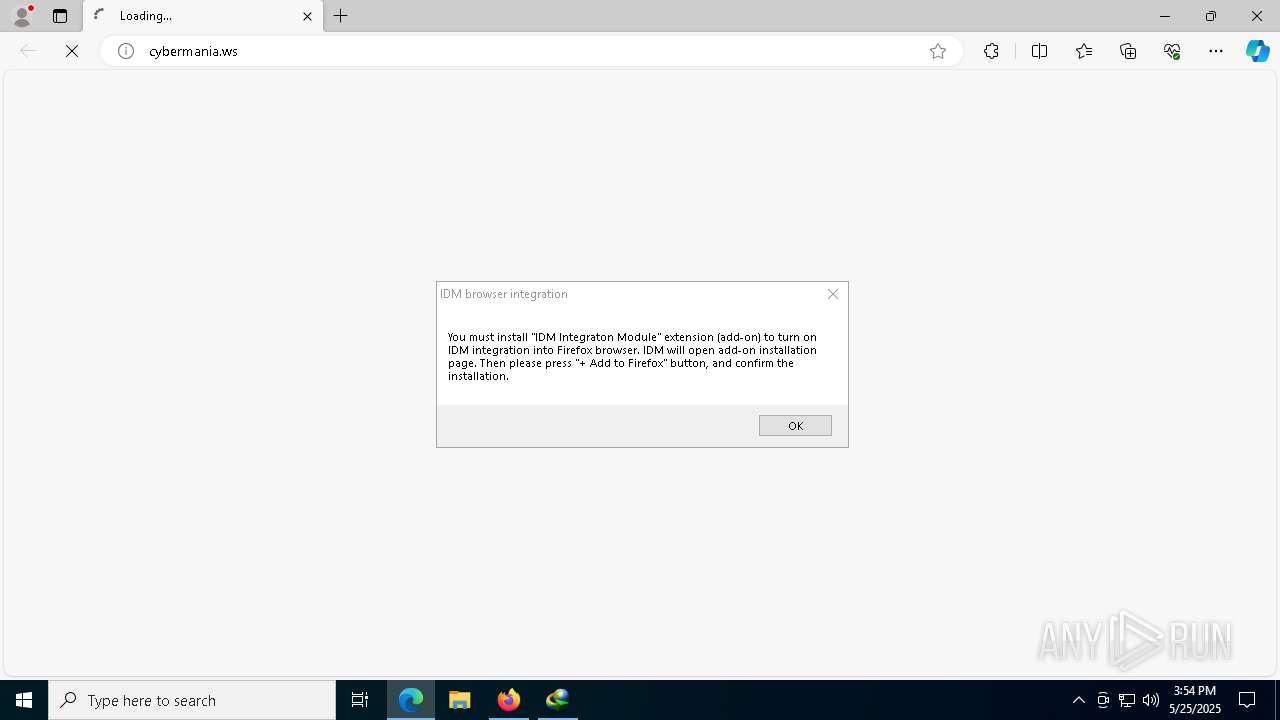
INTERNETDOWNLOADMANAGER mutex has been found
- IDMan.exe (PID: 8044)
- IDMIntegrator64.exe (PID: 8116)
- IDMIntegrator64.exe (PID: 8104)
- IDMan.exe (PID: 8004)
Reads the machine GUID from the registry
- IDMan.exe (PID: 8004)
- IDMan.exe (PID: 8044)
- drvinst.exe (PID: 4688)
Reads the software policy settings
- IDMan.exe (PID: 8004)
- IDMan.exe (PID: 8044)
- drvinst.exe (PID: 4688)
Checks proxy server information
- IDMan.exe (PID: 8004)
- IDMan.exe (PID: 8044)
- 2025-05-25_a597f0f910336931aa0725ec9bef560a_amadey_black-basta_cryptbot_elex_luca-stealer_lynx.exe (PID: 7496)
Creates files or folders in the user directory
- IDMan.exe (PID: 8004)
- IDMan.exe (PID: 8044)
Process checks computer location settings
- IDMan.exe (PID: 8004)
- IDMan.exe (PID: 8044)
- Uninstall.exe (PID: 8180)
- Uninstall.exe (PID: 5408)
Reads security settings of Internet Explorer
- runonce.exe (PID: 6268)
- runonce.exe (PID: 6724)
- runonce.exe (PID: 7696)
Application launched itself
- firefox.exe (PID: 6564)
- firefox.exe (PID: 960)
- msedge.exe (PID: 6632)
- firefox.exe (PID: 4724)
Reads the time zone
- runonce.exe (PID: 6268)
- runonce.exe (PID: 6724)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:02:12 14:02:19+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.42 |
| CodeSize: | 248320 |
| InitializedDataSize: | 180736 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x26560 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
254
Monitored processes
122
Malicious processes
9
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 232 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6600 --field-trial-handle=2344,i,10249507281583930761,14368409378917406296,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 496 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 896 | "C:\Windows\System32\net.exe" start IDMWFP | C:\Windows\SysWOW64\net.exe | — | Uninstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
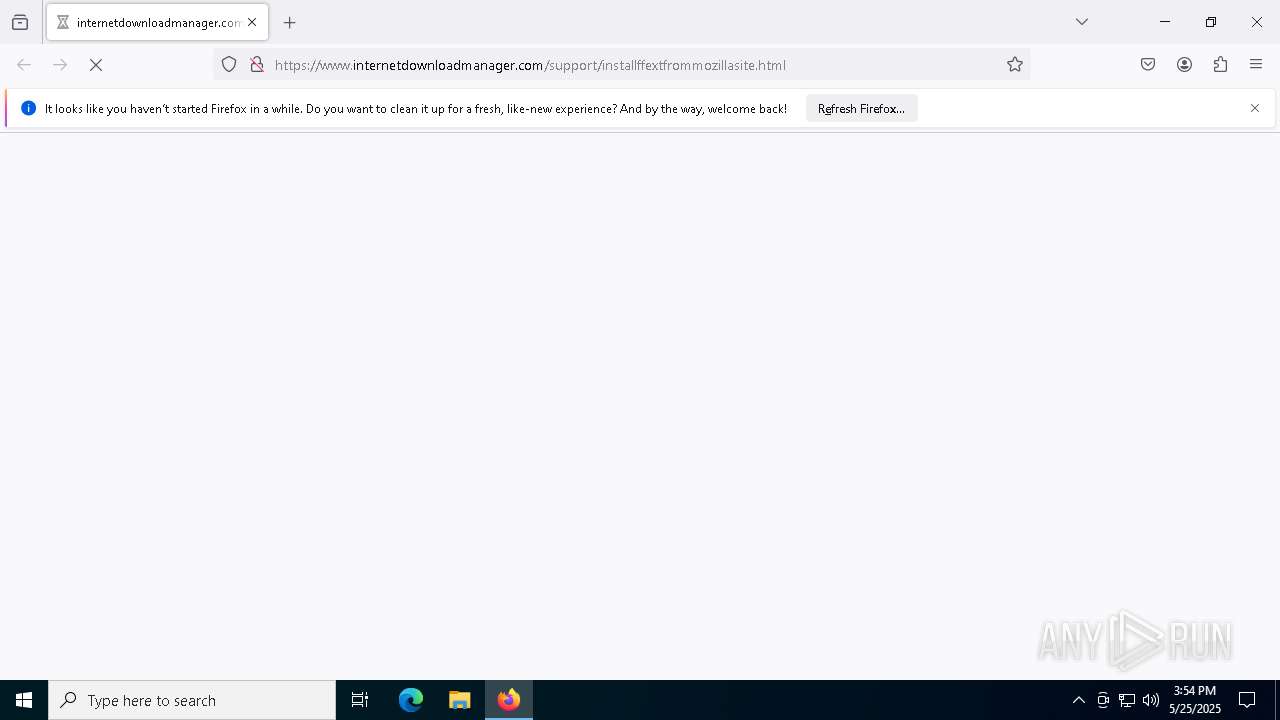
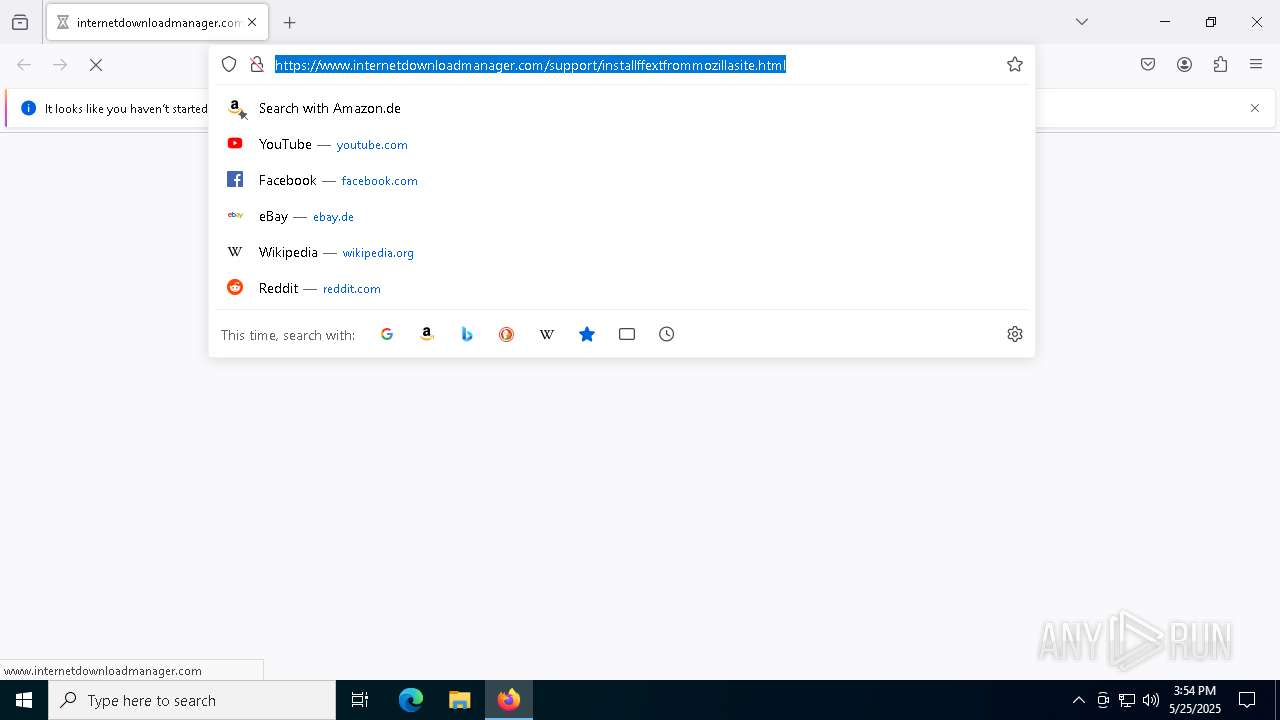
| 960 | "C:\Program Files\Mozilla Firefox\firefox.exe" https://www.internetdownloadmanager.com/support/installffextfrommozillasite.html | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1056 | "C:\Windows\System32\regsvr32.exe" /s "C:\Program Files (x86)\Internet Download Manager\IDMShellExt64.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | Uninstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1116 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --mojo-platform-channel-handle=4864 --field-trial-handle=2344,i,10249507281583930761,14368409378917406296,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1128 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5632 --field-trial-handle=2344,i,10249507281583930761,14368409378917406296,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1168 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5532 --field-trial-handle=2344,i,10249507281583930761,14368409378917406296,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1168 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=5604 --field-trial-handle=2344,i,10249507281583930761,14368409378917406296,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
48 525
Read events
47 743
Write events
727
Delete events
55
Modification events
| (PID) Process: | (7496) 2025-05-25_a597f0f910336931aa0725ec9bef560a_amadey_black-basta_cryptbot_elex_luca-stealer_lynx.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.inf\OpenWithProgids |
| Operation: | write | Name: | inffile |
Value: | |||
| (PID) Process: | (7496) 2025-05-25_a597f0f910336931aa0725ec9bef560a_amadey_black-basta_cryptbot_elex_luca-stealer_lynx.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\System32\InfDefaultInstall.exe.FriendlyAppName |
Value: INF Default Install | |||
| (PID) Process: | (7496) 2025-05-25_a597f0f910336931aa0725ec9bef560a_amadey_black-basta_cryptbot_elex_luca-stealer_lynx.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\System32\InfDefaultInstall.exe.ApplicationCompany |
Value: Microsoft Corporation | |||
| (PID) Process: | (7752) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Internet Download Manager |
| Operation: | write | Name: | AdvIntDriverEnabled2 |
Value: 1 | |||
| (PID) Process: | (7752) rundll32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\DownloadManager |
| Operation: | write | Name: | bShLc2 |
Value: 1 | |||
| (PID) Process: | (7752) rundll32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\DownloadManager |
| Operation: | write | Name: | NewConnType |
Value: 3 | |||
| (PID) Process: | (7752) rundll32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\DownloadManager\netApps |
| Operation: | write | Name: | 00002action |
Value: turn_off | |||
| (PID) Process: | (7752) rundll32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\DownloadManager |
| Operation: | write | Name: | bHDIShwd |
Value: 1 | |||
| (PID) Process: | (7752) rundll32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\DownloadManager |
| Operation: | write | Name: | TrayIcon |
Value: 1 | |||
| (PID) Process: | (7752) rundll32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\DownloadManager |
| Operation: | write | Name: | nDESC8 |
Value: 1 | |||
Executable files
149
Suspicious files
476
Text files
501
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7496 | 2025-05-25_a597f0f910336931aa0725ec9bef560a_amadey_black-basta_cryptbot_elex_luca-stealer_lynx.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\IDM.cab | — | |
MD5:— | SHA256:— | |||
| 7496 | 2025-05-25_a597f0f910336931aa0725ec9bef560a_amadey_black-basta_cryptbot_elex_luca-stealer_lynx.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\EN.inf | binary | |
MD5:A79F1E9F9AA2FA7E4F2C82F3D0AF0024 | SHA256:43210B6F0E7E97477DADD64C278B97807D32753654FB892D3EC7E5405959A7C3 | |||
| 7752 | rundll32.exe | C:\Program Files (x86)\Internet Download Manager\Toolbar\SETD508.tmp | image | |
MD5:0DC0B394953344D464B60D6FA520F2AB | SHA256:EDA9A334B8B18B02809537441BE62656445A4BFB01E19EFEDF415514CDA84476 | |||
| 7496 | 2025-05-25_a597f0f910336931aa0725ec9bef560a_amadey_black-basta_cryptbot_elex_luca-stealer_lynx.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\CN.inf | binary | |
MD5:DA5B29A14112B2D375AAD908740A105A | SHA256:64107E57B92ABF7D0AAC79781FBA1CDC9FAA6601FD5F3AB3E5192E1F6EFD0378 | |||
| 7496 | 2025-05-25_a597f0f910336931aa0725ec9bef560a_amadey_black-basta_cryptbot_elex_luca-stealer_lynx.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\CyberMania.url | url | |
MD5:9994A4E0CDEF79EA6A8180AEA7CD6FEB | SHA256:4A40F4593F87FDA18590179C240DA85A4A895D774BADA80F6CE33D82A7AF0D1B | |||
| 7752 | rundll32.exe | C:\Program Files (x86)\Internet Download Manager\Toolbar\SETD4B7.tmp | image | |
MD5:DEDDE6DA418C816B65BC4EE76302BD82 | SHA256:2C07B067A6B06C7D87D408E16F7047615B098DB2328515E92166FDD6422E7099 | |||
| 7752 | rundll32.exe | C:\Program Files (x86)\Internet Download Manager\Toolbar\SETD4E7.tmp | image | |
MD5:DEDDE6DA418C816B65BC4EE76302BD82 | SHA256:2C07B067A6B06C7D87D408E16F7047615B098DB2328515E92166FDD6422E7099 | |||
| 7752 | rundll32.exe | C:\Program Files (x86)\Internet Download Manager\Toolbar\3d_largeHot_3_hdpi15.bmp | image | |
MD5:0DC0B394953344D464B60D6FA520F2AB | SHA256:EDA9A334B8B18B02809537441BE62656445A4BFB01E19EFEDF415514CDA84476 | |||
| 7752 | rundll32.exe | C:\Program Files (x86)\Internet Download Manager\Toolbar\3d_largeHot_3.bmp | image | |
MD5:DEDDE6DA418C816B65BC4EE76302BD82 | SHA256:2C07B067A6B06C7D87D408E16F7047615B098DB2328515E92166FDD6422E7099 | |||
| 7752 | rundll32.exe | C:\Program Files (x86)\Internet Download Manager\Toolbar\SETD4F7.tmp | image | |
MD5:0DC0B394953344D464B60D6FA520F2AB | SHA256:EDA9A334B8B18B02809537441BE62656445A4BFB01E19EFEDF415514CDA84476 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
585
TCP/UDP connections
226
DNS requests
246
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 204 | 151.101.3.19:443 | https://contile.services.mozilla.com/v1/tiles | unknown | — | — | unknown |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 34.160.144.191:443 | https://content-signature-2.cdn.mozilla.net/chains/remote-settings.content-signature.mozilla.org-2024-03-20-10-07-03.chain | unknown | text | 5.23 Kb | whitelisted |
— | — | POST | 200 | 151.101.3.19:443 | https://spocs.getpocket.com/spocs | unknown | binary | 1.15 Kb | whitelisted |
— | — | GET | 101 | 34.107.243.93:443 | https://push.services.mozilla.com/ | unknown | — | — | unknown |
— | — | GET | 200 | 34.149.100.209:443 | https://firefox.settings.services.mozilla.com/v1/buckets/main/collections/ms-language-packs/records/cfr-v1-en-US | unknown | binary | 330 b | whitelisted |
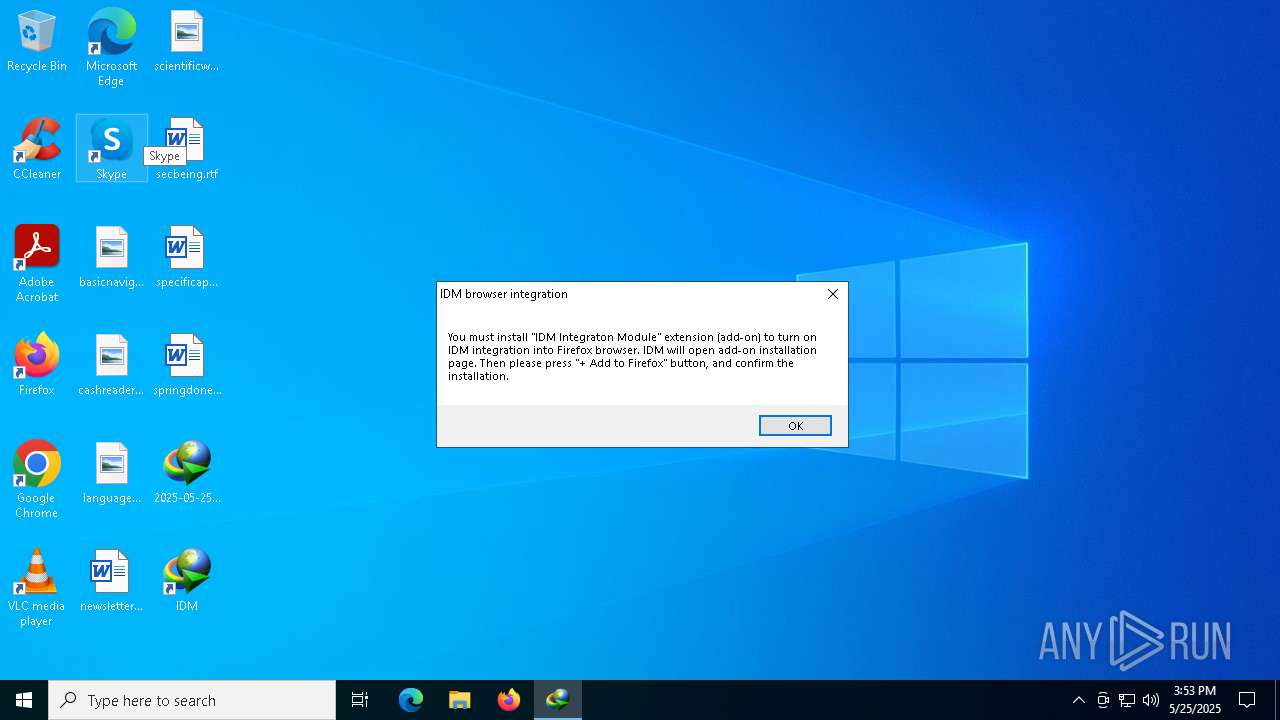
— | — | GET | 302 | 169.61.27.133:443 | https://www.internetdownloadmanager.com/support/installffextfrommozillasite.html | unknown | html | 260 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
2104 | svchost.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
960 | firefox.exe | 169.61.27.133:443 | secure.internetdownloadmanager.com | SOFTLAYER | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
test.internetdownloadmanager.com |
| whitelisted |
secure.internetdownloadmanager.com |
| whitelisted |
www.internetdownloadmanager.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
8216 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
8216 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
8216 | msedge.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
— | — | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
8216 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
8216 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] An application monitoring request to sentry .io |