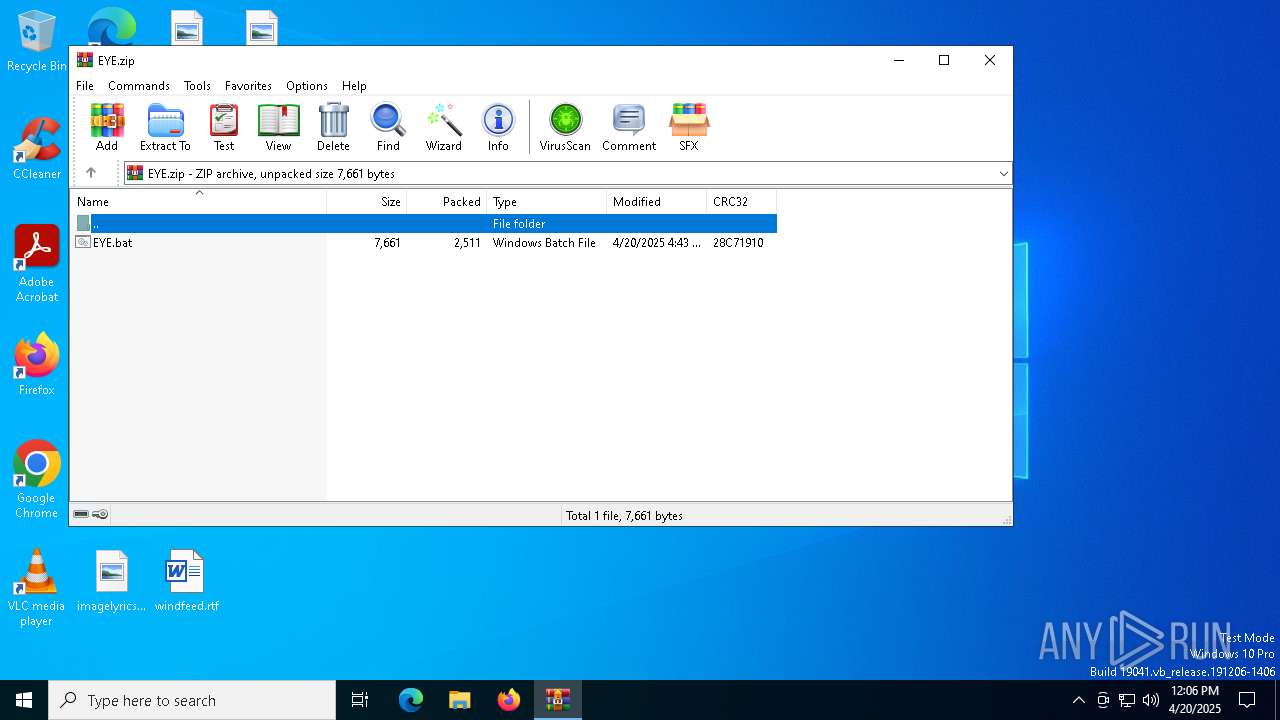
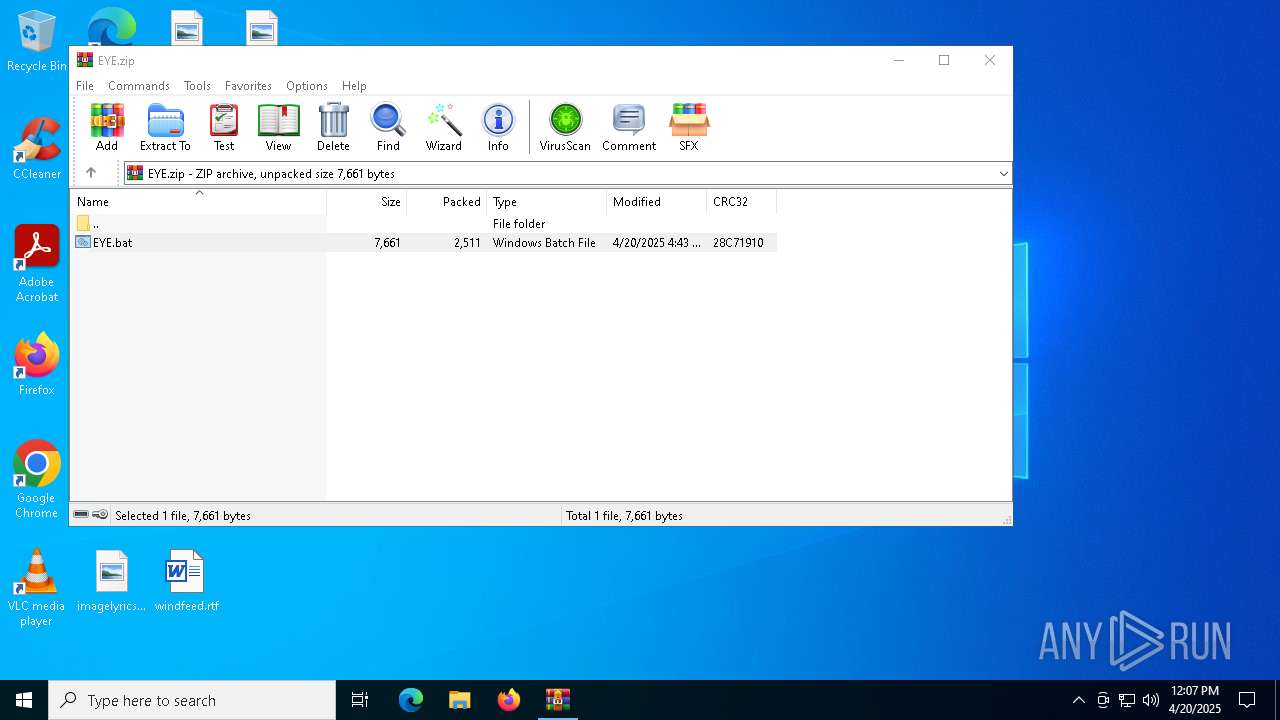
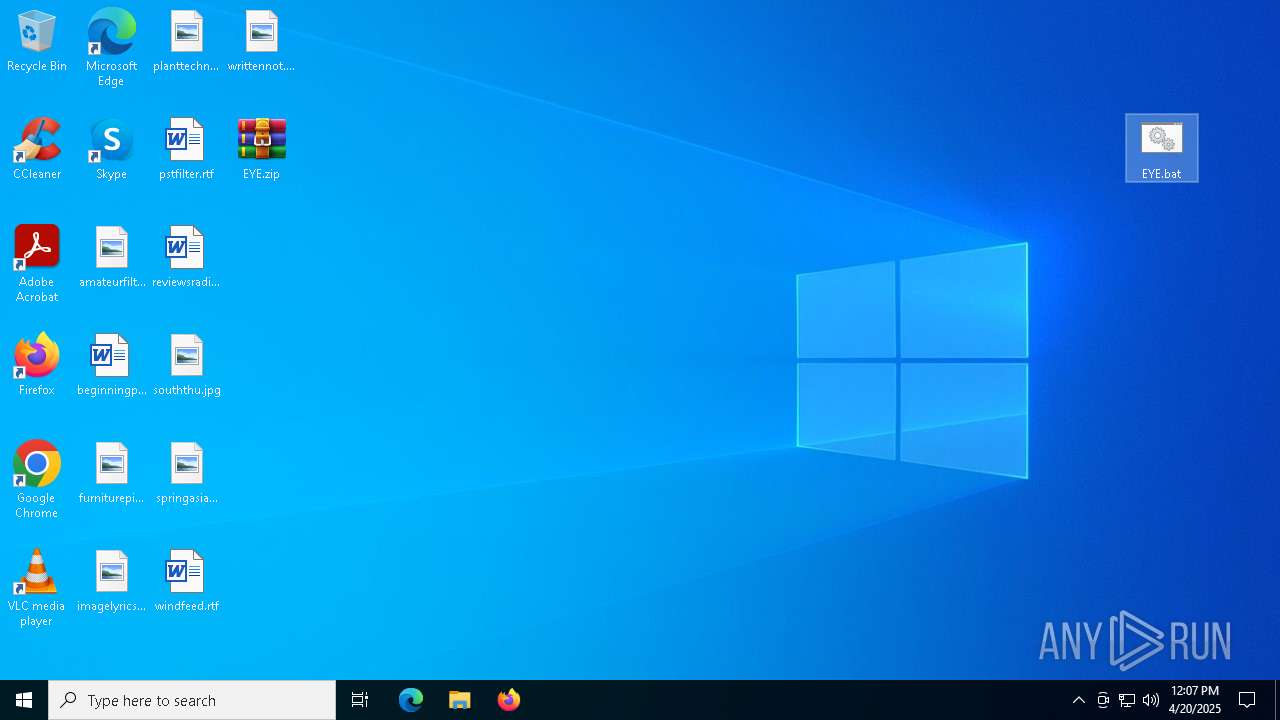
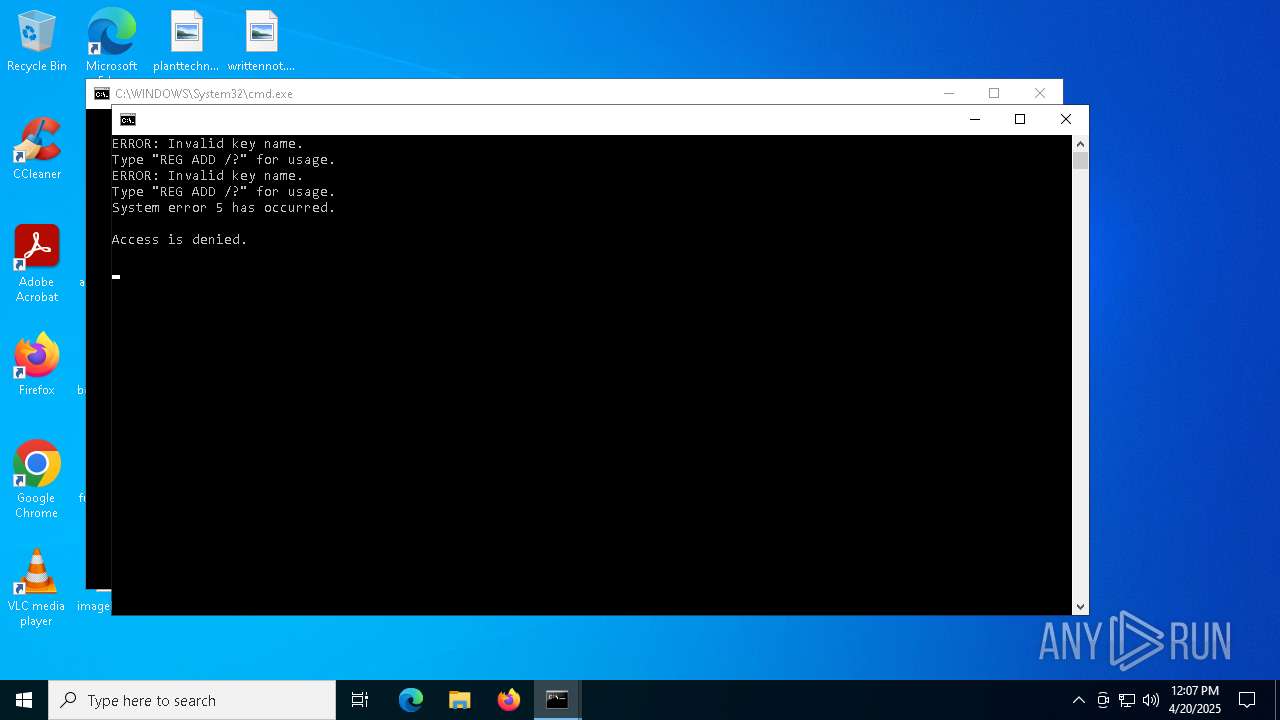
| File name: | EYE.zip |
| Full analysis: | https://app.any.run/tasks/19cc5480-c87f-4d2a-a1c8-5ab713acc268 |
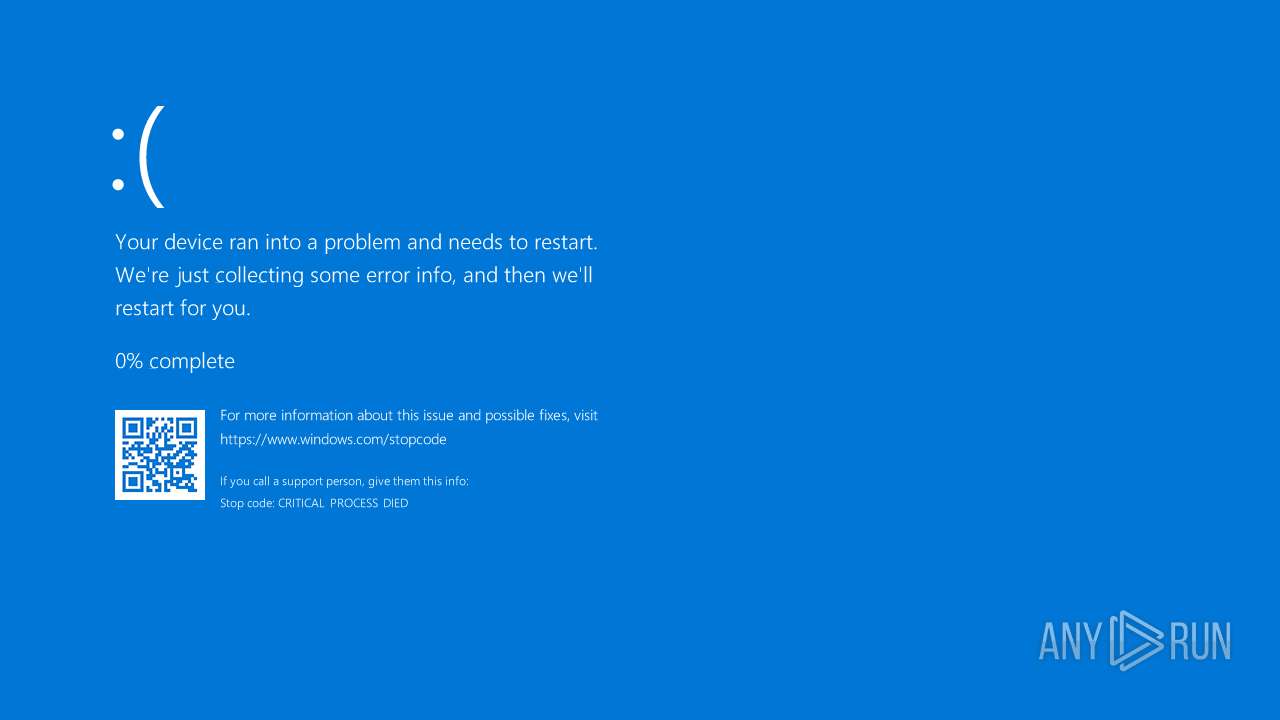
| Verdict: | Malicious activity |
| Analysis date: | April 20, 2025, 12:06:32 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 63559CCBD4C2622F8EED327D32550CA3 |
| SHA1: | B8B3BB57E39D78CE1B9A195ED66CC8950A1BF2B7 |
| SHA256: | B479060FCB1B9797AC23ACAE6C3CA4FF26B8C5A7FF82D403F034372D4792B8EE |
| SSDEEP: | 96:r/Y2avxId5R0TNNBFdzjV0/Z4C7OVBbDipBghbSehHpYqQogdR:rY20CdMD1RmIpipkWeRaR |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5332)
Starts NET.EXE for service management
- cmd.exe (PID: 5756)
- net.exe (PID: 5204)
Create files in the Startup directory
- cmd.exe (PID: 5756)
Starts NET.EXE to view/add/change user profiles
- cmd.exe (PID: 5756)
- net.exe (PID: 6108)
- net.exe (PID: 1748)
- net.exe (PID: 5600)
- net.exe (PID: 1228)
- net.exe (PID: 3100)
- net.exe (PID: 5408)
- net.exe (PID: 4200)
- net.exe (PID: 6424)
- net.exe (PID: 5204)
- net.exe (PID: 6828)
- net.exe (PID: 3020)
- net.exe (PID: 4724)
- net.exe (PID: 208)
- net.exe (PID: 5548)
- net.exe (PID: 1660)
- net.exe (PID: 5304)
- net.exe (PID: 6424)
- net.exe (PID: 5744)
- net.exe (PID: 6828)
- net.exe (PID: 300)
- net.exe (PID: 2088)
- net.exe (PID: 3332)
- net.exe (PID: 5548)
- net.exe (PID: 1512)
- net.exe (PID: 4272)
- net.exe (PID: 6940)
- net.exe (PID: 5960)
- net.exe (PID: 5204)
- net.exe (PID: 6660)
- net.exe (PID: 6424)
- net.exe (PID: 1040)
- net.exe (PID: 2136)
- net.exe (PID: 6940)
- net.exe (PID: 2108)
- net.exe (PID: 5020)
- net.exe (PID: 2064)
- net.exe (PID: 6424)
- net.exe (PID: 3888)
- net.exe (PID: 5512)
- net.exe (PID: 6828)
- net.exe (PID: 5020)
- net.exe (PID: 680)
- net.exe (PID: 5668)
- net.exe (PID: 3968)
- net.exe (PID: 1812)
- net.exe (PID: 2064)
- net.exe (PID: 6640)
- net.exe (PID: 3968)
- net.exe (PID: 5392)
- net.exe (PID: 3140)
- net.exe (PID: 5244)
- net.exe (PID: 4200)
- net.exe (PID: 6940)
- net.exe (PID: 5668)
- net.exe (PID: 5020)
- net.exe (PID: 2064)
- net.exe (PID: 6148)
- net.exe (PID: 2392)
- net.exe (PID: 644)
- net.exe (PID: 4880)
- net.exe (PID: 2392)
- net.exe (PID: 3332)
- net.exe (PID: 6108)
- net.exe (PID: 4688)
- net.exe (PID: 1348)
- net.exe (PID: 920)
- net.exe (PID: 1616)
- net.exe (PID: 1812)
- net.exe (PID: 3396)
- net.exe (PID: 736)
- net.exe (PID: 6940)
- net.exe (PID: 1660)
- net.exe (PID: 208)
- net.exe (PID: 5668)
- net.exe (PID: 5800)
- net.exe (PID: 4152)
- net.exe (PID: 924)
- net.exe (PID: 3140)
- net.exe (PID: 3968)
- net.exe (PID: 4608)
- net.exe (PID: 5216)
- net.exe (PID: 4896)
- net.exe (PID: 7020)
- net.exe (PID: 2344)
- net.exe (PID: 4728)
- net.exe (PID: 6416)
- net.exe (PID: 4000)
- net.exe (PID: 6476)
- net.exe (PID: 3176)
- net.exe (PID: 6852)
- net.exe (PID: 6256)
- net.exe (PID: 776)
- net.exe (PID: 3804)
- net.exe (PID: 5132)
- net.exe (PID: 616)
- net.exe (PID: 6644)
- net.exe (PID: 2664)
- net.exe (PID: 1452)
- net.exe (PID: 6512)
- net.exe (PID: 5124)
- net.exe (PID: 6048)
- net.exe (PID: 6728)
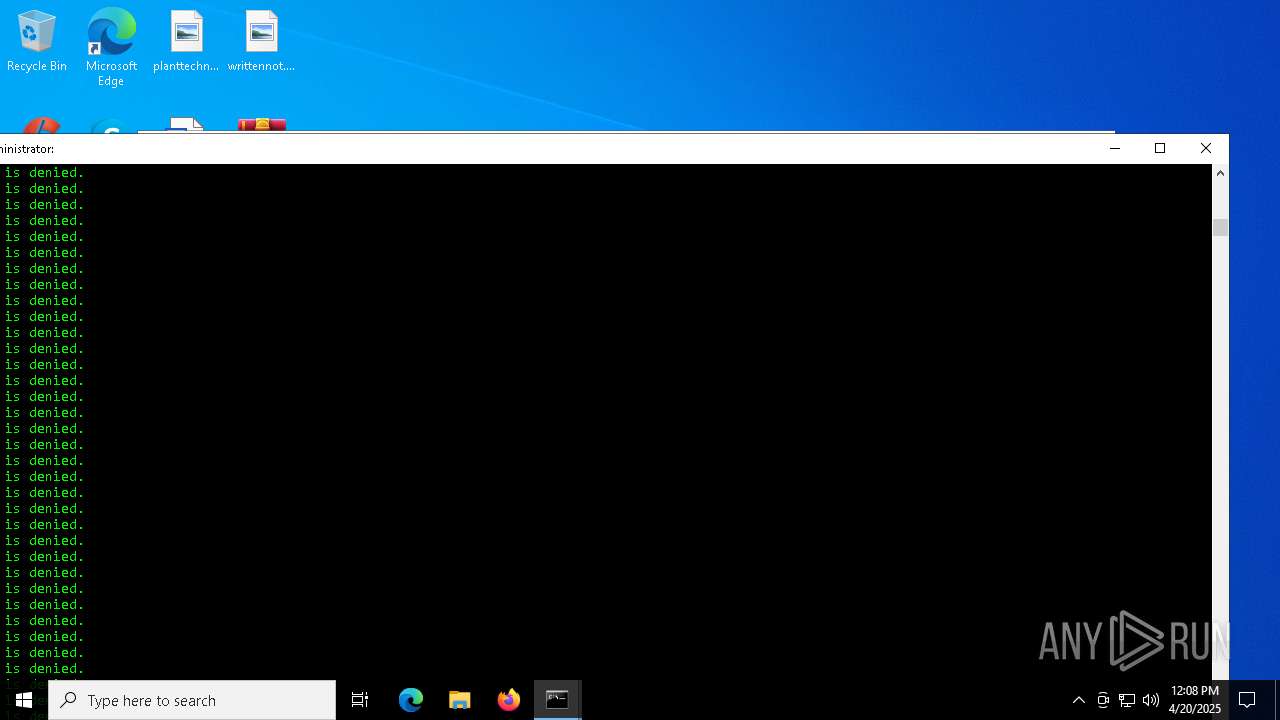
Disables task manager
- reg.exe (PID: 3884)
SUSPICIOUS
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 5256)
- cmd.exe (PID: 5756)
Application launched itself
- cmd.exe (PID: 2240)
- cmd.exe (PID: 5256)
- cmd.exe (PID: 5756)
Executing commands from a ".bat" file
- cmd.exe (PID: 5256)
- cmd.exe (PID: 2240)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 5256)
- cmd.exe (PID: 2240)
- cmd.exe (PID: 5756)
Uses NETSH.EXE to change the status of the firewall
- cmd.exe (PID: 5756)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 5756)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 5756)
Executing commands from ".cmd" file
- cmd.exe (PID: 5756)
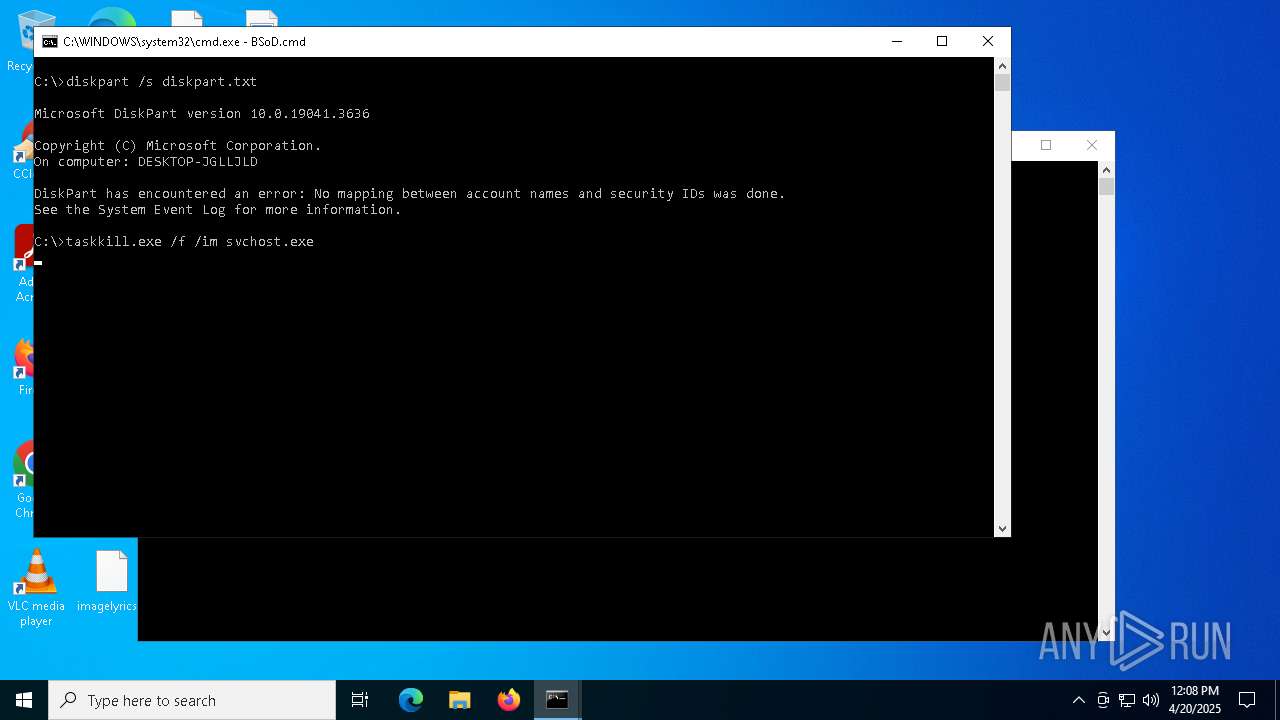
Starts application with an unusual extension
- cmd.exe (PID: 4120)
Process uses IPCONFIG to get network configuration information
- cmd.exe (PID: 5756)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 5756)
Uses WMIC.EXE to obtain physical disk drive information
- cmd.exe (PID: 5756)
Uses WMIC.EXE to obtain CPU information
- cmd.exe (PID: 5756)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 5756)
Uses SYSTEMINFO.EXE to read the environment
- cmd.exe (PID: 5756)
Stops a currently running service
- sc.exe (PID: 2084)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 5756)
Starts SC.EXE for service management
- cmd.exe (PID: 5756)
Windows service management via SC.EXE
- sc.exe (PID: 1812)
Executable content was dropped or overwritten
- Dism.exe (PID: 6192)
- cmd.exe (PID: 5756)
Starts a Microsoft application from unusual location
- DismHost.exe (PID: 4620)
- DismHost.exe (PID: 2800)
The process creates files with name similar to system file names
- Dism.exe (PID: 6192)
Starts NET.EXE to display or manage information about active sessions
- cmd.exe (PID: 5756)
- net.exe (PID: 1276)
Creates or modifies Windows services
- reg.exe (PID: 2100)
Process drops legitimate windows executable
- cmd.exe (PID: 5756)
The process drops C-runtime libraries
- cmd.exe (PID: 5756)
The process checks if it is being run in the virtual environment
- cmd.exe (PID: 5756)
Creates file in the systems drive root
- cmd.exe (PID: 5756)
- cmd.exe (PID: 2244)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2244)
INFO
Manual execution by a user
- cmd.exe (PID: 5256)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 3300)
- WMIC.exe (PID: 4892)
Checks supported languages
- mode.com (PID: 6660)
- scrnsave.scr (PID: 6940)
- DismHost.exe (PID: 4620)
- DismHost.exe (PID: 2800)
Starts MODE.COM to configure console settings
- mode.com (PID: 6660)
Reads the computer name
- scrnsave.scr (PID: 6940)
- DismHost.exe (PID: 4620)
- DismHost.exe (PID: 2800)
Reads the software policy settings
- slui.exe (PID: 5800)
- slui.exe (PID: 668)
Checks proxy server information
- slui.exe (PID: 5800)
The sample compiled with english language support
- Dism.exe (PID: 6192)
- cmd.exe (PID: 5756)
The sample compiled with chinese language support
- cmd.exe (PID: 5756)
The sample compiled with korean language support
- cmd.exe (PID: 5756)
Create files in a temporary directory
- Dism.exe (PID: 6192)
The sample compiled with Italian language support
- cmd.exe (PID: 5756)
The sample compiled with japanese language support
- cmd.exe (PID: 5756)
The sample compiled with russian language support
- cmd.exe (PID: 5756)
The sample compiled with german language support
- cmd.exe (PID: 5756)
The sample compiled with french language support
- cmd.exe (PID: 5756)
The sample compiled with spanish language support
- cmd.exe (PID: 5756)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:04:20 04:43:26 |
| ZipCRC: | 0x28c71910 |
| ZipCompressedSize: | 2511 |
| ZipUncompressedSize: | 7661 |
| ZipFileName: | EYE.bat |
Total processes
455
Monitored processes
321
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | net user 2468 26389 /add | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 208 | C:\WINDOWS\system32\net1 user 30436 22504 /add | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 208 | net user 31844 31199 /add | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 300 | net user 10773 23808 /add | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | net user 30829 5680 /add | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | net user 13171 17412 /add | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | C:\WINDOWS\system32\net1 user 16631 23352 /add | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | tskill /A ESAFE | C:\Windows\System32\tskill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Remote Desktop Services End Process Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | tskill /A norton* | C:\Windows\System32\tskill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Remote Desktop Services End Process Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
12 713
Read events
12 689
Write events
22
Delete events
2
Modification events
| (PID) Process: | (5332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\EYE.zip | |||
| (PID) Process: | (5332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (5332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
154
Suspicious files
9
Text files
17
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5332.13653\EYE.bat | text | |
MD5:3D5B07463A9CF117B46A8ACDE27FAEBF | SHA256:2E95B5D48F930A202F5E7DE4275E617EBAF6B89F3343DA6B394652D5E790027D | |||
| 5756 | cmd.exe | C:\Users\admin\Desktop\kill.txt | text | |
MD5:995F43DB4634D90C81AB3B716FAA1FF5 | SHA256:1AECC13A454167B47D503E8B9576A04DB3E8C4C7510AE8077140DC8EF17E5145 | |||
| 5756 | cmd.exe | C:\Users\admin\Desktop\9K21JM10B.log | text | |
MD5:995F43DB4634D90C81AB3B716FAA1FF5 | SHA256:1AECC13A454167B47D503E8B9576A04DB3E8C4C7510AE8077140DC8EF17E5145 | |||
| 5756 | cmd.exe | C:\Users\admin\Desktop\bsod.cmd | text | |
MD5:995F43DB4634D90C81AB3B716FAA1FF5 | SHA256:1AECC13A454167B47D503E8B9576A04DB3E8C4C7510AE8077140DC8EF17E5145 | |||
| 6192 | Dism.exe | C:\Users\admin\AppData\Local\Temp\2A516668-E618-4A99-99E5-7EF1D471827C\DismCorePS.dll | executable | |
MD5:35A07968EC37231249F3F072AE555E3A | SHA256:E5F25E5A170CB3D165C3D143EAE967B96AB80F88FB09176DA8591B0B68C77E00 | |||
| 6192 | Dism.exe | C:\Users\admin\AppData\Local\Temp\2A516668-E618-4A99-99E5-7EF1D471827C\AppxProvider.dll | executable | |
MD5:396C483D62FEA5FA0FD442C8DC99D4EF | SHA256:36F2AF43F10FD76FEEF65BF574D79D3E27FD40DAF61249880511543C1F17AD91 | |||
| 6192 | Dism.exe | C:\Users\admin\AppData\Local\Temp\2A516668-E618-4A99-99E5-7EF1D471827C\AssocProvider.dll | executable | |
MD5:B7DB592706D3EEFBCF0D5A166D462E56 | SHA256:DE21321272862E7C332E1724DC315F06F3ABE7A0340E61D351CAB208D6BBF059 | |||
| 6192 | Dism.exe | C:\Users\admin\AppData\Local\Temp\2A516668-E618-4A99-99E5-7EF1D471827C\CbsProvider.dll | executable | |
MD5:14932441A96E254B3D29D452CE1263A0 | SHA256:8FFF21CB7C88A0DD8C8E7B386604001F2974E75D229369A87BEE0BA18DA575F3 | |||
| 6192 | Dism.exe | C:\Users\admin\AppData\Local\Temp\2A516668-E618-4A99-99E5-7EF1D471827C\en-US\AppxProvider.dll.mui | executable | |
MD5:BD0DD9C5A602CB0AD7EABC16B3C1ABFC | SHA256:8AF0073F8A023F55866E48BF3B902DFA7F41C51B0E8B0FE06F8C496D41F9A7B3 | |||
| 6192 | Dism.exe | C:\Users\admin\AppData\Local\Temp\2A516668-E618-4A99-99E5-7EF1D471827C\DismHost.exe | executable | |
MD5:97CB1E2FCAB378421C4B91DF0C9F8310 | SHA256:E36BCF02BC11F560761E943D0FAD37417078F6CBB473F85C72FCBC89E2600C58 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
33
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.30:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
5408 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5408 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.216.77.30:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5408 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |