| File name: | Ground.exe |
| Full analysis: | https://app.any.run/tasks/329189ad-4d9d-4975-91a1-3d9087bdeb94 |
| Verdict: | Malicious activity |
| Analysis date: | January 14, 2025, 00:15:57 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 9 sections |
| MD5: | E838F53B2A7DD58BC2DBE4988009A125 |
| SHA1: | 002E41BBC5A477E0BE8D5C2B3183A24DF4E579B3 |
| SHA256: | B461B2FF99979370236584A70FA3C602099DF0D013FDD863CBB4D72FC04132AA |
| SSDEEP: | 12288:xltfL7HcV/td/EMPMtoMeU592ZmxeZZ+2Rf0i4VX7DJ5rSu3VUSVUH2I:xltf3cV3/NPNBNoLDfrSu3VUSVUHj |
MALICIOUS
MALPAINT mutex has been found
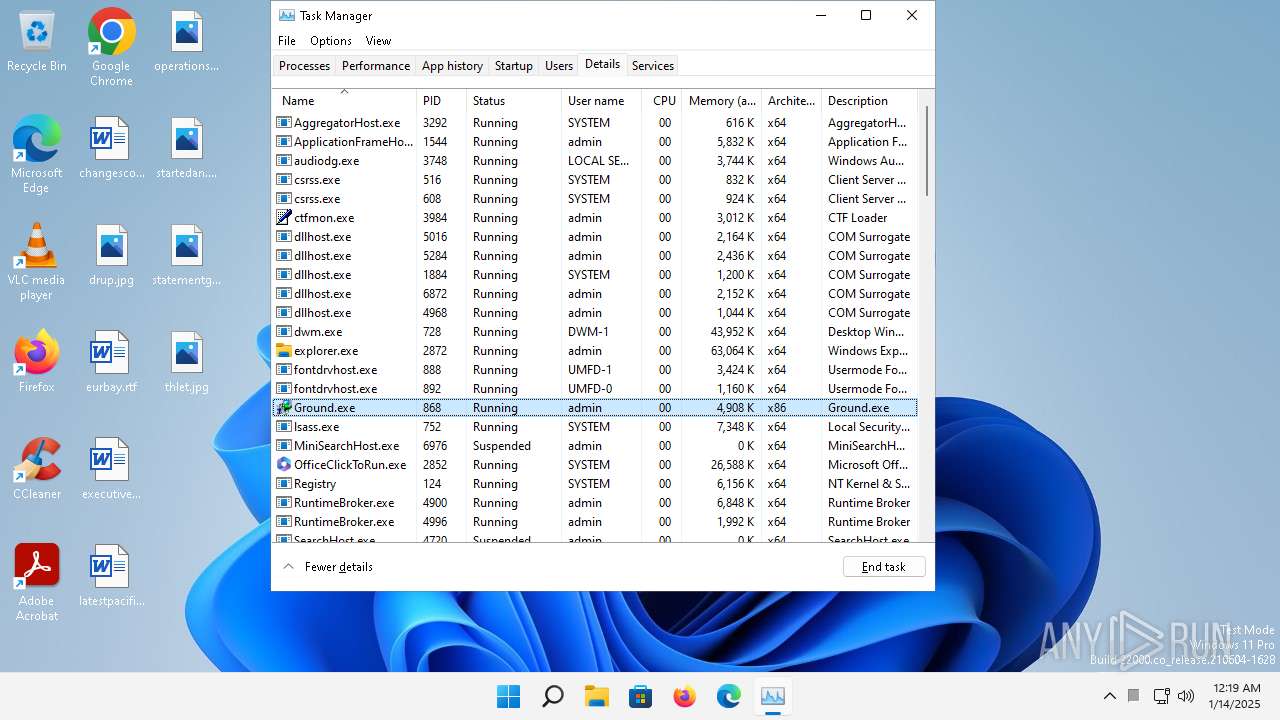
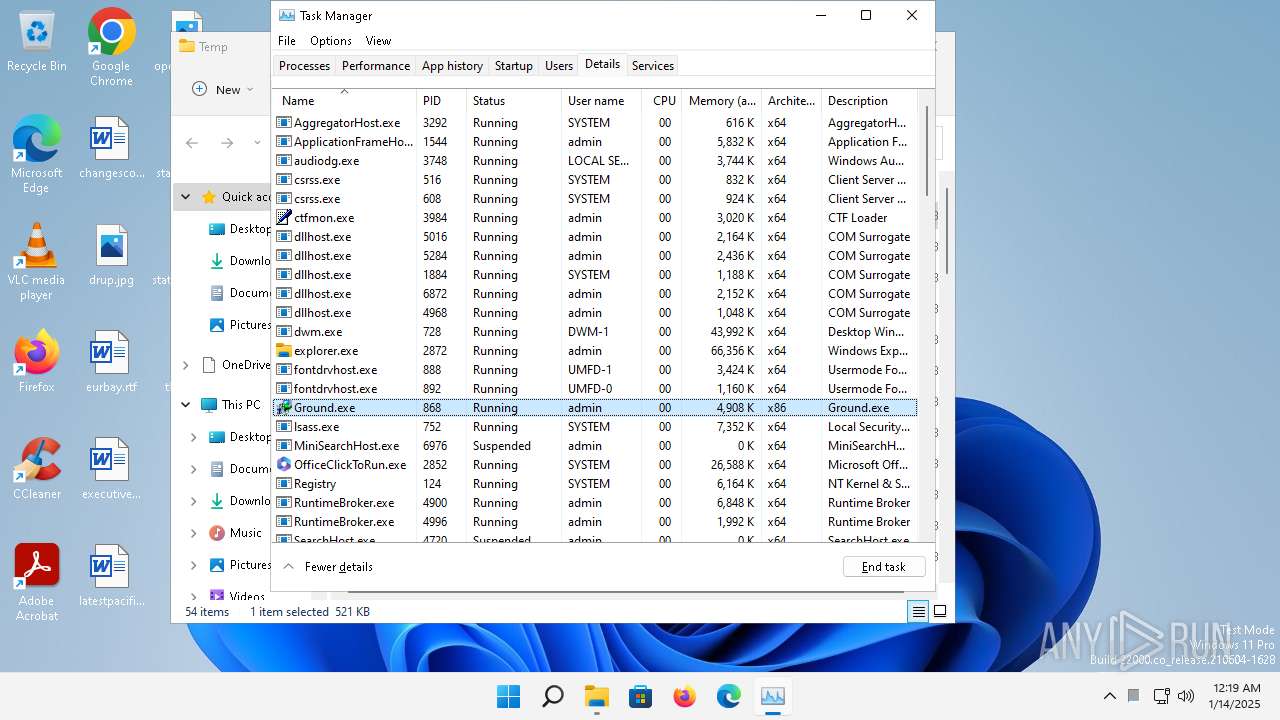
- Ground.exe (PID: 868)
- Ground.exe (PID: 3964)
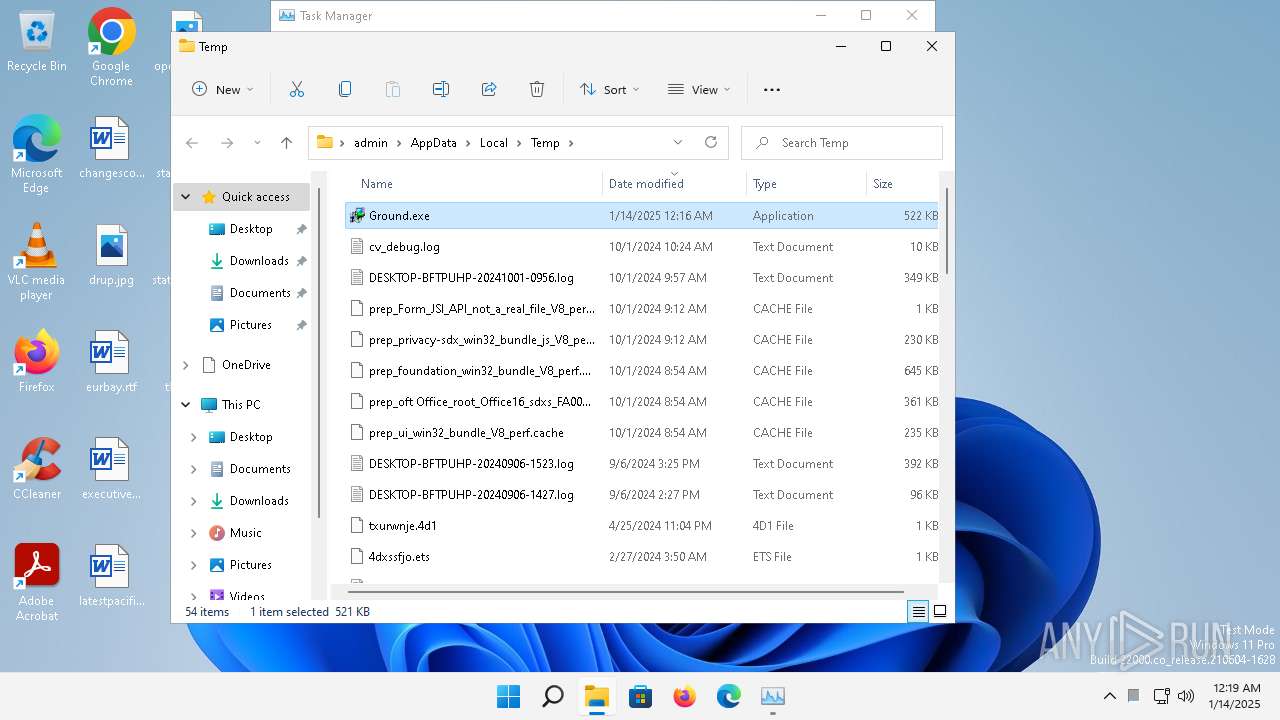
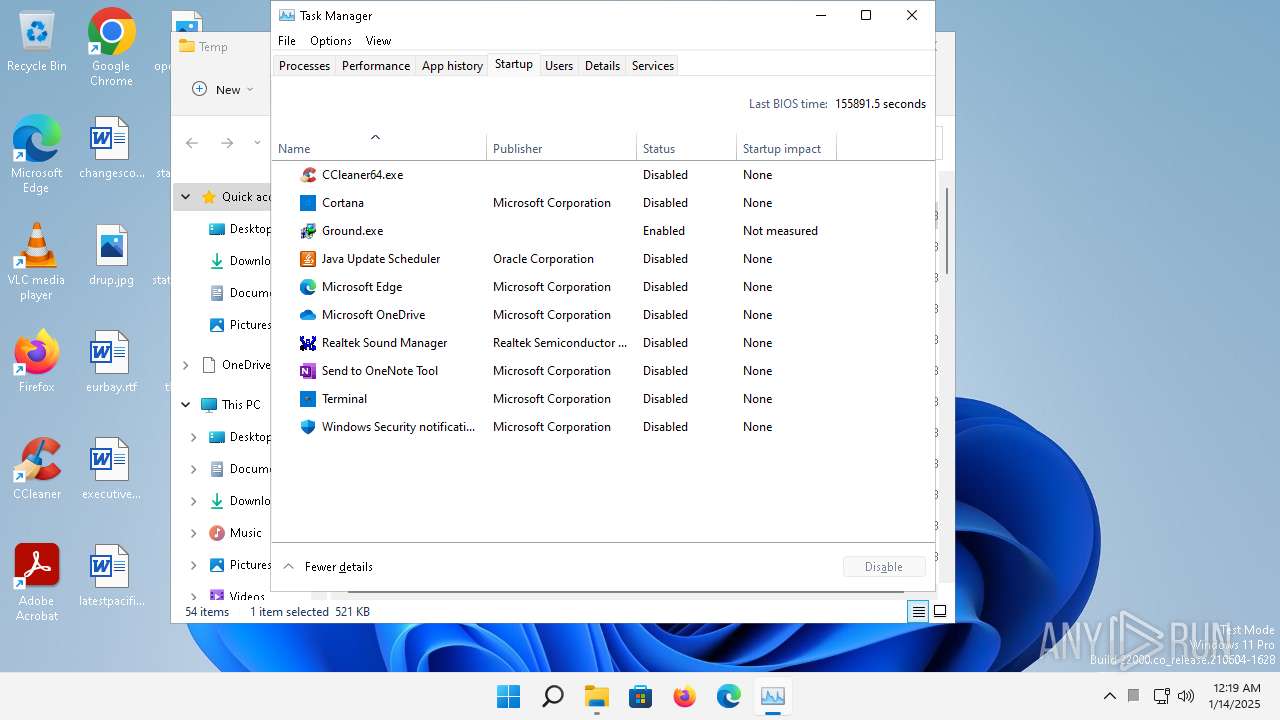
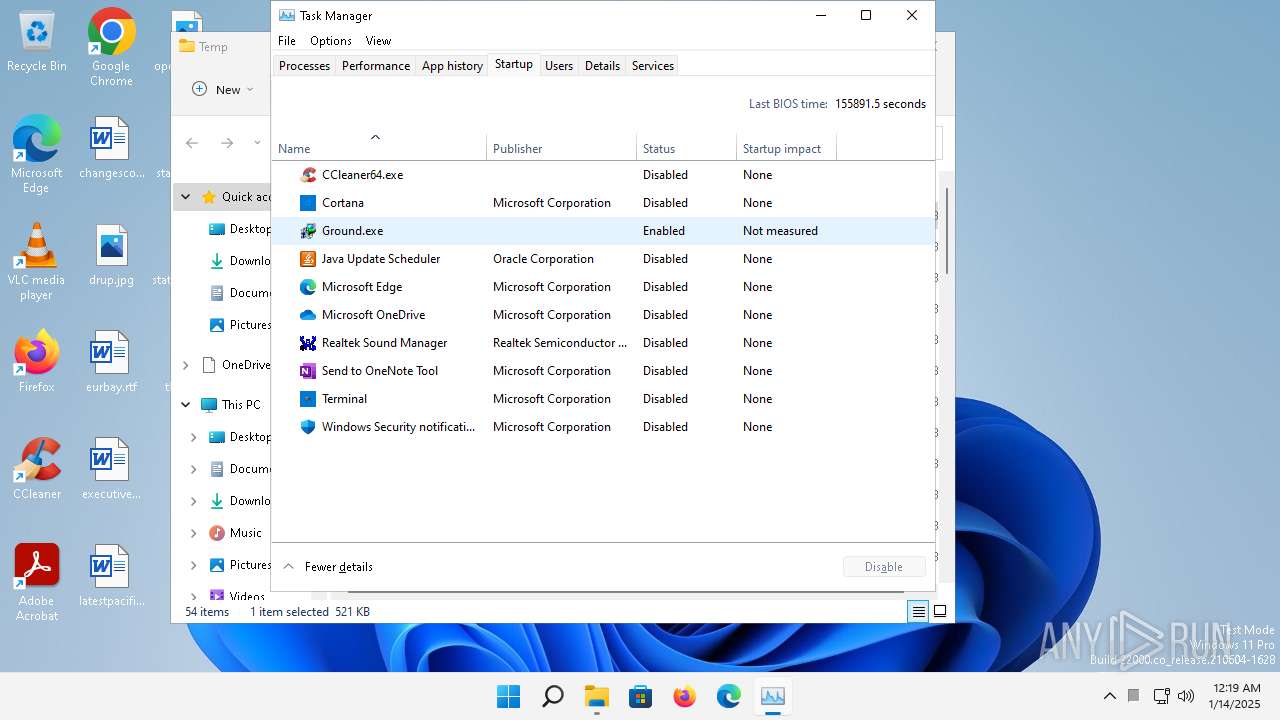
Create files in the Startup directory
- Ground.exe (PID: 3964)
SUSPICIOUS
Executable content was dropped or overwritten
- Ground.exe (PID: 868)
- Ground.exe (PID: 3964)
There is functionality for taking screenshot (YARA)
- Ground.exe (PID: 868)
- Ground.exe (PID: 3964)
Reads the Internet Settings
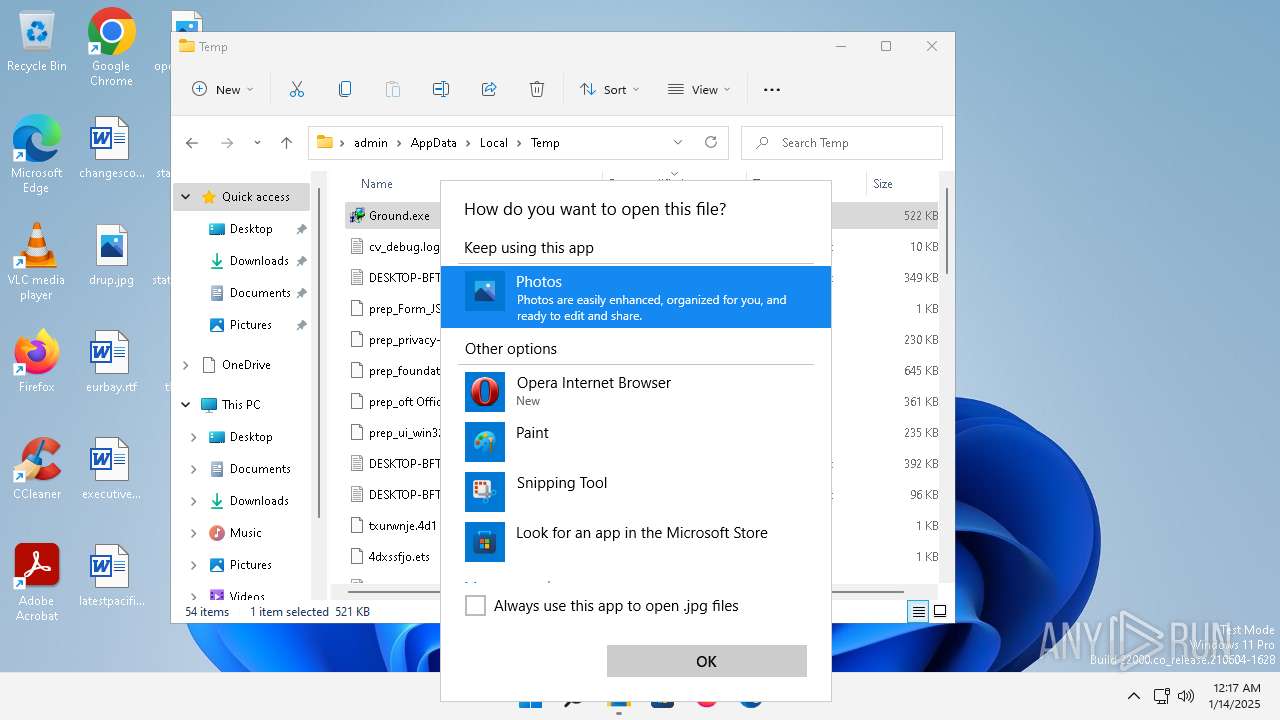
- OpenWith.exe (PID: 1492)
- Microsoft.Photos.exe (PID: 3368)
- Microsoft.Photos.exe (PID: 6752)
The process creates files with name similar to system file names
- Ground.exe (PID: 3964)
Process drops legitimate windows executable
- Ground.exe (PID: 3964)
Reads security settings of Internet Explorer
- Microsoft.Photos.exe (PID: 3368)
- Microsoft.Photos.exe (PID: 6752)
Checks Windows Trust Settings
- Microsoft.Photos.exe (PID: 3368)
- Microsoft.Photos.exe (PID: 6752)
MeshAgent potential remote access (YARA)
- Microsoft.Photos.exe (PID: 6752)
INFO
Manual execution by a user
- Ground.exe (PID: 3964)
Creates files or folders in the user directory
- Ground.exe (PID: 868)
- Ground.exe (PID: 3964)
- Microsoft.Photos.exe (PID: 3368)
Checks supported languages
- Ground.exe (PID: 868)
- Ground.exe (PID: 3964)
- Microsoft.Photos.exe (PID: 3368)
- Microsoft.Photos.exe (PID: 6752)
Failed to create an executable file in Windows directory
- Ground.exe (PID: 868)
Reads the computer name
- Ground.exe (PID: 3964)
- Microsoft.Photos.exe (PID: 3368)
- Microsoft.Photos.exe (PID: 6752)
The sample compiled with english language support
- Ground.exe (PID: 3964)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 1492)
Creates files in the program directory
- Ground.exe (PID: 3964)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 1492)
Sends debugging messages
- Microsoft.Photos.exe (PID: 3368)
- Microsoft.Photos.exe (PID: 6752)
Checks proxy server information
- Microsoft.Photos.exe (PID: 3368)
- Microsoft.Photos.exe (PID: 6752)
Reads Environment values
- Microsoft.Photos.exe (PID: 3368)
- Microsoft.Photos.exe (PID: 6752)
Reads product name
- Microsoft.Photos.exe (PID: 3368)
- Microsoft.Photos.exe (PID: 6752)
Reads the machine GUID from the registry
- Microsoft.Photos.exe (PID: 3368)
- Microsoft.Photos.exe (PID: 6752)
Reads the software policy settings
- Microsoft.Photos.exe (PID: 3368)
- Microsoft.Photos.exe (PID: 6752)
The process uses the downloaded file
- OpenWith.exe (PID: 1492)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (31.9) |
|---|---|---|
| .scr | | | Windows screen saver (29.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (14.8) |
| .exe | | | Win32 Executable (generic) (10.1) |
| .exe | | | Win16/32 Executable Delphi generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2011:08:26 09:37:40+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 461824 |
| InitializedDataSize: | 71168 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x72814 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
123
Monitored processes
5
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 868 | "C:\Users\admin\AppData\Local\Temp\Ground.exe" | C:\Users\admin\AppData\Local\Temp\Ground.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 1492 | C:\Windows\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3368 | "C:\Program Files\WindowsApps\Microsoft.Windows.Photos_2022.31060.30005.0_x64__8wekyb3d8bbwe\Microsoft.Photos.exe" -ServerName:App.AppXzst44mncqdg84v7sv6p7yznqwssy6f7f.mca | C:\Program Files\WindowsApps\Microsoft.Windows.Photos_2022.31060.30005.0_x64__8wekyb3d8bbwe\Microsoft.Photos.exe | svchost.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 3964 | "C:\Users\admin\AppData\Local\Temp\Ground.exe" | C:\Users\admin\AppData\Local\Temp\Ground.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 6752 | "C:\Program Files\WindowsApps\Microsoft.Windows.Photos_2022.31060.30005.0_x64__8wekyb3d8bbwe\Microsoft.Photos.exe" -ServerName:App.AppXzst44mncqdg84v7sv6p7yznqwssy6f7f.mca | C:\Program Files\WindowsApps\Microsoft.Windows.Photos_2022.31060.30005.0_x64__8wekyb3d8bbwe\Microsoft.Photos.exe | svchost.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
Total events
13 592
Read events
13 356
Write events
215
Delete events
21
Modification events
| (PID) Process: | (1492) OpenWith.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.jpg\OpenWithProgids |
| Operation: | write | Name: | jpegfile |
Value: | |||
| (PID) Process: | (1492) OpenWith.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\ApplicationAssociationToasts |
| Operation: | write | Name: | Opera.Image_.jpg |
Value: 0 | |||
| (PID) Process: | (1492) OpenWith.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\ApplicationAssociationToasts |
| Operation: | write | Name: | AppXkv2jqn1pq8ajm0p5dhgqde7aafykkrrn_.jpg |
Value: 0 | |||
| (PID) Process: | (1492) OpenWith.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MrtCache\C:%5CProgram Files%5CWindowsApps%5CMicrosoft.Windows.Photos_2022.31060.30005.0_x64__8wekyb3d8bbwe%5Cmicrosoft.system.package.metadata%5CS-1-5-21-166304369-59083888-3082702900-1001-MergedResources-1.pri\1d89c67ddd3d0fd\4bf12d4 |
| Operation: | write | Name: | @{Microsoft.Windows.Photos_2022.31060.30005.0_x64__8wekyb3d8bbwe?ms-resource://Microsoft.Windows.Photos/Resources/CreateVideoWithPhotos} |
Value: Create a new video | |||
| (PID) Process: | (1492) OpenWith.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MrtCache\C:%5CProgram Files%5CWindowsApps%5CMicrosoft.Windows.Photos_2022.31060.30005.0_x64__8wekyb3d8bbwe%5Cmicrosoft.system.package.metadata%5CS-1-5-21-166304369-59083888-3082702900-1001-MergedResources-1.pri\1d89c67ddd3d0fd\4bf12d4 |
| Operation: | write | Name: | @{Microsoft.Windows.Photos_2022.31060.30005.0_x64__8wekyb3d8bbwe?ms-resource://Microsoft.Windows.Photos/Resources/EditWithPhotos} |
Value: Edit with Photos | |||
| (PID) Process: | (1492) OpenWith.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1492) OpenWith.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1492) OpenWith.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1492) OpenWith.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3368) Microsoft.Photos.exe | Key: | \REGISTRY\A\{14f920ff-71fb-6935-01ec-87179582db84}\LocalState\SessionSummaryData\cc82c8ed-deff-4b8f-ab52-a619d392f28b |
| Operation: | write | Name: | UserLaunchedApp |
Value: 01821512AA1966DB01 | |||
Executable files
523
Suspicious files
2
Text files
96
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3964 | Ground.exe | — | ||
MD5:— | SHA256:— | |||
| 3964 | Ground.exe | C:\Program Files\Adobe\Acrobat DC\Acrobat\gAcrobatInfo.exe | executable | |
MD5:BCFEF2783CC8CA0A00B011EF24926250 | SHA256:C6EC27902D6F9CC50C381620F8D8567BB218822C27279A8376A37BEAC5AC8FD3 | |||
| 3964 | Ground.exe | C:\Program Files\Adobe\Acrobat DC\Acrobat\gacrobat_sl.exe | executable | |
MD5:977E405C109268909FD24A94CC23D4F0 | SHA256:CD24C61FE7DC3896C6C928C92A2ADC58FAB0A3FF61EF7DDCAC1BA794182AB12F | |||
| 3964 | Ground.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Ground.lnk | binary | |
MD5:DAC4FF89DF6DCEA30DB152DD6D12A37F | SHA256:FE1E2DF2D97AA8D9F880A9CC7B7FC76EB852F5B8F5AACB915A7DA7B7D6E5E576 | |||
| 3964 | Ground.exe | C:\Program Files\Adobe\Acrobat DC\Acrobat\gAcrobat.ico | image | |
MD5:372D01BE6D0FE1D84B2416EE0132CE26 | SHA256:19D7D8DE2AF2CDB792C35C6D924654452982860CA34B9FF0A561355C4574145F | |||
| 3964 | Ground.exe | C:\Program Files\Adobe\Acrobat DC\Acrobat\ADelRCP.exe | executable | |
MD5:E838F53B2A7DD58BC2DBE4988009A125 | SHA256:B461B2FF99979370236584A70FA3C602099DF0D013FDD863CBB4D72FC04132AA | |||
| 3964 | Ground.exe | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | executable | |
MD5:6D7EC0399029D89ED75BE092FB1DBC26 | SHA256:2E98DEF5902F735DADA7F229D3B4CBFD3857B9F153AE6021CC58C590F90FFA19 | |||
| 3964 | Ground.exe | C:\Program Files\Adobe\Acrobat DC\Acrobat\RCXF8E2.tmp | executable | |
MD5:6D7EC0399029D89ED75BE092FB1DBC26 | SHA256:2E98DEF5902F735DADA7F229D3B4CBFD3857B9F153AE6021CC58C590F90FFA19 | |||
| 3964 | Ground.exe | C:\Program Files\Adobe\Acrobat DC\Acrobat\AcrobatInfo.exe | executable | |
MD5:E838F53B2A7DD58BC2DBE4988009A125 | SHA256:B461B2FF99979370236584A70FA3C602099DF0D013FDD863CBB4D72FC04132AA | |||
| 3964 | Ground.exe | C:\Program Files\Adobe\Acrobat DC\Acrobat\RCXFA1C.tmp | executable | |
MD5:E39771F020241FCF467A32C24905C377 | SHA256:7A6791EB444D87E1A33AA725BF6492C5768B0A0D3999BB54C1A4A4F227CDC36C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
17
DNS requests
11
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1296 | svchost.exe | GET | 200 | 23.55.161.205:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | whitelisted |
6112 | MoUsoCoreWorker.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e5c1efd4ecba7235 | unknown | — | — | whitelisted |
1592 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3368 | Microsoft.Photos.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
2860 | svchost.exe | GET | 200 | 2.16.100.168:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?a32176130b135011 | unknown | — | — | whitelisted |
2860 | svchost.exe | GET | 304 | 2.16.100.168:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?b505f6e0934a2ada | unknown | — | — | whitelisted |
2860 | svchost.exe | GET | 200 | 2.16.100.168:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?e5bf7775bff1da83 | unknown | — | — | whitelisted |
2860 | svchost.exe | GET | 200 | 2.16.100.168:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?227107f915712478 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1296 | svchost.exe | 23.55.161.172:80 | — | Akamai International B.V. | DE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1296 | svchost.exe | 23.55.161.205:80 | — | Akamai International B.V. | DE | unknown |
6112 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6112 | MoUsoCoreWorker.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
1592 | svchost.exe | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1592 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
6112 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2884 | svchost.exe | 20.189.173.25:443 | v10.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6580 | svchost.exe | 184.28.90.27:443 | fs.microsoft.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
v10.events.data.microsoft.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
evoke-windowsservices-tas.msedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1296 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |