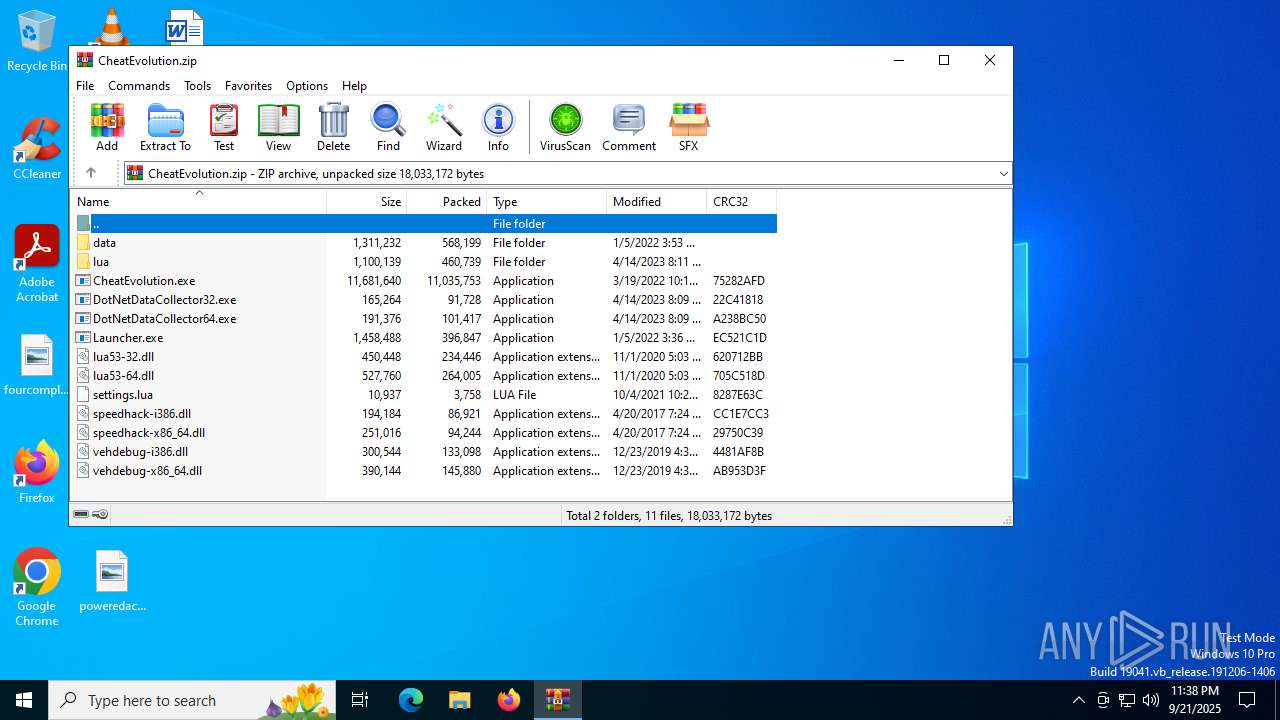
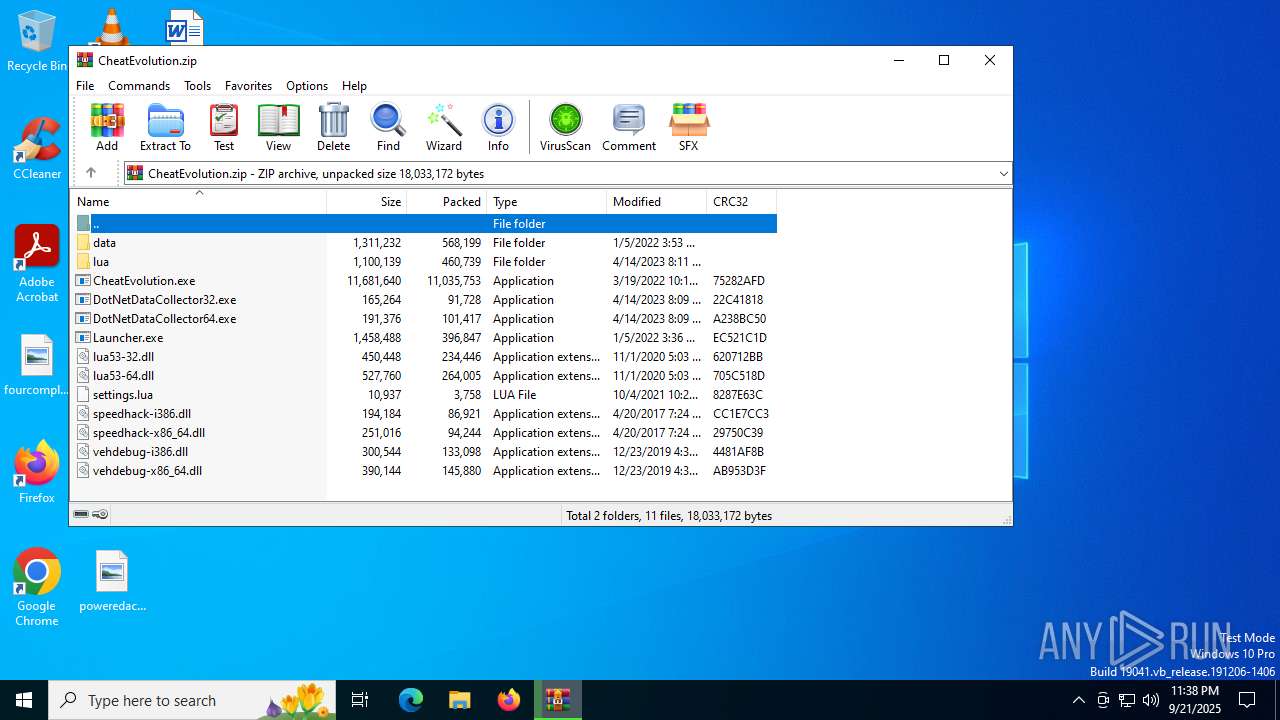
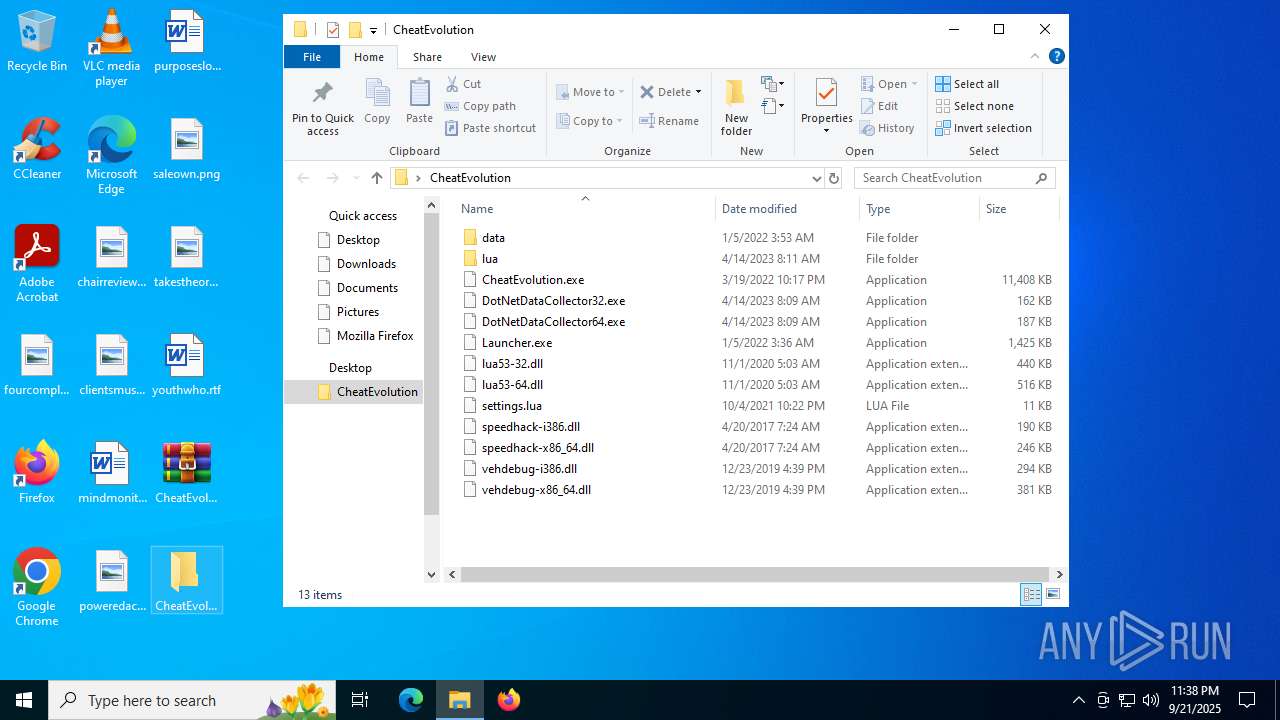
| File name: | CheatEvolution.zip |
| Full analysis: | https://app.any.run/tasks/8a45be72-4f6f-4664-b82c-4acb1fb98f9c |
| Verdict: | Malicious activity |
| Analysis date: | September 21, 2025, 23:37:55 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | DEA58FACE16153F96BDC1355A29AC9C8 |
| SHA1: | B91E02A5D7DEA8B10E602D9DA450CEFDE439EEC3 |
| SHA256: | B45263FB6FFB1E77D097DB738F0D0BC36739FFF680FCAC676675C3DFE70E3148 |
| SSDEEP: | 98304:bMYP9Ou9RBoT/xo2fFymsFbBtCcimYT0J8Hs4pM3/Dk3yjQ1YXi4eUKfvp37kIxc:L6LMhkMl6+Odw6Am4dEo |
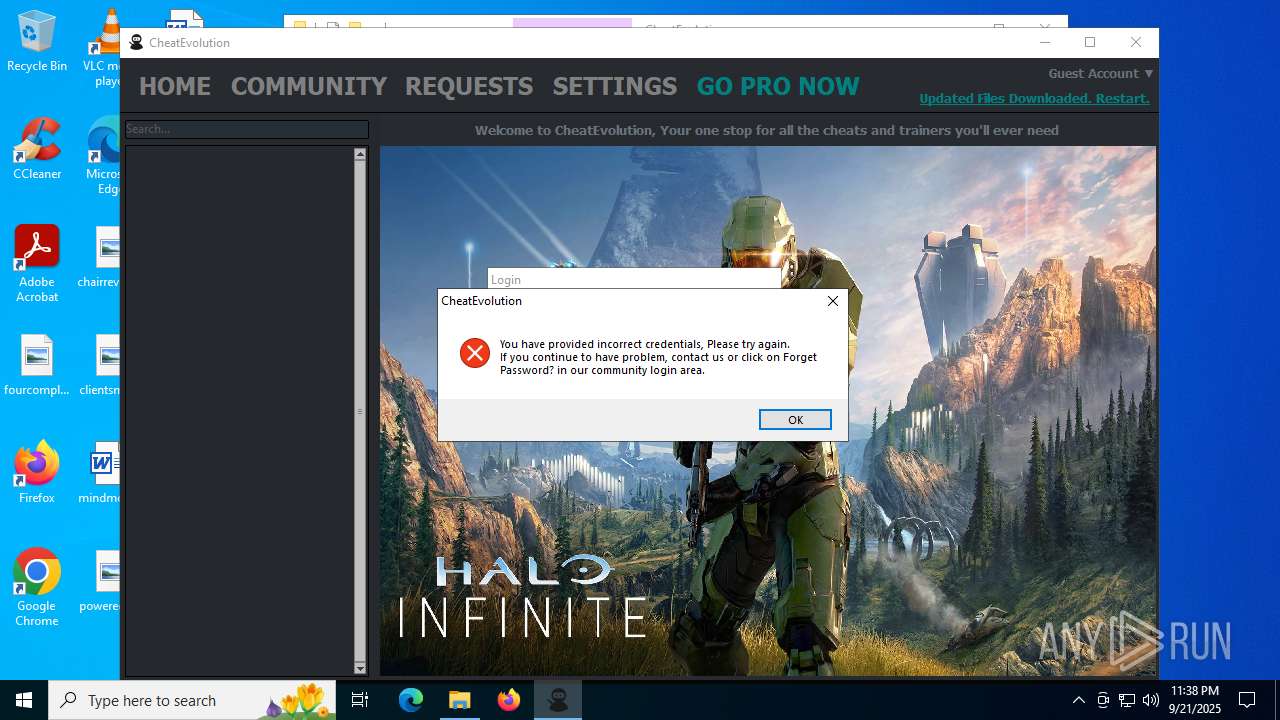
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- Launcher.exe (PID: 6812)
- CheatEvolution.exe (PID: 5368)
There is functionality for taking screenshot (YARA)
- CheatEvolution.exe (PID: 5368)
Launching a dropped file
- CheatEvolution.exe (PID: 5368)
Executable content was dropped or overwritten
- CheatEvolution.exe (PID: 5368)
Reads Internet Explorer settings
- CheatEvolution.exe (PID: 5368)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 1932)
Checks supported languages
- Launcher.exe (PID: 6812)
- CheatEvolution.exe (PID: 5368)
Launching a dropped file
- WinRAR.exe (PID: 1932)
Manual execution by a user
- Launcher.exe (PID: 6860)
- Launcher.exe (PID: 6812)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1932)
Process checks computer location settings
- Launcher.exe (PID: 6812)
Reads the computer name
- Launcher.exe (PID: 6812)
- CheatEvolution.exe (PID: 5368)
Reads the software policy settings
- CheatEvolution.exe (PID: 5368)
Creates files or folders in the user directory
- CheatEvolution.exe (PID: 5368)
Checks proxy server information
- CheatEvolution.exe (PID: 5368)
Reads the machine GUID from the registry
- CheatEvolution.exe (PID: 5368)
Compiled with Borland Delphi (YARA)
- CheatEvolution.exe (PID: 5368)
The process uses Lua
- CheatEvolution.exe (PID: 5368)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:04:14 04:09:22 |
| ZipCRC: | 0x22c41818 |
| ZipCompressedSize: | 91728 |
| ZipUncompressedSize: | 165264 |
| ZipFileName: | DotNetDataCollector32.exe |
Total processes
139
Monitored processes
6
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1852 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1932 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\CheatEvolution.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3640 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
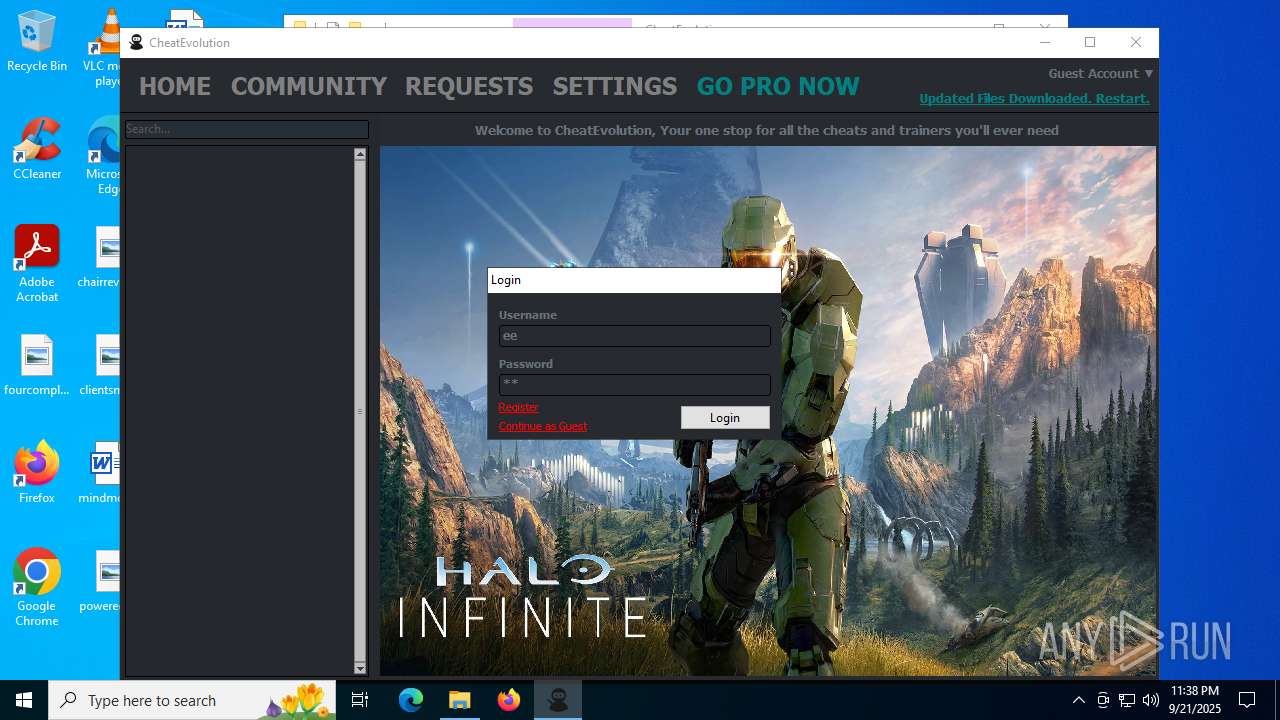
| 5368 | "C:\Users\admin\Desktop\CheatEvolution\CheatEvolution.exe" -start | C:\Users\admin\Desktop\CheatEvolution\CheatEvolution.exe | Launcher.exe | ||||||||||||
User: admin Company: CheatEvolution Integrity Level: HIGH Description: CheatEvolution Version: 2.3.0.0 Modules
| |||||||||||||||
| 6812 | "C:\Users\admin\Desktop\CheatEvolution\Launcher.exe" | C:\Users\admin\Desktop\CheatEvolution\Launcher.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Launcher Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6860 | "C:\Users\admin\Desktop\CheatEvolution\Launcher.exe" | C:\Users\admin\Desktop\CheatEvolution\Launcher.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Launcher Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
3 476
Read events
3 439
Write events
24
Delete events
13
Modification events
| (PID) Process: | (1932) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1932) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1932) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1932) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\CheatEvolution.zip | |||
| (PID) Process: | (1932) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1932) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1932) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1932) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1932) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (1932) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
28
Suspicious files
14
Text files
24
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1932 | WinRAR.exe | C:\Users\admin\Desktop\CheatEvolution\vehdebug-x86_64.dll | executable | |
MD5:FBAF0BF6E47E4026997BE3C2F4EB5599 | SHA256:29866065375542A19C52FF003DA0F2A792D8E0816A52CF8D3E193DD4FE005D22 | |||
| 1932 | WinRAR.exe | C:\Users\admin\Desktop\CheatEvolution\speedhack-x86_64.dll | executable | |
MD5:156249CE92B9A15D71C39160DC05B4A1 | SHA256:3BD69D00774B40132BD621C09C11093F188F06D634DB64A19A78C46A27388C8F | |||
| 1932 | WinRAR.exe | C:\Users\admin\Desktop\CheatEvolution\lua\dlls\MonoDataCollector64.dll | executable | |
MD5:9F12C94F8B3D5C5C07D6E510EA10FE3A | SHA256:93125BB74FCFF6D7C00A8BF28858826BADB62ADD244636296ECF87B5259D239D | |||
| 1932 | WinRAR.exe | C:\Users\admin\Desktop\CheatEvolution\data\data.dll | executable | |
MD5:C11138204609EA63A3E88B4C8C09B035 | SHA256:60C16C2FAB14B344B8343778DCD6BBFDEE3DFE5F83D1AC8D2E50C6877419EEE4 | |||
| 1932 | WinRAR.exe | C:\Users\admin\Desktop\CheatEvolution\vehdebug-i386.dll | executable | |
MD5:E427A09C9DF940D8E642679A0742079C | SHA256:9A7E39788BCAAC1EA29898F4FDFDCB252785F70D551CF602AD87B77B9A64D6F0 | |||
| 1932 | WinRAR.exe | C:\Users\admin\Desktop\CheatEvolution\lua\dotnetinfo.lua | text | |
MD5:880FDCBD218DF2AEDB1EAF3BE84734B7 | SHA256:41DF4679278EB1B39B872799EB5FD39A166EAAD1AC2442CA428C91B90B21A0D5 | |||
| 1932 | WinRAR.exe | C:\Users\admin\Desktop\CheatEvolution\lua\DotNetInterface.lua | text | |
MD5:602EA720E7CE9376D736BC348F3988D2 | SHA256:DFED591417FDF76524E127BFDB022FA6A32394E3A42303F896B39D441BFA6F8E | |||
| 1932 | WinRAR.exe | C:\Users\admin\Desktop\CheatEvolution\lua\dlls\DotNetInterface.dll | executable | |
MD5:5B12656D94B4BBB14C7C59D2C34C3C0B | SHA256:4EAFAC874D7A3E9D1FF72E1810D9B1828F0A99A429290D739246786FA7939E66 | |||
| 1932 | WinRAR.exe | C:\Users\admin\Desktop\CheatEvolution\lua\additional_settings.lua | binary | |
MD5:1F73E4D6E1A5C6EB97B31813EC21D0DB | SHA256:A0343D322F042622040D129C7B5D9F9B4CD10E0EE3B249F280B9DA7C1F7C0222 | |||
| 1932 | WinRAR.exe | C:\Users\admin\Desktop\CheatEvolution\DotNetDataCollector32.exe | executable | |
MD5:5AE652CA00AFA7378B0FCC6F1A85C137 | SHA256:12DFDBEC903CE46E0132F239BA4C8E8665B2020CA4AA781DC96A7CD98ED60CF4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
51
DNS requests
21
Threats
18
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5368 | CheatEvolution.exe | GET | 200 | 142.250.74.195:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5368 | CheatEvolution.exe | GET | 200 | 142.250.74.195:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
6212 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3160 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3160 | SIHClient.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
3160 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
3160 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Time-Stamp%20PCA%202010(1).crl | unknown | — | — | whitelisted |
3160 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
3160 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5348 | RUXIMICS.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 104.79.89.142:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6212 | svchost.exe | 40.126.31.69:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
cheatevolution.com |
| unknown |
c.pki.goog |
| whitelisted |
o.pki.goog |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
— | — | Misc activity | ET INFO Observed UA-CPU Header |
— | — | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
— | — | Misc activity | ET INFO Packed Executable Download |
— | — | Misc activity | ET INFO EXE - Served Attached HTTP |
— | — | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
— | — | Misc activity | ET INFO Packed Executable Download |
— | — | Misc activity | ET INFO EXE - Served Attached HTTP |
— | — | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
— | — | Misc activity | ET INFO EXE - Served Attached HTTP |
Process | Message |
|---|---|
CheatEvolution.exe | arm disassembler |
CheatEvolution.exe | DisassemblerThumb init |
CheatEvolution.exe | MainUnit2 |
CheatEvolution.exe | Offset of LBR_Count=768 |
CheatEvolution.exe | sizeof fxstate = 512 |
CheatEvolution.exe | start |
CheatEvolution.exe | TSymbolListHandler.create 2 |
CheatEvolution.exe | TSymbolListHandler.create 1 |
CheatEvolution.exe | TSymbolListHandler.create exit |
CheatEvolution.exe | TSymbolListHandler.create 1 |