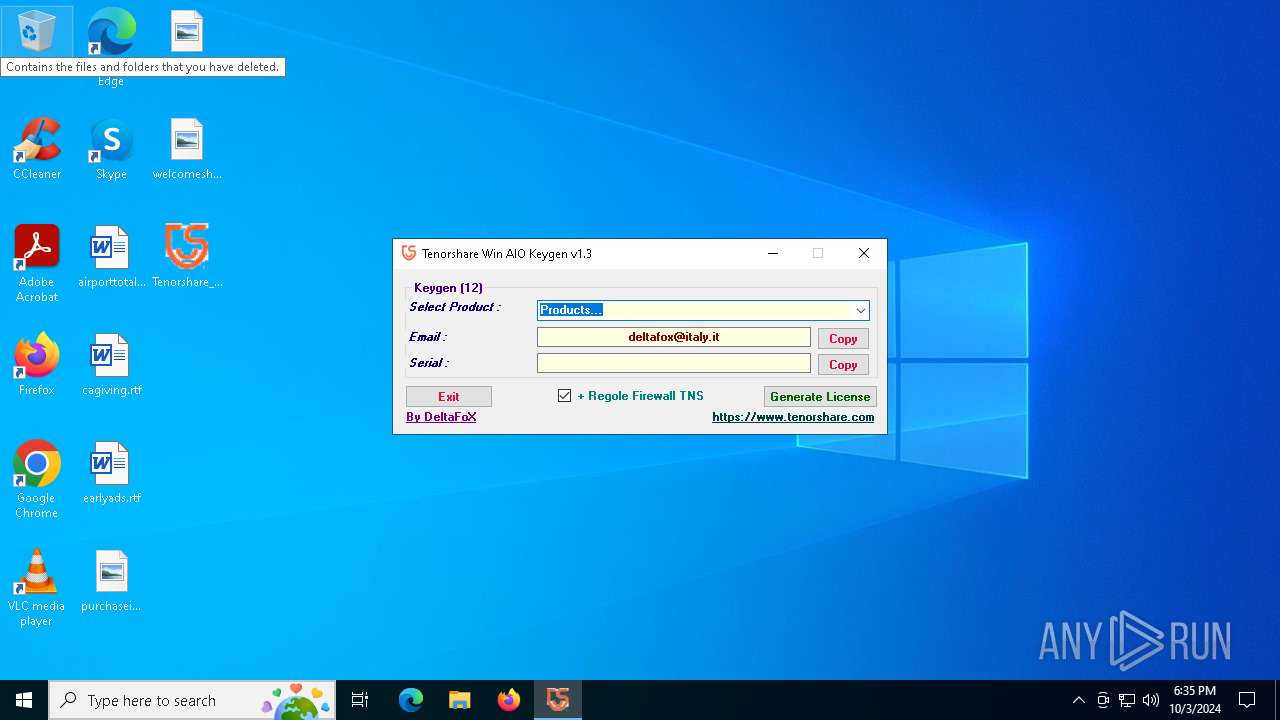
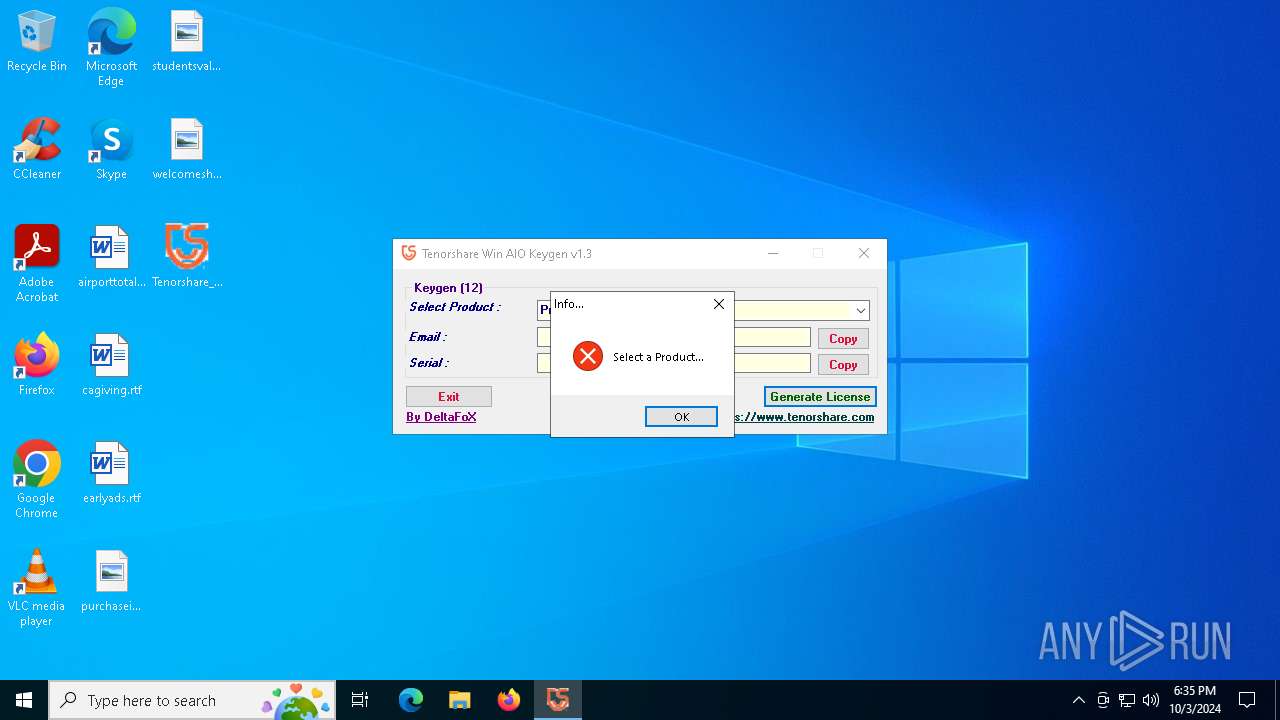
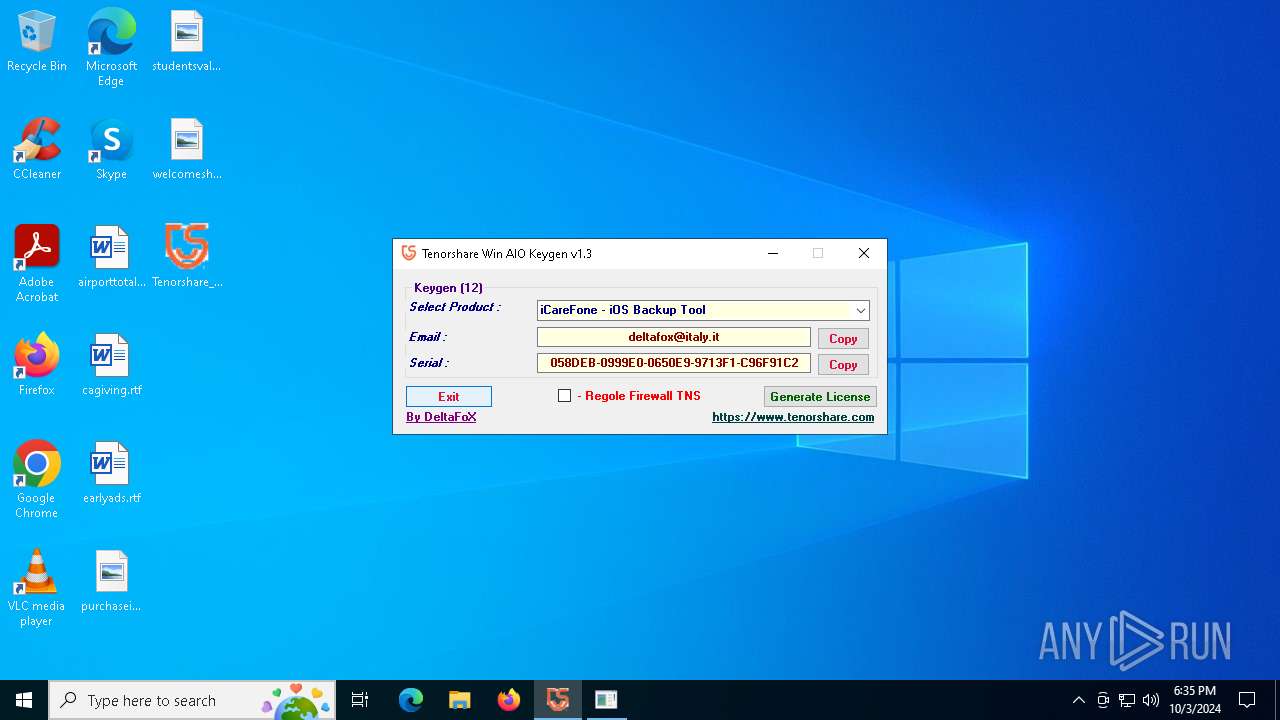
| File name: | Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe |
| Full analysis: | https://app.any.run/tasks/6c704905-bddf-4eef-93ee-616b16f9a1a0 |
| Verdict: | Malicious activity |
| Analysis date: | October 03, 2024, 18:35:08 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | MS-DOS executable PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows, MZ for MS-DOS |
| MD5: | 5D54EF964703592CD7D7CC9DEB66419F |
| SHA1: | 63FE8FD3F6571EE73A702BB975CAE34BC6D94ADD |
| SHA256: | B40C142F99E5F527401F9EF14D1329552114489FBCCCB4CF6C56169CEC33FF75 |
| SSDEEP: | 49152:rn0TnHXEOljdJmoank0a2xuX8bCQ4hLyxmiCMORj/NHQcVhXyqGwtNUrwuTgJ890:rnOnH0OlJJgk0s8bCjhLCRs73FGwtNUO |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe (PID: 1556)
- svchost.exe (PID: 5244)
Executable content was dropped or overwritten
- Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe (PID: 1556)
- svchost.exe (PID: 5244)
The process creates files with name similar to system file names
- Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe (PID: 1556)
Reads Microsoft Outlook installation path
- svchost.exe (PID: 5244)
Starts itself from another location
- svchost.exe (PID: 5244)
The process executes VB scripts
- Aucgna.exe (PID: 15452)
- Aucgna.exe (PID: 19856)
Connects to unusual port
- vbc.exe (PID: 16740)
- vbc.exe (PID: 12924)
INFO
Checks supported languages
- Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe (PID: 1556)
- xx.exe (PID: 6412)
- svchost.exe (PID: 5244)
Reads mouse settings
- Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe (PID: 1556)
Process checks computer location settings
- Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe (PID: 1556)
Reads the computer name
- Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe (PID: 1556)
- xx.exe (PID: 6412)
- svchost.exe (PID: 5244)
Create files in a temporary directory
- Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe (PID: 1556)
The process uses the downloaded file
- Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe (PID: 1556)
Reads the machine GUID from the registry
- xx.exe (PID: 6412)
- svchost.exe (PID: 5244)
Checks proxy server information
- svchost.exe (PID: 5244)
.NET Reactor protector has been detected
- xx.exe (PID: 6412)
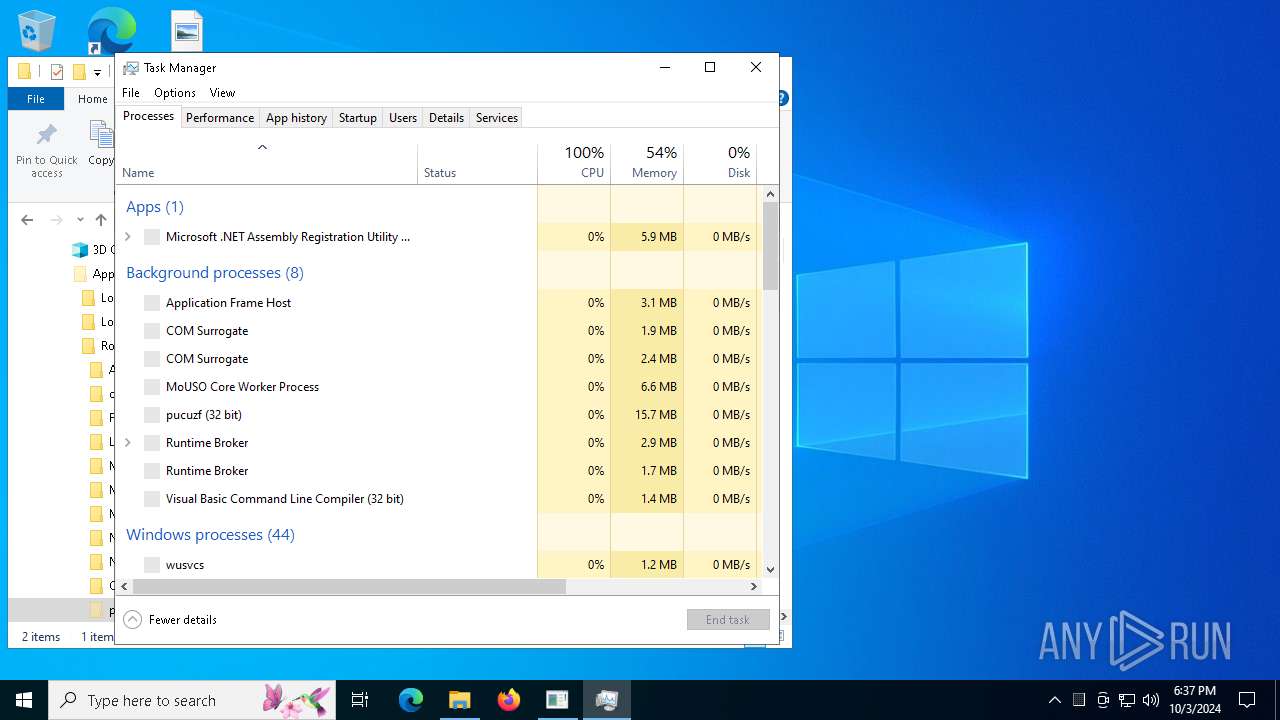
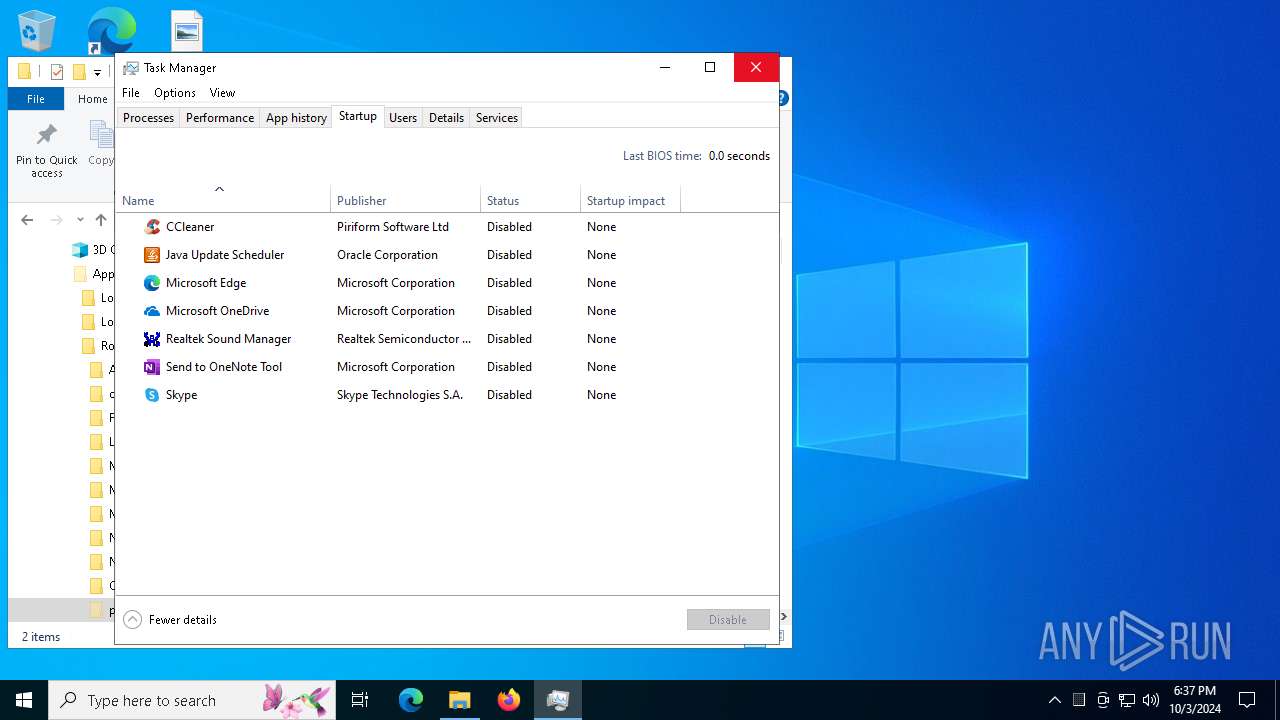
Manual execution by a user
- Taskmgr.exe (PID: 13864)
- Taskmgr.exe (PID: 13784)
- Aucgna.exe (PID: 19856)
- Aucgna.exe (PID: 7432)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:01:10 06:07:32+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 12 |
| CodeSize: | 581120 |
| InitializedDataSize: | 1103360 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1a23f8 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.3.0.0 |
| ProductVersionNumber: | 1.3.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
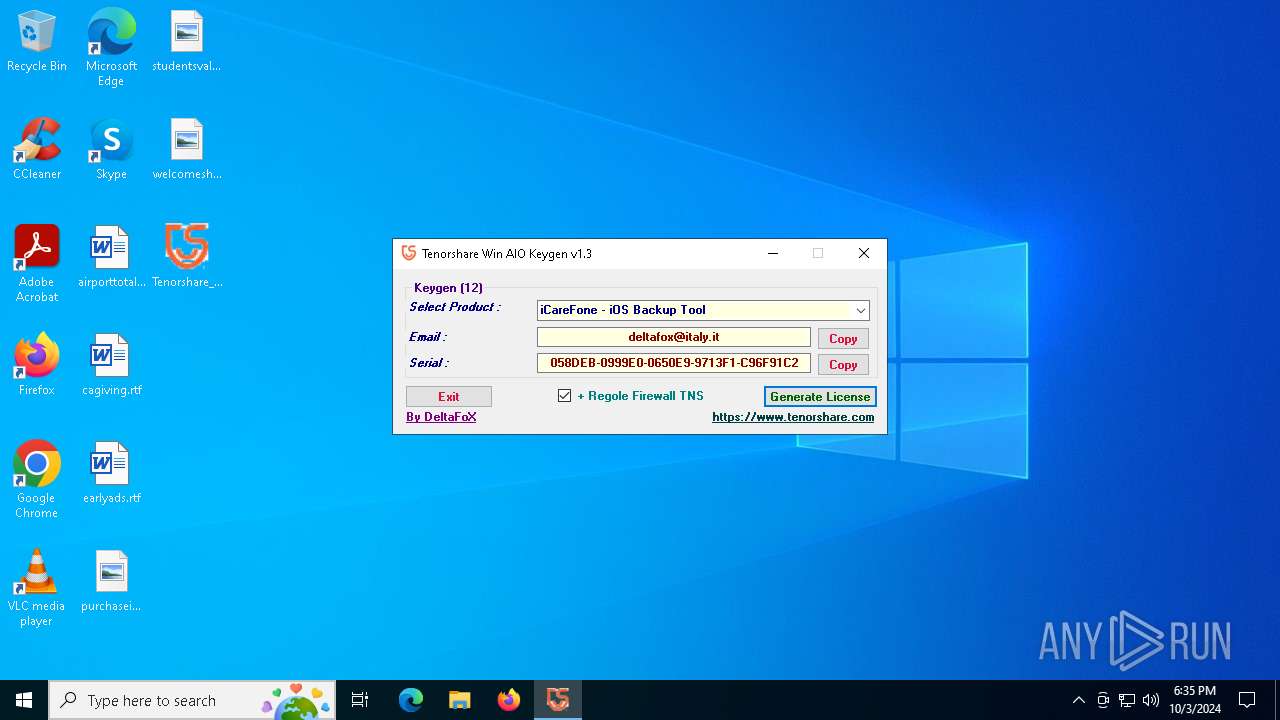
| Comments: | Keygen for all Win 12 Tenorshare Products |
| CompanyName: | DeFconX |
| FileDescription: | Tenorshare_Aio_Keygen_By_DFoX |
| FileVersion: | 1.3.0.0 |
| InternalName: | Tenorshare_Aio_Keygen_By_DFoX.exe |
| LegalCopyright: | Copyright © 2019 |
| LegalTrademarks: | DeltaFoX |
| OriginalFileName: | Tenorshare_Aio_Keygen_By_DFoX.exe |
| ProductName: | Tenorshare_Aio_Keygen_By_DFoX |
| ProductVersion: | 1.3.0.0 |
| AssemblyVersion: | 1.3.0.0 |
Total processes
149
Monitored processes
22
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1556 | "C:\Users\admin\Desktop\Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe" | C:\Users\admin\Desktop\Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe | explorer.exe | ||||||||||||
User: admin Company: DeFconX Integrity Level: MEDIUM Description: Tenorshare_Aio_Keygen_By_DFoX Exit code: 0 Version: 1.3.0.0 Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2796 | "C:\Users\admin\AppData\Local\Temp\xx.exe" | C:\Users\admin\AppData\Local\Temp\xx.exe | — | Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe | |||||||||||
User: admin Company: DeFconX Integrity Level: MEDIUM Description: Tenorshare_Aio_Keygen_By_DFoX Exit code: 3221226540 Version: 1.3.0.0 Modules
| |||||||||||||||
| 5244 | "C:\Users\admin\AppData\Local\Temp\svchost.exe" | C:\Users\admin\AppData\Local\Temp\svchost.exe | Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe | ||||||||||||
User: admin Company: Xvcrima Integrity Level: MEDIUM Description: pucuzf Exit code: 0 Version: 7.5.57.30 Modules
| |||||||||||||||
| 6412 | "C:\Users\admin\AppData\Local\Temp\xx.exe" | C:\Users\admin\AppData\Local\Temp\xx.exe | Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe | ||||||||||||
User: admin Company: DeFconX Integrity Level: HIGH Description: Tenorshare_Aio_Keygen_By_DFoX Exit code: 0 Version: 1.3.0.0 Modules
| |||||||||||||||
| 7432 | "C:\Users\admin\AppData\Roaming\pqsnu\Aucgna.exe" | C:\Users\admin\AppData\Roaming\pqsnu\Aucgna.exe | — | explorer.exe | |||||||||||
User: admin Company: Xvcrima Integrity Level: MEDIUM Description: pucuzf Exit code: 0 Version: 7.5.57.30 Modules
| |||||||||||||||
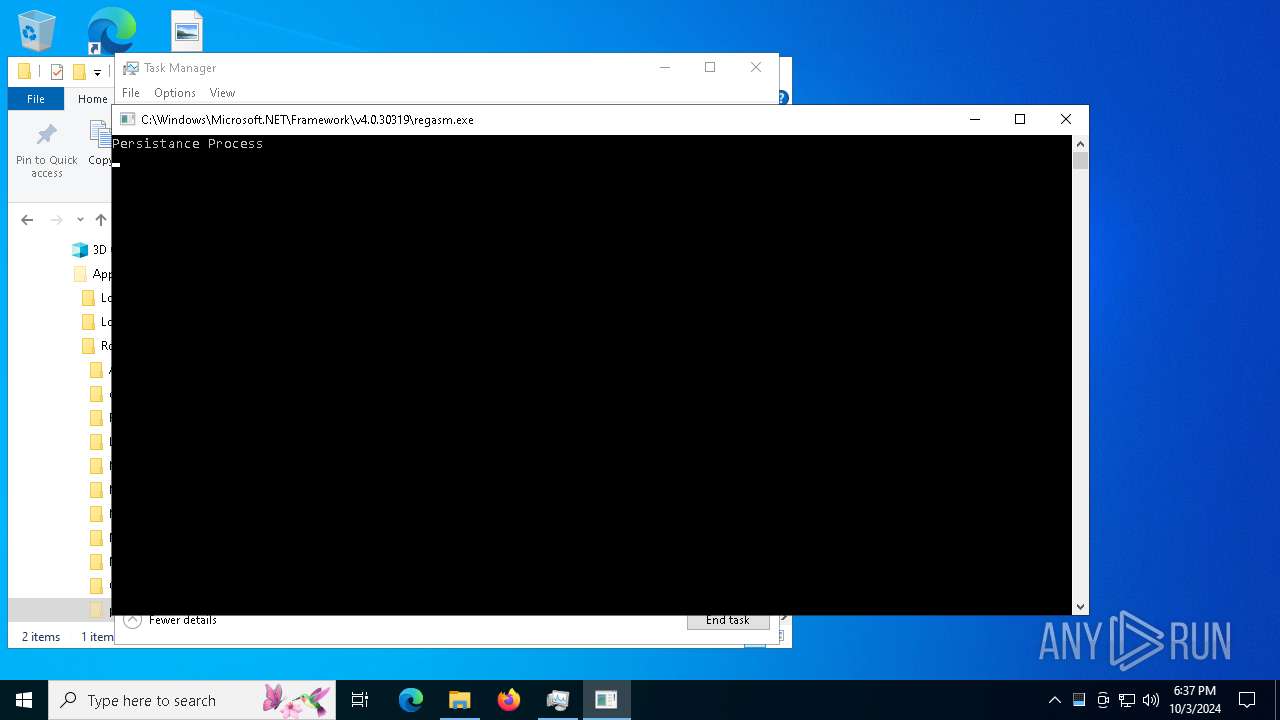
| 12912 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\regasm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | — | Aucgna.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 4294967295 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 12924 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\vbc.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\vbc.exe | Aucgna.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Version: 14.8.9037.0 Modules
| |||||||||||||||
| 13784 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 13864 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
9 796
Read events
9 724
Write events
61
Delete events
11
Modification events
| (PID) Process: | (5244) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5244) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5244) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5244) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFavoritesInitialSelection |
Value: | |||
| (PID) Process: | (5244) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFeedsInitialSelection |
Value: | |||
| (PID) Process: | (5244) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (6412) xx.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (6412) xx.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 040000000E00000010000000030000000F000000000000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (6412) xx.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4\0\4\0 |
| Operation: | write | Name: | 2 |
Value: 7E003100000000004359699411004465736B746F7000680009000400EFBE274B1240435969942E00000056A100000000090000000000000000003E00000000008F9115014400650073006B0074006F007000000040007300680065006C006C00330032002E0064006C006C002C002D0032003100370036003900000016000000 | |||
| (PID) Process: | (6412) xx.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4\0\4\0\2 |
| Operation: | delete value | Name: | MRUList |
Value: | |||
Executable files
3
Suspicious files
6
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 15452 | Aucgna.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:85734E4FDF84905C041035519E27ECE6 | SHA256:DA789ABDA708784216B24BA54F7824001205B39B8B06D5892AA632FE87479464 | |||
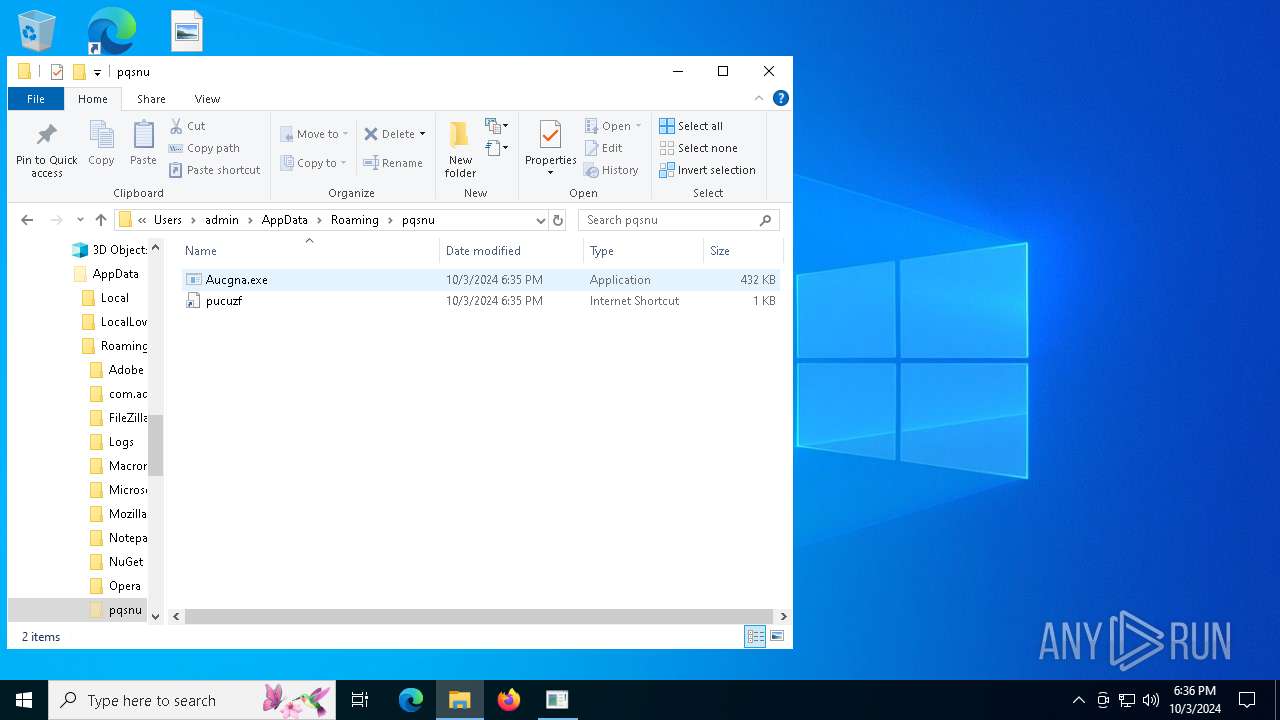
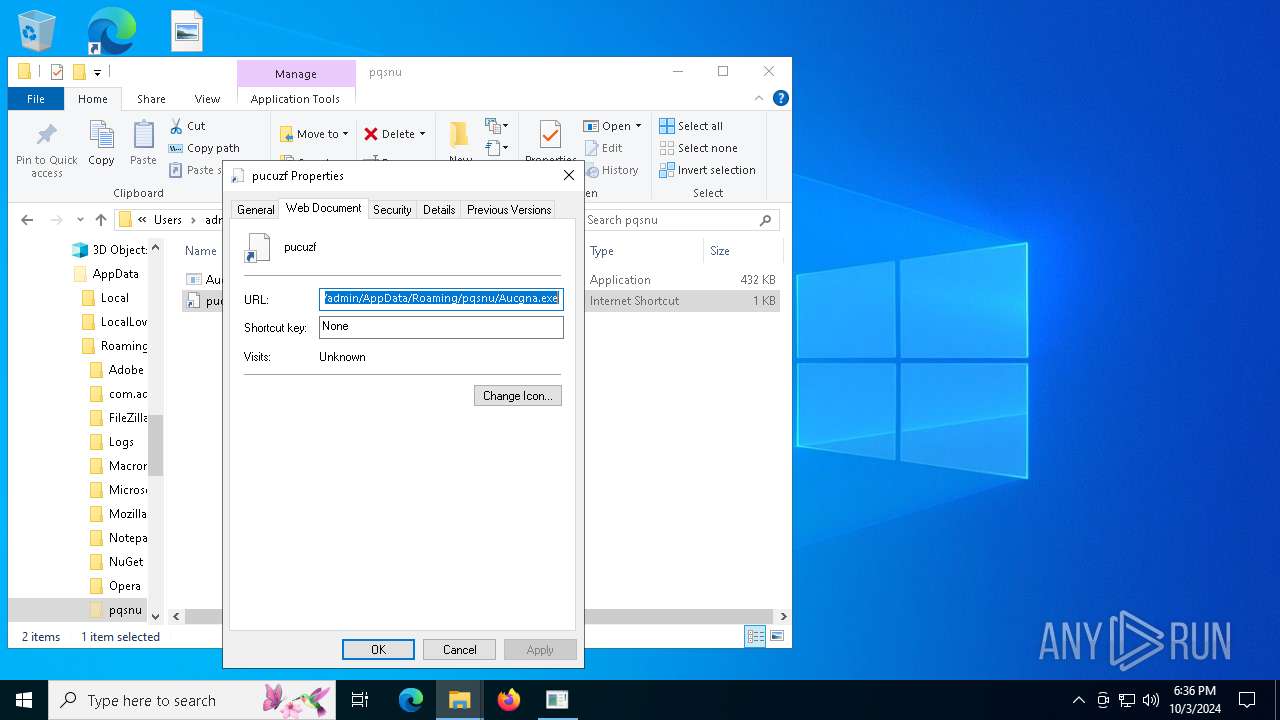
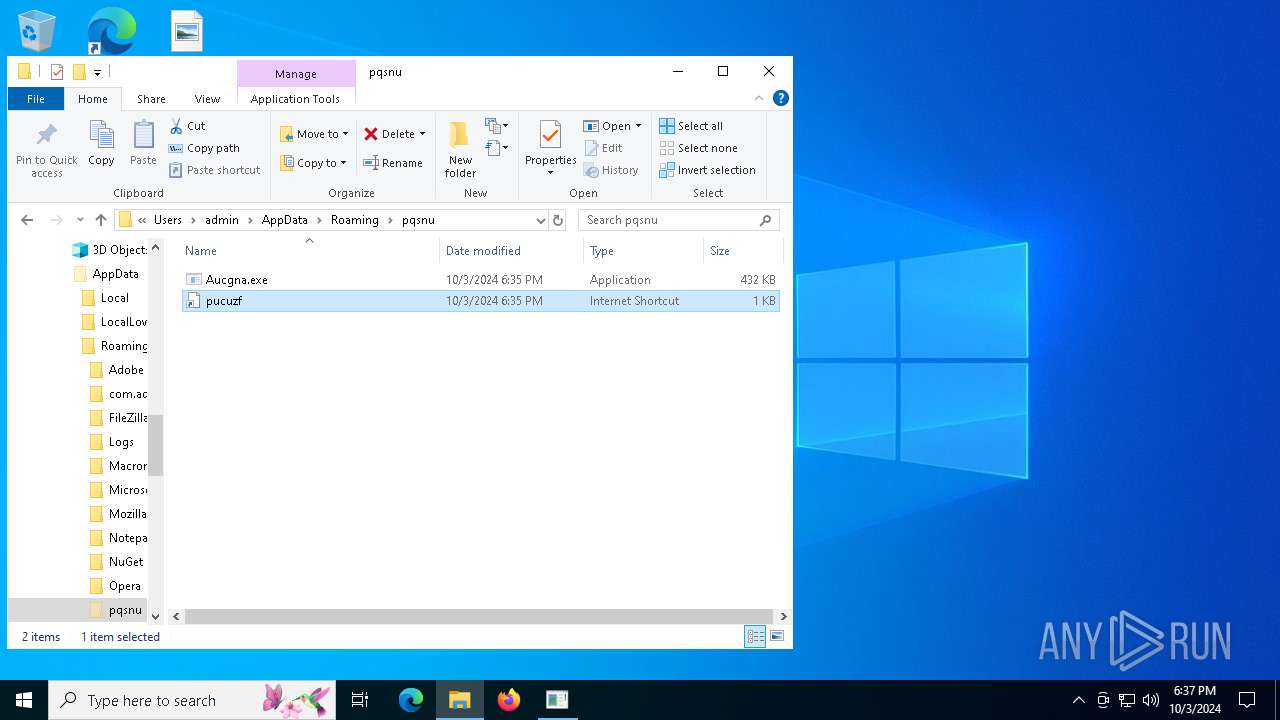
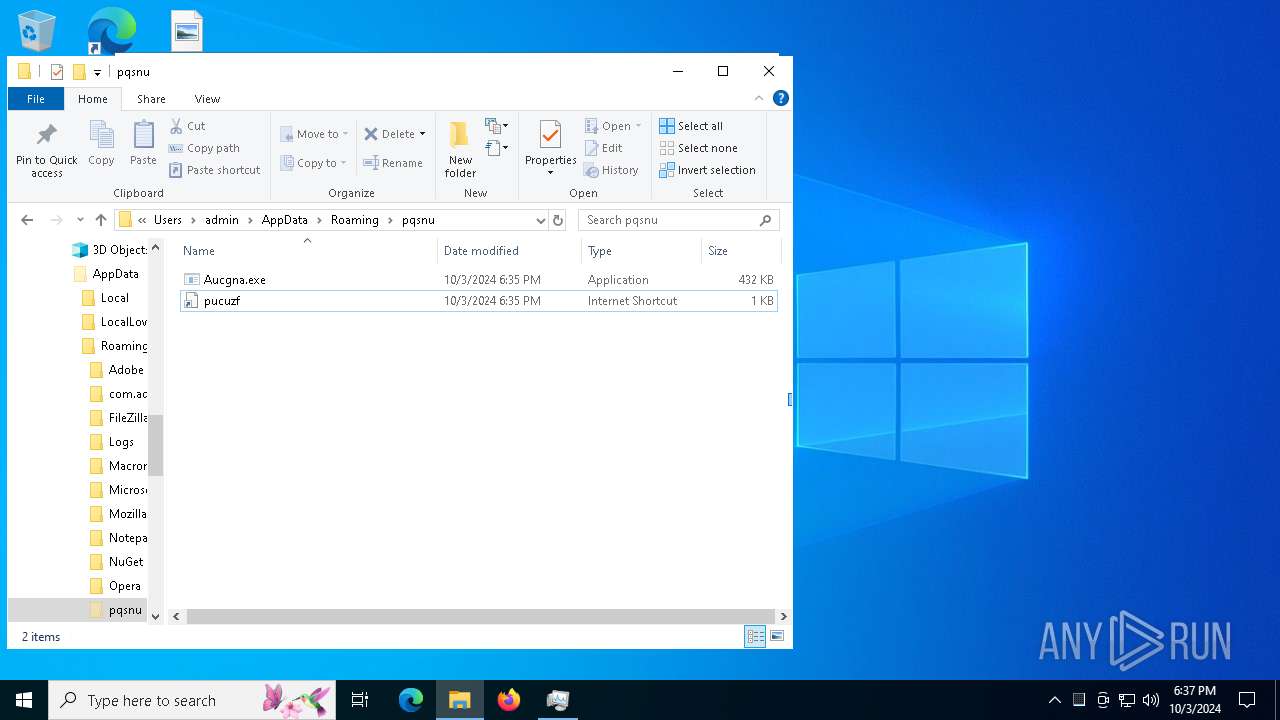
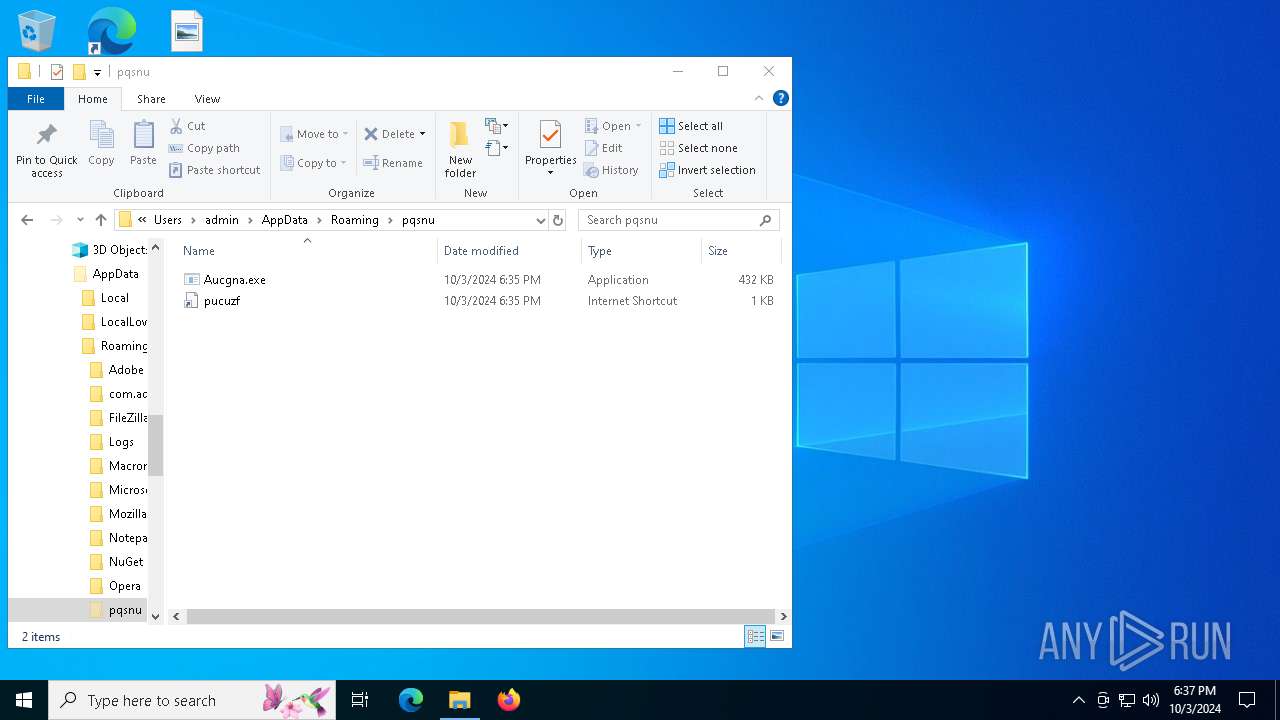
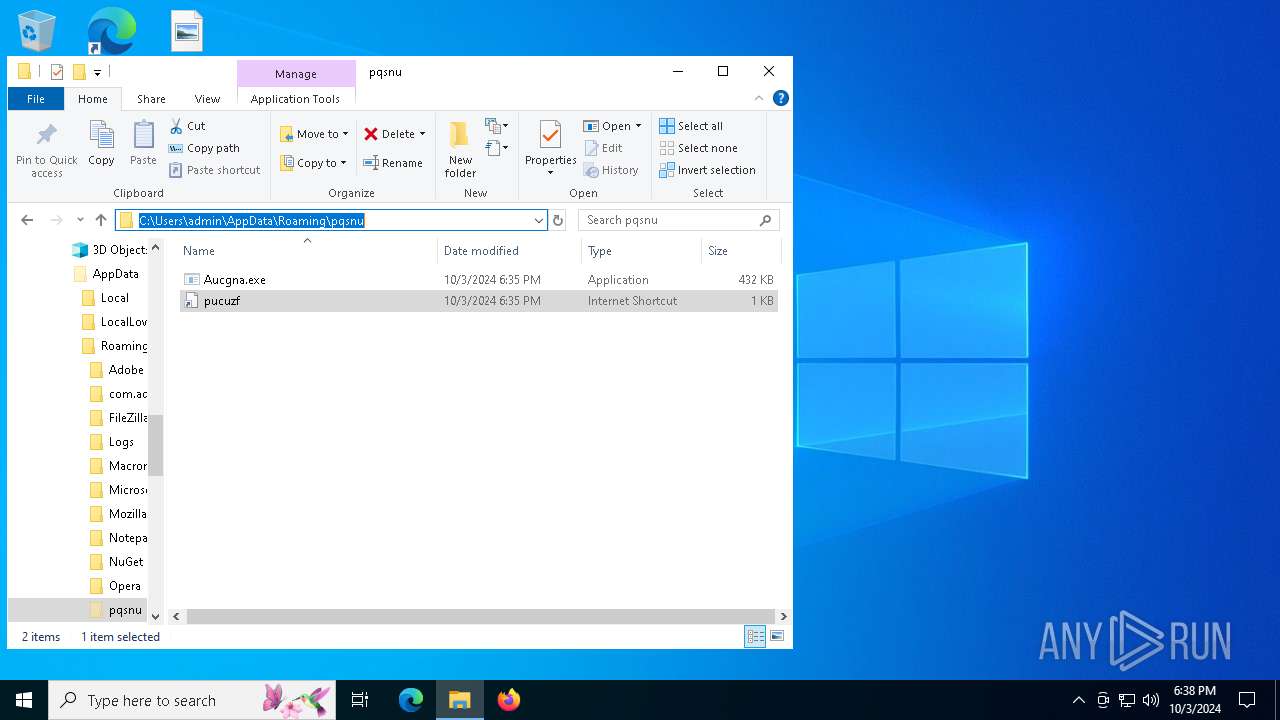
| 5244 | svchost.exe | C:\Users\admin\AppData\Roaming\pqsnu\Aucgna.exe | executable | |
MD5:6BB2EE4138EFE36DB57B688D7F75A6D5 | SHA256:753172DDC65FA78A8268A2351DAD680BC3B9ECB9ED07E4C9828B5E260CBC2657 | |||
| 1556 | Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe | C:\Users\admin\AppData\Local\Temp\svchost.exe | executable | |
MD5:6BB2EE4138EFE36DB57B688D7F75A6D5 | SHA256:753172DDC65FA78A8268A2351DAD680BC3B9ECB9ED07E4C9828B5E260CBC2657 | |||
| 15452 | Aucgna.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\05DDC6AA91765AACACDB0A5F96DF8199 | binary | |
MD5:E2DA8A4E3FFA98948A2482E501669BF1 | SHA256:EF75CBC2CCF7879458ACA6D5E85091FABF0BAF6B3F563AA27F12671D7CD6E4DF | |||
| 1556 | Tenorshare_12in1_Keygen_v1.3_By_DFoX.exe | C:\Users\admin\AppData\Local\Temp\xx.exe | executable | |
MD5:799F58A6C68E17378FADAB1B839A5BD0 | SHA256:4E9E3296030DF5EADED9C3E7522A956342361A6AACD8C148A98F01B3F8FDCA34 | |||
| 15452 | Aucgna.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\05DDC6AA91765AACACDB0A5F96DF8199 | der | |
MD5:E935BC5762068CAF3E24A2683B1B8A88 | SHA256:A8ACCFCFEB51BD73DF23B91F4D89FF1A9EB7438EF5B12E8AFDA1A6FF1769E89D | |||
| 15452 | Aucgna.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B3513D73A177A2707D910183759B389B_78E9BA377D96268BAF8E57FEF7614CD5 | binary | |
MD5:03928CD29500951DE18BCAD7BAD33164 | SHA256:D99181248322C3147CC53B9DD13C8657F7F359B2515A3F6DFC1D7A28DAFCC278 | |||
| 15452 | Aucgna.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:DF02CA62F7B9E56FE339B22CC36D8D91 | SHA256:99C085D3D7DA2A11CD749839A2D79A836693B382C97F5C6DD202BE0EAC81556E | |||
| 13864 | Taskmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\3534848bb9f4cb71\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
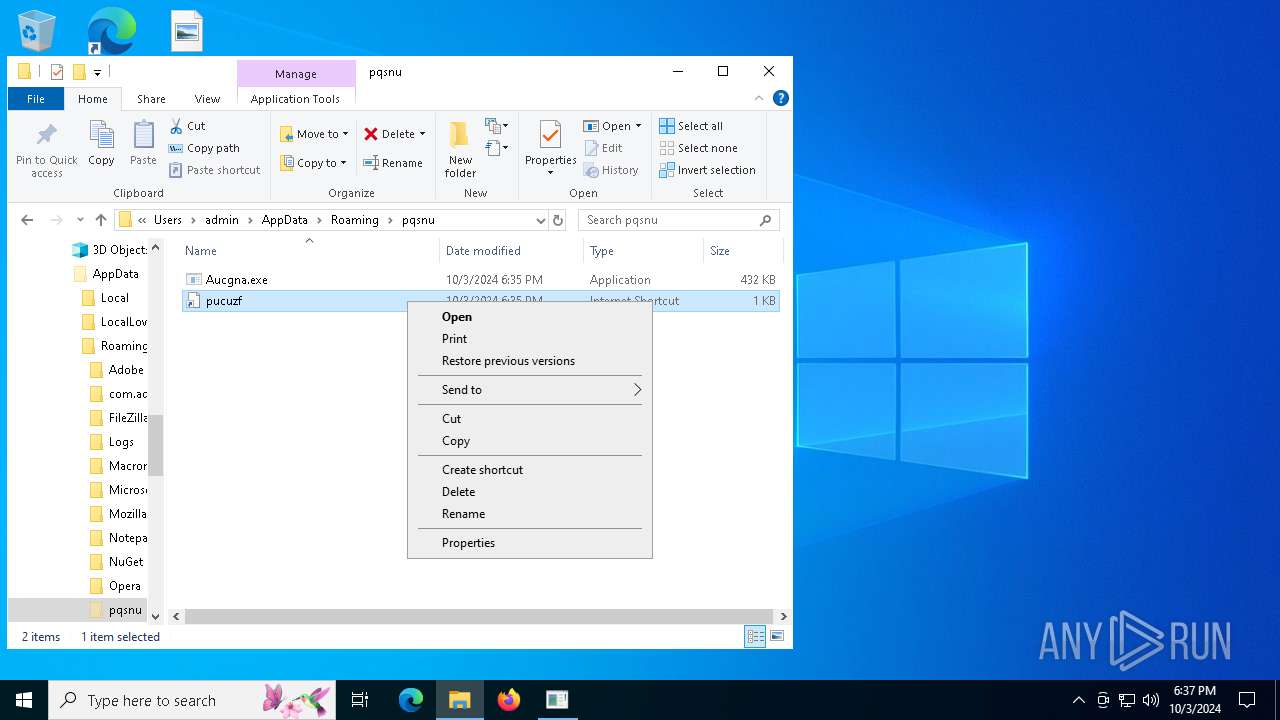
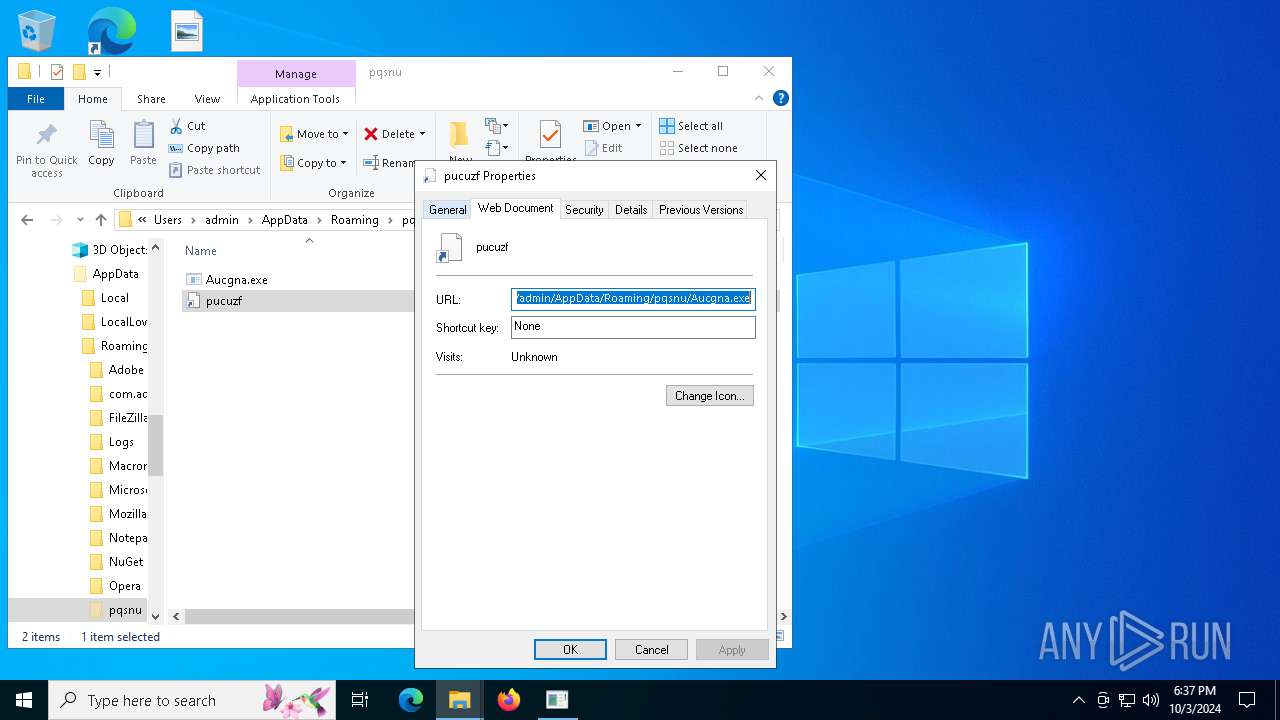
| 15452 | Aucgna.exe | C:\Users\admin\AppData\Roaming\pqsnu\pucuzf.url | url | |
MD5:5B25F687F7B78D62101D9CAE7E6740A7 | SHA256:8BE56F5846286F2FFC5701EDC6431DAA98DBF0C55291F8ACF1C9BACC0C6B2371 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
87
DNS requests
32
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
15104 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
15452 | Aucgna.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | whitelisted |
15452 | Aucgna.exe | GET | 200 | 142.250.185.99:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
15452 | Aucgna.exe | GET | 200 | 142.250.186.67:80 | http://o.pki.goog/wr2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEQCyJ0p8lP846QqzEJ6Bi00f | unknown | — | — | whitelisted |
5136 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
16500 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
16500 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3928 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3928 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5136 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5136 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.mine .nu Domain |
2256 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.mine .nu Domain |
2256 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.mine .nu Domain |