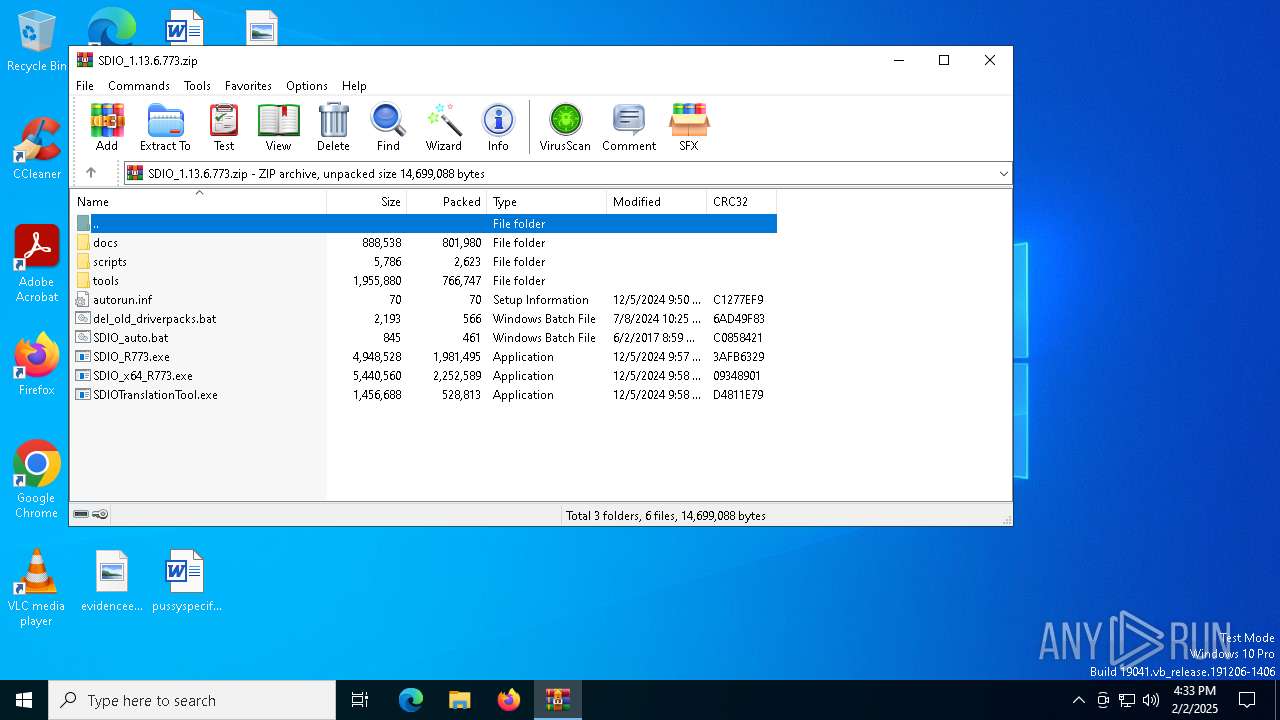
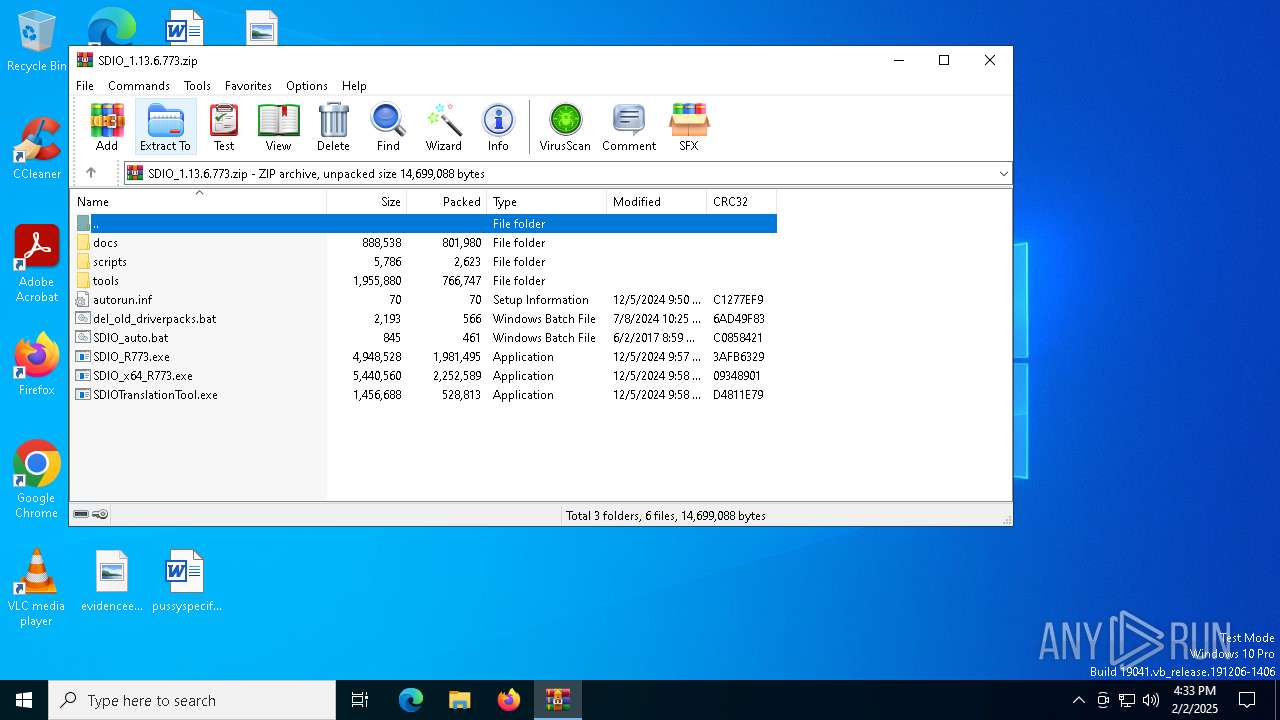
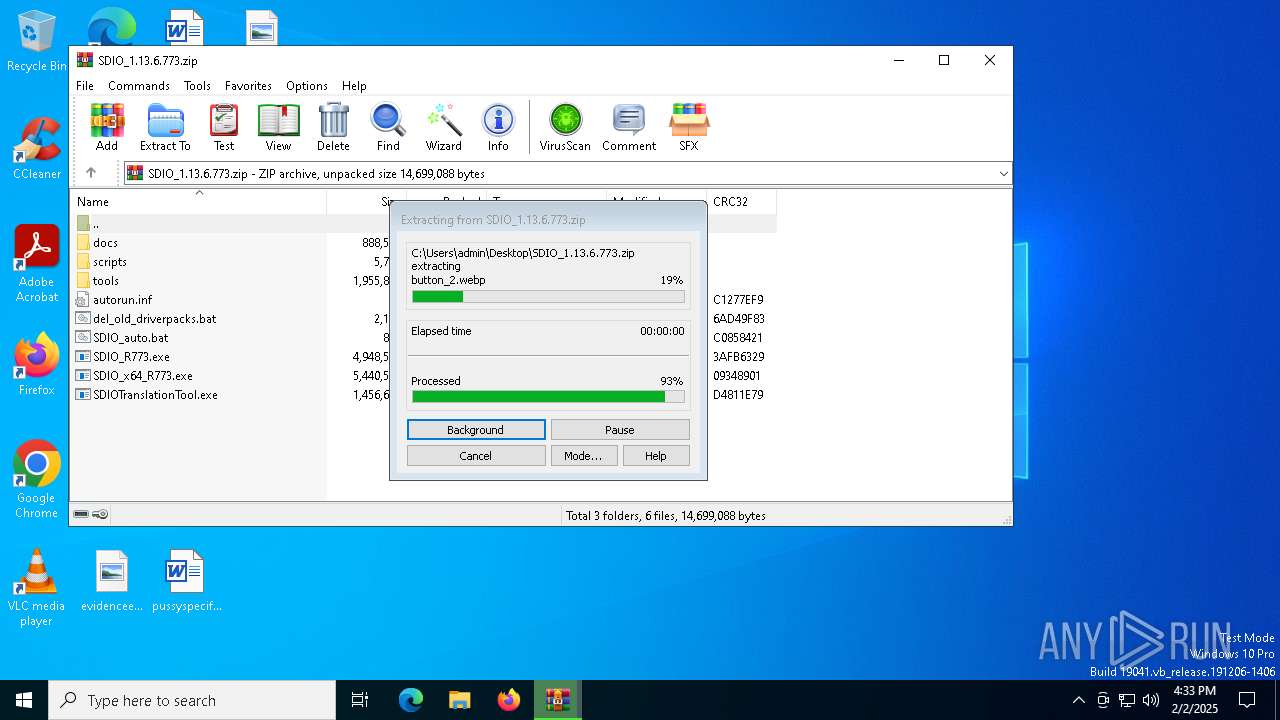
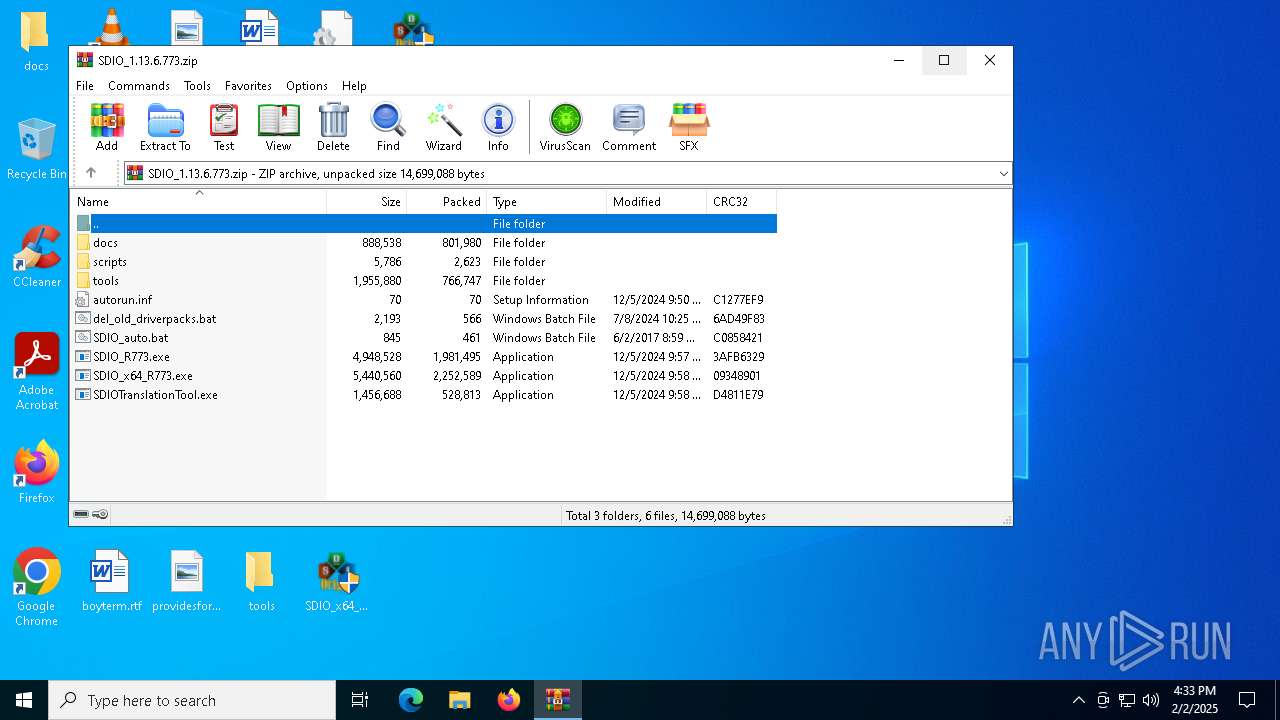
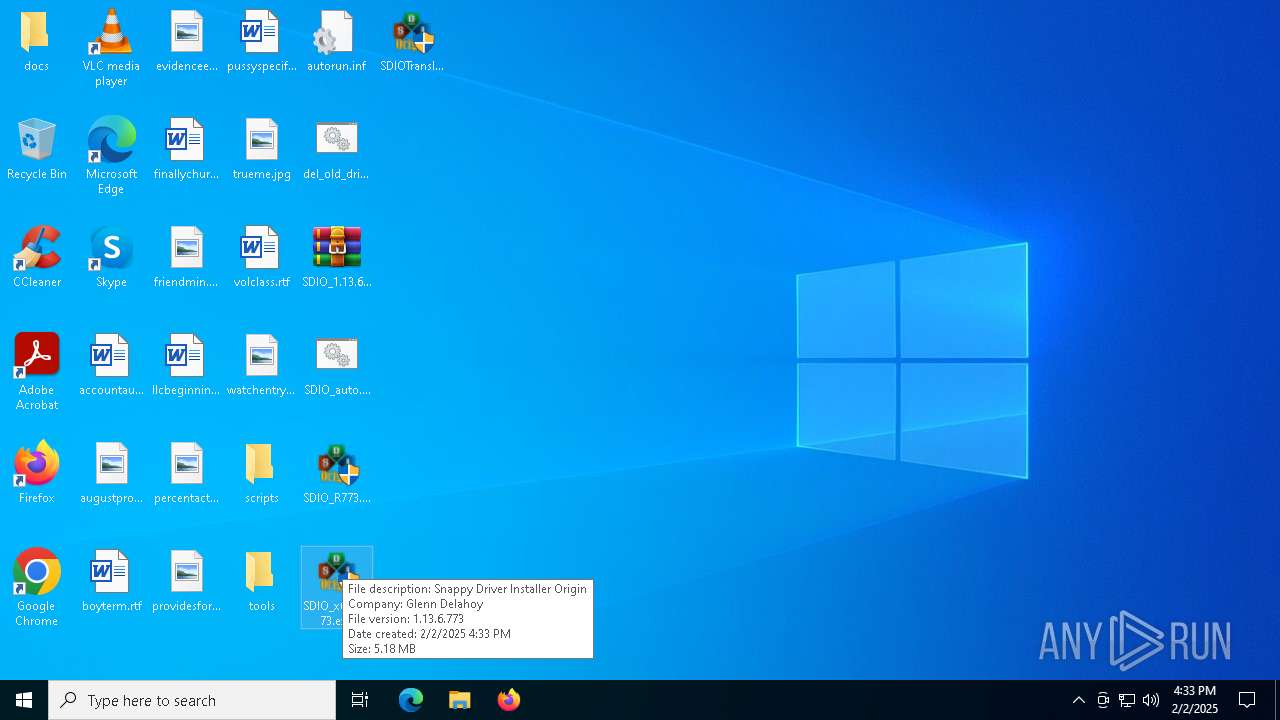
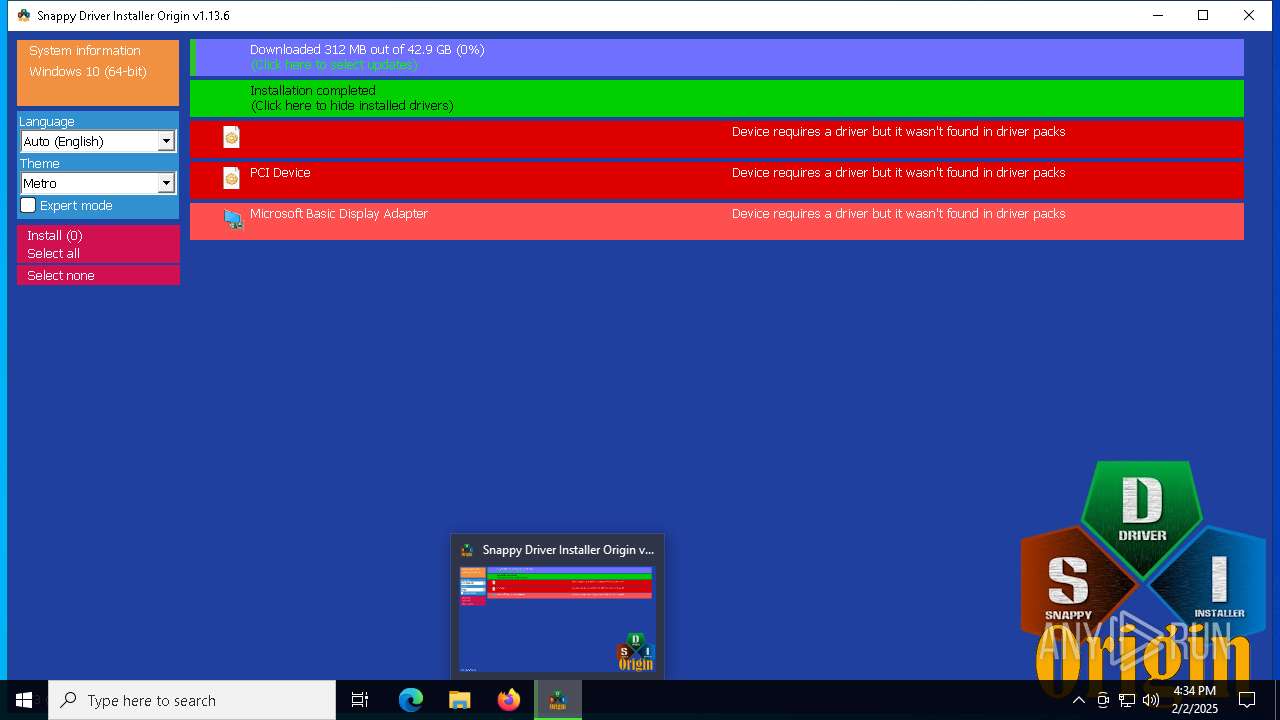
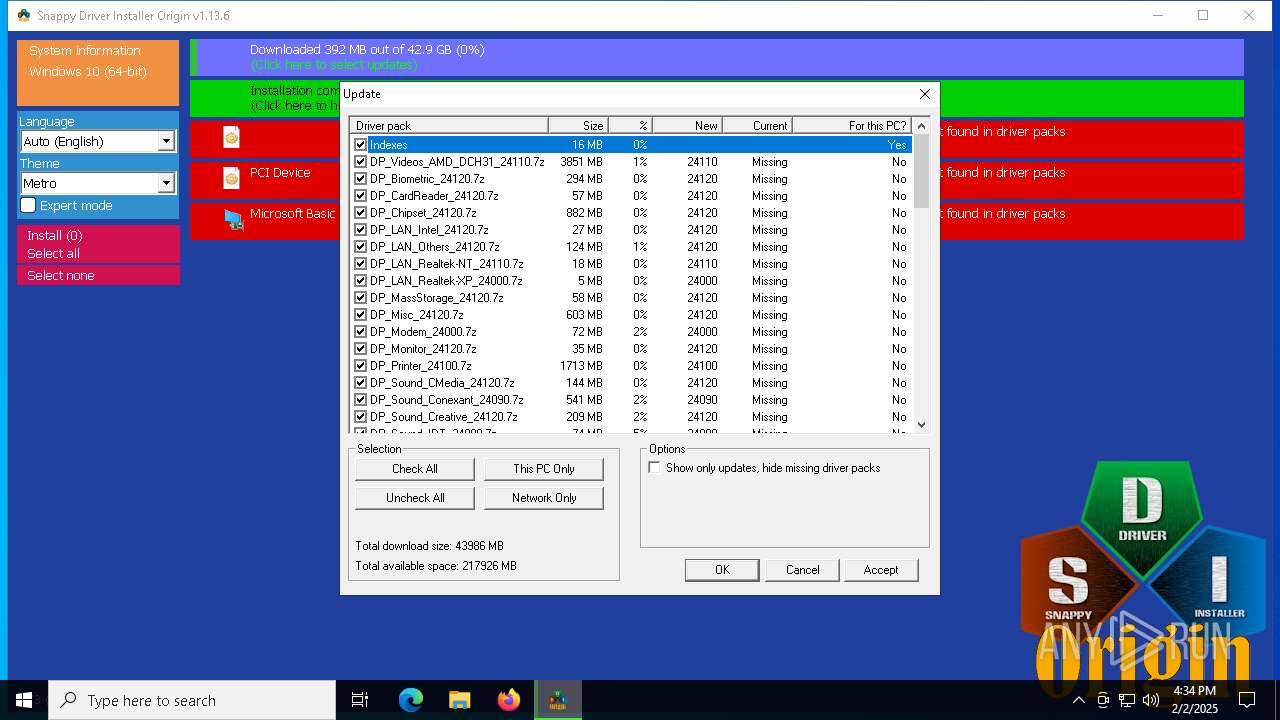
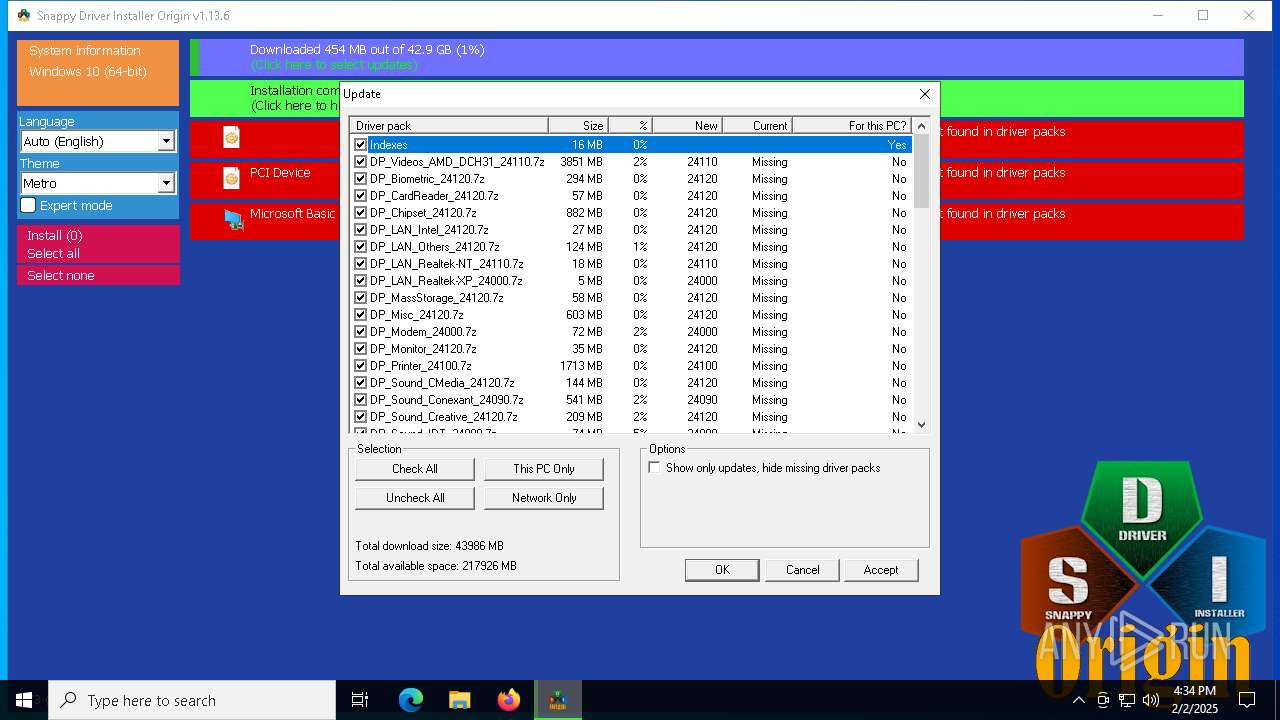
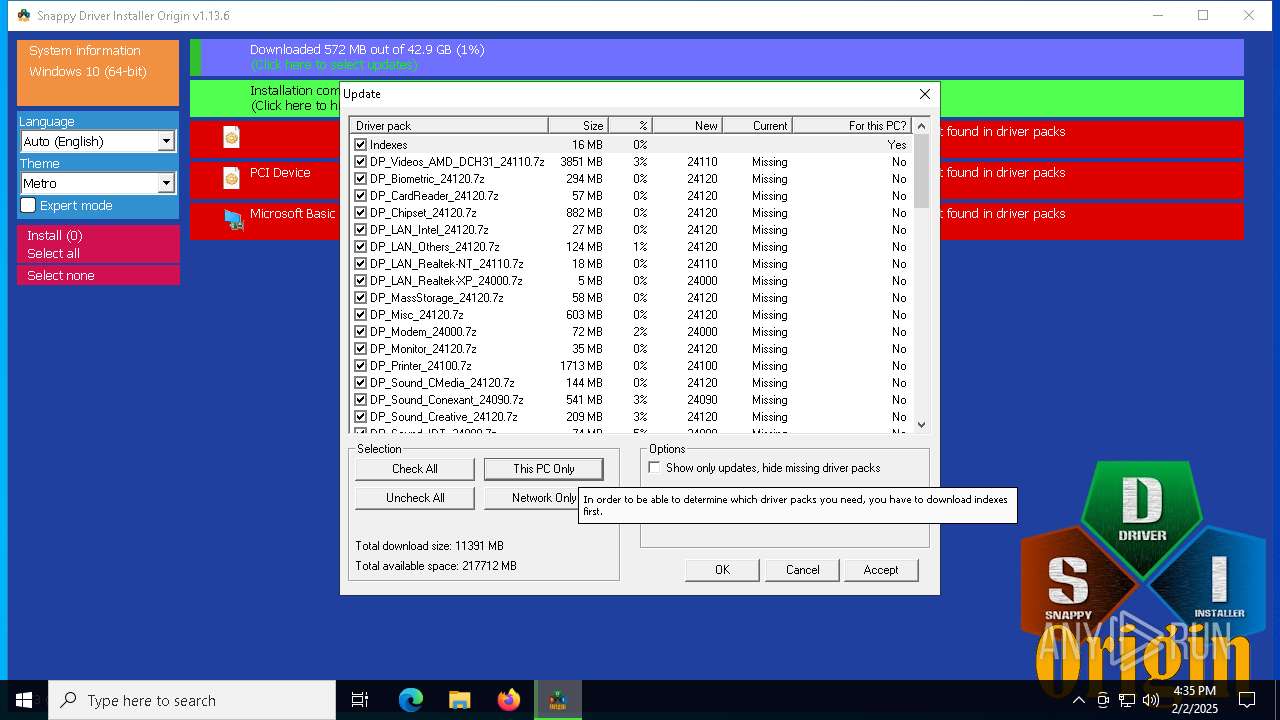
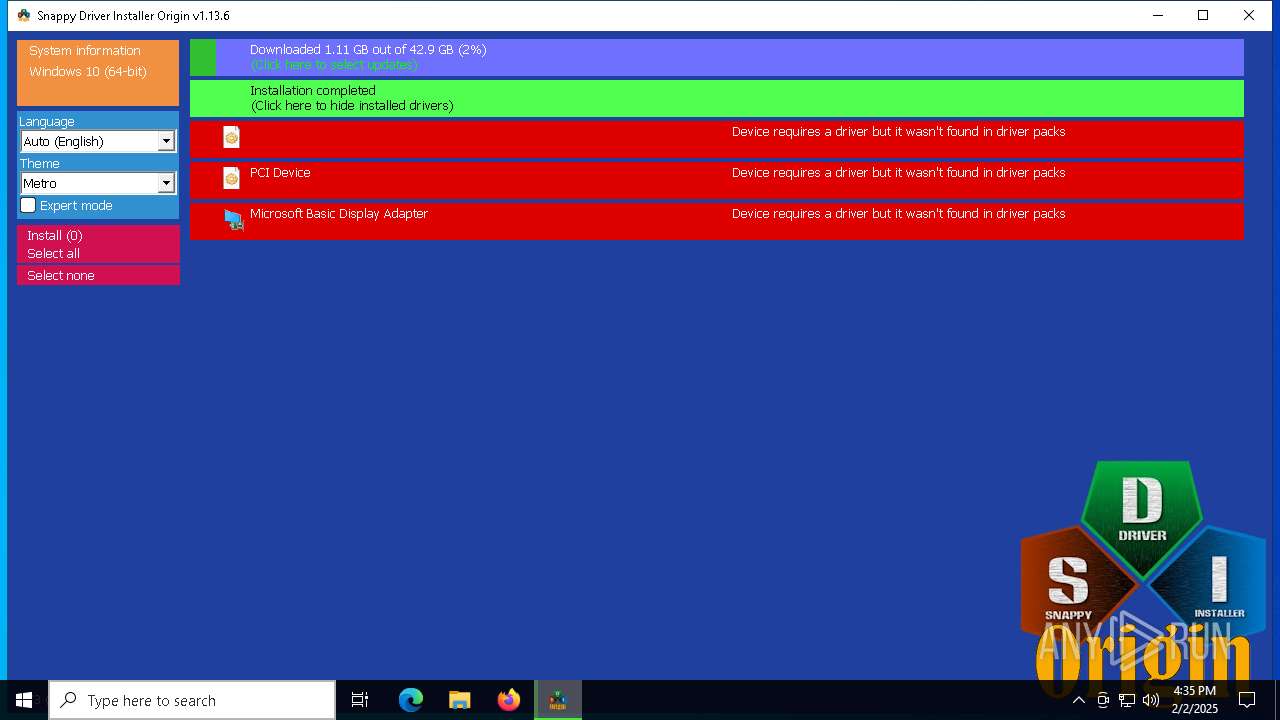
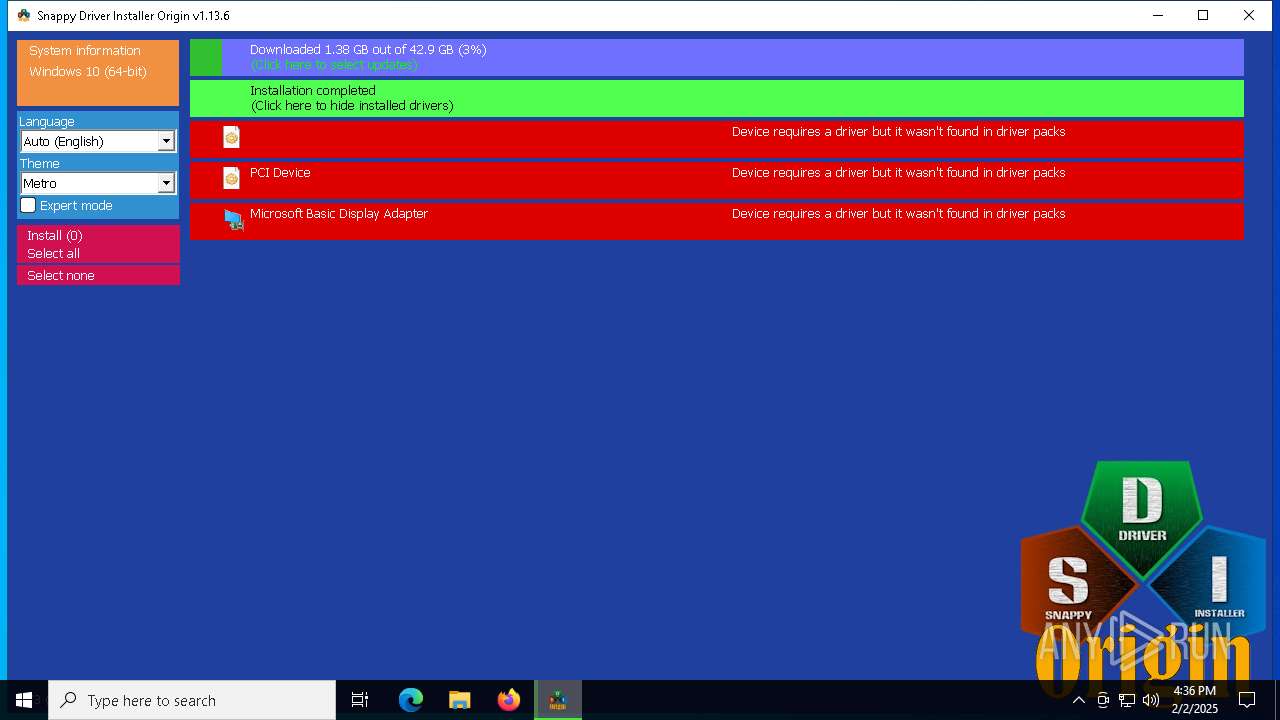
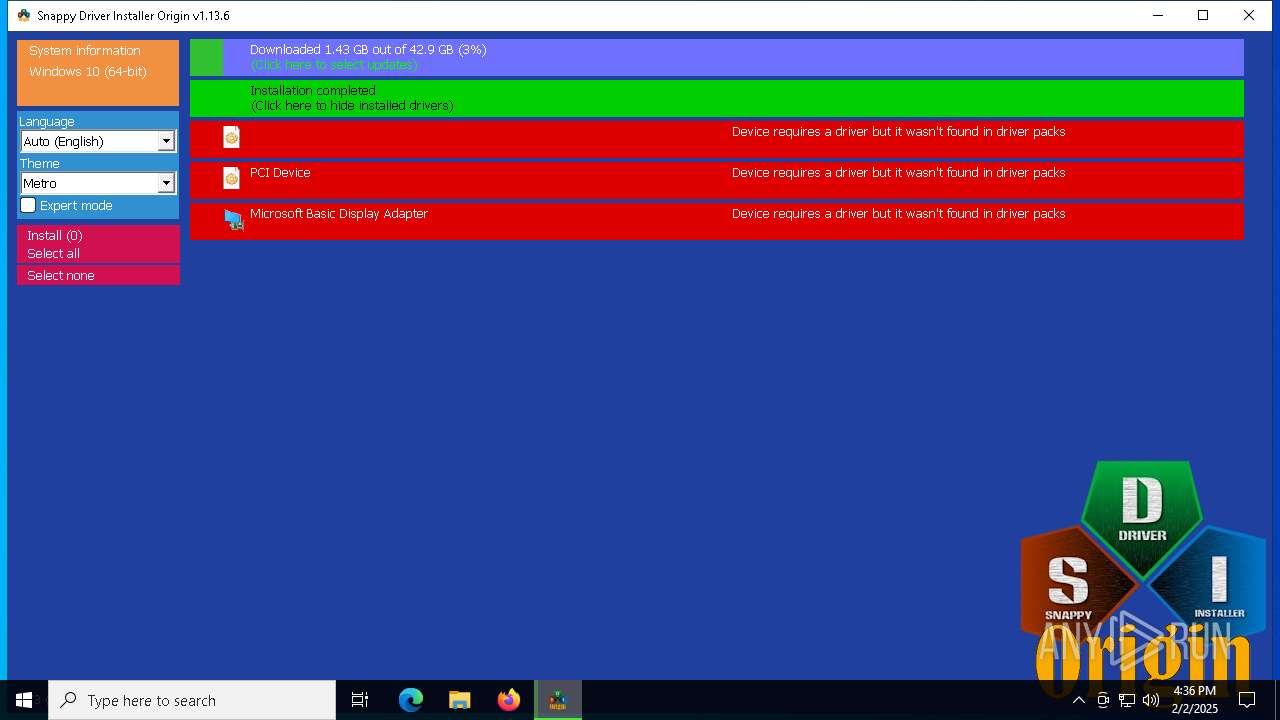
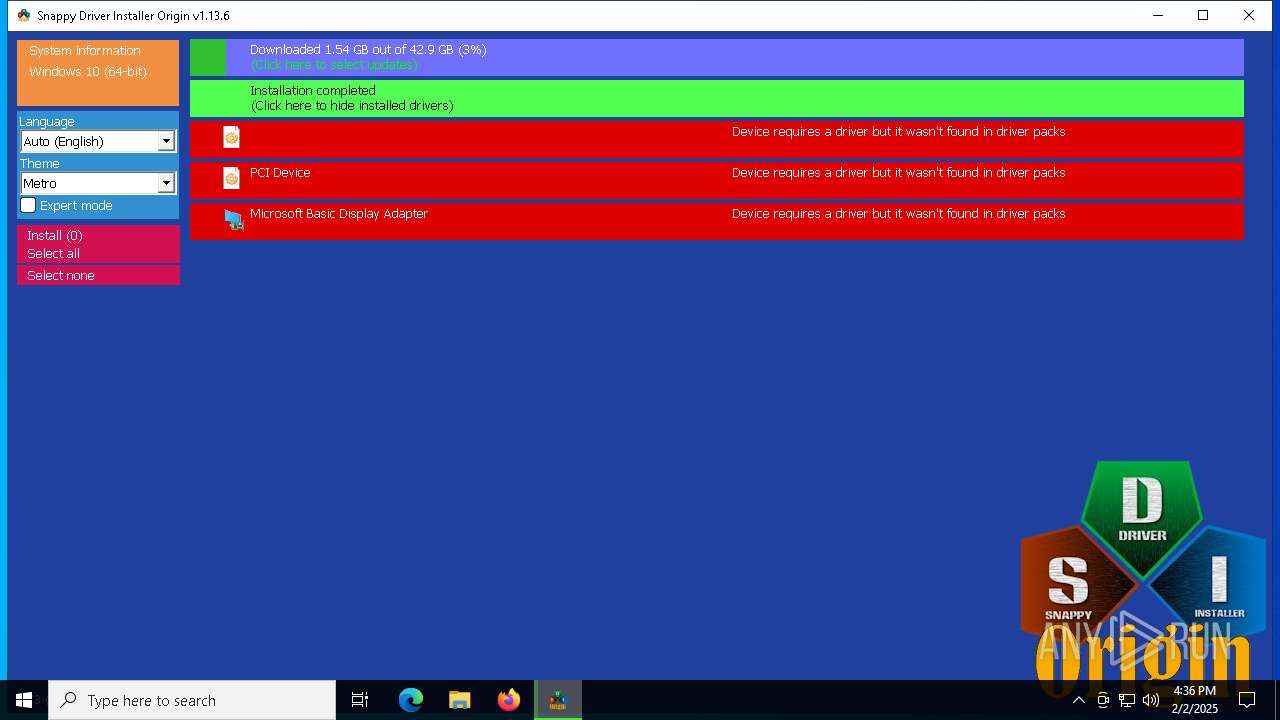
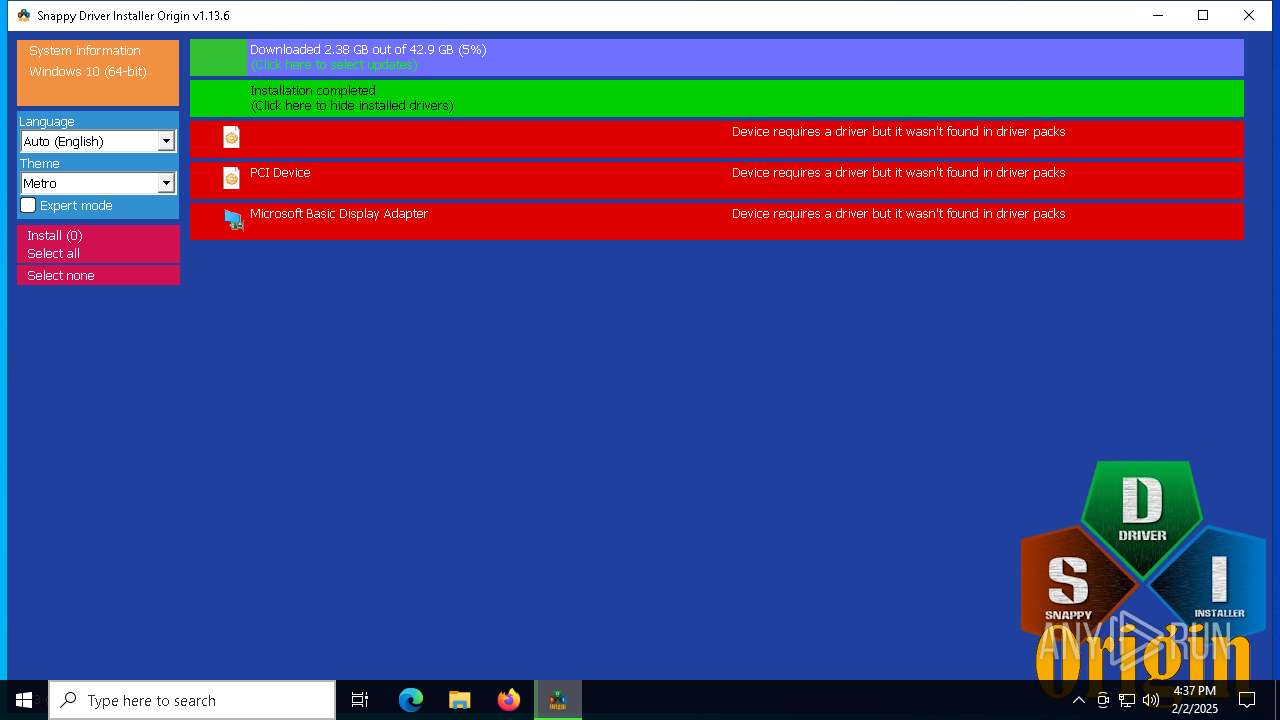
| File name: | SDIO_1.13.6.773.zip |
| Full analysis: | https://app.any.run/tasks/bb812c1e-8433-421b-9c32-d0041fe3e964 |
| Verdict: | Malicious activity |
| Analysis date: | February 02, 2025, 16:33:09 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 1DC08B3993B1E41BA7458C272663FD48 |
| SHA1: | 6A0697E00C6968286D3E4BA2695C0F6F9F52AB3A |
| SHA256: | B40032D3B3E47423356B515FFBFCCA1A9986E7213B36336DB1BCD0920E247223 |
| SSDEEP: | 98304:HE4Wo6DFJlFn7Mtw5AFSG4MkCsvbF/77ysglMFogFMQQZnxZntcJwshVR1FSI0E6:kfaxtQJpzgl |
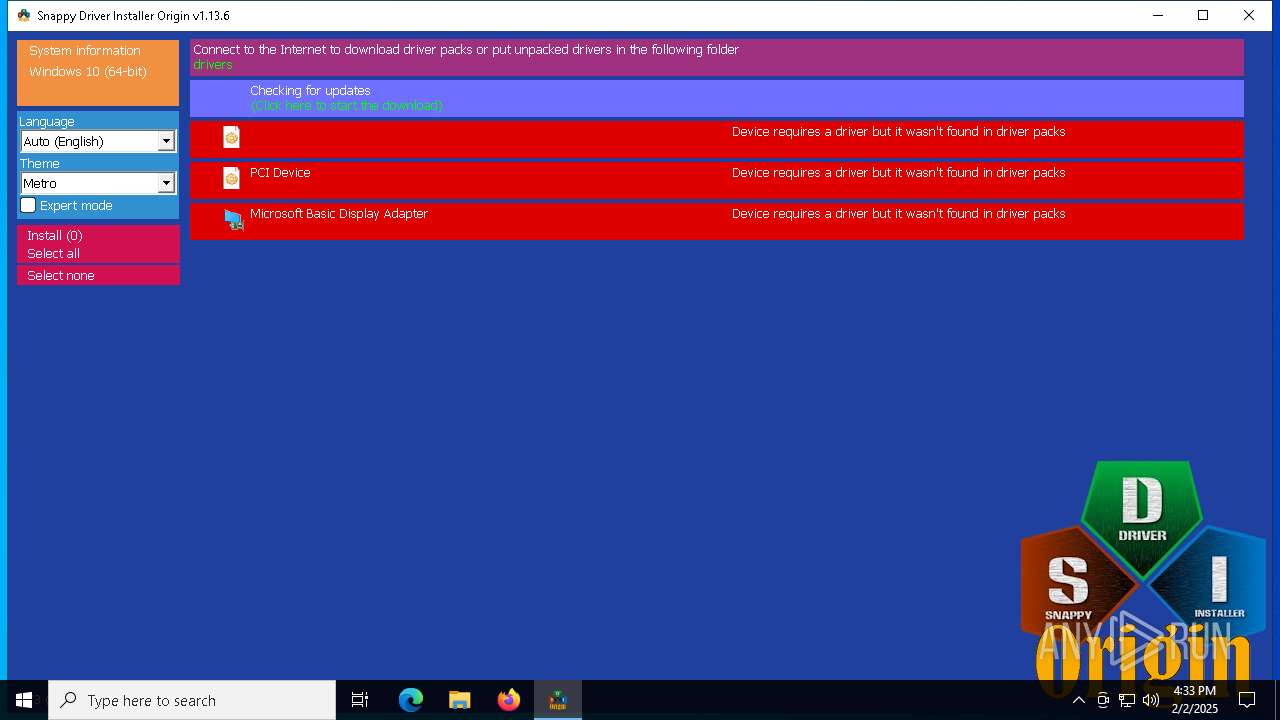
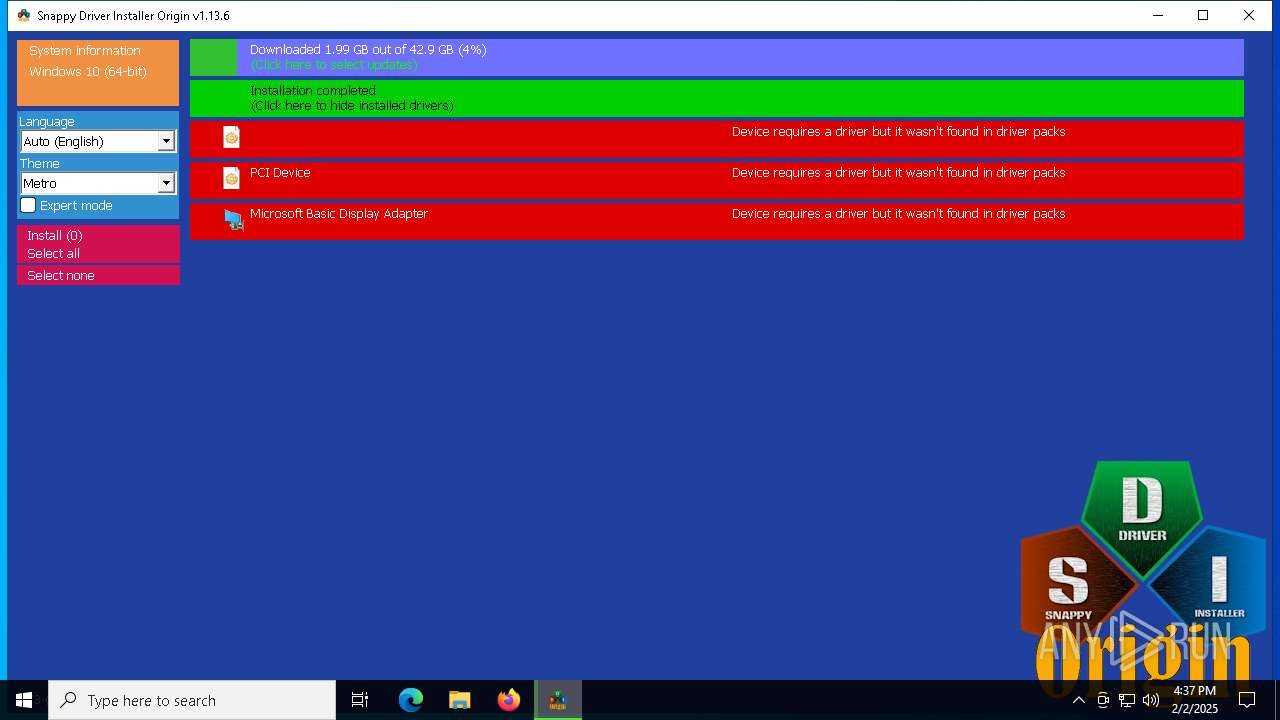
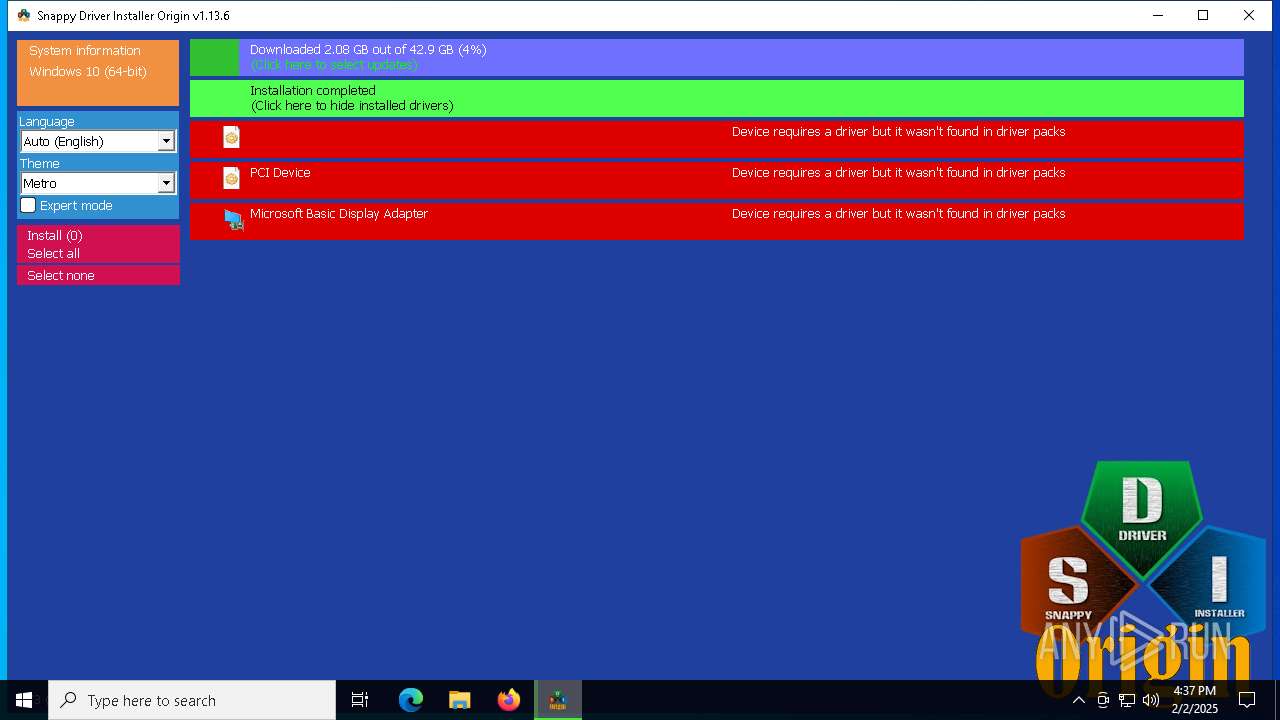
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6332)
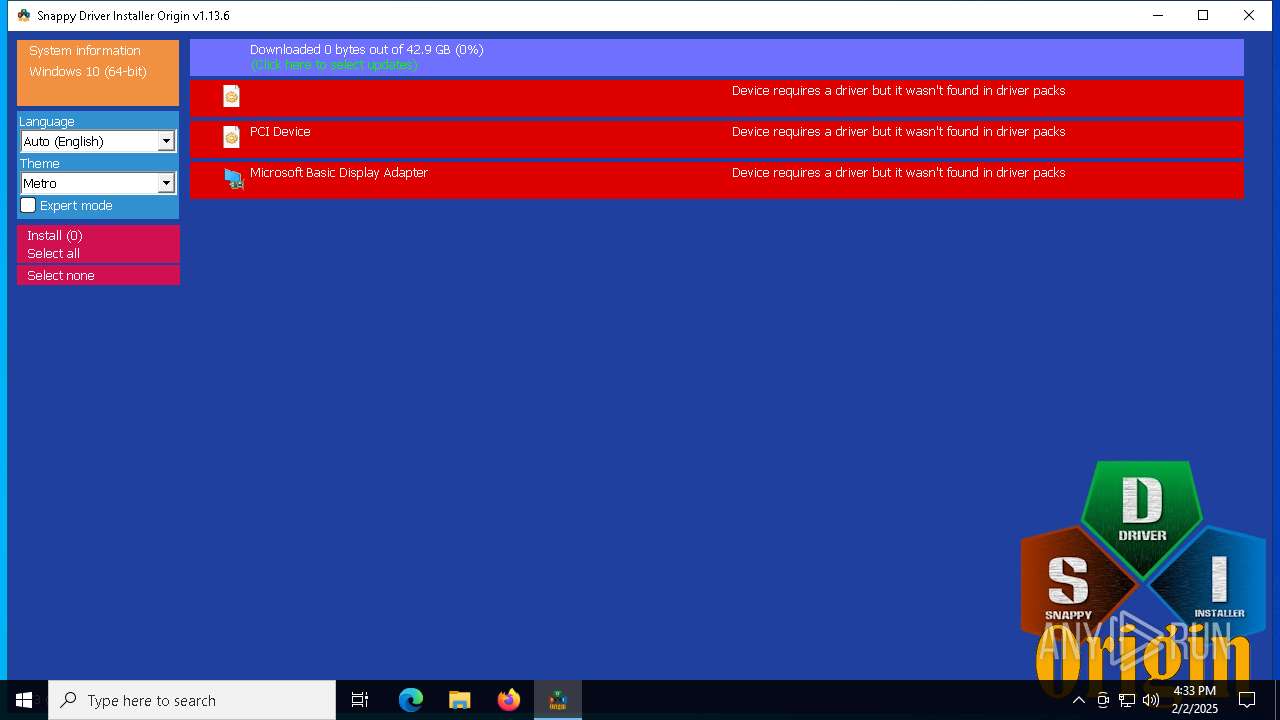
BITTORRENT has been detected (SURICATA)
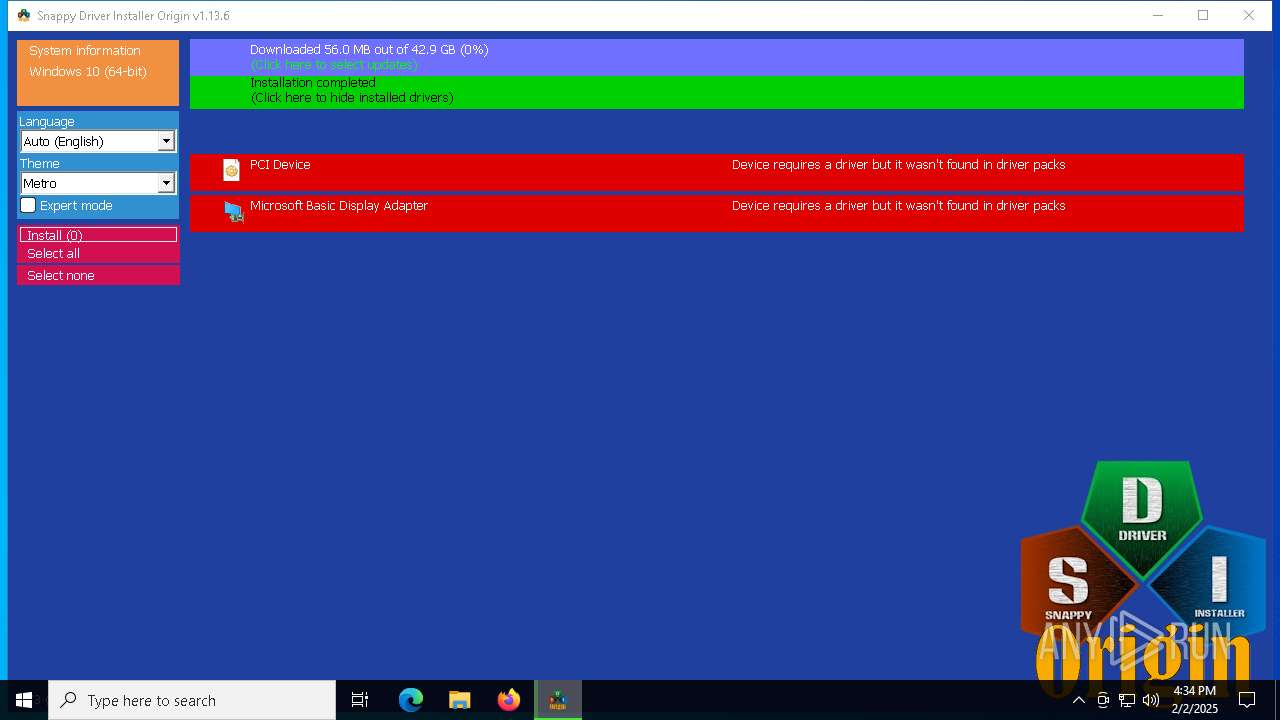
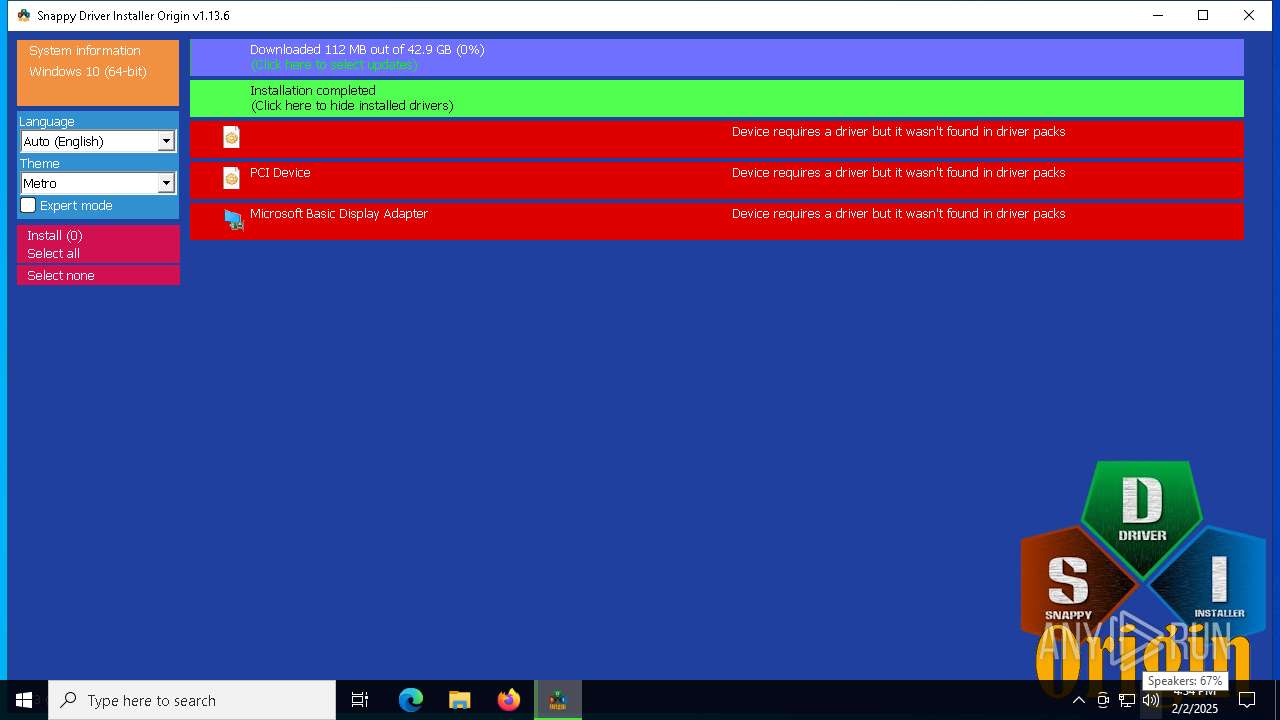
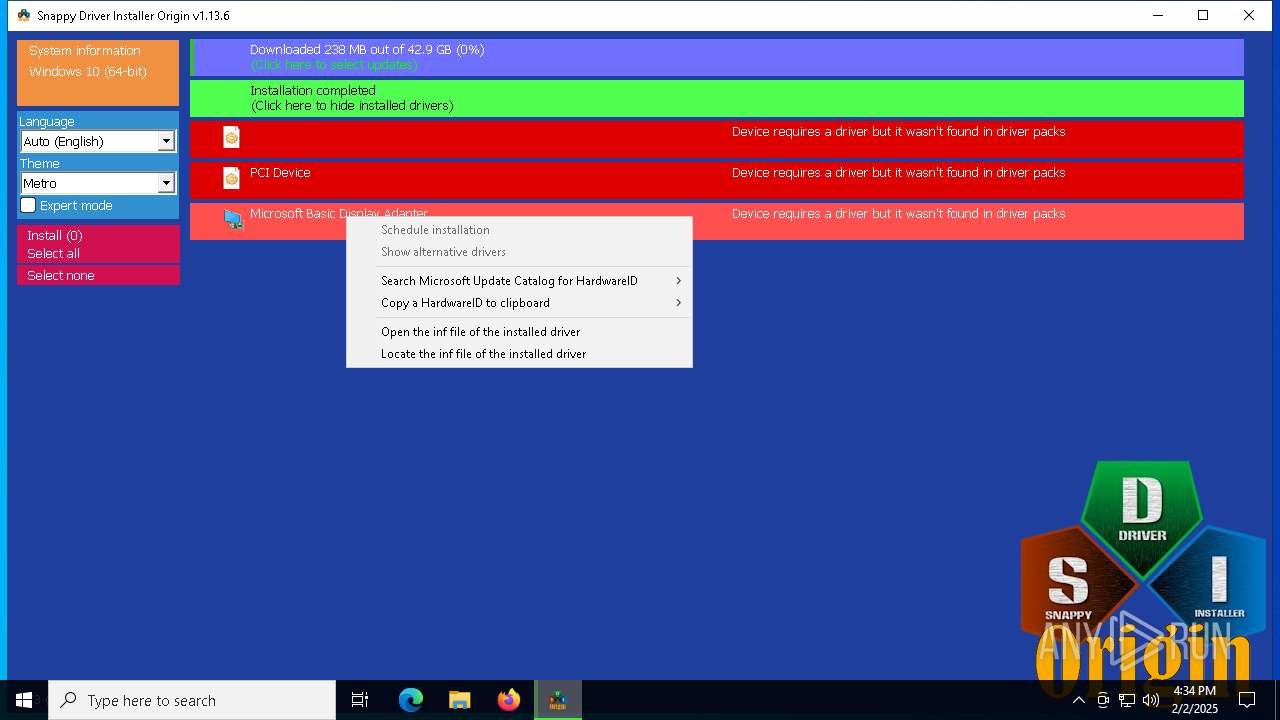
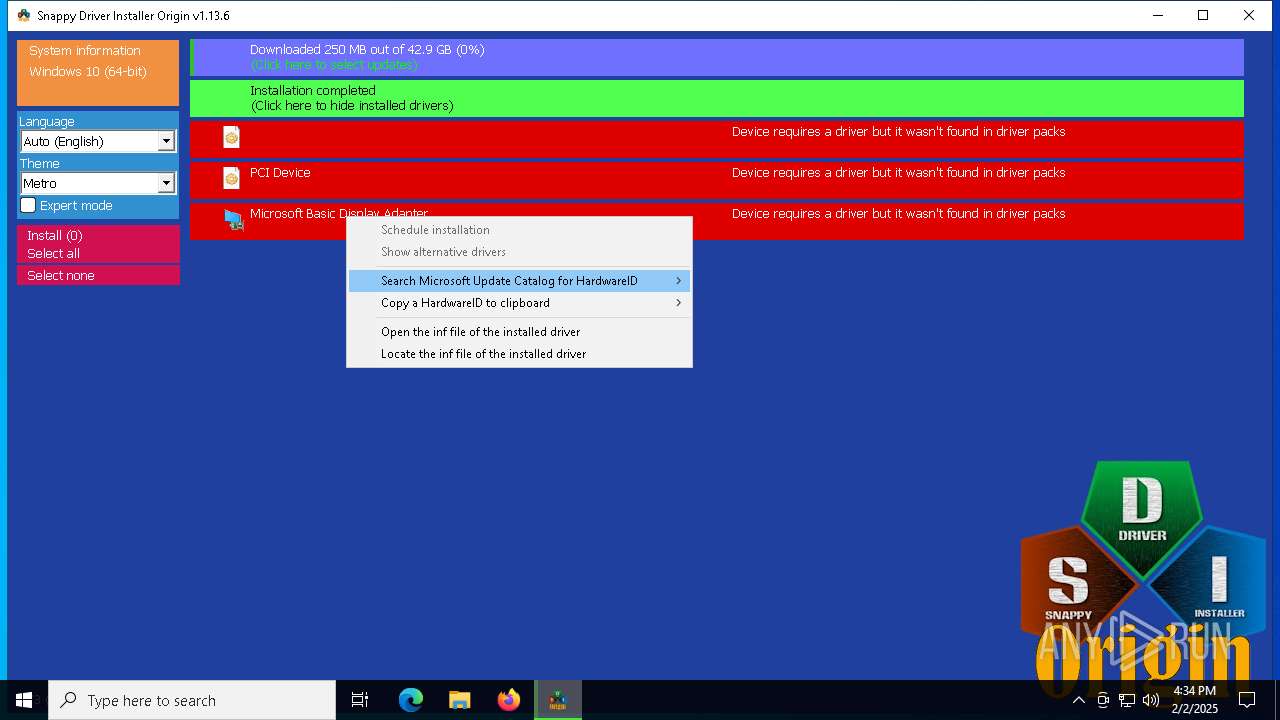
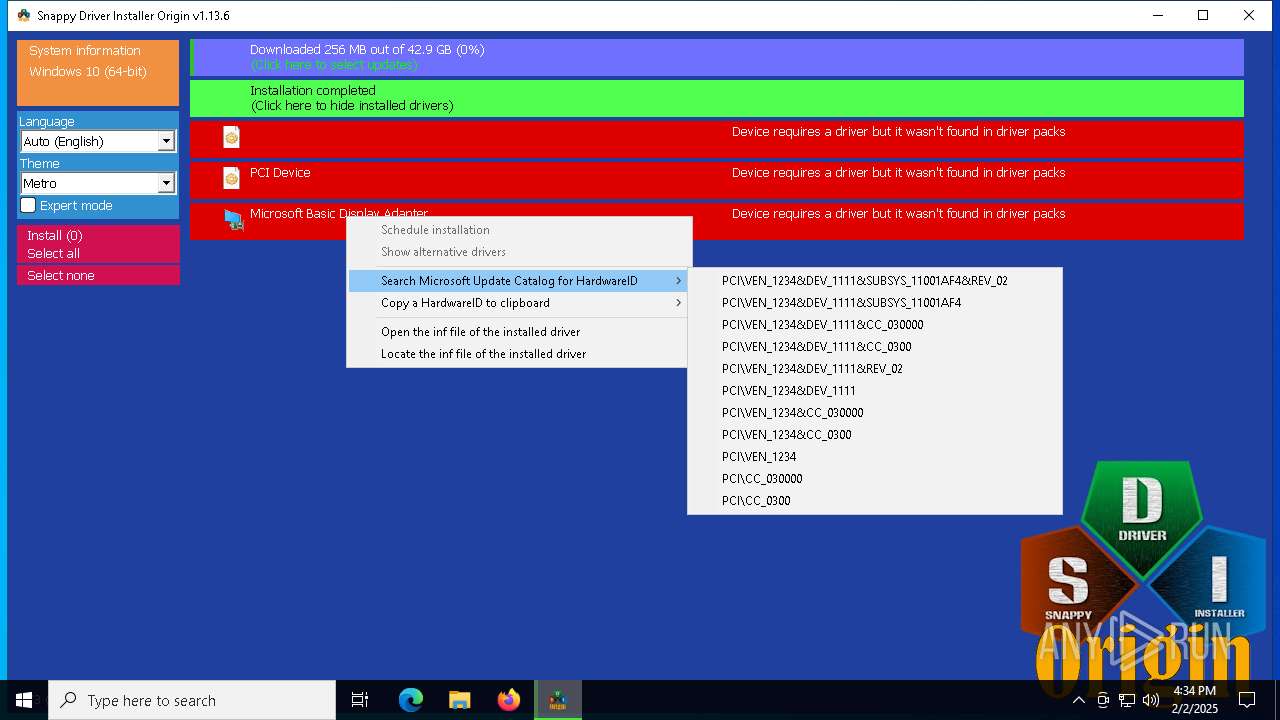
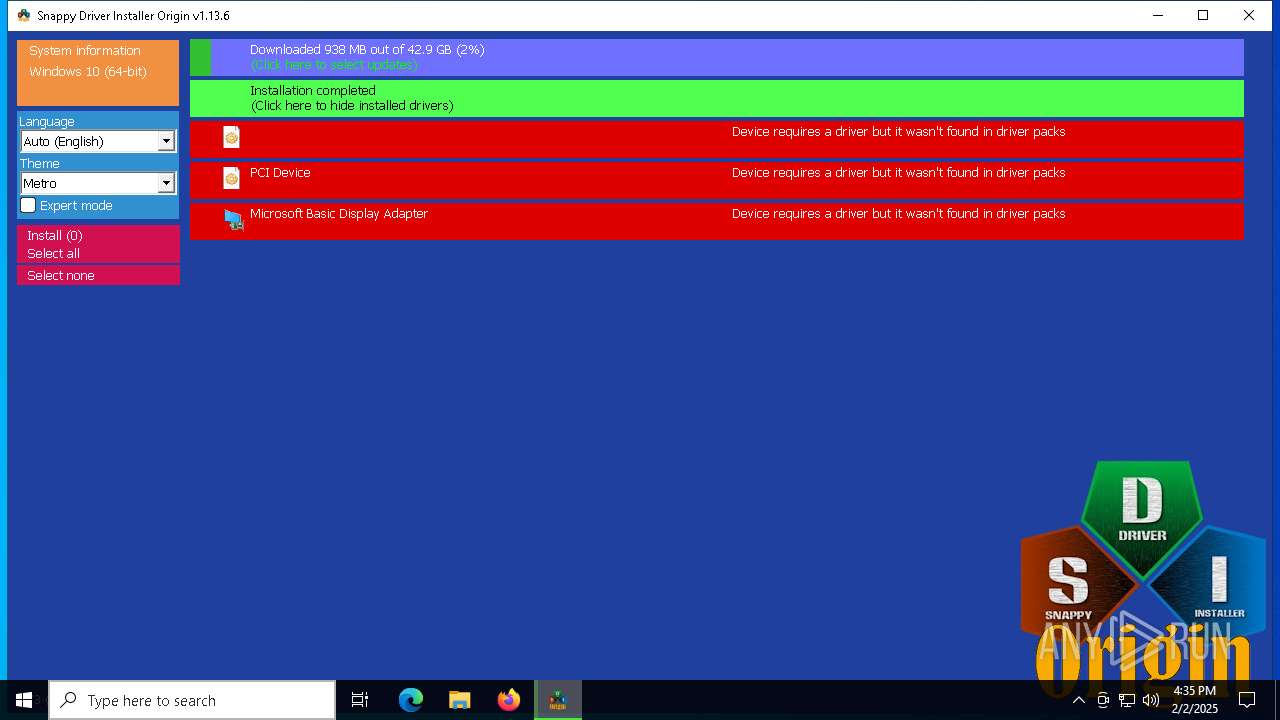
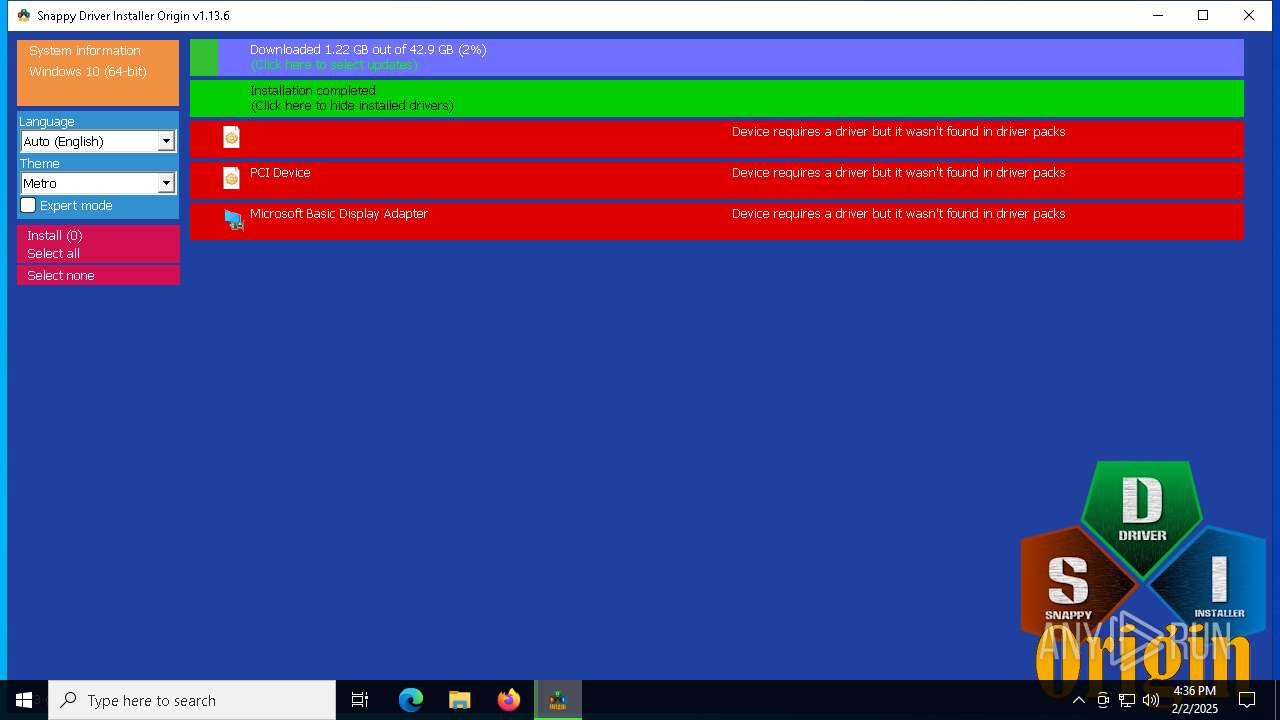
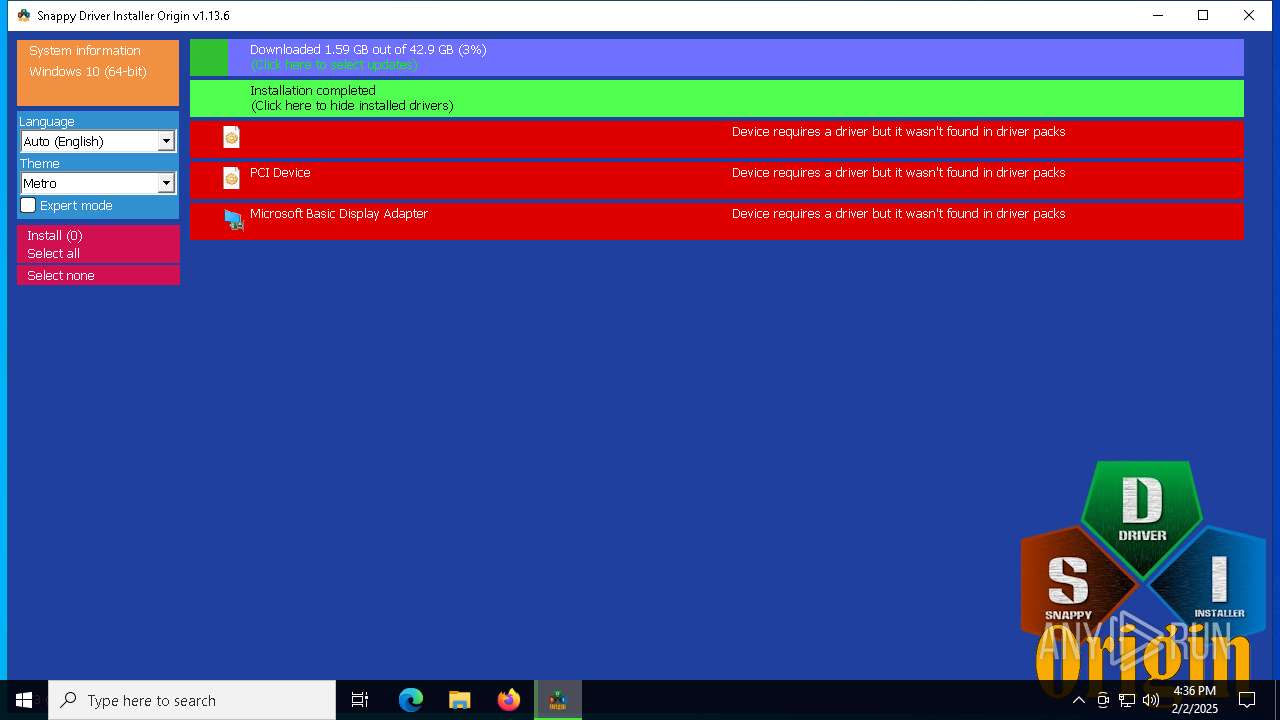
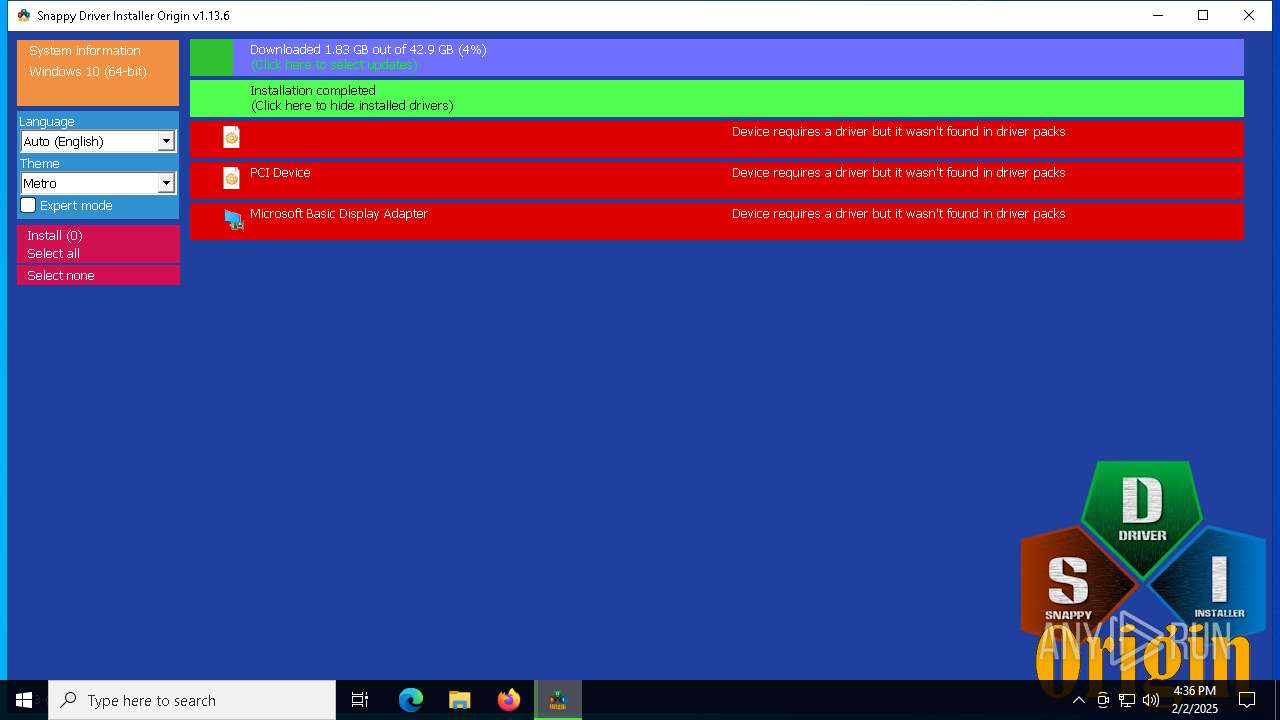
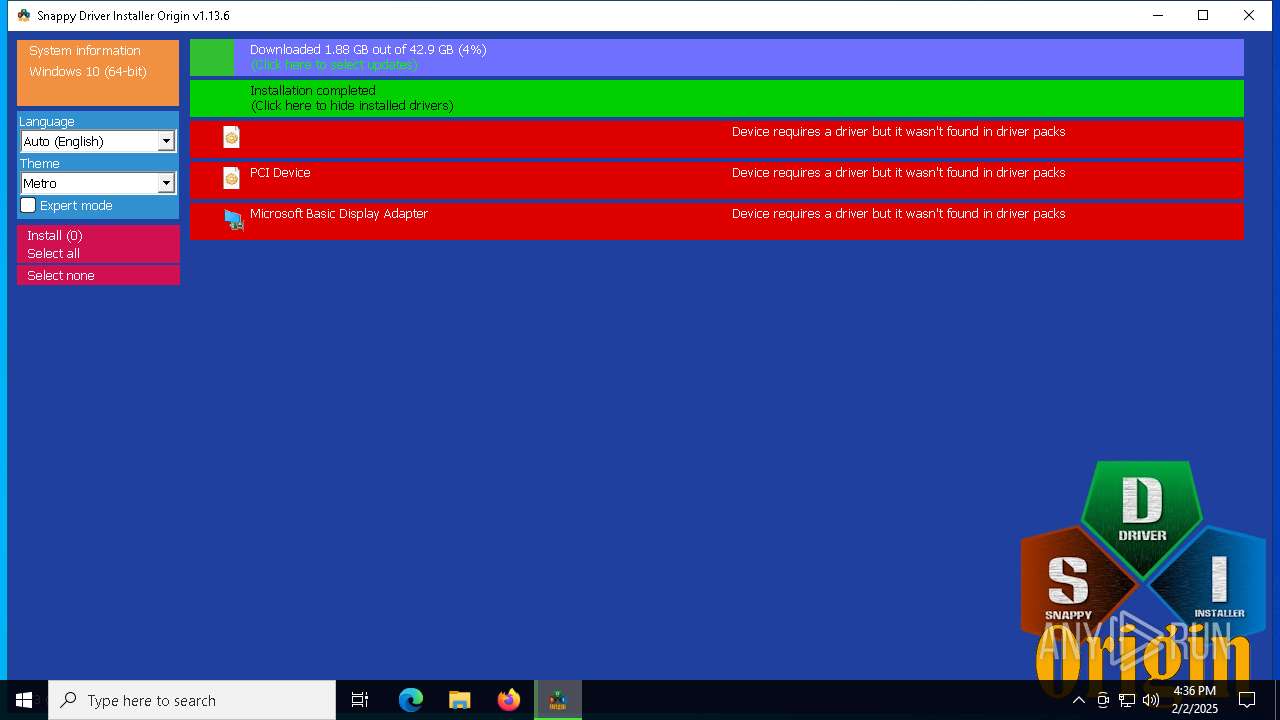
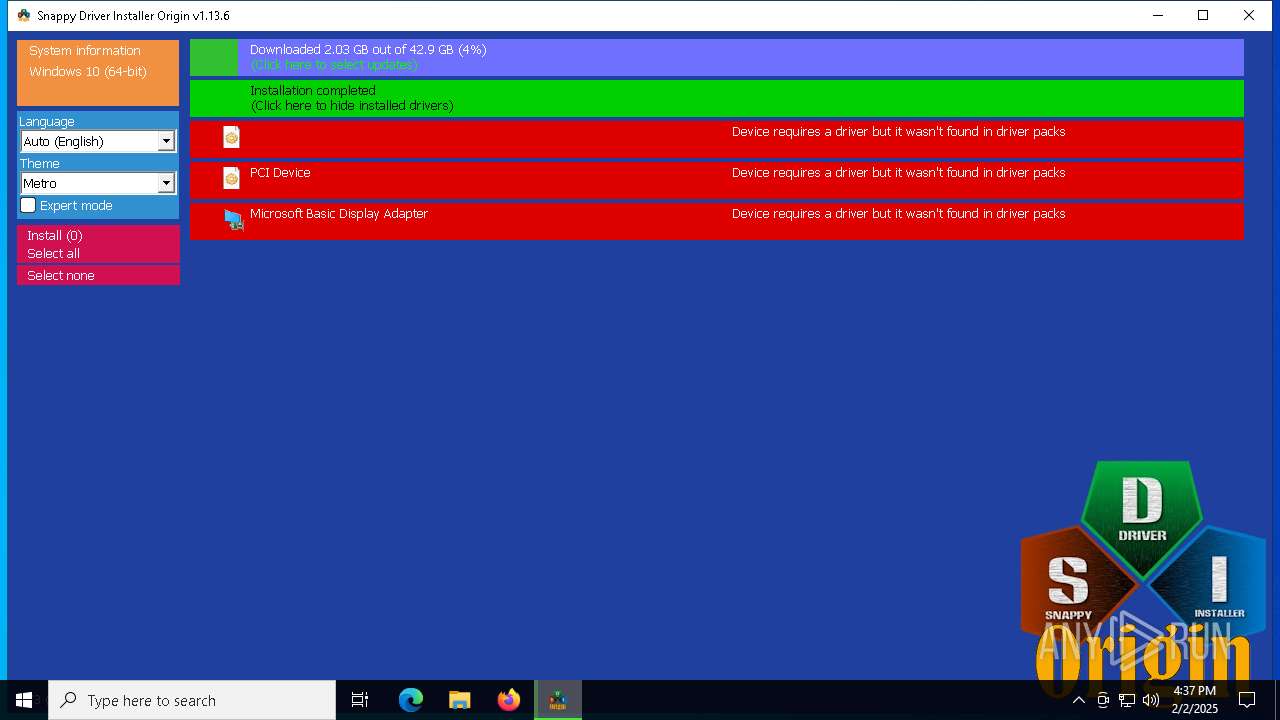
- SDIO_x64_R773.exe (PID: 5564)
SUSPICIOUS
Reads the date of Windows installation
- SDIO_x64_R773.exe (PID: 5564)
There is functionality for taking screenshot (YARA)
- SDIO_x64_R773.exe (PID: 5564)
Potential Corporate Privacy Violation
- SDIO_x64_R773.exe (PID: 5564)
Reads security settings of Internet Explorer
- SDIO_x64_R773.exe (PID: 5564)
Starts CMD.EXE for commands execution
- SDIO_x64_R773.exe (PID: 5564)
Connects to unusual port
- SDIO_x64_R773.exe (PID: 5564)
INFO
Manual execution by a user
- SDIO_x64_R773.exe (PID: 4944)
- SDIO_x64_R773.exe (PID: 5564)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6332)
The sample compiled with english language support
- WinRAR.exe (PID: 6332)
Checks supported languages
- SDIO_x64_R773.exe (PID: 5564)
Reads Environment values
- SDIO_x64_R773.exe (PID: 5564)
Reads the computer name
- SDIO_x64_R773.exe (PID: 5564)
Process checks computer location settings
- SDIO_x64_R773.exe (PID: 5564)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:12:06 08:51:00 |
| ZipCRC: | 0xc1277ef9 |
| ZipCompressedSize: | 70 |
| ZipUncompressedSize: | 70 |
| ZipFileName: | autorun.inf |
Total processes
140
Monitored processes
8
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 524 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SDIO_x64_R773.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4944 | "C:\Users\admin\Desktop\SDIO_x64_R773.exe" | C:\Users\admin\Desktop\SDIO_x64_R773.exe | — | explorer.exe | |||||||||||
User: admin Company: Glenn Delahoy Integrity Level: MEDIUM Description: Snappy Driver Installer Origin Exit code: 3221226540 Version: 1.13.6.773 Modules
| |||||||||||||||
| 5564 | "C:\Users\admin\Desktop\SDIO_x64_R773.exe" | C:\Users\admin\Desktop\SDIO_x64_R773.exe | explorer.exe | ||||||||||||
User: admin Company: Glenn Delahoy Integrity Level: HIGH Description: Snappy Driver Installer Origin Version: 1.13.6.773 Modules
| |||||||||||||||
| 6332 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\SDIO_1.13.6.773.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6472 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6480 | "C:\Windows\System32\cmd.exe" /c rd /s /q "C:\Users\admin\AppData\Local\Temp\SDIO" | C:\Windows\System32\cmd.exe | — | SDIO_x64_R773.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6848 | "C:\Windows\System32\cmd.exe" /c rd /s /q "C:\Users\admin\AppData\Local\Temp\SDIO" | C:\Windows\System32\cmd.exe | — | SDIO_x64_R773.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6872 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 109
Read events
10 075
Write events
21
Delete events
13
Modification events
| (PID) Process: | (6332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\SDIO_1.13.6.773.zip | |||
| (PID) Process: | (6332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (6332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
3
Suspicious files
17
Text files
155
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6332 | WinRAR.exe | C:\Users\admin\Desktop\scripts\example-script.txt | text | |
MD5:B7E03040B6CCEDDC628FF4FAA729BA2B | SHA256:928F4F24F63DFC86847D329C57C01C072989985449D0F8EF64AC1879F11BB507 | |||
| 6332 | WinRAR.exe | C:\Users\admin\Desktop\autorun.inf | binary | |
MD5:C40603D1014DDB706713B8C63CE01DE2 | SHA256:7818509C61D0D0FD56B9EC917A349BFF81C0D9A742512C9F4BA355536B4F0AEE | |||
| 6332 | WinRAR.exe | C:\Users\admin\Desktop\docs\changelog.txt | text | |
MD5:B530640E6175F30D1D2C2D9560D22A82 | SHA256:0DD428D38D5CB3FF0988FF30C2684DABE8F9ED67AF512BBF7EB5A3BDE9A380F0 | |||
| 6332 | WinRAR.exe | C:\Users\admin\Desktop\del_old_driverpacks.bat | text | |
MD5:92D1B494767DEBC2113F9179CBDA5665 | SHA256:2F6FC9D5FEF3A431F4D3282299FF31433C4006B2338215E572BFC98CBACB4361 | |||
| 6332 | WinRAR.exe | C:\Users\admin\Desktop\docs\SDIO Reference Manual.pdf | ||
MD5:F151A59CE4B4DBC7E978C12479CBEDCD | SHA256:1FA2B9FB512986833FE5CDBD6B01A288C5209380DA5567DB155DA05D8493A4BA | |||
| 6332 | WinRAR.exe | C:\Users\admin\Desktop\scripts\install.txt | text | |
MD5:402882E7C06FDAD3F9EB3A5FDC827AEC | SHA256:389E6C0F535341EA56922773B4ADBB481FE9D1C4DFFEC0877E18F5B9DC8EC237 | |||
| 6332 | WinRAR.exe | C:\Users\admin\Desktop\scripts\mahalo-test.txt | text | |
MD5:0D3DACDBFEFBCCF574ABC9468B4F6CBB | SHA256:F82A508192820EE55EA0005E6D6F41AE9E0C12FA303E80F85E74B1AD752E8702 | |||
| 6332 | WinRAR.exe | C:\Users\admin\Desktop\scripts\autoupdate.bat | text | |
MD5:3342F57D5527BDE4740984AA492223F9 | SHA256:3A5EDFAA2CDAACB452D7F09EC7D3BD9A374D335A46173F8E0D2D678FB63FB245 | |||
| 6332 | WinRAR.exe | C:\Users\admin\Desktop\scripts\oakslabs-test.txt | text | |
MD5:17C2A637DF51FC6C067853FA01F69550 | SHA256:4CB226CF93D706345198F2E6DA486509066A4229A44F6A4FFA68036CBE0302BA | |||
| 6332 | WinRAR.exe | C:\Users\admin\Desktop\scripts\prep_unpacked.bat | text | |
MD5:00BDB244439526A613B23F1EA831D926 | SHA256:671C3B573A7A0A617E5A1156EC2C6496846A3A256B64A5AD1CE92FD179904954 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
369
DNS requests
19
Threats
31
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6228 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4144 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5564 | SDIO_x64_R773.exe | GET | 200 | 110.232.143.85:80 | http://www.snappy-driver-installer.org/downloads/SDIO_Update.torrent | unknown | — | — | unknown |
4144 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2088 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1076 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
router.bittorrent.com |
| whitelisted |
router.utorrent.com |
| whitelisted |
router.bitcomet.com |
| unknown |
www.snappy-driver-installer.org |
| unknown |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5564 | SDIO_x64_R773.exe | Potential Corporate Privacy Violation | ET P2P Possible Torrent Download via HTTP Request |
5564 | SDIO_x64_R773.exe | Potential Corporate Privacy Violation | ET P2P BitTorrent - Torrent File Downloaded |
5564 | SDIO_x64_R773.exe | Misc activity | INFO [ANY.RUN] P2P BitTorrent Protocol |
5564 | SDIO_x64_R773.exe | Potential Corporate Privacy Violation | ET P2P Vuze BT UDP Connection (5) |
5564 | SDIO_x64_R773.exe | Misc activity | INFO [ANY.RUN] P2P BitTorrent Protocol |
5564 | SDIO_x64_R773.exe | Potential Corporate Privacy Violation | GPL P2P BitTorrent transfer |
5564 | SDIO_x64_R773.exe | Misc activity | INFO [ANY.RUN] P2P BitTorrent Protocol |
5564 | SDIO_x64_R773.exe | Misc activity | INFO [ANY.RUN] P2P BitTorrent Protocol |
5564 | SDIO_x64_R773.exe | Misc activity | INFO [ANY.RUN] P2P BitTorrent Protocol |
5564 | SDIO_x64_R773.exe | Misc activity | INFO [ANY.RUN] P2P BitTorrent Protocol |