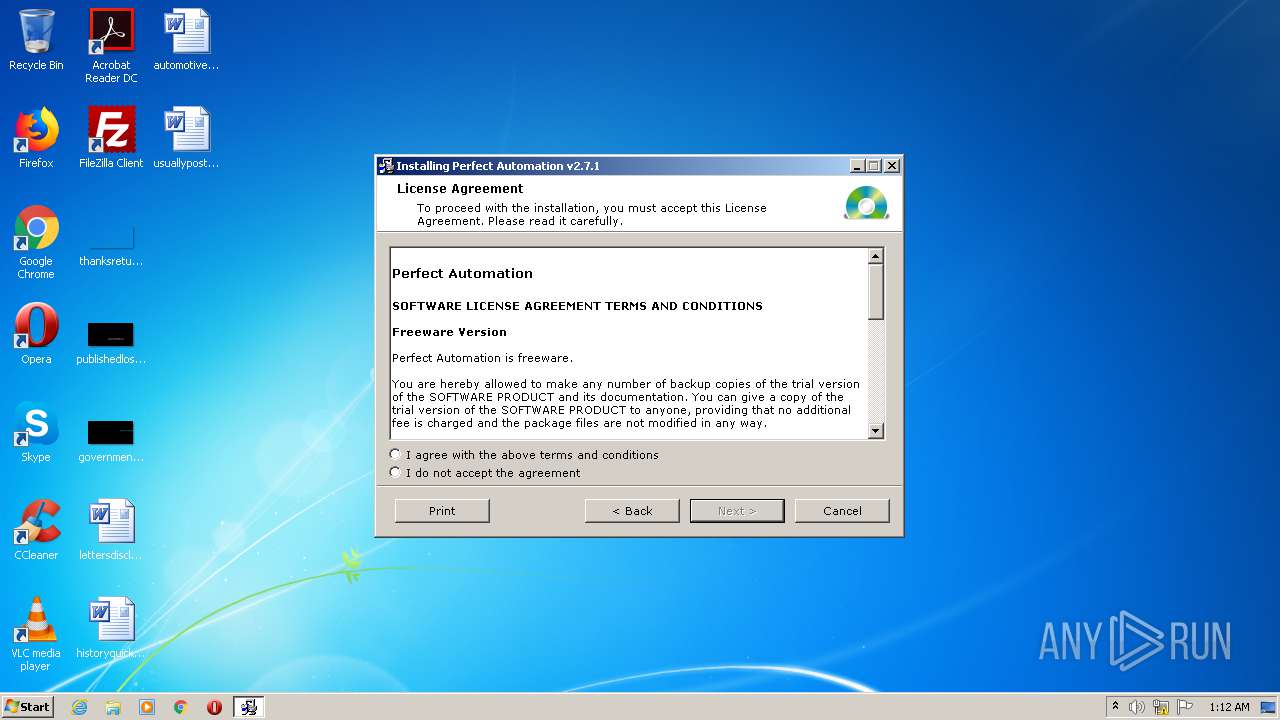
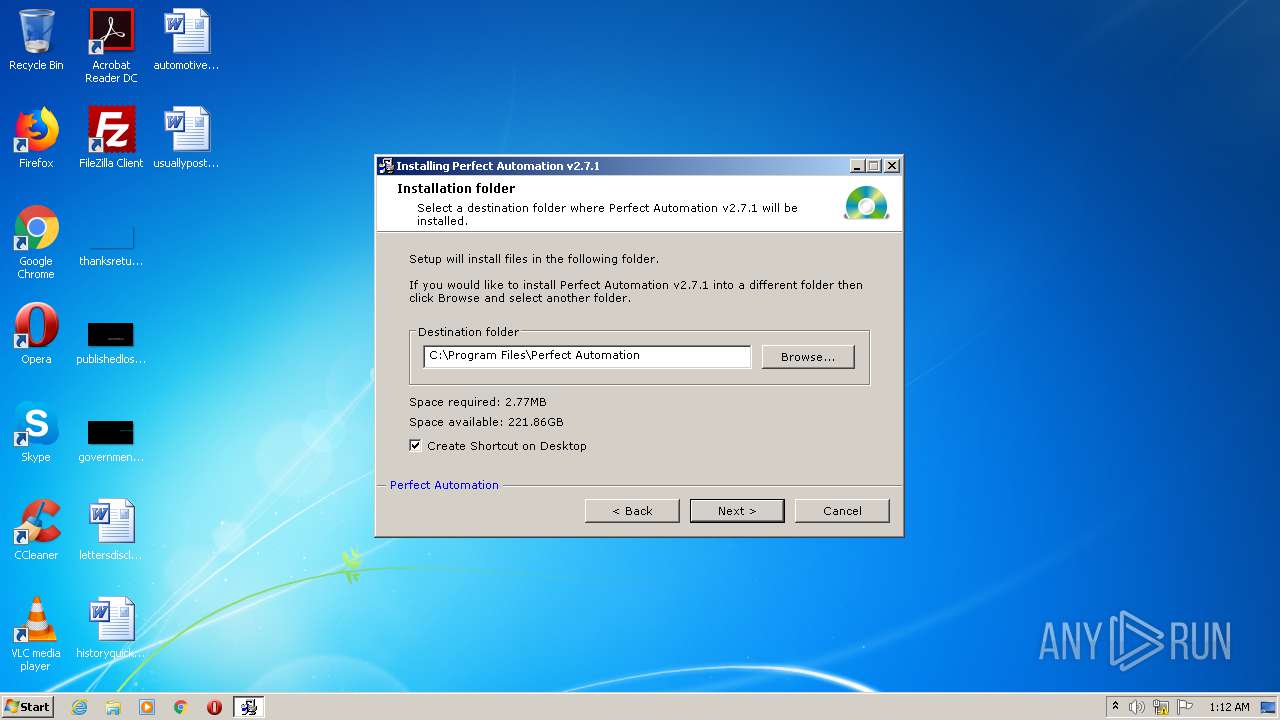
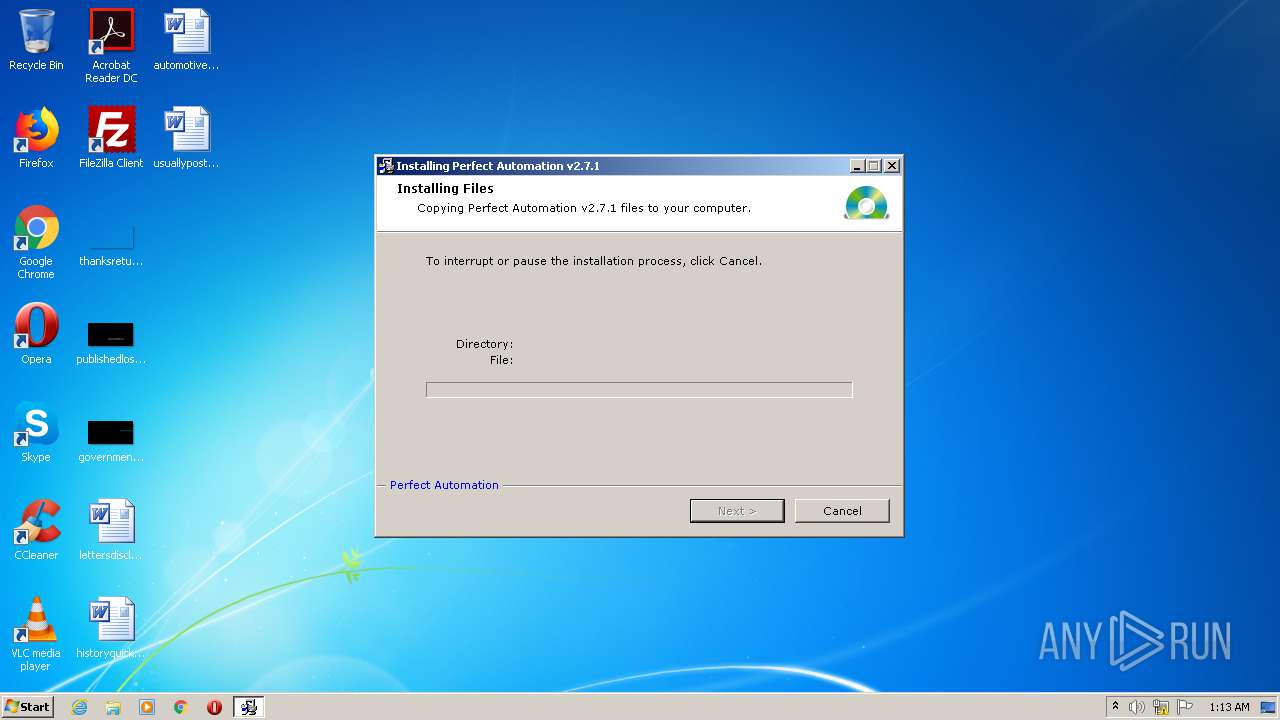
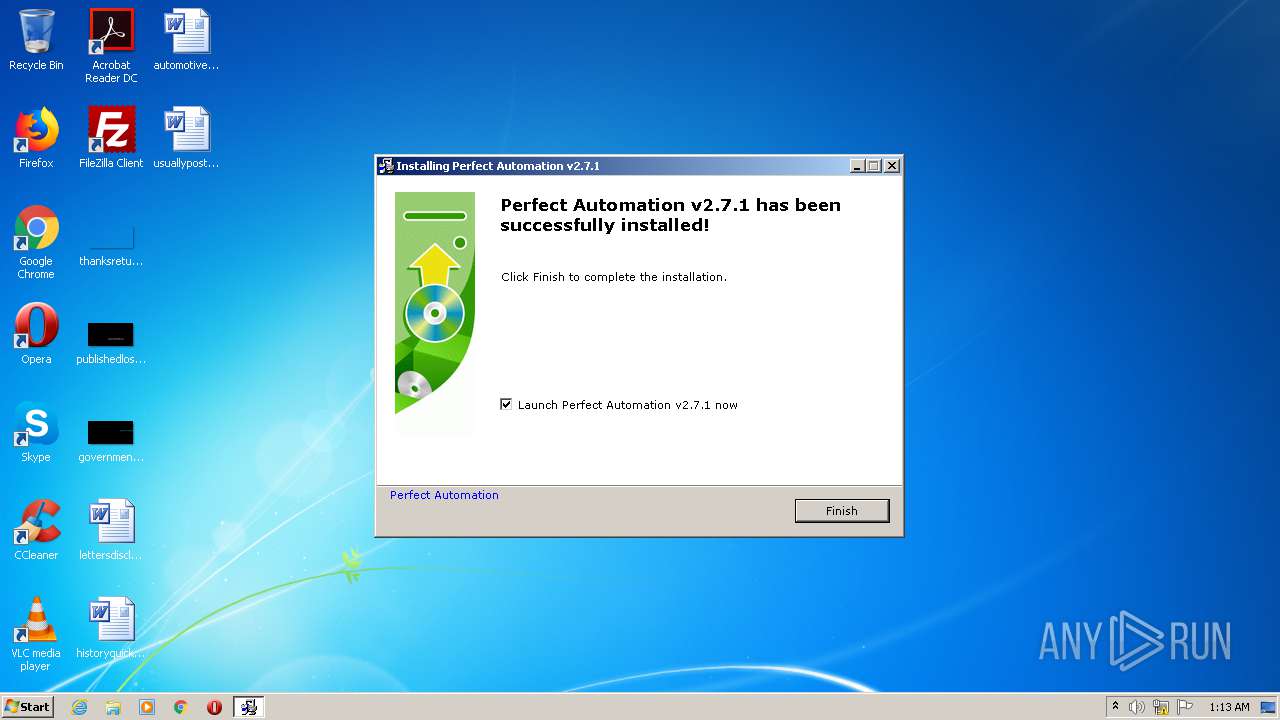
| File name: | pautomation-setup.exe |
| Full analysis: | https://app.any.run/tasks/eff15a4c-6028-48d2-99a6-f255cb81959e |
| Verdict: | Malicious activity |
| Analysis date: | November 30, 2020, 01:12:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | C452D47FBBE0DF86F30908B32842539D |
| SHA1: | FD56CE24A09E2F41584872808538E8A579D2306A |
| SHA256: | B3F5752541186BAE8A929DAFD06F95DE7E006A064CA411DD135B4047A018D5EB |
| SSDEEP: | 24576:lKS859qT1kVYUxEvuUt5WN7q5O0w5gkwC0aoQpsosbrID:4X59YWhEvdyxBfrpso+o |
MALICIOUS
Drops executable file immediately after starts
- pautomation-setup.exe (PID: 3232)
Loads dropped or rewritten executable
- pautomation-setup.exe (PID: 3232)
Application was dropped or rewritten from another process
- pautomation.exe (PID: 2648)
SUSPICIOUS
Drops a file with too old compile date
- pautomation-setup.exe (PID: 3232)
Creates a software uninstall entry
- pautomation-setup.exe (PID: 3232)
Creates files in the user directory
- pautomation-setup.exe (PID: 3232)
Modifies the open verb of a shell class
- pautomation.exe (PID: 2648)
Creates a directory in Program Files
- pautomation-setup.exe (PID: 3232)
Executable content was dropped or overwritten
- pautomation-setup.exe (PID: 3232)
Creates files in the program directory
- pautomation-setup.exe (PID: 3232)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (43.5) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (29.8) |
| .exe | | | Generic Win/DOS Executable (13.2) |
| .exe | | | DOS Executable Generic (13.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:01:30 10:32:26+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 4096 |
| InitializedDataSize: | 114688 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1d20 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.7.1.0 |
| ProductVersionNumber: | 2.7.1.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Pre-release |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unknown (01B5) |
| Comments: | - |
| CompanyName: | Gentee, Inc. |
| FileDescription: | pautomation Setup |
| FileVersion: | 2.7.1 |
| InternalName: | pautomation-setup |
| LegalCopyright: | Copyright © 2010 Gentee, Inc. |
| LegalTrademarks: | - |
| OriginalFileName: | pautomation-setup.exe |
| PrivateBuild: | - |
| ProductName: | pautomation |
| ProductVersion: | 2.7.1 |
| SpecialBuild: | - |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 30-Jan-2010 09:32:26 |
| Detected languages: |
|
| Comments: | - |
| CompanyName: | Gentee, Inc. |
| FileDescription: | pautomation Setup |
| FileVersion: | 2.7.1 |
| InternalName: | pautomation-setup |
| LegalCopyright: | Copyright © 2010 Gentee, Inc. |
| LegalTrademarks: | - |
| OriginalFilename: | pautomation-setup.exe |
| PrivateBuild: | - |
| ProductName: | pautomation |
| ProductVersion: | 2.7.1 |
| SpecialBuild: | - |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 30-Jan-2010 09:32:26 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00000EAC | 0x00001000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.942 |
.rdata | 0x00002000 | 0x00000488 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.74037 |
.data | 0x00003000 | 0x00000560 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 1.01054 |
.gentee | 0x00004000 | 0x0000F35F | 0x00010000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.86821 |
.rsrc | 0x00014000 | 0x00009F58 | 0x0000A000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.58478 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.99313 | 796 | Latin 1 / Western European | English - United States | RT_MANIFEST |
1000 | 2.23119 | 54 | Latin 1 / Western European | English - United States | RT_DIALOG |
IDD_DLGFIN2 | 2.59987 | 440 | Latin 1 / Western European | English - United States | RT_DIALOG |
IDD_DLGLANG | 2.60717 | 344 | Latin 1 / Western European | English - United States | RT_DIALOG |
IDD_DLGLIC2 | 2.88953 | 460 | Latin 1 / Western European | English - United States | RT_DIALOG |
IDD_DLGPATH | 2.68908 | 544 | Latin 1 / Western European | English - United States | RT_DIALOG |
IDD_DLGPROG | 2.71224 | 472 | Latin 1 / Western European | English - United States | RT_DIALOG |
IDD_DLGUCONF2 | 2.48111 | 312 | Latin 1 / Western European | English - United States | RT_DIALOG |
IDD_DLGUFIN2 | 2.56386 | 376 | Latin 1 / Western European | UNKNOWN | RT_DIALOG |
IDD_DLGUNDEL | 2.66424 | 408 | Latin 1 / Western European | UNKNOWN | RT_DIALOG |
Imports
KERNEL32.dll |
MSVCRT.dll |
USER32.dll |
Total processes
41
Monitored processes
3
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2540 | "C:\Users\admin\AppData\Local\Temp\pautomation-setup.exe" | C:\Users\admin\AppData\Local\Temp\pautomation-setup.exe | — | explorer.exe | |||||||||||
User: admin Company: Gentee, Inc. Integrity Level: MEDIUM Description: pautomation Setup Exit code: 3221226540 Version: 2.7.1 Modules
| |||||||||||||||
| 2648 | "C:\Program Files\Perfect Automation\pautomation.exe" | C:\Program Files\Perfect Automation\pautomation.exe | — | pautomation-setup.exe | |||||||||||
User: admin Company: Gentee, Inc. Integrity Level: HIGH Description: Perfect Automation software Exit code: 0 Version: 2.7.1 Modules
| |||||||||||||||
| 3232 | "C:\Users\admin\AppData\Local\Temp\pautomation-setup.exe" | C:\Users\admin\AppData\Local\Temp\pautomation-setup.exe | explorer.exe | ||||||||||||
User: admin Company: Gentee, Inc. Integrity Level: HIGH Description: pautomation Setup Exit code: 0 Version: 2.7.1 Modules
| |||||||||||||||
Total events
585
Read events
564
Write events
21
Delete events
0
Modification events
| (PID) Process: | (3232) pautomation-setup.exe | Key: | HKEY_CURRENT_USER\Software\Perfect Automation |
| Operation: | write | Name: | InstLang |
Value: English | |||
| (PID) Process: | (3232) pautomation-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Perfect Automation |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files\Perfect Automation\uninstall.exe | |||
| (PID) Process: | (3232) pautomation-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Perfect Automation |
| Operation: | write | Name: | DisplayName |
Value: Perfect Automation | |||
| (PID) Process: | (3232) pautomation-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Perfect Automation |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\Perfect Automation\pautomation.exe | |||
| (PID) Process: | (3232) pautomation-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Perfect Automation |
| Operation: | write | Name: | DisplayVersion |
Value: 2.7.1 | |||
| (PID) Process: | (3232) pautomation-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Perfect Automation |
| Operation: | write | Name: | Publisher |
Value: Gentee, Inc. | |||
| (PID) Process: | (3232) pautomation-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Perfect Automation |
| Operation: | write | Name: | URLInfoAbout |
Value: http://www.gentee.com/perfect-automation/ | |||
| (PID) Process: | (3232) pautomation-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Perfect Automation |
| Operation: | write | Name: | URLUpdateInfo |
Value: http://www.gentee.com/perfect-automation/ | |||
| (PID) Process: | (2648) pautomation.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\.pa |
| Operation: | write | Name: | (default) |
Value: pafile | |||
| (PID) Process: | (2648) pautomation.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\pafile\DefaultIcon |
| Operation: | write | Name: | (default) |
Value: C:\Program Files\Perfect Automation\script.exe | |||
Executable files
18
Suspicious files
1
Text files
616
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3232 | pautomation-setup.exe | C:\Program Files\Perfect Automation\uninstall.ini | text | |
MD5:— | SHA256:— | |||
| 3232 | pautomation-setup.exe | C:\Users\admin\AppData\Local\Temp\gentee9F\guig.dll | executable | |
MD5:8757CD8C68B85D668F15BEFC13251D5E | SHA256:96D1906EF8F1AC224830DA79BC9492AA21FFBACD4CAA4FB44CC64DEDF09047A2 | |||
| 3232 | pautomation-setup.exe | C:\Program Files\Perfect Automation\cmds\cmds\Application\shell.gt | text | |
MD5:CA8EE4F36C35EAF580F69C7507535840 | SHA256:E92E8395A4CD027AD8D586244F15C375809E5FDDBD1FE53C07718C83C8877621 | |||
| 3232 | pautomation-setup.exe | C:\Users\admin\AppData\Local\Temp\gentee9F\2install - 1.bmp | image | |
MD5:E168634D6C44995C14608F16C2E28693 | SHA256:06263008AB7AB756D1254CE744B389F71B0DFFB186EBFA8BB0D2603271E9C6DA | |||
| 3232 | pautomation-setup.exe | C:\Program Files\Perfect Automation\cmds\cmds\Application\redircon.gt | html | |
MD5:37E4374B81CFC7EC6B1ED6C2D5420562 | SHA256:1182DA977BE0D21D3554332CD75A40A447CDFB35AD9829C6F80726A02878F56E | |||
| 3232 | pautomation-setup.exe | C:\Program Files\Perfect Automation\uninstall.exe | executable | |
MD5:7301AE9D76F9675F5BFA32C50CBC9F97 | SHA256:1CDE0D4D05A7C90BB08E948CD9AFCEFDE5459A83C5F3A1E7A0932399E8C2019B | |||
| 3232 | pautomation-setup.exe | C:\Program Files\Perfect Automation\cmds\cmds\Application\desc | text | |
MD5:8EFFE3F8495AAFACC290A005CC8BCCE6 | SHA256:743033FA1D368AE7AE3D45A7D5924C0456D9CA165ED30C8189DB757A97AA8E57 | |||
| 3232 | pautomation-setup.exe | C:\Program Files\Perfect Automation\cmds\cmds\Application\ifapp.gt | text | |
MD5:4CFC1939E3D549372E6FE934CA0304CD | SHA256:E0AE81DC63AF3E90A06386CA4B6FA7B521600D95B44FF70CD9CB8447C29B01AF | |||
| 3232 | pautomation-setup.exe | C:\Program Files\Perfect Automation\cmds\cmds\Application\run.gt | text | |
MD5:8BA0C9C0BE98DD9F6FF5B58AC207178A | SHA256:DD972A181BC49F191251B0D5B3F12300A7D1613FC4354C69BBF7D95F9EA21C1D | |||
| 3232 | pautomation-setup.exe | C:\Users\admin\AppData\Local\Temp\genteert.dll | executable | |
MD5:F1D0C343E43B8D4F026BD4C59099812F | SHA256:AEDB5E44C3865767F8CD803342C21658575C7349F4EE26882D2052F16C5ADCF9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report