| URL: | img.sedoparking.com |
| Full analysis: | https://app.any.run/tasks/26f918d3-262e-4c8a-8e73-47c19142150b |
| Verdict: | Malicious activity |
| Analysis date: | February 23, 2024, 19:08:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | A1E6F17ABA54F616A7B4DE74F08B5AA5 |
| SHA1: | 1EA96B2EB874FD3BA0DEE2399AB99928BB48F7DE |
| SHA256: | B3E64371D297288EA49FD1CEDA7CFFCB9B5CB06505188B5D117795C3D2518671 |
| SSDEEP: | 3:JUBroK:i |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 3700)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
40
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 696 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3700 CREDAT:1381660 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3700 | "C:\Program Files\Internet Explorer\iexplore.exe" "img.sedoparking.com" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3952 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3700 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
25 371
Read events
25 131
Write events
126
Delete events
114
Modification events
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31090315 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31090315 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
9
Text files
31
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3700 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | der | |
MD5:C9E698F4208D83CB2FCF21C47316BBDD | SHA256:5B1CBD5CBDE0DCE1AE75216A75EE6ED44E4954787E7AEF8CF3E9DD1FB9664DAE | |||
| 3700 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3700 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\7JONOM7H.htm | html | |
MD5:B24BE00D3F6517268F2881F27BA864FD | SHA256:20BE38EB51F9A069F47295ED2063DC9E8016ACC34B54E4FA9B34152C207492DF | |||
| 3700 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:262EEA2599FBC333FB0A7939B53BEDEB | SHA256:C70650139BD9EAB3110AA29710AABC9C78FBBA0D013850BA03E77FF43009B028 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\80237EE4964FC9C409AAF55BF996A292_C0427F5F77D9B3A439FC620EDAAB6177 | der | |
MD5:34A0629E6AFD8FA0E2AA35F2B1294A4F | SHA256:179EB844F0926681106E8969ADFB0535DCD68D29273DF6987FCBD1E8A712D44C | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\K30WDPU6.txt | text | |
MD5:FE5CAC4977BB050C352E7ABB57B0DC31 | SHA256:DF3DDCEC7C9B4CD5977B5ACDF3CA15B81B6DF3B1EE338B2556BDDFF03F95A377 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\Y0EBXUEI.txt | text | |
MD5:63A9049C673241F3B1689B048ECA9971 | SHA256:19F017B914EAA149B58618C584284090895F3CAA13289DD178CA663D355029CF | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\DERNMAWK.txt | text | |
MD5:59A05AB77CA670A41D0D9565D93BF784 | SHA256:E6A8BC8D913A08C289534B7687BEF95752D2281AC42C51D222E2A5527FA2629C | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\80237EE4964FC9C409AAF55BF996A292_C0427F5F77D9B3A439FC620EDAAB6177 | binary | |
MD5:19DCC6157A979D16479DB88E1702254D | SHA256:6A85EE7C4A493DABEFB8ECEE2E75263DE6B2430412B61C75C021587FF4244F33 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
35
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
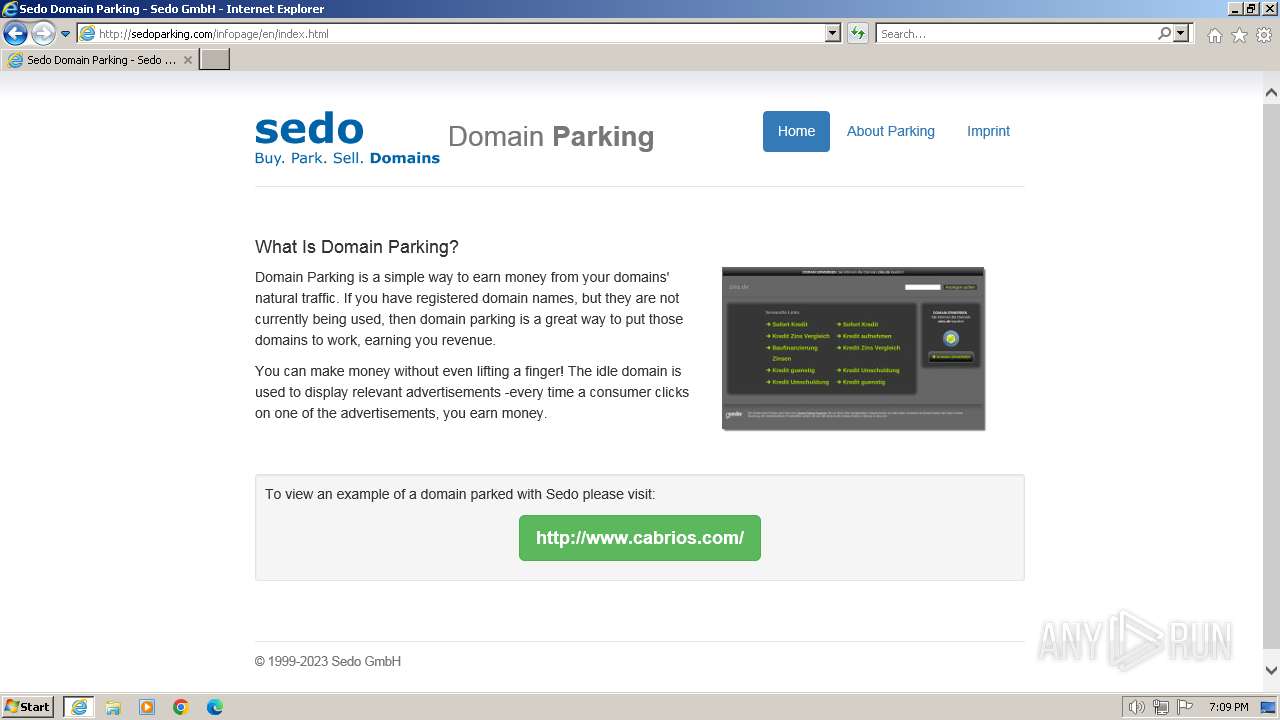
3952 | iexplore.exe | GET | 200 | 205.234.175.175:80 | http://img.sedoparking.com/infopage/css/bootstrap.min.css | unknown | text | 23.3 Kb | unknown |
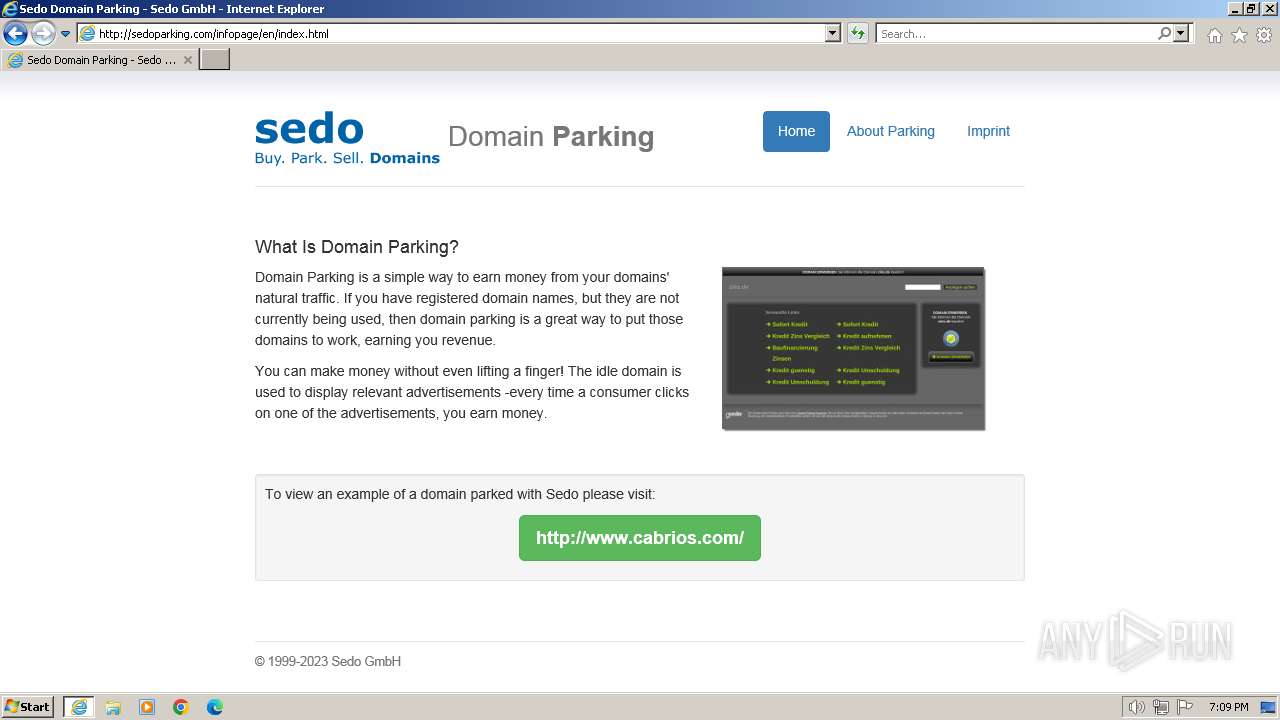
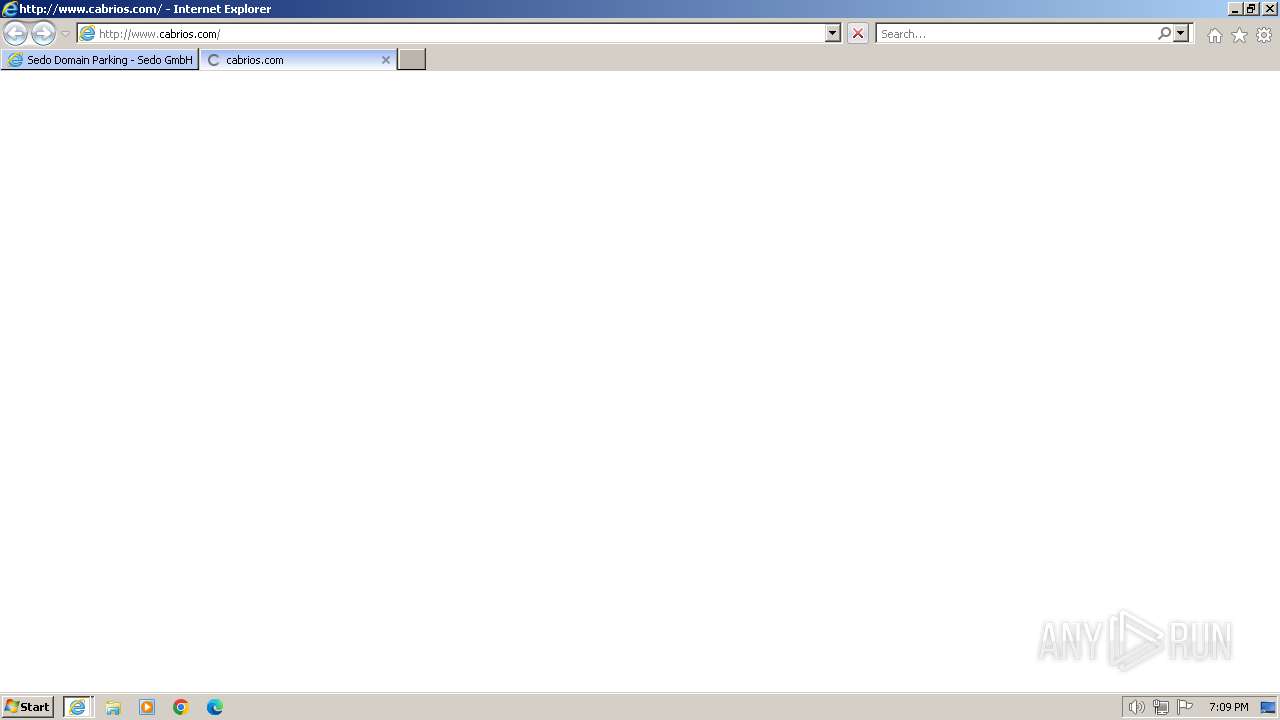
696 | iexplore.exe | GET | 200 | 91.195.240.13:80 | http://www.cabrios.com/ | unknown | compressed | 7.10 Kb | unknown |
3952 | iexplore.exe | GET | 200 | 205.234.175.175:80 | http://img.sedoparking.com/ | unknown | html | 181 b | unknown |
3700 | iexplore.exe | GET | 200 | 205.234.175.175:80 | http://img.sedoparking.com/favicon.ico | unknown | — | — | unknown |
3700 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?96c8eb5dfc595a04 | unknown | — | — | unknown |
3952 | iexplore.exe | GET | 200 | 205.234.175.175:80 | http://img.sedoparking.com/infopage/css/bootstrap_infopage.css | unknown | text | 637 b | unknown |
3700 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
3952 | iexplore.exe | GET | 200 | 205.234.175.175:80 | http://img.sedoparking.com/templates/index/img/sedologo.png | unknown | image | 4.63 Kb | unknown |
696 | iexplore.exe | GET | 200 | 216.58.212.164:80 | http://www.google.com/adsense/domains/caf.js | unknown | text | 51.1 Kb | unknown |
3952 | iexplore.exe | GET | 200 | 205.234.175.175:80 | http://img.sedoparking.com/templates/index/img/bg_wrap.jpg | unknown | image | 404 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3952 | iexplore.exe | 205.234.175.175:80 | img.sedoparking.com | CACHENETWORKS | US | unknown |
3700 | iexplore.exe | 205.234.175.175:80 | img.sedoparking.com | CACHENETWORKS | US | unknown |
3700 | iexplore.exe | 2.19.96.41:443 | www.bing.com | Akamai International B.V. | DE | unknown |
3700 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3700 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3952 | iexplore.exe | 13.107.5.80:443 | api.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3952 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
img.sedoparking.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
sedoparking.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
www.cabrios.com |
| malicious |
www.google.com |
| whitelisted |