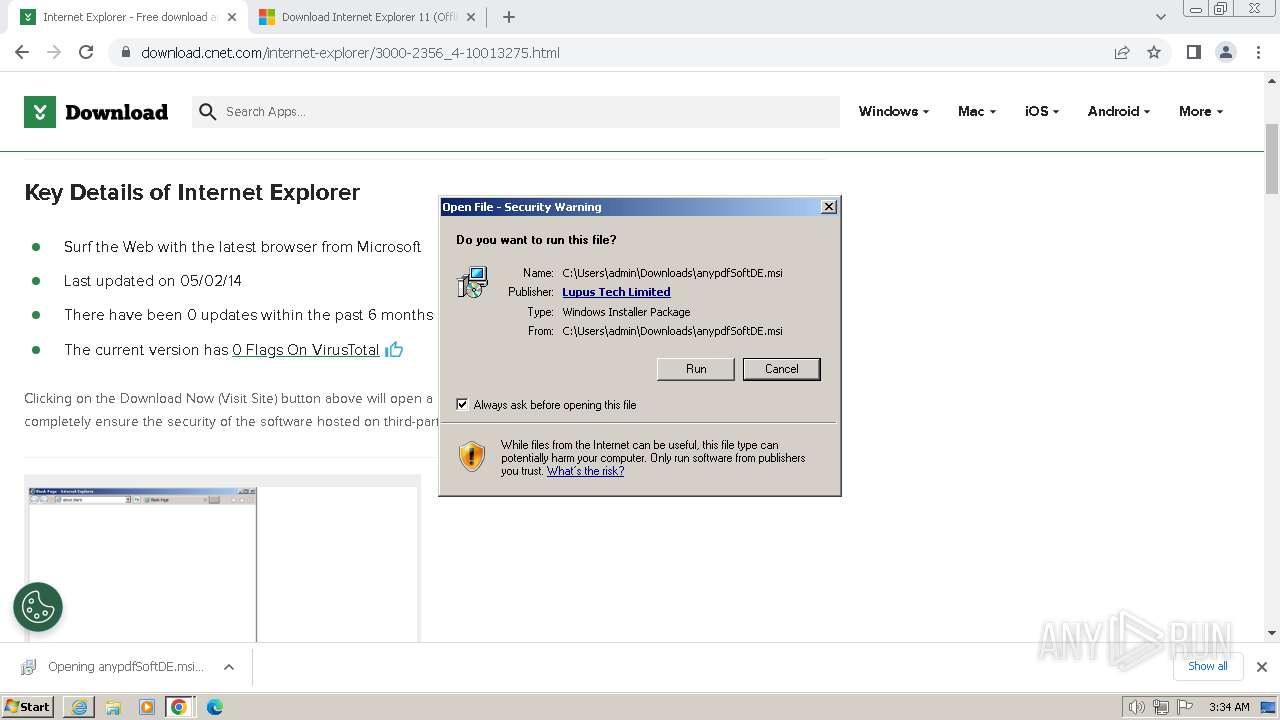
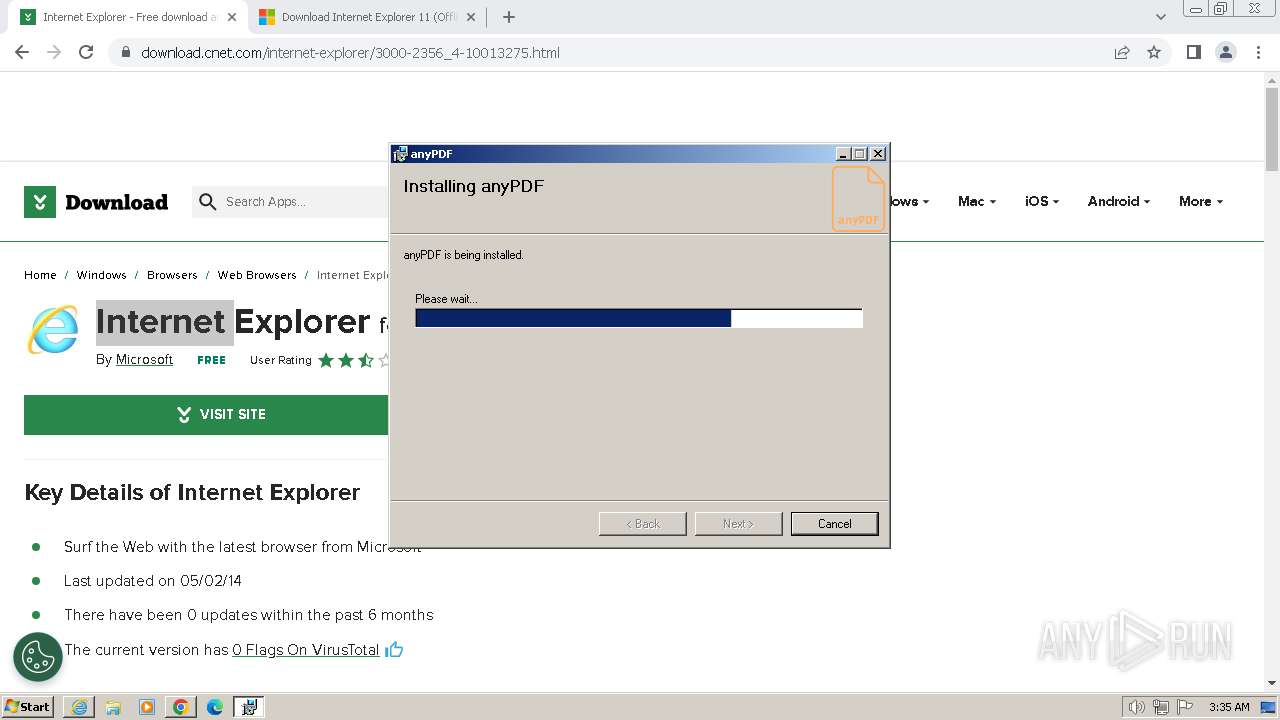
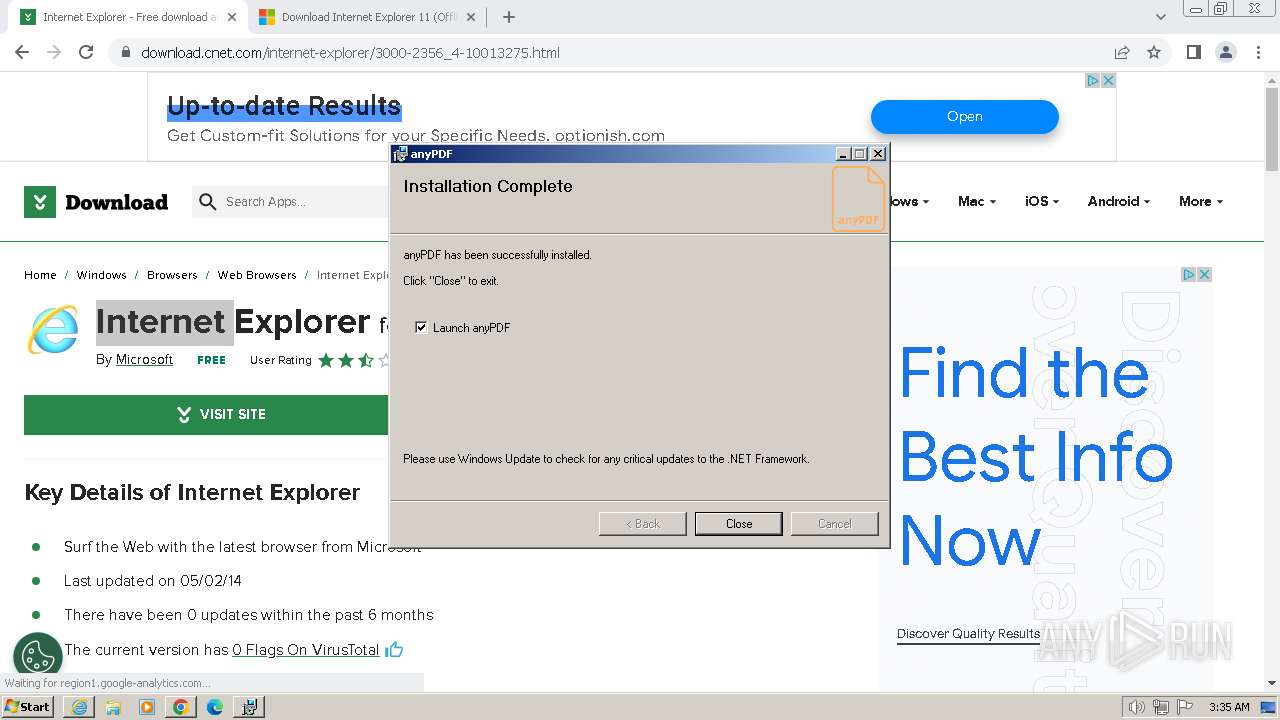
| URL: | https://download.cnet.com/internet-explorer/3000-2356_4-10013275.html |
| Full analysis: | https://app.any.run/tasks/201821c3-dc2a-4216-bcf6-6d4785af2e57 |
| Verdict: | Malicious activity |
| Analysis date: | April 26, 2024, 02:32:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 960C445F79BA5FC3A0E1871A11B91B9E |
| SHA1: | A523E2277CF823EE2533BC5606E5B28736578803 |
| SHA256: | B3DD258037804CA84AD8CE50B8D190F8A510FE537ECBD13EBC3B76B4EAE72E1A |
| SSDEEP: | 3:N8SElbKKS1VF0NHeNG:2SKmKKFu |
MALICIOUS
Changes the autorun value in the registry
- msiexec.exe (PID: 3948)
Drops the executable file immediately after the start
- msiexec.exe (PID: 1784)
Actions looks like stealing of personal data
- PdfOpenDriver.exe (PID: 3472)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 2120)
Checks Windows Trust Settings
- msiexec.exe (PID: 1784)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 1784)
Process drops legitimate windows executable
- msiexec.exe (PID: 1784)
- msiexec.exe (PID: 3604)
Changes default file association
- msiexec.exe (PID: 1784)
The process creates files with name similar to system file names
- msiexec.exe (PID: 1784)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 3948)
- PdfOpenDriver.exe (PID: 3472)
Reads the Internet Settings
- anyPDF.exe (PID: 2416)
- PdfOpenDriver.exe (PID: 3472)
- PdfOpenDriverUpdater.exe (PID: 3076)
Reads settings of System Certificates
- anyPDF.exe (PID: 2416)
- PdfOpenDriver.exe (PID: 3472)
- PdfOpenDriverUpdater.exe (PID: 3076)
INFO
The process uses the downloaded file
- chrome.exe (PID: 3492)
- chrome.exe (PID: 3852)
Reads the software policy settings
- msiexec.exe (PID: 3604)
- msiexec.exe (PID: 1784)
- msiexec.exe (PID: 3948)
- anyPDF.exe (PID: 2416)
- PdfOpenDriver.exe (PID: 3472)
- PdfOpenDriverUpdater.exe (PID: 3076)
Reads the computer name
- msiexec.exe (PID: 1784)
- msiexec.exe (PID: 2228)
- msiexec.exe (PID: 2664)
- anyPDF.exe (PID: 2416)
- PdfOpenDriver.exe (PID: 3472)
- PdfOpenDriverUpdater.exe (PID: 2452)
- PdfOpenDriverUpdater.exe (PID: 3076)
- msiexec.exe (PID: 3948)
Reads the machine GUID from the registry
- msiexec.exe (PID: 1784)
- msiexec.exe (PID: 2228)
- msiexec.exe (PID: 3948)
- msiexec.exe (PID: 2664)
- anyPDF.exe (PID: 2416)
- PdfOpenDriver.exe (PID: 3472)
- PdfOpenDriverUpdater.exe (PID: 3076)
- PdfOpenDriverUpdater.exe (PID: 2452)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 3604)
Application launched itself
- iexplore.exe (PID: 324)
- chrome.exe (PID: 3852)
- msiexec.exe (PID: 1784)
Manual execution by a user
- chrome.exe (PID: 3852)
Checks supported languages
- msiexec.exe (PID: 1784)
- msiexec.exe (PID: 2228)
- msiexec.exe (PID: 3948)
- msiexec.exe (PID: 2664)
- PdfOpenDriver.exe (PID: 3472)
- anyPDF.exe (PID: 2416)
- PdfOpenDriverUpdater.exe (PID: 3076)
- PdfOpenDriverUpdater.exe (PID: 2452)
Drops the executable file immediately after the start
- msiexec.exe (PID: 3604)
- chrome.exe (PID: 3036)
Executable content was dropped or overwritten
- msiexec.exe (PID: 3604)
- msiexec.exe (PID: 1784)
- chrome.exe (PID: 3036)
Create files in a temporary directory
- msiexec.exe (PID: 2228)
- msiexec.exe (PID: 1784)
- msiexec.exe (PID: 2664)
- anyPDF.exe (PID: 2416)
Creates files or folders in the user directory
- msiexec.exe (PID: 1784)
- msiexec.exe (PID: 3948)
- PdfOpenDriver.exe (PID: 3472)
- anyPDF.exe (PID: 2416)
- PdfOpenDriverUpdater.exe (PID: 3076)
Reads product name
- msiexec.exe (PID: 3948)
Reads Environment values
- msiexec.exe (PID: 3948)
- anyPDF.exe (PID: 2416)
- PdfOpenDriver.exe (PID: 3472)
- PdfOpenDriverUpdater.exe (PID: 3076)
Creates a software uninstall entry
- msiexec.exe (PID: 1784)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
87
Monitored processes
46
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 324 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://download.cnet.com/internet-explorer/3000-2356_4-10013275.html" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 896 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=4312 --field-trial-handle=1172,i,6599227830380497258,4457738788971030987,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 968 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=2260 --field-trial-handle=1172,i,6599227830380497258,4457738788971030987,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1232 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=30 --mojo-platform-channel-handle=1164 --field-trial-handle=1172,i,6599227830380497258,4457738788971030987,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1264 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=19 --mojo-platform-channel-handle=4448 --field-trial-handle=1172,i,6599227830380497258,4457738788971030987,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1344 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:324 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1624 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3408 --field-trial-handle=1172,i,6599227830380497258,4457738788971030987,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1740 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=13 --mojo-platform-channel-handle=3836 --field-trial-handle=1172,i,6599227830380497258,4457738788971030987,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1784 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2120 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
58 139
Read events
56 817
Write events
1 260
Delete events
62
Modification events
| (PID) Process: | (324) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (324) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (324) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31102849 | |||
| (PID) Process: | (324) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 251381400 | |||
| (PID) Process: | (324) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31102850 | |||
| (PID) Process: | (324) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (324) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (324) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (324) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (324) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
Executable files
249
Suspicious files
139
Text files
70
Unknown types
91
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 324 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | der | |
MD5:275217601D3297652E25068C68623E97 | SHA256:7CE195D67E8C9CF2EB293FBCEE620CAE499256BC4631876DE68E1D9E21BFA0E0 | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\RMU6SBOP.txt | text | |
MD5:7F77EACE96EFD76BA49A31C5AA0D0635 | SHA256:1CEB5D716B0DD7D103ED88CB54EBD2F4A35EFC108DFEE1A07B4D59B9675398E4 | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\ver5972.tmp | xml | |
MD5:CBD0581678FA40F0EDCBC7C59E0CAD10 | SHA256:159BD4343F344A08F6AF3B716B6FA679859C1BD1D7030D26FF5EF0255B86E1D9 | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | der | |
MD5:2BA153A709E3BFFA0657364C3753240C | SHA256:380C53B1FB1A72BFD4115352886D7D8BD129B17A4216776685832211E8BA1066 | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\80237EE4964FC9C409AAF55BF996A292_C5130A0BDC8C859A2757D77746C10868 | binary | |
MD5:6177F46A15B1321E316A78621F178238 | SHA256:01129B6F7EE90BBA7248155F659306126BFFD4A18974544455B619DCAA57CBAA | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | binary | |
MD5:530AB61CA18D6E4061987FCF9E9F055B | SHA256:D45E86607CF45EE06F9E6C10D468782FD12F6C13B9183DC85645BC86B54A48F0 | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\versionlist.xml | xml | |
MD5:CBD0581678FA40F0EDCBC7C59E0CAD10 | SHA256:159BD4343F344A08F6AF3B716B6FA679859C1BD1D7030D26FF5EF0255B86E1D9 | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\urlblockindex[1].bin | binary | |
MD5:FA518E3DFAE8CA3A0E495460FD60C791 | SHA256:775853600060162C4B4E5F883F9FD5A278E61C471B3EE1826396B6D129499AA7 | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:4DA829D987378C6A19900048A07A2925 | SHA256:82D7FDD36C2601EE2D3CD8487508F2B84E2DCAD4F2EBFF52ECF05545DE9D5B9E | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\80237EE4964FC9C409AAF55BF996A292_C5130A0BDC8C859A2757D77746C10868 | der | |
MD5:93D158A17AB8099F4A7DD2F5501B9306 | SHA256:34DCF43EBFB89AA006CDBDC5E4231E16949A44B2719E7BFE51077CCD68913504 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
136
DNS requests
208
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
324 | iexplore.exe | GET | 304 | 2.19.117.138:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a594c9a2210a21a8 | unknown | — | — | unknown |
324 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | — | — | unknown |
324 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
324 | iexplore.exe | GET | 304 | 2.19.117.138:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ea3c55793538016f | unknown | — | — | unknown |
1080 | svchost.exe | GET | 200 | 2.19.117.146:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?19f07cd4ab637647 | unknown | — | — | unknown |
324 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | unknown | — | — | unknown |
856 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | — | — | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | — | — | unknown |
856 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/h36ko3tmuyiyyv3qwuhlxjh4iy_8704/hfnkpimlhhgieaddgfemjhofmfblmnib_8704_all_acslna2buwd5r7wyfqsreg5onmaq.crx3 | unknown | — | — | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/h36ko3tmuyiyyv3qwuhlxjh4iy_8704/hfnkpimlhhgieaddgfemjhofmfblmnib_8704_all_acslna2buwd5r7wyfqsreg5onmaq.crx3 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1344 | iexplore.exe | 151.101.193.91:443 | download.cnet.com | FASTLY | US | unknown |
324 | iexplore.exe | 92.123.128.161:443 | www.bing.com | Akamai International B.V. | GB | unknown |
324 | iexplore.exe | 2.19.117.138:80 | ctldl.windowsupdate.com | Akamai International B.V. | GB | unknown |
324 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
324 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | EDGECAST | US | whitelisted |
1080 | svchost.exe | 2.19.117.146:80 | ctldl.windowsupdate.com | Akamai International B.V. | GB | unknown |
324 | iexplore.exe | 204.79.197.200:443 | ieonline.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
download.cnet.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.msn.com |
| whitelisted |
Threats
Process | Message |
|---|---|
anyPDF.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files\anyPDF\x86\SQLite.Interop.dll"...
|
PdfOpenDriver.exe | Verify completed in 15.625 milliseconds, total of 1 times in 15.625 milliseconds.
|
PdfOpenDriver.exe | Native library pre-loader is trying to load native SQLite library "C:\Users\admin\AppData\Local\PdfOpenDriver\x86\SQLite.Interop.dll"...
|