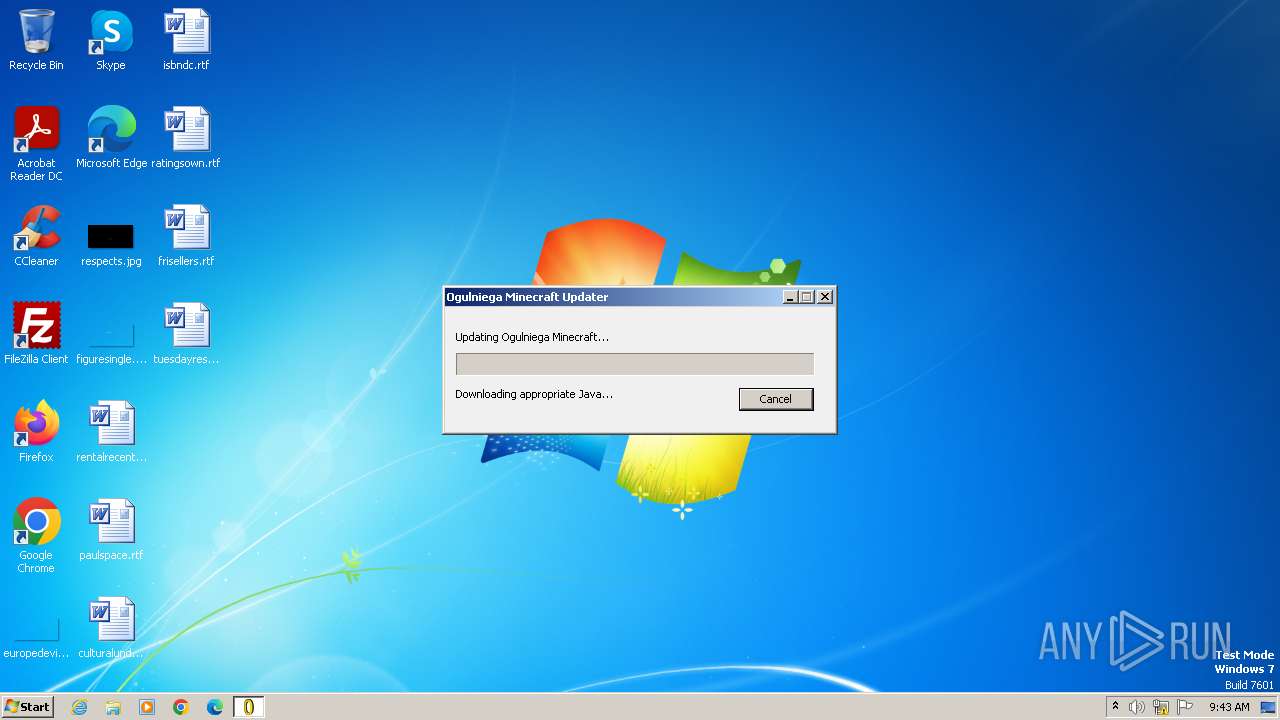
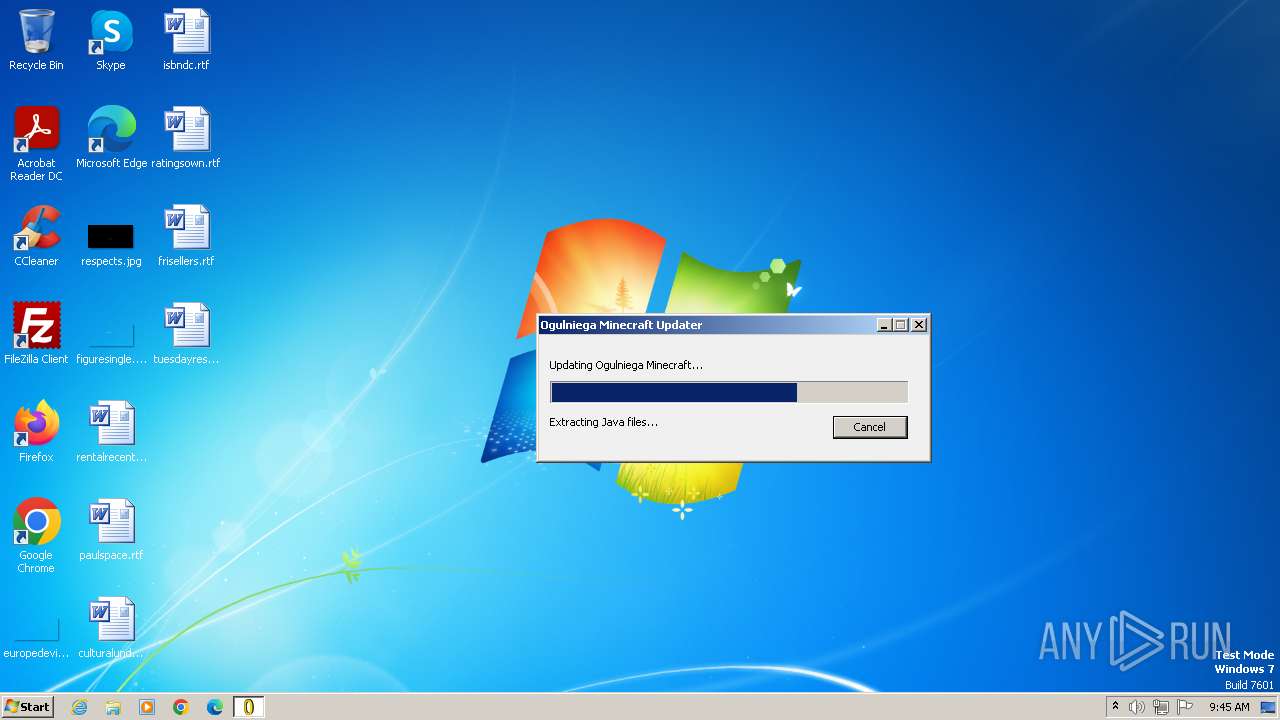
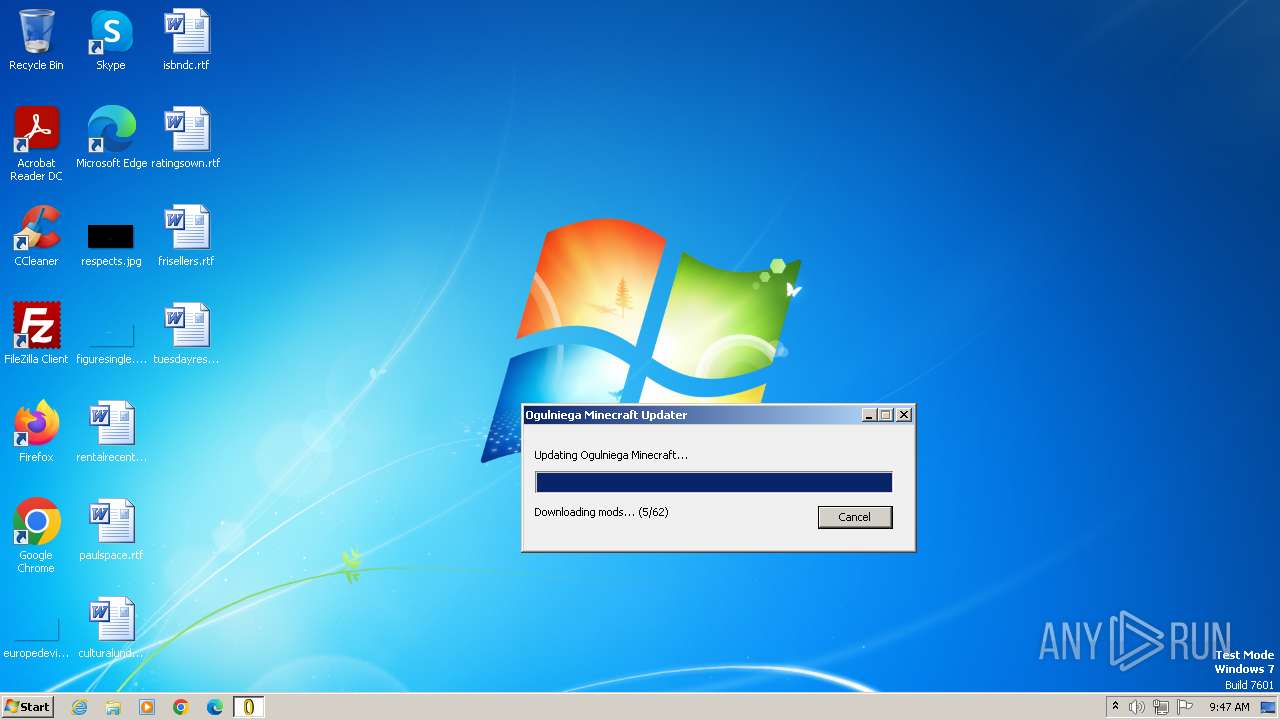
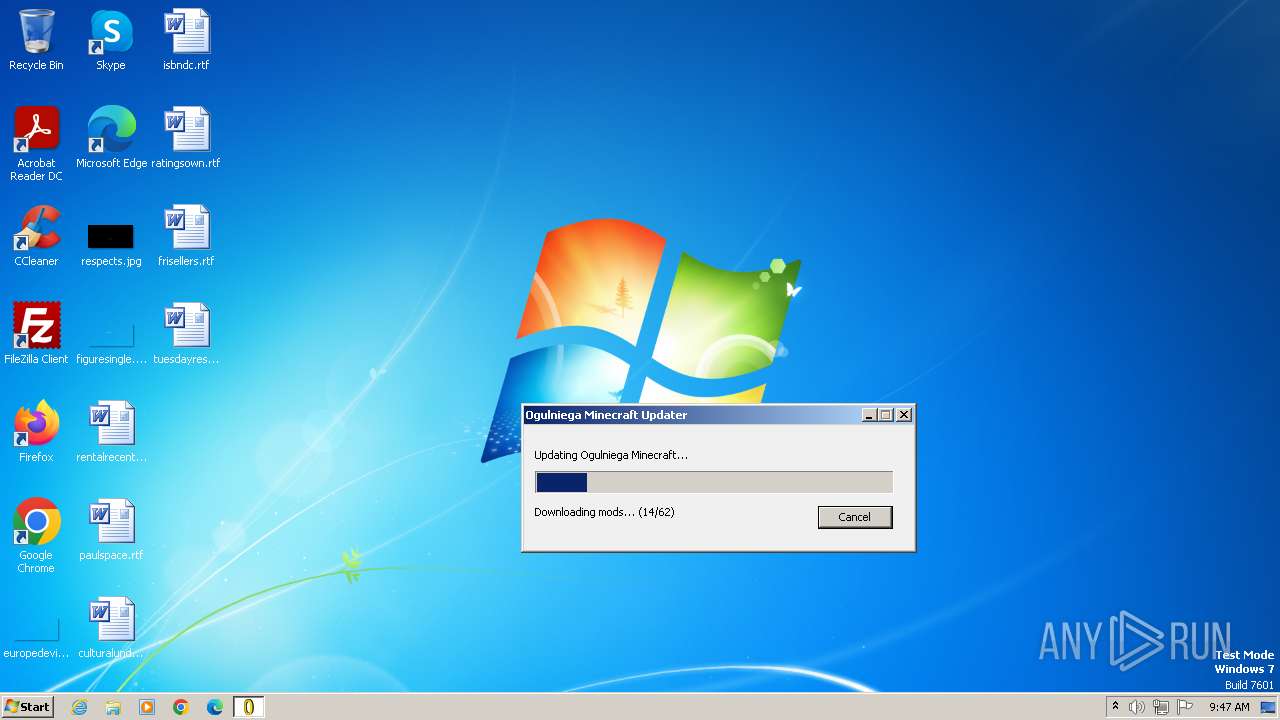
| File name: | Ogulniega Minecraft.exe |
| Full analysis: | https://app.any.run/tasks/595e325c-bbb6-49f0-b2da-0f95e582f7b5 |
| Verdict: | Malicious activity |
| Analysis date: | December 04, 2023, 09:43:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 32144D2122D8E1EBF3739B69E34B8B3A |
| SHA1: | 3803F34A50842A26F8D13C24A96F08E59BDDC5B9 |
| SHA256: | B3DBA0411BEB9AA9BE95E84F8B7B5CE0E6892090F3B5480B32D765C818F02462 |
| SSDEEP: | 12288:DQwX/QYcXhLz9i0C6hytlTIooHrZuk9QhOWjad0wltX64FSSYYYYY8ccc000b50E:D9X/QYcX1zbilbFwltX64cmS770 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts CMD.EXE for commands execution
- Ogulniega Minecraft.exe (PID: 564)
Reads security settings of Internet Explorer
- Ogulniega Minecraft.exe (PID: 564)
Checks Windows Trust Settings
- Ogulniega Minecraft.exe (PID: 564)
Reads the Internet Settings
- Ogulniega Minecraft.exe (PID: 564)
- powershell.exe (PID: 3288)
The process hides Powershell's copyright startup banner
- Ogulniega Minecraft.exe (PID: 564)
Reads settings of System Certificates
- Ogulniega Minecraft.exe (PID: 564)
Base64-obfuscated command line is found
- Ogulniega Minecraft.exe (PID: 564)
Starts POWERSHELL.EXE for commands execution
- Ogulniega Minecraft.exe (PID: 564)
The process bypasses the loading of PowerShell profile settings
- Ogulniega Minecraft.exe (PID: 564)
Powershell version downgrade attack
- powershell.exe (PID: 3924)
- powershell.exe (PID: 3388)
- powershell.exe (PID: 3288)
Process requests binary or script from the Internet
- Ogulniega Minecraft.exe (PID: 564)
INFO
Checks supported languages
- Ogulniega Minecraft.exe (PID: 564)
- wmpnscfg.exe (PID: 2620)
- wmpnscfg.exe (PID: 2868)
Reads the machine GUID from the registry
- Ogulniega Minecraft.exe (PID: 564)
Checks proxy server information
- Ogulniega Minecraft.exe (PID: 564)
Creates files or folders in the user directory
- Ogulniega Minecraft.exe (PID: 564)
Reads the computer name
- Ogulniega Minecraft.exe (PID: 564)
- wmpnscfg.exe (PID: 2620)
- wmpnscfg.exe (PID: 2868)
Manual execution by a user
- wmpnscfg.exe (PID: 2620)
- wmpnscfg.exe (PID: 2868)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:03 12:38:30+01:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.38 |
| CodeSize: | 295936 |
| InitializedDataSize: | 212992 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2772e |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.3 |
| ProductVersionNumber: | 0.0.0.3 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Ogulniega |
| FileVersion: | 3 |
| InternalName: | Ogulniega Minecraft |
| OriginalFileName: | Ogulniega Minecraft |
| ProductName: | Ogulniega Minecraft |
| ProductVersion: | 3 |
Total processes
47
Monitored processes
7
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 564 | "C:\Users\admin\AppData\Local\Temp\Ogulniega Minecraft.exe" | C:\Users\admin\AppData\Local\Temp\Ogulniega Minecraft.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1236 | "C:\Windows\system32\cmd.exe" /c mkdir "C:\Users\admin\AppData\Roaming\.ogulniega\" | C:\Windows\System32\cmd.exe | — | Ogulniega Minecraft.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2620 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2868 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3288 | "C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe" -nologo -noprofile "& {$shell = new-object -com shell.application; $zip = $shell.NameSpace('C:\Users\admin\AppData\Roaming\.ogulniega\profiles\stable\settings_temp.zip'); foreach($item in $zip.items()) { $shell.Namespace('C:\Users\admin\AppData\Roaming\.ogulniega\profiles\stable').copyhere($item, 4 + 16 + 256 + 512); }}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Ogulniega Minecraft.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3388 | "C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe" -nologo -noprofile "& {$shell = new-object -com shell.application; $zip = $shell.NameSpace('C:\Users\admin\AppData\Roaming\.ogulniega\minecraft\minecraft_temp.zip'); foreach($item in $zip.items()) { $shell.Namespace('C:\Users\admin\AppData\Roaming\.ogulniega\minecraft').copyhere($item, 4 + 16 + 256 + 512); }}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Ogulniega Minecraft.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3924 | "C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe" -nologo -noprofile "& {$shell = new-object -com shell.application; $zip = $shell.NameSpace('C:\Users\admin\AppData\Roaming\.ogulniega\java\java_temp.zip'); foreach($item in $zip.items()) { $shell.Namespace('C:\Users\admin\AppData\Roaming\.ogulniega\java').copyhere($item, 4 + 16 + 256 + 512); }}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Ogulniega Minecraft.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
11 799
Read events
11 604
Write events
195
Delete events
0
Modification events
| (PID) Process: | (564) Ogulniega Minecraft.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (564) Ogulniega Minecraft.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005A010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (564) Ogulniega Minecraft.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (564) Ogulniega Minecraft.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (564) Ogulniega Minecraft.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (564) Ogulniega Minecraft.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (564) Ogulniega Minecraft.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (564) Ogulniega Minecraft.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (564) Ogulniega Minecraft.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3924) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
9
Suspicious files
191
Text files
16
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 564 | Ogulniega Minecraft.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\OpenJDK17U-jdk_x86-32_windows_hotspot_17.0.8.1_1[1].zip | — | |
MD5:— | SHA256:— | |||
| 564 | Ogulniega Minecraft.exe | C:\Users\admin\AppData\Roaming\.ogulniega\java\java_temp.zip | — | |
MD5:— | SHA256:— | |||
| 564 | Ogulniega Minecraft.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\50CD3D75D026C82E2E718570BD6F44D0_D222662A57BAA60D2F5EA0D2CC7B2F1C | binary | |
MD5:CDB710516073766210DD560F176970FA | SHA256:4432182653A6CF57C70CD9794EFBB68C207CE6D7BC9DA18144266921B0F812E7 | |||
| 564 | Ogulniega Minecraft.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_ADE4E4D3A3BCBCA5C39C54D362D88565 | binary | |
MD5:B130B837461CB252860250DCA3C8E19F | SHA256:8109B3935ECBEBF50FBABB0AD18BF15AF3521E9AF84B01D952F80580342EA770 | |||
| 564 | Ogulniega Minecraft.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:97C86B600D773485D8793CA90D928F7D | SHA256:228C965B6DBCCD147B78783FC8A22FA789BC26A52FC3FAF18CD3615763D31BA0 | |||
| 564 | Ogulniega Minecraft.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_ADE4E4D3A3BCBCA5C39C54D362D88565 | binary | |
MD5:8D77C804C168824819607397E89F4906 | SHA256:223057A0027DFBC78C5B779805E9A4DB0B9D5D211DEA05DC06769D99CEFC7A0D | |||
| 564 | Ogulniega Minecraft.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | der | |
MD5:8202A1CD02E7D69597995CABBE881A12 | SHA256:58F381C3A0A0ACE6321DA22E40BD44A597BD98B9C9390AB9258426B5CF75A7A5 | |||
| 564 | Ogulniega Minecraft.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:CCD1A020D9FCD8758FB897BDFCF685A6 | SHA256:E5E7AD2C75A30C8DB5015D9A854E33108688DEA2CB3D695822B4E0D08DAC3FDB | |||
| 564 | Ogulniega Minecraft.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\launcher_stable[1].json | binary | |
MD5:5E1D84BACA646ED6A9AD28EB7B5674F9 | SHA256:5CFD9CC0FF57FD288EEF86DCFC96254EED8D480F01EE62E06BF3FFD43E3D242D | |||
| 564 | Ogulniega Minecraft.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\50CD3D75D026C82E2E718570BD6F44D0_D222662A57BAA60D2F5EA0D2CC7B2F1C | binary | |
MD5:8E6462FE2EE4DDE088C61997B6E2BF02 | SHA256:4B2BD821AB73A812929DAC21C9DEE5307DD6FBFE399AA782E3F749FEFEC4E4B6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
21
DNS requests
12
Threats
24
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1080 | svchost.exe | GET | 200 | 2.19.11.178:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?0e12557d322e1eeb | unknown | compressed | 65.2 Kb | unknown |
564 | Ogulniega Minecraft.exe | GET | 200 | 136.243.156.120:80 | http://cdn.ogulniega.ct8.pl/files/default_profile_stable.zip | unknown | compressed | 17.3 Kb | unknown |
564 | Ogulniega Minecraft.exe | GET | — | 136.243.156.120:80 | http://cdn.ogulniega.ct8.pl/files/quilt-loader-0.21.0-1.20.1.zip | unknown | — | — | unknown |
564 | Ogulniega Minecraft.exe | GET | 200 | 23.201.254.55:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
564 | Ogulniega Minecraft.exe | GET | 200 | 23.53.40.9:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6cc4ba5850752e35 | unknown | compressed | 4.66 Kb | unknown |
564 | Ogulniega Minecraft.exe | GET | 200 | 142.250.185.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
564 | Ogulniega Minecraft.exe | GET | 200 | 136.243.156.120:80 | http://cdn.ogulniega.ct8.pl/files/mods/Ogulniega-3+1.20.1.jar | unknown | compressed | 216 Kb | unknown |
564 | Ogulniega Minecraft.exe | GET | 200 | 136.243.156.120:80 | http://cdn.ogulniega.ct8.pl/files/mods/microdurability-0.3.6+1.19.4.jar | unknown | compressed | 26.1 Kb | unknown |
564 | Ogulniega Minecraft.exe | GET | 200 | 136.243.156.120:80 | http://cdn.ogulniega.ct8.pl/files/mods/perspektive-1.3.2.jar | unknown | compressed | 33.4 Kb | unknown |
564 | Ogulniega Minecraft.exe | GET | 200 | 136.243.156.120:80 | http://cdn.ogulniega.ct8.pl/files/mods/enhancedblockentities-0.9+1.20.jar | unknown | compressed | 479 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
564 | Ogulniega Minecraft.exe | 188.114.96.3:443 | ogulnie.ga | CLOUDFLARENET | NL | unknown |
564 | Ogulniega Minecraft.exe | 23.53.40.9:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
564 | Ogulniega Minecraft.exe | 142.250.185.131:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
564 | Ogulniega Minecraft.exe | 140.82.121.4:443 | github.com | GITHUB | US | unknown |
564 | Ogulniega Minecraft.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
564 | Ogulniega Minecraft.exe | 185.199.108.133:443 | objects.githubusercontent.com | FASTLY | US | unknown |
868 | svchost.exe | 23.35.228.137:80 | — | AKAMAI-AS | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
868 | svchost.exe | 184.30.20.134:80 | armmf.adobe.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ogulnie.ga |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
github.com |
| shared |
ocsp.digicert.com |
| whitelisted |
objects.githubusercontent.com |
| shared |
armmf.adobe.com |
| whitelisted |
cdn.ogulniega.ct8.pl |
| unknown |
cdn.modrinth.com |
| unknown |
x1.c.lencr.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET INFO DNS Query for Suspicious .ga Domain |
564 | Ogulniega Minecraft.exe | Misc activity | ET INFO Suspicious Domain (*.ga) in TLS SNI |
1080 | svchost.exe | Misc activity | ET INFO DNS Query to a Free Hosting Domain Domain (*.ct8 pl) |
564 | Ogulniega Minecraft.exe | Misc activity | ET INFO HTTP Request to Free Hosting Domain (*.ct8 .pl) |
564 | Ogulniega Minecraft.exe | Misc activity | ET INFO HTTP Request to Free Hosting Domain (*.ct8 .pl) |
564 | Ogulniega Minecraft.exe | Attempted Administrator Privilege Gain | AV EXPLOIT Potential ZIP file exploiting CVE-2023-36413 |
564 | Ogulniega Minecraft.exe | Misc activity | ET INFO HTTP Request to Free Hosting Domain (*.ct8 .pl) |
564 | Ogulniega Minecraft.exe | Attempted Administrator Privilege Gain | AV EXPLOIT Potential ZIP file exploiting CVE-2023-36413 |
564 | Ogulniega Minecraft.exe | Misc activity | ET INFO HTTP Request to Free Hosting Domain (*.ct8 .pl) |
564 | Ogulniega Minecraft.exe | Attempted Administrator Privilege Gain | AV EXPLOIT Potential ZIP file exploiting CVE-2023-36413 |
7 ETPRO signatures available at the full report