| File name: | Black Hat Rat.zip |
| Full analysis: | https://app.any.run/tasks/db014507-581b-488f-aa62-20b9046a8dc3 |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2023, 06:44:52 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 46C0A52D5D153B62E9DB80D3DF4AB6D3 |
| SHA1: | DC90337CF116964E810C71FCF6F5844A4AC2ABE6 |
| SHA256: | B3D7AC1B309A709307B5EBAD4CB4108879B2EDB0862FF3B5E7BE7A9957BD8392 |
| SSDEEP: | 24576:OxqBExSGxoHItOEPfDnFlZCTBPOYADQBhiPayt5PFAU7L95yLkryP1nmkp/zZHCK:Obt3jPBK9H2QBhiltDZ4INkVIK |
MALICIOUS
Application was dropped or rewritten from another process
- Black Hat Rat.exe (PID: 3468)
Bypass execution policy to execute commands
- powershell.exe (PID: 4052)
Starts Visual C# compiler
- powershell.exe (PID: 4052)
SUSPICIOUS
Reads the Internet Settings
- powershell.exe (PID: 4052)
Uses .NET C# to load dll
- powershell.exe (PID: 4052)
Executable content was dropped or overwritten
- csc.exe (PID: 3572)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 4052)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3096)
Checks supported languages
- Black Hat Rat.exe (PID: 3468)
- cvtres.exe (PID: 744)
- csc.exe (PID: 3572)
Reads Environment values
- Black Hat Rat.exe (PID: 3468)
Reads the computer name
- Black Hat Rat.exe (PID: 3468)
Manual execution by a user
- powershell.exe (PID: 4052)
- Black Hat Rat.exe (PID: 3468)
Reads the machine GUID from the registry
- Black Hat Rat.exe (PID: 3468)
- csc.exe (PID: 3572)
- cvtres.exe (PID: 744)
The process checks LSA protection
- Black Hat Rat.exe (PID: 3468)
- csc.exe (PID: 3572)
- cvtres.exe (PID: 744)
Create files in a temporary directory
- csc.exe (PID: 3572)
- cvtres.exe (PID: 744)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | Black Hat Rat.exe |
|---|---|
| ZipUncompressedSize: | 2083328 |
| ZipCompressedSize: | 817739 |
| ZipCRC: | 0xd28ceb7e |
| ZipModifyDate: | 2020:07:23 10:27:06 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
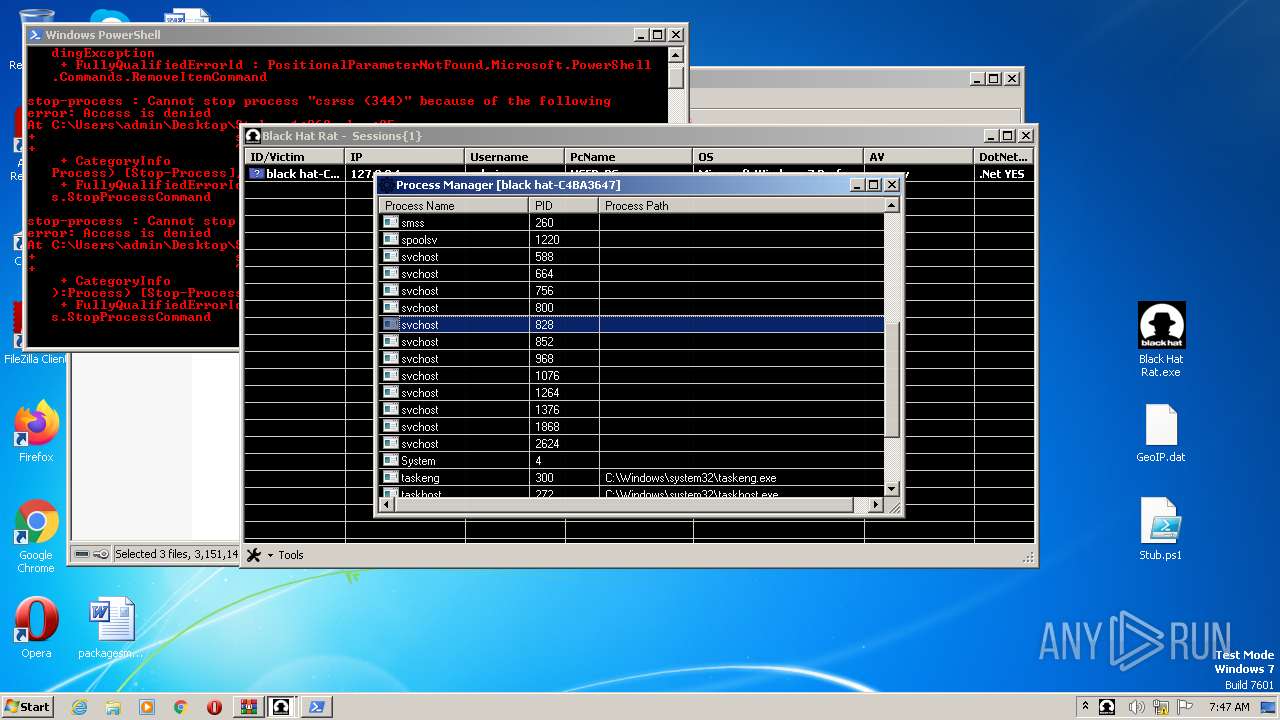
Total processes
47
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 744 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES7056.tmp" "c:\Users\admin\AppData\Local\Temp\CSCC87F12261B8A4470A266D1332BB62ED1.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 12.00.51209.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
| 3096 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Black Hat Rat.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
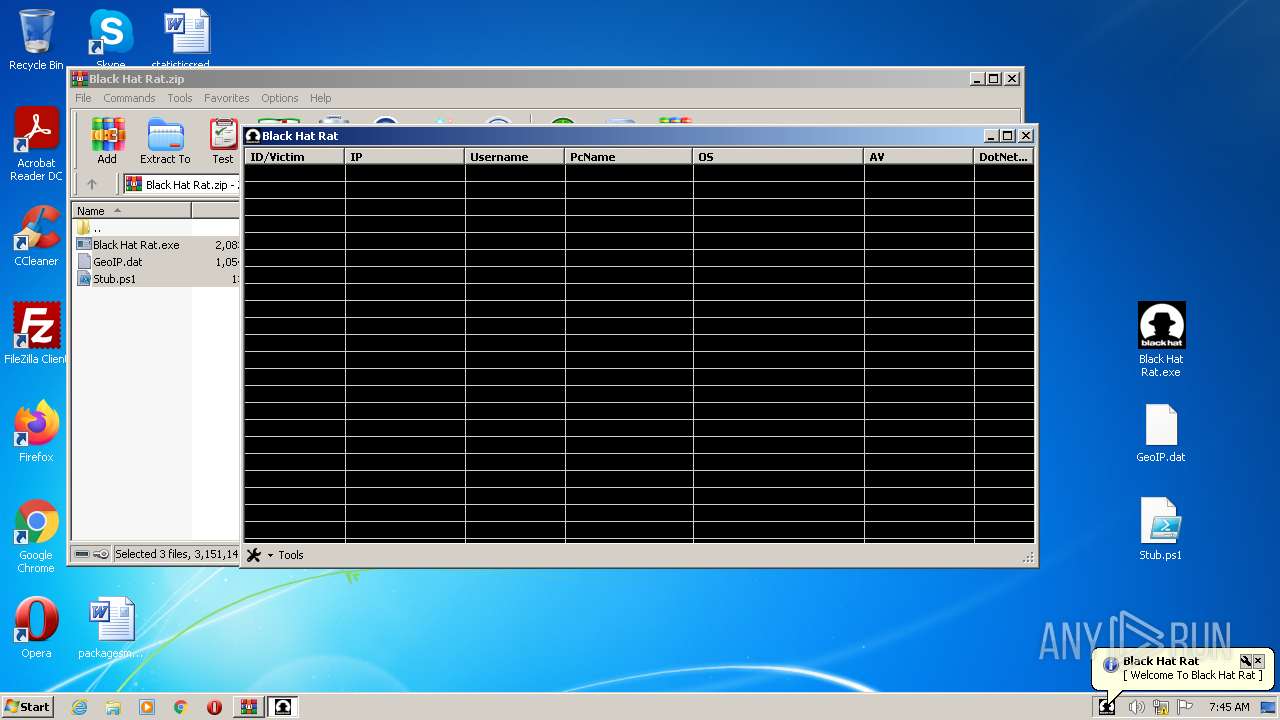
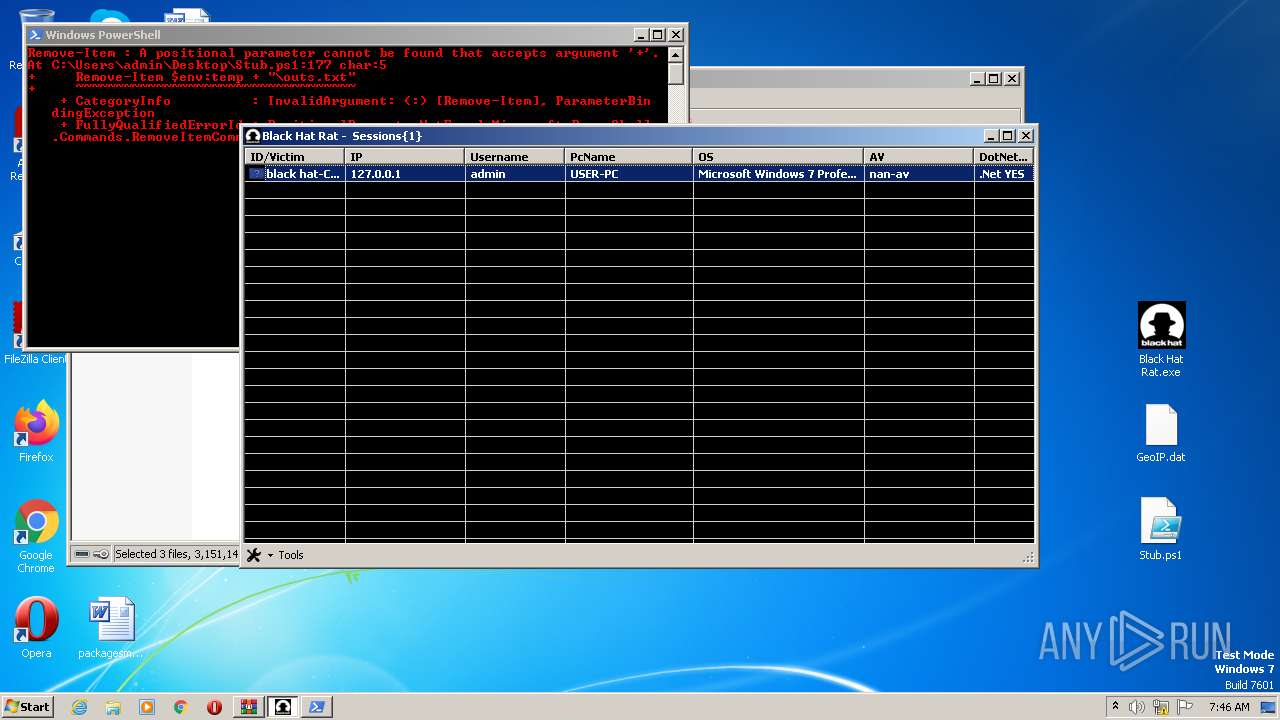
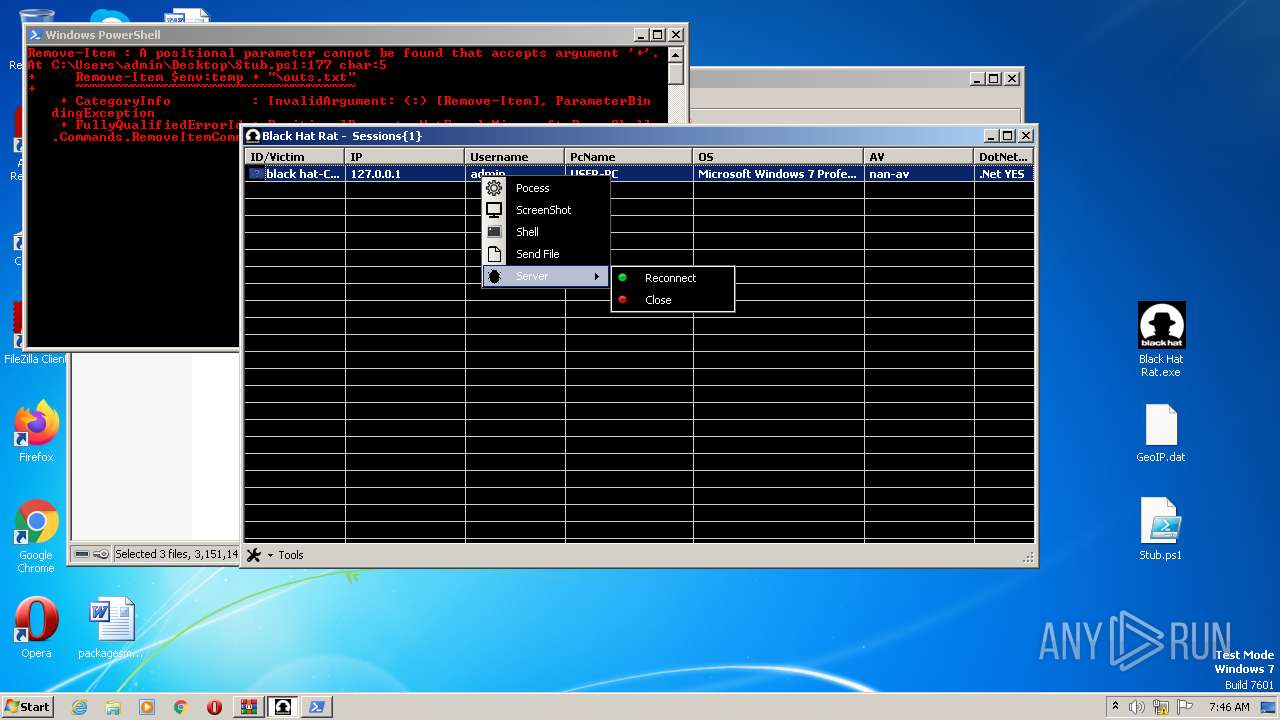
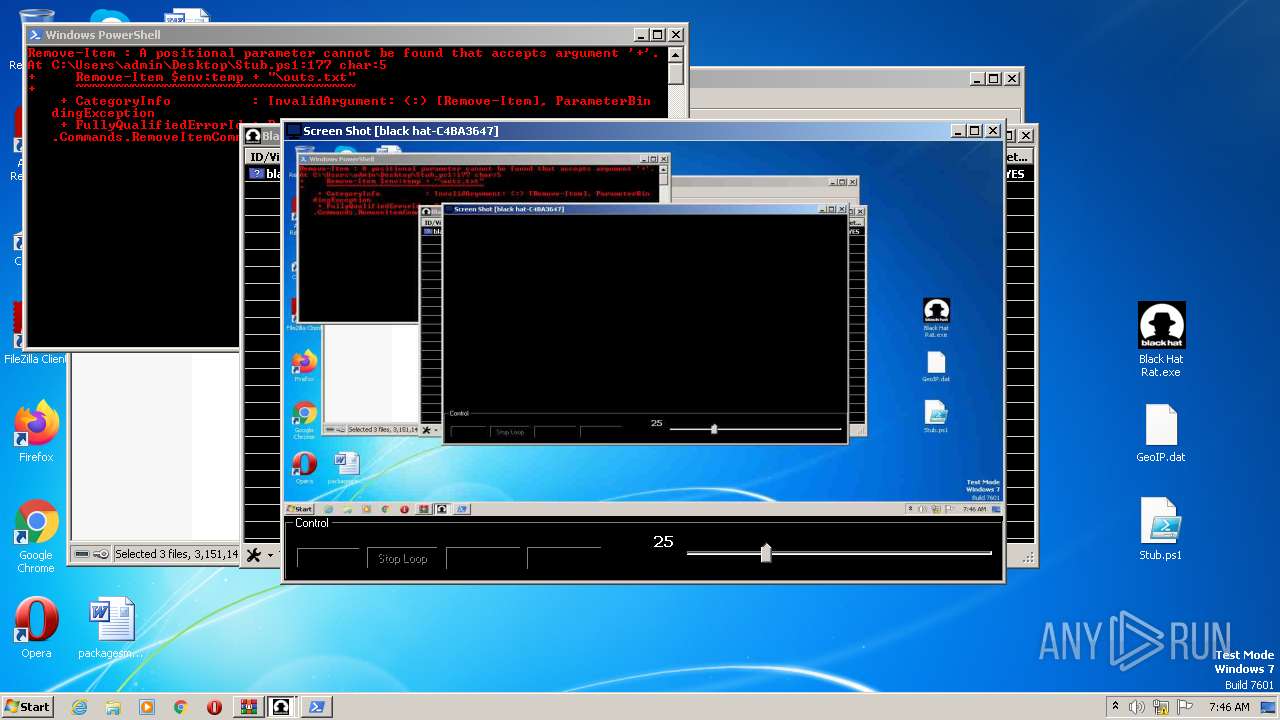
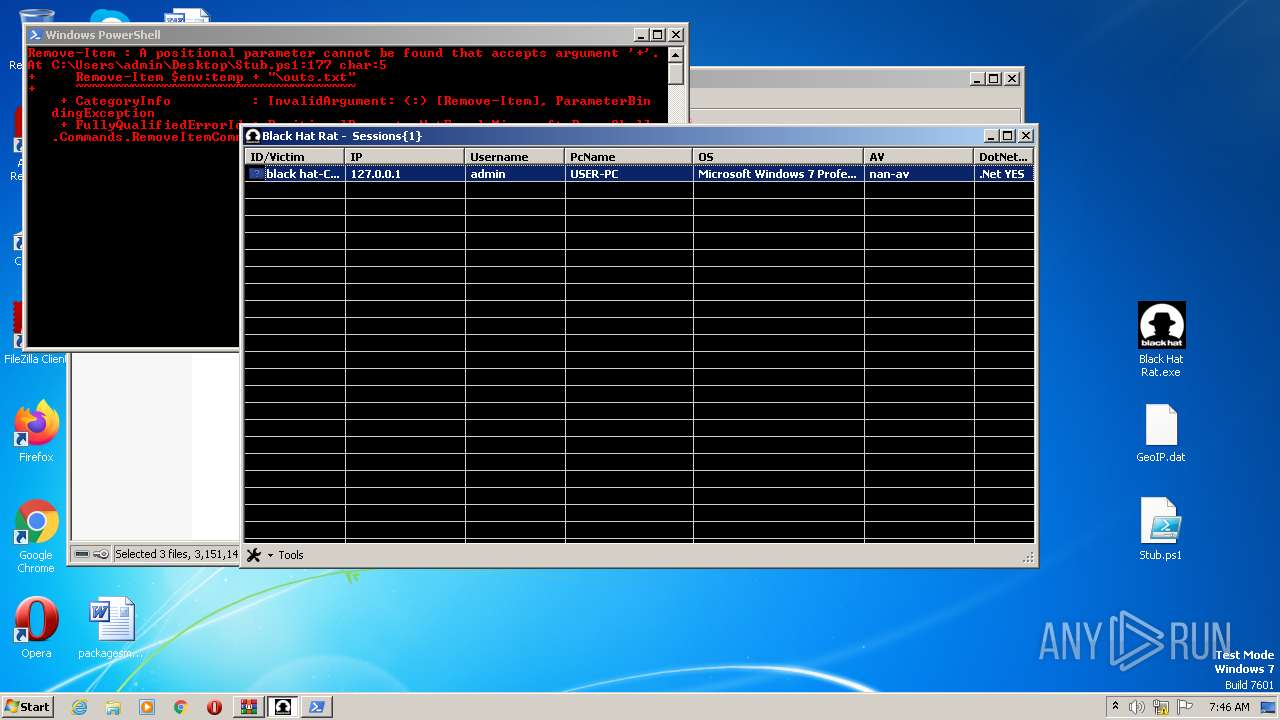
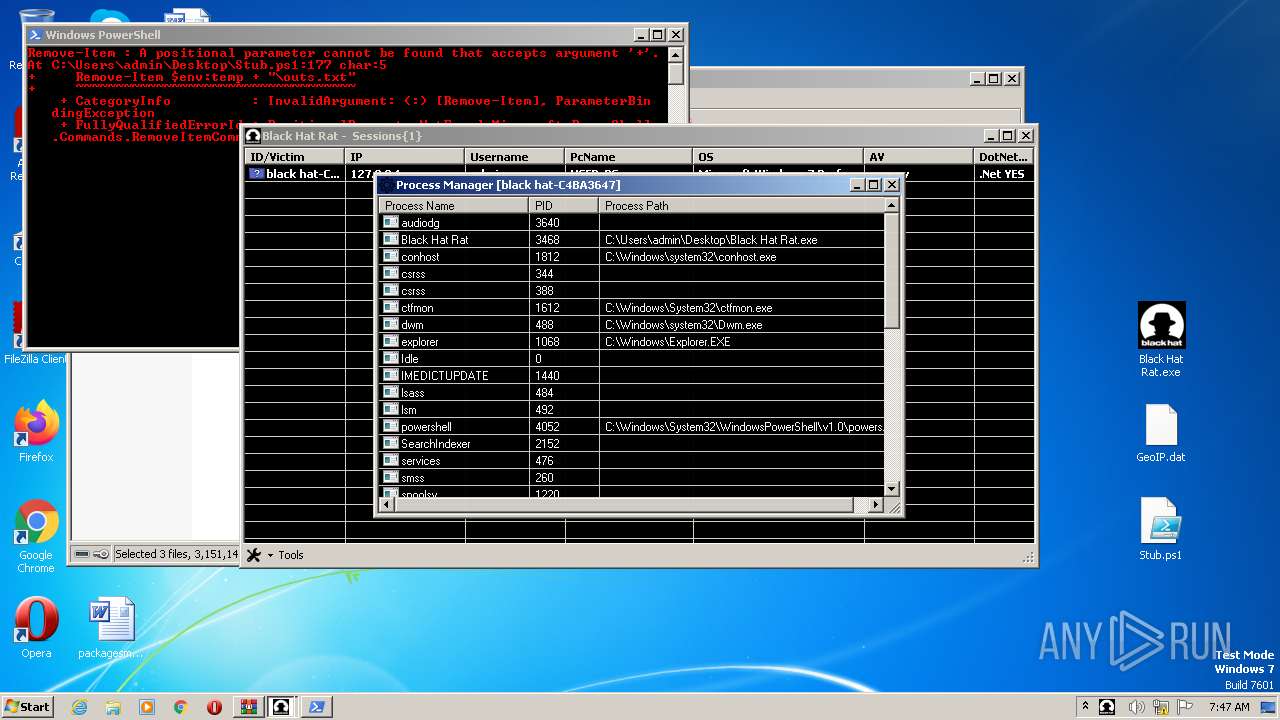
| 3468 | "C:\Users\admin\Desktop\Black Hat Rat.exe" | C:\Users\admin\Desktop\Black Hat Rat.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Black Hat Rat Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3572 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\pxwo3uni.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
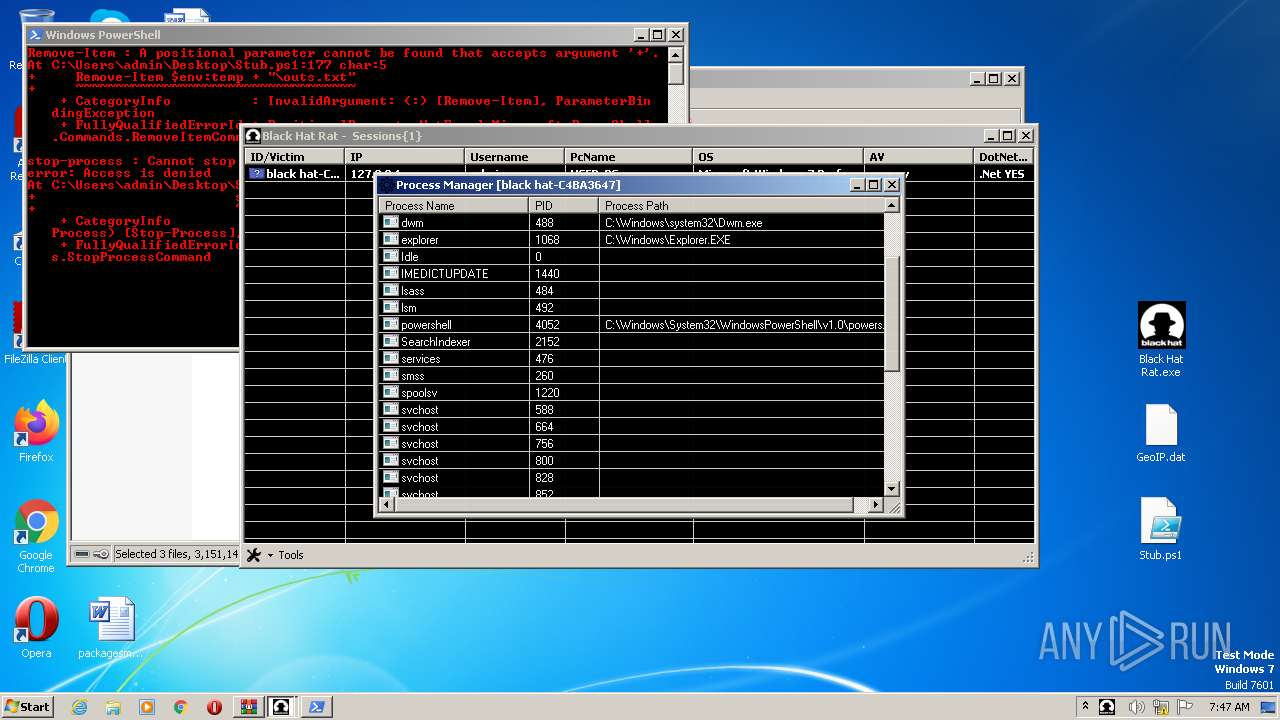
| 4040 | "C:\Windows\System32\cmd.exe" /c ver > C:\Users\admin\AppData\Local\Temp\outs.txt & exit | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 4052 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "-file" "C:\Users\admin\Desktop\Stub.ps1" "-Command" "if((Get-ExecutionPolicy ) -ne AllSigned) { Set-ExecutionPolicy -Scope Process Bypass }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
4 168
Read events
4 097
Write events
71
Delete events
0
Modification events
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4052) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4052) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
2
Suspicious files
8
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3096.29160\Black Hat Rat.exe | executable | |
MD5:3377B9F67F552E05B131EEB19D9997DF | SHA256:059112D9275D8865783E6A5F7145D07861C72045CD2C703BDCC7A722F07F11C9 | |||
| 4052 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF126970.TMP | binary | |
MD5:6E746FD7D50D37D308785006CF8D44E1 | SHA256:4F3C05CF195C5CB4506CE8A2B921073F18D9FBD807EBA875B51E7B83BD2E1A35 | |||
| 744 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES7056.tmp | binary | |
MD5:BC65AD6A4940F39729C343BE3F28EE2B | SHA256:BC639DA9CA54F94F84184EA8C1A2DF6DB0932D5F9BE51EA4FE157119B5D716E8 | |||
| 4052 | powershell.exe | C:\Users\admin\AppData\Local\Temp\ame4txqa.0av.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3572 | csc.exe | C:\Users\admin\AppData\Local\Temp\pxwo3uni.dll | executable | |
MD5:A3195D7606F1377C1F8B24839B360429 | SHA256:B94BB0C6302231CE34C991E9AE472C415ED84122F6A6D775013BEA8FEC97C6C9 | |||
| 4052 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\ZQT675FTSRQYFQKV26RW.temp | binary | |
MD5:BC94E8ADE0AA1E1EDA10EFEA7807ECCA | SHA256:1D22BA6A334C18138A05BFBDDD29C08D1135E5BA84E09CEFD444976450B9E598 | |||
| 4052 | powershell.exe | C:\Users\admin\AppData\Local\Temp\pxwo3uni.0.cs | text | |
MD5:DBA25070D91E5EC9629016BC5CB03A7E | SHA256:D2161C703B36605B5327FE1A89C7920D617A4F5D1DE1173C58F5F61DA13A58B2 | |||
| 3096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3096.29160\Stub.ps1 | text | |
MD5:98D7C085D524E6E5BAADC74EEB446308 | SHA256:1B115F64530BFA161404FC74E9626457D95628C1B20BEC1B08A5CD52360C2989 | |||
| 3096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3096.29160\GeoIP.dat | binary | |
MD5:C8DB63170E85B35CE51B5D1AEF098708 | SHA256:6C15C5F8E3FAEC8ADF4321FD8F9D62F3F4DD645DAFD0F9F6C52B118001654D36 | |||
| 3572 | csc.exe | C:\Users\admin\AppData\Local\Temp\pxwo3uni.out | text | |
MD5:7B459B1E3F9B965B7666D43ACE7C74AD | SHA256:DAE66BF7C912FEC5627C548DD8CDBC97586A4FD99DD4FB419B31ABB0B84364C6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2624 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |