| download: | tasy-acesso-externo.jnlp |
| Full analysis: | https://app.any.run/tasks/b5b81ae2-3e87-40ef-9dce-aee00d184d21 |
| Verdict: | Malicious activity |
| Analysis date: | July 05, 2019, 14:15:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/xml |
| File info: | XML 1.0 document, UTF-8 Unicode text, with CRLF line terminators |
| MD5: | 0DACE67E0ABF18B58A28A4BE1EEA9E3D |
| SHA1: | 40EA3F4E303F6866AAB95E02EEF331BB148870BD |
| SHA256: | B3BBC27C450C48A936872D484D2BB384999F2EE786E6F76B8F26BB853305A071 |
| SSDEEP: | 24:2dtdkGeFm3Uzk28asTsQvDb2b0ixC/HqvBHYH1QfBc9mxwYPLPj6hgOotKua095R:cLeFiU7Mh2xCH4emf3T77TxXa7S0G |
MALICIOUS
No malicious indicators.SUSPICIOUS
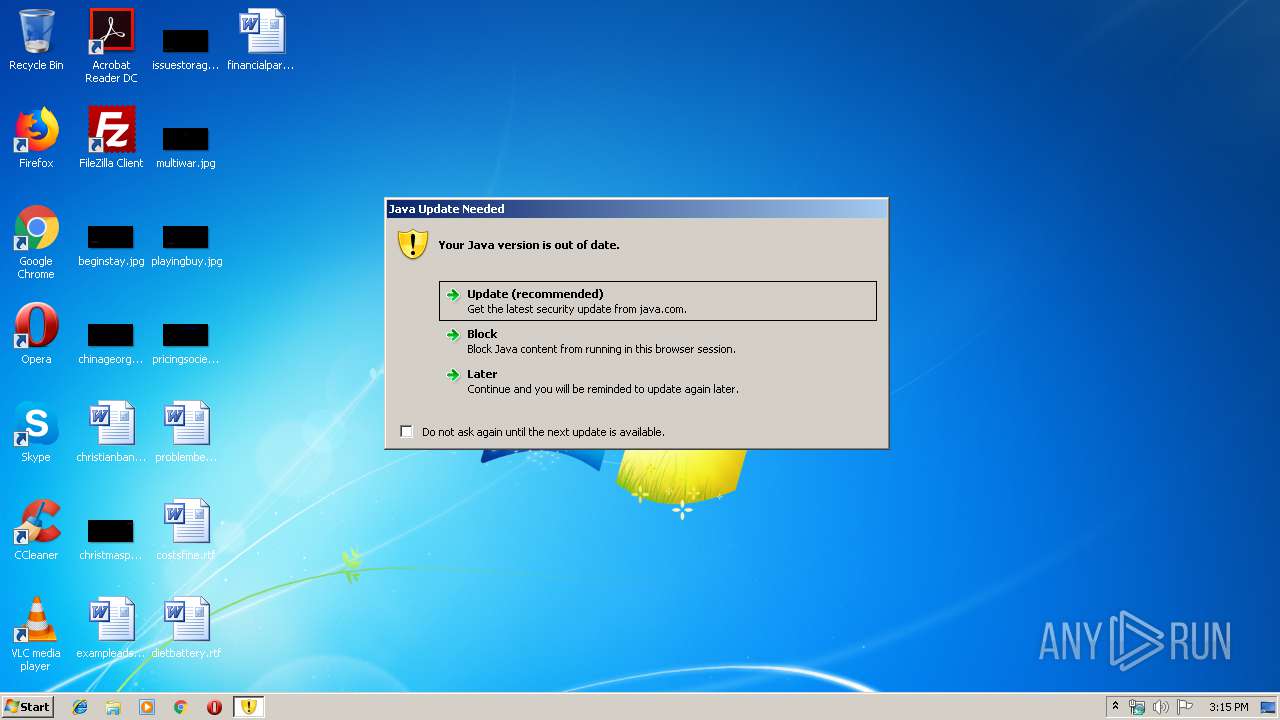
Check for Java to be installed
- javaws.exe (PID: 864)
Executes JAVA applets
- javaws.exe (PID: 864)
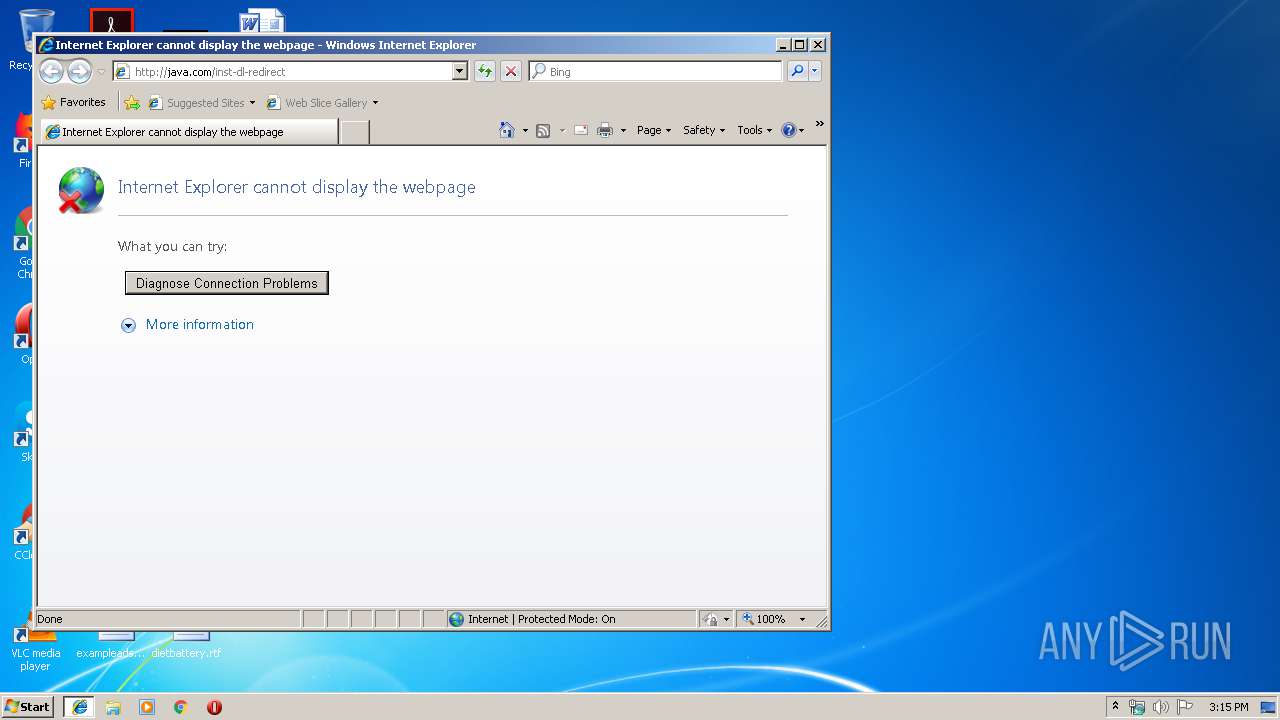
Starts Internet Explorer
- javaws.exe (PID: 864)
INFO
Reads internet explorer settings
- iexplore.exe (PID: 2912)
Reads Internet Cache Settings
- iexplore.exe (PID: 2912)
Application launched itself
- iexplore.exe (PID: 2044)
Creates files in the user directory
- iexplore.exe (PID: 2912)
Changes internet zones settings
- iexplore.exe (PID: 2044)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .jnlp | | | Java Web Start application descriptor (82.6) |
|---|---|---|
| .xml | | | Generic XML (ASCII) (10.8) |
| .html | | | HyperText Markup Language (6.5) |
EXIF
XMP
| JnlpCodebase: | http://tasy.unimedsaocarlos.com.br/Tasy |
|---|---|
| JnlpHref: | tasy-acesso-externo.jnlp |
| JnlpSpec: | 1.0+ |
| JnlpInformationTitle: | Philips Application Loader |
| JnlpInformationVendor: | Philips Clinical Informatics |
| JnlpInformationHomepageHref: | http://www.cilam.philips.com.br |
| JnlpInformationDescription: | PhilipsLoader |
| JnlpInformationDescriptionKind: | short |
| JnlpInformationIconWidth: | 16 |
| JnlpInformationIconHeight: | 16 |
| JnlpInformationIconHref: | figuras/tasy16.png |
| JnlpInformationIconKind: | shortcut |
| JnlpInformationShortcutDesktop: | - |
| JnlpInformationShortcutMenuSubmenu: | Wheb Sistemas |
| JnlpUpdateCheck: | always |
| JnlpSecurityAll-permissions: | - |
| JnlpResourcesJ2seVersion: | 1.6+ |
| JnlpResourcesJarHref: | http://tasy.unimedsaocarlos.com.br/WhebRepositorio/PhilipsLoader.jar |
| JnlpResourcesJarMain: | |
| JnlpApplication-descMain-class: | br.com.philips.launcher.view.PhilipsLauncher |
| JnlpApplication-descArgument: | +VM-Xmx1024m |
Total processes
37
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 864 | "C:\Program Files\Java\jre1.8.0_92\bin\javaws.exe" "C:\Users\admin\AppData\Local\Temp\tasy-acesso-externo.jnlp" | C:\Program Files\Java\jre1.8.0_92\bin\javaws.exe | — | explorer.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Start Launcher Exit code: 1 Version: 11.92.2.14 Modules
| |||||||||||||||
| 2044 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | javaws.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2492 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -cp "C:\PROGRA~1\Java\JRE18~1.0_9\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -userConfig "deployment.expiration.decision.11.92.2" "update" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | — | javaws.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2912 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2044 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3356 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -cp "C:\PROGRA~1\Java\JRE18~1.0_9\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -userConfig "deployment.expiration.decision.timestamp.11.92.2" "1562336137" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | — | javaws.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 3608 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -cp "C:\PROGRA~1\Java\JRE18~1.0_9\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -userConfig "deployment.expiration.decision.suppression.11.92.2" "false" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | — | javaws.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
Total events
452
Read events
359
Write events
86
Delete events
7
Modification events
| (PID) Process: | (2492) javaw.exe | Key: | HKEY_CURRENT_USER\Software\AppDataLow\Software\JavaSoft\DeploymentProperties |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (2492) javaw.exe | Key: | HKEY_CURRENT_USER\Software\AppDataLow\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.modified.timestamp |
Value: 1535457890299 | |||
| (PID) Process: | (2492) javaw.exe | Key: | HKEY_CURRENT_USER\Software\AppDataLow\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.roaming.profile |
Value: false | |||
| (PID) Process: | (2492) javaw.exe | Key: | HKEY_CURRENT_USER\Software\AppDataLow\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.version |
Value: 8 | |||
| (PID) Process: | (2492) javaw.exe | Key: | HKEY_CURRENT_USER\Software\AppDataLow\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.expired.version |
Value: 11.92.2 | |||
| (PID) Process: | (2492) javaw.exe | Key: | HKEY_CURRENT_USER\Software\AppDataLow\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.browser.path |
Value: C:\Program Files\Internet Explorer\iexplore.exe | |||
| (PID) Process: | (2492) javaw.exe | Key: | HKEY_CURRENT_USER\Software\AppDataLow\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.expiration.decision.11.92.2 |
Value: update | |||
| (PID) Process: | (3356) javaw.exe | Key: | HKEY_CURRENT_USER\Software\AppDataLow\Software\JavaSoft\DeploymentProperties |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (3356) javaw.exe | Key: | HKEY_CURRENT_USER\Software\AppDataLow\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.modified.timestamp |
Value: 1562336137811 | |||
| (PID) Process: | (3356) javaw.exe | Key: | HKEY_CURRENT_USER\Software\AppDataLow\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.roaming.profile |
Value: false | |||
Executable files
0
Suspicious files
2
Text files
29
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3356 | javaw.exe | C:\Users\admin\AppData\Local\Temp\JavaDeployReg.log | — | |
MD5:— | SHA256:— | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2492 | javaw.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\deployment.properties | text | |
MD5:— | SHA256:— | |||
| 2492 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 3356 | javaw.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\deployment.properties | text | |
MD5:— | SHA256:— | |||
| 2492 | javaw.exe | C:\Users\admin\AppData\Local\Temp\JavaDeployReg.log | text | |
MD5:— | SHA256:— | |||
| 2912 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\desktop.ini | ini | |
MD5:4A3DEB274BB5F0212C2419D3D8D08612 | SHA256:2842973D15A14323E08598BE1DFB87E54BF88A76BE8C7BC94C56B079446EDF38 | |||
| 2912 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2912 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
6
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
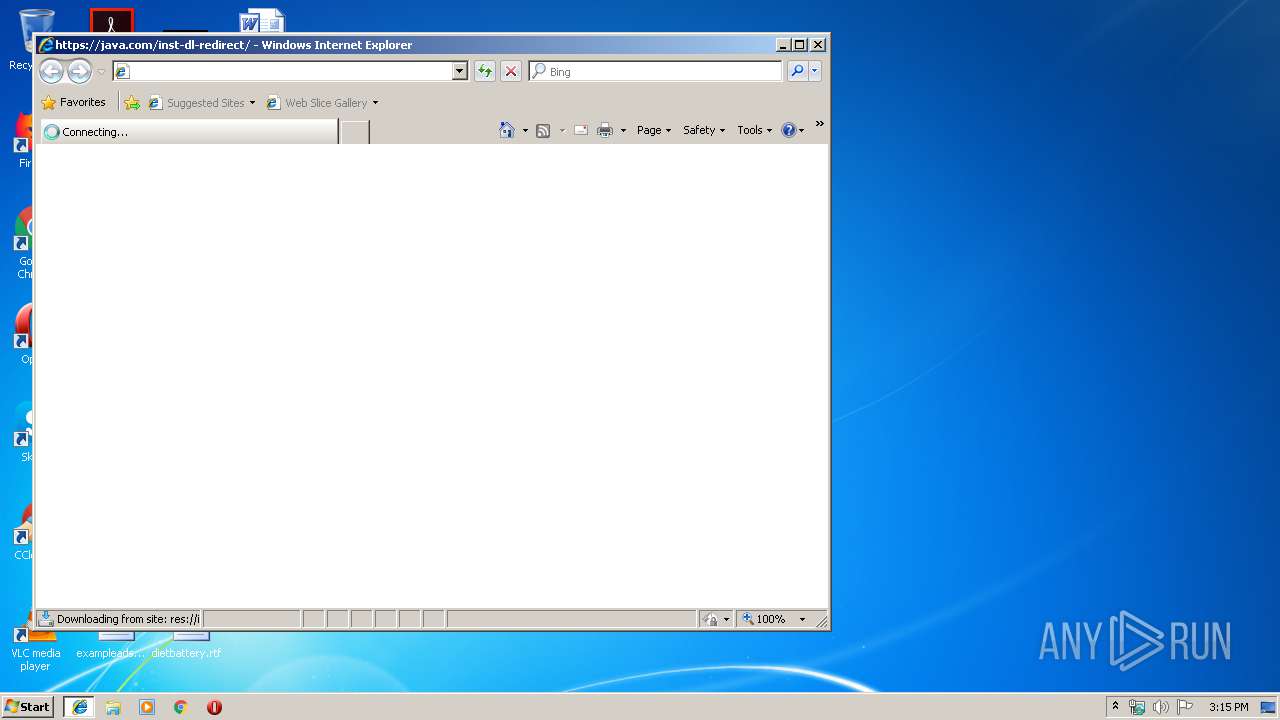
2912 | iexplore.exe | GET | 301 | 23.0.251.10:80 | http://java.com/inst-dl-redirect | NL | — | — | whitelisted |
2912 | iexplore.exe | GET | 301 | 23.0.251.10:80 | http://java.com/inst-dl-redirect/ | NL | — | — | whitelisted |
2044 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2044 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2912 | iexplore.exe | 23.0.251.10:80 | java.com | Akamai Technologies, Inc. | NL | whitelisted |
2912 | iexplore.exe | 23.0.251.10:443 | java.com | Akamai Technologies, Inc. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
java.com |
| whitelisted |