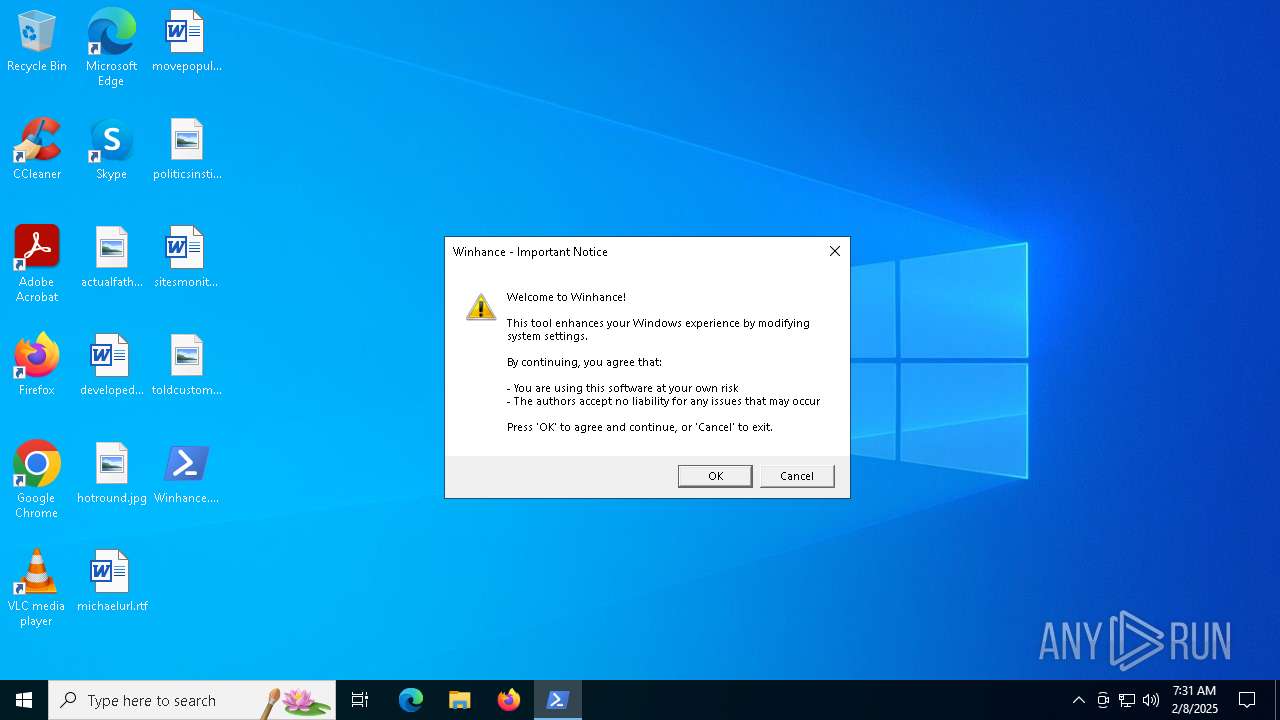
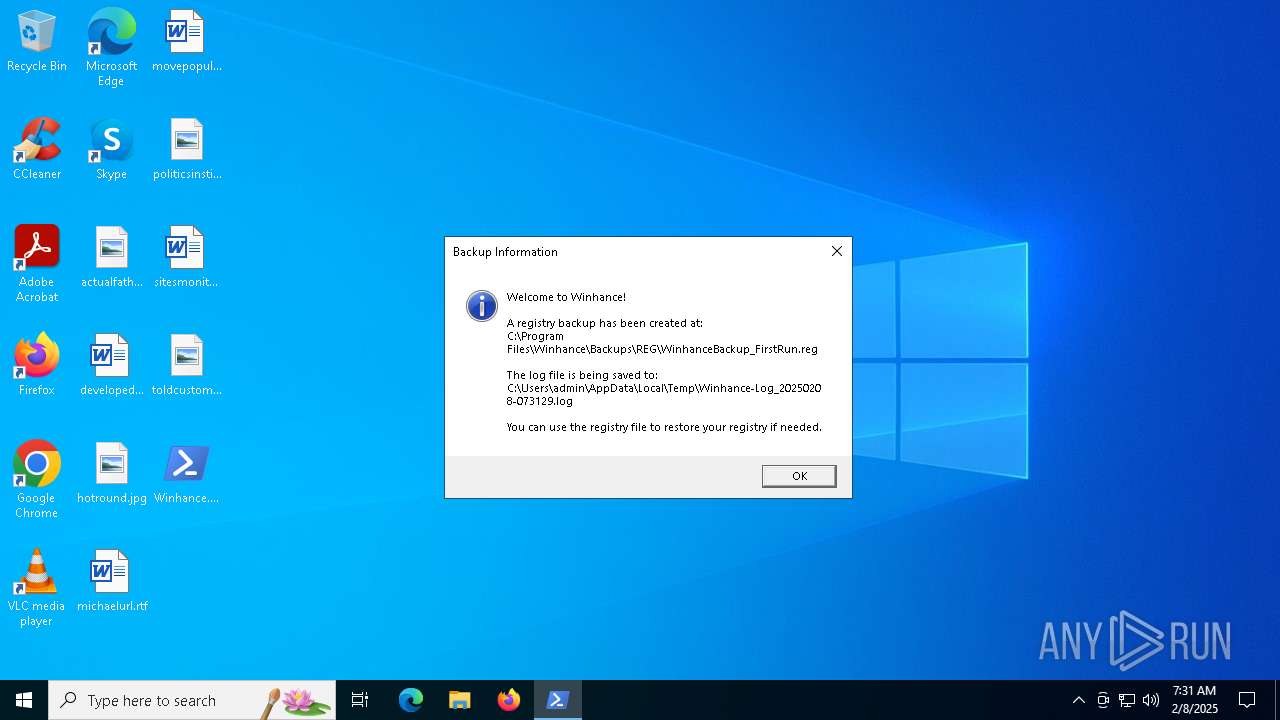
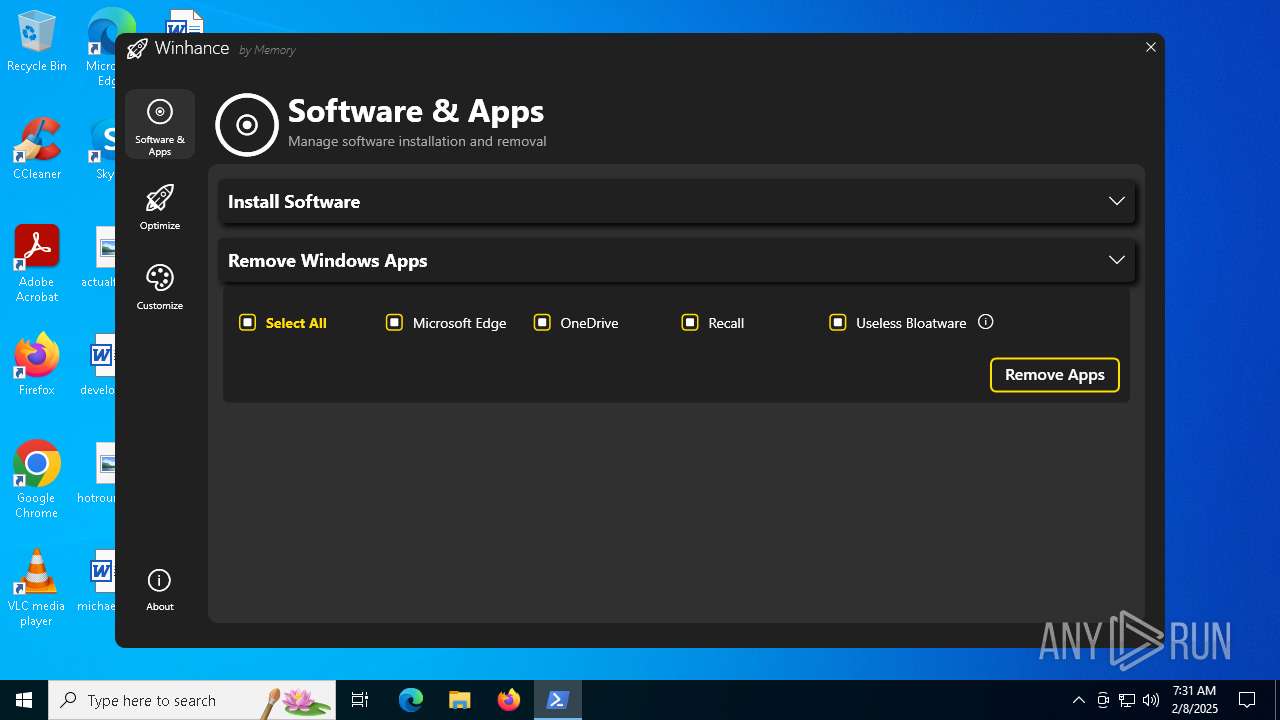
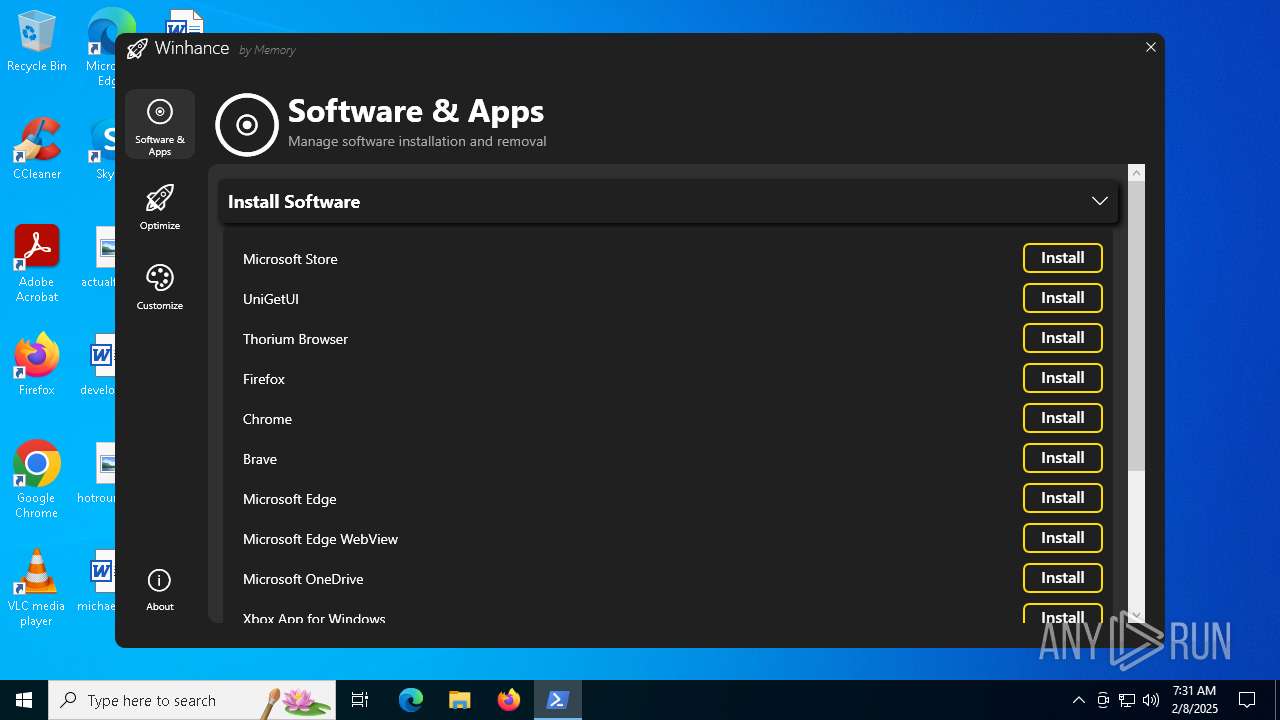
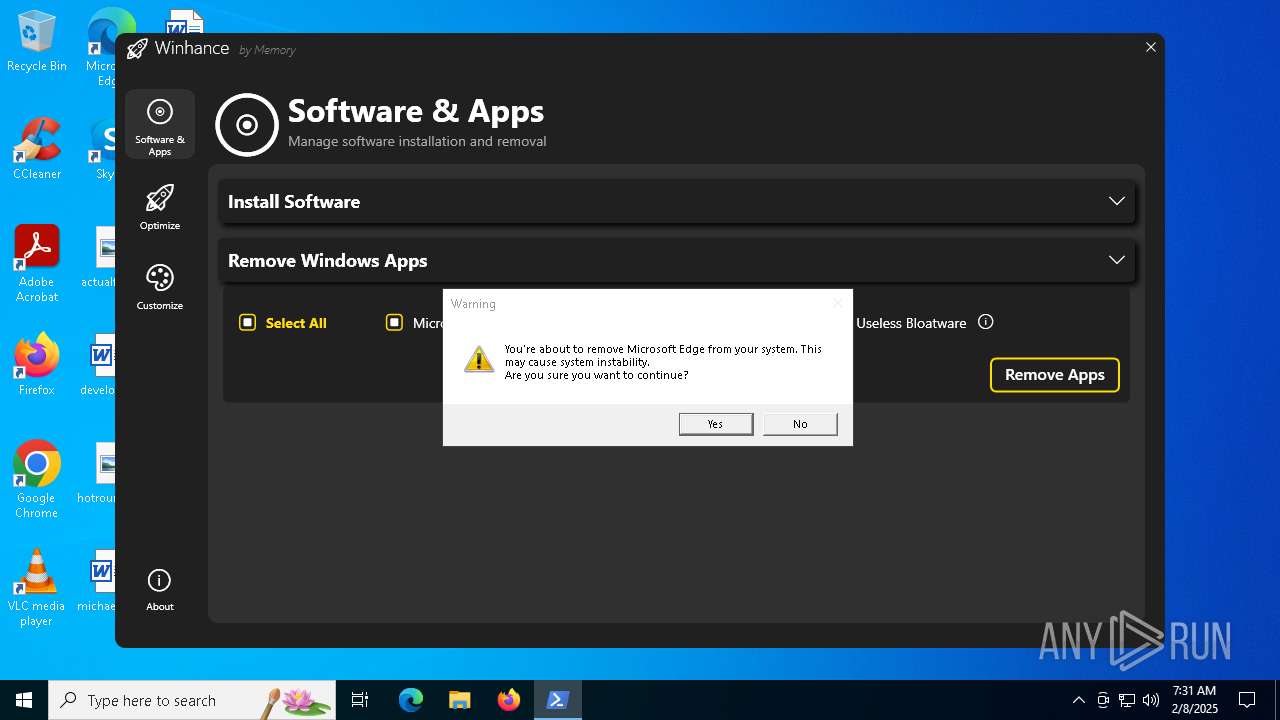
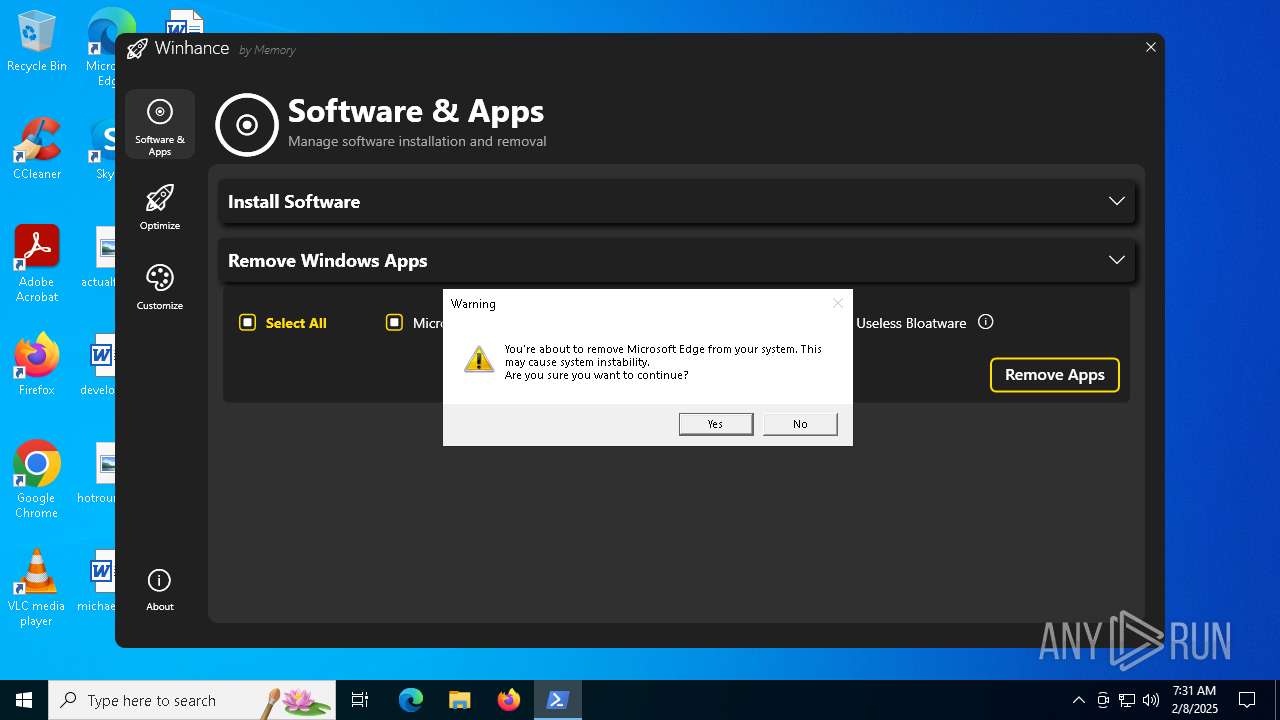
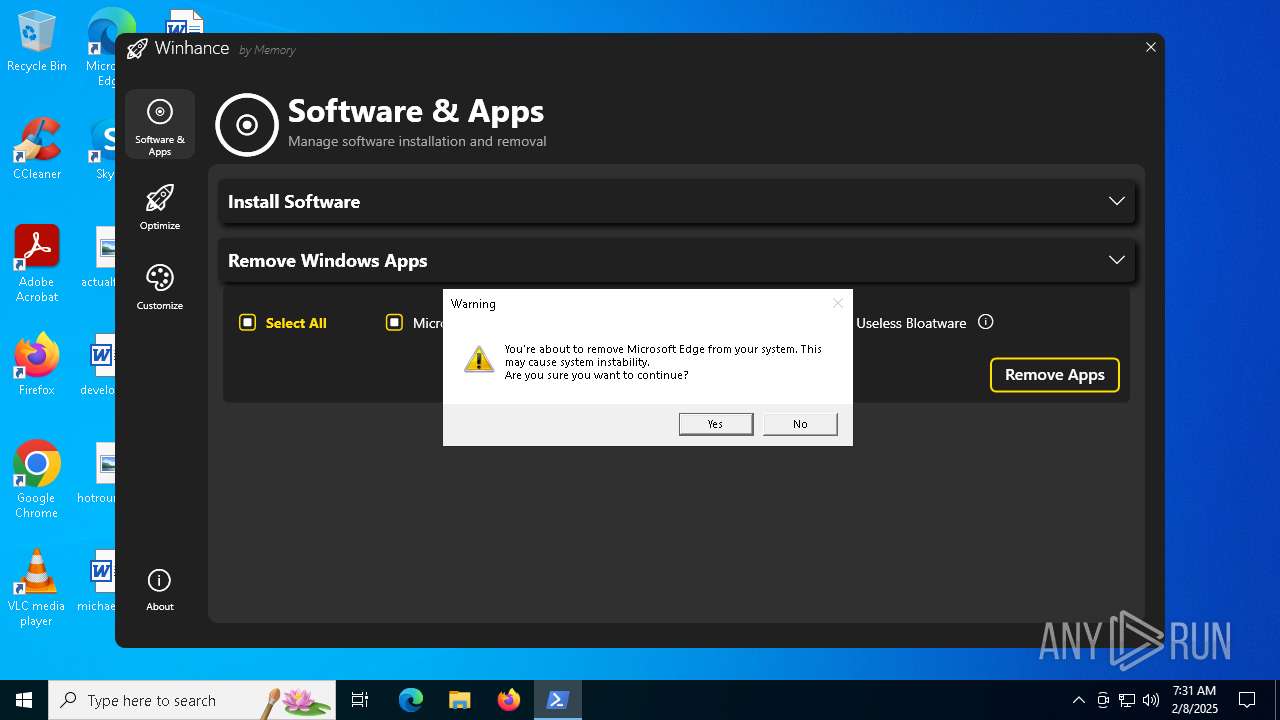
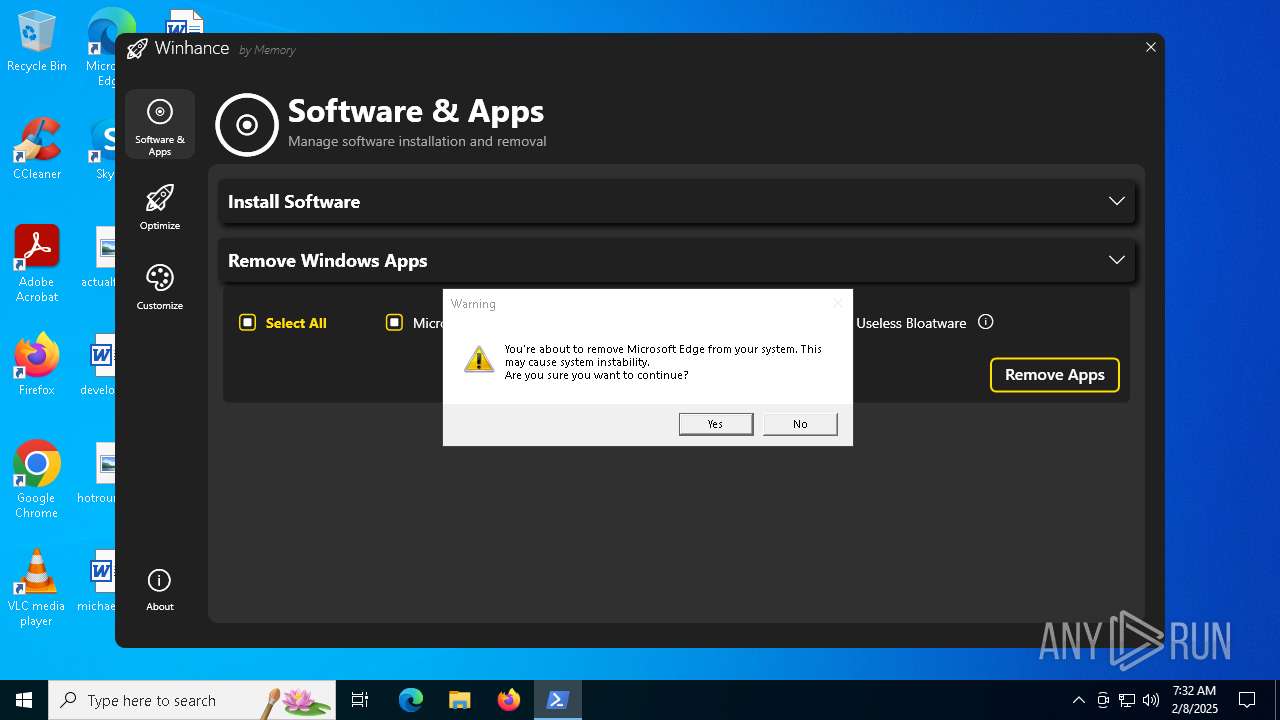
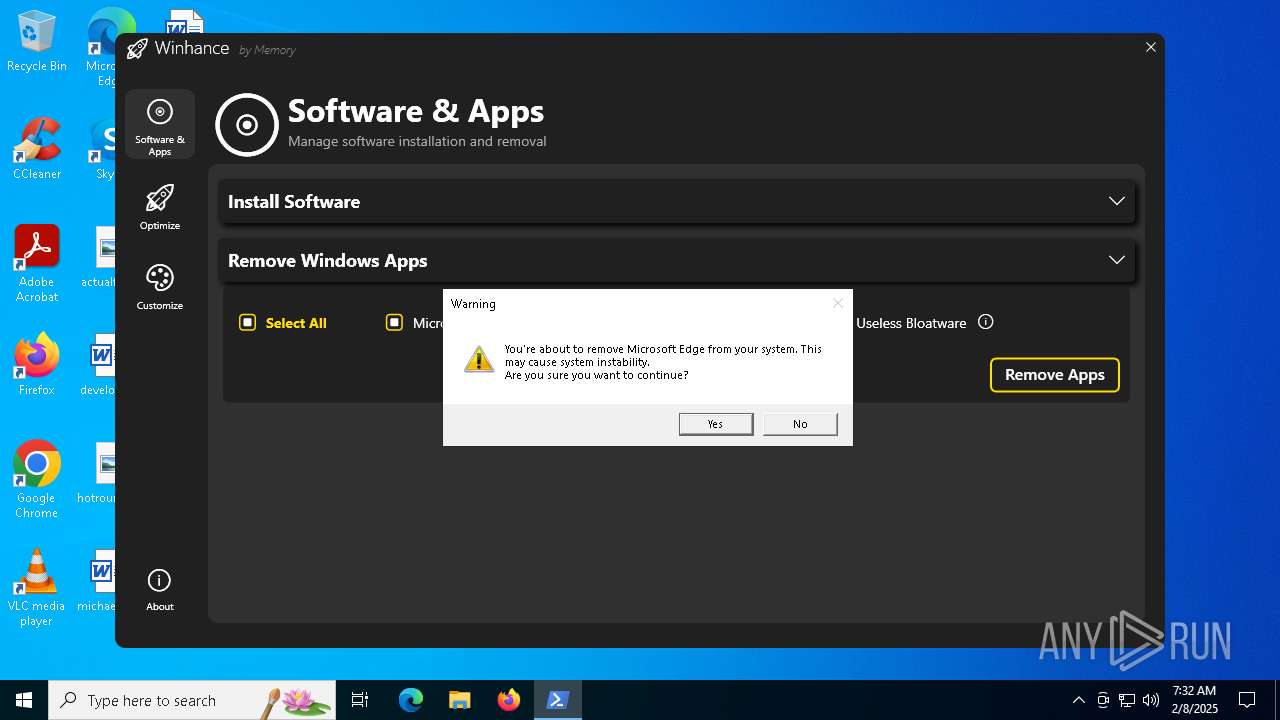
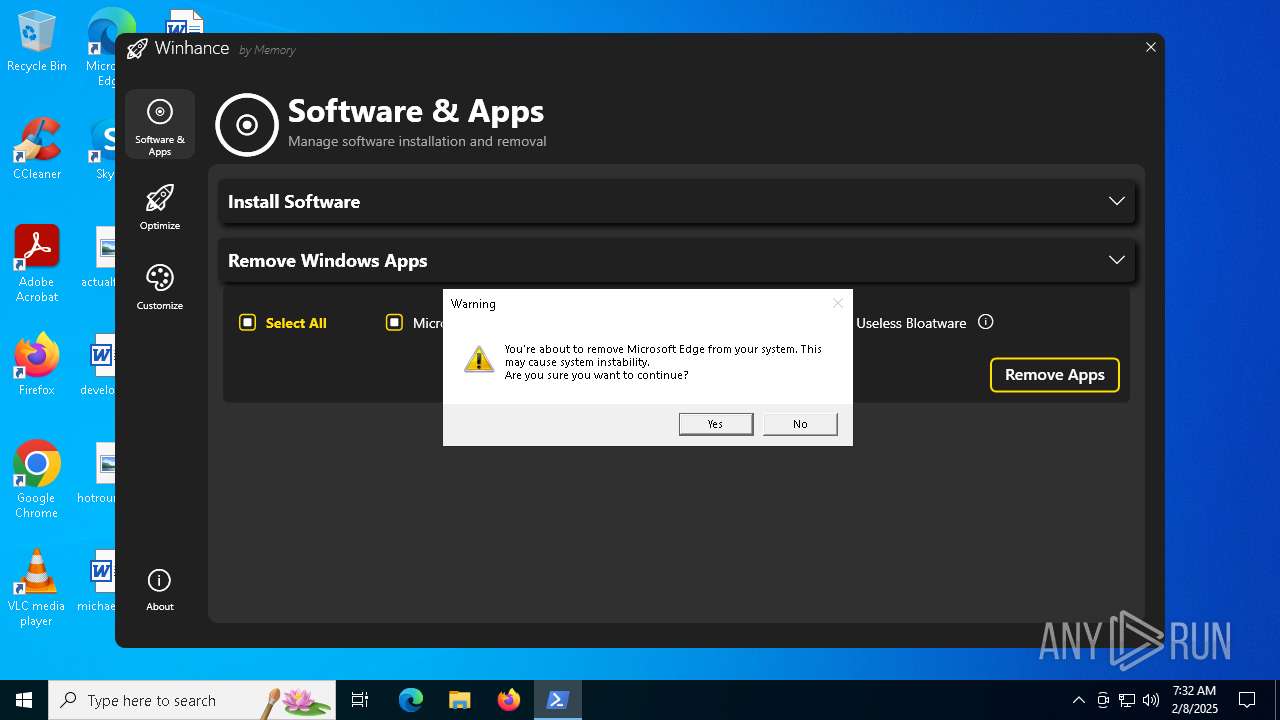
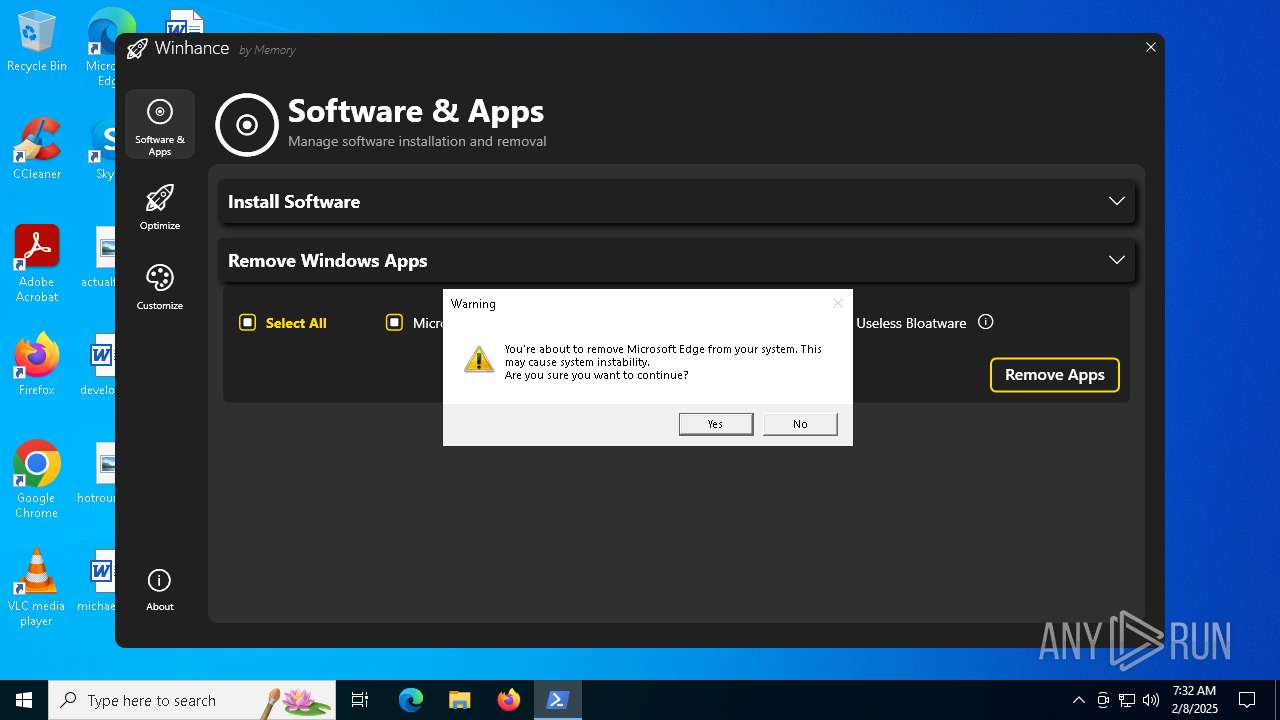
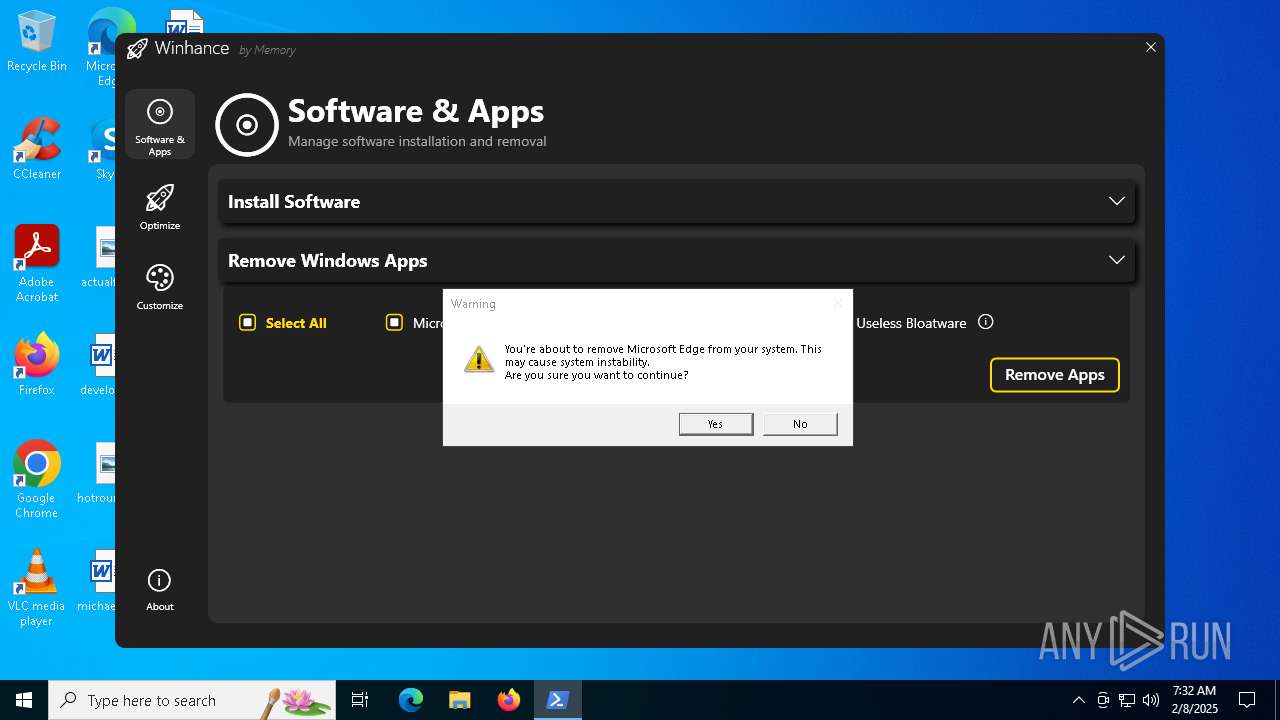
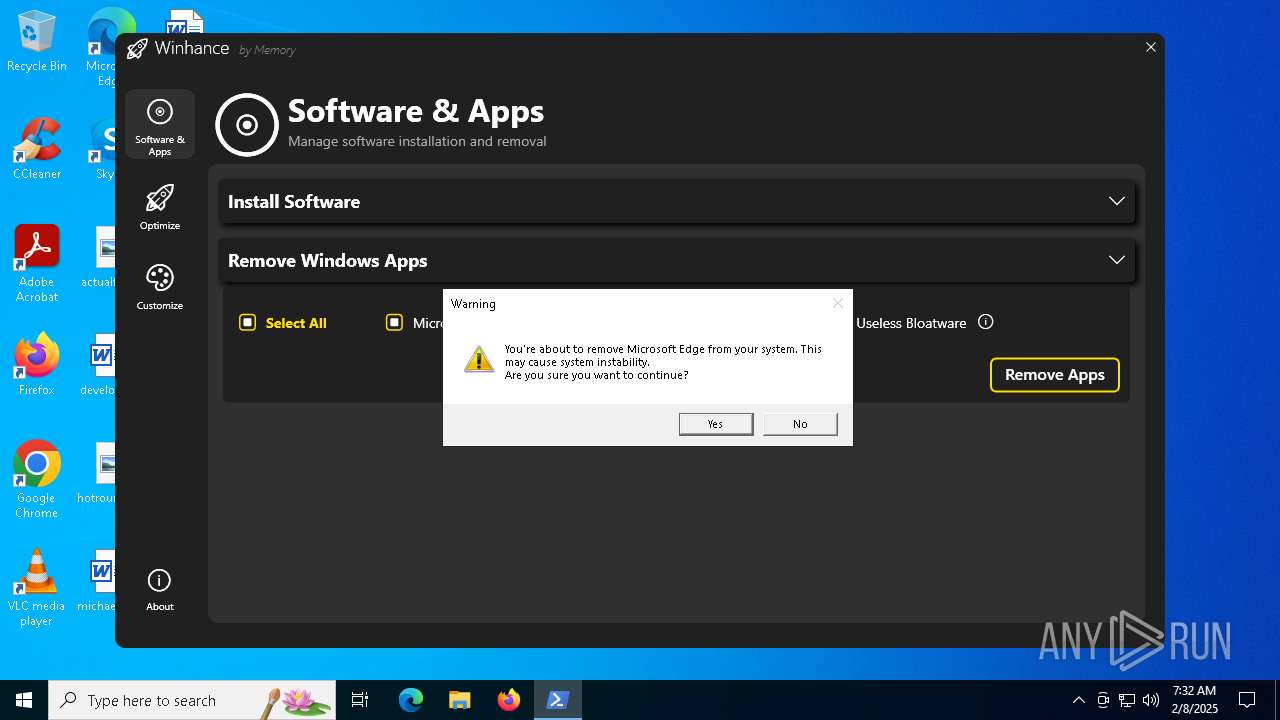
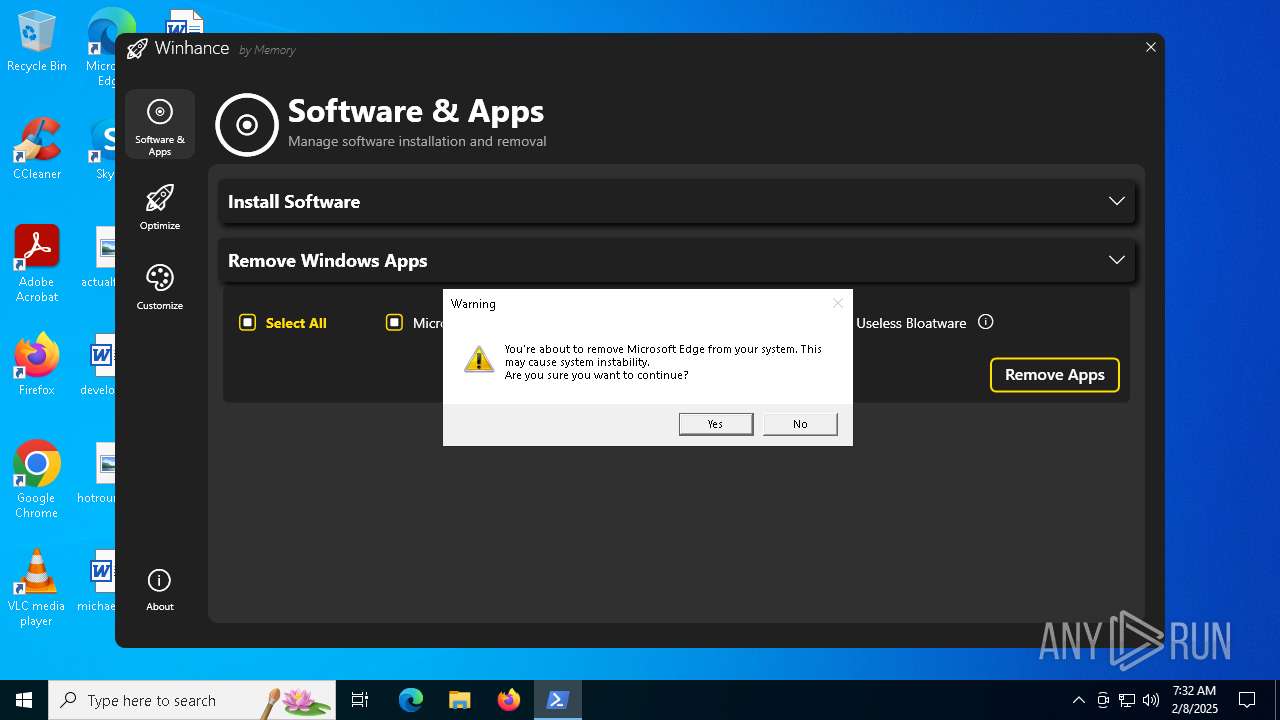
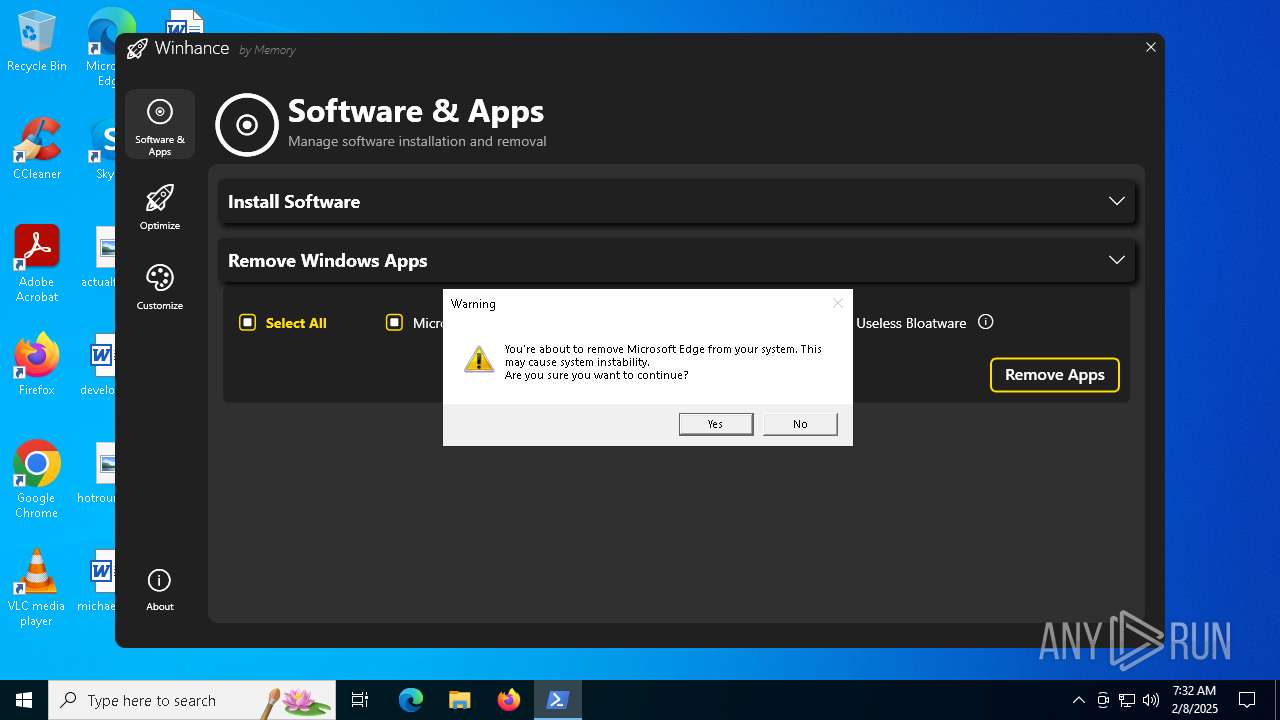
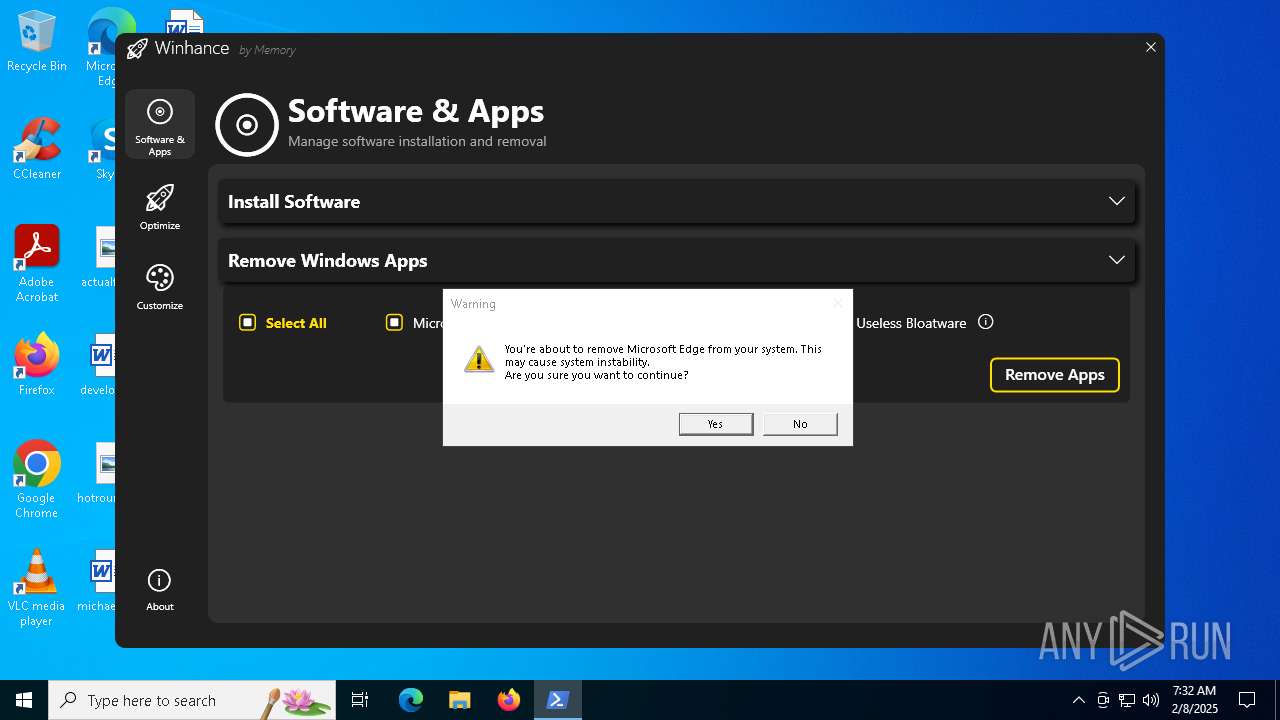
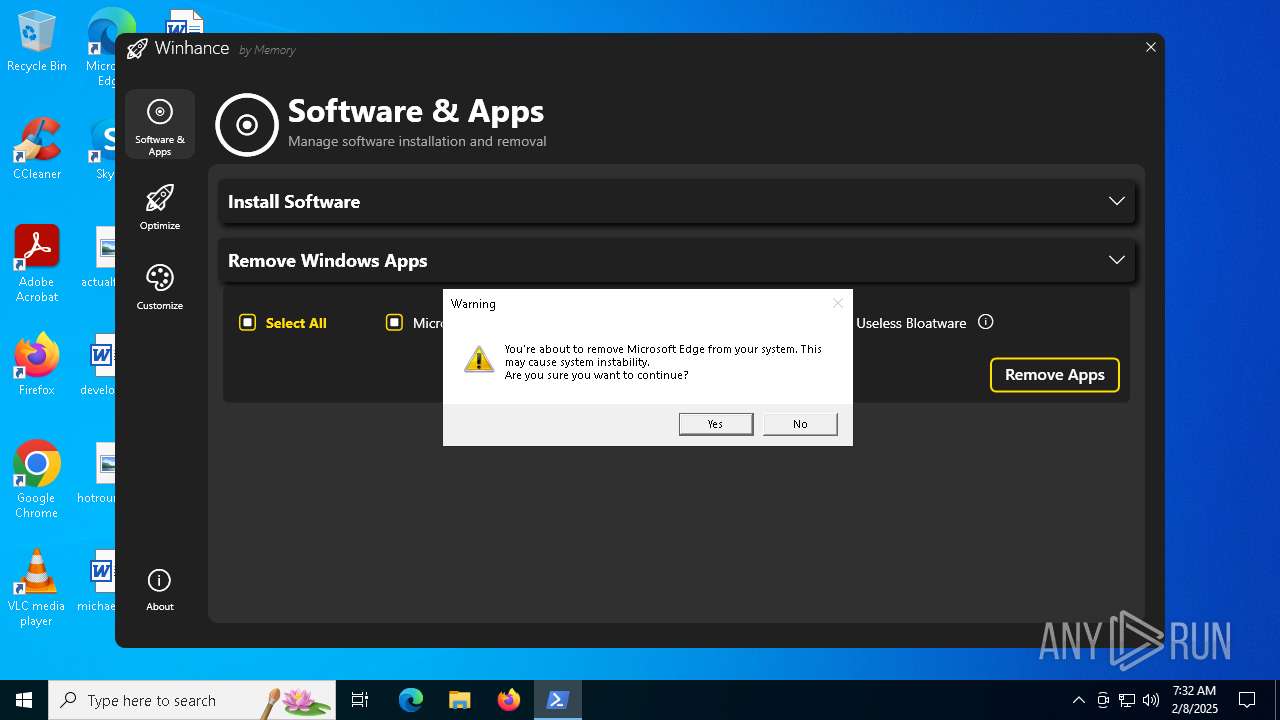
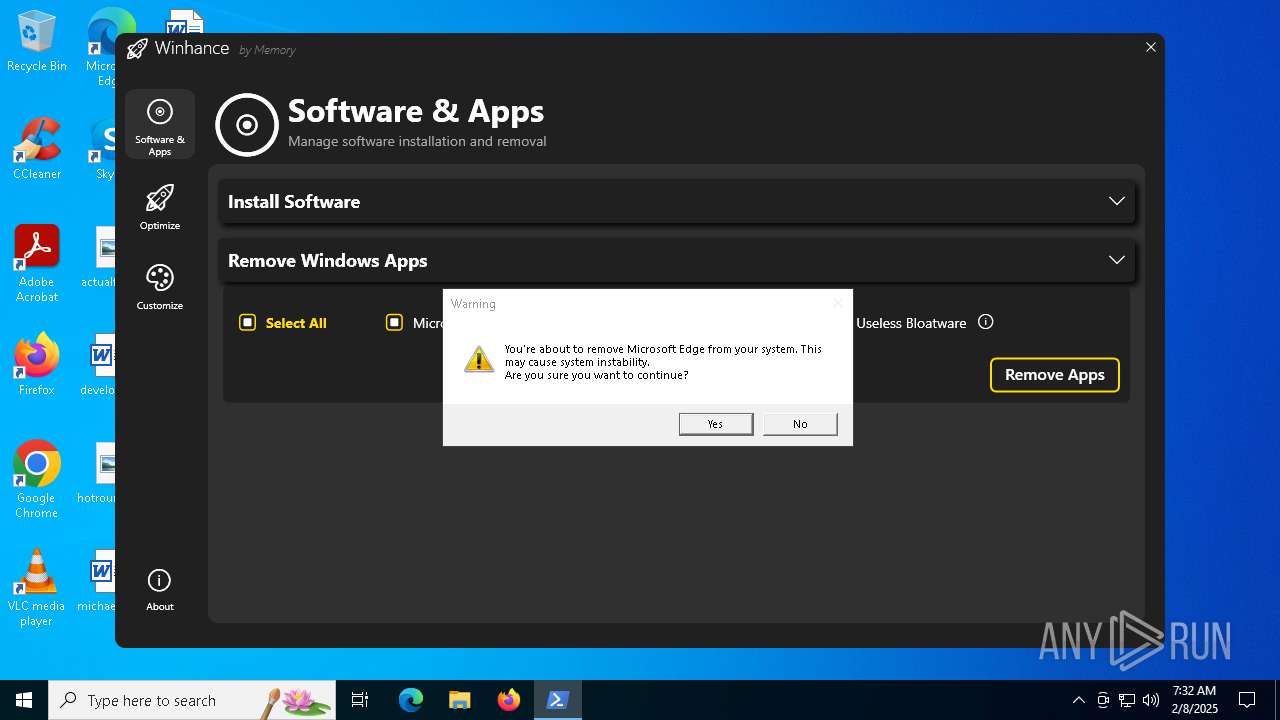
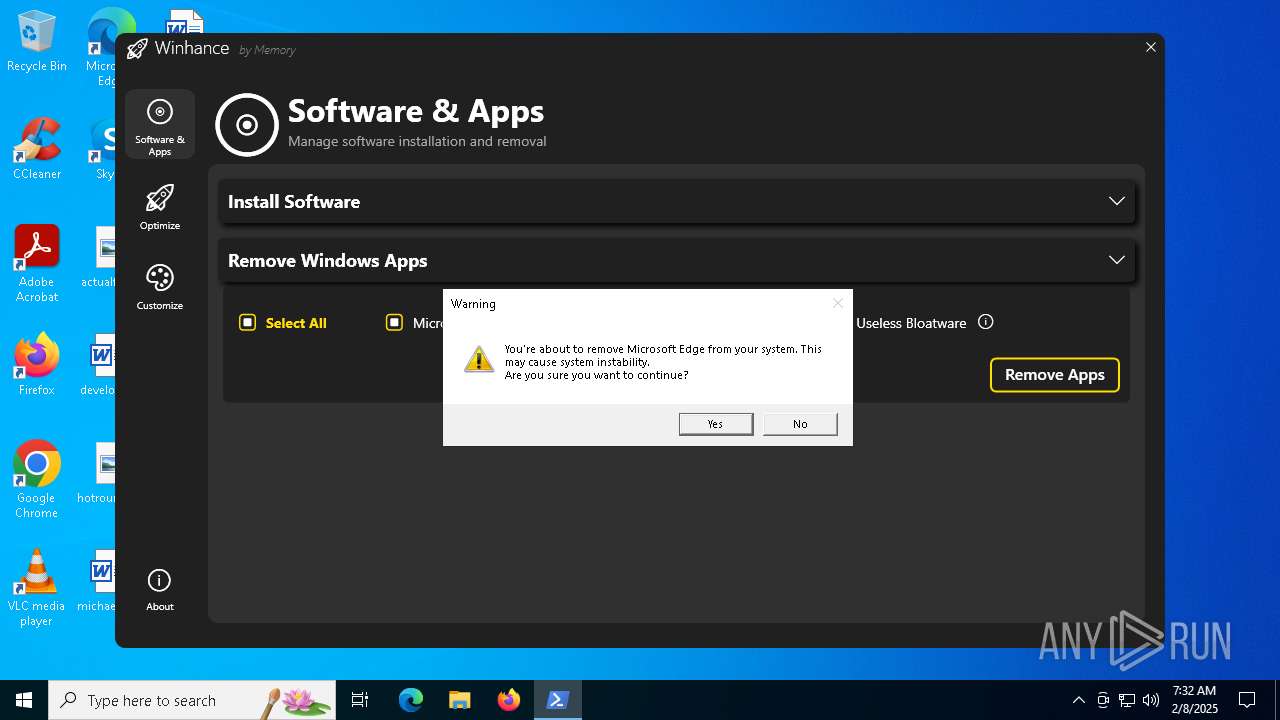
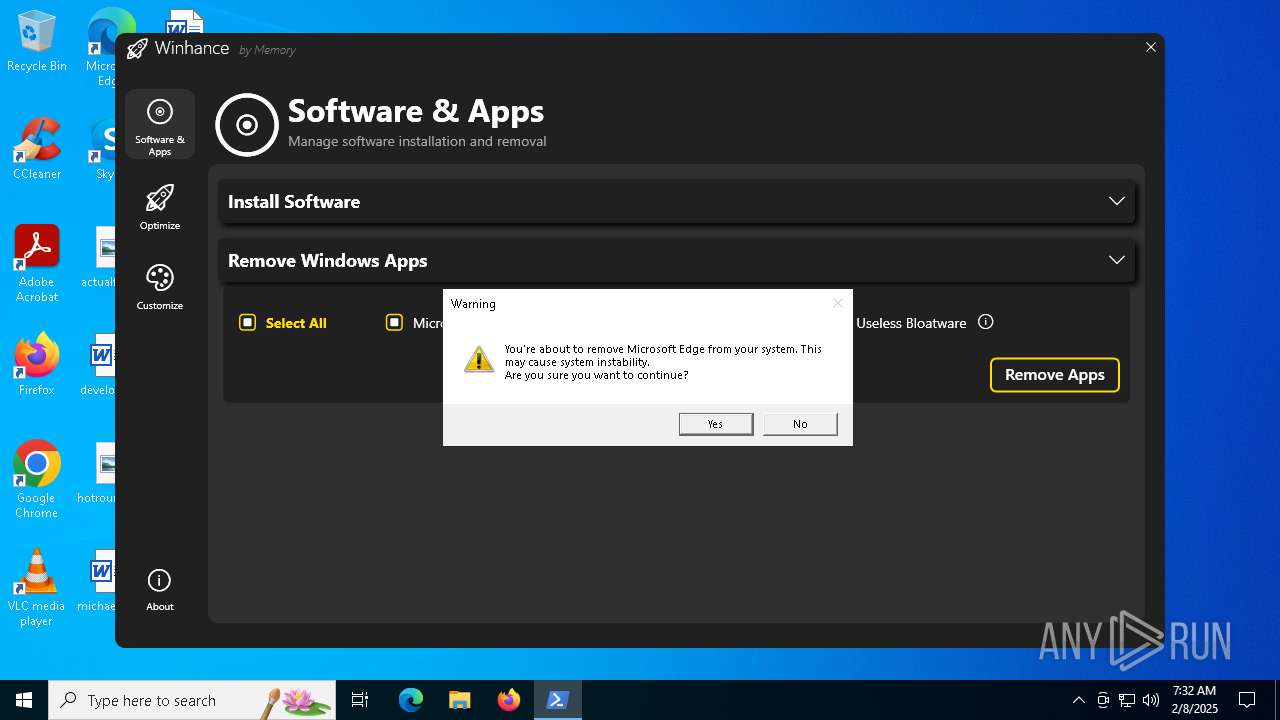
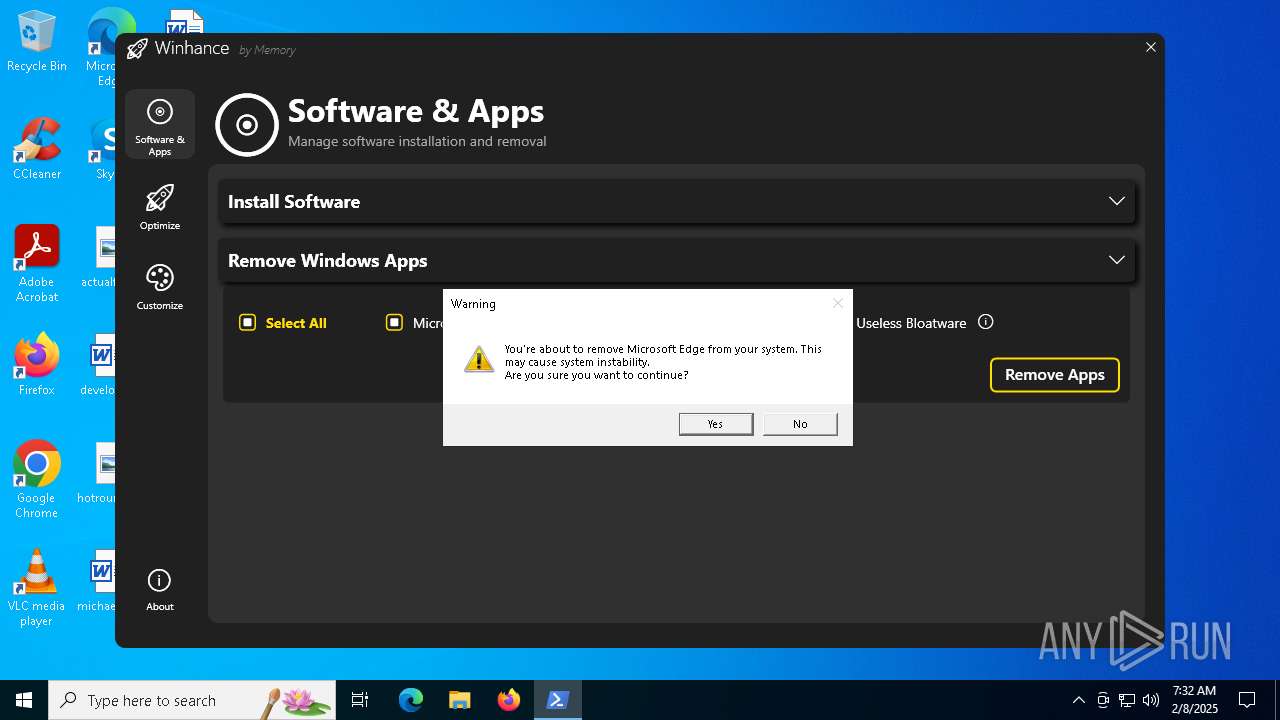
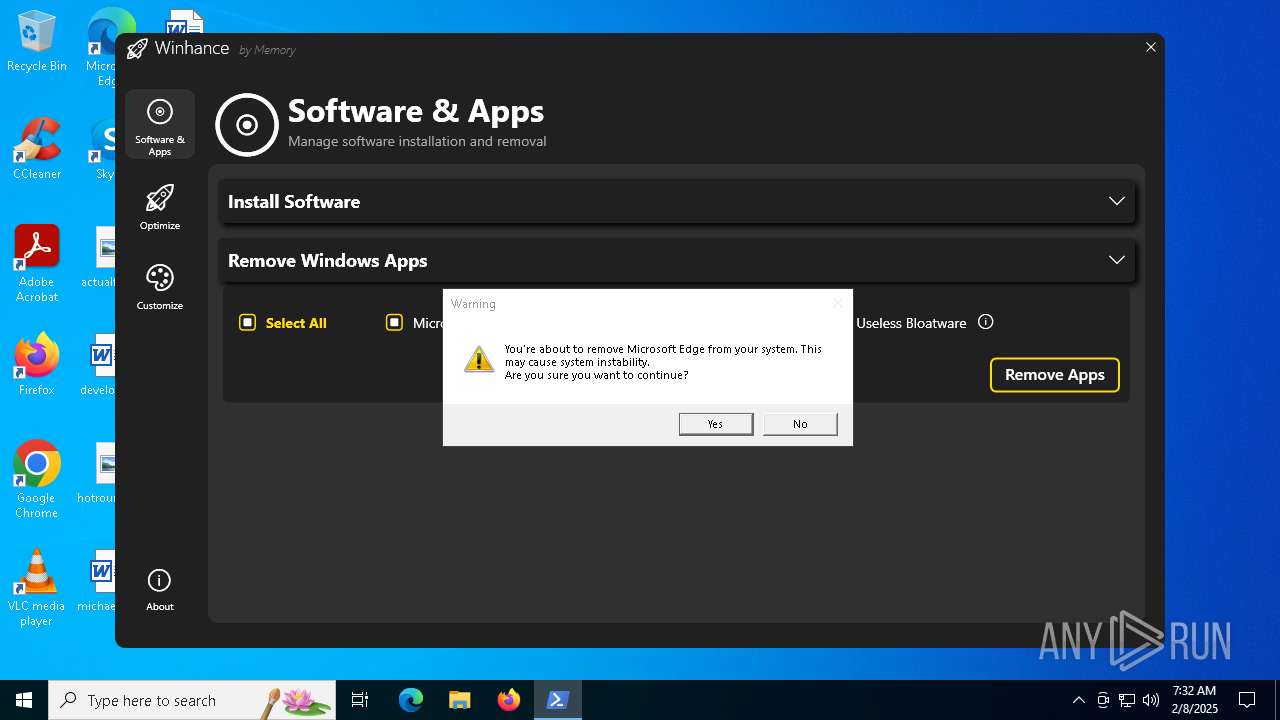
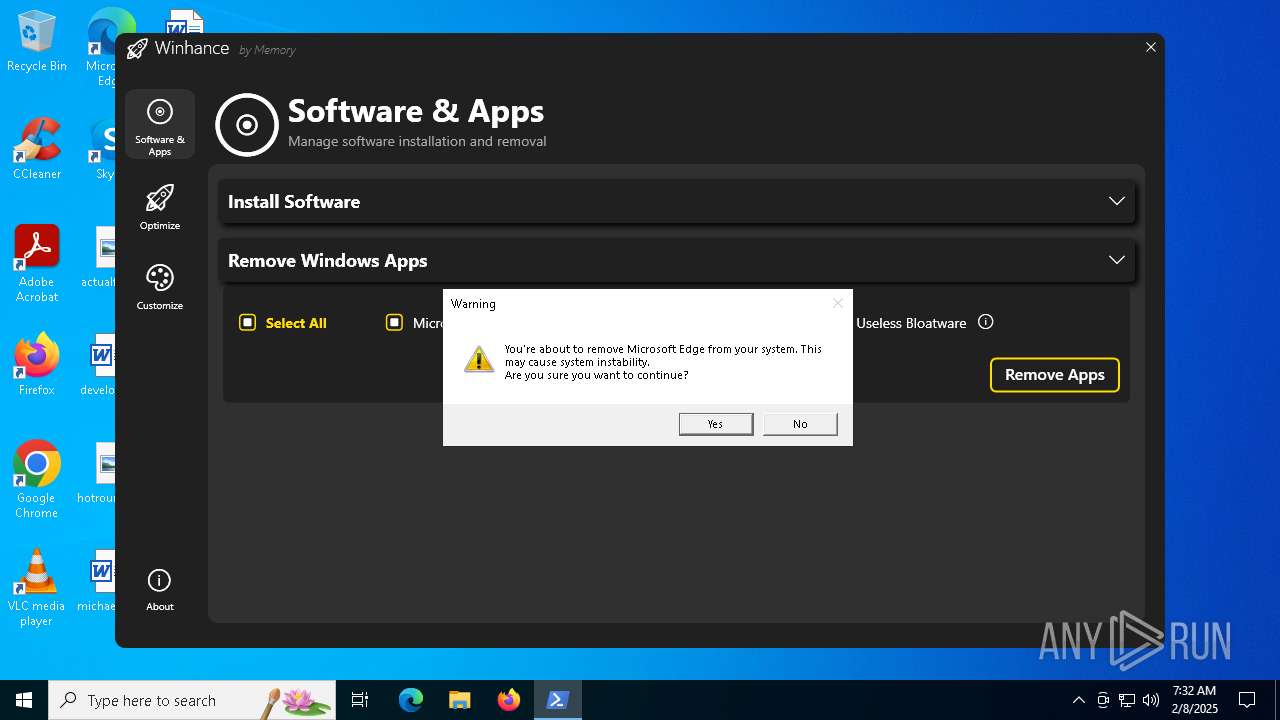
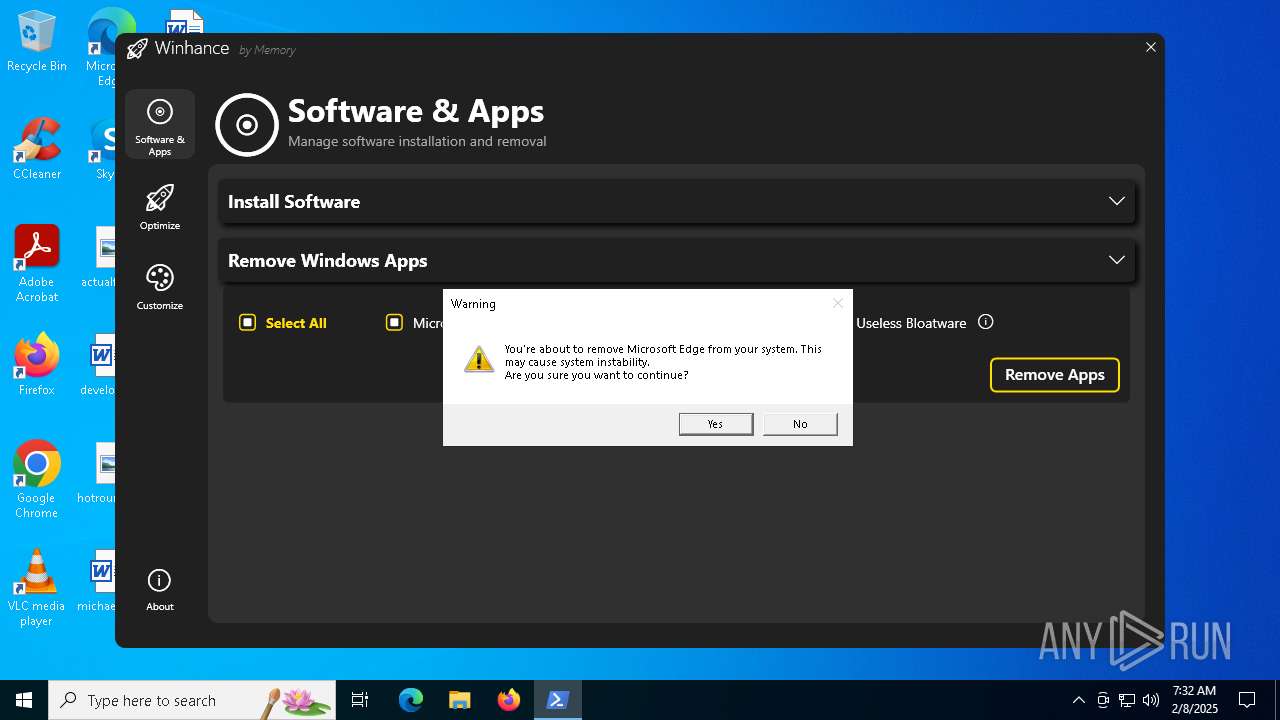
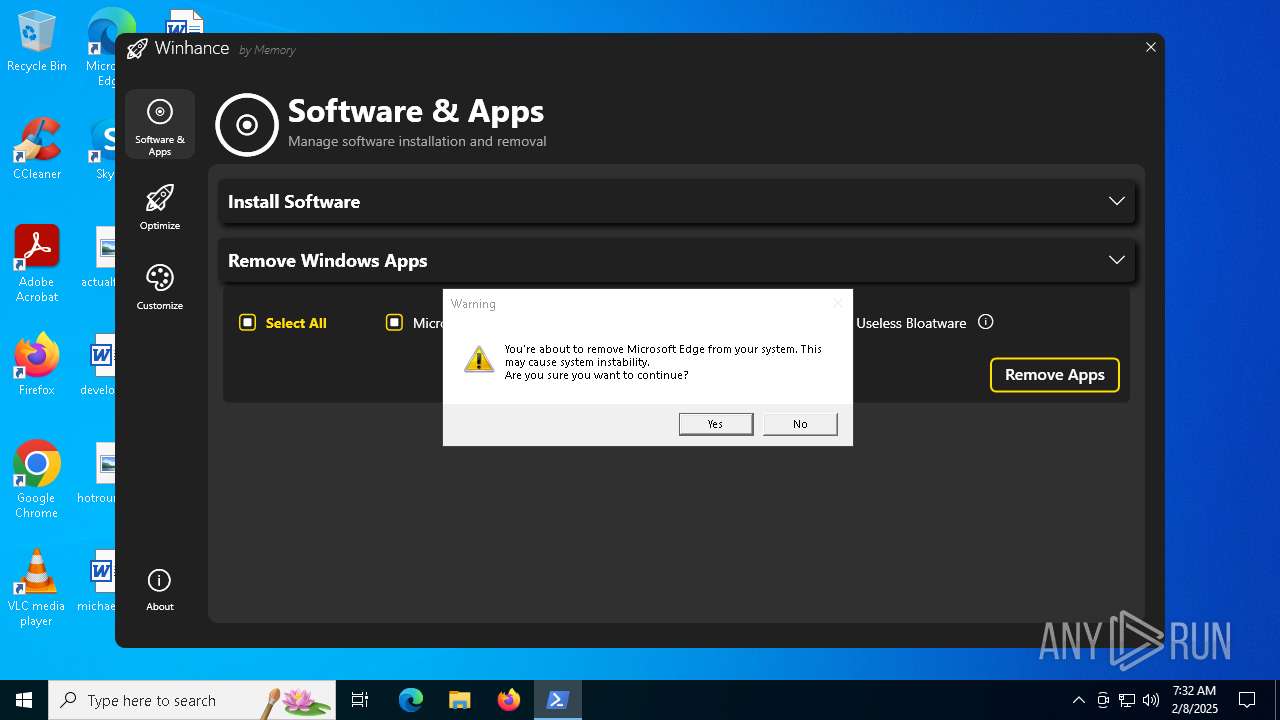
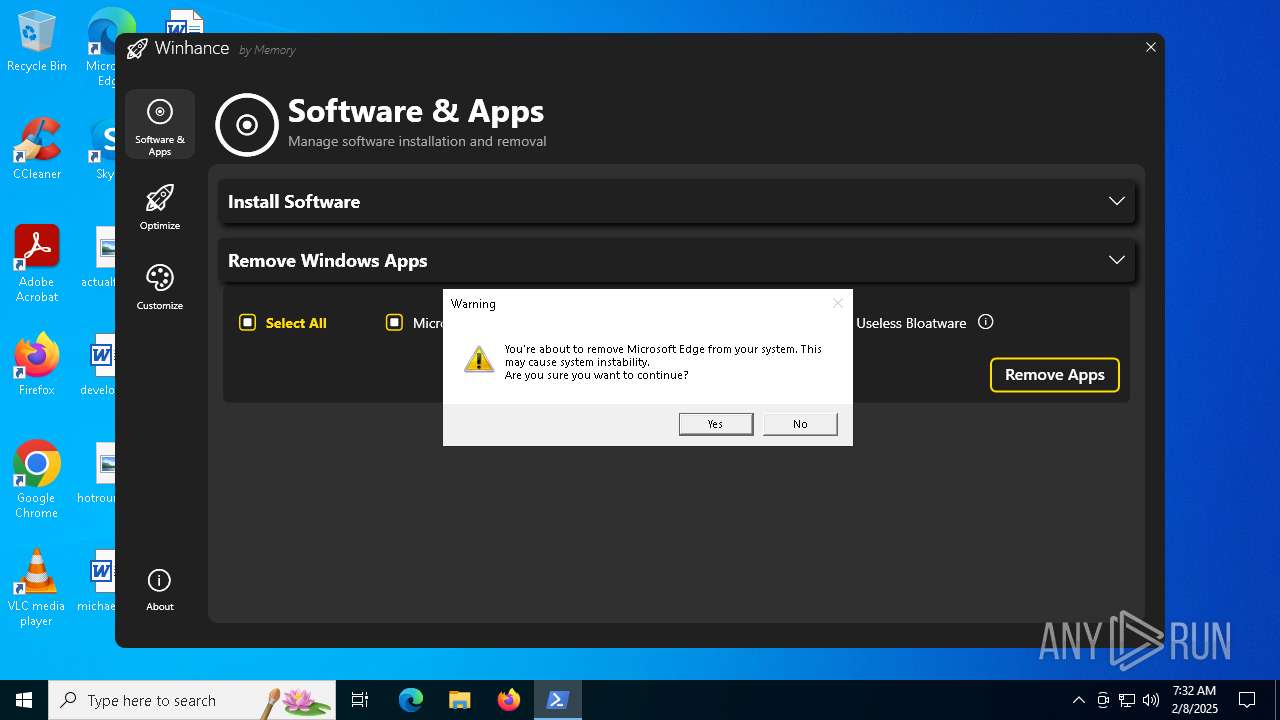
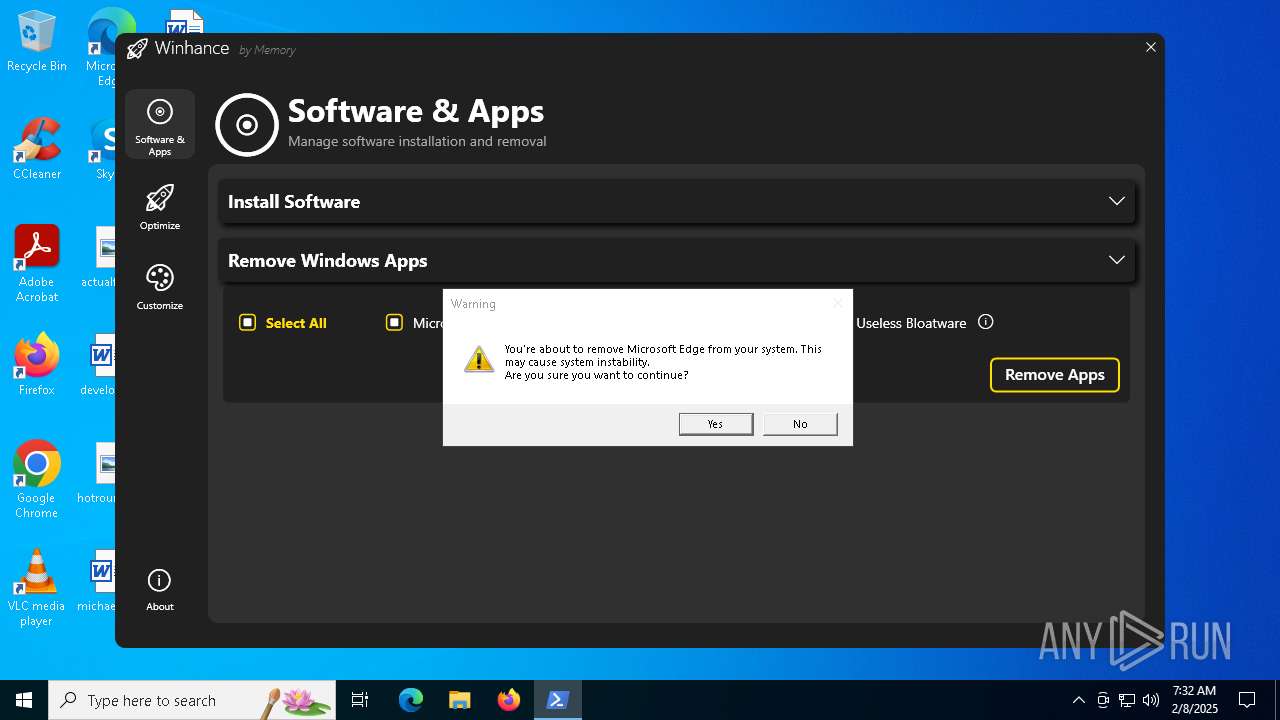
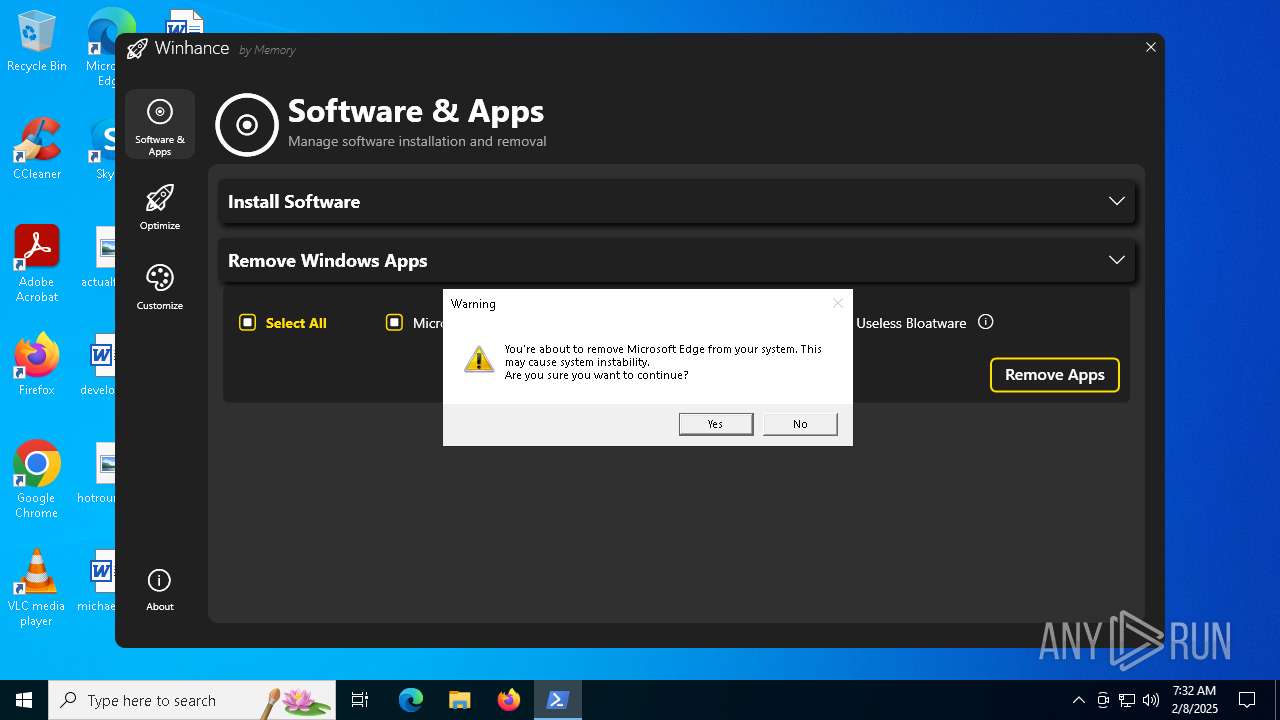
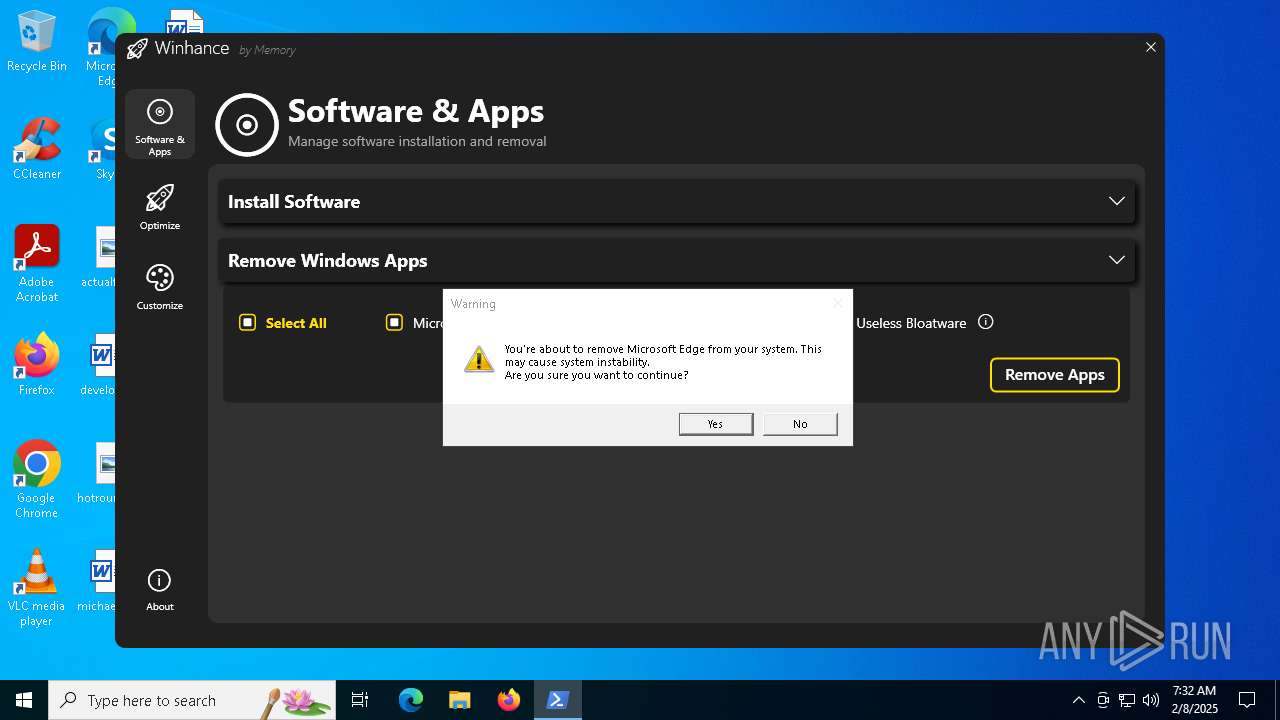
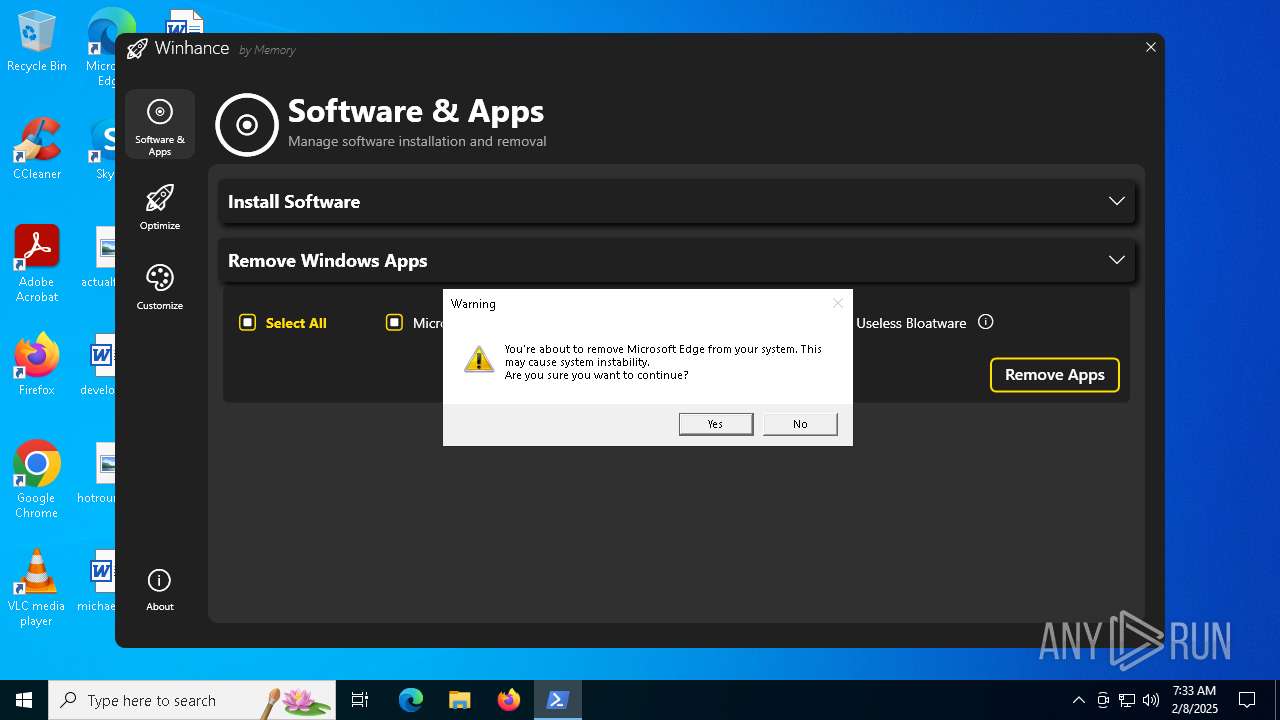
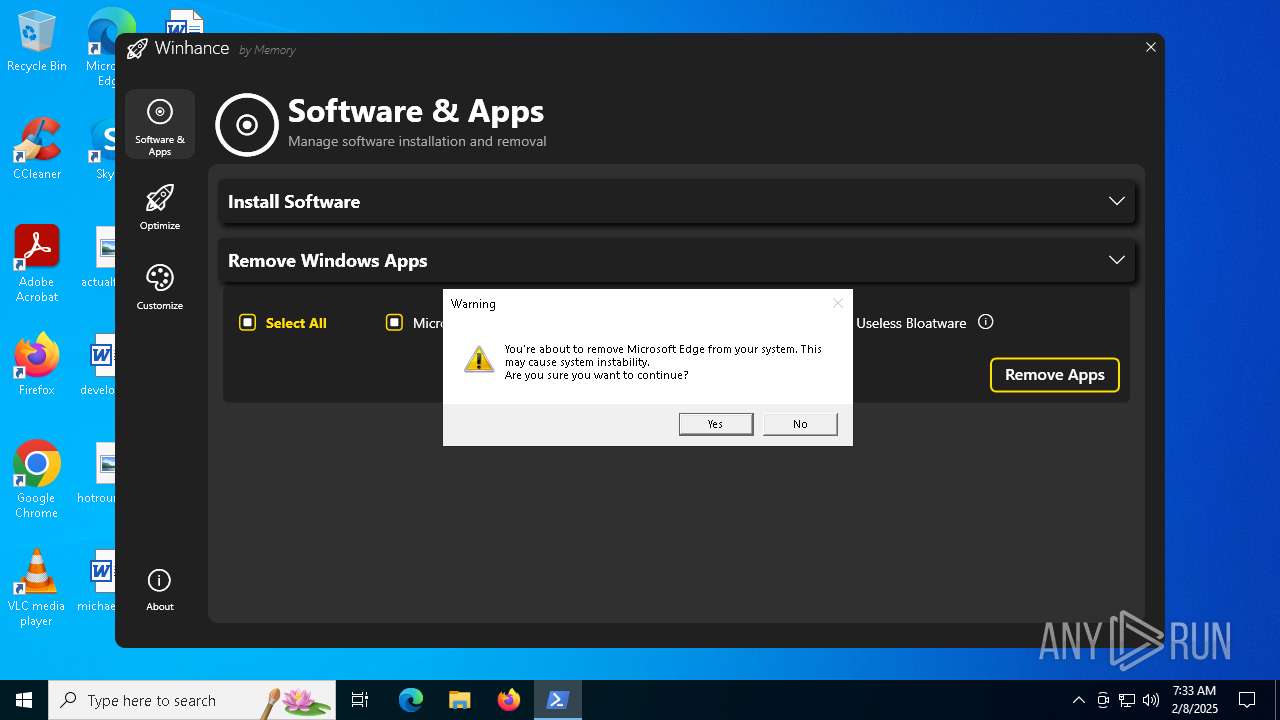
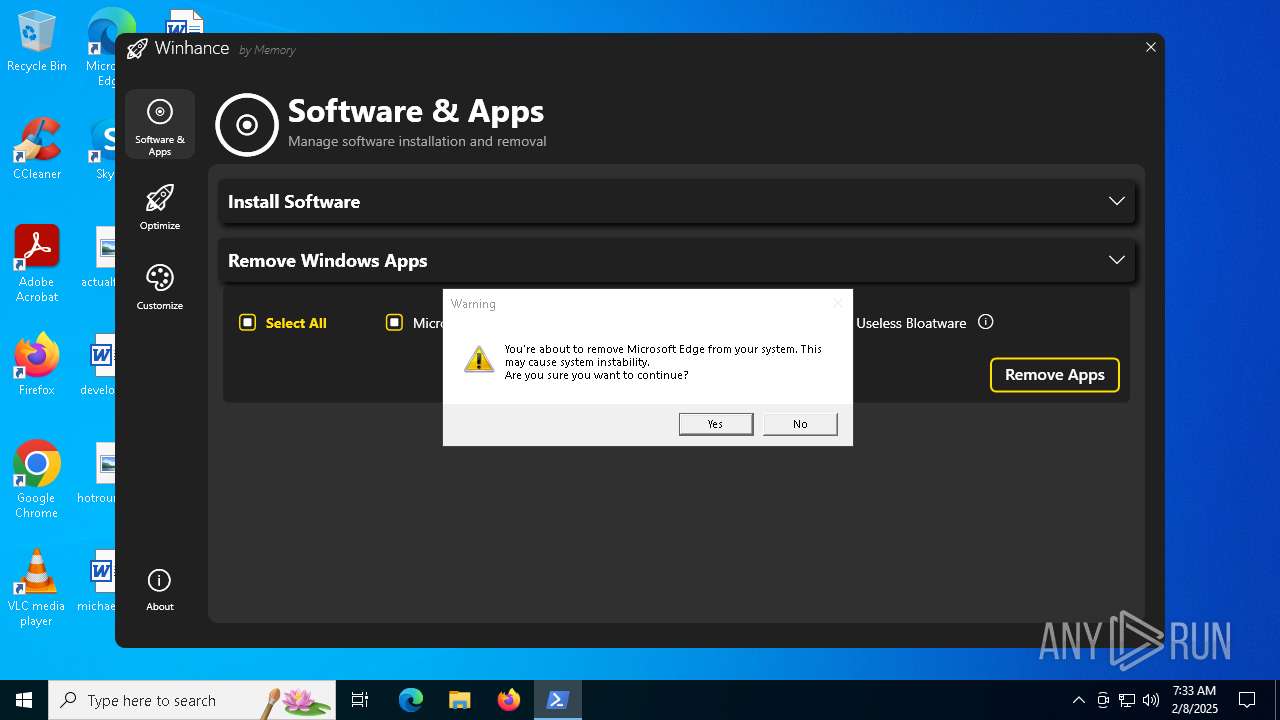
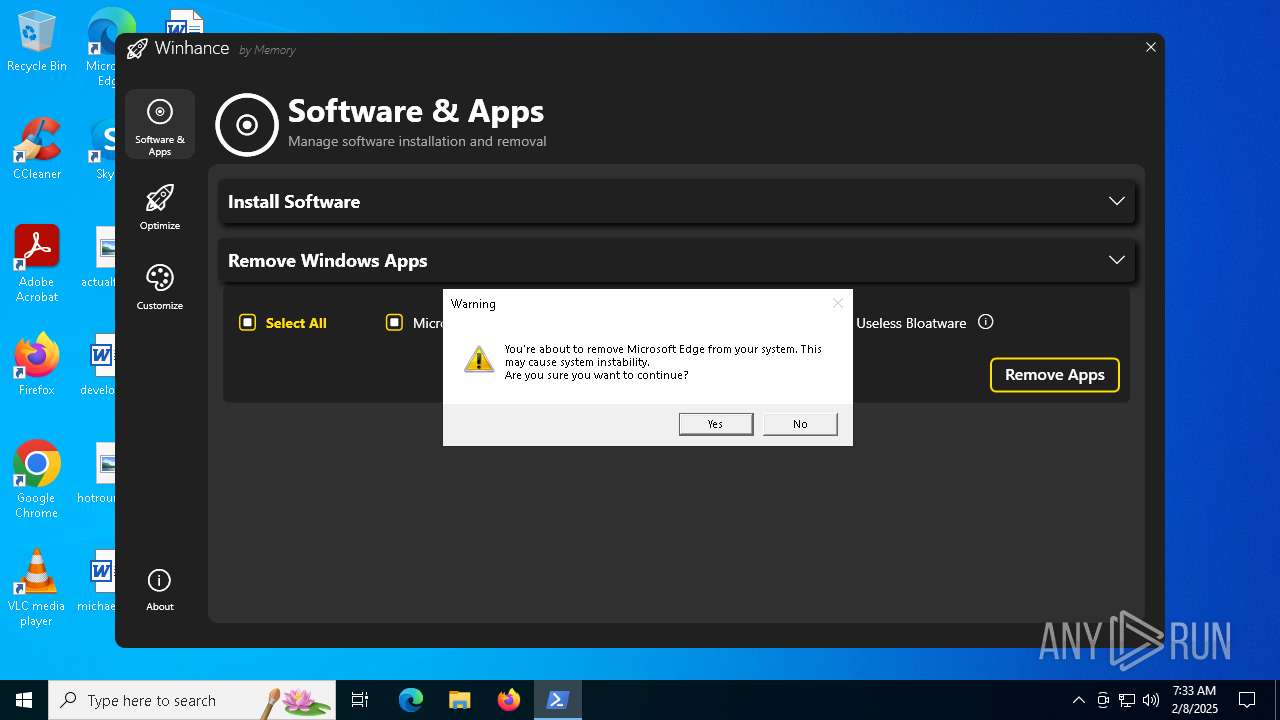
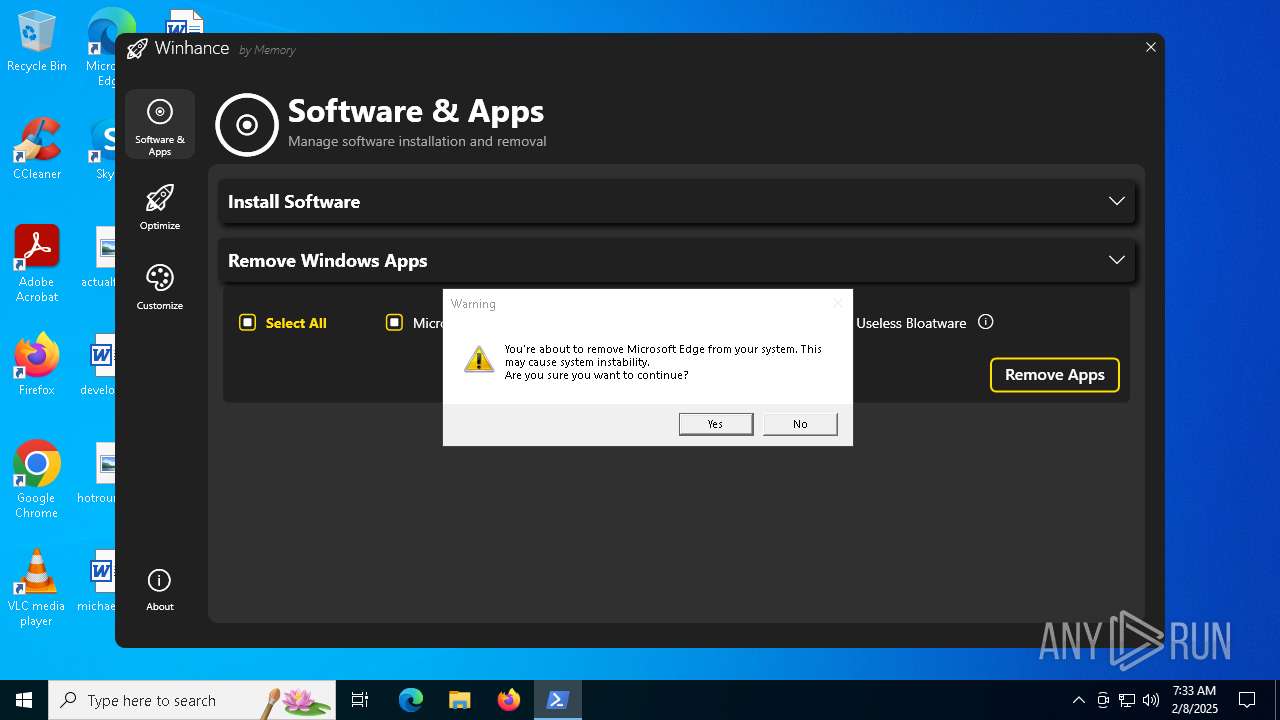
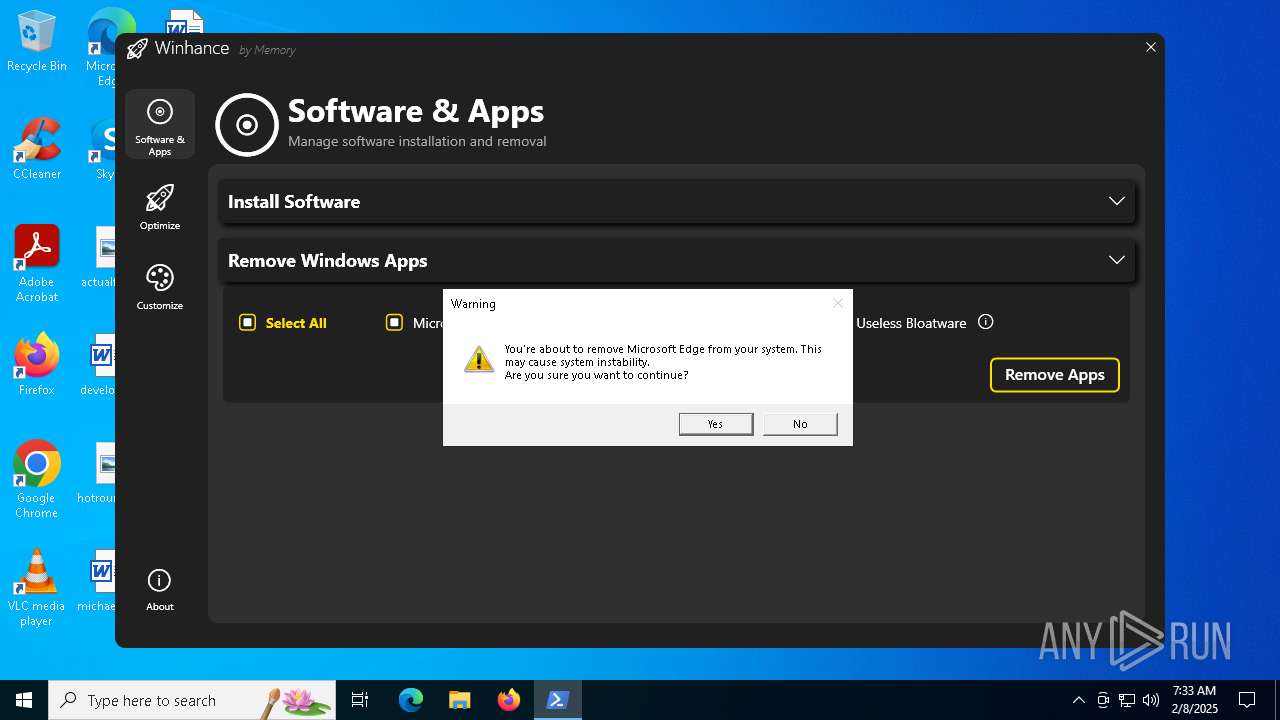
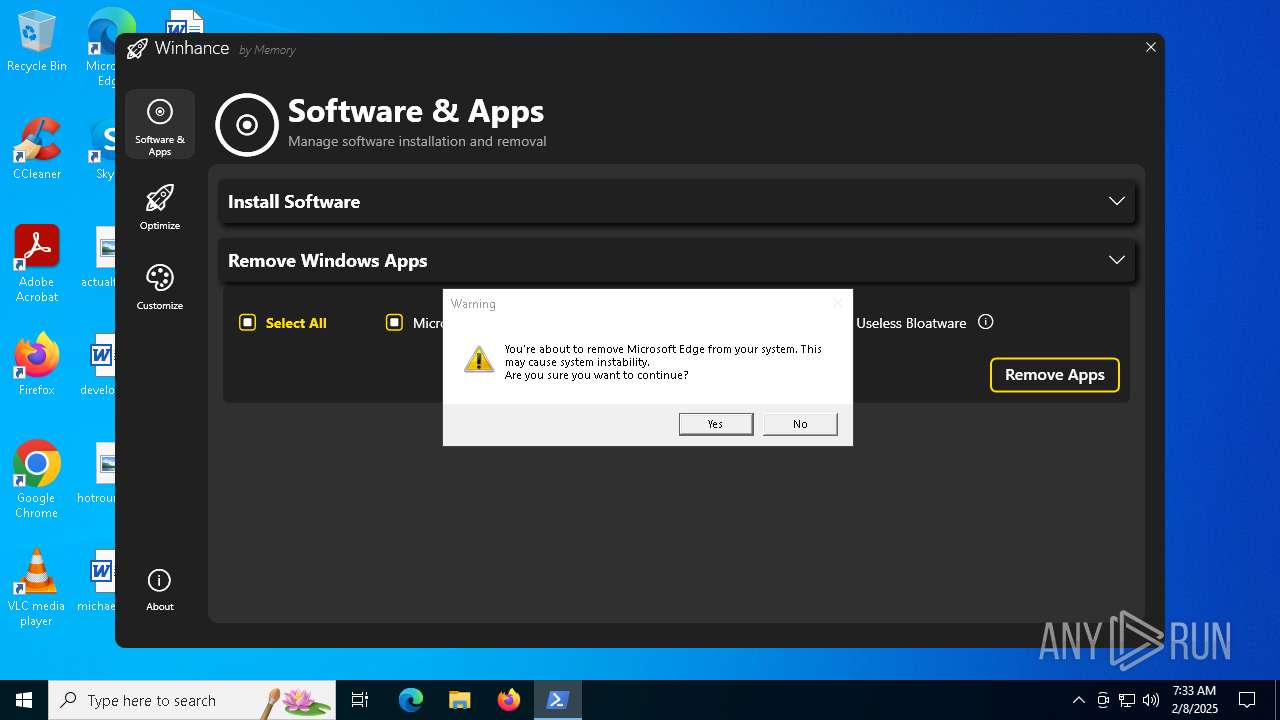
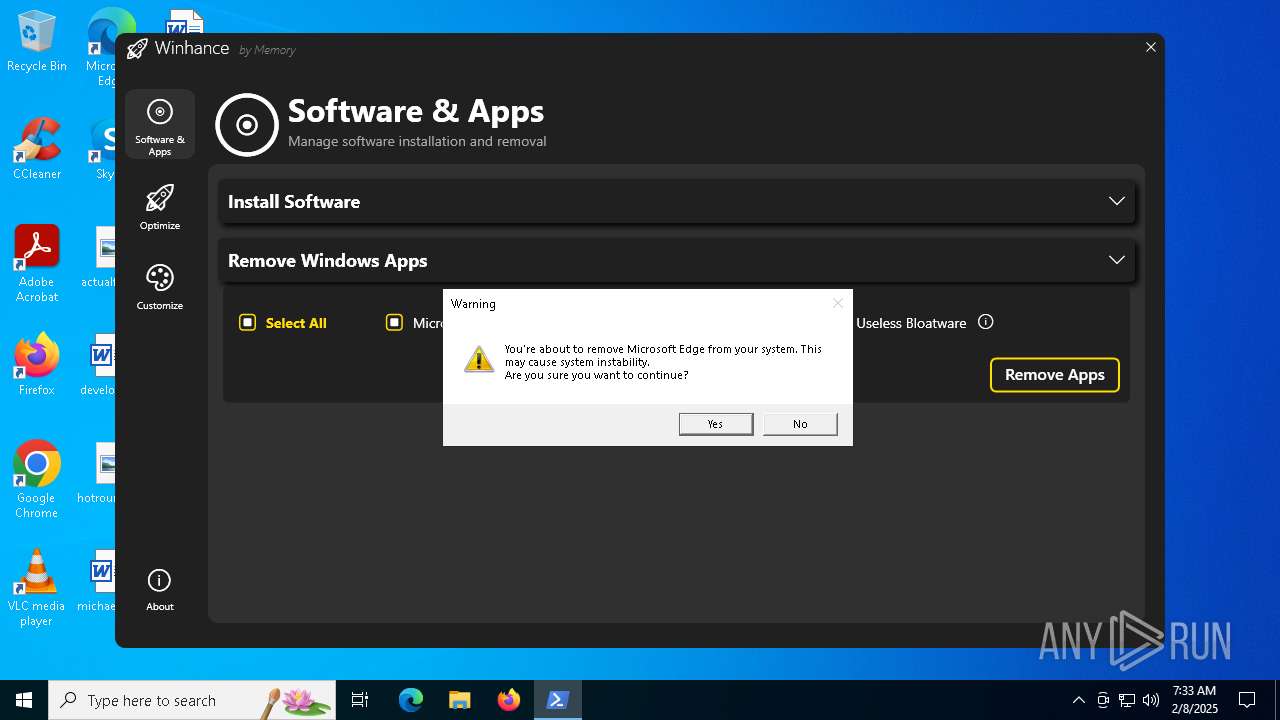
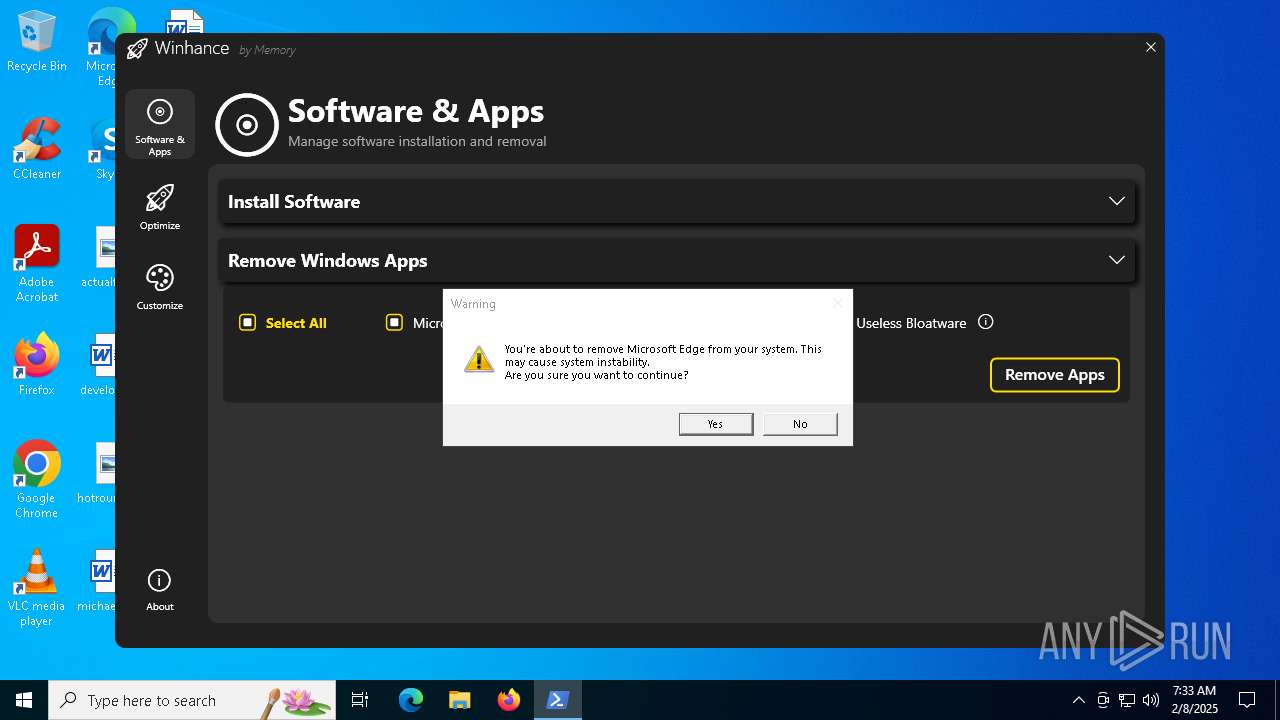
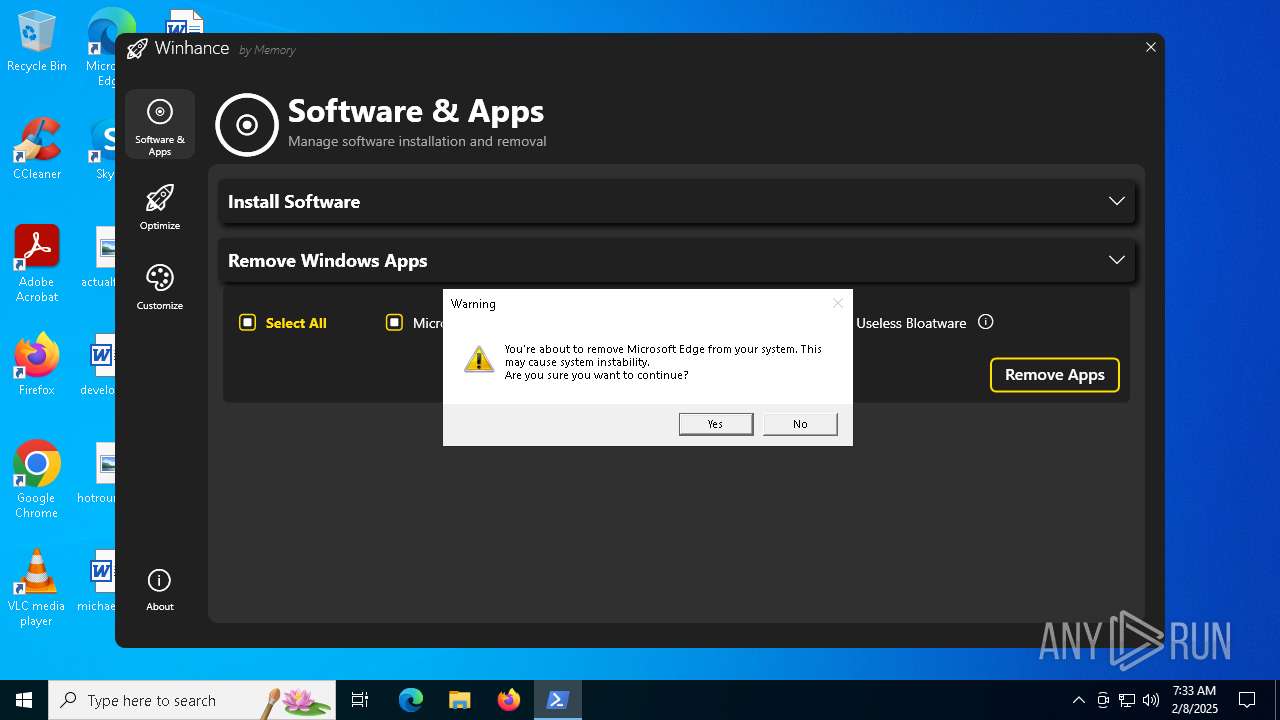
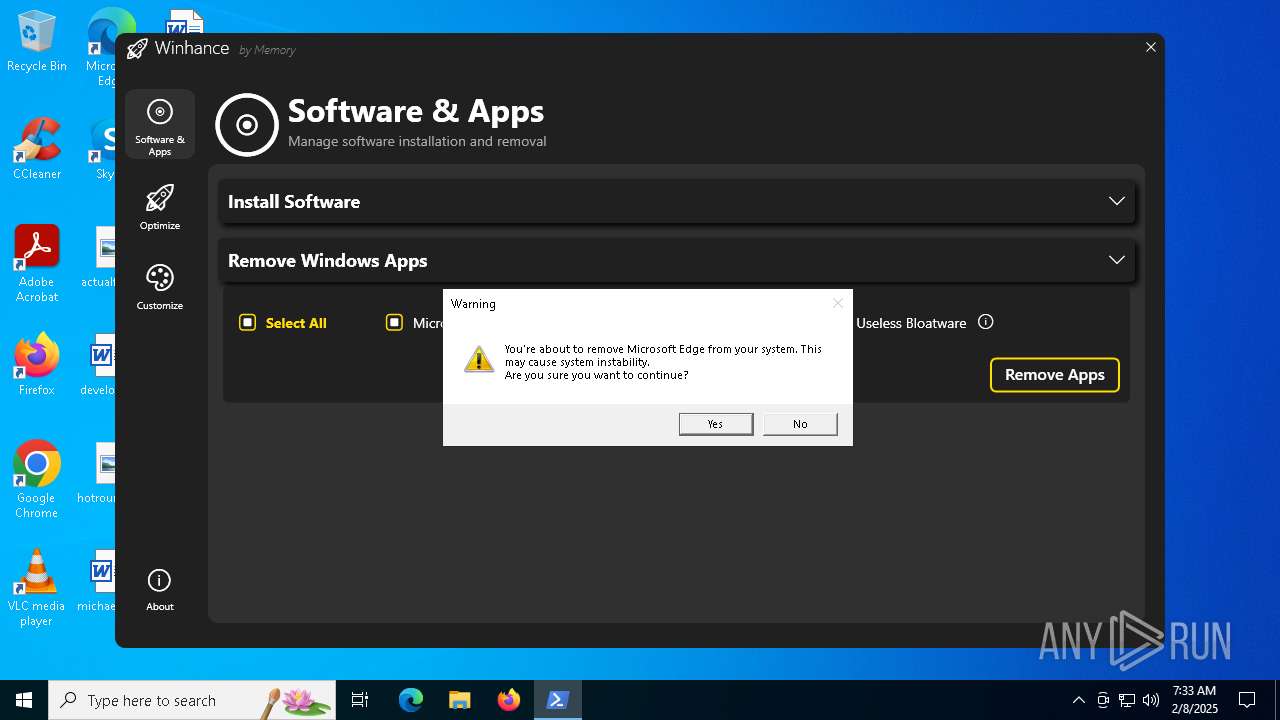
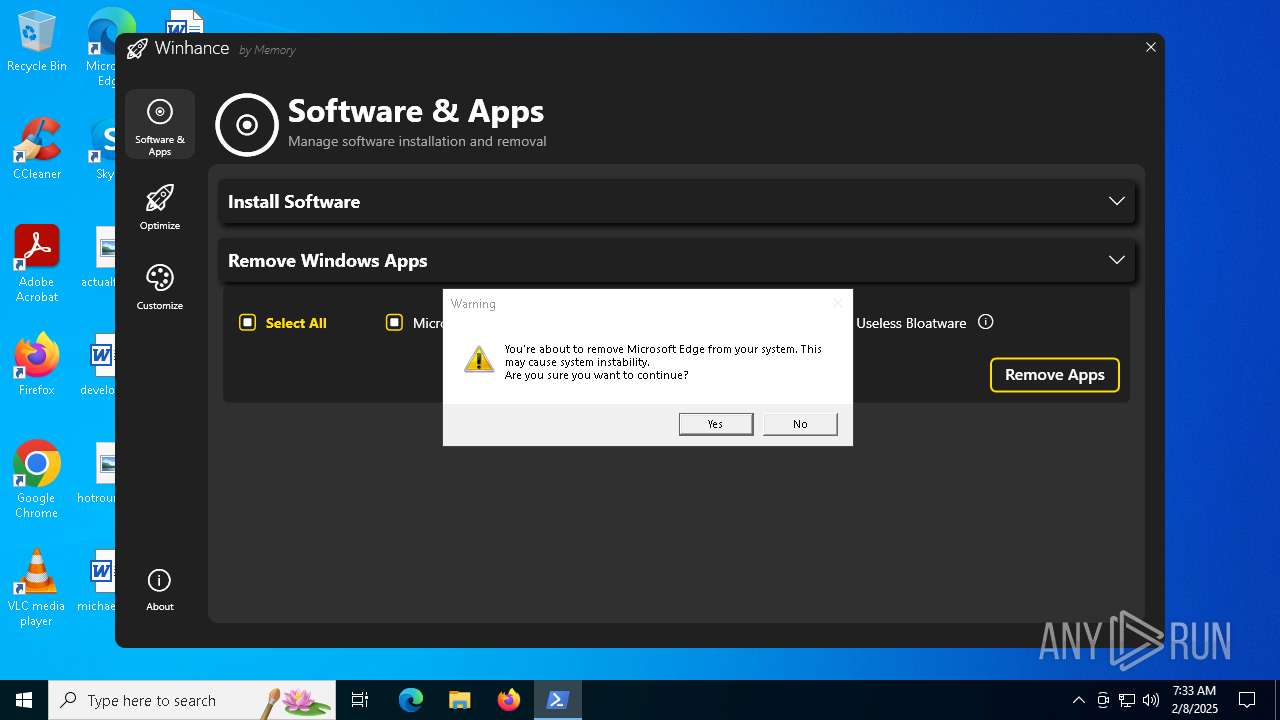
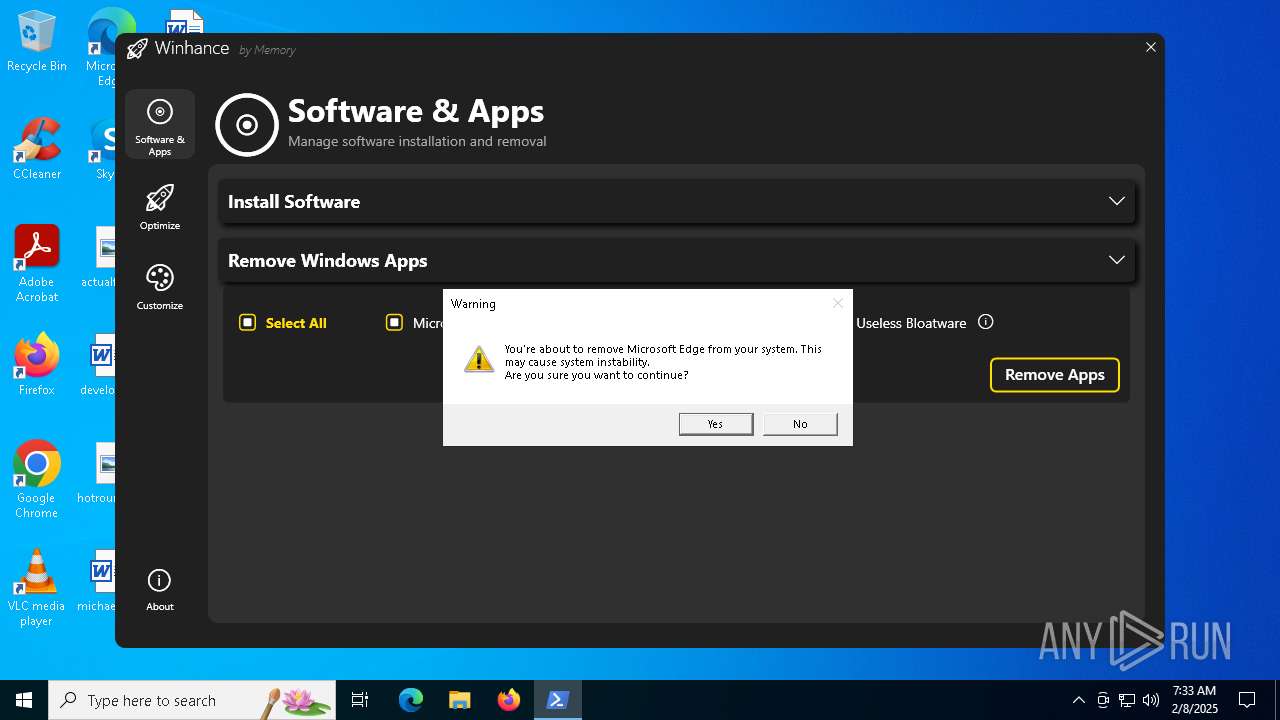
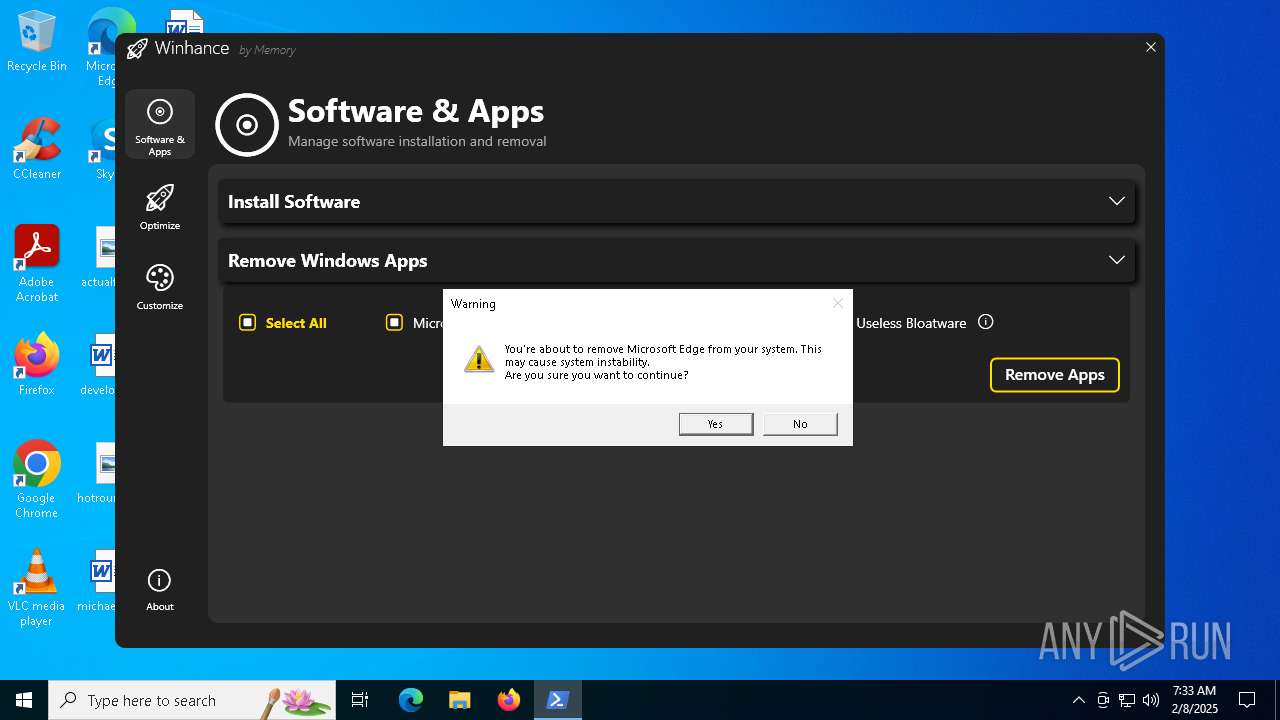
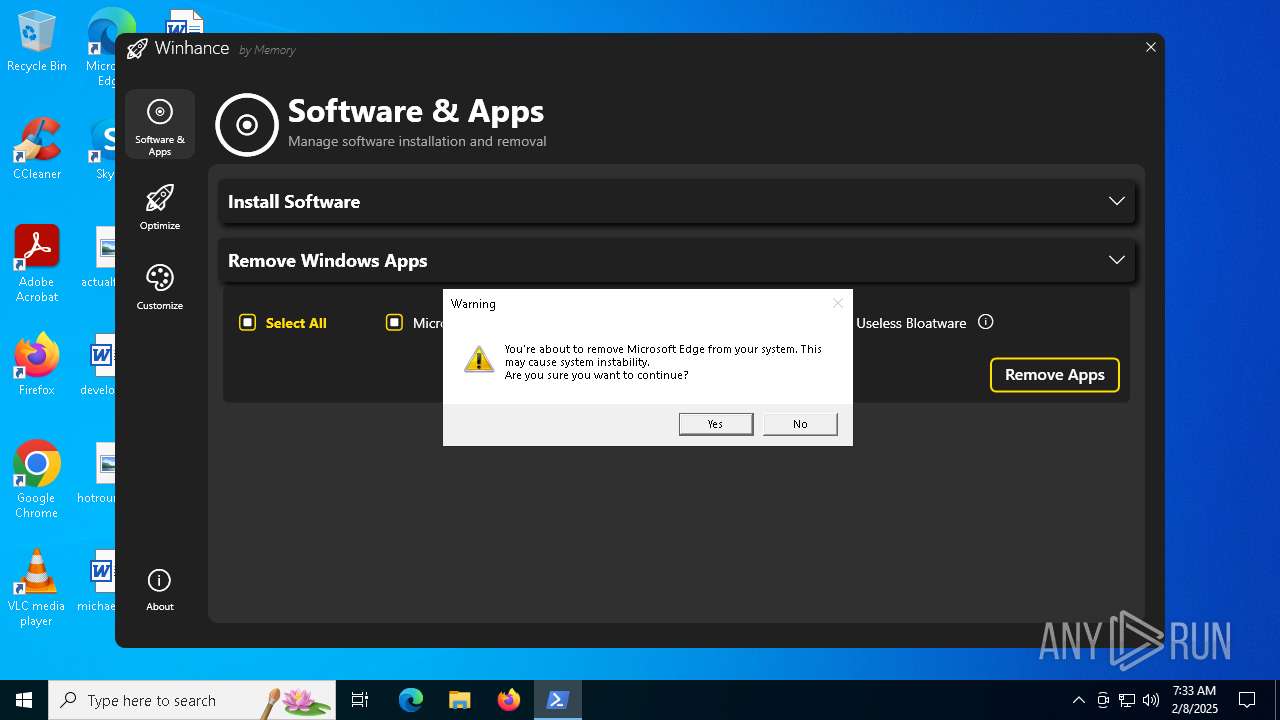
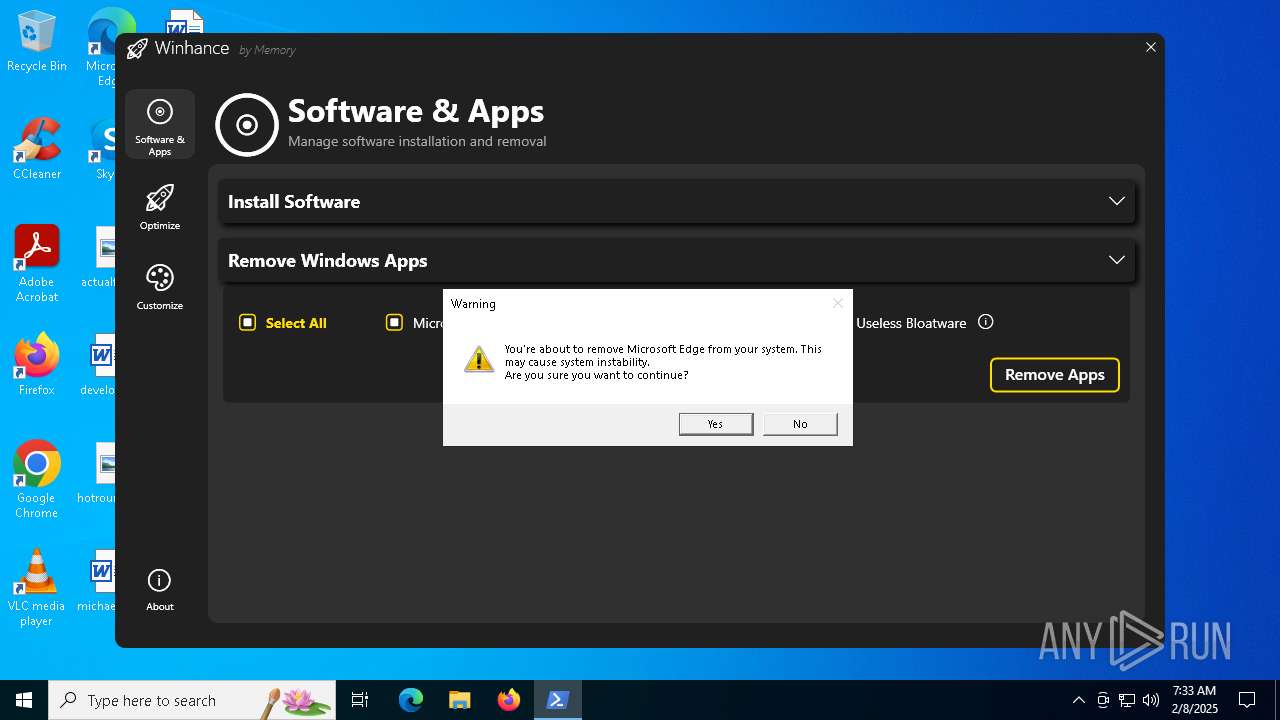
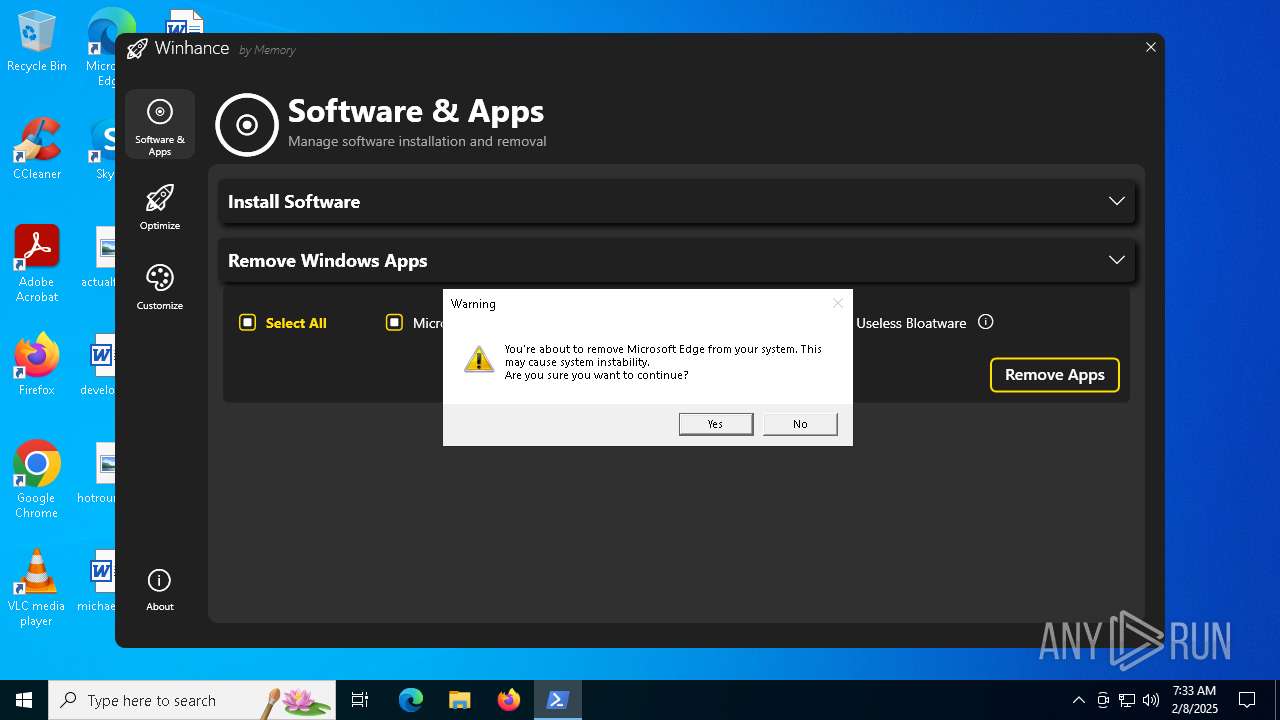
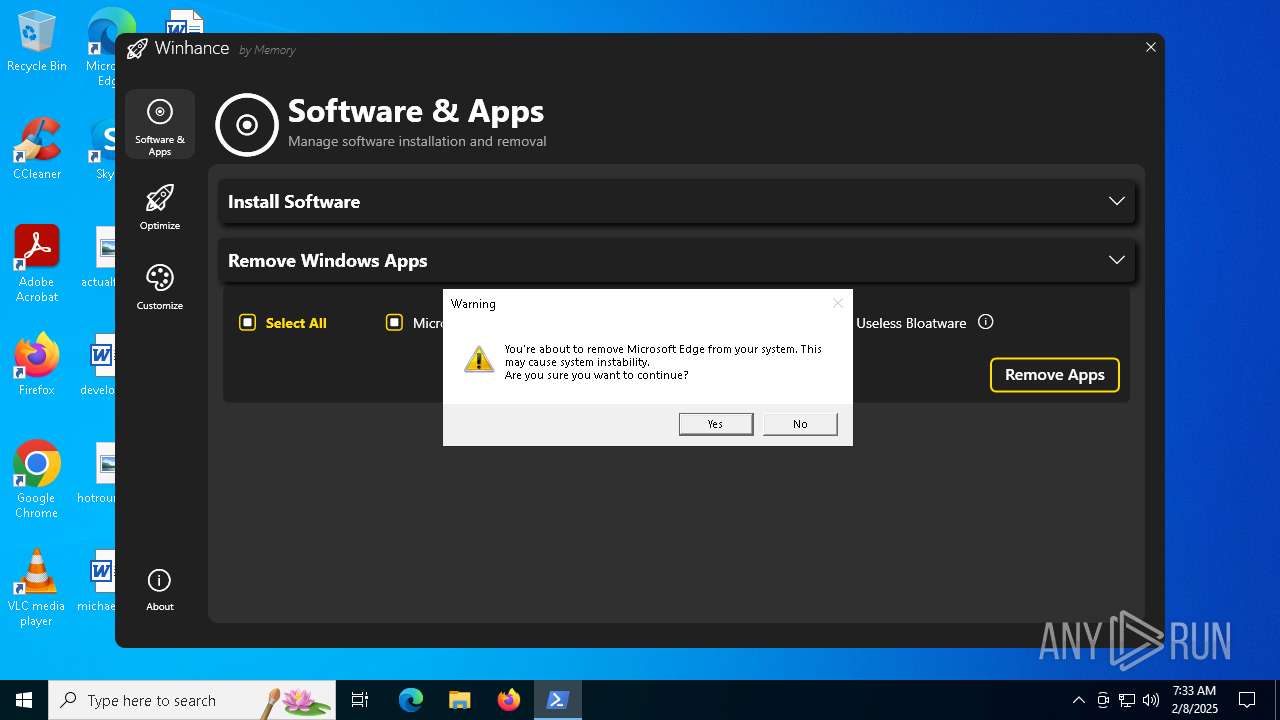
| File name: | Winhance.ps1 |
| Full analysis: | https://app.any.run/tasks/1cb06187-2d48-42fa-819d-91c2e27b77e4 |
| Verdict: | Malicious activity |
| Analysis date: | February 08, 2025, 07:31:08 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | 60CF39CDA00FC2FCA602B924EC1D5700 |
| SHA1: | CE16EB16FA02AD3A2706870673890945618A791A |
| SHA256: | B3B6AEC0DA55A5BFA2FCEE847DBEEF5A5EE327AC2E5F7886629B637B6F7F8954 |
| SSDEEP: | 3072:IC2nUjV7vP5uxu1RkswSiRyw7sVuEK78qpfGdnZYKGwNLn/uVLgoUiqCtnewM:t2ngV7vP/SsVuEKVfGdnZnVn/igtp |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 4628)
- powershell.exe (PID: 3080)
Changes powershell execution policy (Bypass)
- powershell.exe (PID: 4628)
Run PowerShell with an invisible window
- powershell.exe (PID: 3080)
SUSPICIOUS
CSC.EXE is used to compile C# code
- csc.exe (PID: 3724)
- csc.exe (PID: 2928)
- csc.exe (PID: 3436)
- csc.exe (PID: 4716)
Executable content was dropped or overwritten
- csc.exe (PID: 3724)
- csc.exe (PID: 3436)
- csc.exe (PID: 2928)
- csc.exe (PID: 4716)
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 4628)
Checks a user's role membership (POWERSHELL)
- powershell.exe (PID: 4628)
- powershell.exe (PID: 3080)
Application launched itself
- powershell.exe (PID: 4628)
The process bypasses the loading of PowerShell profile settings
- powershell.exe (PID: 4628)
The process executes Powershell scripts
- powershell.exe (PID: 4628)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 3080)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 3080)
INFO
Create files in a temporary directory
- csc.exe (PID: 3724)
- cvtres.exe (PID: 4136)
- csc.exe (PID: 2928)
- cvtres.exe (PID: 4264)
- cvtres.exe (PID: 3532)
- csc.exe (PID: 3436)
- csc.exe (PID: 4716)
- cvtres.exe (PID: 3364)
Checks supported languages
- csc.exe (PID: 3724)
- cvtres.exe (PID: 4136)
- csc.exe (PID: 2928)
- cvtres.exe (PID: 4264)
- csc.exe (PID: 3436)
- cvtres.exe (PID: 3532)
- csc.exe (PID: 4716)
- cvtres.exe (PID: 3364)
Reads the machine GUID from the registry
- csc.exe (PID: 3724)
- csc.exe (PID: 2928)
- csc.exe (PID: 3436)
- csc.exe (PID: 4716)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 3080)
Creates files in the program directory
- powershell.exe (PID: 3080)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3080)
Reads mouse settings
- powershell.exe (PID: 3080)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xaml | | | Microsoft Extensible Application Markup Language (100) |
|---|
Total processes
128
Monitored processes
12
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2928 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\uptfuzzq.cmdline" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 3080 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -NoProfile -WindowStyle Hidden -ExecutionPolicy Bypass -File "C:\Users\admin\Desktop\Winhance.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3364 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESA0C7.tmp" "c:\Users\admin\AppData\Local\Temp\f20a5v2l\CSC9A8F1FB66C514C628829D7AB04D4B48.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
| 3436 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\3xtywtyf\3xtywtyf.cmdline" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 3532 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES9FFC.tmp" "c:\Users\admin\AppData\Local\Temp\3xtywtyf\CSCC82E3F31A5894B89A1CA7E3126DB7A29.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
| 3724 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\e5g5fkoq.cmdline" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 4136 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES8F04.tmp" "c:\Users\admin\AppData\Local\Temp\CSCCCB2E3713BFE4DDEA19F4D5334C3D010.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
| 4264 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES8FA1.tmp" "c:\Users\admin\AppData\Local\Temp\CSCEC3FC73350BA4AC989387A90C76233E.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
| 4320 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4500 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
15 238
Read events
15 238
Write events
0
Delete events
0
Modification events
Executable files
4
Suspicious files
17
Text files
16
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4628 | powershell.exe | C:\Users\admin\AppData\Local\Temp\e5g5fkoq.cmdline | text | |
MD5:29FCA6068AC37D9655F2C6EE7008BD1A | SHA256:25679ED281A2A2B61356AFB9EA6E4AFADAF7FF218AE07A77855EA1A4373FD186 | |||
| 2928 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSCEC3FC73350BA4AC989387A90C76233E.TMP | binary | |
MD5:BA167B7FDEF29E6F2A603FBF488BA783 | SHA256:FEAEB5560D7B42BC5C90B5F8B13C0B134098C22B9FFEE5B7B9FFEE408F2998E8 | |||
| 4628 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:11A32DDF3E016C881FEFB37669CC9196 | SHA256:C31F6FD3E05D38CFC5D9FDA3B6225ACB03B19750140C3CC500C15A050CBE667F | |||
| 4628 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF1379c7.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 4628 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_hvgvoodd.hvh.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4628 | powershell.exe | C:\Users\admin\AppData\Local\Temp\uptfuzzq.0.cs | text | |
MD5:192212FD8703F800C49BA96F01932522 | SHA256:319AF060598B22FCEA608F61EF06539A09578B4AA8CAF3DFD1F5619A3D9F33CC | |||
| 3724 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSCCCB2E3713BFE4DDEA19F4D5334C3D010.TMP | binary | |
MD5:73C609C8EAC06063C7A21DE95FDA9513 | SHA256:24FA0CEF715DABD44C0EA2C6F30A856B66607A7E41DBA7008CCA6BAB81F9EBAB | |||
| 4628 | powershell.exe | C:\Users\admin\AppData\Local\Temp\e5g5fkoq.0.cs | text | |
MD5:0E2CDC2657BE537834C77429EC55CF02 | SHA256:3817813F399AD49DA2ED1F1FF3B044D8E80934C6E83E9FFFE06E6ECDFE1195AE | |||
| 3724 | csc.exe | C:\Users\admin\AppData\Local\Temp\e5g5fkoq.dll | executable | |
MD5:0764408C98593A5DEFE8B1E0CA3F8F50 | SHA256:8ADDE087D57D0FC0159DC87724114CDC7DDD84D848BB29F106E34F7177953AAE | |||
| 4136 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES8F04.tmp | binary | |
MD5:EF0A67709C6404ECD529F037D3759788 | SHA256:7C6BB872697FA37273A7BA24CF2B2A1CF572E96F9E69FDAF1032193FC88868A3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
19
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5392 | svchost.exe | GET | 200 | 23.32.238.112:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.32.238.112:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5392 | svchost.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5392 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5392 | svchost.exe | 23.32.238.112:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.32.238.112:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5392 | svchost.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3976 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5392 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |