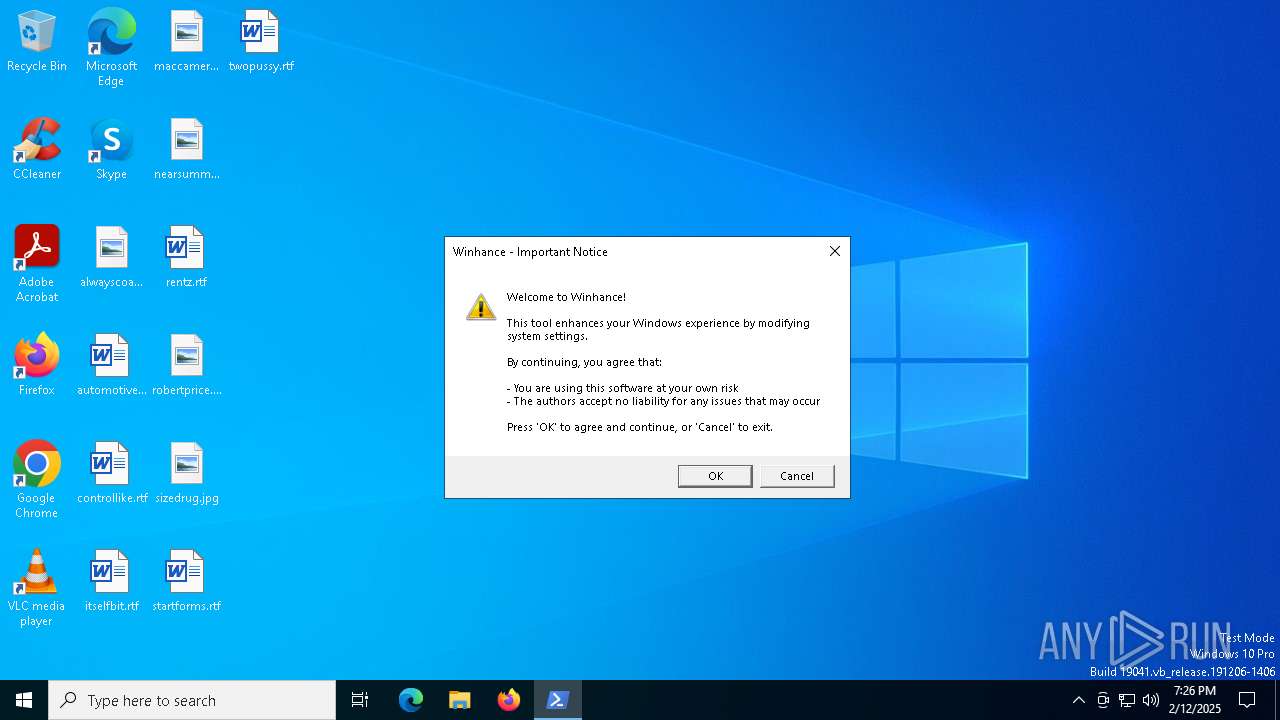
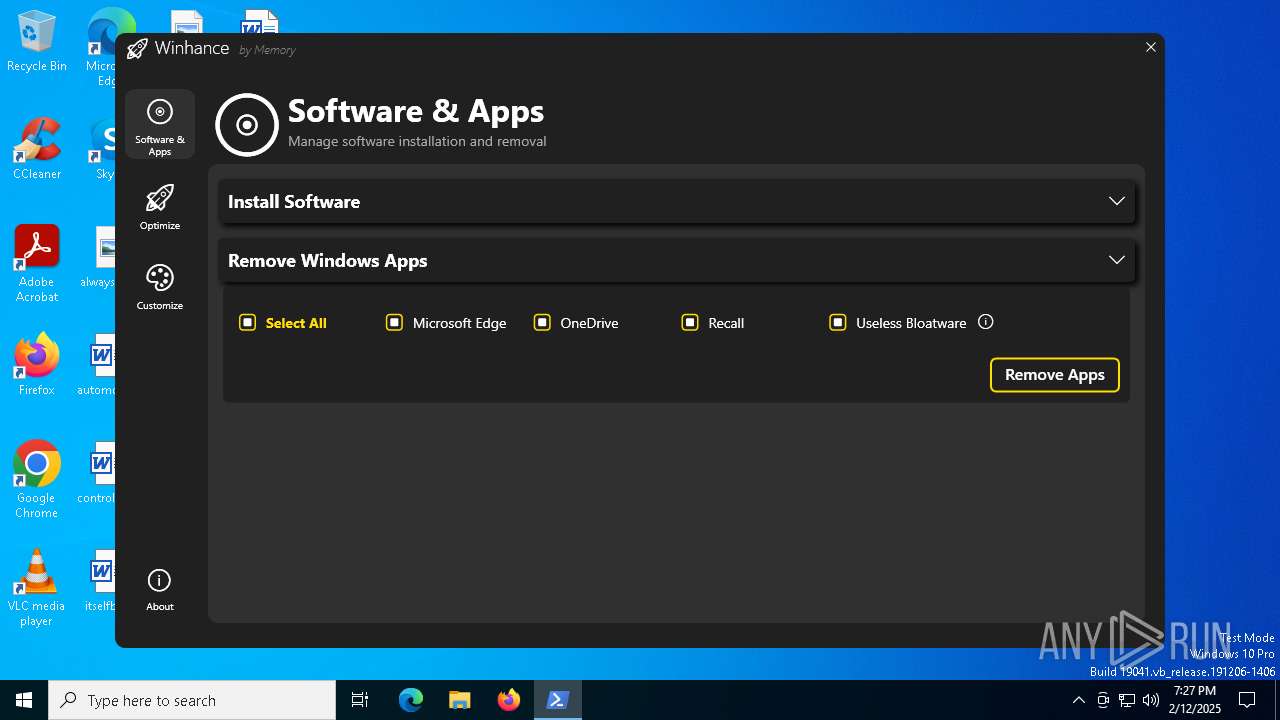
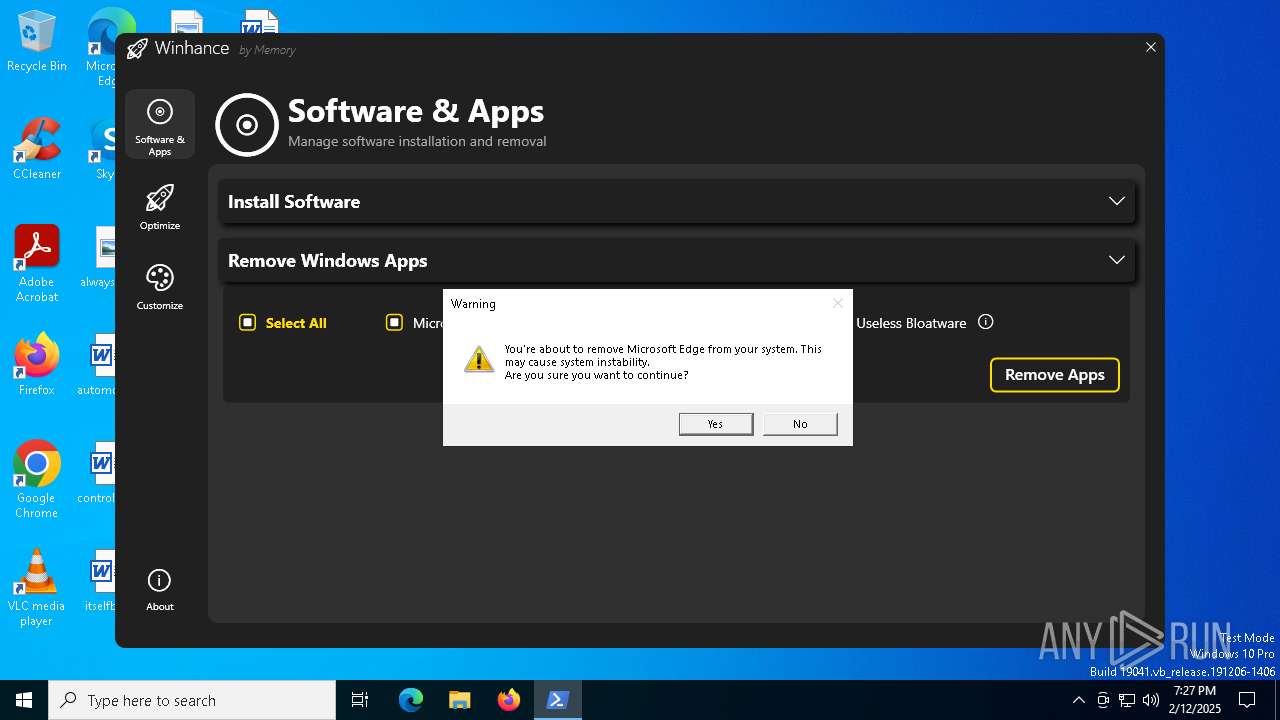
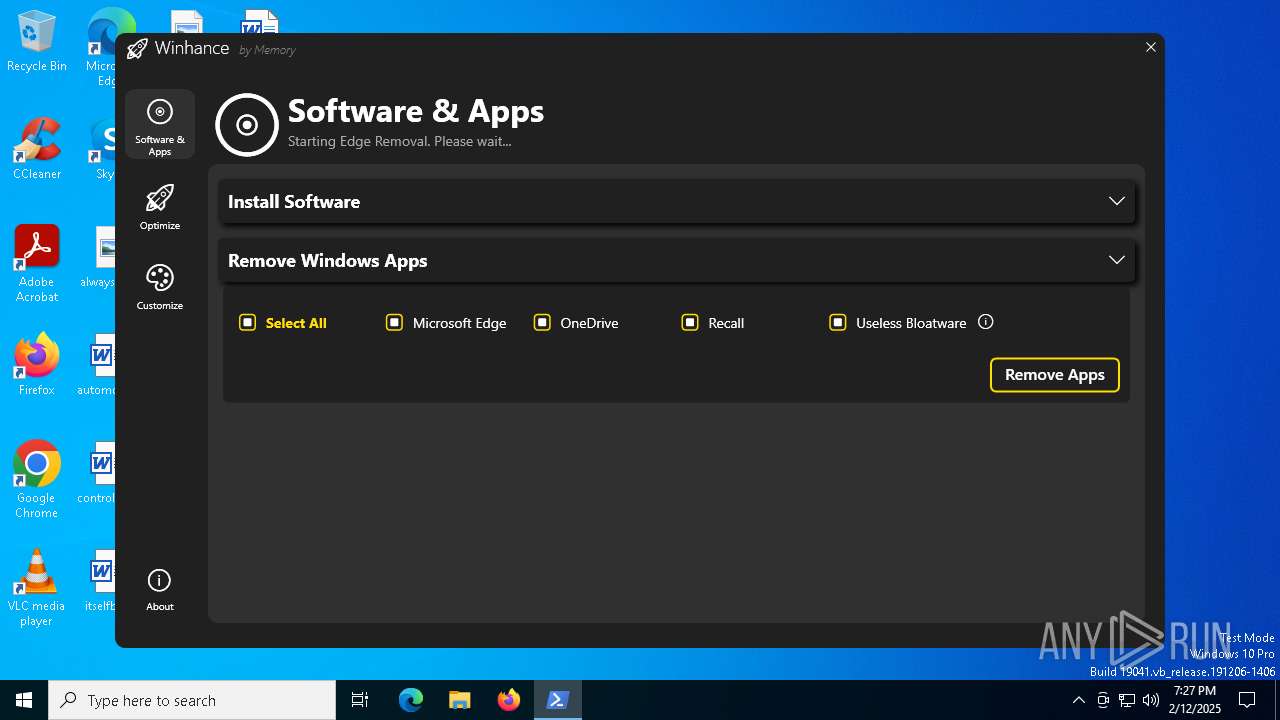
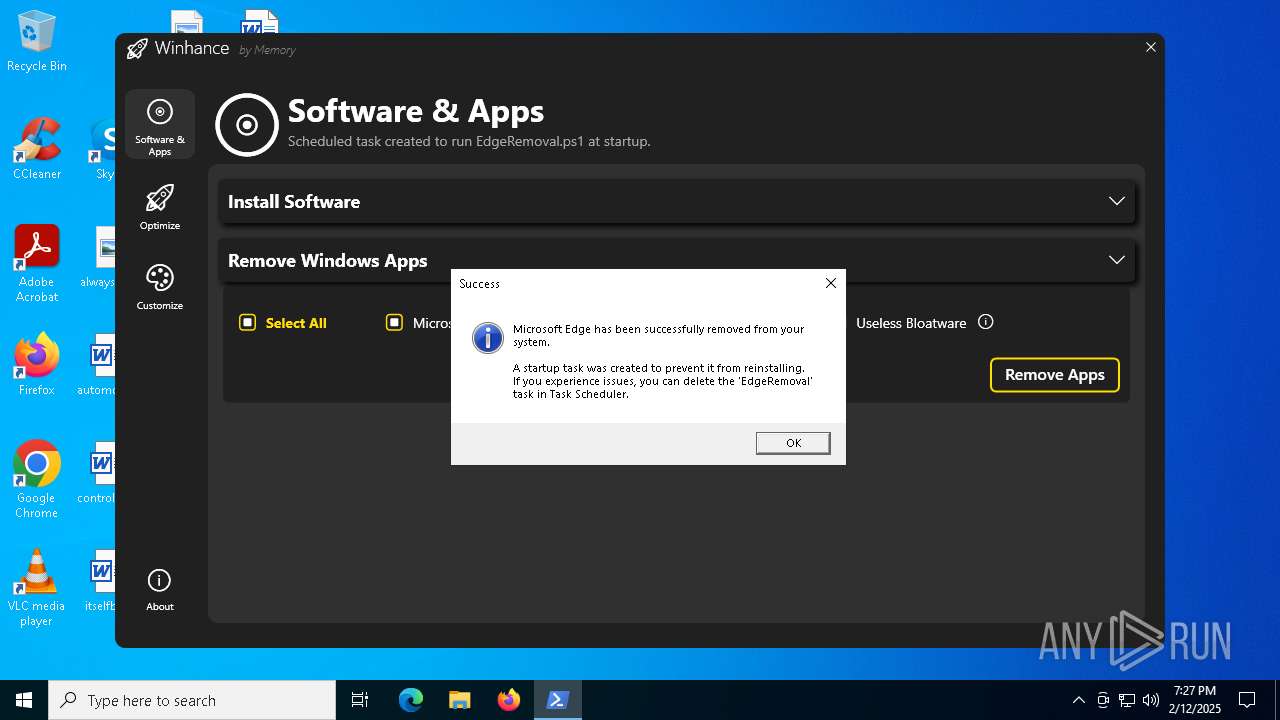
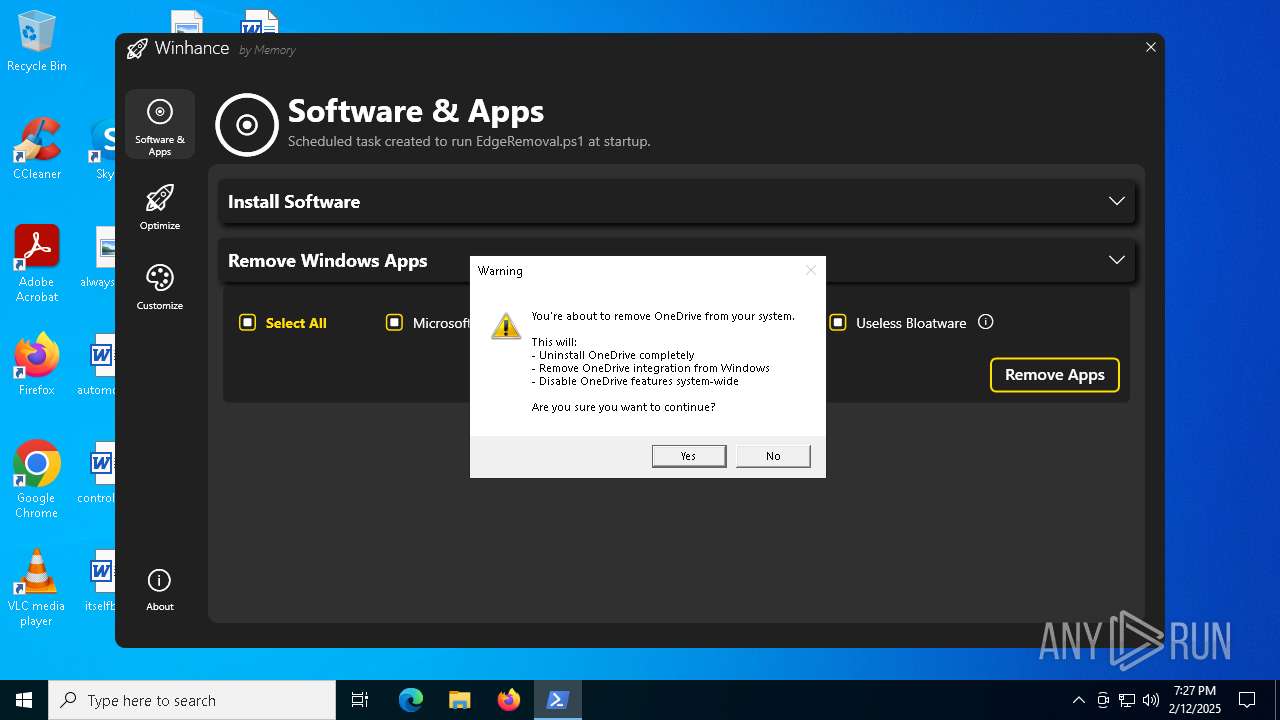
| File name: | Winhance.ps1 |
| Full analysis: | https://app.any.run/tasks/109e6a91-761a-4440-bc35-bdcdb55c8878 |
| Verdict: | Malicious activity |
| Analysis date: | February 12, 2025, 19:26:31 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | 60CF39CDA00FC2FCA602B924EC1D5700 |
| SHA1: | CE16EB16FA02AD3A2706870673890945618A791A |
| SHA256: | B3B6AEC0DA55A5BFA2FCEE847DBEEF5A5EE327AC2E5F7886629B637B6F7F8954 |
| SSDEEP: | 3072:IC2nUjV7vP5uxu1RkswSiRyw7sVuEK78qpfGdnZYKGwNLn/uVLgoUiqCtnewM:t2ngV7vP/SsVuEKVfGdnZnVn/igtp |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 6152)
- powershell.exe (PID: 6932)
Changes powershell execution policy (Bypass)
- powershell.exe (PID: 6152)
Run PowerShell with an invisible window
- powershell.exe (PID: 6932)
SUSPICIOUS
Executable content was dropped or overwritten
- csc.exe (PID: 6588)
- csc.exe (PID: 6752)
- csc.exe (PID: 7084)
- csc.exe (PID: 7132)
CSC.EXE is used to compile C# code
- csc.exe (PID: 6588)
- csc.exe (PID: 6752)
- csc.exe (PID: 7084)
- csc.exe (PID: 7132)
Checks a user's role membership (POWERSHELL)
- powershell.exe (PID: 6152)
- powershell.exe (PID: 6932)
Application launched itself
- powershell.exe (PID: 6152)
- MicrosoftEdgeUpdate.exe (PID: 6708)
The process bypasses the loading of PowerShell profile settings
- powershell.exe (PID: 6152)
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 6152)
The process executes Powershell scripts
- powershell.exe (PID: 6152)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 6932)
Gets path to any of the special folders (POWERSHELL)
- powershell.exe (PID: 6932)
Uses REG/REGEDIT.EXE to modify registry
- powershell.exe (PID: 6932)
- cmd.exe (PID: 6848)
- cmd.exe (PID: 6244)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 6932)
Process drops legitimate windows executable
- MicrosoftEdgeUpdate.exe (PID: 6708)
Hides command output
- cmd.exe (PID: 6244)
- cmd.exe (PID: 6848)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 6932)
INFO
Checks supported languages
- csc.exe (PID: 6588)
- csc.exe (PID: 6752)
- cvtres.exe (PID: 6716)
- cvtres.exe (PID: 6784)
- cvtres.exe (PID: 7104)
- csc.exe (PID: 7084)
- csc.exe (PID: 7132)
- cvtres.exe (PID: 7152)
Create files in a temporary directory
- cvtres.exe (PID: 6716)
- csc.exe (PID: 6588)
- csc.exe (PID: 6752)
- cvtres.exe (PID: 6784)
- csc.exe (PID: 7084)
- csc.exe (PID: 7132)
- cvtres.exe (PID: 7152)
- OneDriveSetup.exe (PID: 4300)
Reads the machine GUID from the registry
- csc.exe (PID: 6588)
- csc.exe (PID: 6752)
- csc.exe (PID: 7084)
- csc.exe (PID: 7132)
The sample compiled with english language support
- MicrosoftEdgeUpdate.exe (PID: 6708)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 6932)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6932)
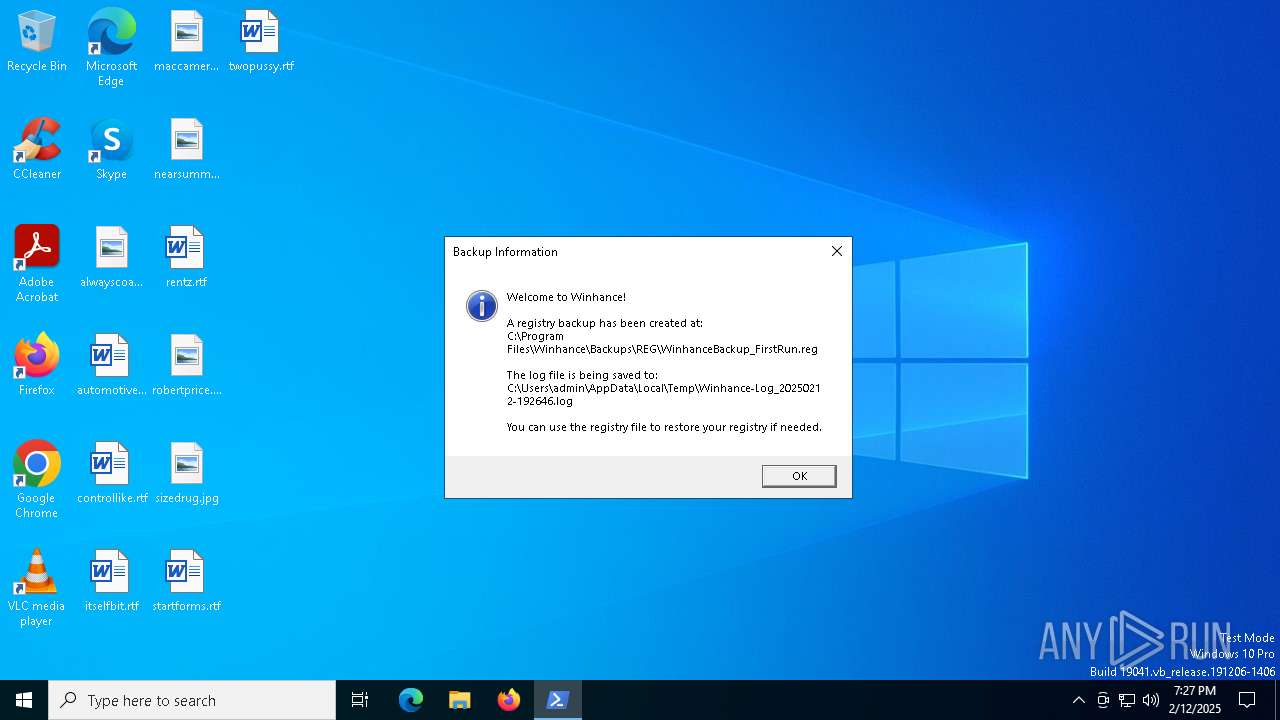
Creates files in the program directory
- powershell.exe (PID: 6932)
Reads mouse settings
- powershell.exe (PID: 6932)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6932)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xaml | | | Microsoft Extensible Application Markup Language (100) |
|---|
Total processes
154
Monitored processes
27
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 932 | "C:\WINDOWS\system32\reg.exe" add HKLM\SOFTWARE\Microsoft\EdgeUpdate /v DoNotUpdateToEdgeWithChromium /t REG_DWORD /d 1 /f | C:\Windows\System32\reg.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2076 | "C:\WINDOWS\system32\reg.exe" add HKLM\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdateDev /v AllowUninstall /t REG_SZ /f | C:\Windows\System32\reg.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4300 | "C:\WINDOWS\SysWOW64\OneDriveSetup.exe" /uninstall | C:\Windows\SysWOW64\OneDriveSetup.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft OneDrive (32 bit) Setup Version: 19.043.0304.0013 Modules
| |||||||||||||||
| 6152 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass C:\Users\admin\AppData\Local\Temp\Winhance.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6160 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6180 | "C:\WINDOWS\system32\reg.exe" load HKU\S-1-5-21-1693682860-607145093-2874071422-500 C:\Users\Administrator\NTUSER.DAT | C:\Windows\System32\reg.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6244 | "C:\WINDOWS\system32\cmd.exe" /c "reg delete "HKCU\Software\Microsoft\Windows\CurrentVersion\Uninstall\Microsoft EdgeWebView" /f >nul 2>&1" | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6316 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6320 | reg delete "HKCU\Software\Microsoft\Windows\CurrentVersion\Uninstall\Microsoft EdgeWebView" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6340 | "C:\WINDOWS\system32\cmd.exe" /c | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
21 561
Read events
21 444
Write events
28
Delete events
89
Modification events
| (PID) Process: | (932) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate |
| Operation: | write | Name: | DoNotUpdateToEdgeWithChromium |
Value: 1 | |||
| (PID) Process: | (2076) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdateDev |
| Operation: | write | Name: | AllowUninstall |
Value: | |||
| (PID) Process: | (6932) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\Clients\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\Commands\on-logon-autolaunch |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6932) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\Clients\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\Commands |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6932) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\Clients\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6932) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\Clients |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6932) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\ClientState |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6932) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\proxy |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6932) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6932) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
6
Suspicious files
20
Text files
22
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6152 | powershell.exe | C:\Users\admin\AppData\Local\Temp\2qz1xlwz.0.cs | text | |
MD5:192212FD8703F800C49BA96F01932522 | SHA256:319AF060598B22FCEA608F61EF06539A09578B4AA8CAF3DFD1F5619A3D9F33CC | |||
| 6588 | csc.exe | C:\Users\admin\AppData\Local\Temp\2npisq3i.dll | executable | |
MD5:9CD06C4AE96507F30C58A0740978BA99 | SHA256:4479DE8E05B743CACEB937A8A322306E8E50D70E109C2979DB756562A898468A | |||
| 6152 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF135c5c.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 6716 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES7255.tmp | binary | |
MD5:FC3E179F0BF285945C6906251D2B9660 | SHA256:FBC915A91D4E884BDD99463B4D282AB1E4055C011A8985B7B5692B90346A43FA | |||
| 6752 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSCA62C8DD3E9FA42C6861F54E8F09C9DB3.TMP | binary | |
MD5:40EBAB9DA28FC00DAE5A8F77CA2BA4ED | SHA256:A346D4F8066999C5F4B2318A743937DDD06CD297BAA88C76BA42F42B52160B09 | |||
| 6752 | csc.exe | C:\Users\admin\AppData\Local\Temp\2qz1xlwz.out | text | |
MD5:A9682158102AFC28C868BD9A8C19A61E | SHA256:79E58CB9B956284147D5C9C57D482598C83C01E7B03464C69CA17C8EABA1321C | |||
| 6152 | powershell.exe | C:\Users\admin\AppData\Local\Temp\2qz1xlwz.cmdline | text | |
MD5:124AD005197D5AE375E5872D9F8D0C16 | SHA256:839D984563C53E0233365B1FC55FD52DE18630B658CD1D8B38DF8D05FD21EF9B | |||
| 6784 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES7301.tmp | binary | |
MD5:AC4B4E148EC5ABF6E8CFE2F9BD50369E | SHA256:0AD810F3E2AA5474EE04F22922ECD954B57006F964FE7B5149ACCCB5B94B2C47 | |||
| 6752 | csc.exe | C:\Users\admin\AppData\Local\Temp\2qz1xlwz.dll | executable | |
MD5:F897AD5D73D026E15EE68650B064E548 | SHA256:0A14FAB26B4093CAF2B3EBBA033F855FBFCD4FB9EA2A75F351B314E53C9F5C3F | |||
| 6152 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:AFFA01770C29464FC7A6A09B24EA4104 | SHA256:773D9BFB94EB8880736535B1F54C7A6DE9446C2E8DC46C5BC83F1AAF4E39454F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
36
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 104.124.11.187:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.45.69.233:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.52.56.216:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.52.56.216:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5536 | backgroundTaskHost.exe | GET | 200 | 23.52.56.216:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6908 | wermgr.exe | GET | 200 | 2.19.101.47:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6012 | SIHClient.exe | GET | 200 | 2.19.101.47:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6012 | SIHClient.exe | GET | 200 | 2.19.101.47:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6908 | wermgr.exe | GET | 200 | 104.124.11.187:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
372 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 104.124.11.187:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.45.69.233:80 | www.microsoft.com | AKAMAI-AS | US | whitelisted |
5064 | SearchApp.exe | 2.19.193.73:443 | www.bing.com | Akamai International B.V. | TR | whitelisted |
— | — | 23.52.56.216:80 | ocsp.digicert.com | AKAMAI-AS | NL | whitelisted |
1176 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1076 | svchost.exe | 2.19.106.8:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |